Man in the Middle Attacks 1 Man in






![Adapted from Vitaly Shmatikov’s lecture slides Anomaly in Needham-Schroeder [published by Lowe] { A, Adapted from Vitaly Shmatikov’s lecture slides Anomaly in Needham-Schroeder [published by Lowe] { A,](https://slidetodoc.com/presentation_image/369323cc2362c1aafdf7477676f878e8/image-10.jpg)

![Adapted from Vitaly Shmatikov’s lecture slides The attack no longer works [published by Lowe] Adapted from Vitaly Shmatikov’s lecture slides The attack no longer works [published by Lowe]](https://slidetodoc.com/presentation_image/369323cc2362c1aafdf7477676f878e8/image-13.jpg)
- Slides: 13

Man in the Middle Attacks 1

Man in the Middle • SSH authentication with agent is an example of (benign) “man in the middle” in authentication • M-i-M is a fundamental problem in all authentication protocols – The protocols can only prove that the legitimate party is talking – But does it yield the desired protection against adversaries? 2

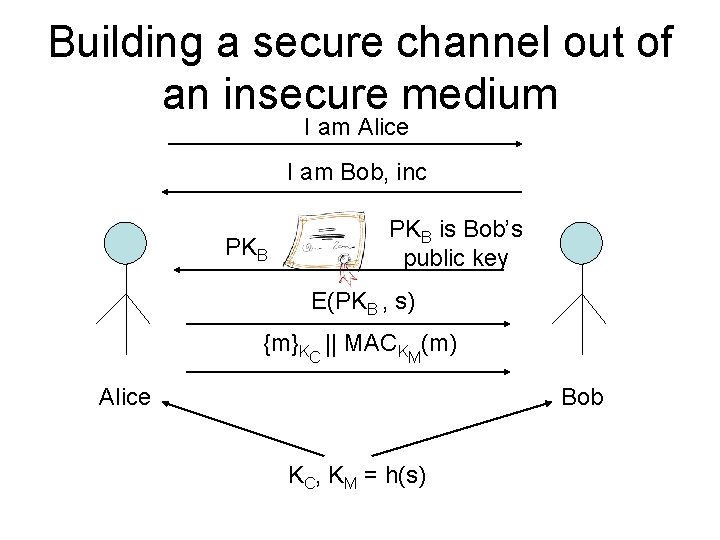
Building a Secure Channel • What is a secure channel? – Messages sent between Alice and Bob should not be • eavesdropped by the attacker • tampered with by the attacker – Provide assurance on who you are talking to

Building a secure channel out of an insecure medium • Use symmetric cipher – Faster than public-key cipher – Encryption ensures confidentiality of communication – Authentication and data integrity ensured by applying message authentication code • Need to establish a shared secret

Building a secure channel out of an insecure medium I am Alice I am Bob, inc PKB is Bob’s public key E(PKB , s) {m}KC || MACKM(m) Alice Bob KC, KM = h(s)

SSL/TLS I am Alice I am Bob, inc PKB is Bob’s public key E(PKB , s) {m}KC || MACKM(m) Alice Bob KC, KM = h(s)

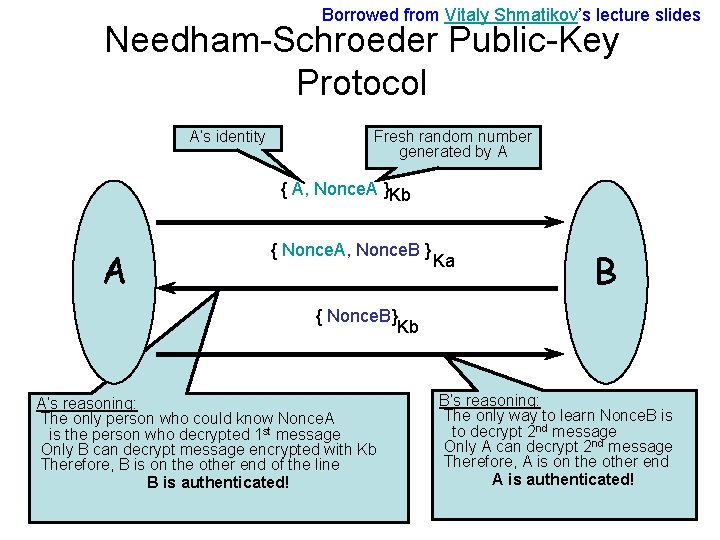
Borrowed from Vitaly Shmatikov’s lecture slides Mi. M Attack Example: Needham-Schroeder • Very (in)famous example – Appeared in a 1979 paper – Goal: authentication in a network of workstations – In 1995, Gavin Lowe discovered unintended property while preparing formal analysis using FDR system • Background: public-key cryptography – Every agent A has a key pair Ka, Ka-1 – Everybody knows public key Ka and can encrypt messages to A with it (we’ll use {m}Ka notation) – Only A knows secret key Ka-1, therefore, only A can decrypt messages encrypted with Ka

Borrowed from Vitaly Shmatikov’s lecture slides Needham-Schroeder Public-Key Protocol A’s identity Fresh random number generated by A { A, Nonce. A }Kb A { Nonce. A, Nonce. B } Ka B { Nonce. B} Kb A’s reasoning: The only person who could know Nonce. A is the person who decrypted 1 st message Only B can decrypt message encrypted with Kb Therefore, B is on the other end of the line B is authenticated! B’s reasoning: The only way to learn Nonce. B is to decrypt 2 nd message Only A can decrypt 2 nd message Therefore, A is on the other end A is authenticated!

