MANAGEMENT of INFORMATION SECURITY Second Edition Organization Introduction
















































- Slides: 58

MANAGEMENT of INFORMATION SECURITY Second Edition

Organization ¨ Introduction ¨ Staffing the Security Function ¨ Qualifications and Requirements for the Security Profession ¨ Information Security Positions ¨ Information Security Professional Credentials ¨ Employment Policies and practices ¨ Conclusions Management of Information Security, 2 nd ed. - Chapter 10 Slide 2

Introduction ¨ Maintaining a secure environment requires that the Info. Sec department be carefully structured and staffed with appropriately credentialed personnel ¨ Proper procedures must be integrated into all human resources activities, including hiring, training, promotion, and termination practices Management of Information Security, 2 nd ed. - Chapter 10 Slide 3

Staffing the Security Function ¨ Selecting an effective mix of information security personnel requires that you consider a number of criteria ¨ Some of these criteria are within the control of the organization, and others are not ¨ Real economy is seldom in a state of equilibrium Management of Information Security, 2 nd ed. - Chapter 10 Slide 4

Staffing the Security Function (continued) ¨ In order to improve the Info. Sec staffing discipline : – The general management community of interest should learn more about the requirements and qualifications for both information security positions and relevant IT positions – Upper management should learn more about information security budgetary and personnel needs – The IT and general management communities of interest must grant the information security function (and CISO) an appropriate level of influence and prestige Management of Information Security, 2 nd ed. - Chapter 10 Slide 5

Staffing the Security Function (continued) ¨ In order to improve the Info. Sec staffing discipline (continued): – Develop an information security organizational staffing plan • E. g. NIST Information Technology Security Staffing Plan Management of Information Security, 2 nd ed. - Chapter 10 Slide 6

Information Technology Security Staffing Plan ¨ The staffing plan can include : – Security staff functions • Describe the key areas of influence, functions in each area, required time to be spent in each area and the amount of staff required to perform the function in each area • E. g. areas of influence: audit, physical security, disaster recovery & contingency planning, procurement, training, personnel, risk management, telecommunications, helpdesk Management of Information Security, 2 nd ed. - Chapter 10 Slide 7

Information Technology Security Staffing Plan (continued) ¨ The staffing plan can include (continued) : – Roles and responsibilities of the security community • Outline the position and security responsibilities of the individuals who make up the decision-making segment • Outline the basic staff roles and responsibilities • Define the authority and reporting relationships – Staffing budget • Security budget allocation for various functions Management of Information Security, 2 nd ed. - Chapter 10 Slide 8

Qualifications and Requirements ¨ When hiring information security professionals at all levels, organizations frequently look for individuals who have the following abilities: – Understand how organizations are structured and operated – Recognize that Info. Sec is a management task that cannot be handled with technology alone – Work well with people in general and communicate effectively using both strong written and verbal communication skills – Acknowledge the role of policy in guiding security efforts – Understand the essential role of information security education and training, which helps make users part of the solution, rather than part of the problem Management of Information Security, 2 nd ed. - Chapter 10 Slide 9

Qualifications and Requirements (continued) ¨ When hiring information security professionals at all levels, organizations frequently look for individuals who have the following abilities (continued): – Perceive threats facing an organization, understand how these threats can become transformed into attacks, and safeguard the organization from information security attacks – Understand how technical controls can be applied to solve specific information security problems – Demonstrate familiarity with the mainstream information technologies Management of Information Security, 2 nd ed. - Chapter 10 Slide 10

Qualifications and Requirements (continued) ¨ When hiring information security professionals at all levels, organizations frequently look for individuals who have the following abilities (continued): – Understand IT and Info. Sec terminology and concepts Management of Information Security, 2 nd ed. - Chapter 10 Slide 11

