Maslows hierarchy of network programming and the unmet













- Slides: 28

Maslow’s hierarchy of network programming and the unmet needs Ratul Mahajan Microsoft Research



How we got here

How we got here Programmability was not a goal!

Why we can escape our fate now Many new networks r o opp y t i tun Bigger networks pr d e e n g n i s s e

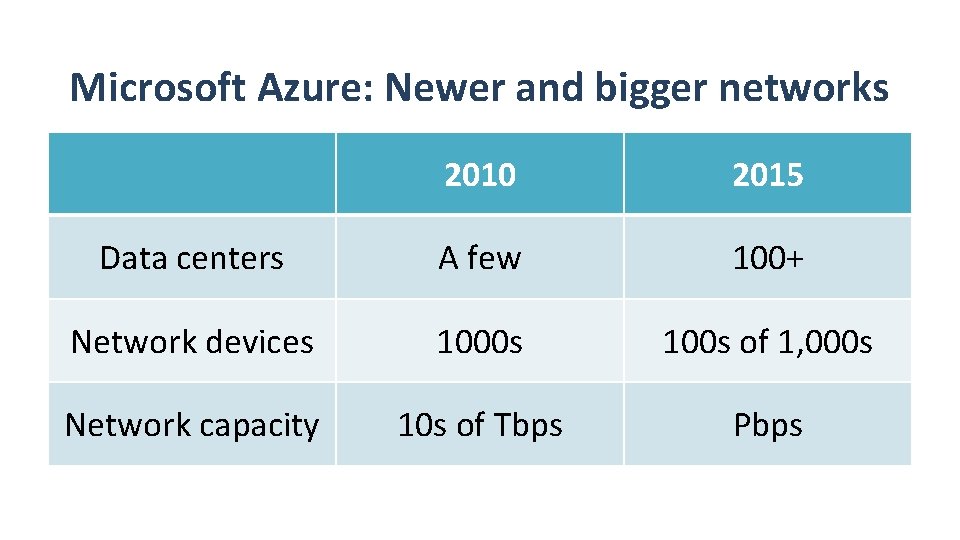
Microsoft Azure: Newer and bigger networks 2010 2015 Data centers A few 100+ Network devices 1000 s 100 s of 1, 000 s Network capacity 10 s of Tbps Pbps

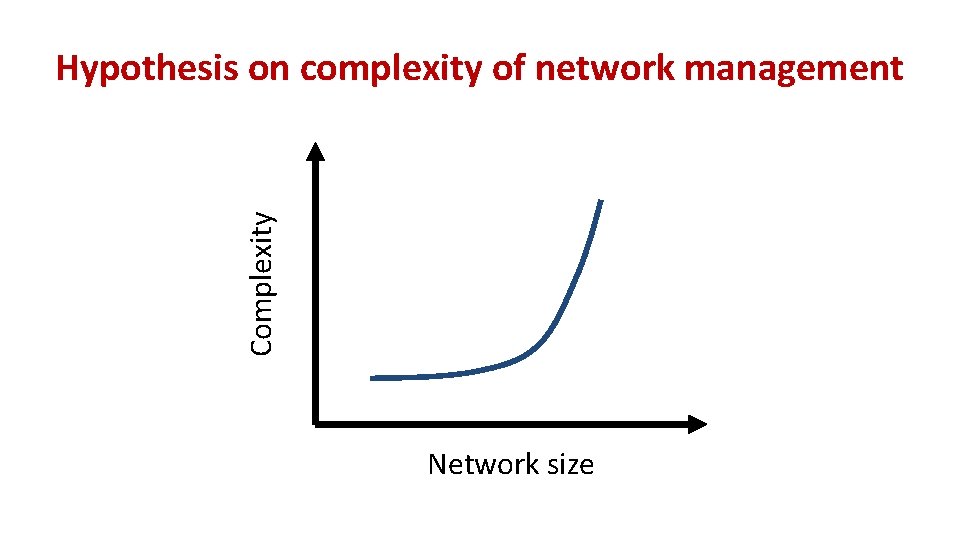
Complexity Hypothesis on complexity of network management Network size

Why we can escape our fate now Many new networks r o opp y t i tun Bigger networks pr d e e n g n i s s e Standardized abstractions key r e l b ena

