March 2009 sgwhitespace090026 r 06 Security AdHoc Report






- Slides: 14

March 2009 sg-whitespace-09/0026 r 06 Security Ad-Hoc Report Draft Date: 2009 -03 -09 Authors: Submission Slide Alex 1 Reznik, Inter. Digital; Ranga Reddy, US

March 2009 sg-whitespace-09/0026 r 06 Abstract • This presentation summarizes the recommendations of the security ad-hoc group. • It consists of 2 parts: – Main section includes recommendation and threat analysis – Main section will be presented as part of the White Spaces ECSG tutorial – Background section includes additional information intended to illustrate, support and explain points made in the main section. Submission Slide Alex 2 Reznik, Inter. Digital; Ranga Reddy, US

March 2009 sg-whitespace-09/0026 r 06 Main Section Submission Alex Slide Reznik, 3 Inter. Digital; Ranga Reddy, US Army;

March 2009 sg-whitespace-09/0026 r 06 Security Goals and General Approach • Within the context of white spaces, security design needs to focus on two goals: – Primary goal: Protection of incumbents – Secondary goal: Protection of unlicensed users • The number of issues and technologies is larger than with protection of incumbents • Requires a comprehensive approach • Approach to Security – The ad-hoc recommends that an end-to-end security analysis be used in developing security aspects of white space technologies – Within 802 this means a focus on the following • The interfaces required for support of higher-level security technologies, such as data/application security, secure identity protocols, device security, etc. • Support of security technologies as discussed below Submission Slide Alex 4 Reznik, Inter. Digital; Ranga Reddy, US

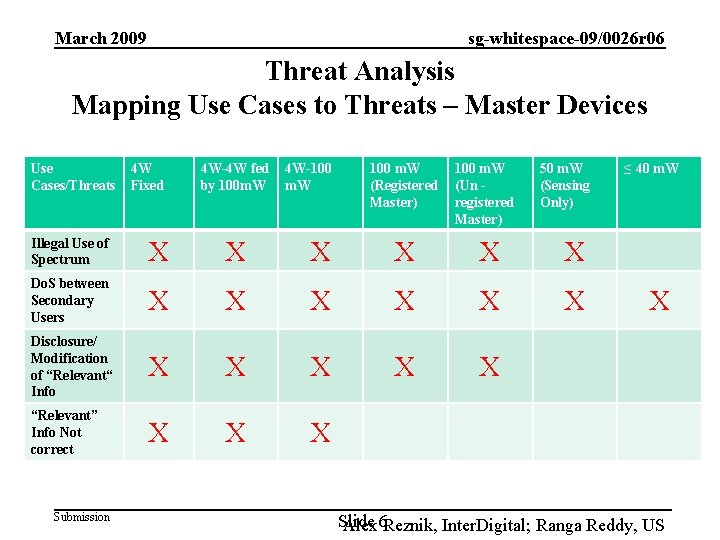
March 2009 sg-whitespace-09/0026 r 06 Threat Analysis: High Level Threats • Illegal Use of Spectrum – • Causing harmful interference to incumbents Denial of Service between Secondary Users – Threats to coexistence protocols between secondary devices • • Unauthorized disclosure or modification of “sensitive user/location” information – – • Disclosure of user location Modification of database info “Sensitive user/location” information is not correct – – • e. g. Stealing/hogging spectrum Registered incumbent or secondary user location Database info poisoning Sensitive user/location information may include – – – Submission User location information User identity Database registration/authentication parameters Sensor measurements reported to the database by user Interference report from the database Etc. Slide Alex 5 Reznik, Inter. Digital; Ranga Reddy, US