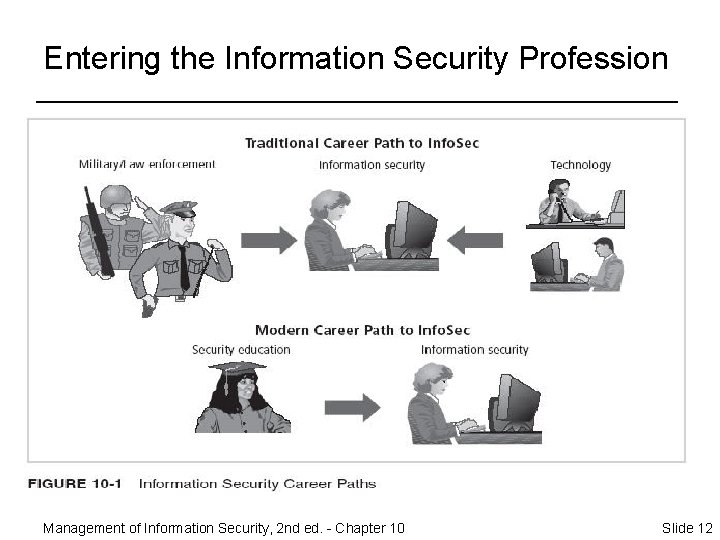
Entering the Information Security Profession Management of Information Security, 2 nd ed. - Chapter 10 Slide 12

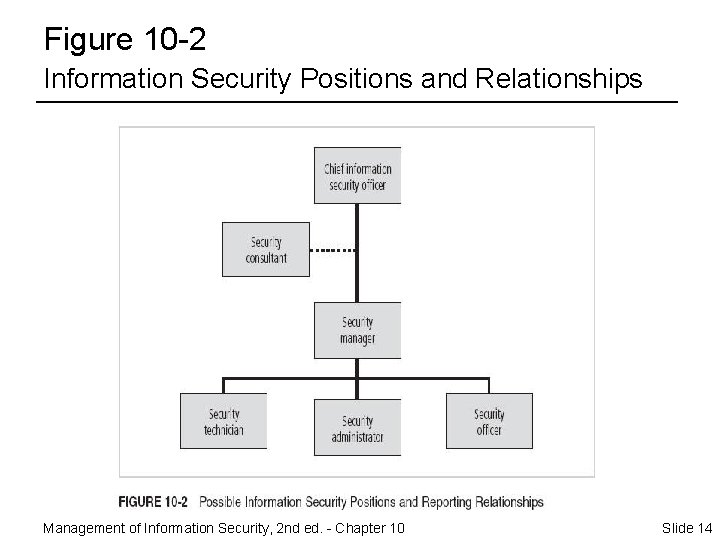
Information Security Positions ¨ Information security positions can be classified into one of three areas: those that define, those that build, and those that administer – Definers provide the policies, guidelines, and standards • The people who do the consulting and the risk assessment, and develop the product and technical architectures • Senior people with a broad knowledge, but not a lot of depth – Builders are the real techies, who create and install security solutions – The people who operate and administer the security tools, the security monitoring function, and the people who continuously improve the processes • This is where all the day-to-day, hard work is done Management of Information Security, 2 nd ed. - Chapter 10 Slide 13

Figure 10 -2 Information Security Positions and Relationships Management of Information Security, 2 nd ed. - Chapter 10 Slide 14

Security Technician Qualifications and Position Requirements ¨ Security technicians are technically qualified individuals who ensure that the security technology is properly implemented ¨ The role of security technician is the typical information security entry-level position, albeit a technical one ¨ Security technicians often tend to be specialized ¨ Organizations typically prefer expert, certified, proficient technicians ¨ Job requirements usually include some level of experience Management of Information Security, 2 nd ed. - Chapter 10 Slide 15

Security Manager Qualifications and Position Requirements ¨ Security Manager is accountable for day to day operations of information security program ¨ These individuals require an understanding of the technology administered ¨ Several types of information security managers exist, and the people who fill these roles tend to be much more specialized ¨ It is not uncommon for a security manager to have a CISSP ¨ These individuals must have experience in traditional business activities Management of Information Security, 2 nd ed. - Chapter 10 Slide 16

