LWIP TCPIP Stack What is LWIP An implementation




- Slides: 19

LWIP TCP/IP Stack 김백규

What is LWIP? An implementation of the TCP/IP protocol stack. ã The focus of the lw. IP stack is to reduce memory usage and code size Ý suitable for embedded systems. ã uses a tailor made API that does not require any data copying. ã

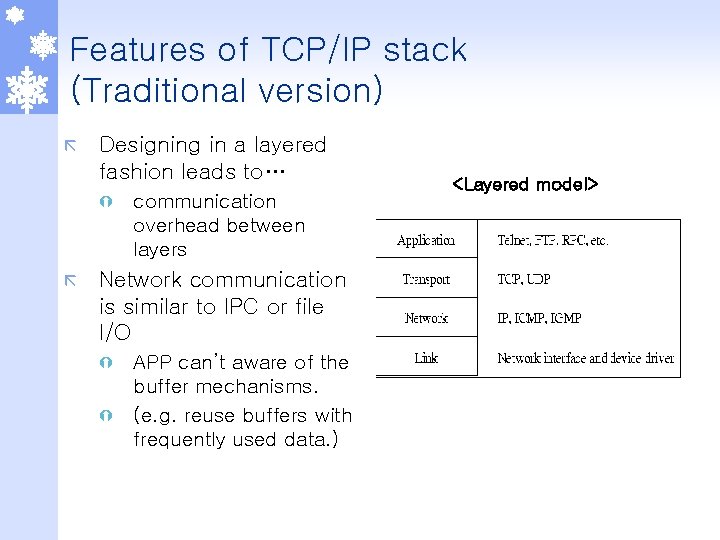
Features of TCP/IP stack (Traditional version) ã Designing in a layered fashion leads to… Ý ã communication overhead between layers Network communication is similar to IPC or file I/O APP can’t aware of the buffer mechanisms. Ý (e. g. reuse buffers with frequently used data. ) Ý <Layered model>

Features of TCP/IP stack (LWIP version) Do not maintain a strict layer. Ý More relaxed scheme for communication between layers. (By means of shared memory) - APP layer can use the buffer handling mechanisms used by the lower layers. APP can more efficiently reuse buffers. ã Application process can use the same memory as the networking code Ý App can read and write directly to the internal buffers. Ý Saving the expense of performing a copy ã

Process model of LWIP ã All protocols reside in a single process thus are separated from the OS kernel. Ý ã Allow to be portable across different OS. APP may either reside in the LWIP process or be in separate processes. Communicate are done by function calls. Ý Or a more abstract API. Ý

The operating system emulation layers ã OS specific function calls and data structures are not used directly in the code. Ý The operating system emulation layer is used. ã The OS emulation layer provides Ý Timers, process synchronization, message passing mechanisms, and so on. ã Porting to a different OS Ý Only need the operating system emulation layer.

Buffer and memory management ã Packet buffers – pbufs Ý LWIP’s internal representation of a packet, Ý Designed for the special needs of the minimal stack. ã Types of pbufs Ý PBUF_RAM, PBUF_ROM, PBUF_POOL Ý A pbuf chain may consist of multiple types of pbufs.

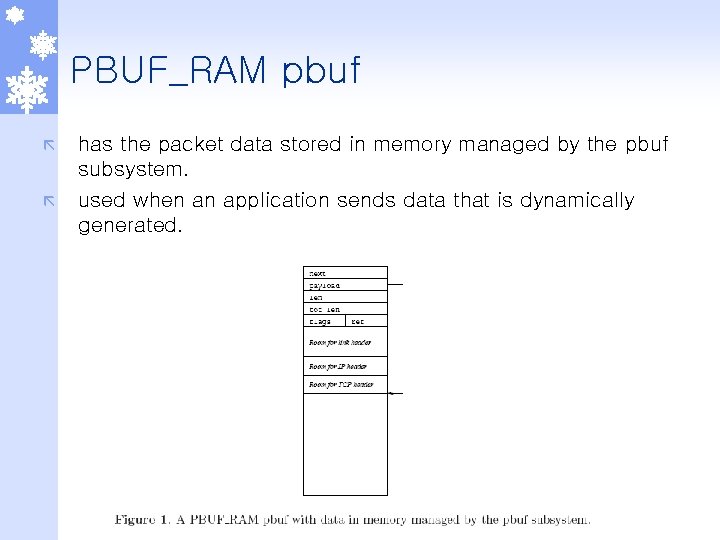
PBUF_RAM pbuf ã ã has the packet data stored in memory managed by the pbuf subsystem. used when an application sends data that is dynamically generated.

