LogSeed Pseudorandom Generators via Iterated Restrictions CCC 2020

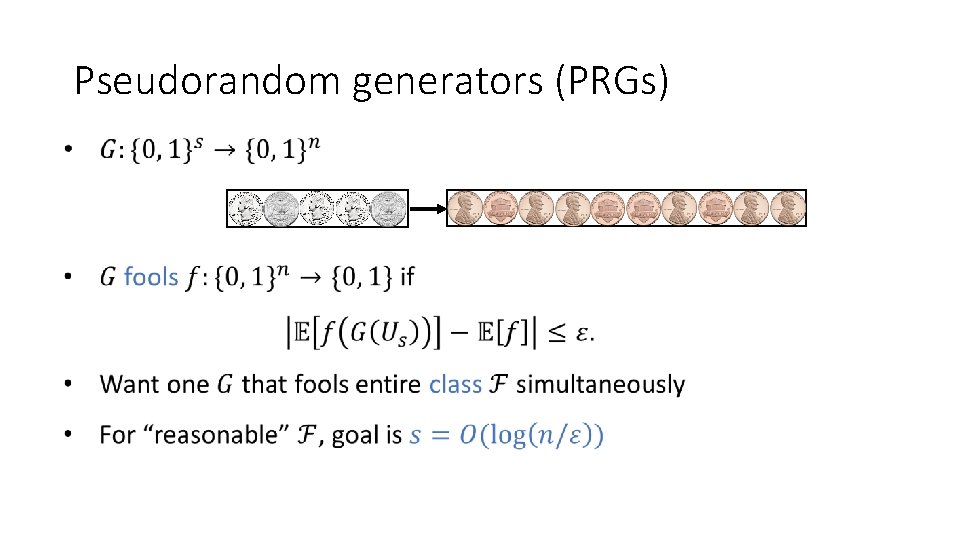
![Prior work and main result Model Seed length Reference … [Nisan 1991] … Read-once Prior work and main result Model Seed length Reference … [Nisan 1991] … Read-once](https://slidetodoc.com/presentation_image_h2/51ae7e4c42e90bc386394b99bc08e7c2/image-6.jpg)
![Ajtai-Wigderson framework • [Ajtai, Wigderson 1985] [Gopalan, Meka, Reingold, Trevisan, Vadhan 2012] Ajtai-Wigderson framework • [Ajtai, Wigderson 1985] [Gopalan, Meka, Reingold, Trevisan, Vadhan 2012]](https://slidetodoc.com/presentation_image_h2/51ae7e4c42e90bc386394b99bc08e7c2/image-7.jpg)
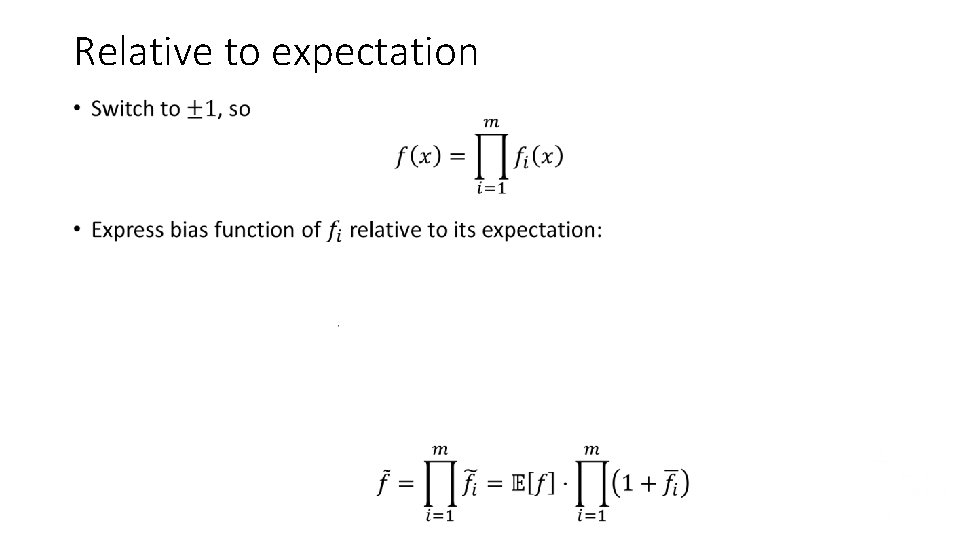
![Conclusions • References • [Ajtai, Wigderson 1985]: Deterministic simulation of probabilistic constant depth circuits. Conclusions • References • [Ajtai, Wigderson 1985]: Deterministic simulation of probabilistic constant depth circuits.](https://slidetodoc.com/presentation_image_h2/51ae7e4c42e90bc386394b99bc08e7c2/image-24.jpg)
- Slides: 24