Chief Information Security Officer (CISO) Qualifications and Position Requirements ¨ The CISO is considered the top information security officer in the organization ¨ This individual is the spokesperson for the security team and is responsible for the overall information security program ¨ The most common qualification for the CISO is the Certified Information Systems Security Professional (CISSP) ¨ A graduate degree in criminal justice, business, technology, or another related field is usually required as well Management of Information Security, 2 nd ed. - Chapter 10 Slide 17

Information Security Professional Credentials ¨ Many organizations rely to some extent on recognizable professional certifications to ascertain the level of proficiency possessed by any given candidate ¨ Many of the certification programs are relatively new, and consequently their precise value is not fully understood by most hiring organizations ¨ The certifying bodies work diligently to educate their constituent communities on the value and qualifications of their certificate recipients ¨ Employers struggle to match certifications to position requirements, while potential information security workers try to determine which certification programs will help them in the job market Management of Information Security, 2 nd ed. - Chapter 10 Slide 18

Certified Information Systems Security Professional (CISSP) ¨ The CISSP is considered the most prestigious certification for security managers and CISOs ¨ The CISSP certification recognizes mastery of an internationally recognized common body of knowledge (CBK) in information security, covering ten domains of information security knowledge: – – – Access control systems and methodology Applications and systems development Business continuity planning Cryptography Law, investigation, and ethics Management of Information Security, 2 nd ed. - Chapter 10 Slide 19

Certified Information Systems Security Professional (CISSP) (continued) ¨ The CISSP certification recognizes mastery of an internationally recognized common body of knowledge (CBK) in information security, covering ten domains of information security knowledge (continued): – – – Operations security Physical security Security architecture and models Security management practices Telecommunications, network, and Internet security Management of Information Security, 2 nd ed. - Chapter 10 Slide 20

Certified Information Systems Security Professional (CISSP) Concentrations ¨ A number of concentrations are available for CISSP’s to demonstrate advanced knowledge beyond CISSP CBK: – Information Systems Security Architecture Professional (ISSAP) – Information Systems Security Engineering Professional (ISSEP) – Information Systems Security Management Professional Enterprise Security Management Practices (ISSMP) Management of Information Security, 2 nd ed. - Chapter 10 Slide 21

Systems Security Certified Practitioner (SSCP) ¨ The SSCP certification is more applicable to the security manager than the technician, as the bulk of its questions focus on the operational nature of information security ¨ The SSCP focuses “on practices, roles, and responsibilities as defined by experts from major IS industries” and covers seven domains: – – – – Access controls Administration Audit and monitoring Risk, response, and recovery Cryptography Data communications Malicious code/malware Management of Information Security, 2 nd ed. - Chapter 10 Slide 22

Certified Information Systems Auditor (CISA) ¨ The Information Systems Audit and Control Association and Foundation (ISACA) touts the CISA as being appropriate for auditing, networking, and security professionals ¨ The exam covers the following areas of information systems auditing: – – – The IS audit process Management, planning, and organization of IS Technical infrastructure and operational practices Protection of information assets Disaster recovery and business continuity Business application system development, acquisition, implementation, and maintenance – Business process evaluation and risk management Management of Information Security, 2 nd ed. - Chapter 10 Slide 23

Certified Information Security Manager (CISM) ¨ The CISM certification is geared towards experienced information security managers ¨ The CISM can assure executive management that a candidate is apposite for security management and consulting ¨ The CISM exam is offered annually ¨ The exam covers: – – – Information security governance Risk management Information security program management Information security management Response management Management of Information Security, 2 nd ed. - Chapter 10 Slide 24

Global Information Assurance Certification (GIAC) ¨ The System Administration, Networking and Security Organization (SANS) has developed a series of technical security certifications known as the GIAC ¨ The GIAC family of certifications can be pursued independently or combined to earn a comprehensive certification called GIAC Security Engineer (GSE), at a silver, gold or platinum level Management of Information Security, 2 nd ed. - Chapter 10 Slide 25

