Maritime Force Protection Operations Analysis Methodology Development Analysis




![RISK ANALYSIS Comparative Risk [after Bhattracharya et al] 5 RISK ANALYSIS Comparative Risk [after Bhattracharya et al] 5](https://slidetodoc.com/presentation_image_h/1644bf53ab742656d5ce53b41fd3731c/image-5.jpg)









- Slides: 27

Maritime Force Protection Operations Analysis Methodology Development Analysis Techniques for Defeating Threats to Naval Assets International Maritime Protection Symposium 12 -14 December 2005 Presented by Dr Darren J. Sutton Navy Scientific Adviser Defence Science and Technology Organisation – Australia 1

Presentation Outline v Maritime Force Protection v Scope the Problem • • • Multiple views Risk Analysis Attribute Analysis Threat Analysis Functional Decomposition v Quantify The Problem • • Modelling Solution Options Evaluation Requirements Determination Examples • Solution Options - Weapons Performance • Requirement for defence against suicide light aircraft v Conclusion 2

TTCP MAR AG-5 • Small Boat Swarm Attack • Suicide Attack on Berthed or Anchored Ship Surface Craft Truck Bomb • Swimmer or SDV Attack on Berthed or Anchored Ship • Attack by Asymmetric Air Threats on Berthed or Anchored Ship 3

Introduction Maritime Force Protection {closely related to security of commercial ships, ports and harbour installations} • Maritime Force Protection To conserve the fighting potential of the force by countering the wider threat to all its elements from adversary, natural and human hazards, and fratricide. • Harbour Protection To protect critical waterfront and floating assets by providing area security (defence) of the harbour or port. • In-Harbour Force Protection To secure ships and naval assets while anchored or alongside in a port or harbour by offboard or onboard means. • Ship-Based Force Protection To protect naval vessels berthed, anchored or underway, close-toshore, at home or away with onboard means. 4
![RISK ANALYSIS Comparative Risk after Bhattracharya et al 5 RISK ANALYSIS Comparative Risk [after Bhattracharya et al] 5](https://slidetodoc.com/presentation_image_h/1644bf53ab742656d5ce53b41fd3731c/image-5.jpg)
RISK ANALYSIS Comparative Risk [after Bhattracharya et al] 5

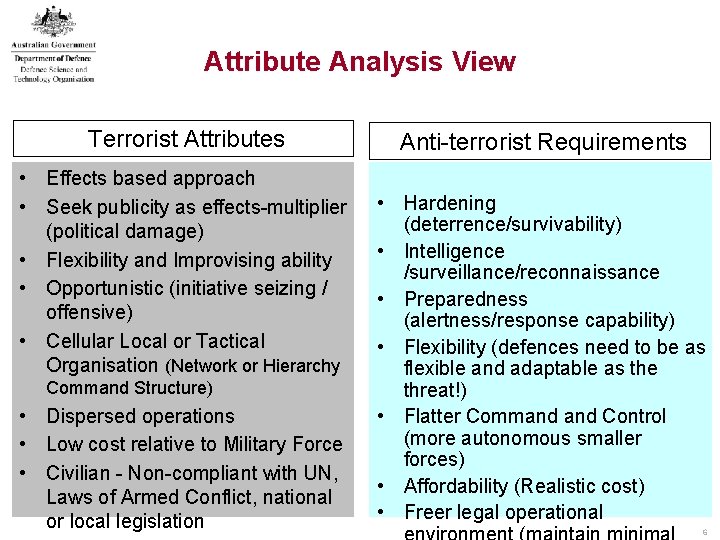
Attribute Analysis View Terrorist Attributes • Effects based approach • Seek publicity as effects-multiplier (political damage) • Flexibility and Improvising ability • Opportunistic (initiative seizing / offensive) • Cellular Local or Tactical Organisation (Network or Hierarchy Command Structure) • Dispersed operations • Low cost relative to Military Force • Civilian - Non-compliant with UN, Laws of Armed Conflict, national or local legislation Anti-terrorist Requirements • Hardening (deterrence/survivability) • Intelligence /surveillance/reconnaissance • Preparedness (alertness/response capability) • Flexibility (defences need to be as flexible and adaptable as the threat!) • Flatter Command Control (more autonomous smaller forces) • Affordability (Realistic cost) • Freer legal operational 6

