May 2006 doc IEEE 15 06 0242 00






























- Slides: 102

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Project: IEEE P 802. 15 Working Group for Wireless Personal Area Networks (WPANs) Submission Title: Ranging with Draft 2. Date Submitted: May 15, 2006 Source: Vern Brethour, Time Domain Corp Contact: Vern Brethour, Time Domain Corp Voice: +1 256. 428. 6331; E-Mail: vern. brethour@timedomain. com; Re: TG 4 a Abstract: Overview of Ranging issues with 15. 4 a Draft 2. Purpose: To inform and enable comment resolution on the recirculation LB 34. Notice: This document has been prepared to assist the IEEE P 802. 15. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) reserve(s) the right to add, amend or withdraw material contained herein. Release: The contributor acknowledges and accepts that this contribution becomes the property of IEEE and may be made publicly available by P 802. 15. TG 4 a 1 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Ranging was improved in Draft 2. • Draft 2 describes a device that would work if it were built. • Draft 2 still has a few rough edges. • This presentation is to aid comment resolution on LB 34. TG 4 a 2 Vern Brethour

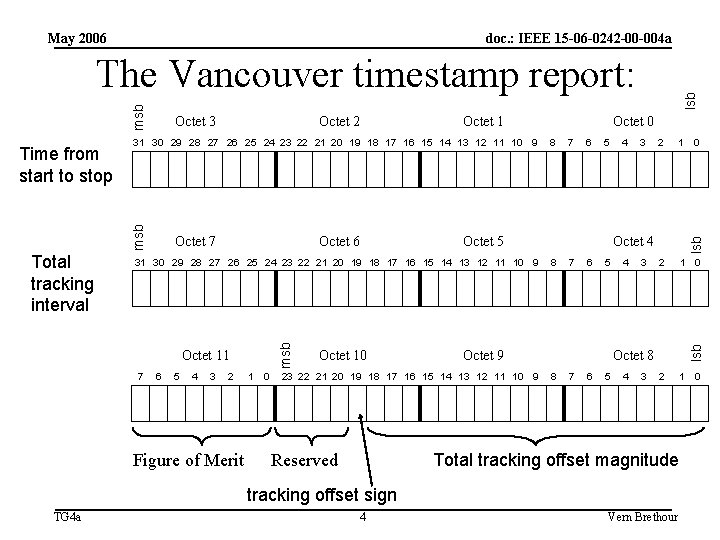
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Draft 2 uses the timestamp report that was adopted in Vancouver. • For Draft 2 we had clear guidance about how to construct the timestamp fields: The following slide represents the minutes of Vancouver Thursday PM 1. • The Vancouver timestamp report is a 12 octet affair consisting of 3 numbers & an 8 bit figure of Merit. TG 4 a 3 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Octet 1 Octet 6 7 6 5 4 3 2 Figure of Merit 1 0 8 7 6 5 Octet 5 31 30 29 28 27 26 25 24 23 22 21 20 19 18 17 16 15 14 13 12 11 10 9 Octet 11 Octet 10 4 3 2 1 2 1 Octet 4 8 7 6 5 Octet 9 23 22 21 20 19 18 17 16 15 14 13 12 11 10 9 lsb Octet 0 4 3 Octet 8 8 7 6 5 4 3 Total tracking offset magnitude Reserved tracking offset sign TG 4 a 4 0 lsb Octet 7 msb Total tracking interval Octet 2 31 30 29 28 27 26 25 24 23 22 21 20 19 18 17 16 15 14 13 12 11 10 9 msb Time from start to stop Octet 3 0 lsb msb The Vancouver timestamp report: Vern Brethour 0

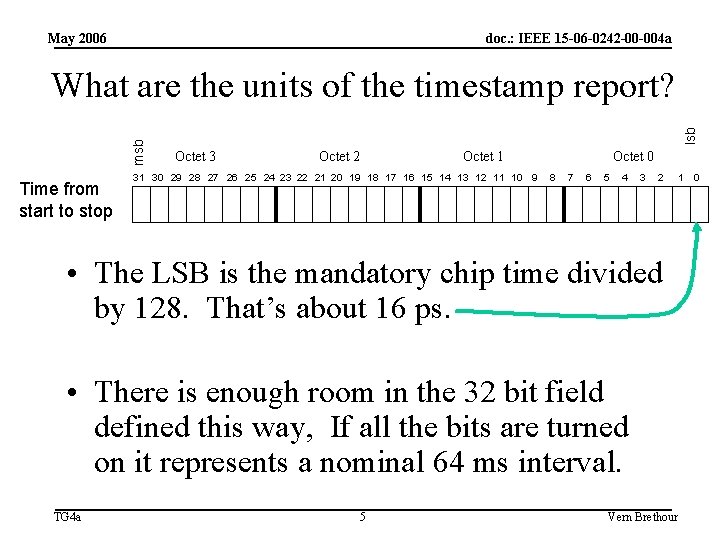
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Time from start to stop lsb msb What are the units of the timestamp report? Octet 3 Octet 2 Octet 1 31 30 29 28 27 26 25 24 23 22 21 20 19 18 17 16 15 14 13 12 11 10 9 Octet 0 8 7 6 5 4 3 2 • The LSB is the mandatory chip time divided by 128. That’s about 16 ps. • There is enough room in the 32 bit field defined this way, If all the bits are turned on it represents a nominal 64 ms interval. TG 4 a 5 Vern Brethour 1 0

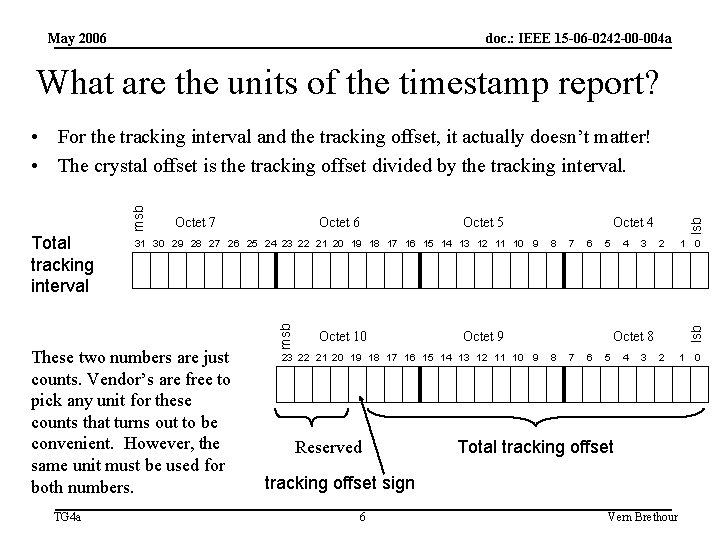
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What are the units of the timestamp report? Octet 10 8 7 6 5 Octet 9 23 22 21 20 19 18 17 16 15 14 13 12 11 10 9 Reserved Octet 4 4 3 lsb Octet 5 31 30 29 28 27 26 25 24 23 22 21 20 19 18 17 16 15 14 13 12 11 10 9 These two numbers are just counts. Vendor’s are free to pick any unit for these counts that turns out to be convenient. However, the same unit must be used for both numbers. TG 4 a Octet 6 msb Total tracking interval Octet 7 2 1 Octet 8 8 7 6 5 4 3 Total tracking offset sign 6 0 lsb msb • For the tracking interval and the tracking offset, it actually doesn’t matter! • The crystal offset is the tracking offset divided by the tracking interval. Vern Brethour 0

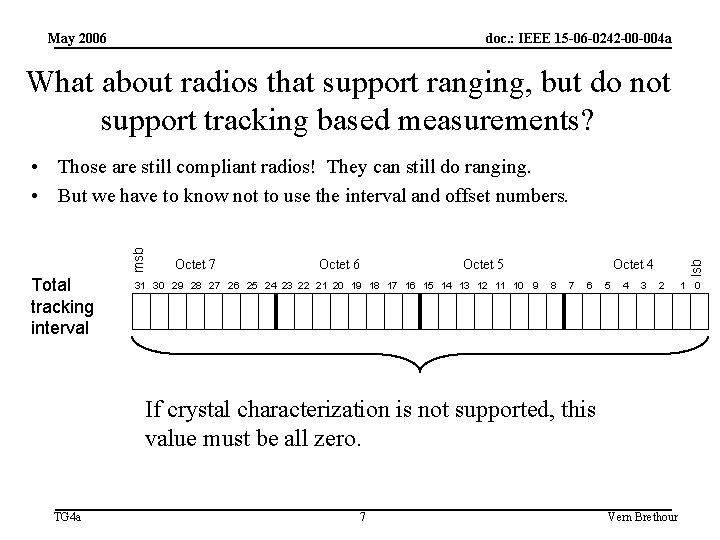
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What about radios that support ranging, but do not support tracking based measurements? Total tracking interval Octet 7 Octet 6 Octet 5 31 30 29 28 27 26 25 24 23 22 21 20 19 18 17 16 15 14 13 12 11 10 9 Octet 4 8 7 6 5 4 3 lsb msb • Those are still compliant radios! They can still do ranging. • But we have to know not to use the interval and offset numbers. 2 If crystal characterization is not supported, this value must be all zero. TG 4 a 7 Vern Brethour 1 0

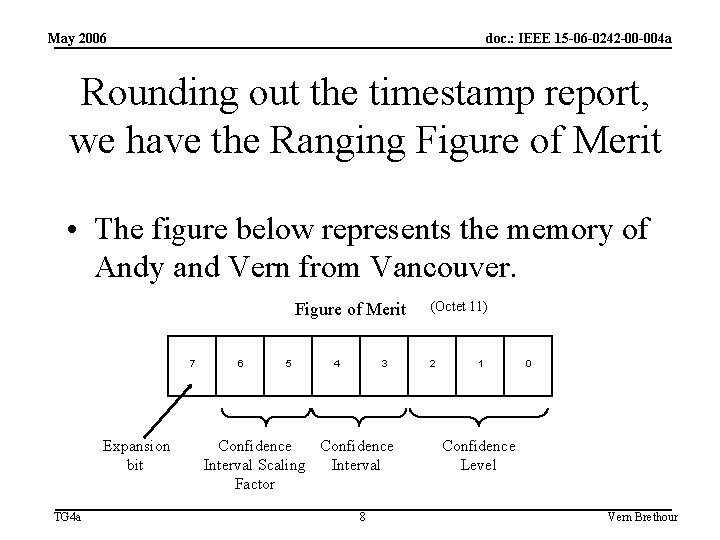
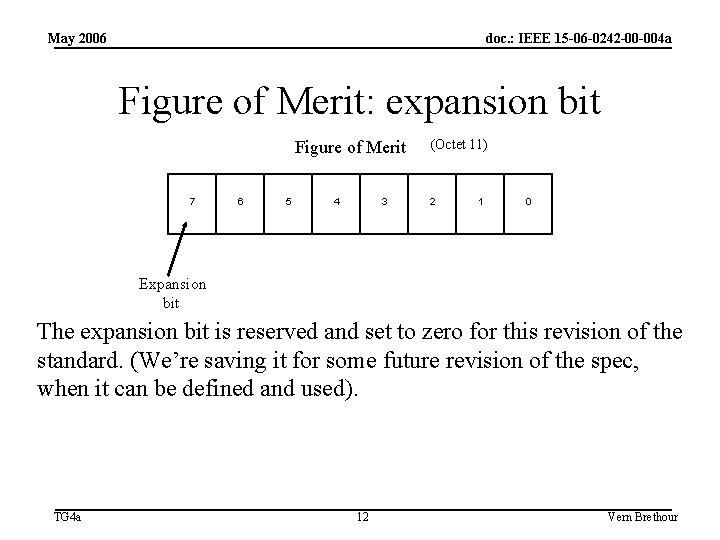
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Rounding out the timestamp report, we have the Ranging Figure of Merit • The figure below represents the memory of Andy and Vern from Vancouver. Figure of Merit 7 Expansion bit TG 4 a 6 5 4 3 Confidence Interval Scaling Interval Factor 8 (Octet 11) 2 1 0 Confidence Level Vern Brethour

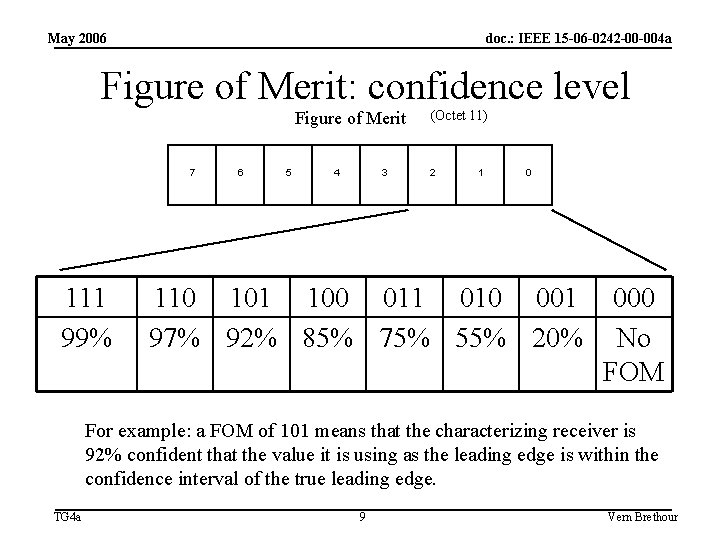
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Figure of Merit: confidence level Figure of Merit 7 111 99% 6 5 4 3 (Octet 11) 2 1 0 110 101 100 011 010 001 97% 92% 85% 75% 55% 20% 000 No FOM For example: a FOM of 101 means that the characterizing receiver is 92% confident that the value it is using as the leading edge is within the confidence interval of the true leading edge. TG 4 a 9 Vern Brethour