Security Certified Program (SCP) ¨ The SCP offers three tracks: the Security Certified Network Specialist (SCNS), the Security Certified Network Professional (SCNP), and the Security Certified Network Architect (SCNA) ¨ All are designed for the security technician and emphasize technical knowledge; the latter also includes authentication principles ¨ The SCNS is the introductory certification and covers Tactical Perimeter Defense (TPD) ¨ The SCNP track is the second level of certification and covers Strategic Infrastructure Security (SIS) ¨ The SCNA program is the advanced certification and covers Enterprise Security Solution (ESS) and Advanced Security Implementation (ASI) Management of Information Security, 2 nd ed. - Chapter 10 Slide 26

Security+ ¨ The Comp. TIA Security+ certification tests for security knowledge mastery of an individual ¨ The exam covers five domains: – 1. 0 General security concepts – 2. 0 Communication security – 3. 0 Infrastructure security – 4. 0 Basics of cryptography – 5. 0 Operational/Organizational security Management of Information Security, 2 nd ed. - Chapter 10 Slide 27

Certified Computer Examiner (CCE) ¨ The CCE certification is a computer forensics certification provided by the International Society of Forensic Computer Examiners ¨ This certification has concentrations/endorsements corresponding to various operating systems ¨ A CCE who earns three or more of these endorsements qualifies as Master Certified Computer Examiner (MCE) Management of Information Security, 2 nd ed. - Chapter 10 Slide 28

Certified Information Forensics Investigator (CIFI) ¨ The International Information Security Forensics Association is developing the Certified Information Systems Forensics Investigator certification ¨ This program will evaluate expertise in the tasks and responsibilities of a security administrator or security manager ¨ The body of knowledge includes: – – – Countermeasures Auditing Incident response teams Law enforcement and investigation Traceback Tools and techniques Management of Information Security, 2 nd ed. - Chapter 10 Slide 29

Certification Costs ¨ Certifications cost money, and the preferred certifications can be expensive ¨ Given the nature of the knowledge needed to pass the examinations, most experienced professionals find it difficult to do well without at least some review ¨ Certifications are designed to recognize experts in their respective fields, and the cost of certification deters those who might otherwise take the exam just to see if they can pass ¨ Most examinations require between two and three years of work experience, and they are often structured to reward candidates who have significant hands-on experience Management of Information Security, 2 nd ed. - Chapter 10 Slide 30

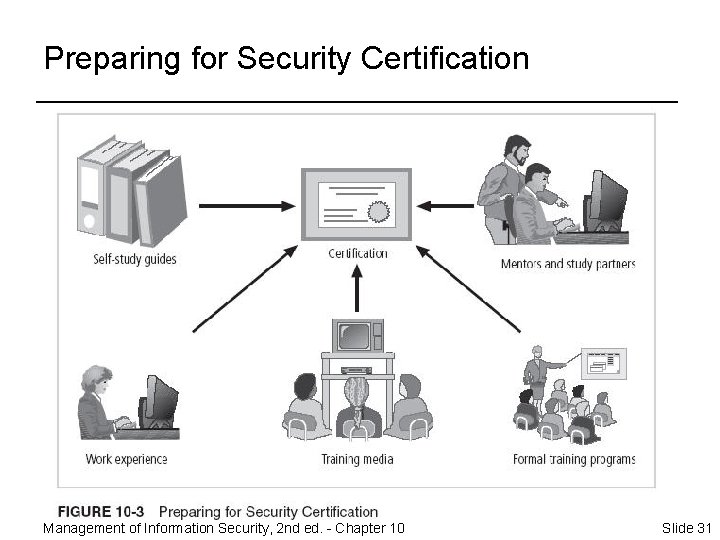
Preparing for Security Certification Management of Information Security, 2 nd ed. - Chapter 10 Slide 31

