Managing Information Security Chapter 11 Information Systems Management

























- Slides: 33

Managing Information Security Chapter 11 Information Systems Management in Practice 8 th Edition © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -1

Chapter 11 l l Introduction Information Security l l l l The Threats Data Thefts: The Biggest Worry and Insider Threats Scope of Security Management An Array of Perils Security’s Five Pillars Technical Countermeasures Playing Cat and Mouse: Tools for Computer Security Management Countermeasures © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -2

Chapter 11 l Planning for Business Continuity l l Using Internal Resources Using External Resources Security as a Core Competency Conclusion © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -3

Information Security l l l Information security is more than just protecting hardware and software from being crashed… It’s about protecting the information resources that keep the company operating Goals are to ensure: l l Data integrity, availability and confidentiality Business continuity © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -4

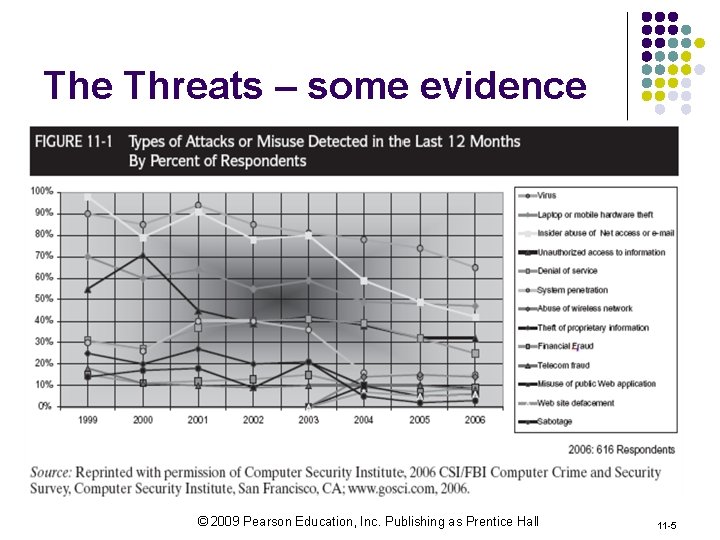
The Threats – some evidence © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -5

Data Thefts: The Biggest Worry and Insider Threats Here a few examples of possible criminal acts from an insider of a company: l l l A computer staff illegally accesses employees’ e mails to steal information that could be used for malicious intent An employee who is angry about the low bonus he receives brings down the entire company’s computer system by deleted sensitive data records A system administrator is not happy with his life and decides to change the code of legacy systems, creating bad data A marketing salesperson steals sensitive data and sells them to a competitor Threats are getting more and more sophisticated, cat- and-mouse game © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -6

Scope of Security Management l l l l Personnel security Application security Operating systems security Network security Middleware and Web services security Facility security Egress security should be enforced © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -7

Case Example Credit card fraud l l l One Bug in a Software Package Two Foreign Cybercriminals Simple Steps to Protect Credit Card © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -8

Single Steps to Protect Credit Cards l l l l Do not lend card Do not write PIN on card Do not carry too many cards at the same time Write down telephone number of credit banks and keep them safe but handy Immediately report lost or stolen card Check your credit card activities frequently (online) Set automated alert/notification © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -9

An Array of Perils l l l l Cracking the password Tricking someone Network sniffing Misusing administrative tools Playing middleman Denial of service Viruses or worms Spoofing © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -10

Some Common Attacks l Virus: A computer program that appears to perform a legitimate task, but is a hidden malware l l E. g. , wipe out a hard drive; send out an unauthorized email, etc. Sniffing: Interception and reading of electronic messages as they travel over the Internet l E. g. , copy passwords, or credit card information © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -11

Some Common Attacks l l Spoofing: Masquerade a Web site and redirect traffic to a fraudulent site Denial of Service: Attacks from coordinated computers that floods a site with so many requests until the site crashes l E. g. , thousands of email with large file attachments; simultaneous queries to overwhelm the database system © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -12

Other tricks… l l Con artists: calling to offer credit card account to obtain info about email, SSN, etc. Phishing or Fishing: Fraudulent email attempt to obtain sensitive information l E. g. , email notifying a bank account owner that s/he account had a security breach, and request the owner to log in a fraudulent website to “reset the password” © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -13

Security’s Five Pillars l Authentication: Verifying the authenticity of users l l Identification: Identifying users to grant them appropriate access l l E. g. , verify authenticity of digital signature; biometric authentication (finger printing) E. g. , password protection, spyware Privacy: Protecting information from being seen l E. g. , spyware installed without consent in a computer to collect information © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -14

Security Five Pillars l Integrity: Keeping information in its original form l l E. g. , Bots that alter document contents; Instant Messaging intercepted and altered Non-repudiation: Preventing parties from denying actions they have taken l E. g. , proof-of-origin to prove that a particular message (placing a stock order) is associated with a particular individual © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -15

