March 2008 doc IEEE 802 11 080755 r





- Slides: 11

March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Review of 802. 11 n A-MPDU Do. S Issues – Progress and Status Authors: Submission 1 Luke Qian etc, Cisco Systems, Inc

March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Objective Provide a brief review of the current status and evolvement of A-MPDU Deny of Service (Do. S) Issues for the convenience of further discussion in TGn for an acceptable solution. We also propose an approach to going forward. Submission 2 Luke Qian etc, Cisco Systems, Inc

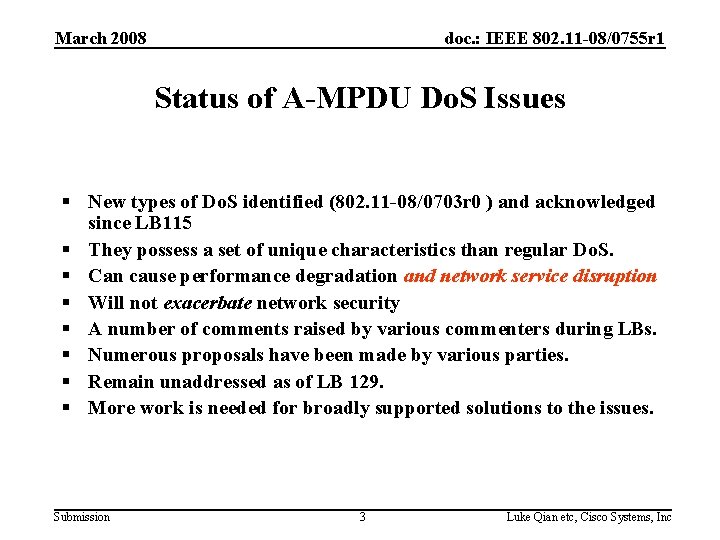
March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Status of A-MPDU Do. S Issues § New types of Do. S identified (802. 11 -08/0703 r 0 ) and acknowledged since LB 115 § They possess a set of unique characteristics than regular Do. S. § Can cause performance degradation and network service disruption § Will not exacerbate network security § A number of comments raised by various commenters during LBs. § Numerous proposals have been made by various parties. § Remain unaddressed as of LB 129. § More work is needed for broadly supported solutions to the issues. Submission 3 Luke Qian etc, Cisco Systems, Inc

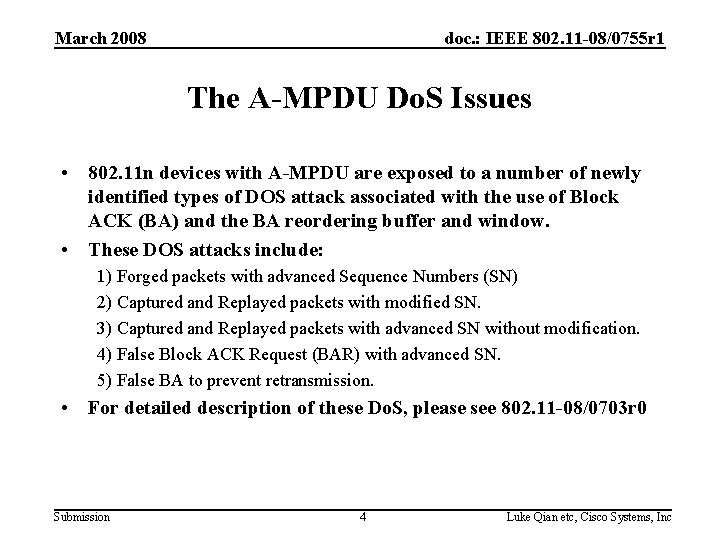
March 2008 doc. : IEEE 802. 11 -08/0755 r 1 The A-MPDU Do. S Issues • 802. 11 n devices with A-MPDU are exposed to a number of newly identified types of DOS attack associated with the use of Block ACK (BA) and the BA reordering buffer and window. • These DOS attacks include: 1) Forged packets with advanced Sequence Numbers (SN) 2) Captured and Replayed packets with modified SN. 3) Captured and Replayed packets with advanced SN without modification. 4) False Block ACK Request (BAR) with advanced SN. 5) False BA to prevent retransmission. • For detailed description of these Do. S, please see 802. 11 -08/0703 r 0 Submission 4 Luke Qian etc, Cisco Systems, Inc

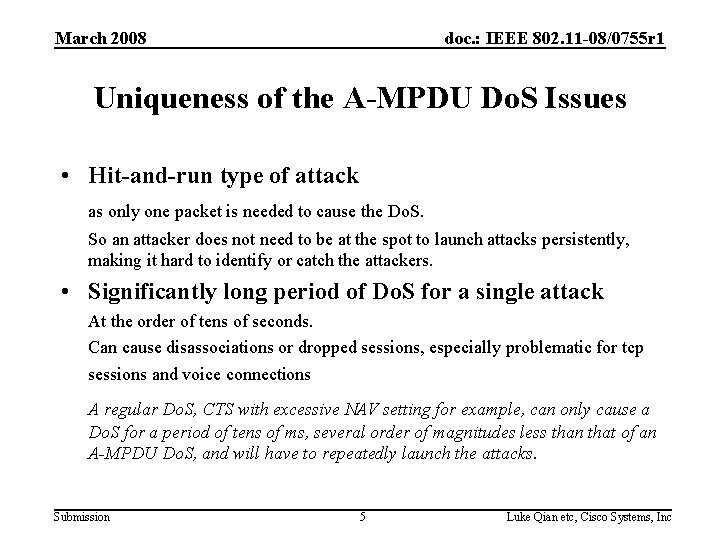
March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Uniqueness of the A-MPDU Do. S Issues • Hit-and-run type of attack as only one packet is needed to cause the Do. S. So an attacker does not need to be at the spot to launch attacks persistently, making it hard to identify or catch the attackers. • Significantly long period of Do. S for a single attack At the order of tens of seconds. Can cause disassociations or dropped sessions, especially problematic for tcp sessions and voice connections A regular Do. S, CTS with excessive NAV setting for example, can only cause a Do. S for a period of tens of ms, several order of magnitudes less than that of an A-MPDU Do. S, and will have to repeatedly launch the attacks. Submission 5 Luke Qian etc, Cisco Systems, Inc