Employment Policies and Practices ¨ The general management community of interest should integrate solid information security concepts across all of the organization’s employment policies and practices ¨ Security concepts should be associated with hiring, firing or releasing, and management of human resources Management of Information Security, 2 nd ed. - Chapter 10 Slide 32

Hiring ¨ From an information security perspective, the hiring of employees is laden with potential security pitfalls ¨ Information security considerations need to be made a part of the hiring process Management of Information Security, 2 nd ed. - Chapter 10 Slide 33

Hiring (continued) ¨ Integrating information security into the hiring process requires that security considerations are applied to: – Job Descriptions • When advertising open positions, omit the elements of the job description that describe access privileges – Interviews • It is advisable to limit the information provided to the candidates on the access rights of the position • When an interview includes a site visit, the tour should avoid secure and restricted sites Management of Information Security, 2 nd ed. - Chapter 10 Slide 34

Hiring (continued) ¨ Integrating information security into the hiring process requires that security considerations are applied to (continued): – Security Checks • A background check should be conducted before the organization extends an offer to any candidate • Background checks differ in their levels of detain and depth Management of Information Security, 2 nd ed. - Chapter 10 Slide 35

Common Background Checks ¨ Some of the common security background checks include – – – Identity checks Education and credential checks Previous employment verification Reference checks Worker’s compensation history Motor vehicle records Drug history Medical history Credit history Civil court history Criminal court history Management of Information Security, 2 nd ed. - Chapter 10 Slide 36

Hiring (continued) ¨ Integrating information security into the hiring process requires that security considerations are applied to (continued): – Contracts and Employment • Monitoring and nondisclosure agreements must be made a part of the employment contracts • Apply “employment contingent upon agreement” where required – New Hire Orientation • New employees should receive, as part of their orientation, an extensive information security briefing Management of Information Security, 2 nd ed. - Chapter 10 Slide 37

Personnel Security Practices ¨ The ever present threat associated with personnel is the insider threat ¨ Insider threats can be either intentional or unintentional ¨ Unintentional compromise of information from an insider can be due to lack of policy awareness or failure to adhere to the organizational policies ¨ Intentional compromise of information from an insider is the bigger of the two threats Management of Information Security, 2 nd ed. - Chapter 10 Slide 38

Personnel Security Practices (continued) ¨ Unintentional information compromise can be handled by incorporating: – On-the-Job Security Training • Organizations should conduct periodic security awareness and training activities to keep security at the forefront of the employees’ minds and minimize employee mistakes Management of Information Security, 2 nd ed. - Chapter 10 Slide 39

Personnel Security Practices (continued) ¨ Unintentional information compromise can be handled by incorporating (continued): – Security as Part of Performance Evaluation • Employees pay close attention to job performance evaluations • Including information security tasks in them will motivate employees to take more care when performing these tasks Management of Information Security, 2 nd ed. - Chapter 10 Slide 40

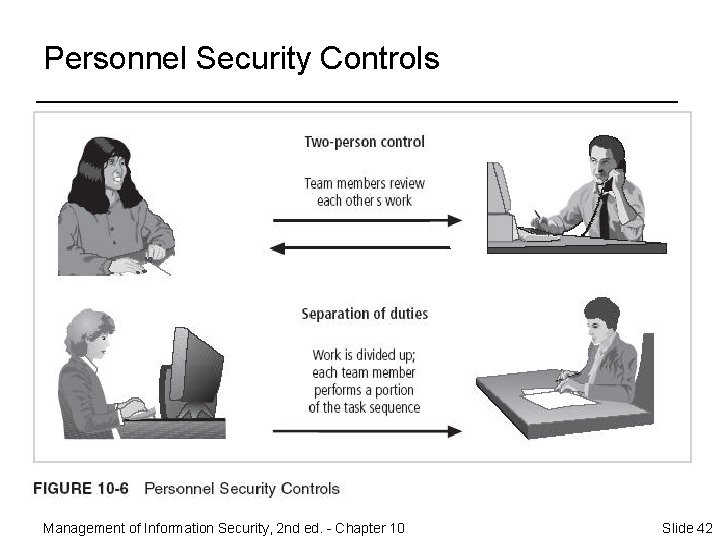
Personnel Security Practices (continued) ¨ Intentional information compromise can be handled by: – Separation of duties – Two-person control – Job rotation – Task rotation – Mandatory vacation – Principle of least privilege Management of Information Security, 2 nd ed. - Chapter 10 Slide 41