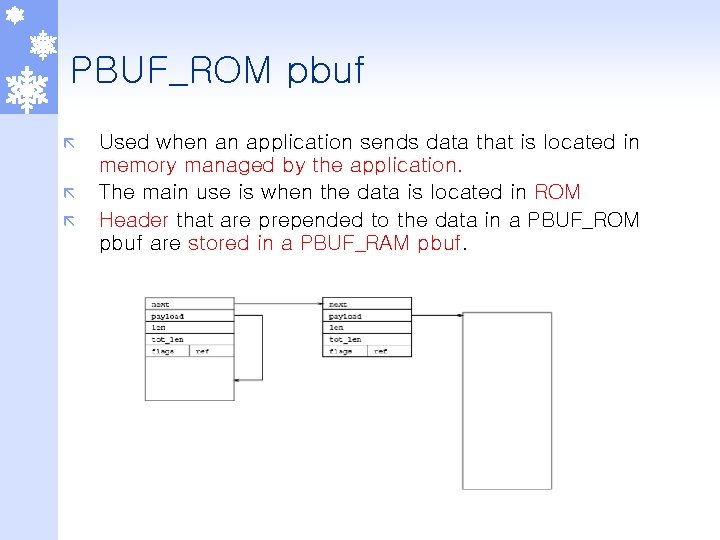
PBUF_ROM pbuf ã ã ã Used when an application sends data that is located in memory managed by the application. The main use is when the data is located in ROM Header that are prepended to the data in a PBUF_ROM pbuf are stored in a PBUF_RAM pbuf.

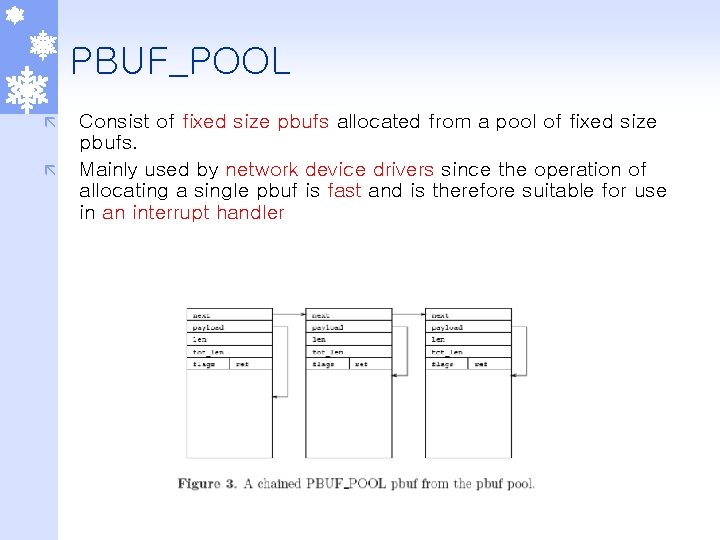
PBUF_POOL ã ã Consist of fixed size pbufs allocated from a pool of fixed size pbufs. Mainly used by network device drivers since the operation of allocating a single pbuf is fast and is therefore suitable for use in an interrupt handler

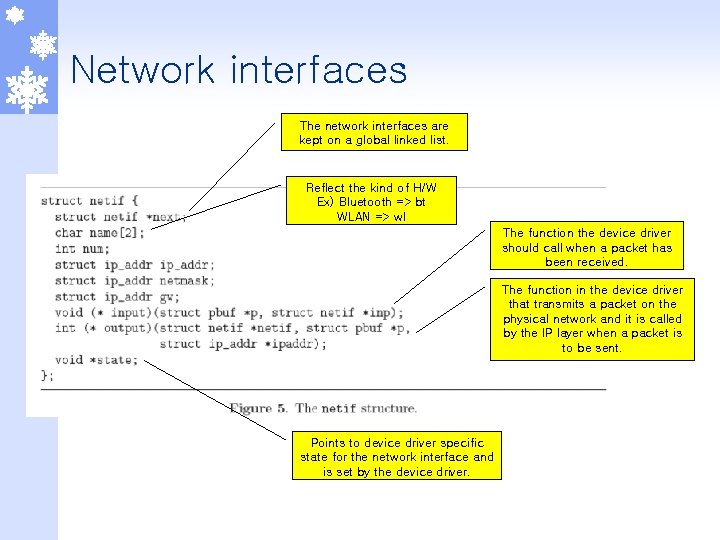
Network interfaces The network interfaces are kept on a global linked list. Reflect the kind of H/W Ex) Bluetooth => bt WLAN => wl The function the device driver should call when a packet has been received. The function in the device driver that transmits a packet on the physical network and it is called by the IP layer when a packet is to be sent. Points to device driver specific state for the network interface and is set by the device driver.

