March 2003 doc IEEE 802 11 03202 r





- Slides: 25

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Keying for Fast Roaming Nancy Cam-Winget, Cisco Systems Keith Amann, Spectralink Bill Arbaugh, University of Maryland Greg Chesson, Atheros Dan Harkins, Trapeze Russ Housley, Vigil Security Fred Stivers, Texas Instruments Jesse Walker, Intel Corporation Submission 1 Cam-Winget et. al.

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Agenda • • Concepts Fast Roaming Key Hierarchy Keying Reassociations Fast Roaming PMK/PTK Usage Protocol Properties Back-end Protocol Considerations Open Issues Submission 2 Cam-Winget et. al.

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Concepts • • • AS-STA Session – MKID – Master Key Identifier, names a key PMK Caching PMK Timeout PMK – unique per AP Submission 3 Cam-Winget et. al.

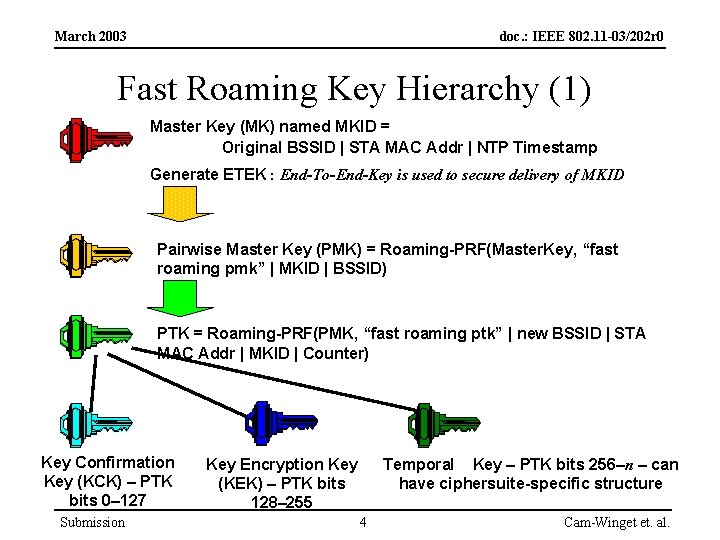
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Fast Roaming Key Hierarchy (1) Master Key (MK) named MKID = Original BSSID | STA MAC Addr | NTP Timestamp Generate ETEK : End-To-End-Key is used to secure delivery of MKID Pairwise Master Key (PMK) = Roaming-PRF(Master. Key, “fast roaming pmk” | MKID | BSSID) PTK = Roaming-PRF(PMK, “fast roaming ptk” | new BSSID | STA MAC Addr | MKID | Counter) Key Confirmation Key (KCK) – PTK bits 0– 127 Submission Temporal Key – PTK bits 256–n – can have ciphersuite-specific structure Key Encryption Key (KEK) – PTK bits 128– 255 4 Cam-Winget et. al.

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Fast Roaming Key Hierarchy (2) • No random nonces mixed into PTK – Rationale: Allow STA to pre-compute PTK – Consequence: PMK must be fresh across AS-STA sessions • MKID identifies keys – Rationale: optimizing performance requires identifying right key earlier in key confirmation handshake Submission 5 Cam-Winget et. al.