Log-Seed Pseudorandom Generators via Iterated Restrictions CCC 2020 Dean Doron 1 Stanford ddoron@stanford. edu 1 This Pooya Hatami 2 Ohio State University pooyahat@gmail. com William M. Hoza 3 University of Texas at Austin whoza@utexas. edu work was done while at UT Austin, supported by NSF Grant CCF-1705028. work was done while at UT Austin and supported by a Simons Investigator Award (#409864, David Zuckerman) 3 Supported by the NSF GRFP under Grant DGE-1610403 and by a Harrington Fellowship from UT Austin. 2 This

Randomness in computing • Randomness is an expensive computational resource • Like time or space • Using less randomness is better than using more randomness
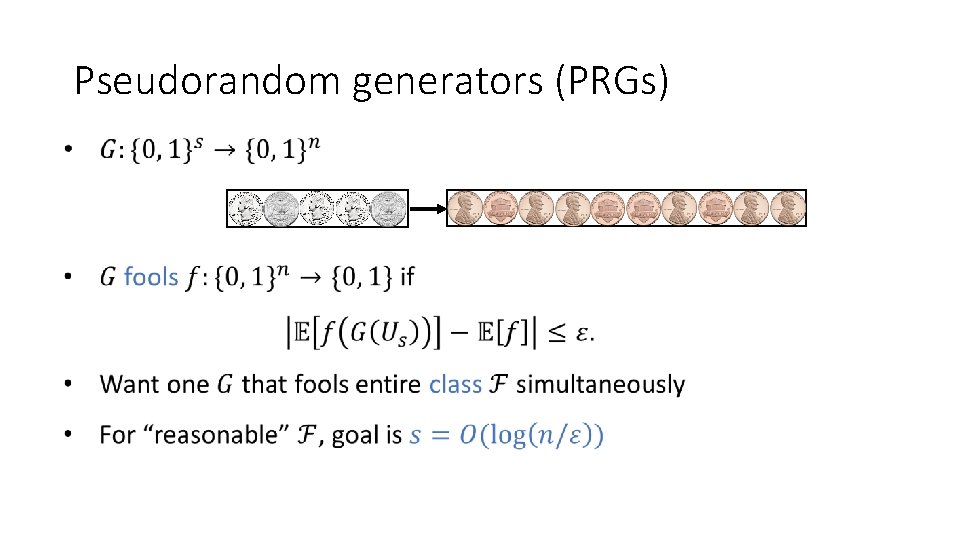
Pseudorandom generators (PRGs)


![Prior work and main result Model Seed length Reference Nisan 1991 Readonce Prior work and main result Model Seed length Reference … [Nisan 1991] … Read-once](https://slidetodoc.com/presentation_image_h2/51ae7e4c42e90bc386394b99bc08e7c2/image-6.jpg)
Prior work and main result Model Seed length Reference … [Nisan 1991] … Read-once CNFs [Chari, Rohatgi, Srinivasan 1994] [De, Etesami, Trevisan, Tulsiani 2010] [Gopalan, Meka, Reingold, Trevisan, Vadhan 2012] [Luby, Veličković, Wigderson 1993] [Gavinsky, Lovett, Srinivasan 2012] Read-once polynomials [Lee, Viola 2017] Read-once polynomials [Meka, Reingold, Tal 2019] Read-once polynomials [Lee 2019] [This work]
![AjtaiWigderson framework Ajtai Wigderson 1985 Gopalan Meka Reingold Trevisan Vadhan 2012 Ajtai-Wigderson framework • [Ajtai, Wigderson 1985] [Gopalan, Meka, Reingold, Trevisan, Vadhan 2012]](https://slidetodoc.com/presentation_image_h2/51ae7e4c42e90bc386394b99bc08e7c2/image-7.jpg)
Ajtai-Wigderson framework • [Ajtai, Wigderson 1985] [Gopalan, Meka, Reingold, Trevisan, Vadhan 2012]