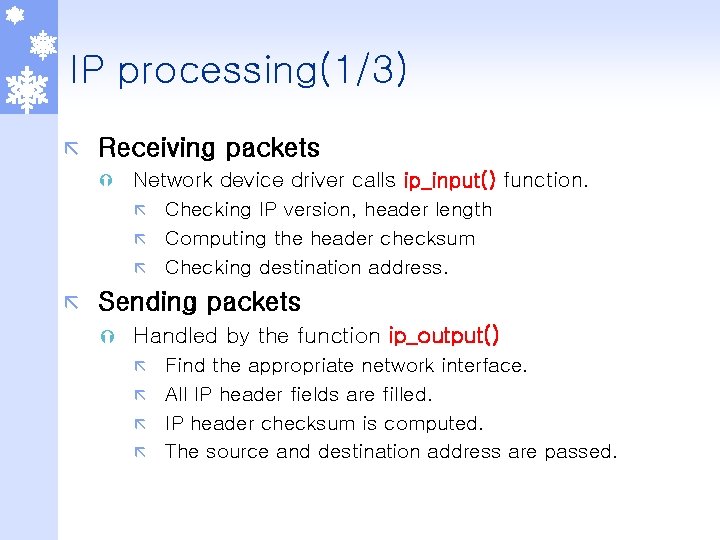
IP processing(1/3) ã Receiving packets Ý ã Network device driver calls ip_input() function. ã Checking IP version, header length ã Computing the header checksum ã Checking destination address. Sending packets Ý Handled by the function ip_output() Find the appropriate network interface. ã All IP header fields are filled. ã IP header checksum is computed. ã The source and destination address are passed. ã

IP processing(2/3) ã Forwarding packets Ý The packet should be forwarded… ã Ý When none of the network interfaces has the same IP address as an incoming packet’s destination address. This is done by the function ip_forward() ttl field is decreased. ã If ttl reaches zero, an ICMP error message is sent. ã

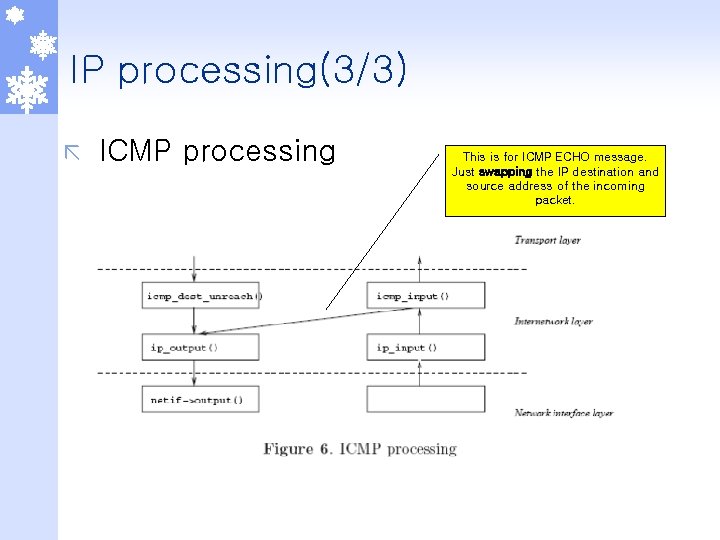
IP processing(3/3) ã ICMP processing This is for ICMP ECHO message. Just swapping the IP destination and source address of the incoming packet.

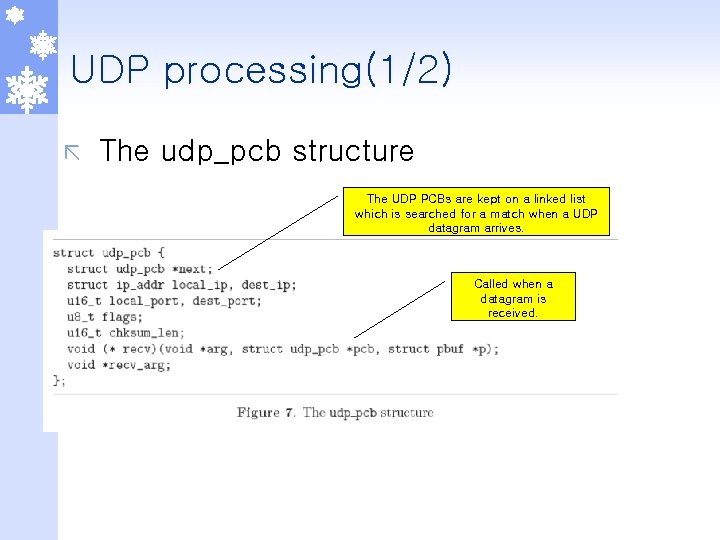
UDP processing(1/2) ã The udp_pcb structure The UDP PCBs are kept on a linked list which is searched for a match when a UDP datagram arrives. Called when a datagram is received.