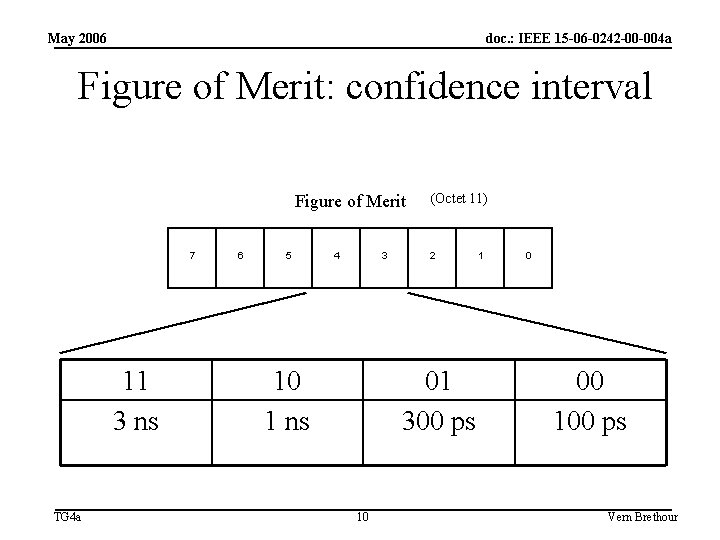
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Figure of Merit: confidence interval Figure of Merit 7 11 3 ns TG 4 a 6 5 4 3 10 1 ns (Octet 11) 2 01 300 ps 10 1 0 00 100 ps Vern Brethour

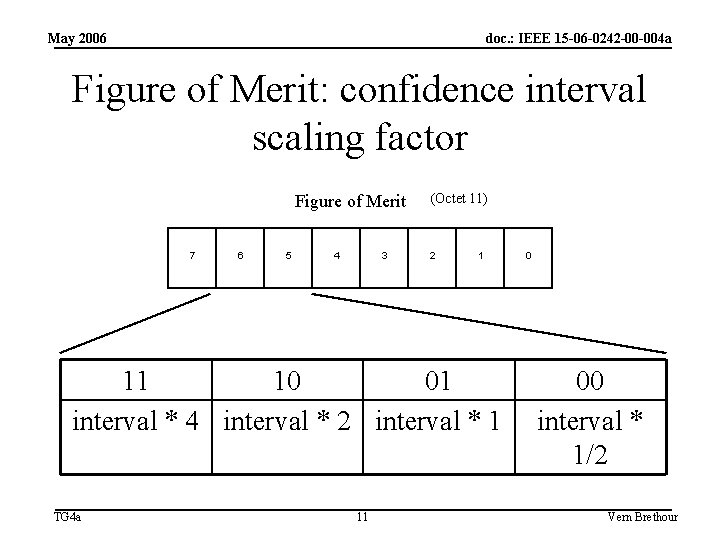
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Figure of Merit: confidence interval scaling factor Figure of Merit 7 6 5 4 3 (Octet 11) 2 1 11 10 01 interval * 4 interval * 2 interval * 1 TG 4 a 11 0 00 interval * 1/2 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Figure of Merit: expansion bit Figure of Merit 7 6 5 4 3 (Octet 11) 2 1 0 Expansion bit The expansion bit is reserved and set to zero for this revision of the standard. (We’re saving it for some future revision of the spec, when it can be defined and used). TG 4 a 12 Vern Brethour

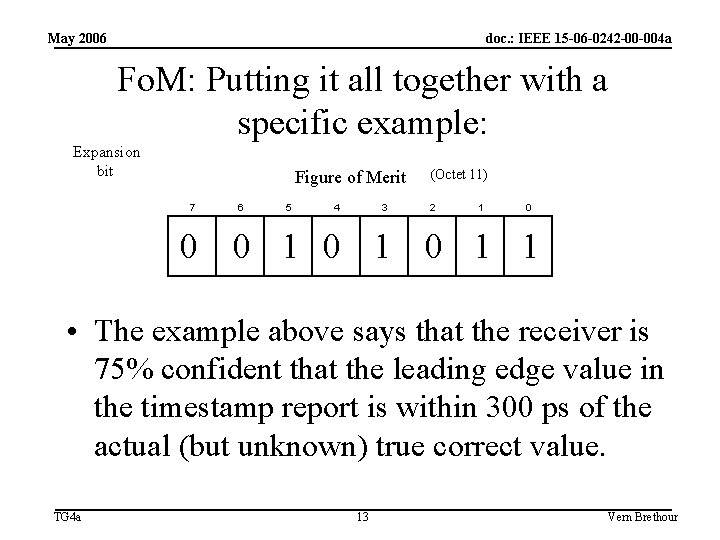
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Fo. M: Putting it all together with a specific example: Expansion bit Figure of Merit 7 6 5 4 3 (Octet 11) 2 1 0 0 0 1 0 1 1 • The example above says that the receiver is 75% confident that the leading edge value in the timestamp report is within 300 ps of the actual (but unknown) true correct value. TG 4 a 13 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a So Fine… that’s what the Fo. M means… What do the values really relate to? • The inaccuracies in a ranging effort come from a multitude of sources. The Fo. M tries to capture and express some of them. • Let’s look at a ranging exchange and see how it works and think about how it might not work so well…. TG 4 a 14 Vern Brethour

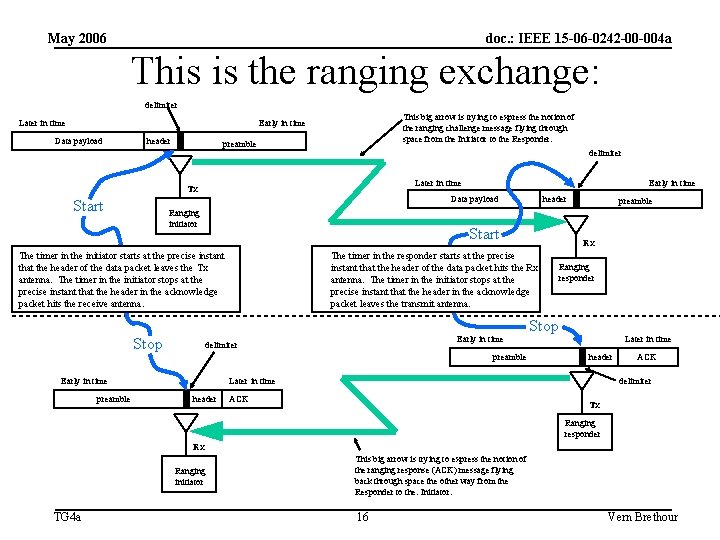
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The Ranging exchange: The essential heart of ranging. • In most ways, this exchange is just a normal Data transmission followed by normal ACK transmission: What makes it different is that the MCPS-DATA. request had the parameter “ALL_RANGING” causing the PHYs on both ends of the exchange have counters running after delimiter detection. Then, when they discover the “UWB Rangingsub-field” bit is set in the PHY header, they keep the counters running. TG 4 a 15 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a This is the ranging exchange: delimiter Later in time This big arrow is trying to express the notion of the ranging challenge message flying through space from the Initiator to the Responder. Early in time Data payload header preamble delimiter Later in time Tx Start Data payload Ranging initiator Early in time preamble Rx The timer in the responder starts at the precise instant that the header of the data packet hits the Rx antenna. The timer in the initiator stops at the precise instant that the header in the acknowledge packet leaves the transmit antenna. delimiter Early in time preamble header Start The timer in the initiator starts at the precise instant that the header of the data packet leaves the Tx antenna. The timer in the initiator stops at the precise instant that the header in the acknowledge packet hits the receive antenna. Stop Early in time Ranging responder Stop Later in time header ACK delimiter ACK Tx Ranging responder Rx Ranging initiator TG 4 a This big arrow is trying to express the notion of the ranging response (ACK) message flying back through space the other way from the Responder to the. Initiator. 16 Vern Brethour

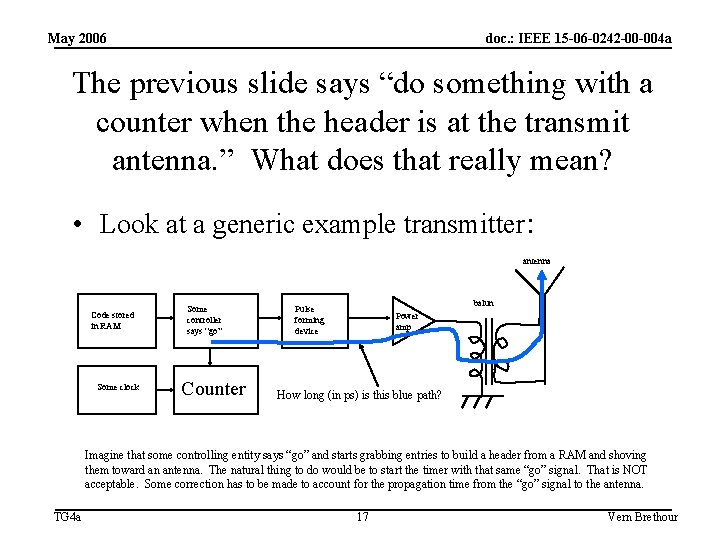
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The previous slide says “do something with a counter when the header is at the transmit antenna. ” What does that really mean? • Look at a generic example transmitter: antenna Code stored in RAM Some clock Some controller says “go” Counter balun Pulse forming device Power amp How long (in ps) is this blue path? Imagine that some controlling entity says “go” and starts grabbing entries to build a header from a RAM and shoving them toward an antenna. The natural thing to do would be to start the timer with that same “go” signal. That is NOT acceptable. Some correction has to be made to account for the propagation time from the “go” signal to the antenna. TG 4 a 17 Vern Brethour

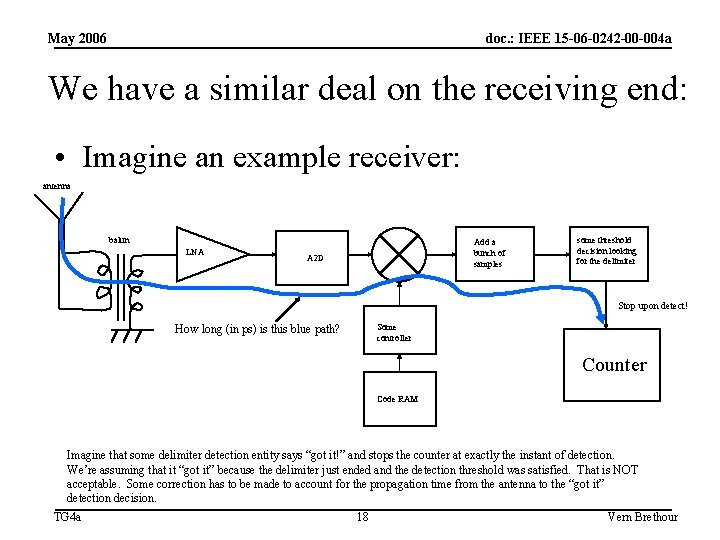
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a We have a similar deal on the receiving end: • Imagine an example receiver: antenna balun LNA Add a bunch of samples A 2 D some threshold decision looking for the delimiter Stop upon detect! Some controller How long (in ps) is this blue path? Counter Code RAM Imagine that some delimiter detection entity says “got it!” and stops the counter at exactly the instant of detection. We’re assuming that it “got it” because the delimiter just ended and the detection threshold was satisfied. That is NOT acceptable. Some correction has to be made to account for the propagation time from the antenna to the “got it” detection decision. TG 4 a 18 Vern Brethour

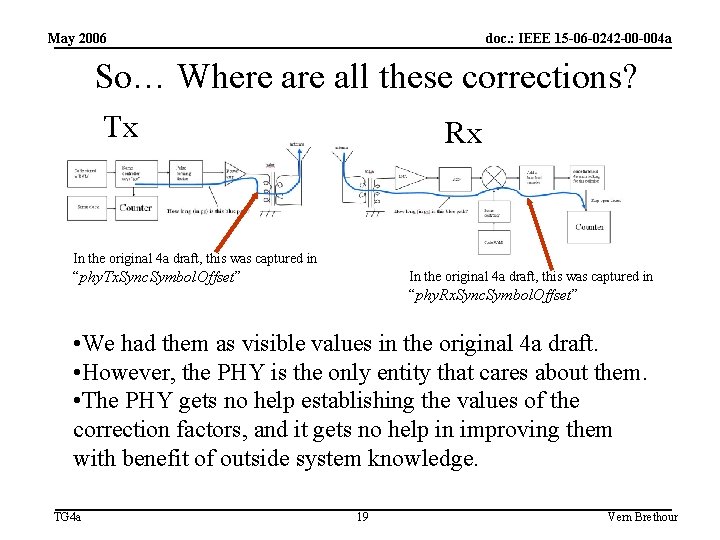
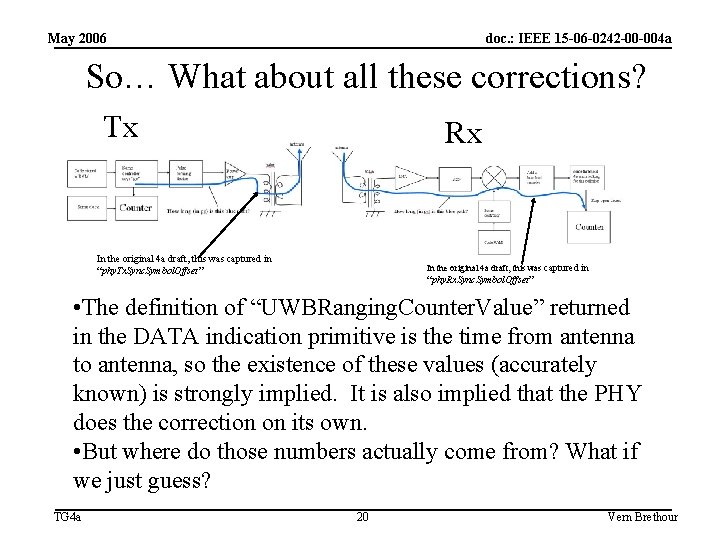
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a So… Where all these corrections? Tx Rx In the original 4 a draft, this was captured in “phy. Tx. Sync. Symbol. Offset” In the original 4 a draft, this was captured in “phy. Rx. Sync. Symbol. Offset” • We had them as visible values in the original 4 a draft. • However, the PHY is the only entity that cares about them. • The PHY gets no help establishing the values of the correction factors, and it gets no help in improving them with benefit of outside system knowledge. TG 4 a 19 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a So… What about all these corrections? Tx Rx In the original 4 a draft, this was captured in “phy. Tx. Sync. Symbol. Offset” In the original 4 a draft, this was captured in “phy. Rx. Sync. Symbol. Offset” • The definition of “UWBRanging. Counter. Value” returned in the DATA indication primitive is the time from antenna to antenna, so the existence of these values (accurately known) is strongly implied. It is also implied that the PHY does the correction on its own. • But where do those numbers actually come from? What if we just guess? TG 4 a 20 Vern Brethour