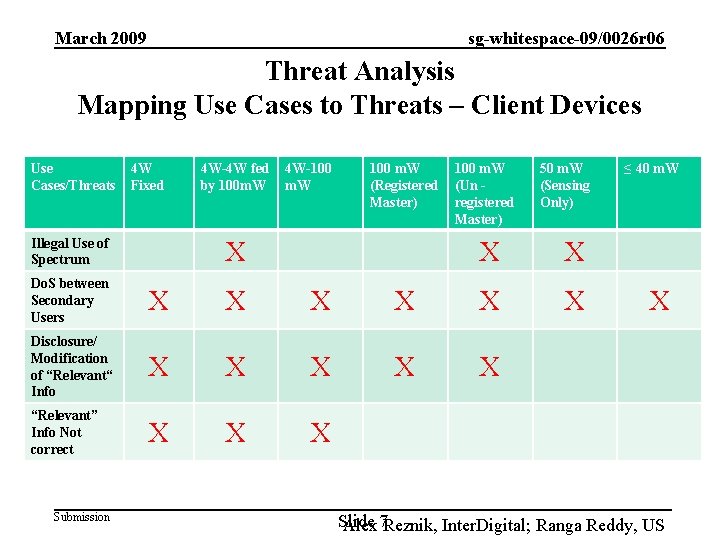
March 2009 sg-whitespace-09/0026 r 06 Threat Analysis Mapping Use Cases to Threats – Master Devices Use Cases/Threats 4 W Fixed 4 W-4 W fed by 100 m. W 4 W-100 m. W (Registered Master) 100 m. W (Un registered Master) 50 m. W (Sensing Only) Illegal Use of Spectrum X X X Do. S between Secondary Users X X X Disclosure/ Modification of “Relevant“ Info X X X “Relevant” Info Not correct X X X Submission ≤ 40 m. W X Slide Alex 6 Reznik, Inter. Digital; Ranga Reddy, US

March 2009 sg-whitespace-09/0026 r 06 Threat Analysis Mapping Use Cases to Threats – Client Devices Use Cases/Threats 4 W Fixed Illegal Use of Spectrum 4 W-4 W fed by 100 m. W 4 W-100 m. W (Registered Master) X 100 m. W (Un registered Master) X X X Do. S between Secondary Users X X X Disclosure/ Modification of “Relevant“ Info X X X “Relevant” Info Not correct X X X Submission 50 m. W (Sensing Only) ≤ 40 m. W X Slide Alex 7 Reznik, Inter. Digital; Ranga Reddy, US

March 2009 sg-whitespace-09/0026 r 06 Threat Analysis: Caveats • For the “ 50 m. W (Sensing Only)” and “≤ 40 m. W” the Disclosure/Modification of Relevant Info & Relevant Info Not Correct threats, are not applicable as those devices will not make use of the database. • The “≤ 40 m. W” use case is not affected by the Illegal Use of Spectrum threat due to low power. Devices can operate in adjacent channels. • Client devices cannot pose the Illegal Use of Spectrum threat in some use cases because the master chooses the spectrum, polls the database, and bears the responsibility for violation. The exception is when the master device is unregistered. – Given that registration for the lower power devices is not required. This also may be applicable for lower power networks operating in a mesh or peer topology, where every device would be considered a master. Submission Slide Alex 8 Reznik, Inter. Digital; Ranga Reddy, US

March 2009 sg-whitespace-09/0026 r 06 Ad-Hoc Recommendations • Further Work – – Present recommendation represents the best that could be accomplished with a limited time-span of this SG The contributors and other security ad-hoc participant recognize the need for a much more detailed analysis resulting in • • – – • 802 should plan to further pursue this topic either in a separate SG or as part of other whitespace activities Device security is an important requirement for protection of incumbents. Further study is needed to determine whether device security has an impact on 802. Low-Layer Security – Support of low-layer techniques by 802 is recommended to address the following • • • – • Incumbent classification / identification of malicious and negligent impersonators Protection of coexistence signaling It is recommended that the WGs coordinate their efforts in this area Sensor and location measurement security – • A detailed use-case based threat analysis Detailed recommendation for addressing identified threats Support by 802 of techniques that secure and attest sensing and location measurements is recommended Protection of database information – Submission Protection of database information on the device and its transmission over the air interface links is recommended and appropriate techniques should be supported by 802 Slide Alex 9 Reznik, Inter. Digital; Ranga Reddy, US

March 2009 sg-whitespace-09/0026 r 06 Background and Additional Information Submission Alex. Slide Reznik, 10 Inter. Digital; Ranga Reddy, US Army;