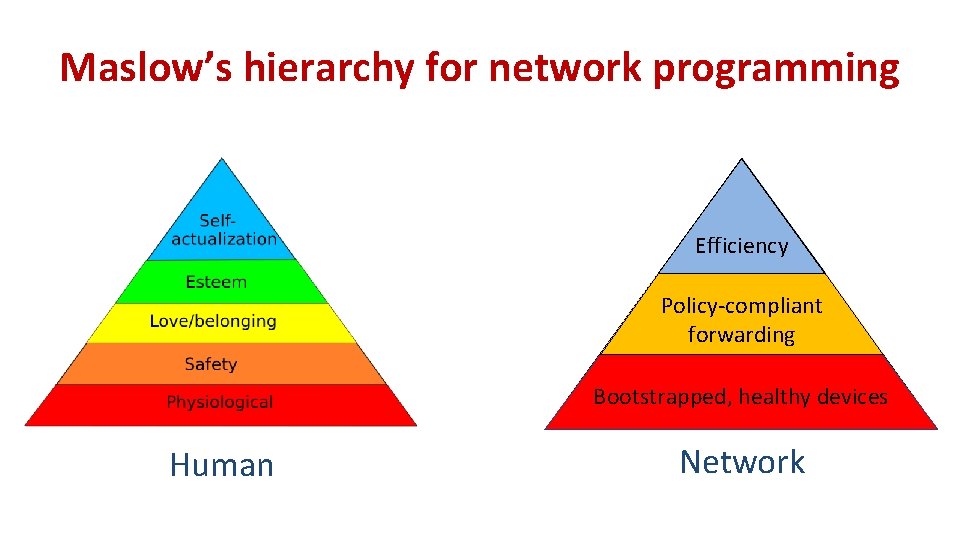
Maslow’s hierarchy for network programming Efficiency Policy-compliant forwarding Bootstrapped, healthy devices Human Network

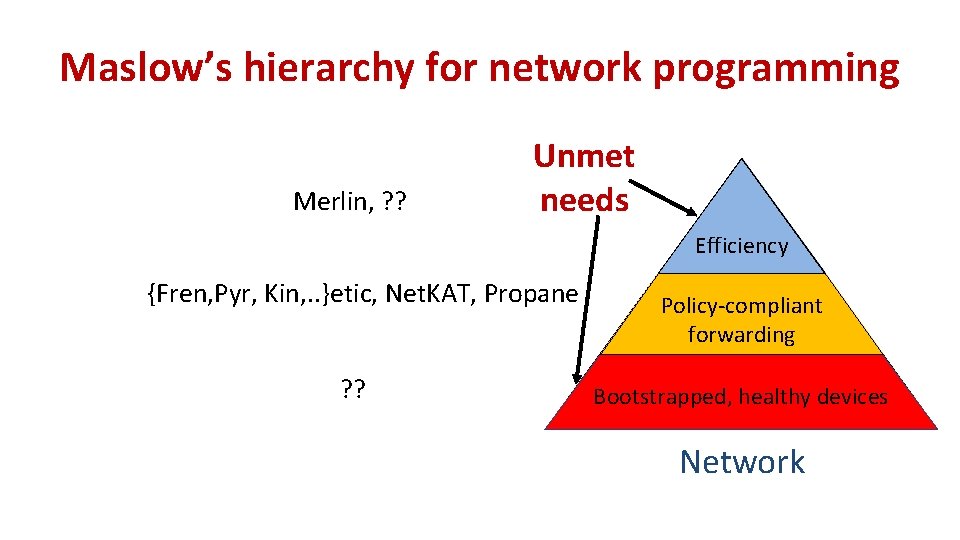
Maslow’s hierarchy for network programming Merlin, ? ? Unmet needs Efficiency {Fren, Pyr, Kin, . . }etic, Net. KAT, Propane ? ? Policy-compliant forwarding Bootstrapped, healthy devices Network