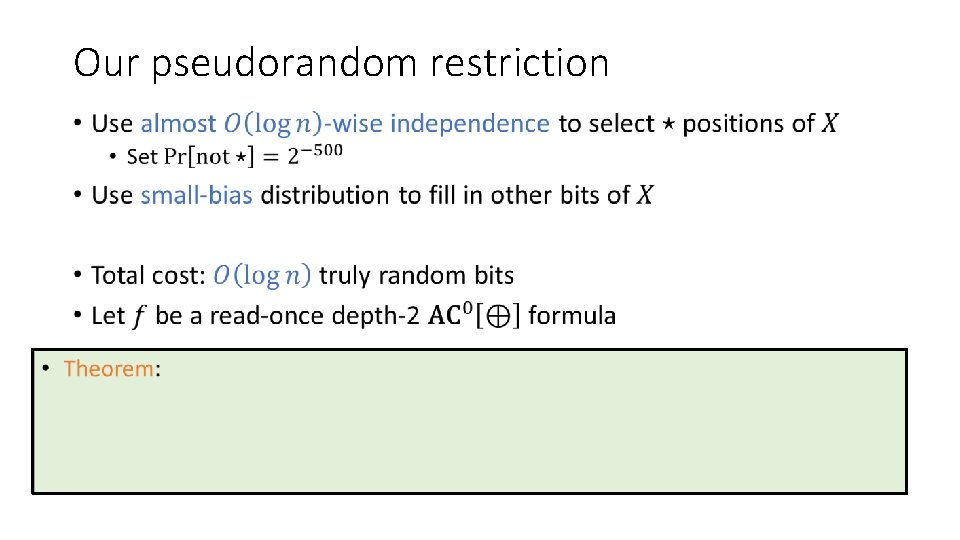
Our pseudorandom restriction •

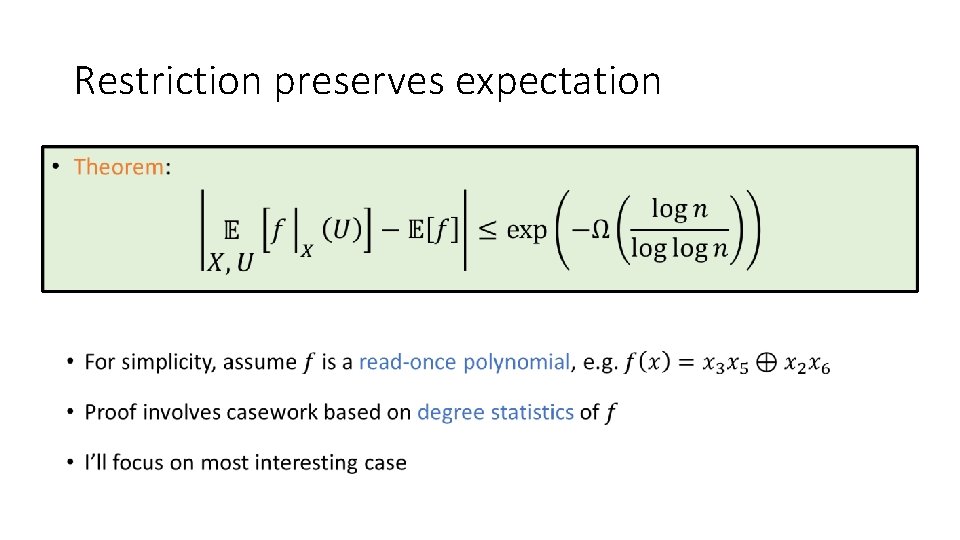
Restriction preserves expectation •

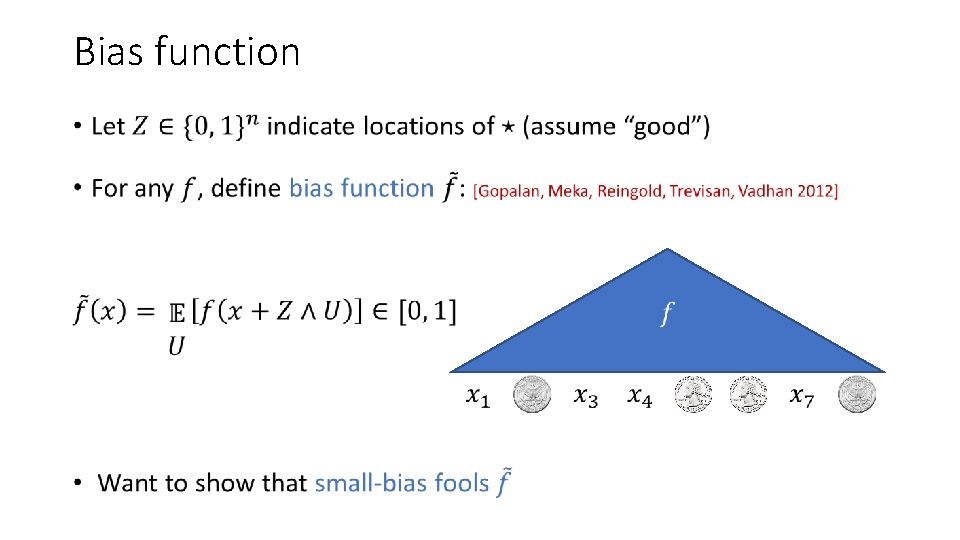
Bias function •
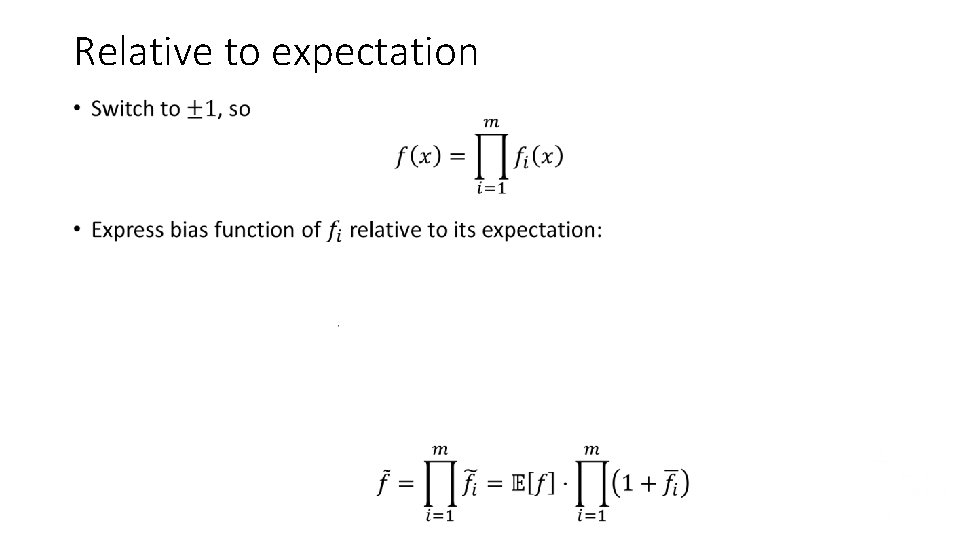
Relative to expectation •