Threat Analysis View Maritime Terrorist Threats may be characterised by • mission or intent • harassment or attention-seeking non-lethal attacks • lethal weapon attacks • suicidal explosive attacks • effector delivery method • Surface, sub-surface, air; Manned, unmanned • physical features of the threat platform • form, material, dimensions • speed, agility • stability • signatures. • cross platform features • manning strategy (recruitment, training, practicing, command control) • interoperability and tactical skill • strategy • radical unpredictability • opportunistic • employ quantity versus quality of forces 7

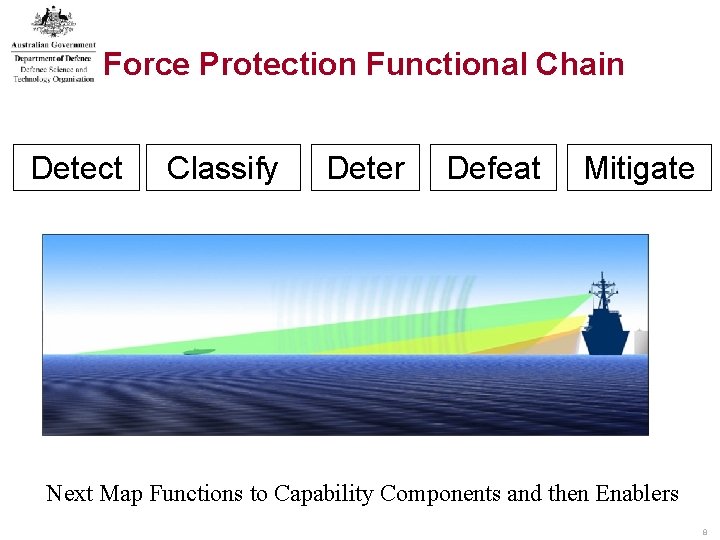
Force Protection Functional Chain Detect Classify Deter Defeat Mitigate Next Map Functions to Capability Components and then Enablers 8

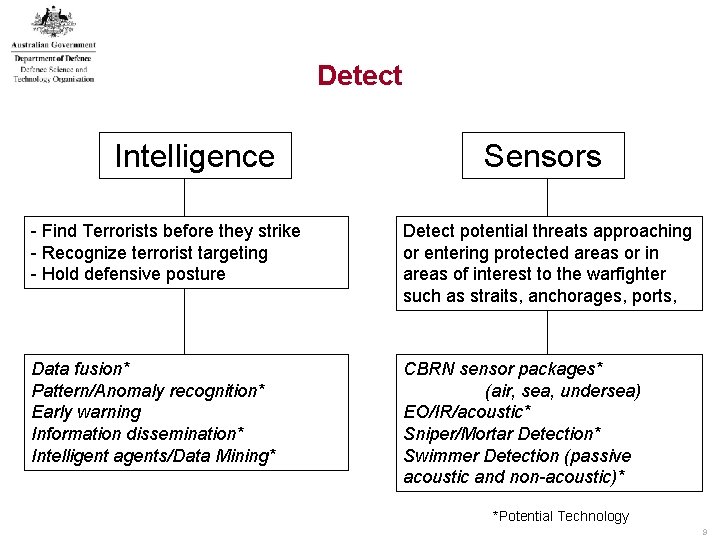
Detect Intelligence Sensors - Find Terrorists before they strike - Recognize terrorist targeting - Hold defensive posture Detect potential threats approaching or entering protected areas or in areas of interest to the warfighter such as straits, anchorages, ports, Data fusion* Pattern/Anomaly recognition* Early warning Information dissemination* Intelligent agents/Data Mining* CBRN sensor packages* (air, sea, undersea) EO/IR/acoustic* Sniper/Mortar Detection* Swimmer Detection (passive acoustic and non-acoustic)* *Potential Technology 9

