Long Term Evolution LTE Fifth Generation 5 G





- Slides: 15

Long Term Evolution (LTE) / Fifth Generation (5 G) mobile networks for military use The views in this paper are those of the authors and do not represent the views of LAND 2072 or the Department of Defence. Douglas Stapleton, Andrew Mc. Larty, Merlin Nichols Department of Defence Project Land 2072 Prime System Integration Canberra, Australia UNCLASSIFIED

Problem Statement • The bandwidth requirements on the modern battlefield are exploding, and heading beyond traditional voice communications to encompass video, imagery and data. For example, Army vehicles will become increasingly networked for logistic and tactical information. This will build up a second machine oriented set of end points in the new Battlespace network. UNCLASSIFIED

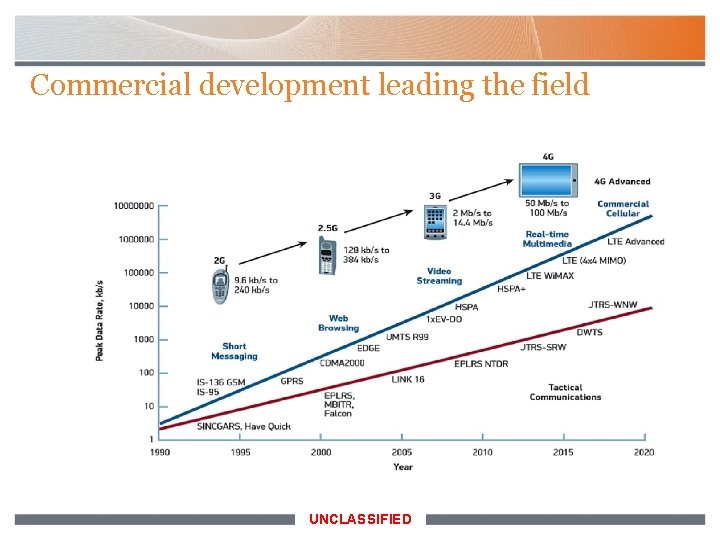
Commercial development leading the field UNCLASSIFIED

5 G is coming 2020+ • There are two defining requirements for 5 G that separate it from previous developments. They are: – its near-zero latency and – data rates of 1– 10 Gbps. • 5 G technologies are now on the planning horizon for the future Land Network. UNCLASSIFIED

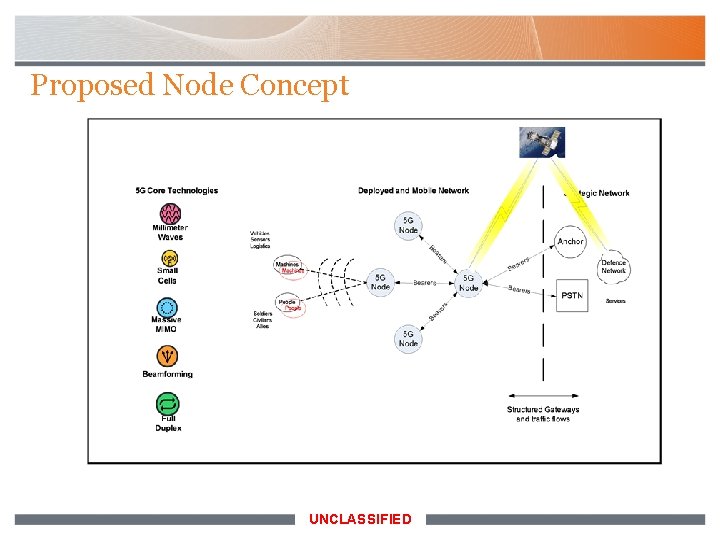
Proposed Node Concept UNCLASSIFIED

Security Considerations • LTE and 5 G systems are being developed conscious of a more hostile RF spectrum based on having to address self-interference and high network density. • 5 G standards are still being ratified, the first round of 5 G standards are due to become available in 2018 UNCLASSIFIED

