Master Card International Credit Card Security Risk IS






































































- Slides: 92

Master. Card International Credit Card Security & Risk IS 6800 Group Presentation Mike Cornish Kathleen Delpha Mary Erslon November 2004 1

Agenda n n Master. Card Organization Credit Card 101 Credit Card Fraud Case Studies ¡ ¡ n Card Not Present Fraud Identity Theft Fraud Best Practices for Credit Card Security 2

Master. Card Organization 3

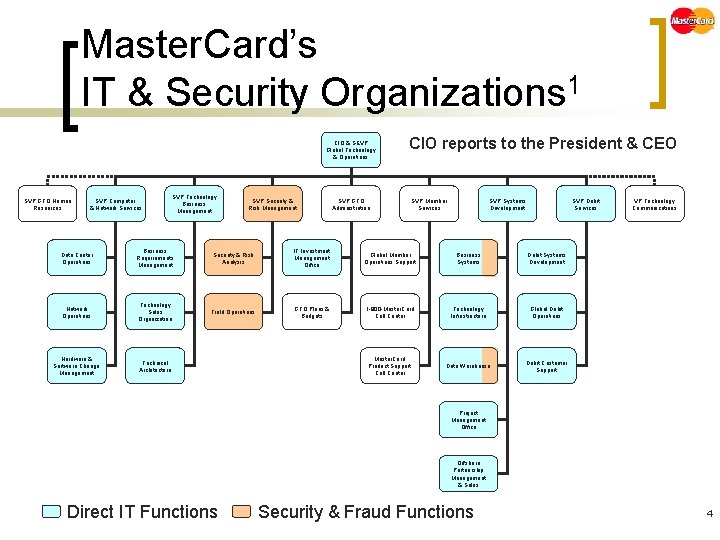
Master. Card’s IT & Security Organizations 1 CIO & SEVP Global Technology & Operations SVP GTO Human Resources SVP Computer & Network Services SVP Technology Business Management SVP Security & Risk Management CIO reports to the President & CEO SVP GTO Administration SVP Member Services SVP Systems Development SVP Debit Services Data Center Operations Business Requirements Management Security & Risk Analysis IT Investment Management Office Global Member Operations Support Business Systems Debit Systems Development Network Operations Technology Sales Organization Field Operations GTO Plans & Budgets 1 -800 -Master. Card Call Center Technology Infrastructure Global Debit Operations Hardware & Software Change Management Technical Architecture Master. Card Product Support Call Center Data Warehouse Debit Customer Support VP Technology Communications Project Management Office Offshore Partnership Management & Sales Direct IT Functions Security & Fraud Functions 4

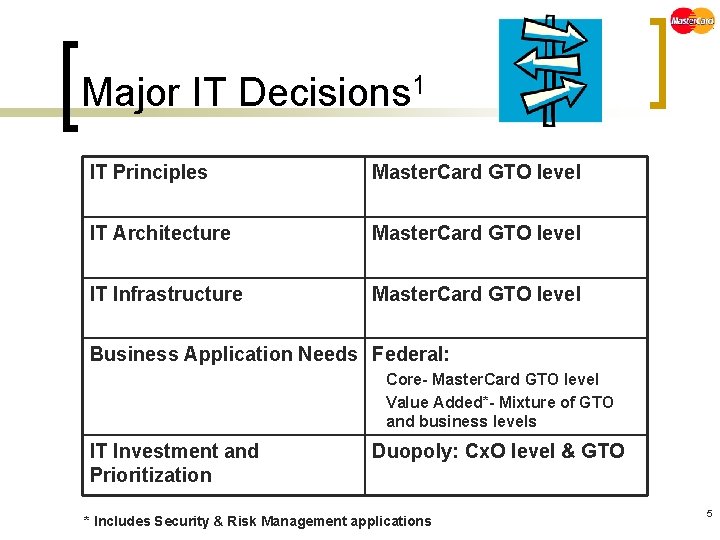
Major IT Decisions 1 IT Principles Master. Card GTO level IT Architecture Master. Card GTO level IT Infrastructure Master. Card GTO level Business Application Needs Federal: Core- Master. Card GTO level Value Added*- Mixture of GTO and business levels IT Investment and Prioritization Duopoly: Cx. O level & GTO * Includes Security & Risk Management applications 5

Governance 1 n Transitioning to IT Duopoly at the Cx. O level from IT Monarchy ¡ ¡ All IT spending remains under control of GTO led initiative to bring transparency to the IT decision making processes, and to bring business involvement into IT investment management Cx. O level sets budget for technology investment & decides priorities GTO investment management office n n Facilitates business prioritization by Cx. O level Allocates & tracks technology spending across GTO 6

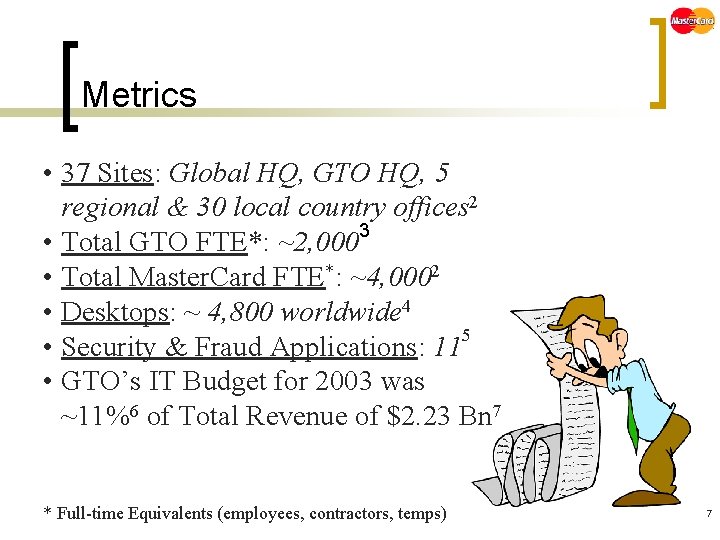
Metrics • 37 Sites: Global HQ, GTO HQ, 5 regional & 30 local country offices 2 • Total GTO FTE*: ~2, 0003 • Total Master. Card FTE*: ~4, 0002 • Desktops: ~ 4, 800 worldwide 4 • Security & Fraud Applications: 115 • GTO’s IT Budget for 2003 was ~11%6 of Total Revenue of $2. 23 Bn 7 * Full-time Equivalents (employees, contractors, temps) 7