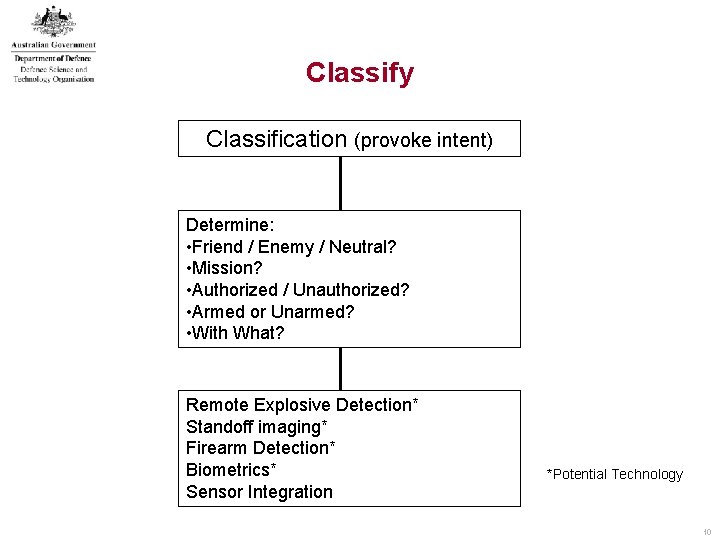
Classify Classification (provoke intent) Determine: • Friend / Enemy / Neutral? • Mission? • Authorized / Unauthorized? • Armed or Unarmed? • With What? Remote Explosive Detection* Standoff imaging* Firearm Detection* Biometrics* Sensor Integration *Potential Technology 10

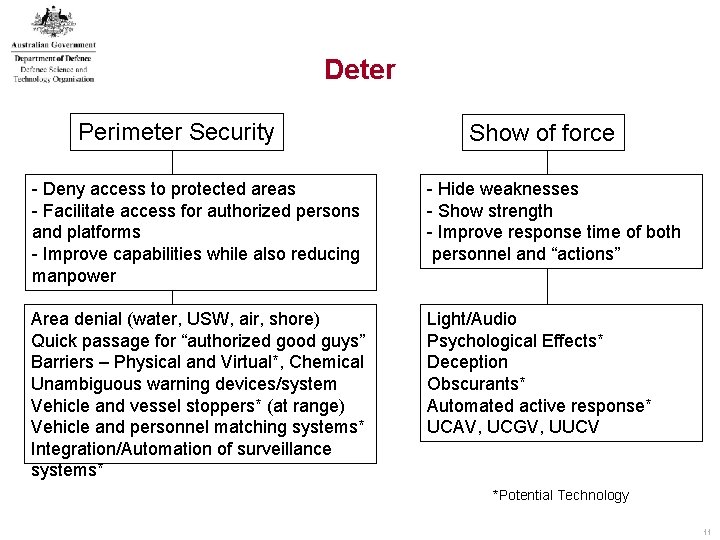
Deter Perimeter Security Show of force - Deny access to protected areas - Facilitate access for authorized persons and platforms - Improve capabilities while also reducing manpower - Hide weaknesses - Show strength - Improve response time of both personnel and “actions” Area denial (water, USW, air, shore) Quick passage for “authorized good guys” Barriers – Physical and Virtual*, Chemical Unambiguous warning devices/system Vehicle and vessel stoppers* (at range) Vehicle and personnel matching systems* Integration/Automation of surveillance systems* Light/Audio Psychological Effects* Deception Obscurants* Automated active response* UCAV, UCGV, UUCV *Potential Technology 11

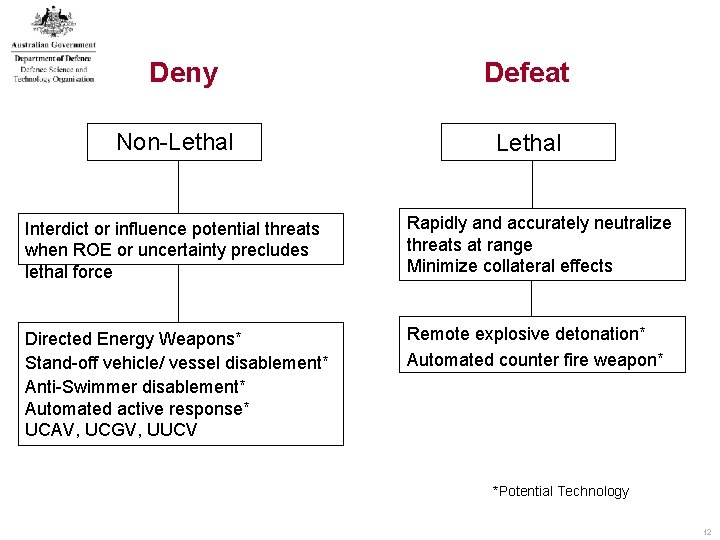
Deny Non-Lethal Defeat Lethal Interdict or influence potential threats when ROE or uncertainty precludes lethal force Rapidly and accurately neutralize threats at range Minimize collateral effects Directed Energy Weapons* Stand-off vehicle/ vessel disablement* Anti-Swimmer disablement* Automated active response* UCAV, UCGV, UUCV Remote explosive detonation* Automated counter fire weapon* *Potential Technology 12