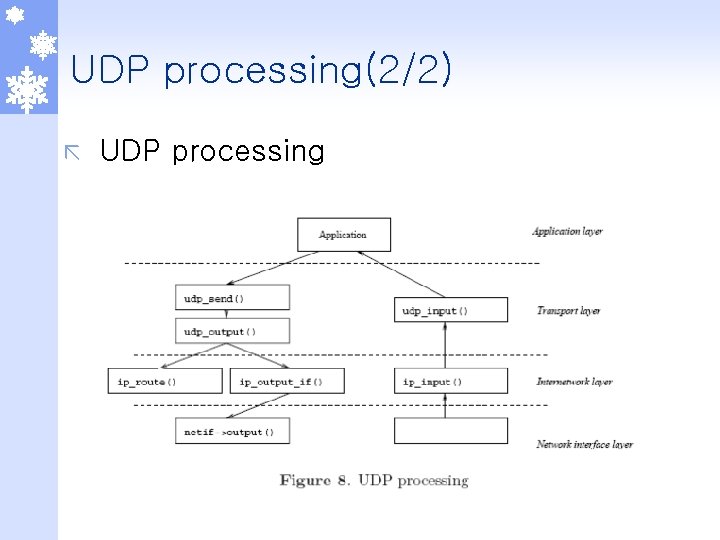
UDP processing(2/2) ã UDP processing

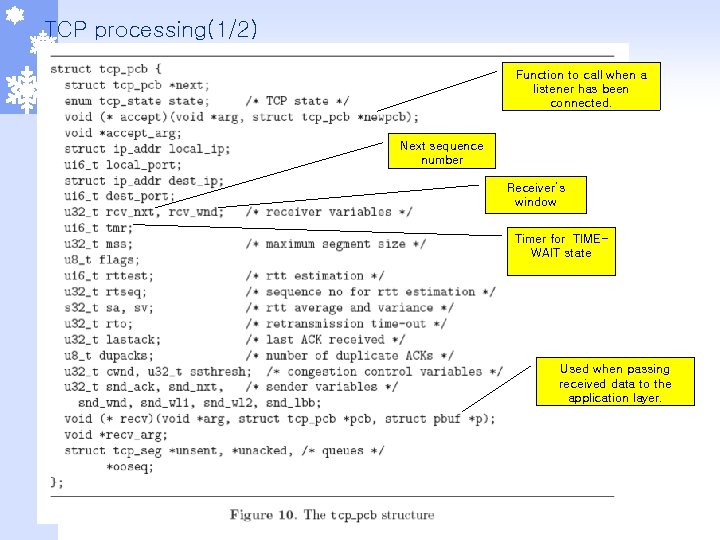
TCP processing(1/2) Function to call when a listener has been connected. Next sequence number Receiver’s window Timer for TIMEWAIT state Used when passing received data to the application layer.

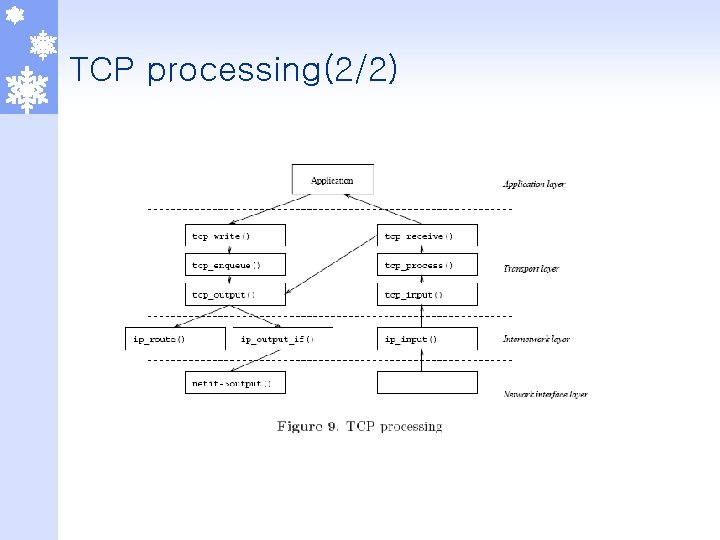
TCP processing(2/2)

Application Program Interface ã The BSD socket API Require data that is to be sent to be copied from application program to internal buffers in the TCP/IP stack. Ý Since the two layers reside in different protection domains. Ý ã The LWIP socket API Utilizes knowledge of the internal structure of LWIP to achieve effectiveness. Ý Does not require that data is copied. Ý Since the application program can manipulate the internal buffers directly. Ý