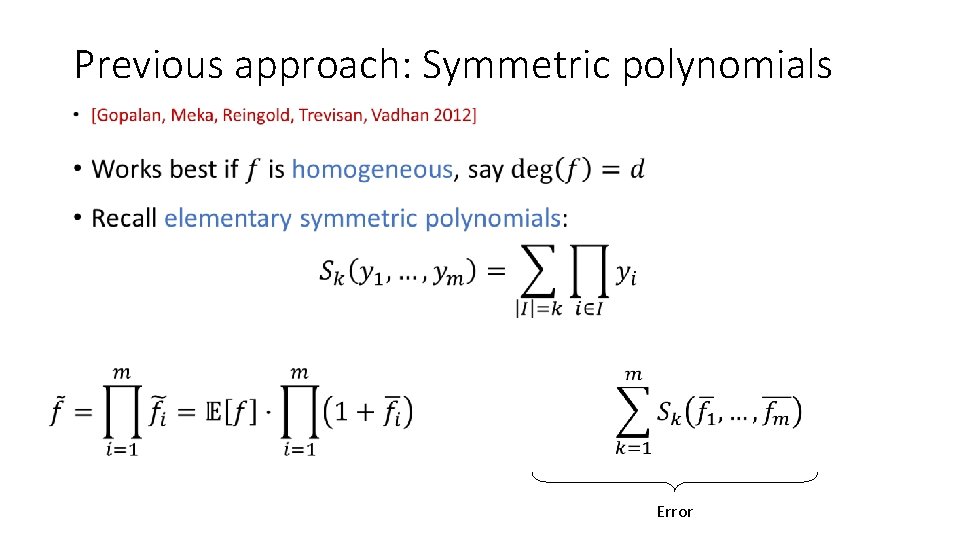
Previous approach: Symmetric polynomials • Error