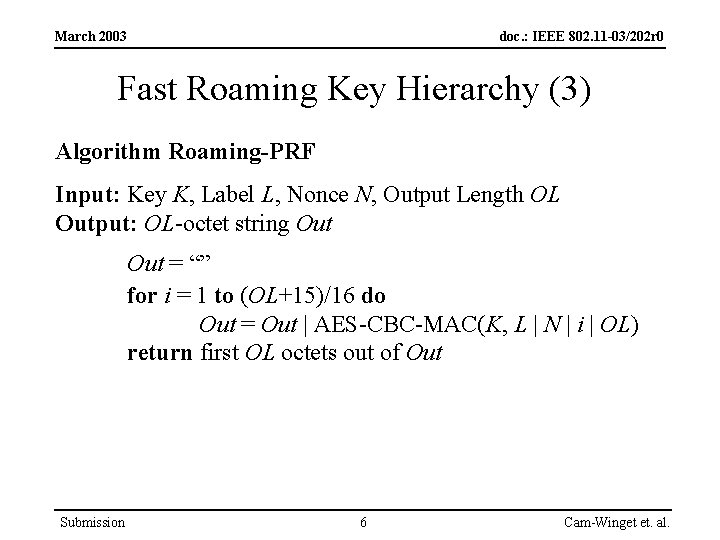
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Fast Roaming Key Hierarchy (3) Algorithm Roaming-PRF Input: Key K, Label L, Nonce N, Output Length OL Output: OL-octet string Out = “” for i = 1 to (OL+15)/16 do Out = Out | AES-CBC-MAC(K, L | N | i | OL) return first OL octets out of Out Submission 6 Cam-Winget et. al.

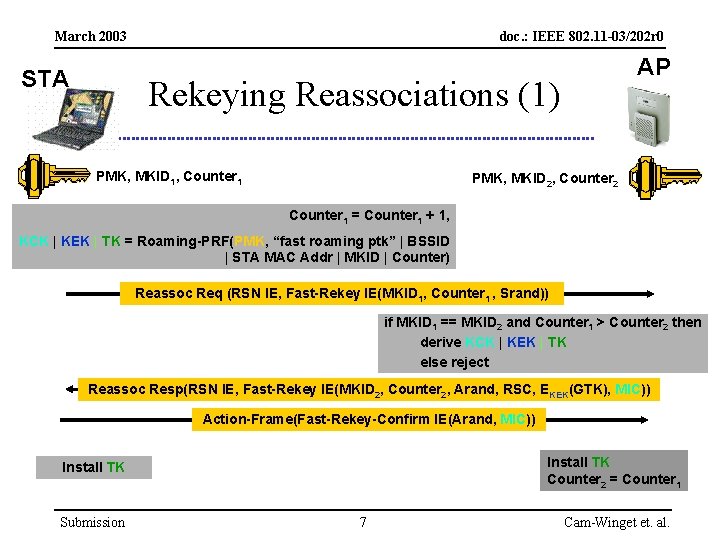
March 2003 STA doc. : IEEE 802. 11 -03/202 r 0 AP Rekeying Reassociations (1) PMK, MKID 1, Counter 1 PMK, MKID 2, Counter 2 Counter 1 = Counter 1 + 1, KCK | KEK | TK = Roaming-PRF(PMK, “fast roaming ptk” | BSSID | STA MAC Addr | MKID | Counter) Reassoc Req (RSN IE, Fast-Rekey IE(MKID 1, Counter 1 , Srand)) if MKID 1 == MKID 2 and Counter 1 > Counter 2 then derive KCK | KEK | TK else reject Reassoc Resp(RSN IE, Fast-Rekey IE(MKID 2, Counter 2, Arand, RSC, EKEK(GTK), MIC)) Action-Frame(Fast-Rekey-Confirm IE(Arand, MIC)) Install TK Counter 2 = Counter 1 Install TK Submission 7 Cam-Winget et. al.