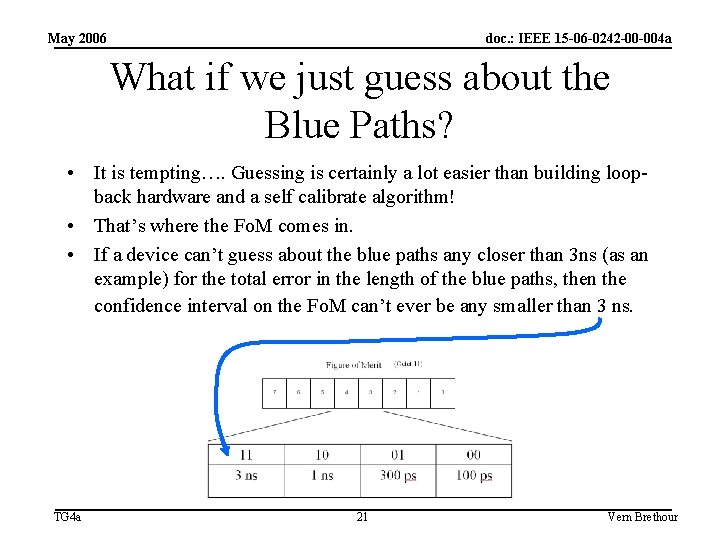
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What if we just guess about the Blue Paths? • It is tempting…. Guessing is certainly a lot easier than building loopback hardware and a self calibrate algorithm! • That’s where the Fo. M comes in. • If a device can’t guess about the blue paths any closer than 3 ns (as an example) for the total error in the length of the blue paths, then the confidence interval on the Fo. M can’t ever be any smaller than 3 ns. TG 4 a 21 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Okay…. So if the PHY folks make a Tx-Rx loopback and do a calibrate algorithm to measure the Blue Paths exactly right…. Are we done? • No! • A calibrating loop-back is the easy part. • We must make our counter action exactly upon the arrival of the very first pulse of the header at the antenna. TG 4 a 22 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Start or stop the counter exactly upon the first pulse of the header…. Okay! • We know perfectly well how long the delimiter is and how long the detection takes, so…. . What’s so hard about that? • Actually, the first pulse of the header arrives at the antenna once for every multipath reflection in the environment. TG 4 a 23 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Do something with the counter when the first pulse arrives…. . • Not only does the first pulse arrive off of every reflection in the environment. It can even arrive off of the reflections! • In an indoor environment, the “first pulse” can arrive hundreds of different times! • So we must find the first arrival of the first pulse. TG 4 a 24 Vern Brethour

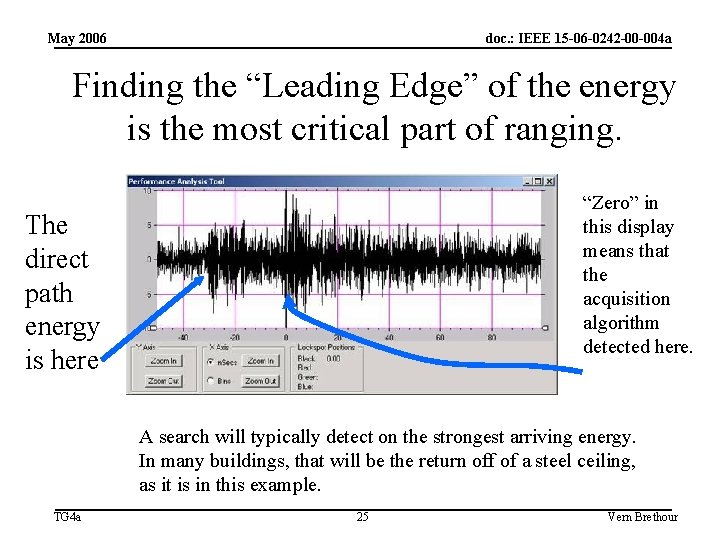
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Finding the “Leading Edge” of the energy is the most critical part of ranging. “Zero” in this display means that the acquisition algorithm detected here. The direct path energy is here A search will typically detect on the strongest arriving energy. In many buildings, that will be the return off of a steel ceiling, as it is in this example. TG 4 a 25 Vern Brethour

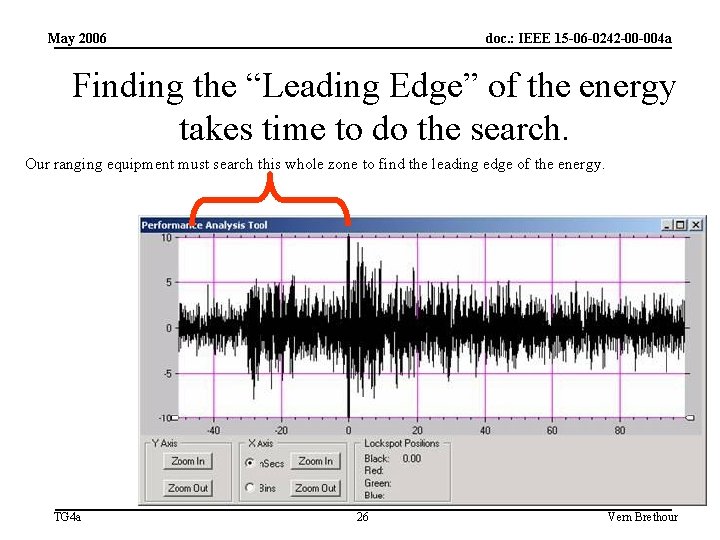
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Finding the “Leading Edge” of the energy takes time to do the search. Our ranging equipment must search this whole zone to find the leading edge of the energy. TG 4 a 26 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a That’s why we have the long preambles! • Use of the long preambles is not mandatory for ranging. • But, depending on the sophistication of the receiver’s leading edge search engine, long preambles are very helpful! • The receiver does not necessarily know how much preamble remains after the detection and before the delimiter. TG 4 a 27 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What does the search engine do with the unknown amount of time before the delimiter? • The best job it can! • The search engine brackets the search zone and keeps improving the estimate of the leading edge till it runs out of time. It’s out of time when the delimiter is detected. • If the preamble is short (like 16 symbols) the delimiter will come almost immediately - before the search is very refined. • If the preamble is long (like 4096 symbols) the search can be evaluating very fine resolution steps by the time the delimiter arrives. TG 4 a 28 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What do we do if we want to improve the search more? • The easiest time (by far) to do the leading edge search and improve the estimate of it’s true position is during the preamble. • It is also possible to (fairly easily) further improve the search during the payload section of the packet if the pilot pulses are being used for CSMA. • It is also possible (but not easy) to further improve the search during the payload section of the packet using the data signal. TG 4 a 29 Vern Brethour

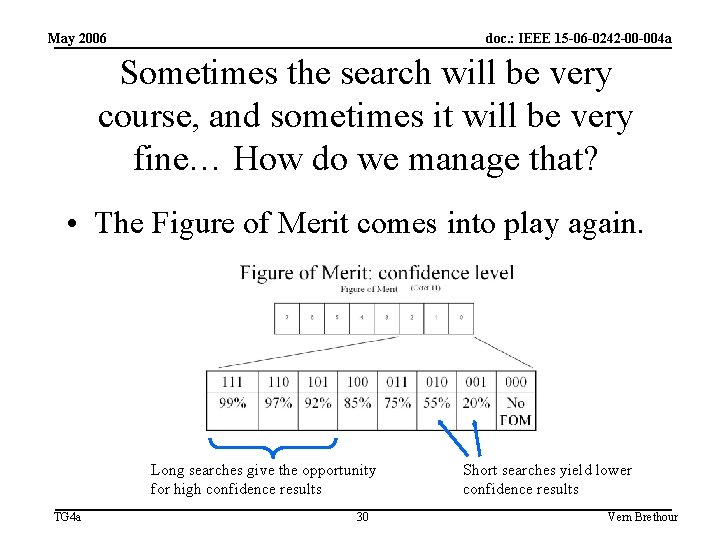
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Sometimes the search will be very course, and sometimes it will be very fine… How do we manage that? • The Figure of Merit comes into play again. Long searches give the opportunity for high confidence results TG 4 a 30 Short searches yield lower confidence results Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The Figure of Merit is capturing multiple effects. • The signal to noise ratio of the link affects the confidence level. • The amount of search time after preamble detection affects the confidence level, and if it is very short, it can also effect the confidence interval. • The self calibrating capability (or more critically, if there is a lack of self-calibrate capability) of the device affects the confidence interval. TG 4 a 31 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What should the PHY do if the leading search goes very badly? • When the PHY knows that the leading edge search did not go well, it should NOT present a Fo. M of all zeros… That indicates “no Fo. M” which is not the situation that we’re trying to express. • The appropriate value to describe a train wreak is “ 0 x 79”. • 0 x 79 in the Fo. M is telling the next higher layer that even if the other nodes’ timer value is exactly perfect there is an 80% chance that the computed range will be wrong by more than 2 meters. TG 4 a 32 Vern Brethour

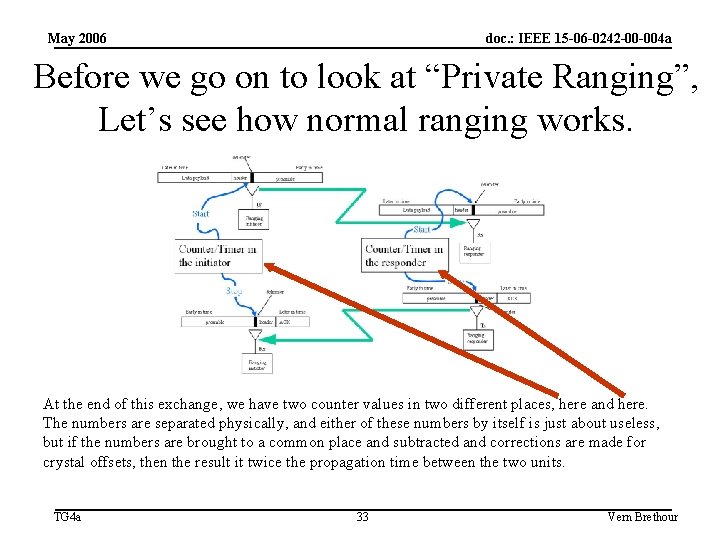
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Before we go on to look at “Private Ranging”, Let’s see how normal ranging works. At the end of this exchange, we have two counter values in two different places, here and here. The numbers are separated physically, and either of these numbers by itself is just about useless, but if the numbers are brought to a common place and subtracted and corrections are made for crystal offsets, then the result it twice the propagation time between the two units. TG 4 a 33 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Can a hostile node learn anything about the position of the nodes by listening to the message exchanges? • It would be undesirable if that were the case. After all, in some applications, the position of the devices IS the essential information being communicated. • Think about an application tracking high value assets (children in an amusement park) and through sloppy design we made it easy for bad people to track these very same UWB nodes. TG 4 a 34 Vern Brethour

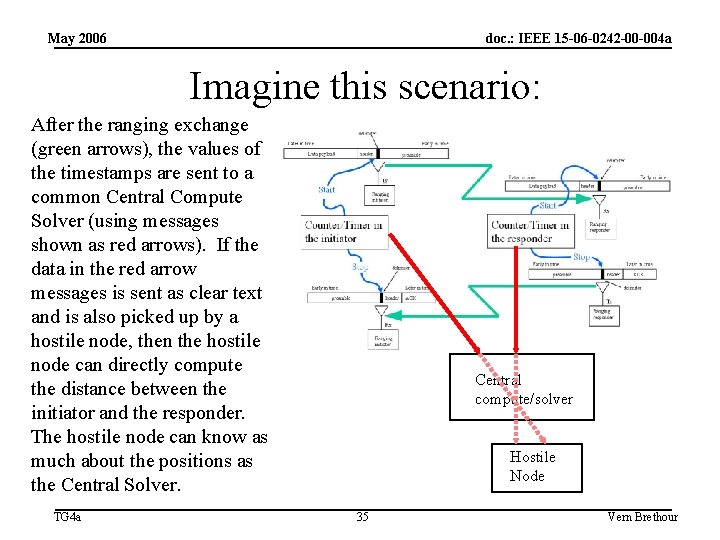
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Imagine this scenario: After the ranging exchange (green arrows), the values of the timestamps are sent to a common Central Compute Solver (using messages shown as red arrows). If the data in the red arrow messages is sent as clear text and is also picked up by a hostile node, then the hostile node can directly compute the distance between the initiator and the responder. The hostile node can know as much about the positions as the Central Solver. TG 4 a Central compute/solver Hostile Node 35 Vern Brethour

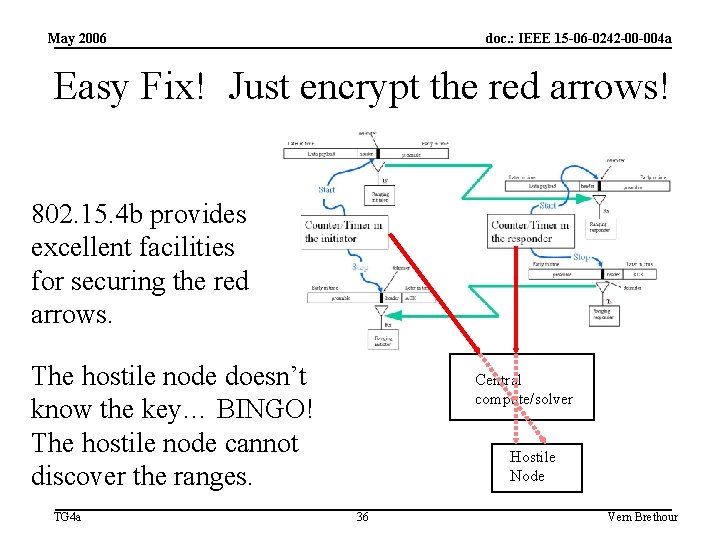
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Easy Fix! Just encrypt the red arrows! 802. 15. 4 b provides excellent facilities for securing the red arrows. The hostile node doesn’t know the key… BINGO! The hostile node cannot discover the ranges. TG 4 a Central compute/solver Hostile Node 36 Vern Brethour