Credit Card 101 8

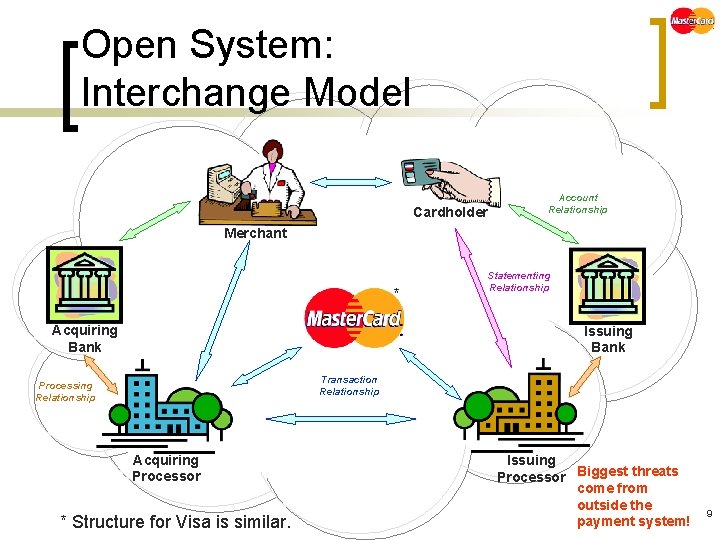
Open System: Interchange Model Cardholder Account Relationship Merchant * Acquiring Bank Statementing Relationship Issuing Bank Transaction Relationship Processing Relationship Acquiring Processor * Structure for Visa is similar. Issuing Processor Biggest threats come from outside the payment system! 9

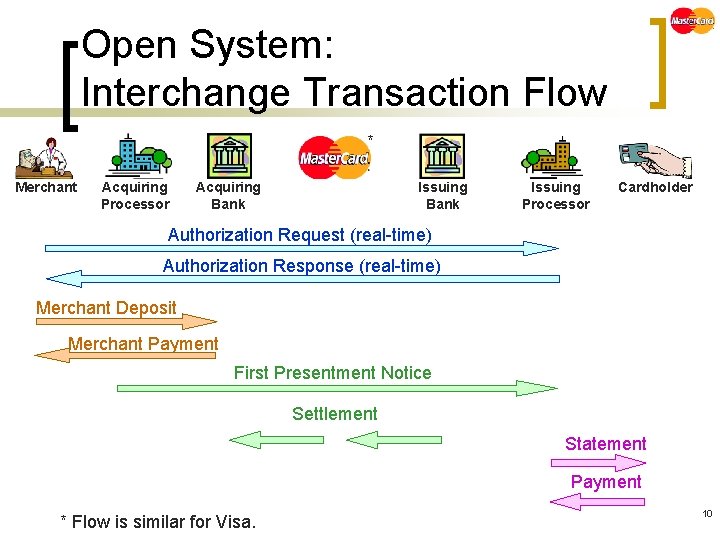
Open System: Interchange Transaction Flow * Merchant Acquiring Processor Acquiring Bank Issuing Processor Cardholder Authorization Request (real-time) Authorization Response (real-time) Merchant Deposit Merchant Payment First Presentment Notice Settlement Statement Payment * Flow is similar for Visa. 10

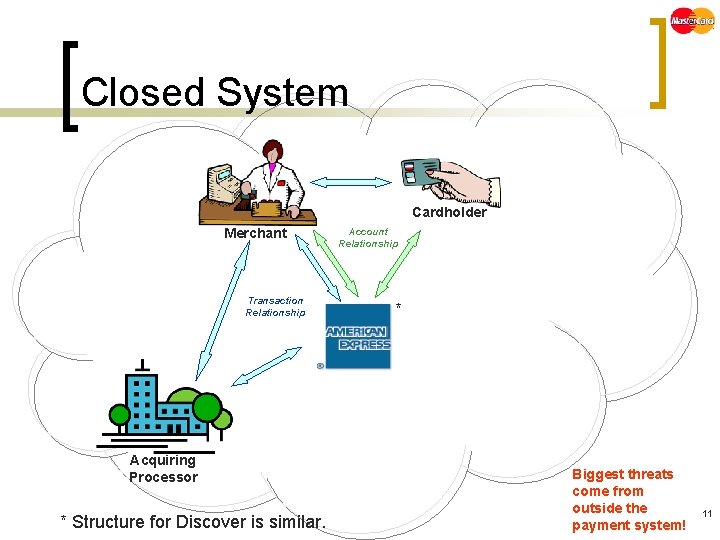
Closed System Cardholder Merchant Transaction Relationship Acquiring Processor * Structure for Discover is similar. Account Relationship * Biggest threats come from outside the payment system! 11

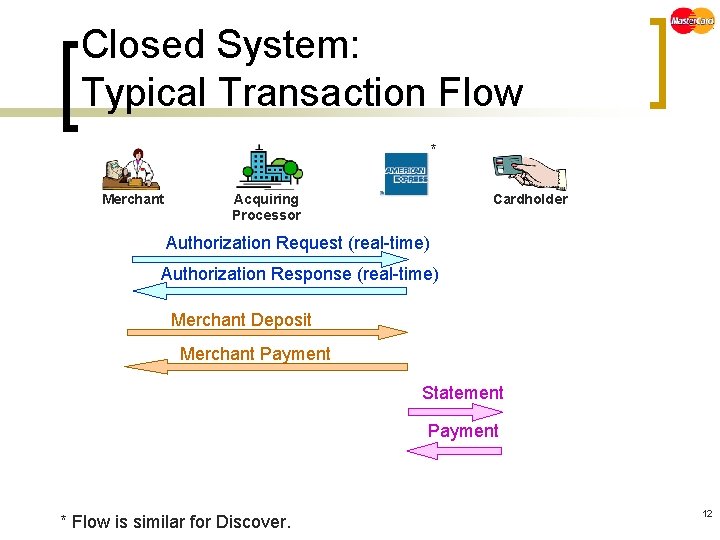
Closed System: Typical Transaction Flow * Merchant Acquiring Processor Cardholder Authorization Request (real-time) Authorization Response (real-time) Merchant Deposit Merchant Payment Statement Payment * Flow is similar for Discover. 12