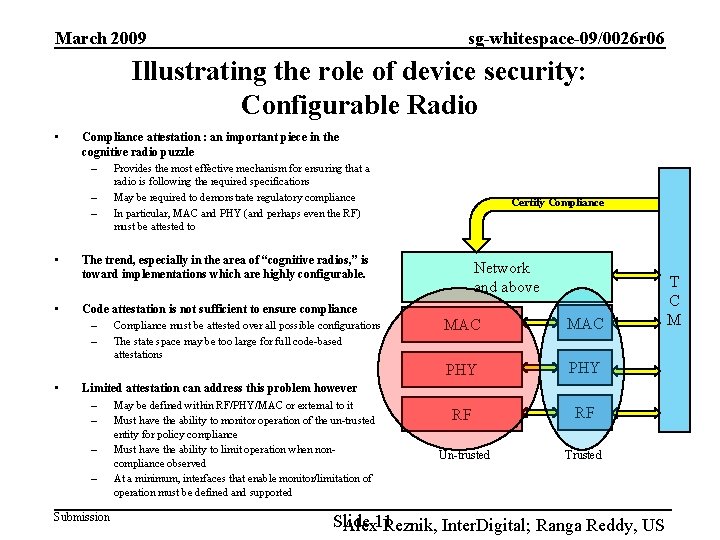
March 2009 sg-whitespace-09/0026 r 06 Illustrating the role of device security: Configurable Radio • Compliance attestation : an important piece in the cognitive radio puzzle – Provides the most effective mechanism for ensuring that a – – • • radio is following the required specifications May be required to demonstrate regulatory compliance In particular, MAC and PHY (and perhaps even the RF) must be attested to Certify Compliance The trend, especially in the area of “cognitive radios, ” is toward implementations which are highly configurable. Code attestation is not sufficient to ensure compliance – Compliance must be attested over all possible configurations – The state space may be too large for full code-based Network and above MAC PHY RF RF Un-trusted Trusted attestations • Limited attestation can address this problem however – May be defined within RF/PHY/MAC or external to it – Must have the ability to monitor operation of the un-trusted – – Submission entity for policy compliance Must have the ability to limit operation when noncompliance observed At a minimum, interfaces that enable monitor/limitation of operation must be defined and supported Slide Alex 11 Reznik, Inter. Digital; Ranga Reddy, US T C M

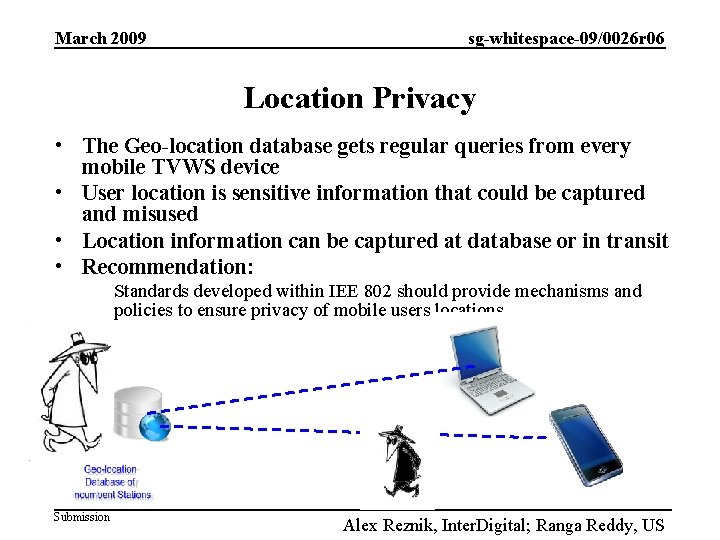
March 2009 sg-whitespace-09/0026 r 06 Location Privacy • The Geo-location database gets regular queries from every mobile TVWS device • User location is sensitive information that could be captured and misused • Location information can be captured at database or in transit • Recommendation: Standards developed within IEE 802 should provide mechanisms and policies to ensure privacy of mobile users locations. Submission Alex Reznik, Inter. Digital; Ranga Reddy, US