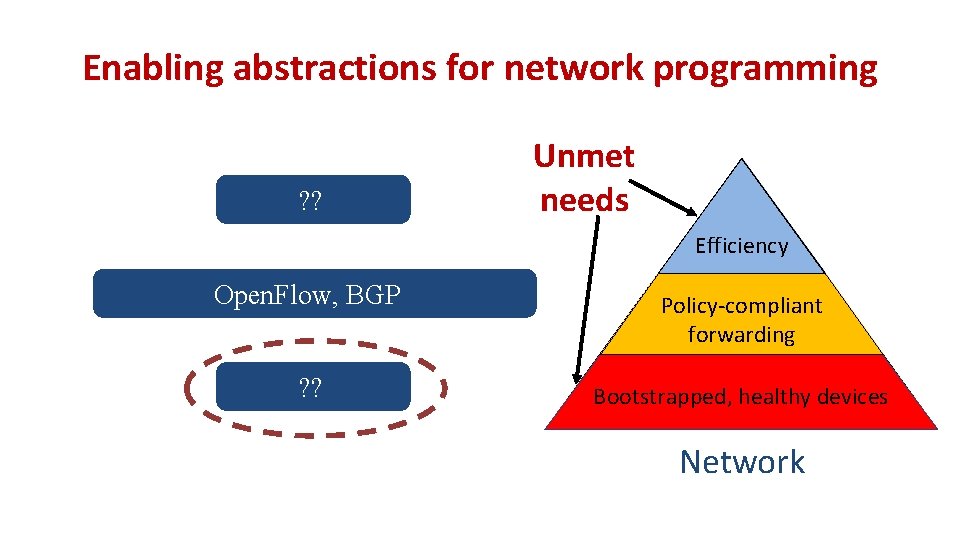
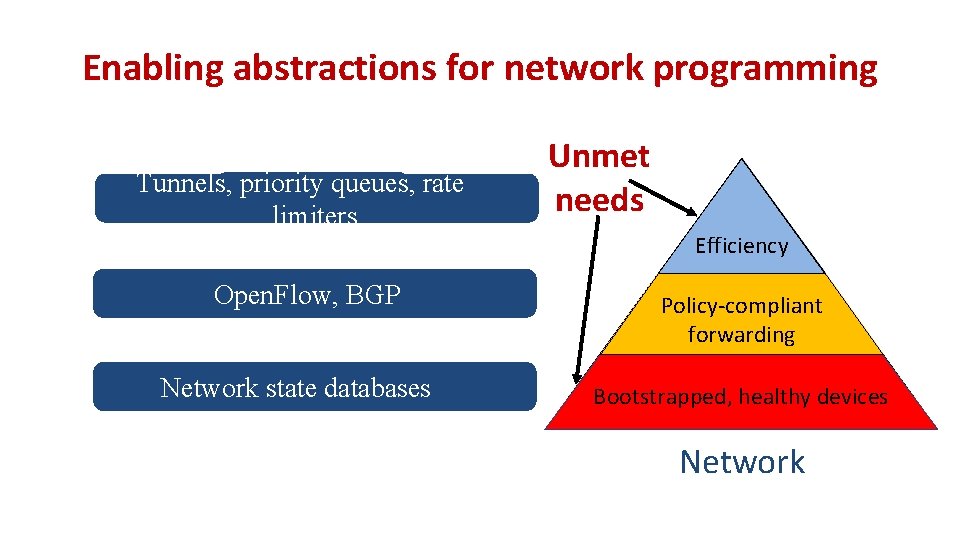
Enabling abstractions for network programming ? ? Unmet needs Efficiency Open. Flow, BGP Policy-compliant forwarding ? ? Bootstrapped, healthy devices Network

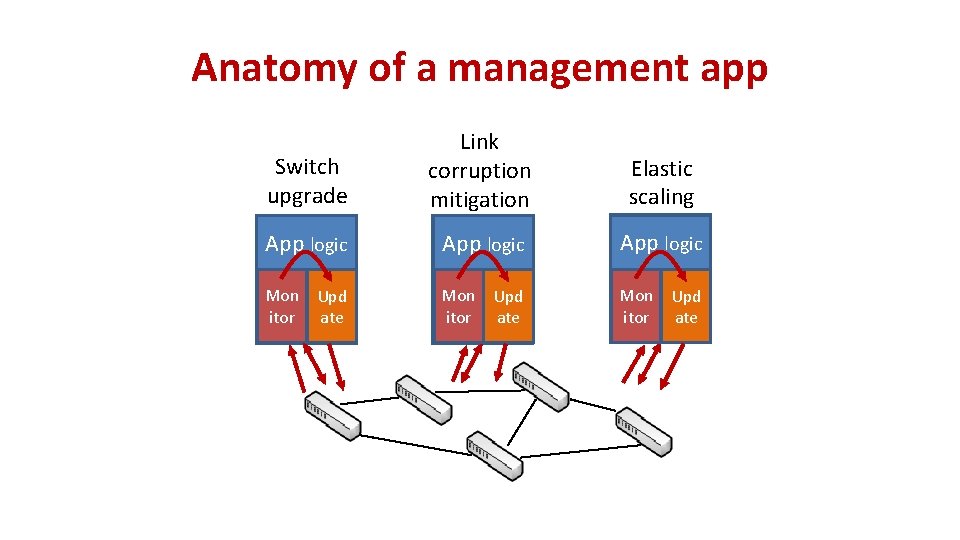
Past: Management apps interacted with devices Switch upgrade Link corruption mitigation Elastic scaling Conflicts among apps Hard to guarantee SLAs Hard to develop applications