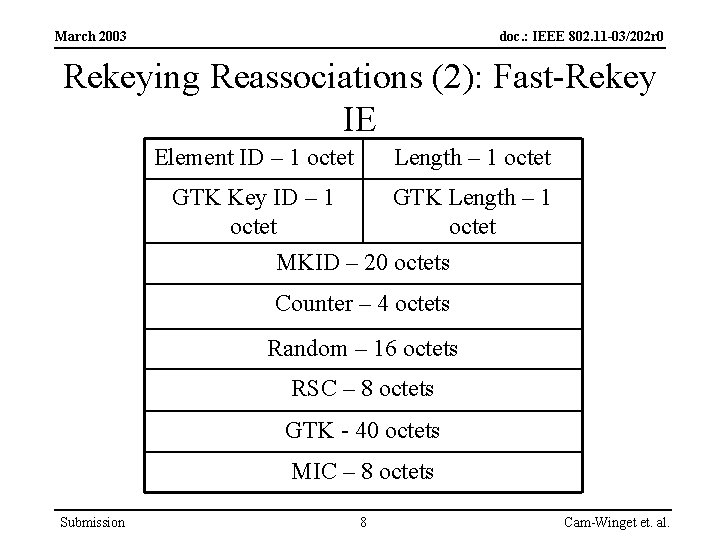
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Rekeying Reassociations (2): Fast-Rekey IE Element ID – 1 octet Length – 1 octet GTK Key ID – 1 octet GTK Length – 1 octet MKID – 20 octets Counter – 4 octets Random – 16 octets RSC – 8 octets GTK - 40 octets MIC – 8 octets Submission 8 Cam-Winget et. al.

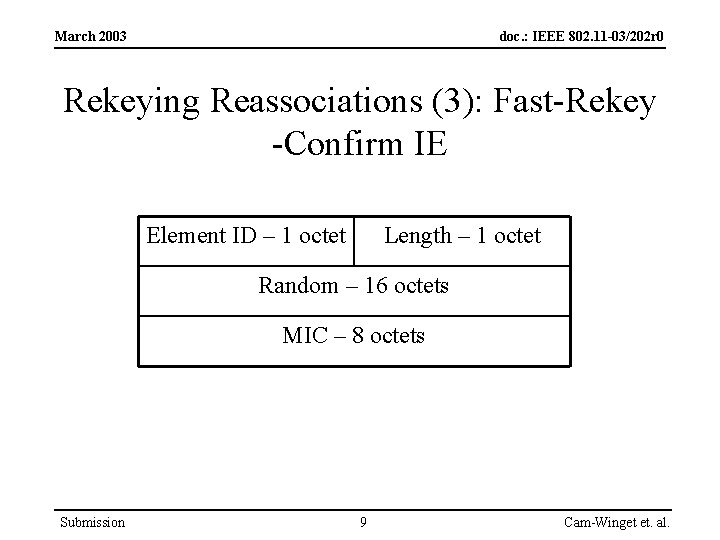
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Rekeying Reassociations (3): Fast-Rekey -Confirm IE Element ID – 1 octet Length – 1 octet Random – 16 octets MIC – 8 octets Submission 9 Cam-Winget et. al.

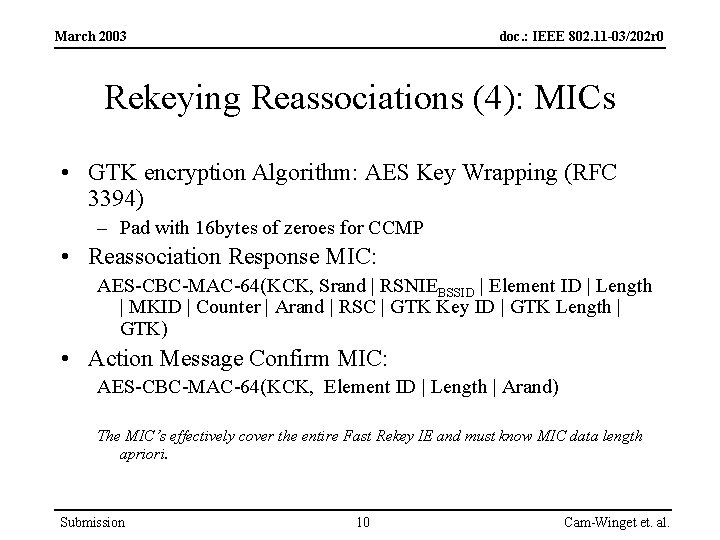
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Rekeying Reassociations (4): MICs • GTK encryption Algorithm: AES Key Wrapping (RFC 3394) – Pad with 16 bytes of zeroes for CCMP • Reassociation Response MIC: AES-CBC-MAC-64(KCK, Srand | RSNIEBSSID | Element ID | Length | MKID | Counter | Arand | RSC | GTK Key ID | GTK Length | GTK) • Action Message Confirm MIC: AES-CBC-MAC-64(KCK, Element ID | Length | Arand) The MIC’s effectively cover the entire Fast Rekey IE and must know MIC data length apriori. Submission 10 Cam-Winget et. al.