Master. Card’s Space n Master. Card International is a global payments company 2 ¡ ¡ n Membership corporation of 25, 000 financial institutions that issue Master. Card, Maestro, and Cirrus branded cards Licensor and franchisor for the Master. Card, Maestro, and Cirrus payment brands 2003 Key Business Indicators 2, 8 ¡ ¡ ¡ Gross volume: US$ 1, 272 Bn Number of transactions: 13. 2 Bn Number of account: 529. 5 MM Number of cards: 632. 4 MM Number of merchants: 22. 0+ MM in 210 Countries Number of ATMs: 900 K+ in 120+ Countries 13

Not Master. Card’s Space 2 n Master. Card does not… ¡ ¡ Issue cards Set annual fees on cards Determine annual percentage rates (APRs) Solicit merchants to accept cards or set their discount rates 14

Credit Card Fraud Master. Card’s Strategies 15

Headlines “ ” “ Jan 23, 2003 ” “ Sep 12, 2003 ” “ Aug 5, 2004 ” Oct 24, 2003 “ ” Feb 19, 2003 “ ” March 17, 2003 “ “ ” Nov 20, 2001 ” Feb 27, 2003 ” “ Sep 12, 2003 16

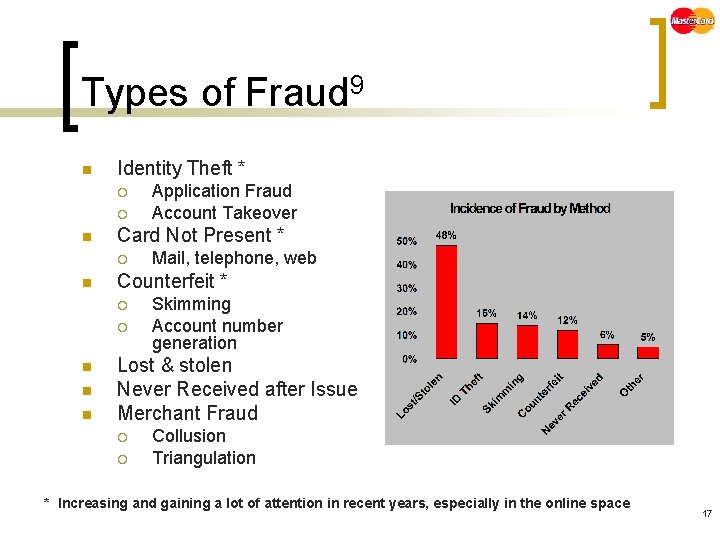
Types of Fraud 9 n Identity Theft * ¡ ¡ n Card Not Present * ¡ n n Mail, telephone, web Counterfeit * ¡ n Application Fraud Account Takeover Skimming Account number generation Lost & stolen Never Received after Issue Merchant Fraud ¡ ¡ Collusion Triangulation * Increasing and gaining a lot of attention in recent years, especially in the online space 17

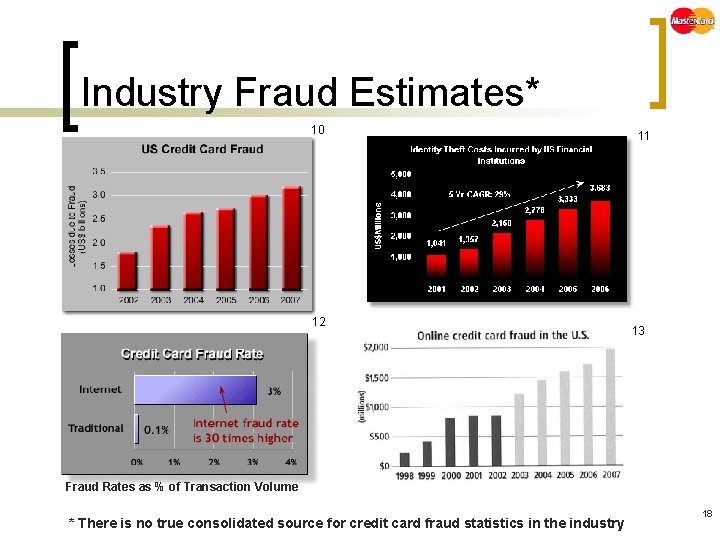
Industry Fraud Estimates* 10 12 11 13 Fraud Rates as % of Transaction Volume * There is no true consolidated source for credit card fraud statistics in the industry 18

Master. Card’s Security & Risk Mission: 14 “Protect brand integrity and manage fraud risk through best in class core and value added services with integrated end to end solutions to help position Master. Card as the Global Payments Leader ” 19

Security & Risk Management Applications & Services 5 Application or Service Fraud Type 20 Awareness Detection Prevention

Case Study Card Not Present Fraud 21

“Card Not Present” Defined n Definition 9: ¡ ¡ ¡ n Neither the card nor the cardholder is present at the point-of-sale Merchants are unable to check the physical security features of the card to determine if it is genuine Ecommerce; online or telephone transactions No way to dispute a cardholder claim that a purchase wasn’t made 22

Ecommerce Market 15 n > $3 Trillion worldwide n Master. Card research shows that 90% of online buyers worry about their personal and financial information online 23

Statistics n n n Master. Card CNP incidents account for between 80 and 84% of credit card fraud 16 Online fraud rates up to 30 x higher than in the physical world 17 2003 - $1. 6 B or ~2% of all online sales lost to credit care fraud 17 2004 credit card fraud rate has decreased by 0. 5% since 2000, but the amount lost has increased by 60%19 Projected losses to internet merchants in 2005 expected to be $5 - $15 billion 9 24