Anatomy of a management app Switch upgrade Link corruption mitigation Elastic scaling App logic Mon Upd itor ate

Statesman: Network state management service App logic Network state database Monitor [A network-state management service, SIGCOMM 2014] Update Power on/off Firmware version Link state Tunnels …. .

Statesman: Network state management service App logic Observed state Proposed state Monitor Update Target state

State databases emerging at device level too SAI and SONi. C (OCP) https: //github. com/opencomputeproject/SAI https: //github. com/Azure/SONi. C Switch state service

What is missing from state databases High-level languages to read and write network state – Program network as a whole, given operator goals – Statesman, So. NIC are low-level • E. g. , read/write individual state variables

Enabling abstractions for network programming ? ? Unmet needs Efficiency Open. Flow, BGP Network state ? ? databases Policy-compliant forwarding Bootstrapped, healthy devices Network

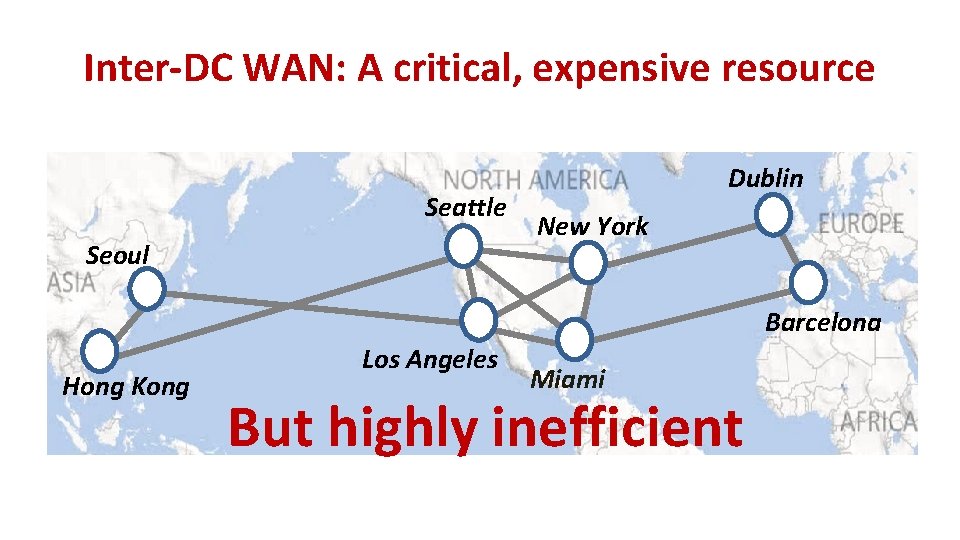
Inter-DC WAN: A critical, expensive resource Seattle Seoul Dublin New York Barcelona Hong Kong Los Angeles Miami But highly inefficient