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Rekeying Reassociations (5) • AP proves it is live by MICing SRand in Reassociation Response • STA proves it is live by MICing Arand in Action Message • Counter value rules insure PTK is fresh if PMK is fresh – STA must maintain Counter over MK lifetime – AP must maintain Counter over PMK lifetime Submission 11 Cam-Winget et. al.

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Rekeying Reassociations (6) • AES-CBC-MAC requires Fast-Rekey IE, Fast. Rekey-Confirm IE have fixed lengths – Use only with TKIP and CCMP Submission 12 Cam-Winget et. al.

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Protocol Properties • Scheme works with – proactive keying (Arbaugh et al) – on-demand key refresh (Cam-Winget) • Scheme aids fast roaming by – Supporting PTK pre-computation – PMK caching at the AP and STA – Reducing roundtrips at reassociation from 7. 5 to 2. 5 • Scheme is optional Submission 13 Cam-Winget et. al.

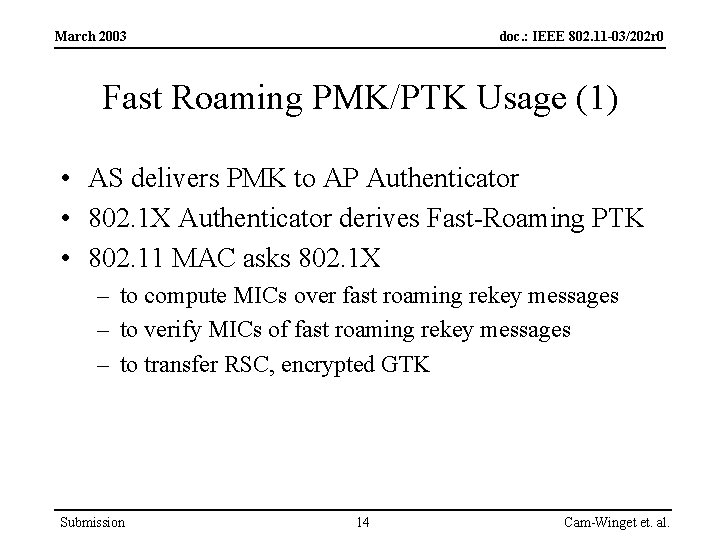
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Fast Roaming PMK/PTK Usage (1) • AS delivers PMK to AP Authenticator • 802. 1 X Authenticator derives Fast-Roaming PTK • 802. 11 MAC asks 802. 1 X – to compute MICs over fast roaming rekey messages – to verify MICs of fast roaming rekey messages – to transfer RSC, encrypted GTK Submission 14 Cam-Winget et. al.