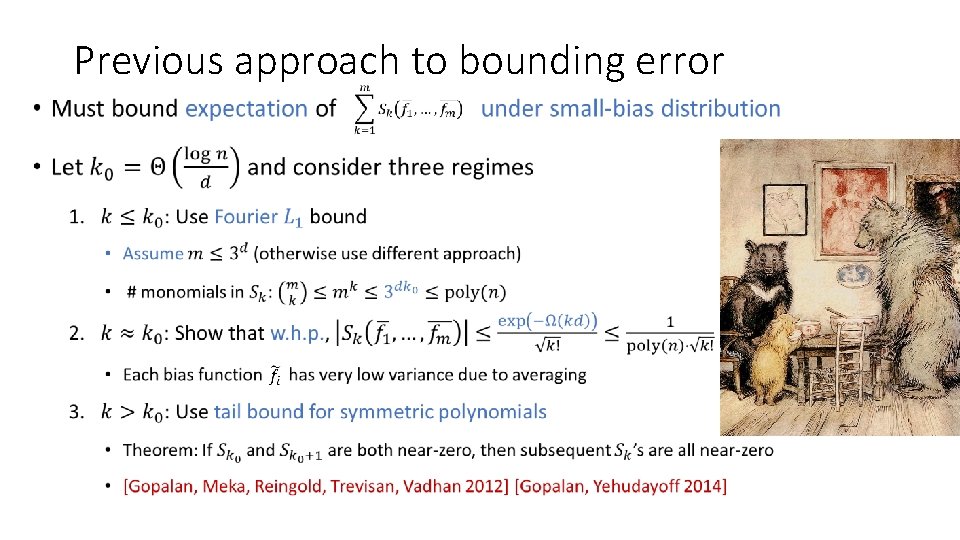
Previous approach to bounding error •

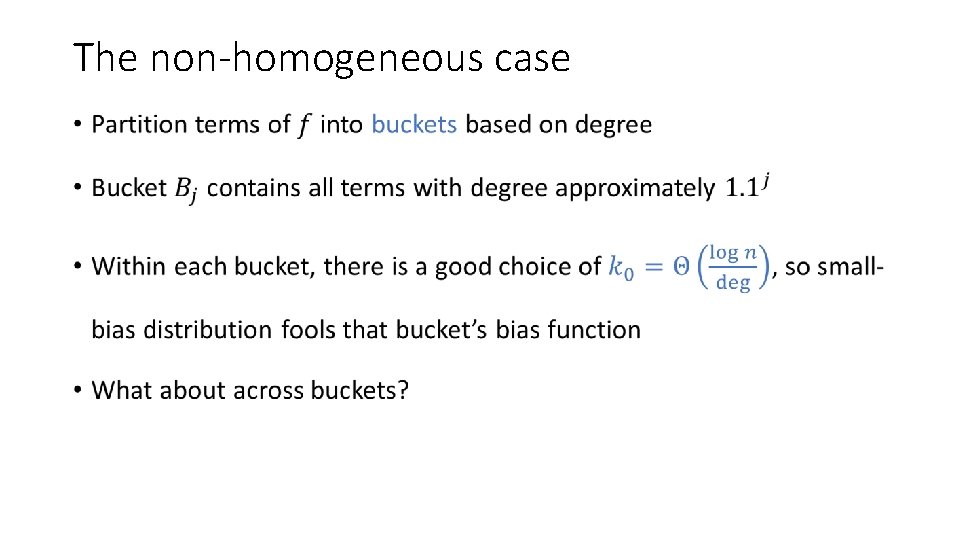
The non-homogeneous case •

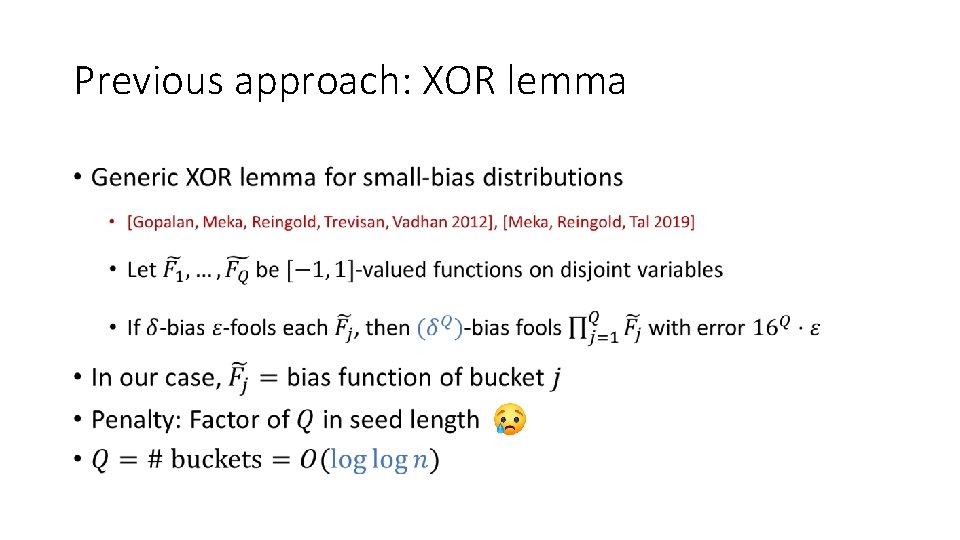
Previous approach: XOR lemma •