Cause of inefficiency: Lack of coordination

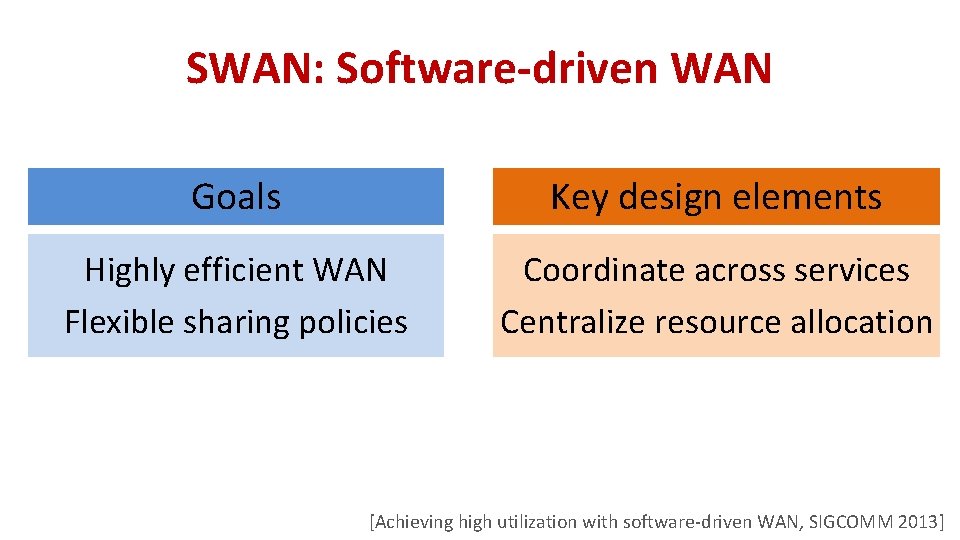
SWAN: Software-driven WAN Goals Key design elements Highly efficient WAN Flexible sharing policies Coordinate across services Centralize resource allocation [Achieving high utilization with software-driven WAN, SIGCOMM 2013]

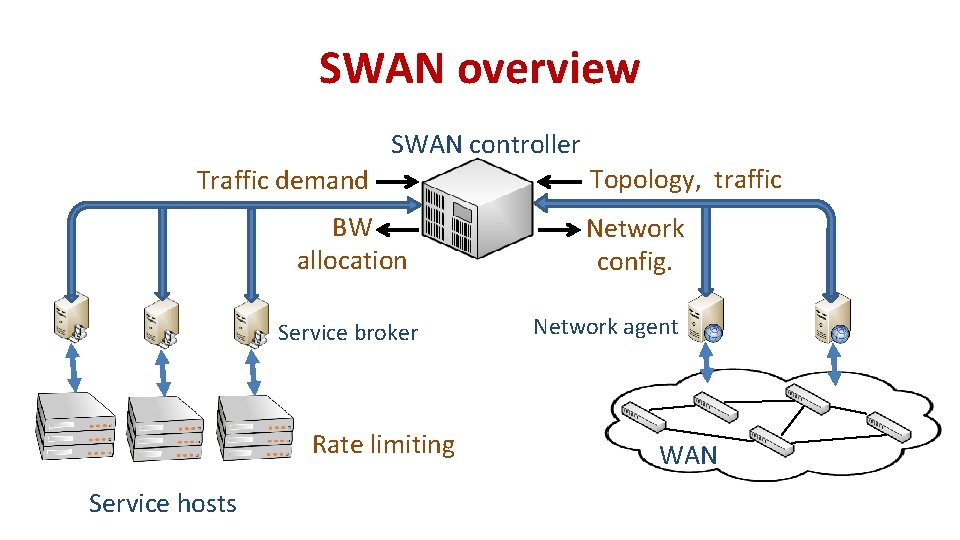
SWAN overview SWAN controller Traffic demand BW allocation Service broker Rate limiting Service hosts Topology, traffic Network config. Network agent WAN

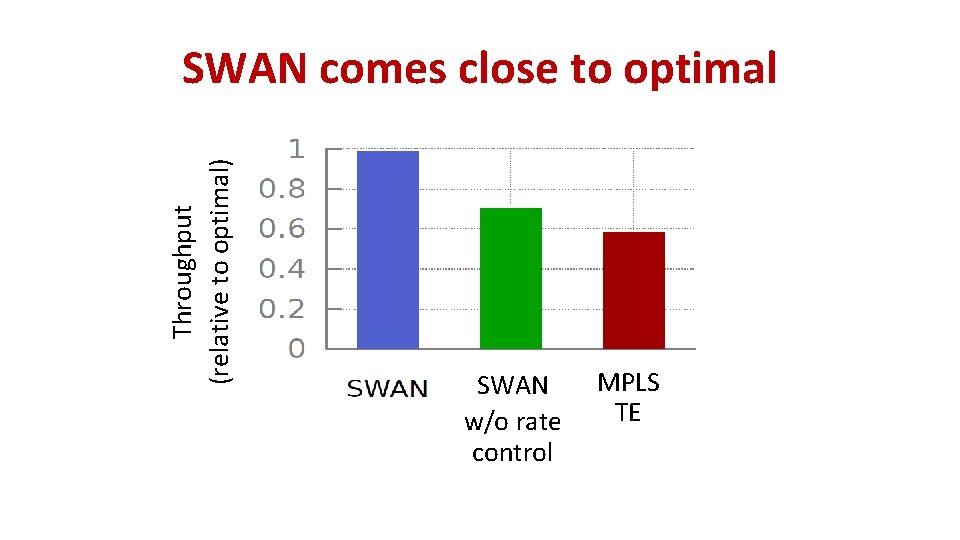
Throughput (relative to optimal) SWAN comes close to optimal SWAN w/o rate control MPLS TE