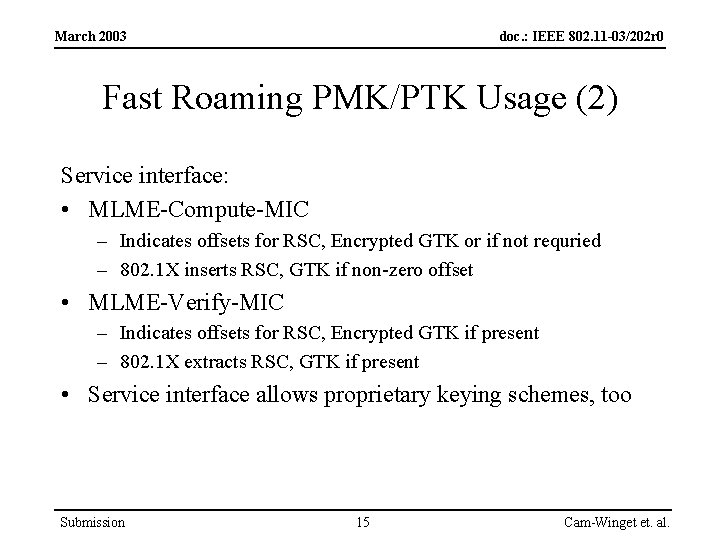
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Fast Roaming PMK/PTK Usage (2) Service interface: • MLME-Compute-MIC – Indicates offsets for RSC, Encrypted GTK or if not requried – 802. 1 X inserts RSC, GTK if non-zero offset • MLME-Verify-MIC – Indicates offsets for RSC, Encrypted GTK if present – 802. 1 X extracts RSC, GTK if present • Service interface allows proprietary keying schemes, too Submission 15 Cam-Winget et. al.

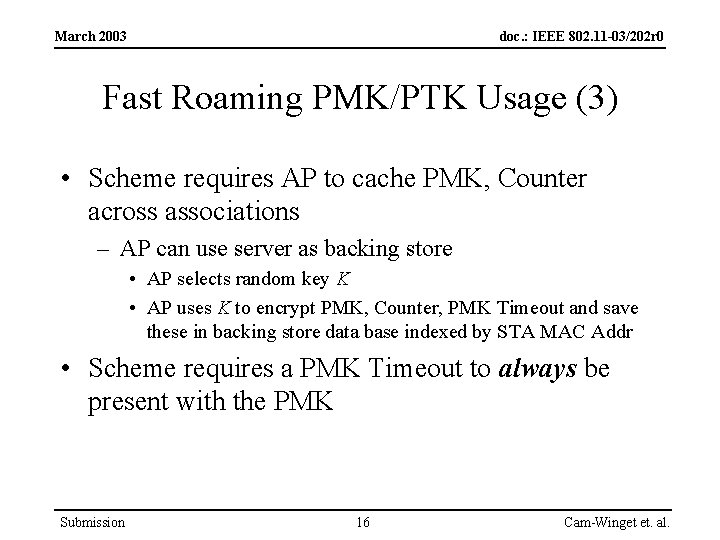
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Fast Roaming PMK/PTK Usage (3) • Scheme requires AP to cache PMK, Counter across associations – AP can use server as backing store • AP selects random key K • AP uses K to encrypt PMK, Counter, PMK Timeout and save these in backing store data base indexed by STA MAC Addr • Scheme requires a PMK Timeout to always be present with the PMK Submission 16 Cam-Winget et. al.

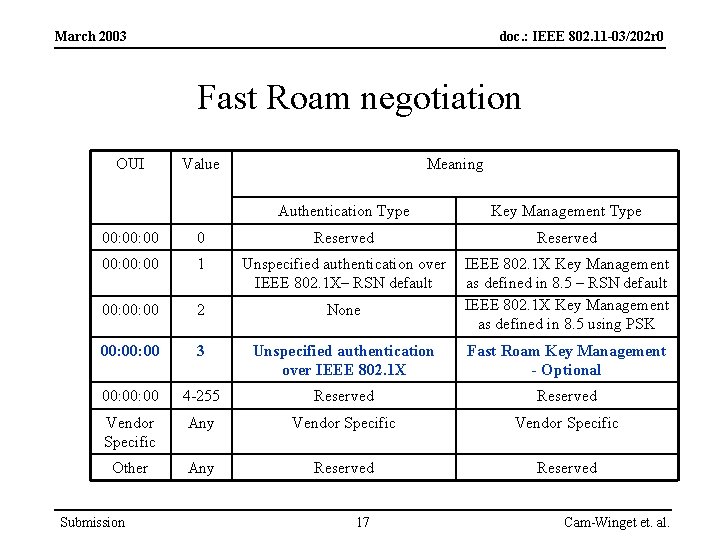
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Fast Roam negotiation OUI Value Meaning Authentication Type Key Management Type 00: 00 0 Reserved 00: 00 1 Unspecified authentication over IEEE 802. 1 X– RSN default 00: 00 2 None IEEE 802. 1 X Key Management as defined in 8. 5 – RSN default IEEE 802. 1 X Key Management as defined in 8. 5 using PSK 00: 00 3 Unspecified authentication over IEEE 802. 1 X Fast Roam Key Management - Optional 00: 00 4 -255 Reserved Vendor Specific Any Vendor Specific Other Any Reserved Submission 17 Cam-Winget et. al.