Statistics (continued) n Merchant Risk Council Survey 200319 ¡ Fraud chargeback rates > 1% = 9. 7% n ¡ Fraud chargeback rates < 0. 35% = 64% n ¡ 50% reduction since 2002 30% increase since 2002 17% of merchants spent > 2% of revenue on fraud prevention n 30% increase since 2002 25

Examples of Card Not Present Credit Card Fraud n Low-Tech: ¡ ¡ n Dumpster Diving Card Loss/Theft High Tech: ¡ ¡ ¡ Phishing or site cloning Account number generators Online “auctions” or false merchant sites 26

Card Not Present n May be caused by ¡ ¡ ¡ Less-than-diligent cardholder (dumpster diving, theft) Cardholder response to plausible ploy (phishing) May be out of cardholder’s control (numbers generator, hacking) 27

Combating CNP Fraud: Legislative Examples n Anti-Phishing Act of 200420 ¡ ¡ ¡ Introduced 07/04 by Sen. Leahy (D-VT) Phishing responsible for $2 B in merchant losses/year Enters 2 new crimes into US Crime Code n n E-mail that links to sham websites with the intent of committing a crime The sham websites that are the true scene of the crime 28

Combating CNP Fraud: Legislative Examples n n n State laws 21 regulate the amount of information on a credit card receipt to the last four numbers of the credit card Expiration date may not appear on receipt CA, WA, MD, CT enacting legislation 29

Combating CNP Fraud: Consumer n n Education and Awareness Consumer “Best Practices” 30

Combating CNP Fraud: Merchant n Multi-level technical solutions ¡ ¡ Cardholder Authentication Neural Networks 31

Case Study: Secure. Code™ n Licensed Master. Card cardholder authentication solution 15 enables cardholders to authenticate themselves to their issuer through the use of a unique personal code (PIN) A VISA counterpart is “Verified by VISA” or “Vby. V. ” 32

Secure. Code 15 n Cardholders enter their secure code in a separate browser window before an online transaction can be authorized ¡ ¡ Requires a merchant “plug-in, ” or software module, to be deployed on the merchant’s website Requires the merchant to use a data transport mechanism and processing support 33

Secure. Code 15 n n n The participating merchant gets explicit evidence of an authorized purchase (authentication data) Fully guaranteed online payments – protection from chargebacks Master. Card mandated that issuers implement support for Master. Card Secure Code by November 1, 2004 34

Secure. Code and e. Tronics 22 n A Top Ten Internet consumer electronics retailer ¡ ¡ n n n >200, 000 customers and 300, 000 orders annually Over $65 million in yearly sale In 2002, e. Tronics had credit card chargeback costs of over 1 million/year Implemented Secure. Code in 2003 “Too soon to tell” impact since Secure. Code is not yet implemented globally, but e. Tronics is “optimistic and enthusiastic” about its success 35

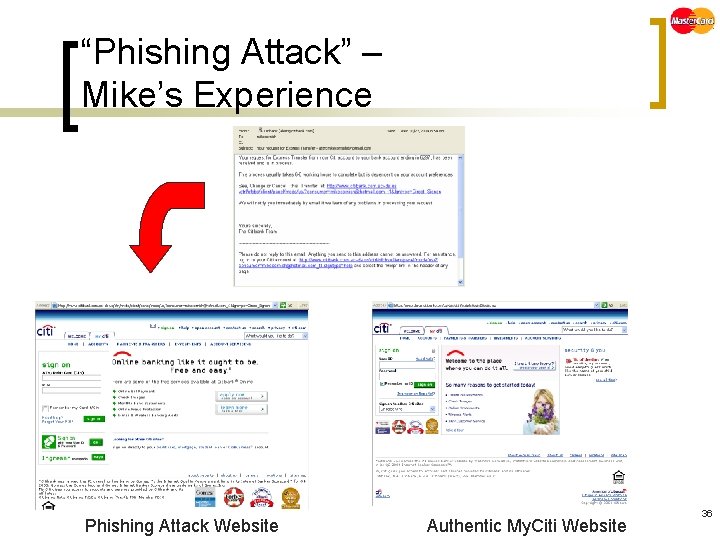
“Phishing Attack” – Mike’s Experience Phishing Attack Website Authentic My. Citi Website 36

Case Study: Risk. Finder™ n n n A “neural network” system Fair Isaac’s proprietary profiling technology for fraud prevention – Risk. Finder 23 is a Master. Card-specific application Enables transactions to be “scored” based on highly detailed cardholder patterns/behavior, existing patterns of fraud, and merchant trend data 23 37

Case Study: Risk. Finder™ n n The institution can establish a transaction score threshold, and conduct supplemental review and cardholder follow-up on any transaction that scores above threshold 23 Risk. Finder has saved issuers up to 50% in fraud losses 23 38

Citibank Fraud Detection (Click the thumbnail to play the commercial) www. fightidentitytheft. com/video/babe_magnet. mpeg, Viewed, October 30, 2004 39

Risk. Finder and Kathleen’s Story n Kathleen’s daughter goes camping in Venice. 40

Case Study Identity Theft Fraud 41

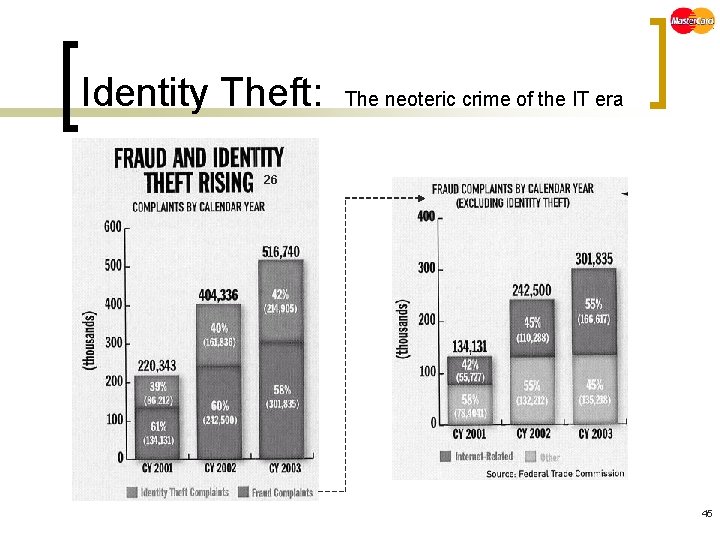
Identity Theft: The neoteric crime of the IT era n 24 Identity theft is the illicit use of another individual’s identifying facts to perpetrate an economic fraud, such as ¡ ¡ Opening a bank account Obtaining bank loans or credit Applying for bank or department store cards Or leasing cars or apartments in the name of another. 24 42