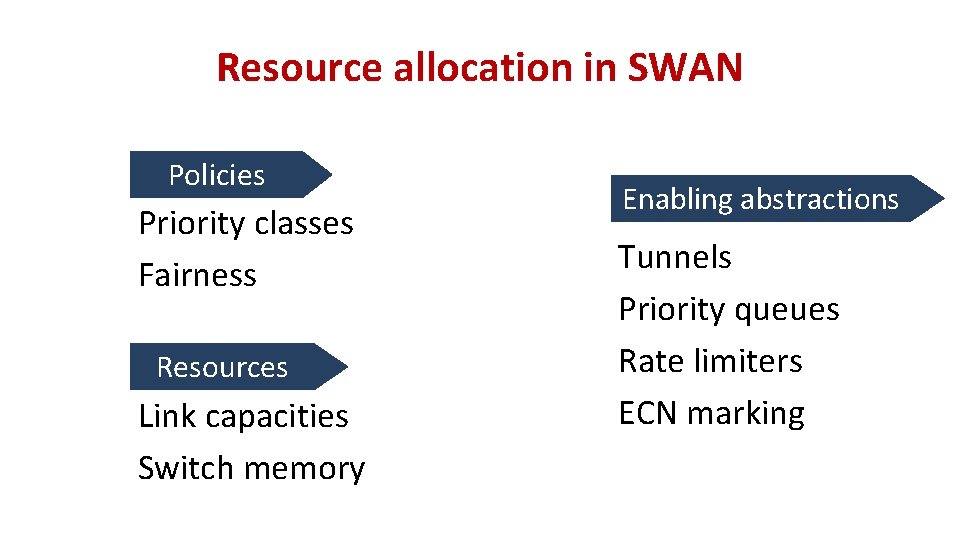
Resource allocation in SWAN Policies Priority classes Fairness Resources Link capacities Switch memory Enabling abstractions Tunnels Priority queues Rate limiters ECN marking

Enabling abstractions for network programming Tunnels, priority queues, rate ? ? limiters Open. Flow, BGP Network state databases Unmet needs Efficiency Policy-compliant forwarding Bootstrapped, healthy devices Network

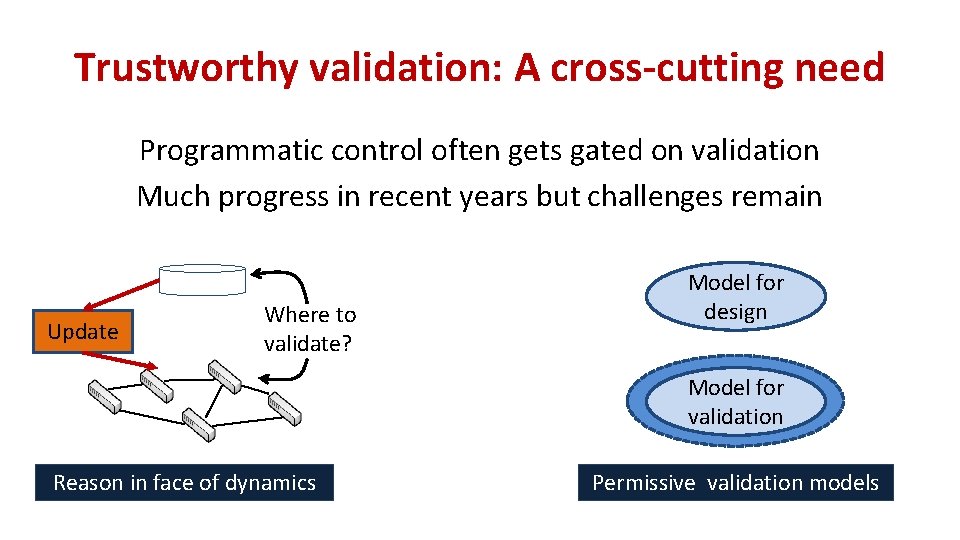
Trustworthy validation: A cross-cutting need Programmatic control often gets gated on validation Much progress in recent years but challenges remain Update Where to validate? Model for design Model for validation Reason in face of dynamics Permissive validation models