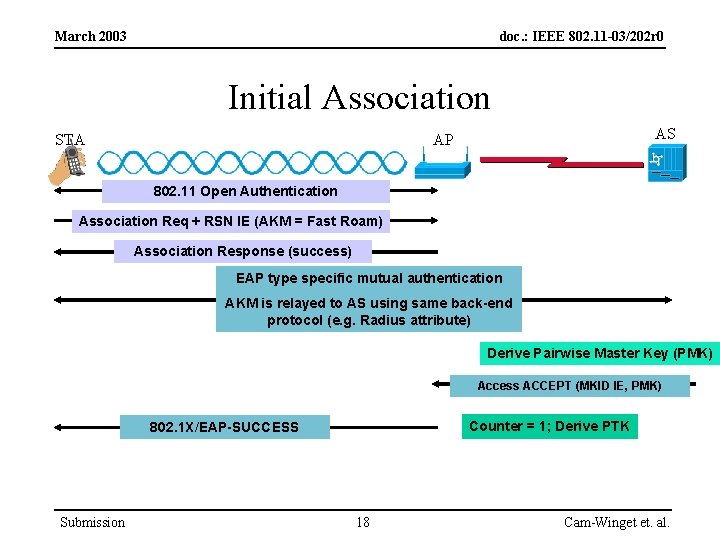
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Initial Association STA AS AP 802. 11 Open Authentication Association Req + RSN IE (AKM = Fast Roam) Association Response (success) EAP type specific mutual authentication AKM is relayed to AS using same back-end protocol (e. g. Radius attribute) Derive Pairwise Master Key (PMK) Access ACCEPT (MKID IE, PMK) Counter = 1; Derive PTK 802. 1 X/EAP-SUCCESS Submission 18 Cam-Winget et. al.

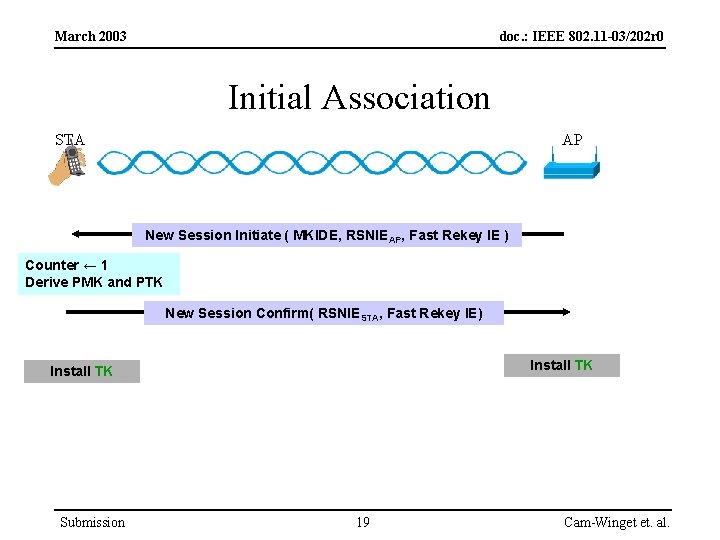
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Initial Association STA AP New Session Initiate ( MKIDE, RSNIEAP, Fast Rekey IE ) Counter ← 1 Derive PMK and PTK New Session Confirm( RSNIESTA, Fast Rekey IE) Install TK Submission 19 Cam-Winget et. al.