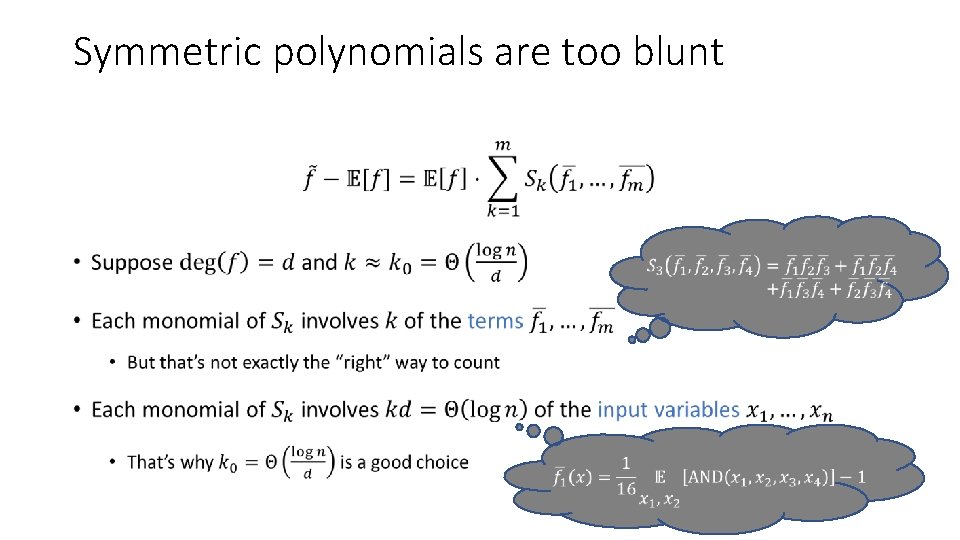
Symmetric polynomials are too blunt •

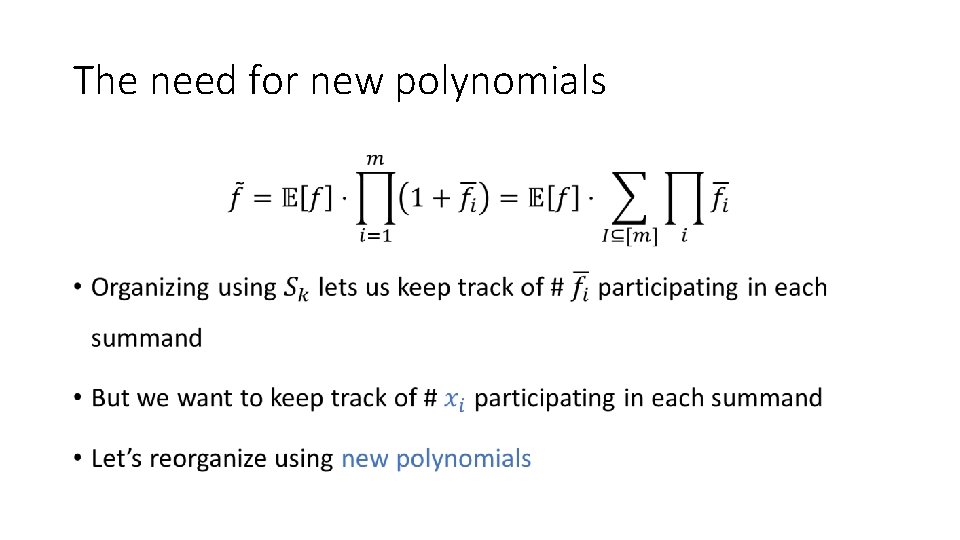
The need for new polynomials •

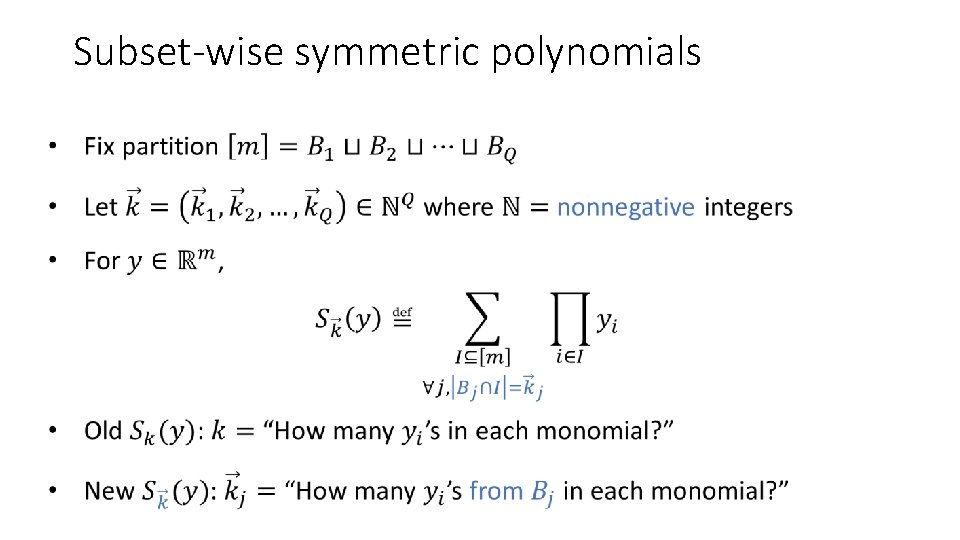