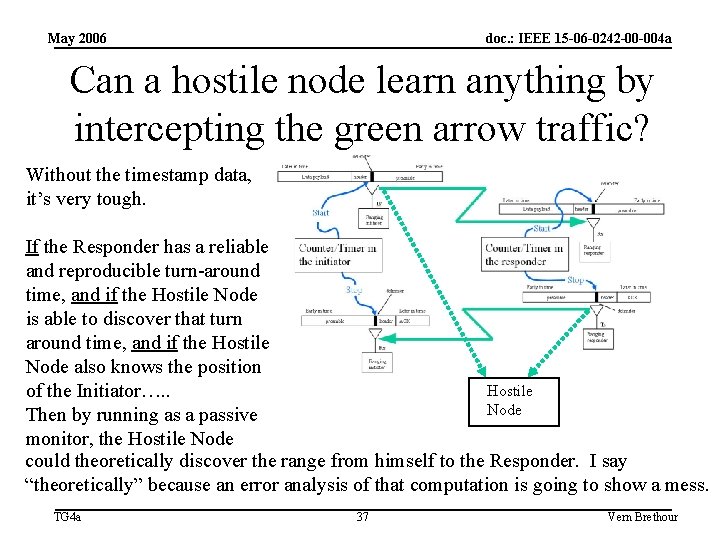
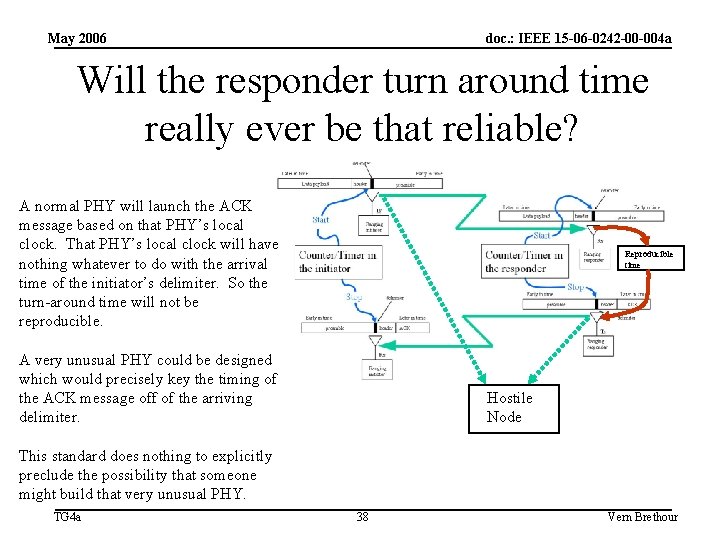
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Can a hostile node learn anything by intercepting the green arrow traffic? Without the timestamp data, it’s very tough. If the Responder has a reliable and reproducible turn-around time, and if the Hostile Node is able to discover that turn around time, and if the Hostile Node also knows the position Hostile of the Initiator…. . Node Then by running as a passive monitor, the Hostile Node could theoretically discover the range from himself to the Responder. I say “theoretically” because an error analysis of that computation is going to show a mess. TG 4 a 37 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Will the responder turn around time really ever be that reliable? A normal PHY will launch the ACK message based on that PHY’s local clock. That PHY’s local clock will have nothing whatever to do with the arrival time of the initiator’s delimiter. So the turn-around time will not be reproducible. Reproducible time A very unusual PHY could be designed which would precisely key the timing of the ACK message off of the arriving delimiter. Hostile Node This standard does nothing to explicitly preclude the possibility that someone might build that very unusual PHY. TG 4 a 38 Vern Brethour

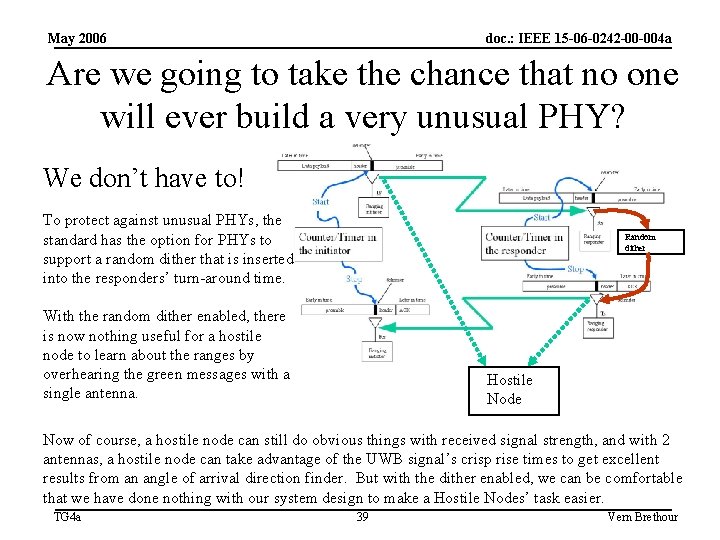
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Are we going to take the chance that no one will ever build a very unusual PHY? We don’t have to! To protect against unusual PHYs, the standard has the option for PHYs to support a random dither that is inserted into the responders’ turn-around time. Random dither With the random dither enabled, there is now nothing useful for a hostile node to learn about the ranges by overhearing the green messages with a single antenna. Hostile Node Now of course, a hostile node can still do obvious things with received signal strength, and with 2 antennas, a hostile node can take advantage of the UWB signal’s crisp rise times to get excellent results from an angle of arrival direction finder. But with the dither enabled, we can be comfortable that we have done nothing with our system design to make a Hostile Nodes’ task easier. TG 4 a 39 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Okay, so how much are we supposed to dither? • Just about anything will work great. • We only need to break up any regular and predictable turnaround times. TG 4 a Random dither Hostile node 40 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Isn’t this dither thing a lot of work to protect against something that isn’t much of a threat anyway? Nah! It may not be protecting against much of a threat, but the dither thing is not much work for us either. Random dither The optional dither is super easy to build and support…. . and if it helps people feel more secure: What harm? TG 4 a Hostile node 41 Vern Brethour

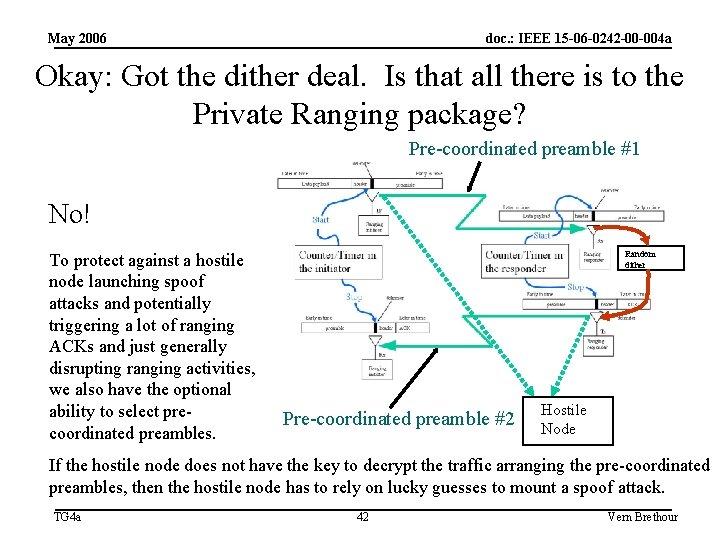
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Okay: Got the dither deal. Is that all there is to the Private Ranging package? Pre-coordinated preamble #1 No! To protect against a hostile node launching spoof attacks and potentially triggering a lot of ranging ACKs and just generally disrupting ranging activities, we also have the optional ability to select precoordinated preambles. Random dither Pre-coordinated preamble #2 Hostile Node If the hostile node does not have the key to decrypt the traffic arranging the pre-coordinated preambles, then the hostile node has to rely on lucky guesses to mount a spoof attack. TG 4 a 42 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Pre-coordinated Preambles? Is that going to be tough to manage? It does require some care, but it’s not too bad. Setting it up: Managing the traffic to the nodes to tell them what preambles to use…. that is handled (out of scope) naturally enough with traffic secured using the normal 15. 4 b security suite. The hostile node doesn’t know the keys so it is denied knowledge of the preambles. The tricky part comes in making sure we do not loose control of the nodes. TG 4 a 43 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Loosing control of the nodes? • Yeah… If we are not careful, it could happen. • Once the ranging nodes are told to go off into their own special unique signaling space to do their private ranging thing, they can no longer talk to (or hear) other normal nodes. The pre-coordinated preambles are one-time use affairs with no re-tries, so after their ranging exchange is over, the ranging nodes are supposed to come back to the regular world and talk to and listen to normal nodes using normal preambles. • However, if the ranging exchange does not complete normally, we could be left with nodes listening forever for unique preambles that are never going to come. TG 4 a 44 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Loosing control of the nodes… Really? • Nah, not really. • That’s why we have timeouts! • If the ranging exchange completes routinely, then the MACs of the nodes involved revert their PHYs back to the normal preambles. • If the ranging exchange does not complete normally (for whatever reason) then the MACs will have their PHYs return to the normal preambles when the timer expires. • The only tricky thing left is that the timers in both nodes need to be started at approximately the same time and the timer value needs to be long enough to cover whatever amount of “not the same start time” we have as well as giving adequate life expectancy to the pre-coordinated preambles that the ranging exchange can complete normally. TG 4 a 45 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Okay Great! Now we have a way to irritate the operators of hostile nodes. Is that all there is to UWB ranging? • No, not quite. • Remember a few slides back there was mention of dealing with crystal offsets? • Dealing with crystal offsets is absolutely essential. • When we (eventually) subtract the two counter values we are subtracting two very large and nearly equal numbers. The amount that they differ by is the round-trip time of flight of the UWB signal. The two measurements were made with different crystals. So if that difference is not compensated for, then the error due to crystal differences will completely dominate the calculation. TG 4 a 46 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a It’s easy to correct for the difference in the crystals if we happen to know the difference in the crystals! ………. ? ? ? . . . . That’s true enough, but how are we supposed to somehow know the differences in the crystals? Lucky for us, the tracking loop in the receiver is measuring exactly that difference. TG 4 a 47 Vern Brethour

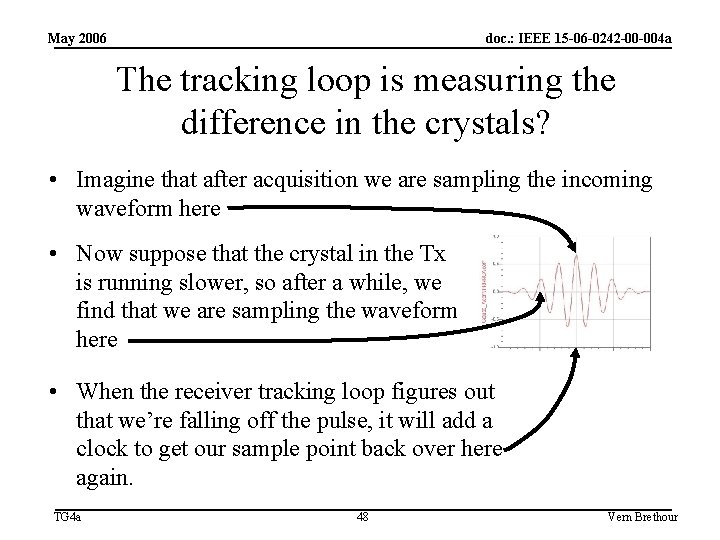
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The tracking loop is measuring the difference in the crystals? • Imagine that after acquisition we are sampling the incoming waveform here • Now suppose that the crystal in the Tx is running slower, so after a while, we find that we are sampling the waveform here • When the receiver tracking loop figures out that we’re falling off the pulse, it will add a clock to get our sample point back over here again. TG 4 a 48 Vern Brethour

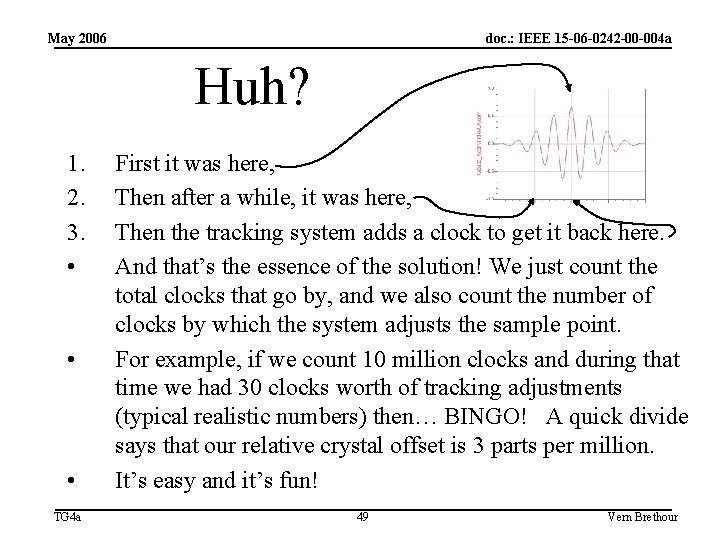
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Huh? 1. 2. 3. • • • TG 4 a First it was here, Then after a while, it was here, Then the tracking system adds a clock to get it back here. And that’s the essence of the solution! We just count the total clocks that go by, and we also count the number of clocks by which the system adjusts the sample point. For example, if we count 10 million clocks and during that time we had 30 clocks worth of tracking adjustments (typical realistic numbers) then… BINGO! A quick divide says that our relative crystal offset is 3 parts per million. It’s easy and it’s fun! 49 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Is it really that easy? • Yep! • The count is a signed number and to interoperate, all PHYs must use the same convention for the sign bit. • It’s always the receiver that’s doing the counting and so the sign bit has it’s meaning from the receivers’ perspective. If the Tx oscillator is running slower, and the Rx is adding clocks, the sign bit is positive. If the Tx is running faster, and the Rx is dropping clocks to keep up, the sign bit is negative. TG 4 a 50 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a So…. the offset correction is the total number of clocks divided by the number of equivalent clocks worth of tracking adjustment… is that all? • Is that all? …. Indeed…. That’s too much! • PHY designers would rather suffer flaming oil dumped on them from the castle parapet than do a hardware divide. • If some silly standard asks for a PHY that does a divide…. . It ain’t gon’na happen. TG 4 a 51 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a PHY designers don’t wash windows; PHY designers don’t do divide. • The information about the crystal offset is contained in the two count numbers. • The PHY simply reports those two numbers to the MAC. • The MAC reports those numbers to the Next Higher Layer. Somewhere, some entity is going to do a divide, but it ain’t us. TG 4 a 52 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What about PHYs that do everything with an analogue PLL? They are not adjusting their tracking points with discrete countable events. • That’s right: There a couple of choices. 1. The PLL steady state error signal is a direct measure of the tracking offset. So that PHY can convert the error signal to a number and put that in the offset count field (remember to get the sign bit right) and put a convenient scaling number (like a million) in the total clock count field. 2. Or the PHY can put zero in the total clock count field and that makes it known that this PHY is not supporting crystal offset characterization. This has the effect of making it the other nodes problem. TG 4 a 53 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Can we manage crystal offsets if one of the nodes is not supporting the offset characterization? • Sure! • Both PHY’s are looking at their partners crystal oscillator with their own tracking equipment. They are making the same measurement and will be reporting the same ratio (the sign bits will be opposites). • Only one of the PHYs needs to do the characterization for the offset correction to work for the pair. TG 4 a 54 Vern Brethour