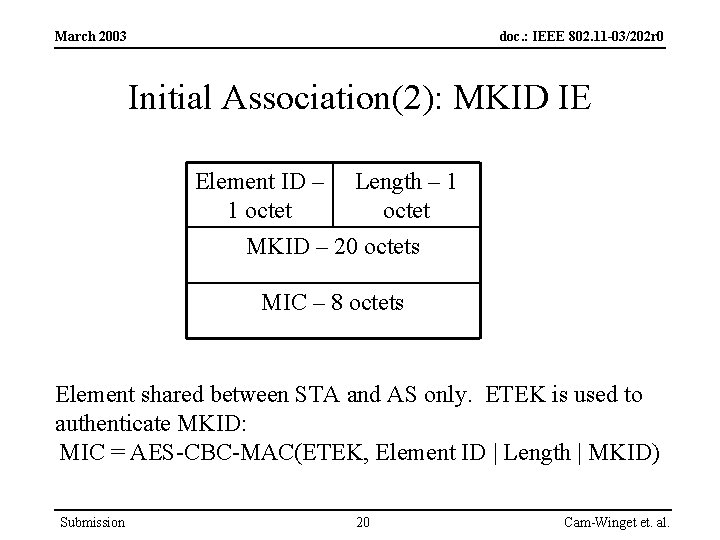
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Initial Association(2): MKID IE Element ID – 1 octet Length – 1 octet MKID – 20 octets MIC – 8 octets Element shared between STA and AS only. ETEK is used to authenticate MKID: MIC = AES-CBC-MAC(ETEK, Element ID | Length | MKID) Submission 20 Cam-Winget et. al.

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Initial Association (3) • New Session Initiate Fast Rekey IE : MIC = AES-CBC-MAC(KCK, RSNIEBSSID | Element ID | Length | GTK Key ID | GTK Length | MKID | Counter | ARand | RSC | GTK) • New Session Confirm Fast Rekey IE: MIC = AES-CBC-MAC(KCK, Element ID | Length | Arand) Submission 21 Cam-Winget et. al.

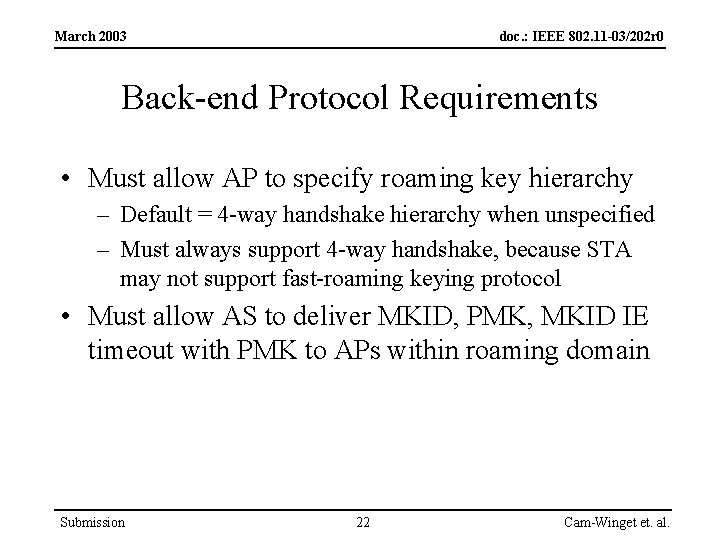
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Back-end Protocol Requirements • Must allow AP to specify roaming key hierarchy – Default = 4 -way handshake hierarchy when unspecified – Must always support 4 -way handshake, because STA may not support fast-roaming keying protocol • Must allow AS to deliver MKID, PMK, MKID IE timeout with PMK to APs within roaming domain Submission 22 Cam-Winget et. al.