Citibank Identity Theft (Click the thumbnail to play the commercial) www. fightidentitytheft. com/video/flaps_mpls_te_mpg. mpeg, Viewed, October 30, 2004 43

Identity Theft: n n The neoteric crime of the IT era Number one source of consumer complaints to the Federal Trade Commission (FTC) in 2001(and thereafter)25 Credit card fraud was most common form of identity theft in 2002 according to the FT 25 44

Identity Theft: The neoteric crime of the IT era 26 45

Identity Theft: n The neoteric crime of the IT era “Compared to equally profitable crimes involving drug or gun trafficking, the sentencing for identity fraud is much lighter—and these folks are tough to catch. ” - Bruce Townsend Special Agent in charge of Financial Crimes Division Secret Service 27 46

Identity Theft: n n The neoteric crime of the IT era In 52% of cases in which the victim discovered how the information was stolen, the thief turned out to be a family member, neighbor, or coworker. 28 Low-Tech sources include: ¡ Paper records of personal information kept by numerous sources. 47

Identity Theft: The neoteric crime of the IT era 29 48

Identity Theft: Causes n Phishing ¡ “Stealing corporations’ identities as a means to impersonating individuals” 30 n Greater number pieces of personal information = greater chance of Identity Theft 49

Identity Theft: ¡ ¡ To counteract phishing, corporations are using software to search for sites breaching their copyrights, then go directly to the company hosting the bogus site to get it shut down. 30 5% of consumers respond to phishing according to the Anti-Phishing Working Group. 31 50

Identity Theft: High Tech Causes n Hacking merchant sites, home computers and any place where personal information is stored. ¡ ¡ Servers that aren’t set up correctly can be compromised by techniques like “end-mapping, ” which “pings” servers systematically until it finds an open port to exploit. Trojan horse content can slip by ordinary packet filter devices deployed by firewalls (spyware, keyloggers). 32 51

Identity Theft: ¡ ¡ High Tech Causes Commandeering other applications. Eavesdropping Software that reports to the hacker a person’s keystrokes and uses it to pick up passwords and gain entry. 32 52

Identity Theft: High tech Causes n Case Study: “Operation Firewall”. ¡ ¡ ¡ 28 Identity Theft Suspects arrested 1. 7 million stolen credit card numbers Investigation instigated by Master. Card’s senior vice president of security risk services. 33 53

Identity Theft: Low tech Causes n n Security firms tend to stress physical security issues, which are easier to identify and remedy than human vulnerabilities. Financial institutions, in order to reduce the risk from within, must create and sustain an institutional culture that values and promotes critical thinking, high self-esteem and genuine loyalty to the institution. 34 54

Identity Theft: Actions to Combat n Legislative ¡ ¡ ¡ ¡ Identity Theft and Assumption Deterrence Act of 199824 Privacy Act of 200135 Consumer Privacy Protection Act, May 200229 Identity Theft Prevention Act, Jan 200329 SSN Misuse Prevention Act, Jan 200329 Fair and Accurate Credit Transactions Act of 200336 Anti-Phishing Act of 2004 20 55

Identity Theft: Actions to Combat n Payment Industry—calling for implementation of technology that definitively corresponds the user to the instrument. 27 56

Identity Theft: Actions to Combat ¡ Identity Authentication Technologies n Biometrics ¡ ¡ ¡ n Face recognition Retina scans Fingerprint authentication Voice /speech verification Handwriting analysis Genetic Engineering ¡ Analyzing DNA components of human fluids & cells. 25 57

Identity Theft: Actions to Combat ¡ Use of Public Key Infrastructure (PKI) n n n Digital signature Protects electronic records Inherent security hinges on who has access to system. 25 58

Identity Theft: Actions to Combat ¡ System embedded security controls to enhance the privacy and confidentiality of information processed across Internet architectures n n Data encryption Digital signatures Secure socket layers (SSL) Cryptographic protocols such as hypertext transfer protocol over SSL (HTTPS)37 59

Identity Theft: Actions to Combat ¡ Smart Cards n n Contain embedded CPU (electronic chip). 32 -kilobyte mini-processors are capable of generating 72 quadrillion encryption keys. Can be programmed to perform tasks & store information. Practically impossible to fraudulently decode. 9 60

Identity Theft: Actions to Combat ¡ Personnel & Procedures n n n Background checks Limit access through password protection Leave an audit trail of who got into files & when Shred information being thrown away Train staff by creating a security handbook 25 61

Identity Theft: Actions to Combat n Designate a Privacy Officer –could be the Information Manager “Privacy and security do not work if you do not have top-level buy-in. Information managers might very well be the key people within the organization to help accomplish this. ” - Gary Clayton Founder & Chairman The Privacy Council 25 62

Identity Theft: Actions to Combat ¡ Use of a layered approach to security n n ¡ Perimeter App-layer protection Intrusion detection Monitoring tools Strategic rather than silver-bullet approach 32 63

Issuers Clearinghouse n n n Joint Master. Card and Visa service. To detect fraudulent and high-risk credit card applications. Screens, validates & tracks ¡ ¡ ¡ Addresses Phone numbers Social Security numbers 38 64

Name. Protect® n n n Monitors Internet 24 x 7 Watches all g. TLD and cc. TLDs, new registrations, and activations. “Identifies Web sites, emails, chat rooms and other electronic venues where personal credit card data is published, sold or traded. ” 39 65