March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Proposals for the Issues A number of proposals have been submitted by various parties to address the issues: – 802. 11 -07/2163 r 0 “A-MPDU Security Issues” – 802. 11 -08/0026 r 0 “BA Reordering for A-MPDU” – 802. 11 -08/0703 r 0 “Issues and Solutions to IEEE 802. 11 n AMPDU Denial of Service Attacks” – 802. 11 -08/0562 r 0 “A ‘detect and mitigate’ solution to the BA Do. S problems” – 802. 11 -08/0665 r 0 “Block Ack Security“ None of them reached 75% consensus. Submission 6 Luke Qian etc, Cisco Systems, Inc

March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Relating Comments and Resolutions in LB 115 (Jan 2008) • CID 5899 for example: There is a potential Do. S attack identified on the receiving side of the data plane • Proposed solution: “BA Reordering for A-MPDU" 802. 11 -08/0026 r 0, Jan, 2008 • Resolution MAC: 2008 -01 -11 10: 17: 55 Z Reject - as follows: It is accepted that a denial of service (Do. S) attack exists in which a forger generates Data MPDUs with an arbitrary SN, forcing a STA to consider validly sent MPDUs to be outside its BA window. The proposed change correctly addresses this attack. However, the same Do. S attack also exists as a replay attack. In this case the hacker captures a single encrypted Data MPDU addressed to the victim. It then replays this MPDU as much as it wants to, while changing its SN field. Because the SN field is not part of the AAD, this MPDU continues to pass through the integrity check logic, and will still cause the Block Ack receiver buffer to be flushed. Eventually the problematic MPDU reaches the replay logic, where it is discarded - but not before the damage to the Block. Ack buffer has been done. Given that the proposed solution does not fully address the attack on the block ack reordering buffer. èRequest a more complete solution. Submission 7 Luke Qian etc, Cisco Systems, Inc

March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Relating Comments and Resolutions in LB 124 (May 2008) • Comments: CID 6232, 6233, 6070, 6071 etc • Proposed solutions: Ø " Issues and Solutions to IEEE 802. 11 n A-MPDU Denial of Service Attacks“, by Cisco, 802. 11 -08/0703 r 0, merged with 11 -08/0665, 0537 Ø “A detect and mitigate solution to the BA Do. S problems“, by Intel, 11 -08/0562 r 0 Ø "Block Ack Security", 11 -08/0665, 11 -08/0537, by Broadcomm and Cisso, proposed as a merged solution and was rejected. • Resolution "GEN: 2008 -05 -15 17: 35: 58 Z Reject - While the described Do. S attack is a potential vulnerability, the additional complexity and cost of implementation of the jointly developed solutions in 08/0665 r 4 was considered to be unacceptable. " èRequest a less complex solution. Submission 8 Luke Qian etc, Cisco Systems, Inc

March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Relating Comments in LB 129 (June 2008) • Comments: CID 8075, 8076 Essentially the same comments carried over from the previous LBs. • Proposed approach to going forward: – the resolution in LB 115 requests a more complete solution than 802. 11 -08/0026 r 0 – the resolution in LB 124 requests a less complex solution than 802. 11 -08/0665 r 0 – The TG seems to suggest finding a solution in the middle ground of the above two in terms of complexity. – To going forward, we propose: • prioritize these Do. S attacks on their severity, • address only those more severer than regular Do. S • Limit the fix to reducing the damages by Do. S to regular Do. S attacks. èWill work within TGn for an acceptable solution. Submission 9 Luke Qian etc, Cisco Systems, Inc

March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Prioritizing the A-MPDU Do. S Attacks Sort the A-MPDU Do. S Types on their ease of launching: 1) Forged packets with advanced Sequence Numbers (SN) easy to launch, can be addressed, e. g. , by reversing the order of BA reordering and decryption. 4) False Block ACK Request (BAR) with advanced SN. easy to launch, can be addressed, e. g. , by protecting the BAR by wrapping it in an encrypted management frame, an 11 w mechanism. 2) Captured and Replayed packets with modified SN. more difficult, can be addressed by encrypting the SN, ( drop this one ? ) 3) Captured and Replayed packets with advanced SN without modification. more difficult, less likely to be successful, can be addressed by, e. g. , a replay check before BA reordering, ( drop this one? ) 5) False BA to prevent retransmission. less likely be successful, not unique since regular ACK can cause similar Do. S. , (drop this one? ) Submission 10 Luke Qian etc, Cisco Systems, Inc

March 2008 doc. : IEEE 802. 11 -08/0755 r 1 Recommendation Focus solutions on addressing only these two most severer Do. S: 1) Forged packets with advanced Sequence Numbers (SN). 4) False Block ACK Request (BAR) with advanced SN. with a simplified version of 802. 11 -08/0665 r 0 “Block Ack Security“ or adopt other proposals. Submission 11 Luke Qian etc, Cisco Systems, Inc