Personnel Security Controls Management of Information Security, 2 nd ed. - Chapter 10 Slide 42

Personnel Security Practices (continued) ¨ Intentional information compromise can be handled by (continued) : – Some additional measures that can be taken may be: • Forming an internal security group • Clearly emphasizing on the consequences of being detected of fraud – Detection of security compromise is important, this can be achieved by: • Periodic review of logs • Using honey tokens Management of Information Security, 2 nd ed. - Chapter 10 Slide 43

Security Considerations for Non-employees ¨ Many individuals who are not employees often have access to sensitive organizational information ¨ Relationships with individuals in this category should be carefully managed to prevent threats to information assets from materializing Management of Information Security, 2 nd ed. - Chapter 10 Slide 44

Temporary Workers ¨ Because temporary workers are not employed by the organization for which they’re working, they may not be subject to the contractual obligations or general policies that govern other employees ¨ Unless specified in its contract with the organization, the temp agency may not be liable for losses caused by its workers ¨ From a security standpoint, access to information for these individuals should be limited to what is necessary to perform their duties ¨ It should be made sure that these individuals follow good security practices Management of Information Security, 2 nd ed. - Chapter 10 Slide 45

Contract Employees ¨ While professional contractors may require access to virtually all areas of the organization to do their jobs, service contractors usually need access only to specific facilities ¨ In a secure facility – All service contractors are escorted from room to room, and into and out of the facility – Someone must verify that services are actually requested or scheduled – Advance notice for scheduling, rescheduling or cancellation of maintenance visits must be given Management of Information Security, 2 nd ed. - Chapter 10 Slide 46

Consultants ¨ Consultants have their own security requirements and contractual obligations ¨ Special requirements, such as information or facility access requirements, being integrated into the contract before they are given free access to the facility ¨ In particular, security and technology consultants must be prescreened, escorted, and subjected to nondisclosure agreements to protect the organization from intentional or accidental breaches of confidentiality ¨ Always remember to apply the principle of least privilege when working with consultants. Management of Information Security, 2 nd ed. - Chapter 10 Slide 47

Business Partners ¨ Businesses sometimes engage in strategic alliances with other organizations to exchange information, integrate systems, or enjoy some other mutual advantage ¨ A prior business agreement must specify the levels of exposure that both organizations are willing to tolerate ¨ Nondisclosure agreements are an important part of any such collaborative effort Management of Information Security, 2 nd ed. - Chapter 10 Slide 48

Termination Issues ¨ When an employee leaves an organization, the following tasks must be performed: – The former employee’s access to the organization’s systems must be disabled – The former employee must return all removable media – The former employee’s hard drives must be secured – File cabinet locks must be changed – Office door locks must be changed – The former employee’s keycard access must be revoked – The former employee’s personal effects must be removed from the premises – The former employee should be escorted from the premises, once keys, keycards, and other business property have been turned over Management of Information Security, 2 nd ed. - Chapter 10 Slide 49

Termination Issues (continued) ¨ In addition to performing these tasks, many organizations conduct an exit interview ¨ Some organizations adopt the policy of immediate severance ¨ Two methods for handling employee out processing, depending on the employee’s reasons for leaving, are: – Hostile departures – Friendly departures Management of Information Security, 2 nd ed. - Chapter 10 Slide 50