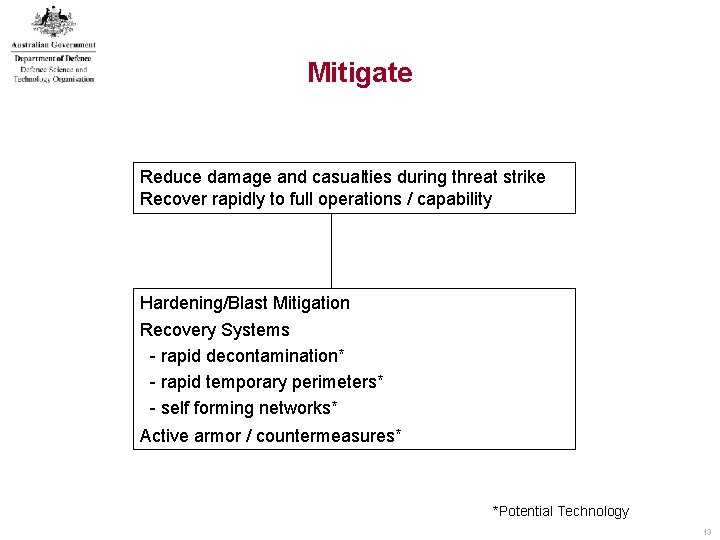
Mitigate Reduce damage and casualties during threat strike Recover rapidly to full operations / capability Hardening/Blast Mitigation Recovery Systems - rapid decontamination* - rapid temporary perimeters* - self forming networks* Active armor / countermeasures* *Potential Technology 13

Quantify the Problem • • • Variables Constraints Inclusions Exclusions Measures of Performance Derive mathematical relationship between Variables • Temporal • Spacial • Spectral • Develop Model • Exploratory (parametric) • Deterministic 14

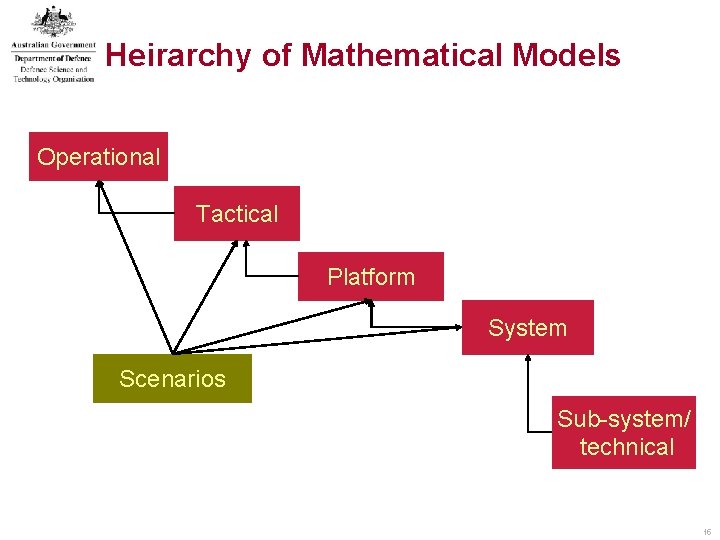
Heirarchy of Mathematical Models Operational Tactical Platform System Scenarios Sub-system/ technical 15