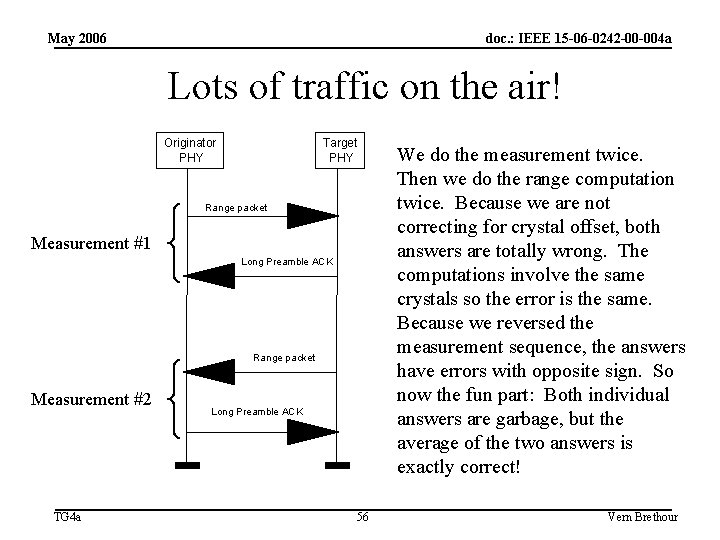
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Can we still do ranging if NEITHER of the PHYs supports crystal offset characterization? • Yes we can! • It involves a lot of traffic on the air, but answer is definitely “yes”. • We just do the measurement twice. The first time is simply the normal exchange. On the second time, the roles are reversed. The node that was the initiator on the first measurement is the responder for the second measurement, and likewise with the responder on the first measurement becomes the initiator for the second measurement. TG 4 a 55 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Lots of traffic on the air! Originator PHY Target PHY Range packet Measurement #1 Long Preamble ACK Range packet Measurement #2 TG 4 a Long Preamble ACK 56 We do the measurement twice. Then we do the range computation twice. Because we are not correcting for crystal offset, both answers are totally wrong. The computations involve the same crystals so the error is the same. Because we reversed the measurement sequence, the answers have errors with opposite sign. So now the fun part: Both individual answers are garbage, but the average of the two answers is exactly correct! Vern Brethour

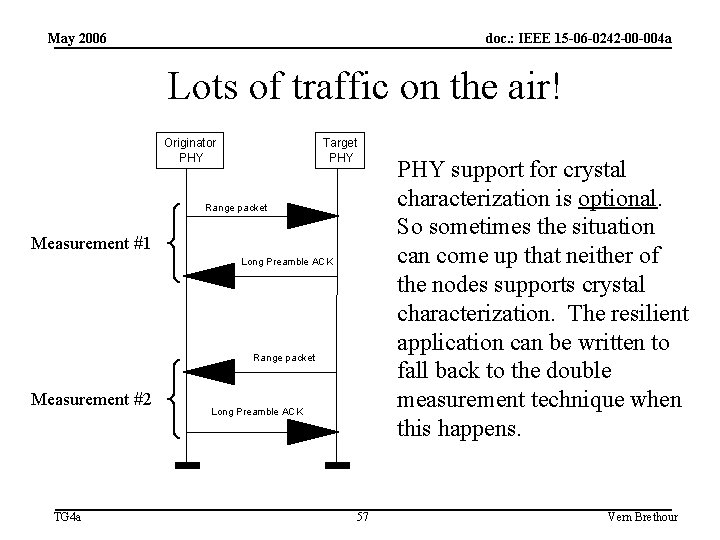
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Lots of traffic on the air! Originator PHY Target PHY Range packet Measurement #1 Long Preamble ACK Range packet Measurement #2 TG 4 a Long Preamble ACK 57 PHY support for crystal characterization is optional. So sometimes the situation can come up that neither of the nodes supports crystal characterization. The resilient application can be written to fall back to the double measurement technique when this happens. Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Okay!. . . We’ve got privacy, we’ve got crystals, we’ve got calibrators & leading edge searchers. . (Looks like we’ve got every imaginable thing, except a hardware divide. ). . How is it all supposed to work? • Let’s run through a sequence of a ranging activity and discuss the individual steps. TG 4 a 58 Vern Brethour

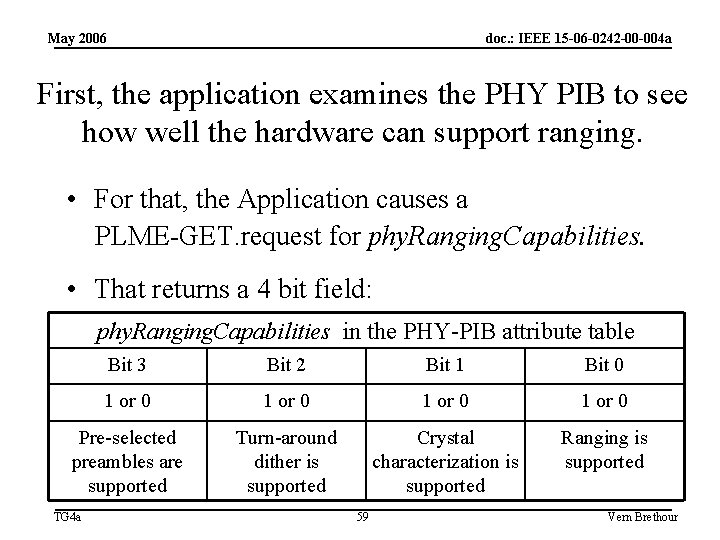
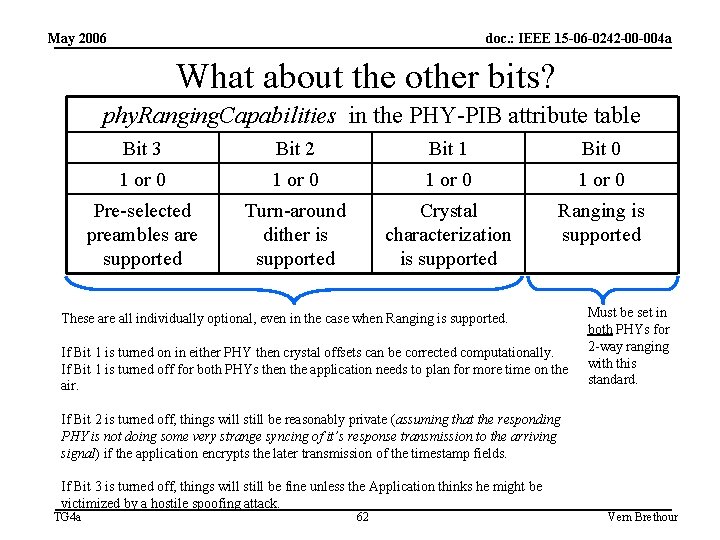
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a First, the application examines the PHY PIB to see how well the hardware can support ranging. • For that, the Application causes a PLME-GET. request for phy. Ranging. Capabilities. • That returns a 4 bit field: phy. Ranging. Capabilities in the PHY-PIB attribute table Bit 3 Bit 2 Bit 1 Bit 0 1 or 0 Pre-selected preambles are supported Turn-around dither is supported Crystal characterization is supported Ranging is supported TG 4 a 59 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a If bit zero is set, the PHY claims that ranging is supported: What does that really mean? • Unfortunately, all it might mean is that the PHY has a counter rigged up to the delimiter detector and is willing to make the attempt! There may not be any self calibrate capability, and the leading edge searcher might be crude as hell, or nonexistent. • The application will find out later (when the Fo. M comes in) how capable the PHY actually is. TG 4 a 60 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Let me repeat for emphasis: Just because this bit is set… don’t get too excited. phy. Ranging. Capabilities in the PHY-PIB attribute table Bit 3 Bit 2 Bit 1 Bit 0 1 or 0 Pre-selected preambles are supported Turn-around dither is supported Crystal characterization is supported Ranging is supported • For example: If a PHY has no leading edge search capability, and just wants to make a lucky guess about the Blue Paths…. It can still rig up a counter to the delimiter detector and successfully do ranging if there is no multipath. To be compliant, that PHY would have a simple detector for multipath and set the Fo. M equal to 0 x 79 (the appropriate value for train wreaks) whenever multipath is present. TG 4 a 61 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What about the other bits? phy. Ranging. Capabilities in the PHY-PIB attribute table Bit 3 Bit 2 Bit 1 Bit 0 1 or 0 Pre-selected preambles are supported Turn-around dither is supported Crystal characterization is supported Ranging is supported These are all individually optional, even in the case when Ranging is supported. If Bit 1 is turned on in either PHY then crystal offsets can be corrected computationally. If Bit 1 is turned off for both PHYs then the application needs to plan for more time on the air. Must be set in both PHYs for 2 -way ranging with this standard. If Bit 2 is turned off, things will still be reasonably private (assuming that the responding PHY is not doing some very strange syncing of it’s response transmission to the arriving signal) if the application encrypts the later transmission of the timestamp fields. If Bit 3 is turned off, things will still be fine unless the Application thinks he might be victimized by a hostile spoofing attack. TG 4 a 62 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a After the application knows the capabilities of the nodes, it’s Ranging decision time. • If either of the nodes does not support ranging, the choice is easy: No ranging is possible between this pair of nodes within the 15. 4 a standard protocols. • However, even this choice {“Can’t do it. ”} is a little bit nuanced. TG 4 a still supports the determination of position of ANY UWB device in a field of Ranging capable devices running a oneway ranging support infrastructure. TG 4 a 63 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Ranging decision time…. Continued: • If either node is capable of crystal characterization, then ranging can be accomplished by a single challenge/response exchange. • If neither node is capable of crystal characterization, then the application must plan for twice as much traffic on the air and measure everything twice reversing the order on the second measurement. TG 4 a 64 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Ranging decision time…. Continued: • If the nodes report that they support turn-around dither, it does no harm to use it. • The technique has nothing to do with the initiating node. It is only applicable to the responding node. It does no harm to enable it in the initiating node, it simply is not used. • Do not be concerned if the nodes do not support turnaround dither. The only situation where it could become an issue would be if the PHY designer has done something very unusual with the transmitter timing and somehow linked the response transmit time to the arrival time of the leading edge of the previous signal’s delimiter. TG 4 a 65 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Ranging decision time…. Continued: • If both nodes are capable of using pre-selected preambles, and if the application wants to take defensive measures against a potential spoof attack, then it can decide to use this feature. • If a spoof attack seems unlikely, it might be wise to forgo using the pre-selected preambles, because their selection coordination does (in general) require more traffic on-the-air. • Even if the pre-selected preamble feature is supported and enabled, a hostile node mounting a spoof attack can still disrupt the (now extra) traffic that is coordinating the pre-selected preambles. • An alternative response to a spoof attack is what we call “physical intervention”. TG 4 a 66 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The “spoof attack” and Physical Intervention. • Physical Intervention is a two step process. It is algorithmically effective and personally satisfying. • The first step is to find the offending device. This is very do-able. It is, after all, a UWB transmitter with wonderfully crisp rising edges working in a known band with a known protocol and known codes. • The second step is to smash it to crumbs with a 16 oz (450 grams) claw hammer. Always wear eye protection when smashing battery powered devices. TG 4 a 67 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Ranging decision time…. Continued: • The preamble length is chosen to give the receiver sufficient time to go a good job on the leading edge search. • Even though 100% of the decision concerning preamble length is about the capabilities of the receiver and the channel it is immersed in. . the actual implementation of the decision is done by telling the value to the transmitter! • Theoretically, an exceptionally capable receiver (that refines the leading edge search during data demodulation) could successfully do ranging with a 16 symbol preamble. A less capable receiver operating at long distance in a difficult channel could effectively use more than the maximum 4096 symbol preamble. • A suggested strategy is to start ranging with 1024 symbol preambles and watch what Fo. Ms are reported. A well implemented application will keep a history of the Fo. Ms and adjust the preamble lengths for each node as experience accumulates. TG 4 a 68 Vern Brethour

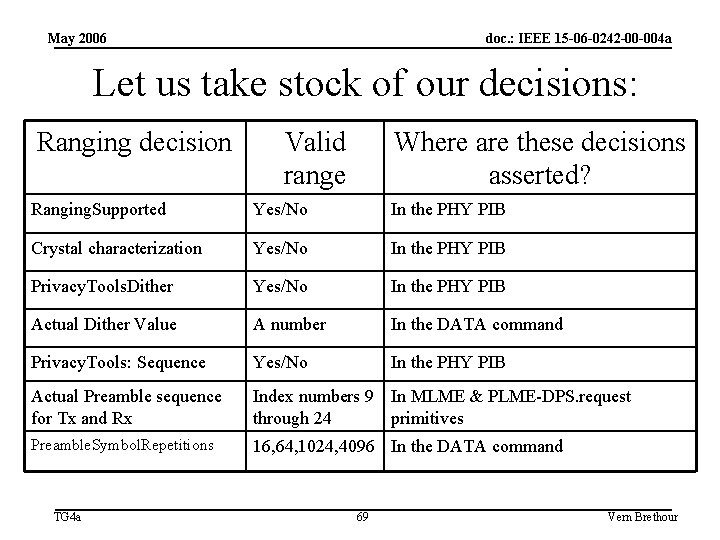
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Let us take stock of our decisions: Ranging decision Valid range Where are these decisions asserted? Ranging. Supported Yes/No In the PHY PIB Crystal characterization Yes/No In the PHY PIB Privacy. Tools. Dither Yes/No In the PHY PIB Actual Dither Value A number In the DATA command Privacy. Tools: Sequence Yes/No In the PHY PIB Actual Preamble sequence for Tx and Rx Index numbers 9 In MLME & PLME-DPS. request through 24 primitives Preamble. Symbol. Repetitions 16, 64, 1024, 4096 In the DATA command TG 4 a 69 Vern Brethour