Subset-wise symmetric polynomials

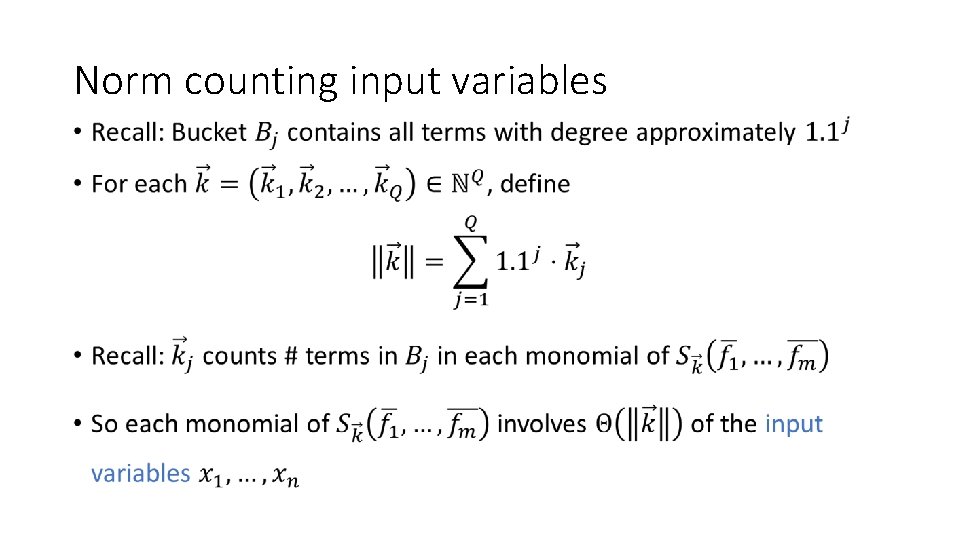
Norm counting input variables •

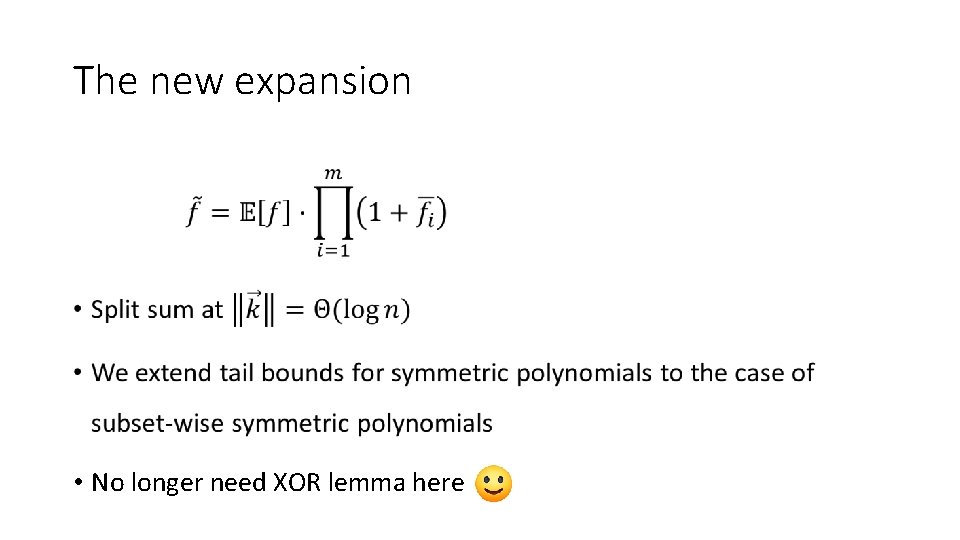
The new expansion • • No longer need XOR lemma here