Identity Theft “Rather than posing security as a hurdle to overcome, companies should view their customers’ privacy needs as an opportunity through which they can differentiate themselves as trust leaders, increase their financial value and even energize entire economies. ” Glover T. Ferguson Chief Scientist Accenture 26 66

Best Practices 67

Best Practices: All Industries 40 n Protect your employees and customers from ID theft ¡ ¡ Ask only for necessary information Don’t use SSNs as identifiers Regularly check backgrounds of employees who have access to identifying information Define a privacy policy and communicate it to your customers and employees 68

Best Practices: All Industries 40 n Protect sensitive paper information like payment card numbers, social security numbers, and customer identifying data ¡ ¡ Secure records in a vault or under lock-and-key Restrict access only to persons with a legitimate need to know Shred records when they are no longer needed Immediately report security breaches to affected customers and law enforcement 69

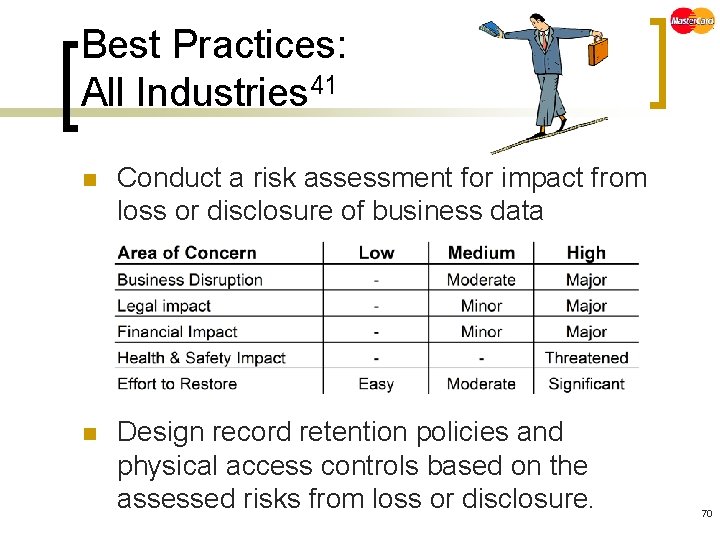
Best Practices: All Industries 41 n Conduct a risk assessment for impact from loss or disclosure of business data n Design record retention policies and physical access controls based on the assessed risks from loss or disclosure. 70

Best Practices: IT Functions 42, 43 n n n Use firewalls, anti-virus, anti-spyware, and access control software to protect networks and computers Keep operating system and security software up-todate with latest security patches from vendors Define policies for strong passwords and change them frequently Monitor for signs of network and web server attack Monitor security websites for breaking information about new threats and best practices (e. g. , CERT® Coordination Center) 71

Best Practices: IT Functions 43 n Protect sensitive electronic info like customer identifying data and account numbers ¡ Segregate sensitive data on separate servers from web servers ¡ Restrict data access rights to only those persons and systems with legitimate need to know ¡ Consider encrypting sensitive information housed in databases 72

Best Practices: Consumers 44 n n Only give payment account numbers or personal identification information to companies you have contacted ¡ Challenge businesses that ask for it about why they need to know ¡ Avoid saying information over the phone when others may hear Do not carry unnecessary payment cards or identification papers (e. g. , social security card, birth certificate) in your wallet or purse ¡ Do not use SSN for your driver’s license or other identification cards 73

Best Practices: Consumers 44 n Keep track of receipts for payment card transactions ¡ n n Shred receipts and account statements having full account numbers Cancel unused credit card accounts* Keep a list of all of your payment card account numbers along with their issuers’ names and contact numbers so you cancel them quickly if lost or stolen * But be aware of potential credit score impact 74

Best Practices: Consumers 45 n n Use firewall, anti-virus, and anti-spyware software Keep your PC operating system and security software up-to-date with latest security patches from your vendors Be suspicious of emails and websites requesting private information Verify URLs and make sure websites are secure before entering account numbers and personal identifying information ¡ ¡ Be careful locating sites through search engines Call the company if you are unsure of the validity of a site 75

Best Practices: Merchants 46 n Card Present ¡ ¡ ¡ Check that the embossing extends into the hologram Check the hologram and indent printing Compare the signature on the card and sales draft Check that the magnetic strip appears authentic Call for a “Code 10” authorization if something doesn’t feel right 76

Best Practices: Merchants 21 n Card not Present ¡ ¡ ¡ Use address verification systems to check the account holder’s billing address Implement Secure. Code and Verified by Visa services Include card verification values/codes in authorization messages (but do not store them in your database) 77

Best Practices: Merchants 21 n Card not Present (Continued) ¡ ¡ Require complete customer contact and payment information before completing an order Process transactions in real-time n ¡ keep the customer on the website until the payment card is authorized and the sale is completed Monitor international transactions 78

Best Practices: Merchants 21 n Card not Present (Continued) ¡ ¡ ¡ Employ rules-based systems to screen and detect suspicious order activity Maintain negative databases of fraudulent orders & offenders, and positive databases of trusted returning customers Adopt Master. Card’s Best Practices for e. Commerce websites n Have a Site Data Protection audit done on your e. Commerce website 79

Best Practices: Acquirers & Merchant Processors n Merchant Acquirers & Processors ¡ ¡ ¡ Provide security features like Address and Card Verification services to merchants Monitor merchant deposit velocity for unexpected increases in deposits Check & report merchant’s termination history 80

Best Practices: Issuers & Card Processors n Card Issuers & Processors ¡ ¡ Monitor cardholder purchase and cash velocity for drastic changes Use behavioral models/neural network software to detect fundamental changes in cardholders’ behaviors 81

Best Practices: Payment Companies n Payment Companies ¡ ¡ ¡ Create, refresh & enforce standards Monitor to detect shifts in types and volumes of fraudulent activity Conduct research to innovate new fraud detection and prevention mechanisms 82