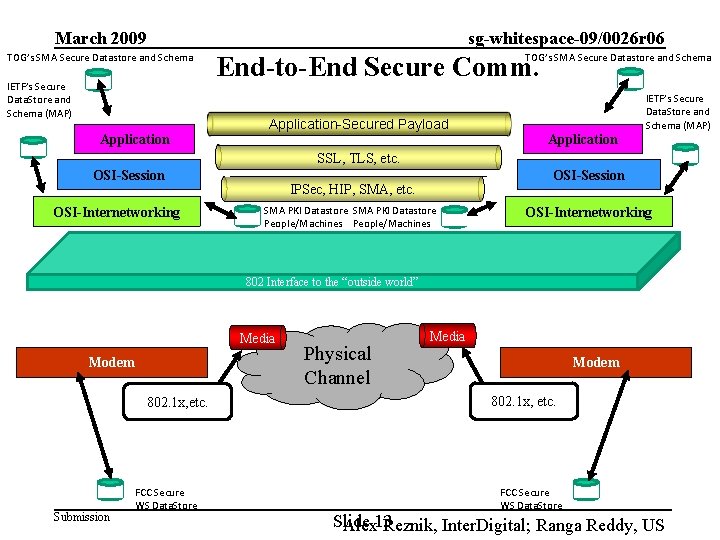
March 2009 TOG’s SMA Secure Datastore and Schema IETF’s Secure Data. Store and Schema (MAP) Application sg-whitespace-09/0026 r 06 TOG’s SMA Secure Datastore and Schema End-to-End Secure Comm. Application-Secured Payload IETF’s Secure Data. Store and Schema (MAP) Application SSL, TLS, etc. OSI-Session OSI-Internetworking OSI-Session IPSec, HIP, SMA, etc. SMA PKI Datastore People/Machines OSI-Internetworking 802 Interface to the “outside world” Media Modem 802. 1 x, etc. Submission FCC Secure WS Data. Store Physical Channel Media Modem 802. 1 x, etc. FCC Secure WS Data. Store Slide Alex 13 Reznik, Inter. Digital; Ranga Reddy, US

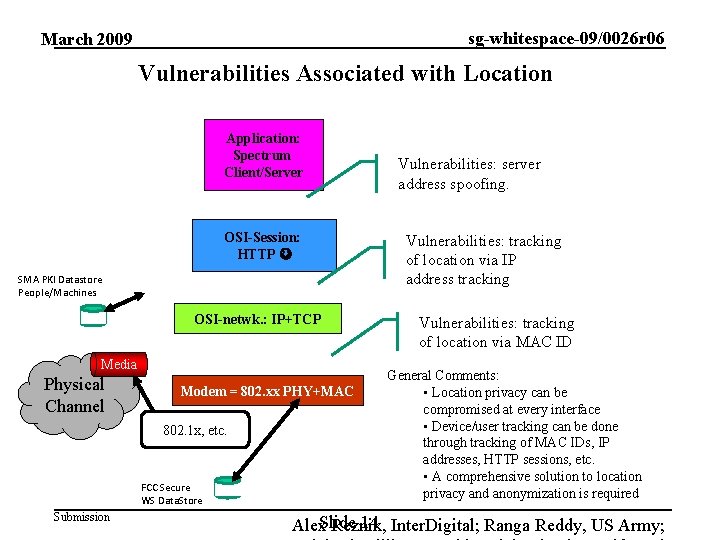
sg-whitespace-09/0026 r 06 March 2009 Vulnerabilities Associated with Location Application: Spectrum Client/Server OSI-Session: HTTP SMA PKI Datastore People/Machines OSI-netwk. : IP+TCP Media Physical Channel Modem = 802. xx PHY+MAC 802. 1 x, etc. FCC Secure WS Data. Store Submission Vulnerabilities: server address spoofing. Vulnerabilities: tracking of location via IP address tracking Vulnerabilities: tracking of location via MAC ID General Comments: • Location privacy can be compromised at every interface • Device/user tracking can be done through tracking of MAC IDs, IP addresses, HTTP sessions, etc. • A comprehensive solution to location privacy and anonymization is required 14 Inter. Digital; Ranga Reddy, US Army; Alex. Slide Reznik,
 Poland national anthem lyrics
Poland national anthem lyrics Ad hoc polymorphism c++
Ad hoc polymorphism c++ Adhoc.com
Adhoc.com Private secuirty
Private secuirty Yashpal committee report
Yashpal committee report Aeis report 2009
Aeis report 2009 Osi security architecture with neat diagram
Osi security architecture with neat diagram Security guide to network security fundamentals
Security guide to network security fundamentals Wireless security in cryptography and network security
Wireless security in cryptography and network security Visa international security model in information security
Visa international security model in information security Electronic mail security in network security
Electronic mail security in network security Explain about cnss security model
Explain about cnss security model Electronic commerce security
Electronic commerce security Software security touchpoints
Software security touchpoints Security guide to network security fundamentals
Security guide to network security fundamentals