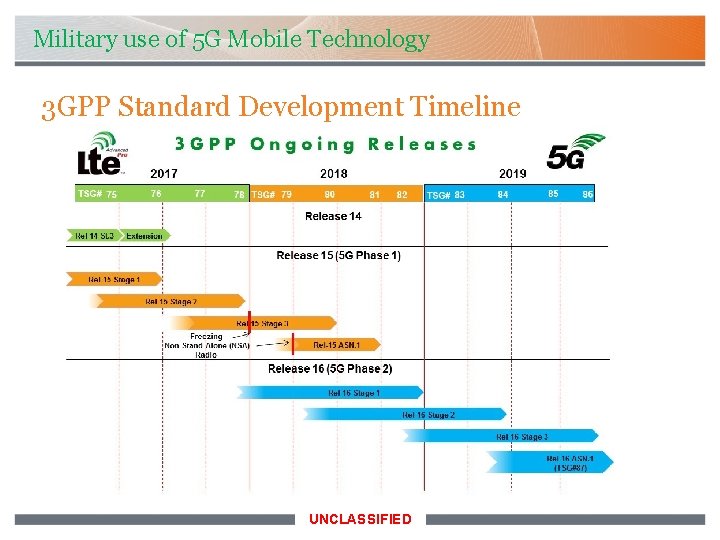
Military use of 5 G Mobile Technology 3 GPP Standard Development Timeline UNCLASSIFIED

Military use of 5 G Mobile Technology Classes of Vulnerabilities • • Mobile Malware Attacks Targeting EU 5 G Mobile Botnets UE Location Tracking He. NB Femtocell Attacks User Data and Identity Privacy Attacks Mobile Operator’s Core Network External IP Networks UNCLASSIFIED

Military use of 5 G Mobile Technology Security Considerations • Concern is mostly for an adversary’s EW Attack capability • RF jamming creates a localised Do. S • Since the introduction of LTE we see an IP based open architecture • The land communications network should be limited to the use of IPv 6 • Coexistence of multiple technologies 2 G, 3 G, 4 G, and 5 G increases attack surface UNCLASSIFIED

Military use of 5 G Mobile Technology Cont. . • Rogue base stations cross the boundary between cyber and EW • International Mobile Subscriber Identity (IMSI) protection was provided in the 3 G standards • IMSI catchers, stingrays or GSM interceptors as they’re also called, force a phone to connect to the rogue cell UNCLASSIFIED

Military use of 5 G Mobile Technology Cont. . • Network Function Virtualisation and • Software Defined Networking are two key concepts for the delivery of future complex networks • Provides separation of the control and packet forwarding capabilities of the network UNCLASSIFIED

Military use of 5 G Mobile Technology Potential Countermeasures • To counter attacks targeting RAT, use: – frequency spreading modulation techniques, – signal randomisation and – encryption techniques • provide mutual authentication between network devices • Proper configuration of security settings and disabling unused services • Use NFV and SDN recommendations to develop security policy for the future network UNCLASSIFIED

Military use of 5 G Mobile Technology Potential Countermeasures • network security measures including firewalls, intrusion prevention and network segmentation • Defence endorse future research on methods of protecting LTE and 5 G from smart jamming attacks UNCLASSIFIED

Long Term Evolution (LTE) / Fifth Generation (5 G) mobile networks for military use Summary The future is beginning to look like a high-speed lowlatency data network supporting applications across the battlespace. Voice will be but one application on the data network, unlike heritage networks which have been primarily voice radio networks with limited bandwidth available for data, as an addition. 5 G becomes a broader specialised network, with a simpler node pattern concept. Future military organisations may become operators of their own 5 G networks that will reach out to utilise commercial 4 G/5 G networks as the opportunities arise. UNCLASSIFIED

Q&A • doug. stapleton@hinfosec. com. au • amclarty@dxc. com • merlin. nichols@defence. gov. au UNCLASSIFIED