Questions & Answers 83

References 84

References 1. 2. 3. 4. 5. 6. Fisher, Bill. Pers. Comm. VP Processing Strategy, Master. Card International. Interviewed by telephone by Mike Cornish, October 26, 2004. “Master. Card Corporate Fact Sheet, ” www. mastercardinternational. com/docs/corporate_fact_sheet_0804. pdf, viewed October 18, 2004. “Global Technology and Operations, ” Fact Sheet. www. mastercardinternational. com/newsroom/gto. html, viewed October 18, 2004. “Total Cost of Ownership Analysis. ” Internal document: Powerpoint Presentation. Technology & Architecture Services, Master. Card International, February 26, 2003, page 4. “Application Portfolio: Security & Risk Applications. ” Internal document: Word document. Master. Card International, March 27, 2003. “ 2003 GTO & Division Level Financial Data. ” Internal document: Excel Sheet. GTO Division, Master. Card International, January 3, 2003. 85

References 7. 8. 9. 10. 11. 12. Master. Card International SEC Form 10 K – March 4, 2004, www. sec. gov/Archives/edgar/data/1141391/000095012304002820/ y 94488 e 10 vk. htm, pages 6, 22 -24, viewed October 19, 2004. Master. Card International SEC Form 8 K – February 3, 2004, www. sec. gov/Archives/edgar/data/1141391/000095012304001154/ y 93767 e 8 vk. txt, viewed October 18, 2004, pages 3. Bhatla, TP, Prabhu, V, and Dua, A. “Understanding Credit Card Frauds”. Card Business Review #2003 -01, June 2003, pp 1 -15. “Taking a Bite our of Credit Card Fraud, ” Celent Communications, www. celent. com/Press. Releases/20030121/Credit. Card. Fraud. htm, viewed October 28, 2004. “Identity Theft: Protecting the Customer – Protecting the Institution, ” Celent Communications, www. celent. com/Press. Releases/20020731(2)/IDTheft. htm, viewed October 28, 2004. “Online Payment Fraud: The Grinch who stole Christmas? ” Celent Communications, www. celent. com/Press. Releases/20001218/Online. Fraud. htm, viewed October 28, 2004. 86

References 13. 14. 15. 16. 17. 18. Valentine, Lisa. “The Fraudsters’ Playground. ” American Bankers Association. ABA Banking Journal, 95(8), Aug. 2003, p. 39. “Security & Risk Mission & Overview. ” Document, Master. Card International, February 24, 2003. “Master. Card Secure. Code for Online Merchants. ” Online security document for merchants. http: //www. mastercardmerchant. com/docs/securecode/Merchant_B rochure. pdf, viewed October 20, 2004. Bennett, RA. “I didn’t do it. ”. USBanker 111(12), December 2001, p. 48. “Online fraudsters take $1. 6 B out of 2003 e. Commerce. ” Cyber. Source, www. retailindustry. about. com/cs/lp_internet/a/bl_cs 111803. htm, viewed October 20, 2004. US Credit Card Fraud Statistics 2000 -2007. Celent Communications, www. epaynews. com/statistics/fraud. html, viewed October 18, 2004. 87

References 19. 20. 21. 22. 23. Merchant Risk Council Press Release, www. merchantriskcouncil. org/press. php? p_press_id+13, February 3, 2003, viewed October 21, 2004. “New Leahy Bill Targets INTERNET “PHISHING” That Steals $2 b. /yr. from Consumers. ” July 2004. www. leahy. senate. gov/press/200404/070904 c. html. Micci-Barreca, D. “Unawed by Fraud. ” Security Management 47(9), p. 75. “Master. Card Secure. Code Case Study: e. Tronics. ” 2003. http: //www. mastercardmerchant. com/docs/SC_Case_Studye. Tronics. pdf. , viewed October 21, 2004. Master. Card Risk. Finder. “Solutions. ” http: //www. fairisaac. com/cgibin/Msm. Go. exe? grab_id=13&page_id=655872&query=Risk. Finder& hiword=Risk. Finder+, viewed October 21, 2004. 88

References 24. 25. 26. 27. 28. 29. Saunders, Kurt M. , and Zucker, Bruce, “Counteracting Identity Fraud in the Information Age: The Identity Theft and Assumption of Deterrence Act” International Review of Law, Computers & Technology, August 1999, 183– 192. Groves, Shanna, “Protecting Your Identity” Information Management Journal, May/June 2002, 27 -31. Myron, David, “Stolen Names, Big Numbers” American Demographics, September 2004, 36 -38. Bielski, Lauren, “Identity Theft” ABA Banking Journal, January 2001, 27 -30. Diller-Haas, Amy, “Identity Theft: It Can Happen to You” The CPA Journal, April 2004, 42 -44. Riordan, Diane A. , and Riordan, Michael P. , “Who Has Your Numbers? ” Strategic Finance, April 2003, 22 -26. 89

References 30. 31. 32. 33. 34. 35. 36. O’Sullivan, Orla, “Gone ‘Phishing’” ABA Banking Journal, November 2003, 7 -8. Bauerle, James F. , “Pattern Recognition Software and Dramas of Deception: New Challenges in Electronic Financial Services” The RMA Journal, October 2004, 2 -5. Bielski, Lauren, “Striving to Create a Safe Haven Online” ABA Banking Journal, May 2003, 53 -59. Krebs, Brian, “ 28 Identity Theft Suspects Arrested in Transatlantic Sting, ” The Washington Post, October 29, 2004. Bauerle, James F. , “Golden Eye Redux” The Banking Law Journal, March 2003, 1 -15. Heller, Jason, “New Senate Privacy Bill Addresses Personally Identifiable Information” Intellectual Property & Technology Law Journal, September 2001, 31 -32. http: //frwebgate. access. gpo. gov/cgibin/useftp. cgi? IPaddress=162. 140. 64. 21&filename=h 2622 eas. pdf& directory=/diskb/wais/data/108_cong_bills , viewed October 25, 2004. 90