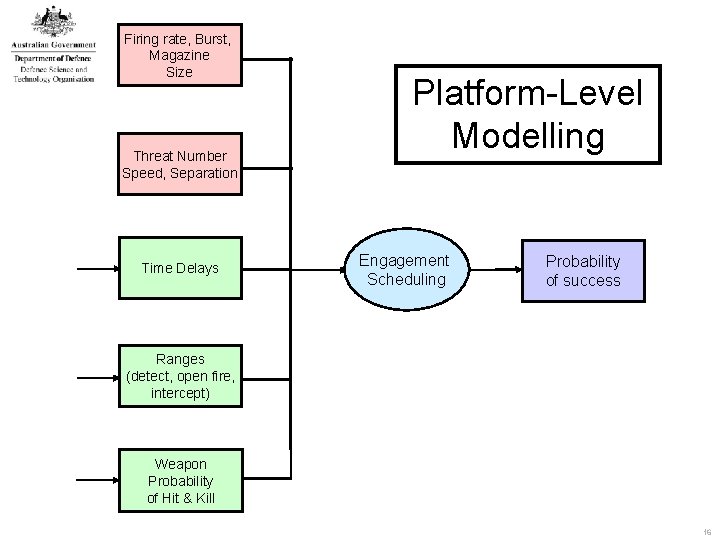
Firing rate, Burst, Magazine Size Threat Number Speed, Separation Time Delays Platform-Level Modelling Engagement Scheduling Probability of success Ranges (detect, open fire, intercept) Weapon Probability of Hit & Kill 16

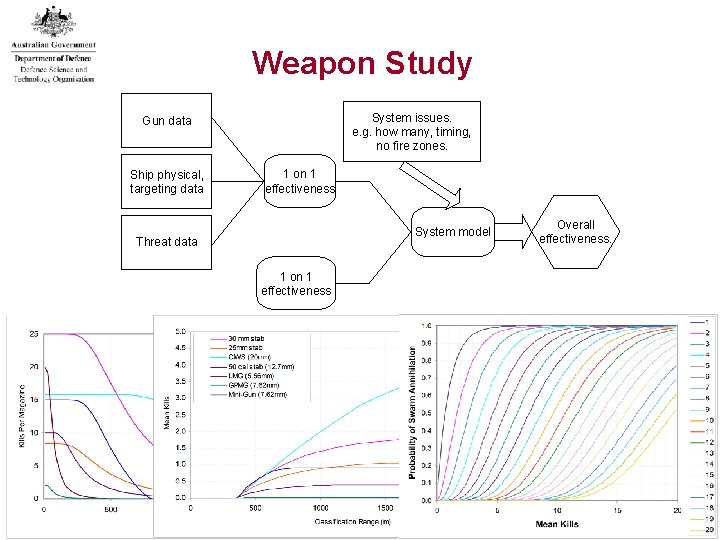
Weapon Performance Study • Aim – to compare general classes of gun based weapons against surface threats • Options • • • 30 mm stabilised 25 mm stabilised 20 mm Close in Weapon System 50 cal (stabilised or unstabilised) 7. 26 mm gun 5. 56 mm • Deconstruction • • Single Gun vs single target • Platform vs multiple targets • Swarm Annihilation Tools • Gun Operational Analysis Model (GOAT), • Ship weapons scheduling model, • Target kill rate model. 17

Weapon Study System issues. e. g. how many, timing, no fire zones. Gun data Ship physical, targeting data 1 on 1 effectiveness System model Threat data Overall effectiveness. 1 on 1 effectiveness 18

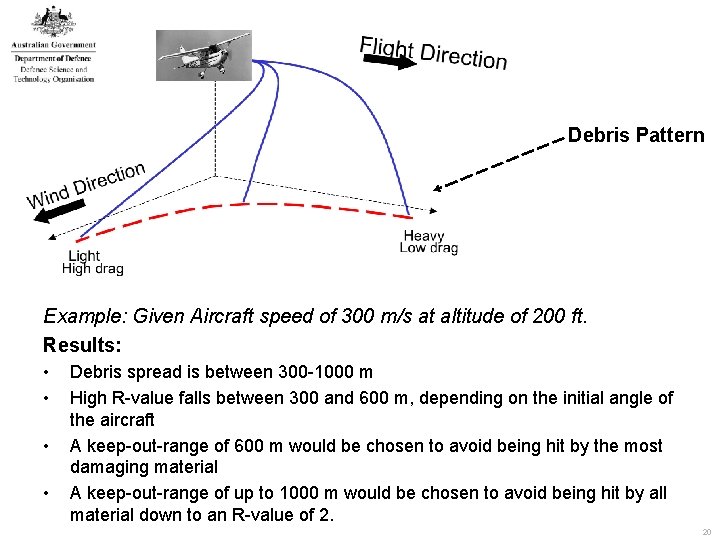
Terrorist Aircraft Attack Keep-Out-Range Requirement Study • Scenario: Vessel attacked by low slow aircraft • Problem: Survive the Attack • Engage the target • Avoid debris damage Questions: • What is Close-in Weapons System effectiveness ? • What distance must the aircraft be defeated so heavy debris does not hit the ship ? • What are the effects of wind on collateral damage ? 19