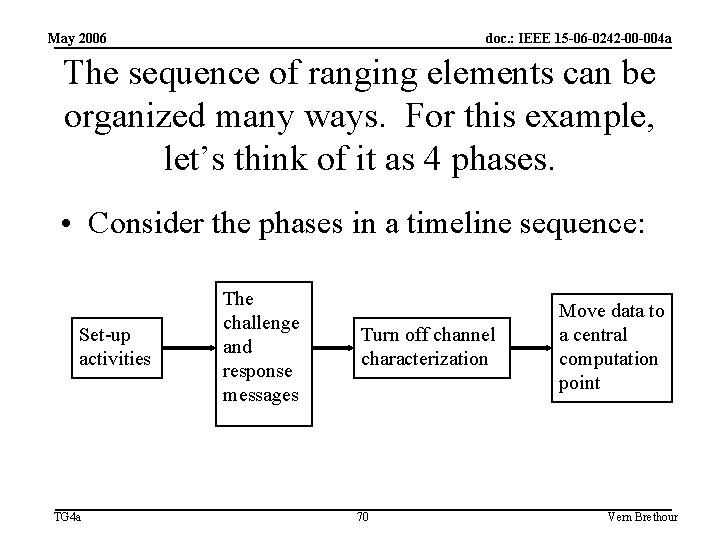
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The sequence of ranging elements can be organized many ways. For this example, let’s think of it as 4 phases. • Consider the phases in a timeline sequence: Set-up activities TG 4 a The challenge and response messages Turn off channel characterization 70 Move data to a central computation point Vern Brethour

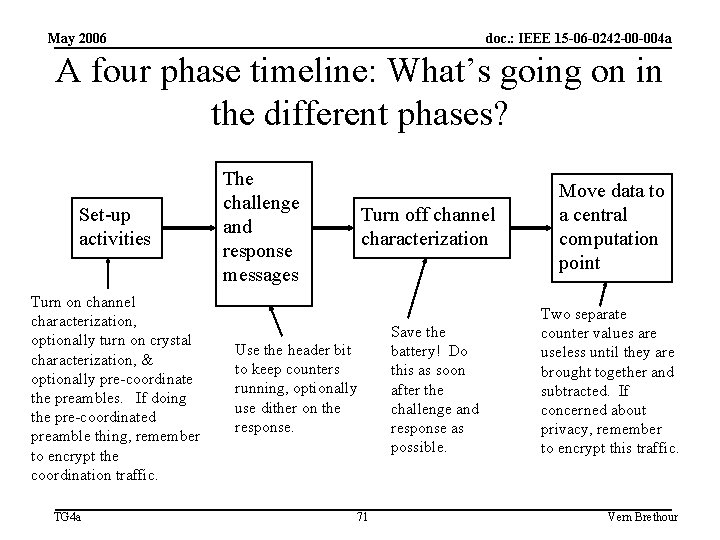
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a A four phase timeline: What’s going on in the different phases? Set-up activities Turn on channel characterization, optionally turn on crystal characterization, & optionally pre-coordinate the preambles. If doing the pre-coordinated preamble thing, remember to encrypt the coordination traffic. TG 4 a The challenge and response messages Turn off channel characterization Use the header bit to keep counters running, optionally use dither on the response. 71 Save the battery! Do this as soon after the challenge and response as possible. Move data to a central computation point Two separate counter values are useless until they are brought together and subtracted. If concerned about privacy, remember to encrypt this traffic. Vern Brethour

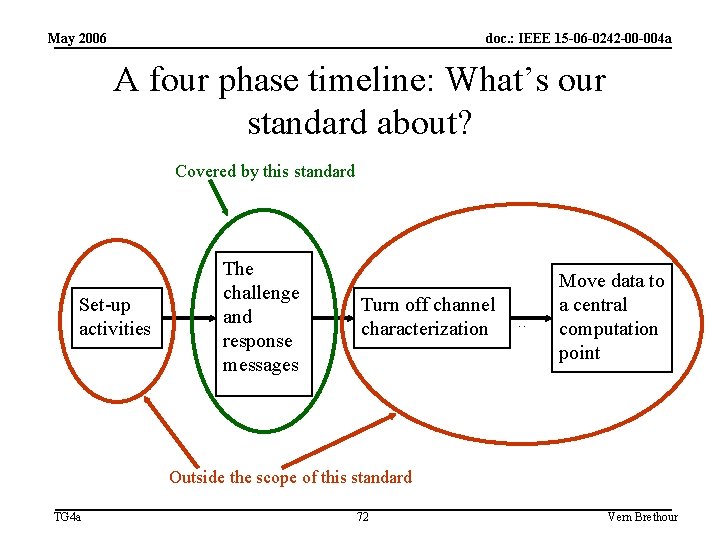
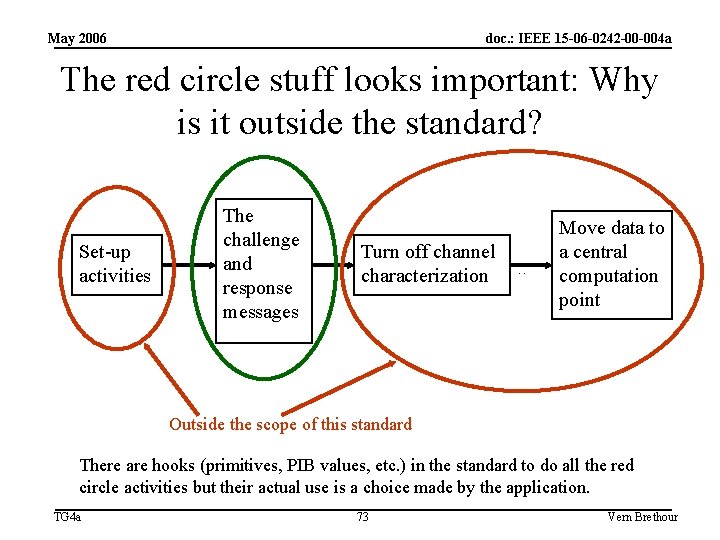
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a A four phase timeline: What’s our standard about? Covered by this standard Set-up activities The challenge and response messages Turn off channel characterization … Move data to a central computation point Outside the scope of this standard TG 4 a 72 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The red circle stuff looks important: Why is it outside the standard? Set-up activities The challenge and response messages Turn off channel characterization … Move data to a central computation point Outside the scope of this standard There are hooks (primitives, PIB values, etc. ) in the standard to do all the red circle activities but their actual use is a choice made by the application. TG 4 a 73 Vern Brethour

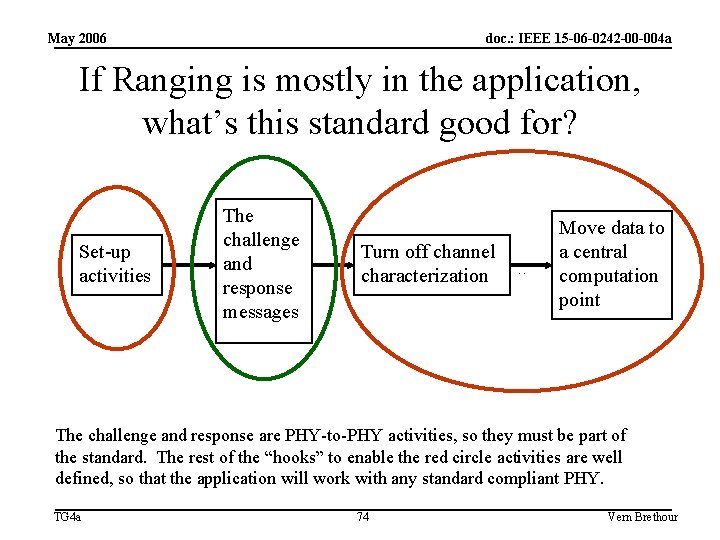
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a If Ranging is mostly in the application, what’s this standard good for? Set-up activities The challenge and response messages Turn off channel characterization … Move data to a central computation point The challenge and response are PHY-to-PHY activities, so they must be part of the standard. The rest of the “hooks” to enable the red circle activities are well defined, so that the application will work with any standard compliant PHY. TG 4 a 74 Vern Brethour

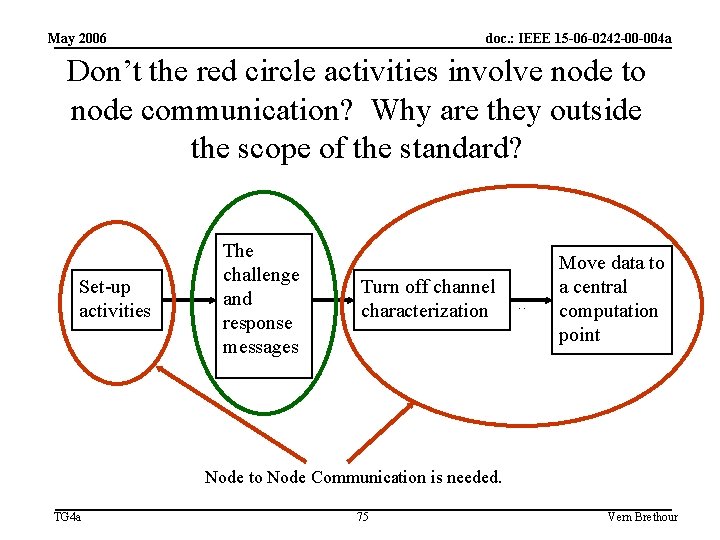
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Don’t the red circle activities involve node to node communication? Why are they outside the scope of the standard? Set-up activities The challenge and response messages Turn off channel characterization … Move data to a central computation point Node to Node Communication is needed. TG 4 a 75 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Node to node communication for Ranging. • We will show the primitives that enable this communication, but some applications may want to combine this traffic with other messaging that is going on and other applications may have a different attitude about the importance of air-time efficiency vs. battery life. This standard deliberately does not specify these protocols. TG 4 a 76 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Let’s look at the hooks for setup: • We already talked about using the MCPS-DATA. request to get the channel characterization and the counters turned on. • Using the pre-coordinated preambles is set up using a PLMEDPS. request. TG 4 a 77 Vern Brethour

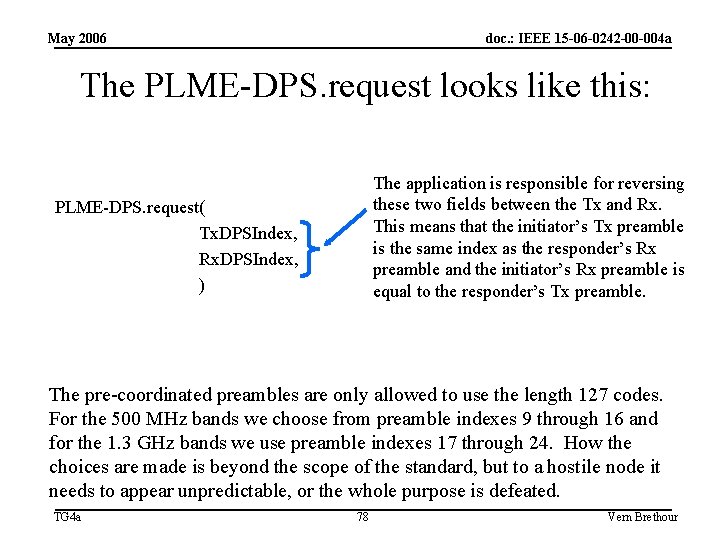
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The PLME-DPS. request looks like this: The application is responsible for reversing these two fields between the Tx and Rx. This means that the initiator’s Tx preamble is the same index as the responder’s Rx preamble and the initiator’s Rx preamble is equal to the responder’s Tx preamble. PLME-DPS. request( Tx. DPSIndex, Rx. DPSIndex, ) The pre-coordinated preambles are only allowed to use the length 127 codes. For the 500 MHz bands we choose from preamble indexes 9 through 16 and for the 1. 3 GHz bands we use preamble indexes 17 through 24. How the choices are made is beyond the scope of the standard, but to a hostile node it needs to appear unpredictable, or the whole purpose is defeated. TG 4 a 78 Vern Brethour

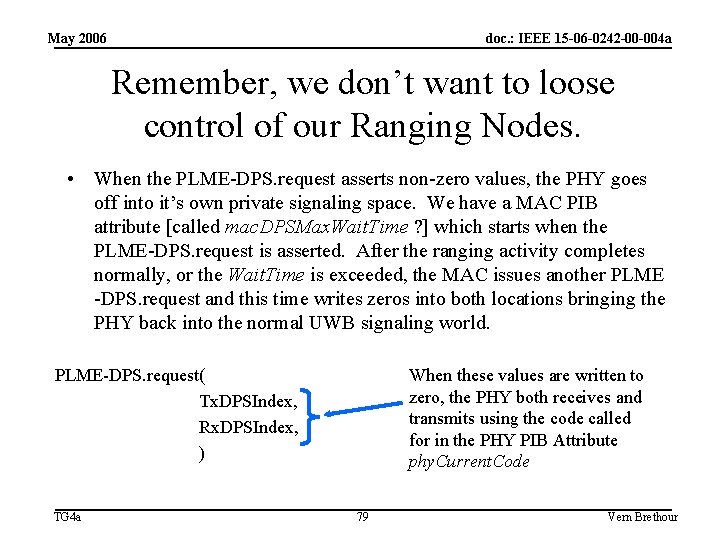
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Remember, we don’t want to loose control of our Ranging Nodes. • When the PLME-DPS. request asserts non-zero values, the PHY goes off into it’s own private signaling space. We have a MAC PIB attribute [called mac. DPSMax. Wait. Time ? ] which starts when the PLME-DPS. request is asserted. After the ranging activity completes normally, or the Wait. Time is exceeded, the MAC issues another PLME -DPS. request and this time writes zeros into both locations bringing the PHY back into the normal UWB signaling world. When these values are written to zero, the PHY both receives and transmits using the code called for in the PHY PIB Attribute phy. Current. Code PLME-DPS. request( Tx. DPSIndex, Rx. DPSIndex, ) TG 4 a 79 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Why aren’t the Tx. DPSIndex & Rx. DPSIndex in the PHY PIB table? • They could be, but there is no need for them to be. • The intent of their use was that they would only be non-zero for very brief periods and that whenever they are non-zero, there is an impatient timer running against them anxious to jerk them back to zero at timer expiration. TG 4 a 80 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Now let’s look at the data exchange. To keep track of where we are in here, we will use this message sequence chart: TG 4 a 81 Vern Brethour