References 37. 38. 39. 40. 41. 42. 43. Phillips, John T. , “Privacy vs. Cybersecurity” Information Management Journal, May/June 2002, 46 -50. https: //www. merchantconnect. com/CWRWeb/glossary. do? glossar y. Letter=i , Viewed October 30, 2004. http: //www. nameprotect. com/html/services/id_theft/credit_card. htm l, Viewed October 30, 2004. “How can I protect my customers from identify theft? ” Colorado Attorney General: ID Theft Prevention & Information, www. ago. state. co. us/idtheft/clients. htm, viewed November 3, 2003. “Network Security Policy: Best Practices White Paper, ” Cisco Systems, www. cisco. com/warp/public/126/secpol. html, Page 2, viewed November 2, 2004. CERT® Security Improvement Modules, CERT® Coordination Center, www. cert. org/security-improvement, viewed November 2, 2004. “Webserver Security Best Practices”, PC Magazine, www. pcmag. com/article 2/0, 4149, 11525, 00. asp, viewed November 2, 2004. 91

References 44. 45. 46. “Tips for Preventing Credit Card Fraud, ” Master. Card International, www. mastercardinternational. com/newsroom/security_risk. html, viewed October 22, 2004. “Best Practices for Preventing Online identity Theft”, Public Safety and Emergency Preparedness Canada, www. ocipepbpiepc. gc. ca/opsprods/info_notes/IN 04 -002_e. asp, viewed November 2, 2004. “Preventing Fraud: Fighting Fraud is a Shared Responsibility, ” Master. Card International, www. mastercardmerchant. com/preventing_fraud, viewed October 28, 2004. 92
 Market risk assessment
Market risk assessment Credit risk in international trade
Credit risk in international trade 3 1 checking accounts worksheet answers
3 1 checking accounts worksheet answers Disadvantages of debit cards
Disadvantages of debit cards Provate security
Provate security Explain about visa international security mode
Explain about visa international security mode This can be avoided by giving credit where credit is due.
This can be avoided by giving credit where credit is due. What is basel 3
What is basel 3 Hedge fund credit risk
Hedge fund credit risk Credit risk types
Credit risk types Anz risk management framework
Anz risk management framework Credit risk management and advisory goldman sachs
Credit risk management and advisory goldman sachs Lending policies and procedures managing credit risk
Lending policies and procedures managing credit risk Measuring and managing credit risk
Measuring and managing credit risk Credit risk management framework
Credit risk management framework Quantifying credit risk
Quantifying credit risk Christoffersen elements of financial risk management
Christoffersen elements of financial risk management Hedging credit risk with options
Hedging credit risk with options Metodo irb
Metodo irb Ncua aires questionnaire
Ncua aires questionnaire International credit
International credit Mlict
Mlict University of washington credit card
University of washington credit card Randolph brooks credit card
Randolph brooks credit card Credit card
Credit card Wells fargo credit card machine
Wells fargo credit card machine Ravi credit card
Ravi credit card Credit card trivia
Credit card trivia Raspberry pi credit card
Raspberry pi credit card Credit card statement worksheet
Credit card statement worksheet 4024 credit card
4024 credit card Lisa purchases a professional racing bicycle
Lisa purchases a professional racing bicycle Credit cards 101
Credit cards 101 Caribbean credit card corporation
Caribbean credit card corporation Objectives of credit card
Objectives of credit card Lillian purchased a guitar from smash
Lillian purchased a guitar from smash 3 6 credit card statement
3 6 credit card statement Unicredit consumer financing
Unicredit consumer financing Sandander credit card
Sandander credit card Pivotal credit card processing
Pivotal credit card processing Credit card presentation
Credit card presentation Citidirect card management system
Citidirect card management system Citi commercial card app
Citi commercial card app Crutchfield credit card
Crutchfield credit card Travel and entertainment card
Travel and entertainment card Piqst
Piqst Freedom pay credit card processing
Freedom pay credit card processing Credit card vocabulary
Credit card vocabulary Moneysmart credit card
Moneysmart credit card Lanpass card
Lanpass card Cornell credit card
Cornell credit card Us bank perks
Us bank perks The minimum monthly payment for janet's credit card is 2%
The minimum monthly payment for janet's credit card is 2% Airplus portal
Airplus portal John biggins credit card
John biggins credit card Credit card
Credit card Nedbank senior travel insurance
Nedbank senior travel insurance Sequence diagram for credit card fraud detection
Sequence diagram for credit card fraud detection Advantages and disadvantages of debit card
Advantages and disadvantages of debit card Recorded cash and credit card sales
Recorded cash and credit card sales Internet only bank
Internet only bank Lesson nine credit card charge
Lesson nine credit card charge Adcb bank rate aed to inr
Adcb bank rate aed to inr Credit card derivatives
Credit card derivatives Credit card journal entry
Credit card journal entry Secret history of the credit card worksheet answers
Secret history of the credit card worksheet answers Recorded cash and credit card sales
Recorded cash and credit card sales Six rulers nfl team
Six rulers nfl team Spring security zero to master download
Spring security zero to master download Master your card lovelifepassport
Master your card lovelifepassport Risk projection
Risk projection Risk avoidance insurance
Risk avoidance insurance Absolute risk vs relative risk
Absolute risk vs relative risk Residual risk and secondary risk pmp
Residual risk and secondary risk pmp Inherent risks examples
Inherent risks examples Absolute risk vs relative risk
Absolute risk vs relative risk Activity sheet 2: stock market calculations
Activity sheet 2: stock market calculations Pestle risk classification system
Pestle risk classification system Pembelanjaan risiko
Pembelanjaan risiko The biggest risk is not taking any risks
The biggest risk is not taking any risks Fiduciary investment risk management association
Fiduciary investment risk management association Ar = ir x cr x dr
Ar = ir x cr x dr Business vs financial risk
Business vs financial risk Attributable risk
Attributable risk Risk map
Risk map Relative risk
Relative risk Chapter 13 return risk and the security market line
Chapter 13 return risk and the security market line Risk in security analysis and portfolio management
Risk in security analysis and portfolio management Mips security risk analysis
Mips security risk analysis Maritime security risk analysis model
Maritime security risk analysis model Professional risk managers international association
Professional risk managers international association Legal risks in international business
Legal risks in international business Riskminds americas
Riskminds americas