Debris Pattern Example: Given Aircraft speed of 300 m/s at altitude of 200 ft. Results: • • Debris spread is between 300 -1000 m High R-value falls between 300 and 600 m, depending on the initial angle of the aircraft A keep-out-range of 600 m would be chosen to avoid being hit by the most damaging material A keep-out-range of up to 1000 m would be chosen to avoid being hit by all material down to an R-value of 2. 20

Suicide Aircraft Attack In Port or at Anchor • Weapon Solution Options • Guns, Missiles • Variables • Effective Range • Lethality • Magazine capacity • Measure of Performance • Probability of hit • Conditional Probability of kill / hit • Salvo probability of kill 21

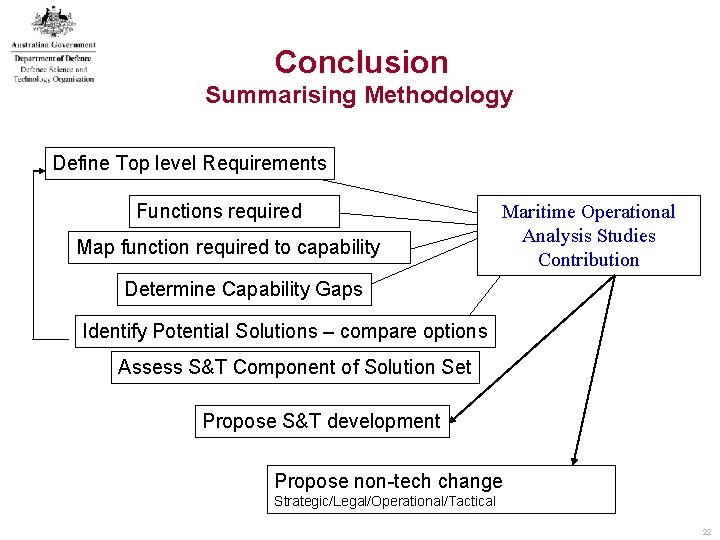
Conclusion Summarising Methodology Define Top level Requirements Functions required Map function required to capability Maritime Operational Analysis Studies Contribution Determine Capability Gaps Identify Potential Solutions – compare options Assess S&T Component of Solution Set Propose S&T development Propose non-tech change Strategic/Legal/Operational/Tactical 22

Finally Continuing Research Operations Analysis Methodology Development • Analysis Techniques for Maritime Force Protection • Applications to the Royal Australian Navy capability analysis for development and acquisition of ship and harbour force protection improvements. Eileen Moran eileen. moran@dsto. defence. gov. au Defence Science and Technology Organisation Maritime Operations Division Wharf 17, Pirrama Road Pyrmont NSW 2009 Australia. 23

SPARES 24

Functions - Deter, Deny, Defeat Graded Responses • • • Avoidance/deterrence Persistent Situational Awareness Interrogations (IFF) Warnings (illuminators, acoustic, pyrotechnics) Non-lethal effectors (floodlights, water hose, flash-bang, acoustic blast) • Lethal Weapons (guns, missiles, torpedos ) • Mitigation - Survivability, Recovery 25

Non - lethal Options • • • Acoustic (LRAD) Electrical (Stun Gun) Mechanical/Kinetic (Water cannon, nets) Electromagnetic (Active Denial system) Optical (Laser dazzle, spotlights) Bio/Chemical (Foam, Smoke) 26

Measures of Performance for the Defender • Prob uncovering plans to attack • Prob detection outside restricted zone • Prob determining hostile intent outside restricted zone • Prob warning-off/dissuading outside a keep-out-zone • Prob destroying/disabling by keep-out-zone • Or • Prob halting attack at outer layer boundary • Prob halting attack at inner layer boundary 27