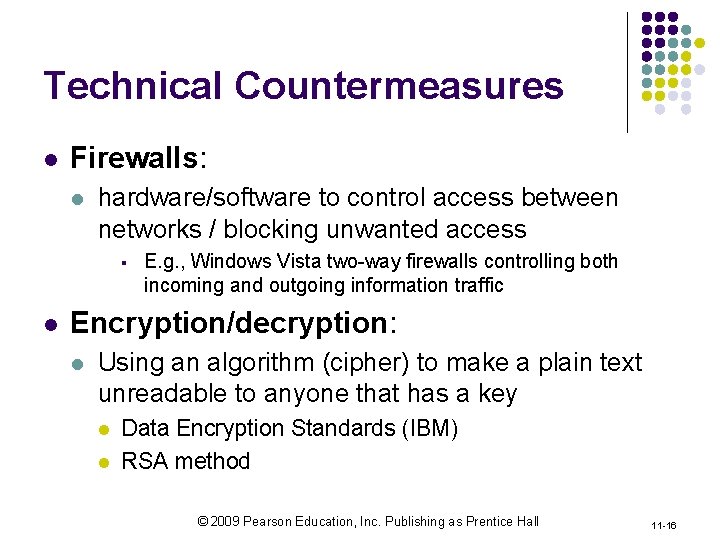
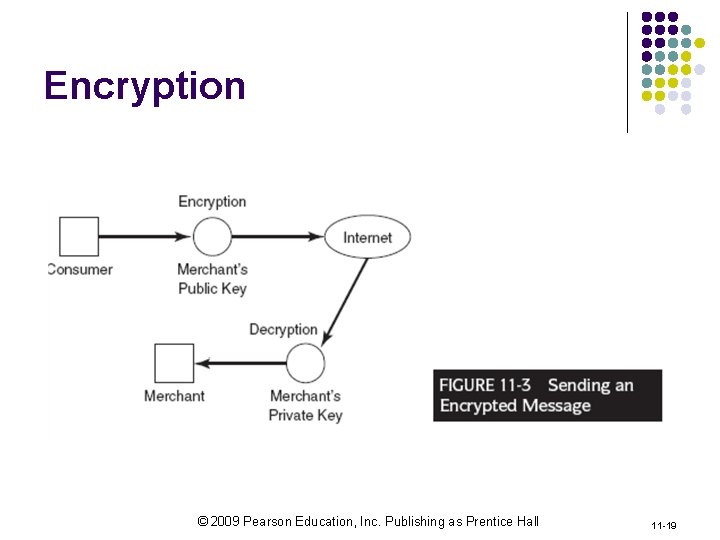
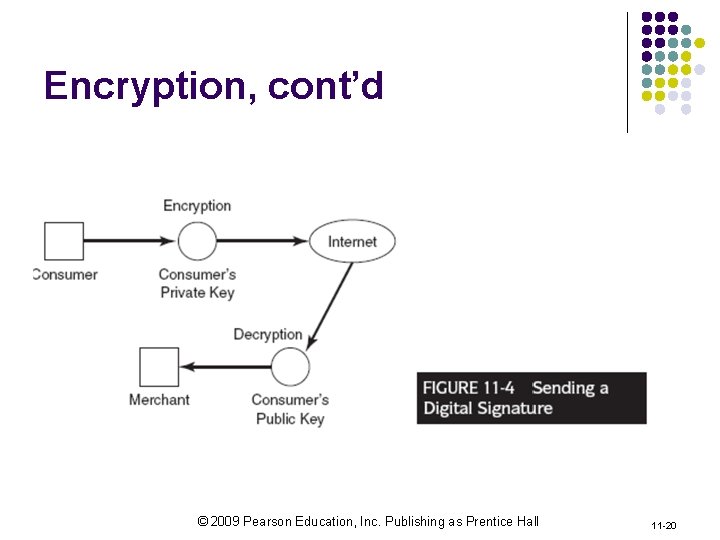
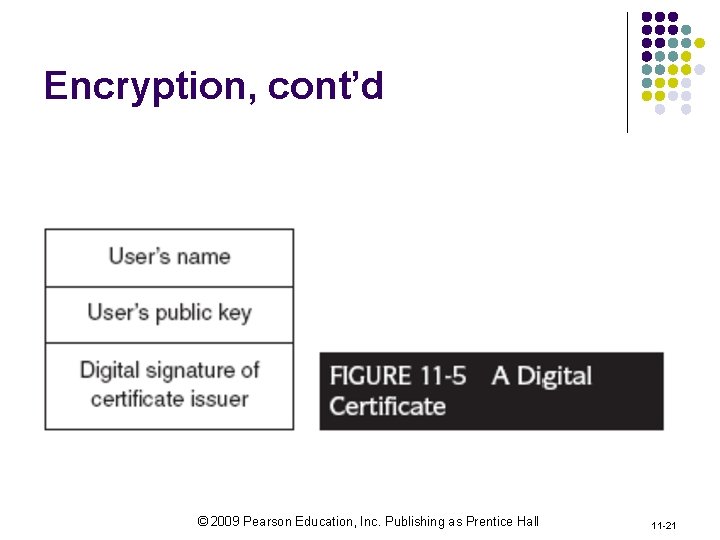
Technical Countermeasures l Firewalls: l hardware/software to control access between networks / blocking unwanted access § l E. g. , Windows Vista two-way firewalls controlling both incoming and outgoing information traffic Encryption/decryption: l Using an algorithm (cipher) to make a plain text unreadable to anyone that has a key l l Data Encryption Standards (IBM) RSA method © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -16