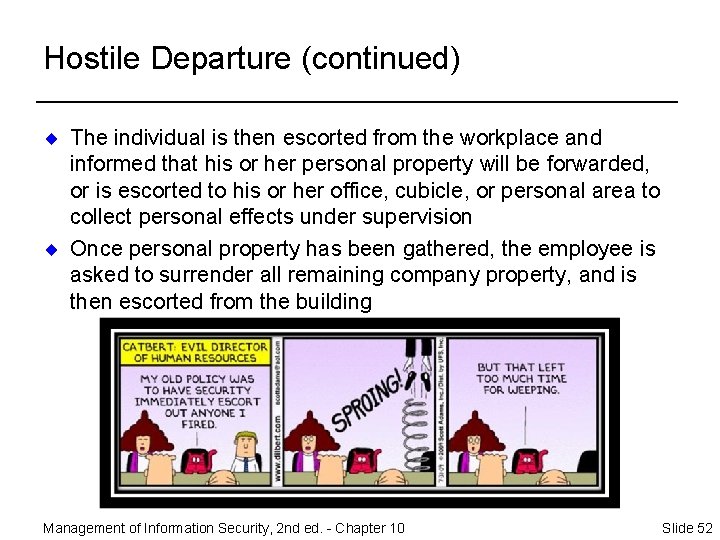
Hostile Departure ¨ Security cuts off all logical and keycard access, before the employee is terminated ¨ The employee reports for work, and is escorted into the supervisor’s office to receive the bad news Management of Information Security, 2 nd ed. - Chapter 10 Slide 51

Hostile Departure (continued) ¨ The individual is then escorted from the workplace and informed that his or her personal property will be forwarded, or is escorted to his or her office, cubicle, or personal area to collect personal effects under supervision ¨ Once personal property has been gathered, the employee is asked to surrender all remaining company property, and is then escorted from the building Management of Information Security, 2 nd ed. - Chapter 10 Slide 52

Friendly Departure ¨ The employee may have tendered notice well in advance of the actual departure date ¨ Employee accounts are usually allowed to continue, with a new expiration date ¨ The employee can come and go at will and usually collects any belongings and leaves without escort ¨ The employee is asked to drop off all organizational property before departing. Management of Information Security, 2 nd ed. - Chapter 10 Slide 53

Termination Issues ¨ In either circumstance, the offices and information used by departing employees must be inventoried, their files stored or destroyed, and all property returned to organizational stores ¨ It is possible that departing employees have collected and taken home information or assets that could be valuable in their future jobs ¨ Only by scrutinizing system logs during the transition period can the organization determine whether a breach of policy or a loss of information has occurred Management of Information Security, 2 nd ed. - Chapter 10 Slide 54

Summary ¨ Introduction ¨ Staffing the Security Function ¨ Information Security Professional Credentials ¨ Employment Policies and Practices Management of Information Security, 2 nd ed. - Chapter 10 Slide 55

Case Discussion ¨ What do you think Amy should do now ? ¨ What could be the consequences of her action? ¨ How do you think should the management react to this incident? Management of Information Security, 2 nd ed. - Chapter 10 Slide 56

References ¨ Whitman, Michael E. , and Herbert J. Mattord. 2008. Management of information security. Boston: Thomson Course Technology ¨ Whitman, Michael E. , and Herbert J. Mattord. 2008. Readings and cases in management of information security. Boston: Thomson Course Technology ¨ Carroll, M. D. 2006. Information security: examining and managing the insider threat. In Proceedings of the 3 rd Annual Conference on information Security Curriculum Development (Kennesaw, Georgia, September 22 - 23, 2006). Info. Sec. CD '06. ACM, New York, NY, 156 -158. DOI= http: //doi. acm. org/10. 1145/1231047. 1231082 ¨ Sample Information technology security staffing plan, NISTComputer Security Division/Archives Management of Information Security, 2 nd ed. - Chapter 10 Slide 57

Thank you for your time Questions and comments are welcome! Management of Information Security, 2 nd ed. - Chapter 10 Slide 58