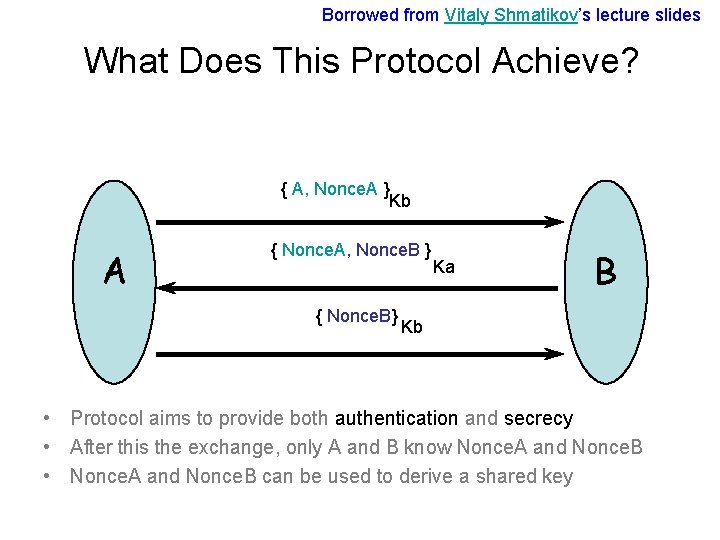
Borrowed from Vitaly Shmatikov’s lecture slides What Does This Protocol Achieve? { A, Nonce. A } Kb A { Nonce. A, Nonce. B } { Nonce. B} Ka B Kb • Protocol aims to provide both authentication and secrecy • After this the exchange, only A and B know Nonce. A and Nonce. B • Nonce. A and Nonce. B can be used to derive a shared key
![Adapted from Vitaly Shmatikovs lecture slides Anomaly in NeedhamSchroeder published by Lowe A Adapted from Vitaly Shmatikov’s lecture slides Anomaly in Needham-Schroeder [published by Lowe] { A,](https://slidetodoc.com/presentation_image/369323cc2362c1aafdf7477676f878e8/image-10.jpg)
Adapted from Vitaly Shmatikov’s lecture slides Anomaly in Needham-Schroeder [published by Lowe] { A, Na }Kb A { Na, Nc }Ka { Nc } B can’t decrypt this message, but he can forward it Evil agent B tricks honest A into revealing C’s private value Nc C is convinced that he is talking to A! B Kb Evil B pretends that he is A { Nc }Kc { A, Na } Kc { Na, Nc } Ka C

Adapted from Vitaly Shmatikov’s lecture slides Lessons of Needham-Schroeder • Classic man-in-the-middle attack • Exploits participants’ reasoning to fool them • A is correct that B must have decrypted {A, Na}Kb message, but this does not mean that message {Na, Nb}Ka came from B • The attack has nothing to do with cryptography! • It is important to realize limitations of attacks – The attack requires that A willingly talk to adversary – In the original setting, each workstation is assumed to be well-behaved, and the protocol is correct!

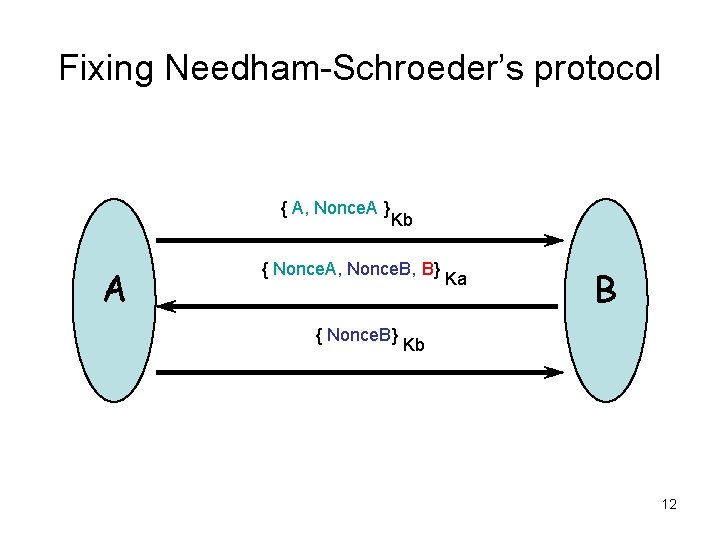
Fixing Needham-Schroeder’s protocol { A, Nonce. A } A Kb { Nonce. A, Nonce. B, B} { Nonce. B} Ka B Kb 12
![Adapted from Vitaly Shmatikovs lecture slides The attack no longer works published by Lowe Adapted from Vitaly Shmatikov’s lecture slides The attack no longer works [published by Lowe]](https://slidetodoc.com/presentation_image/369323cc2362c1aafdf7477676f878e8/image-13.jpg)
Adapted from Vitaly Shmatikov’s lecture slides The attack no longer works [published by Lowe] { A, Na } Kb A { Na, Nc, C } Ka B Evil B pretends that he is A A will detect that the message was actually sent by C. { A, Na } Kc { Na, Nc, C } Ka C