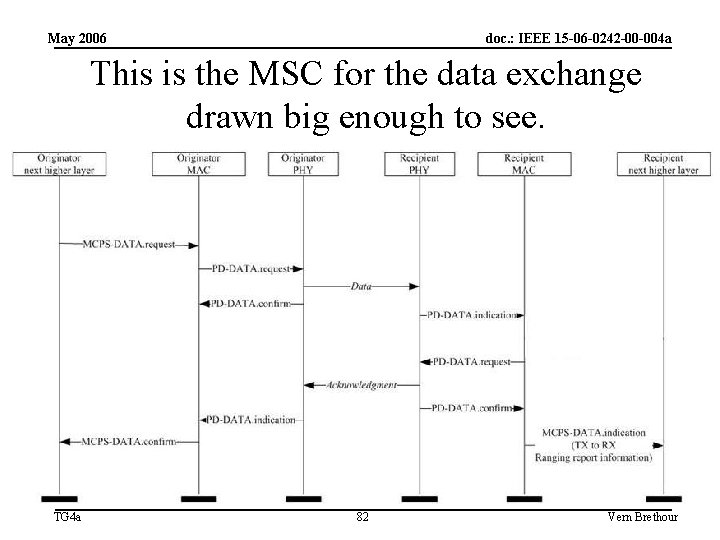
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a This is the MSC for the data exchange drawn big enough to see. TG 4 a 82 Vern Brethour

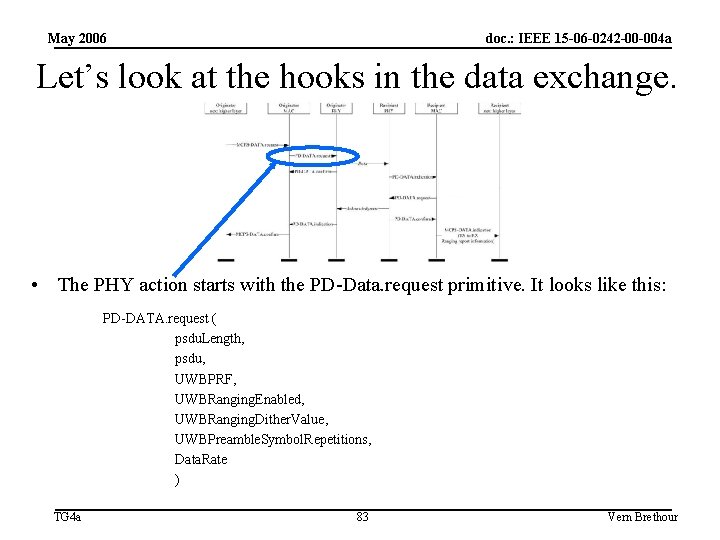
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Let’s look at the hooks in the data exchange. • The PHY action starts with the PD-Data. request primitive. It looks like this: PD-DATA. request ( psdu. Length, psdu, UWBPRF, UWBRanging. Enabled, UWBRanging. Dither. Value, UWBPreamble. Symbol. Repetitions, Data. Rate ) TG 4 a 83 Vern Brethour

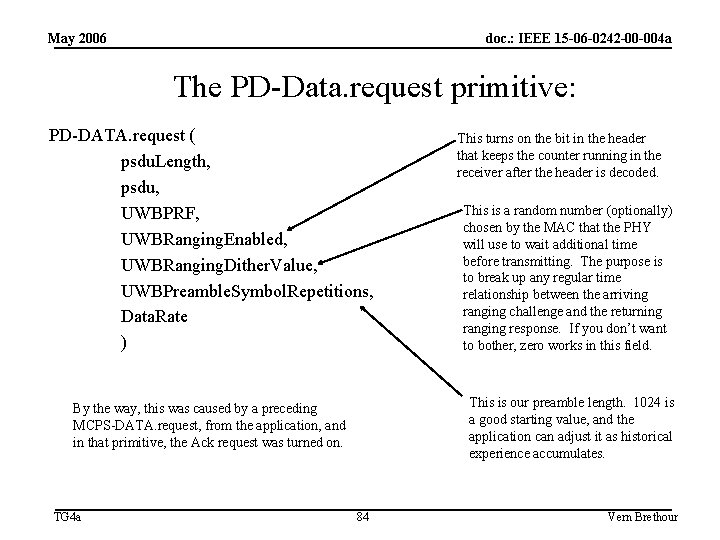
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a The PD-Data. request primitive: PD-DATA. request ( psdu. Length, psdu, UWBPRF, UWBRanging. Enabled, UWBRanging. Dither. Value, UWBPreamble. Symbol. Repetitions, Data. Rate ) This is a random number (optionally) chosen by the MAC that the PHY will use to wait additional time before transmitting. The purpose is to break up any regular time relationship between the arriving ranging challenge and the returning ranging response. If you don’t want to bother, zero works in this field. This is our preamble length. 1024 is a good starting value, and the application can adjust it as historical experience accumulates. By the way, this was caused by a preceding MCPS-DATA. request, from the application, and in that primitive, the Ack request was turned on. TG 4 a This turns on the bit in the header that keeps the counter running in the receiver after the header is decoded. 84 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Now we come to location awareness of non-ranging capable UWB 4 a devices. What if this is PHYHEADERONLY for a non-ranging-capable PHY? • Assuming that the request came in when the Tx was enabled, the non-ranging capable PHY will simply transmit the message using the preamble length specified and PD-DATA. request ( with the ranging bit turned on in the PHY psdu. Length, header. The PHY doesn’t know it, but the psdu, Ack request will also be turned off in the UWBPRF, MAC’s Frame Control field making this a UWBRanging, one-way ranging transmission. This PHY is UWBRanging. Dither. Value, really not ranging capable: No problem! UWBPreamble. Symbol. Repetitions, The infrastructure is going to take care of Data. Rate everything for him. ) No Problem, Just turn on the ranging bit in the PHY header and send it! TG 4 a 85 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What are the infrastructure nodes doing when these one-way transmissions arrive? . • Each arrival event at every infrastructure node causes a timestamp report to go to the local NHL for as long as the infrastructure device is enabled. • The standard expects the devices to keep up with this without regard for how quickly the one-way messages might arrive. TG 4 a 86 Vern Brethour

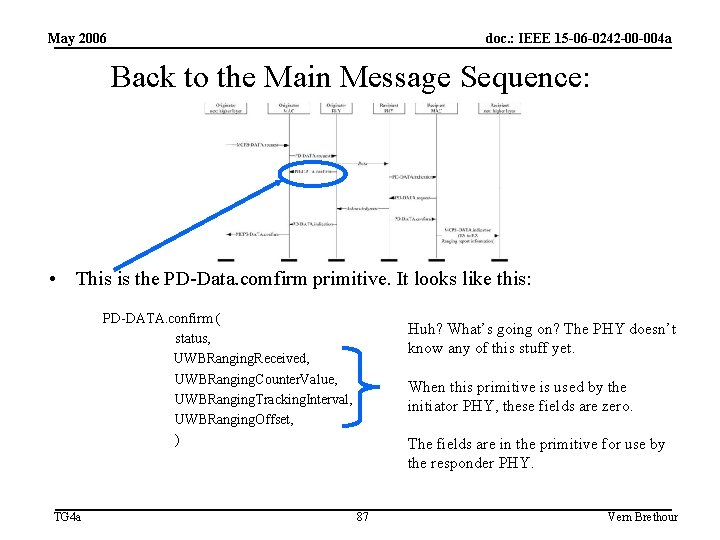
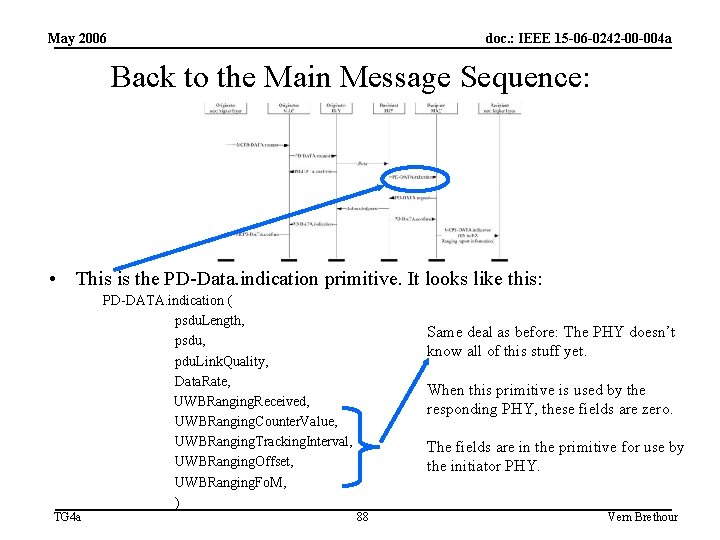
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Back to the Main Message Sequence: • This is the PD-Data. comfirm primitive. It looks like this: PD-DATA. confirm ( status, UWBRanging. Received, UWBRanging. Counter. Value, UWBRanging. Tracking. Interval, UWBRanging. Offset, ) TG 4 a Huh? What’s going on? The PHY doesn’t know any of this stuff yet. When this primitive is used by the initiator PHY, these fields are zero. The fields are in the primitive for use by the responder PHY. 87 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Back to the Main Message Sequence: • This is the PD-Data. indication primitive. It looks like this: PD-DATA. indication ( psdu. Length, psdu, pdu. Link. Quality, Data. Rate, UWBRanging. Received, UWBRanging. Counter. Value, UWBRanging. Tracking. Interval, UWBRanging. Offset, UWBRanging. Fo. M, ) TG 4 a Same deal as before: The PHY doesn’t know all of this stuff yet. When this primitive is used by the responding PHY, these fields are zero. The fields are in the primitive for use by the initiator PHY. 88 Vern Brethour

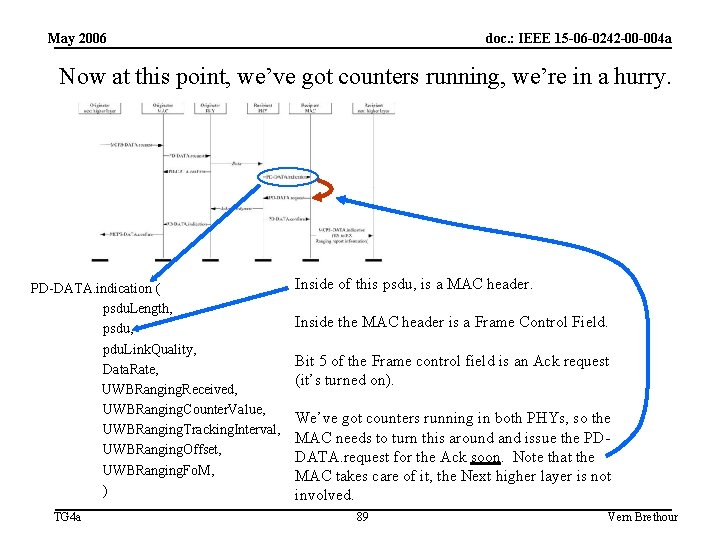
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Now at this point, we’ve got counters running, we’re in a hurry. PD-DATA. indication ( psdu. Length, psdu, pdu. Link. Quality, Data. Rate, UWBRanging. Received, UWBRanging. Counter. Value, UWBRanging. Tracking. Interval, UWBRanging. Offset, UWBRanging. Fo. M, ) TG 4 a Inside of this psdu, is a MAC header. Inside the MAC header is a Frame Control Field. Bit 5 of the Frame control field is an Ack request (it’s turned on). We’ve got counters running in both PHYs, so the MAC needs to turn this around and issue the PDDATA. request for the Ack soon. Note that the MAC takes care of it, the Next higher layer is not involved. 89 Vern Brethour

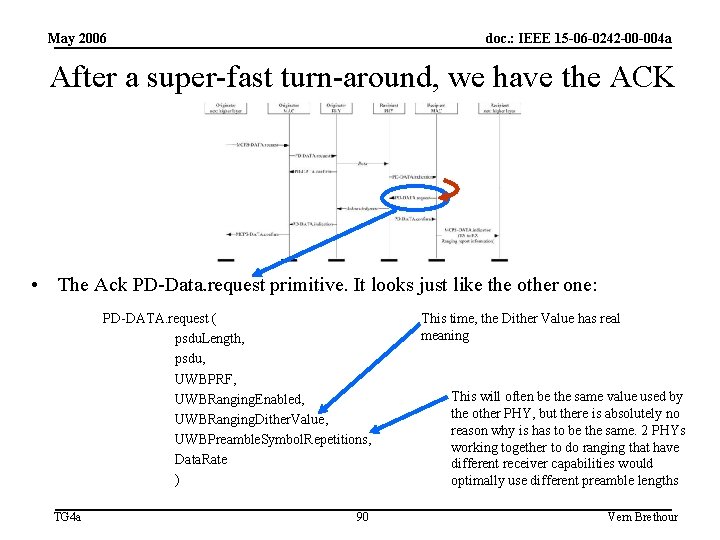
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a After a super-fast turn-around, we have the ACK • The Ack PD-Data. request primitive. It looks just like the other one: PD-DATA. request ( psdu. Length, psdu, UWBPRF, UWBRanging. Enabled, UWBRanging. Dither. Value, UWBPreamble. Symbol. Repetitions, Data. Rate ) TG 4 a 90 This time, the Dither Value has real meaning This will often be the same value used by the other PHY, but there is absolutely no reason why is has to be the same. 2 PHYs working together to do ranging that have different receiver capabilities would optimally use different preamble lengths Vern Brethour