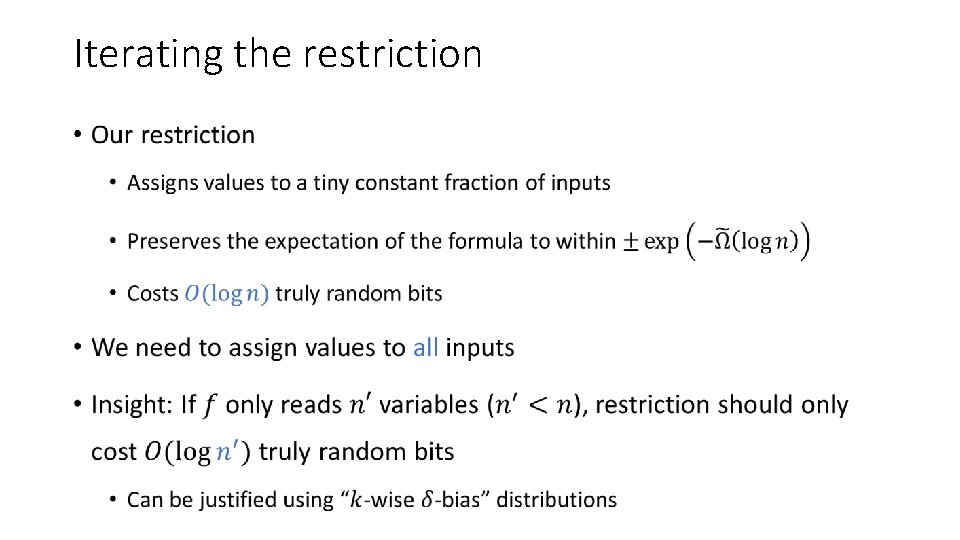
Iterating the restriction •

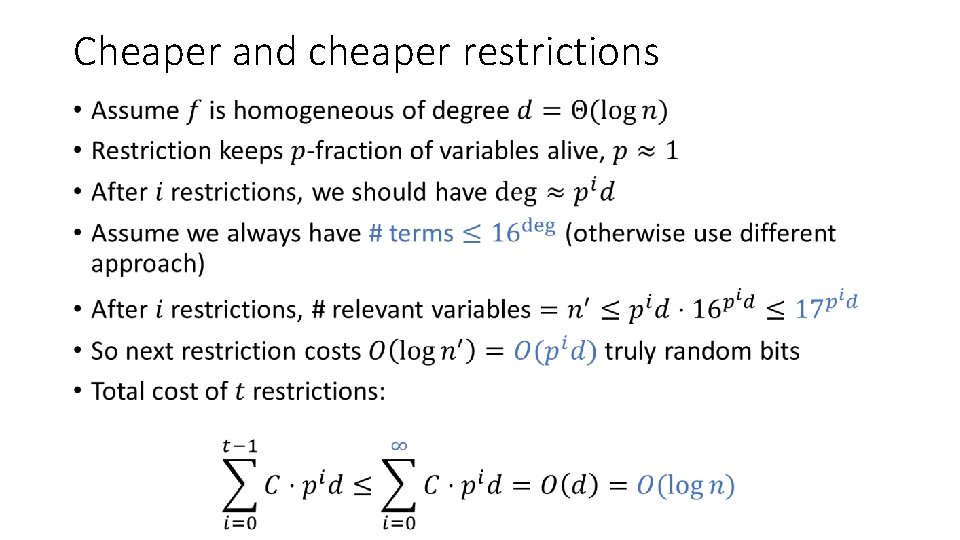
Cheaper and cheaper restrictions •

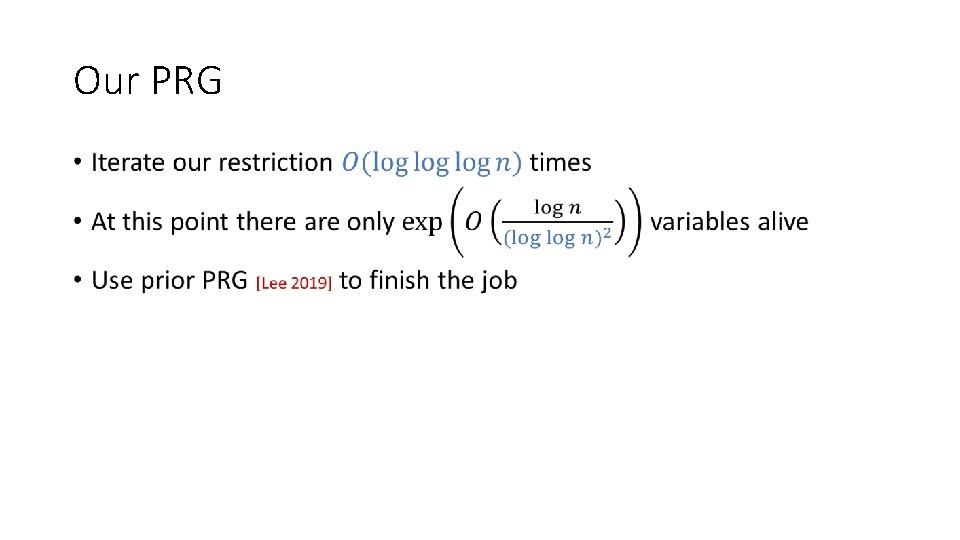
Our PRG •
![Conclusions References Ajtai Wigderson 1985 Deterministic simulation of probabilistic constant depth circuits Conclusions • References • [Ajtai, Wigderson 1985]: Deterministic simulation of probabilistic constant depth circuits.](https://slidetodoc.com/presentation_image_h2/51ae7e4c42e90bc386394b99bc08e7c2/image-24.jpg)
Conclusions • References • [Ajtai, Wigderson 1985]: Deterministic simulation of probabilistic constant depth circuits. In Advances in Computing Research, volume 5, issue 1, pages 199222, 1989. (Preliminary version in FOCS 1985) • [Chari, Rohatgi, Srinivasan 1994]: Improved algorithms via approximations of probability distributions. In JCSS, volume 61, issue 1, pages 81107, 2000. (Preliminary version in STOC 1994) • [De, Etesami, Trevisan, Tulsiani 2010]: Improved pseudorandom generators for depth 2 circuits. In APPROX/RANDOM 2010, pages 504 -517.