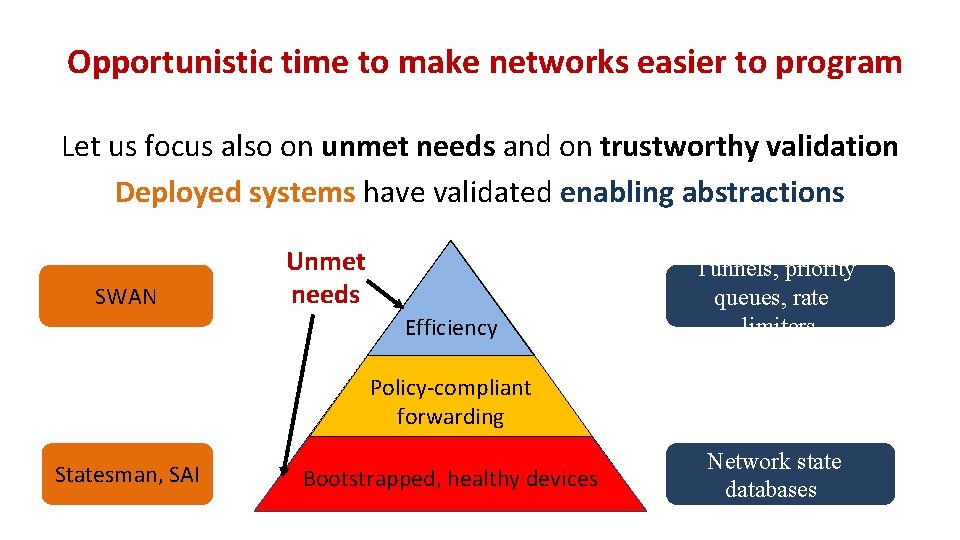
Opportunistic time to make networks easier to program Let us focus also on unmet needs and on trustworthy validation Deployed systems have validated enabling abstractions SWAN Unmet needs Efficiency Tunnels, priority queues, rate limiters Policy-compliant forwarding Statesman, SAI Bootstrapped, healthy devices Network state databases
 Unmet financial need
Unmet financial need Unmet needs in severe asthma
Unmet needs in severe asthma Maslows behovstrappa wifi
Maslows behovstrappa wifi Maslow's theory maintains that________.
Maslow's theory maintains that________. Maslows behovspyramide eksempler
Maslows behovspyramide eksempler Sociodemografiske variable
Sociodemografiske variable 14 behov virginia henderson
14 behov virginia henderson Idealsjälvet
Idealsjälvet þarfapýramídi maslows
þarfapýramídi maslows Maslows behovspyramide
Maslows behovspyramide Hierarchy of computer languages
Hierarchy of computer languages Hierarchy in a pseudo code
Hierarchy in a pseudo code Hierarchy chart programming
Hierarchy chart programming Perbedaan linear programming dan integer programming
Perbedaan linear programming dan integer programming Greedy algorithm vs dynamic programming
Greedy algorithm vs dynamic programming What is system program
What is system program Linear vs integer programming
Linear vs integer programming Definisi integer
Definisi integer Tcp echo client
Tcp echo client File and record locking in network programming
File and record locking in network programming Stevens unix network programming
Stevens unix network programming Qradar network hierarchy best practices
Qradar network hierarchy best practices Hierarchy network
Hierarchy network Socketaddr_in
Socketaddr_in Android network programming
Android network programming Network model linear programming
Network model linear programming Raw socket in networking
Raw socket in networking Ipc vs tcp
Ipc vs tcp Nctu network programming github
Nctu network programming github