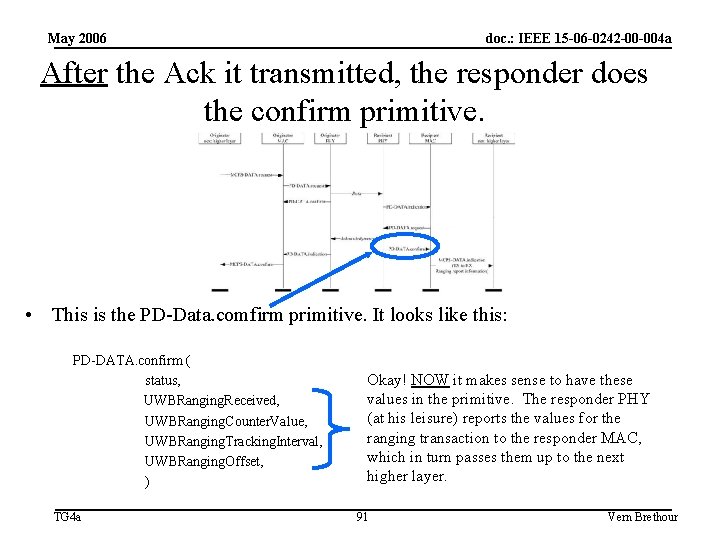
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a After the Ack it transmitted, the responder does the confirm primitive. • This is the PD-Data. comfirm primitive. It looks like this: PD-DATA. confirm ( status, UWBRanging. Received, UWBRanging. Counter. Value, UWBRanging. Tracking. Interval, UWBRanging. Offset, ) TG 4 a Okay! NOW it makes sense to have these values in the primitive. The responder PHY (at his leisure) reports the values for the ranging transaction to the responder MAC, which in turn passes them up to the next higher layer. 91 Vern Brethour

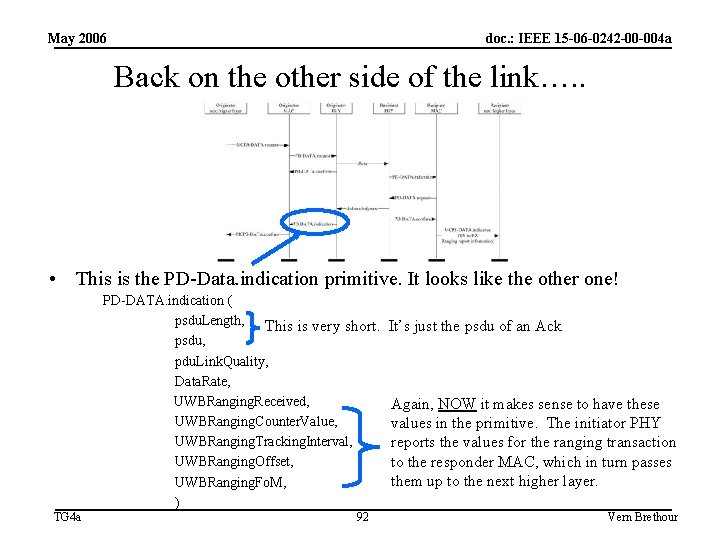
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Back on the other side of the link…. . • This is the PD-Data. indication primitive. It looks like the other one! PD-DATA. indication ( psdu. Length, This is very short. psdu, pdu. Link. Quality, Data. Rate, UWBRanging. Received, UWBRanging. Counter. Value, UWBRanging. Tracking. Interval, UWBRanging. Offset, UWBRanging. Fo. M, ) TG 4 a 92 It’s just the psdu of an Ack Again, NOW it makes sense to have these values in the primitive. The initiator PHY reports the values for the ranging transaction to the responder MAC, which in turn passes them up to the next higher layer. Vern Brethour

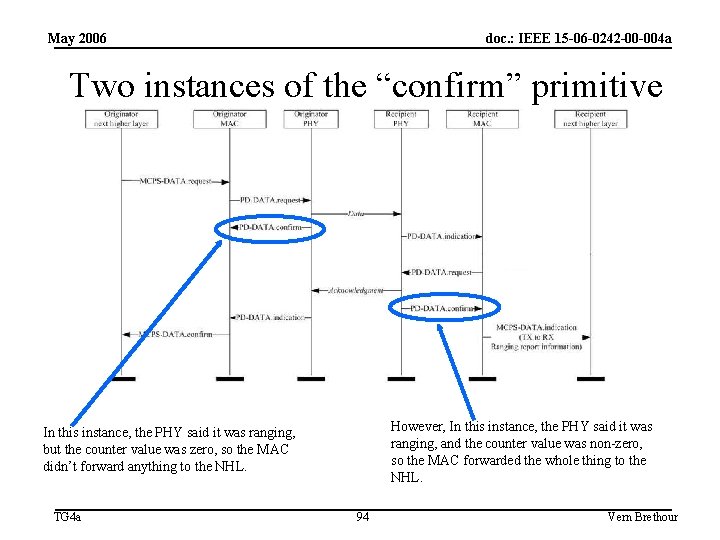
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Now that we see the general flow, let’s review what happened. • The trickiest thing might have been the dual use of the “indication” and the “confirm” primitives. • They were each used twice in the sequence, but the MAC response to them was not the same each time. • Let’s start with the “confirm” primitive. TG 4 a 93 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Two instances of the “confirm” primitive However, In this instance, the PHY said it was ranging, and the counter value was non-zero, so the MAC forwarded the whole thing to the NHL. In this instance, the PHY said it was ranging, but the counter value was zero, so the MAC didn’t forward anything to the NHL. TG 4 a 94 Vern Brethour

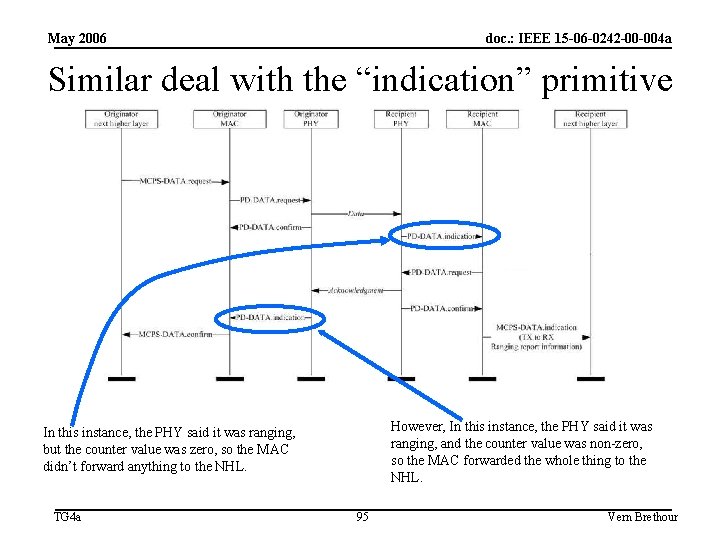
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Similar deal with the “indication” primitive However, In this instance, the PHY said it was ranging, and the counter value was non-zero, so the MAC forwarded the whole thing to the NHL. In this instance, the PHY said it was ranging, but the counter value was zero, so the MAC didn’t forward anything to the NHL. TG 4 a 95 Vern Brethour

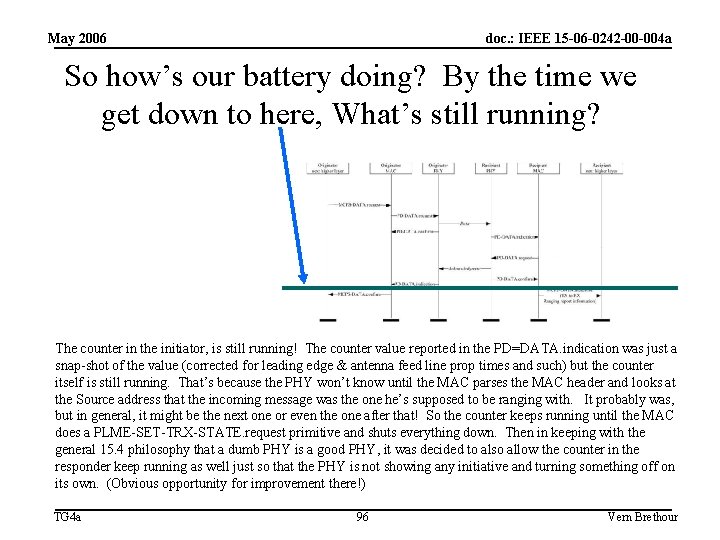
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a So how’s our battery doing? By the time we get down to here, What’s still running? The counter in the initiator, is still running! The counter value reported in the PD=DATA. indication was just a snap-shot of the value (corrected for leading edge & antenna feed line prop times and such) but the counter itself is still running. That’s because the PHY won’t know until the MAC parses the MAC header and looks at the Source address that the incoming message was the one he’s supposed to be ranging with. It probably was, but in general, it might be the next one or even the one after that! So the counter keeps running until the MAC does a PLME-SET-TRX-STATE. request primitive and shuts everything down. Then in keeping with the general 15. 4 philosophy that a dumb PHY is a good PHY, it was decided to also allow the counter in the responder keep running as well just so that the PHY is not showing any initiative and turning something off on its own. (Obvious opportunity for improvement there!) TG 4 a 96 Vern Brethour

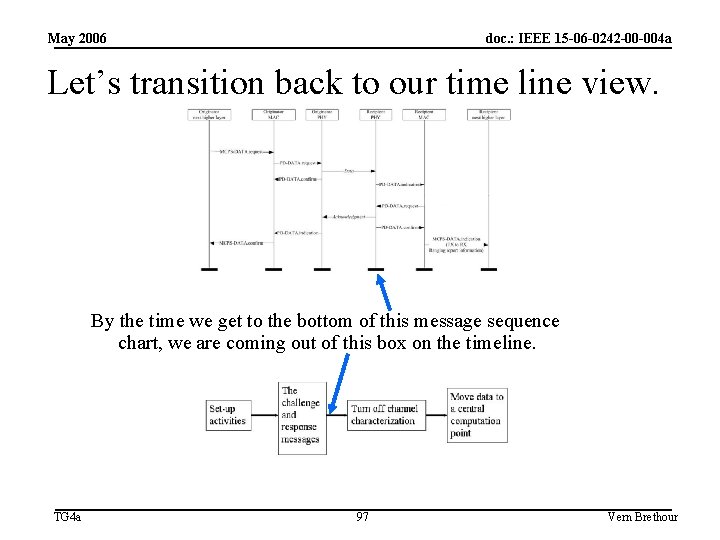
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Let’s transition back to our time line view. By the time we get to the bottom of this message sequence chart, we are coming out of this box on the timeline. TG 4 a 97 Vern Brethour

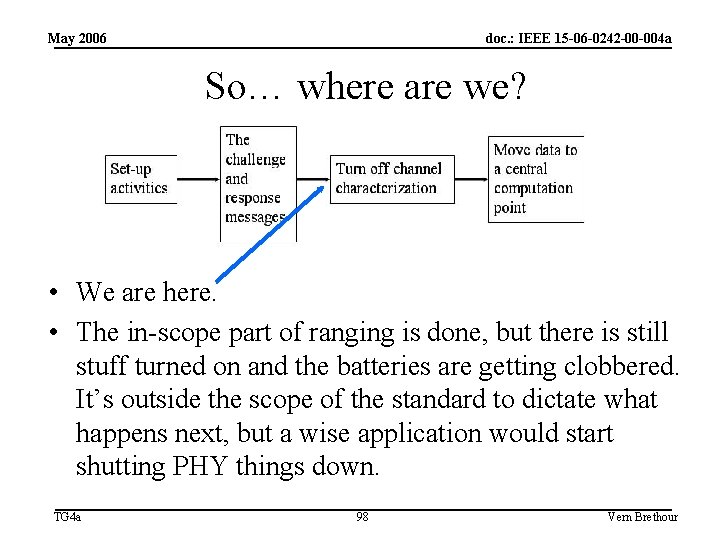
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a So… where are we? • We are here. • The in-scope part of ranging is done, but there is still stuff turned on and the batteries are getting clobbered. It’s outside the scope of the standard to dictate what happens next, but a wise application would start shutting PHY things down. TG 4 a 98 Vern Brethour

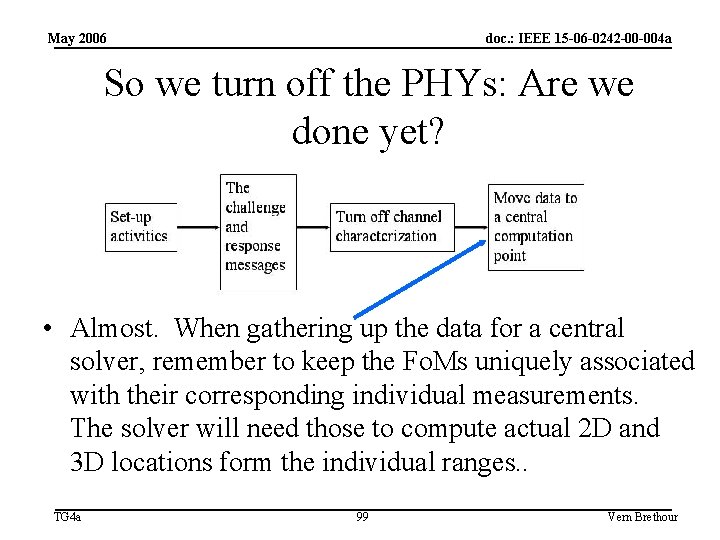
May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a So we turn off the PHYs: Are we done yet? • Almost. When gathering up the data for a central solver, remember to keep the Fo. Ms uniquely associated with their corresponding individual measurements. The solver will need those to compute actual 2 D and 3 D locations form the individual ranges. . TG 4 a 99 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a So there we have it! • That’s the way ranging is set up in Draft 2. • There was only the very slightest and most modest tampering with the MAC established by 802. 15. 4 b • What’s not to love about this? TG 4 a 100 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a What’s not to love about ranging in Draft 2? • Well, actually, at least 4 things: 1. The way Draft 2 is written, the PHY gets no help with calibration tasks. {CID 146, 25, 26, 46, & 48} 2. The way Draft 2 is written, the PHY has to do the timestamp arithmetic between start and stop. {CID 2, 23, 28, 30, 44, 50, & 52} 3. The way Draft 2 is written, the PHY gets no help with leading edge computations. {CID 145} 4. The way Draft 2 is written, the PHY is supposed to keep up with a steady stream of leading edge computations. {CID 7} TG 4 a 101 Vern Brethour

May 2006 doc. : IEEE 15 -06 -0242 -00 -004 a Are these things fixable? • Yes. • More to follow. TG 4 a 102 Vern Brethour