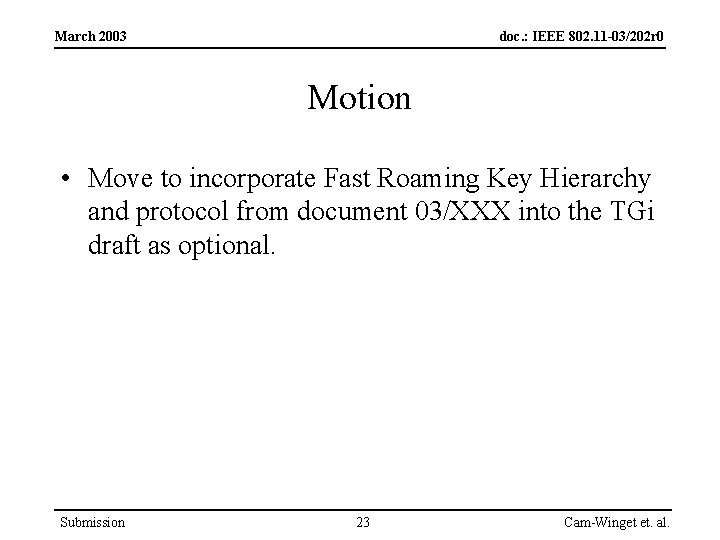
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Motion • Move to incorporate Fast Roaming Key Hierarchy and protocol from document 03/XXX into the TGi draft as optional. Submission 23 Cam-Winget et. al.

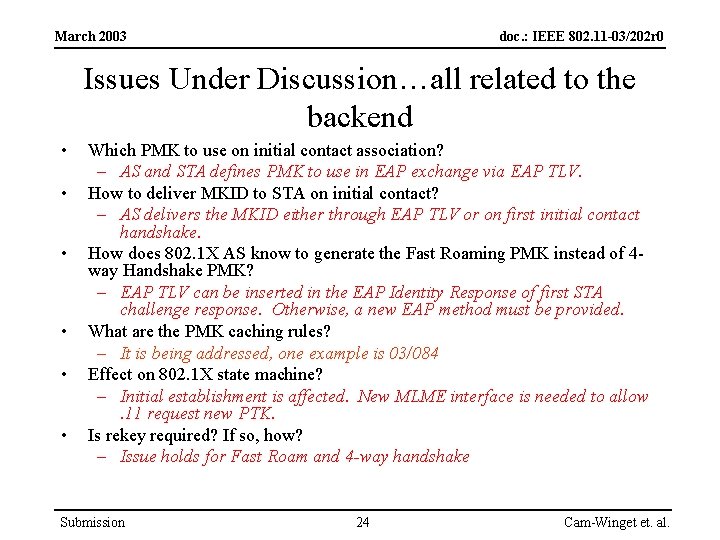
March 2003 doc. : IEEE 802. 11 -03/202 r 0 Issues Under Discussion…all related to the backend • • • Which PMK to use on initial contact association? – AS and STA defines PMK to use in EAP exchange via EAP TLV. How to deliver MKID to STA on initial contact? – AS delivers the MKID either through EAP TLV or on first initial contact handshake. How does 802. 1 X AS know to generate the Fast Roaming PMK instead of 4 way Handshake PMK? – EAP TLV can be inserted in the EAP Identity Response of first STA challenge response. Otherwise, a new EAP method must be provided. What are the PMK caching rules? – It is being addressed, one example is 03/084 Effect on 802. 1 X state machine? – Initial establishment is affected. New MLME interface is needed to allow. 11 request new PTK. Is rekey required? If so, how? – Issue holds for Fast Roam and 4 -way handshake Submission 24 Cam-Winget et. al.

March 2003 doc. : IEEE 802. 11 -03/202 r 0 Feedback? Submission 25 Cam-Winget et. al.