Technical Countermeasures l Virtual Private Networks (VPNs) l l Allow strong protection for data communications Cheaper than private networks, but do not provide 100% end-to-end security © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -17

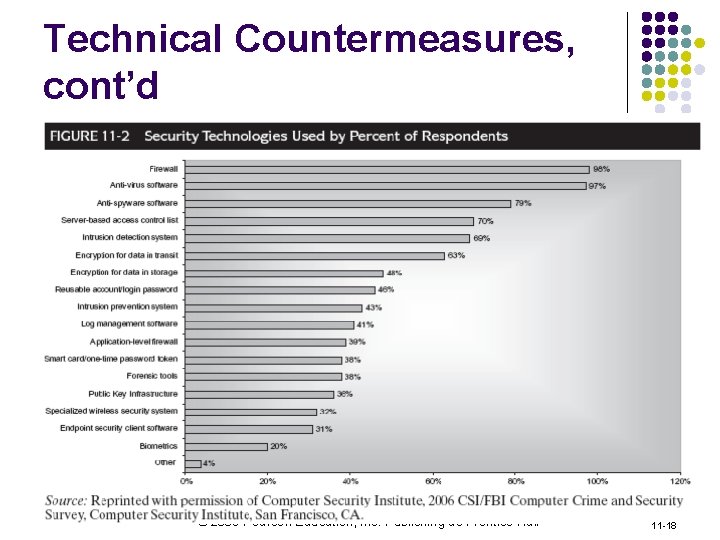
Technical Countermeasures, cont’d © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -18

Encryption © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -19

Encryption, cont’d © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -20

Encryption, cont’d © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -21

VPN VPNs can be used in three ways: l l l Remote access VPNs Remote office VPNs Extranet VPNs © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -22

Playing Cat and Mouse: Tools for Computer Security l Hardware tools l l Include locks, security cables, secured buildings preventing signal (wave) interceptions Dedicated database servers that are not connected to the Internet Backups systems Auxiliary tools: security cameras © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -23

Tools for Computer Security l Software Tools l l l Security modules built in Operating Systems to monitor activities Security scanners observing traffic activities for entire networks Special software for intrusion detection Packet sniffer searching “illegal” content, trojan viruses and worms Password crackers / security analyzers © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -24

Tools for Computer Security l Management Countermeasures l Computer auditing: make sure business programs do exactly what they are supposed to do § § l Computer monitoring: § l E. g. , alter algorithms in banking/accounting applications Sarbanes-Oxley Acts raises the threat of info security – more information to be generated Audit logs; search for security loopholes Economic evaluation of security measures § § Conduct Cost-Benefit analyses, ROI of countermeasures Determine what would be the most cost-effective level of security © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -25

Case Example An Internet Service Company l Planning and Building for Security l l l Monitoring l l l System architecture for security Information policy (e. g. , email, FTP policy) Logs of bugs, attacks, security breaches Simulation/ drills Education: The Key to Improving security (security enforcement and awareness) © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -26

A Concept for Business Continuity l l l Alternate workspace for people with working computers and communications Backup IT sites (business programs and data) Backup mobile devices with corporate information Up-to-date evacuation plans and drills Disaster recovery support (emergency procedures, etc. ) © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -27

Planning for Business Continuity l Companies have two options for disaster recovery l l Using Internal Resources l Multiple data centers l Distributed processing l Backup telecommunications facilities l LANs Using External Resources l Integrated disaster recovery services l Specialized disaster recovery services l Online and off-line data storage facilities © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -28

Case Example UT Austin responds to data thefts l l l Unauthorized access to Business School computer system Executing Remediation Plan Improving Overall Information Security l l l Security audit (external) Countermeasures (internal) Cooperation with other agencies (cooperation) © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -29

Some Online Resources l l l Federal Trade Commission Social Security Fraud Online Identity Theft Resource Center Internet Crime Complaint Center Department of Justice © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -30

Security as a Core Competency l Steps for an information-centric strategy l l l Create and communicate an enterprise software security framework Knowledge management training Secure the information infrastructure Assure internal security policy and external regulator compliance Governance © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -31

Conclusion l As suggested by the National Institute of Standards and Technology (NIST), all businesses should put into place information strategies that: l l are aligned with and support business mission and objectives are consistent with applicable laws and regulations through adherence to policies and internal controls hold people accountable for the security effort they are responsible for. The only constant is change – new security problems require new solutions © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -32

All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. Printed in the United States of America. Copyright © 2009 Pearson Education, Inc. Publishing as Prentice Hall © 2009 Pearson Education, Inc. Publishing as Prentice Hall 11 -33