Lockheed Martin Cyber Security Ensuring Mission Integrity Assurance

Lockheed Martin Cyber Security Ensuring Mission Integrity, Assurance, & Resilience To Fight Through The Attack Craig Solem , CISSP Lockheed Martin Information Systems and Global Services Program Manager, Joint Medical information Systems for Naval Space and Warfare systems Center Atlantic January 8, 2010 INFORMATION SYSTEMS & GLOBAL SERVICES
Outline • • Who We Are Cyber Security Customers Cyber Tradeoff Model Characteristics of LM Solutions Security Approach Cyber Security Technology Center for Cyber Security Innovation INFORMATION SYSTEMS & GLOBAL SERVICES

Lockheed Martin Information Systems & Global Services • The leading provider of Information System Solutions and Services for the US Government for 14 years • Over $10 Billion in annual sales • 52, 000 Employees across every state and 50 countries • CMMI Level 5, ITIL v 2/3, ISO 27001 • 4, 000 Customer programs • 80 – 120 Vendors Evaluated Yearly INFORMATION SYSTEMS & GLOBAL SERVICES
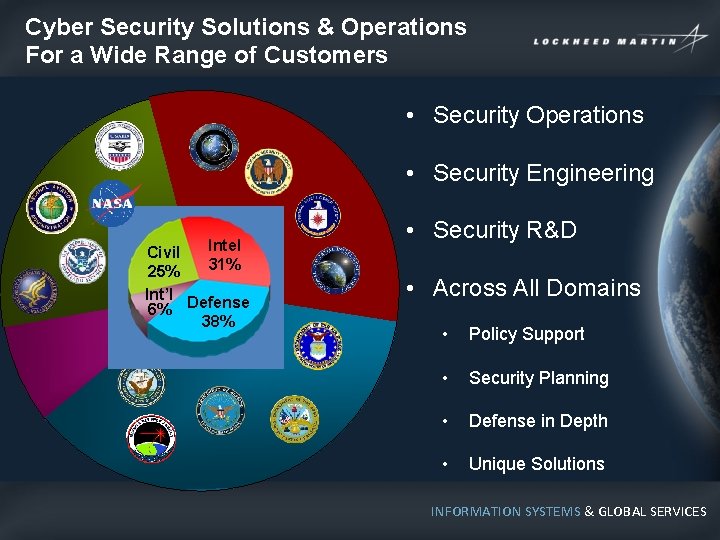
Cyber Security Solutions & Operations For a Wide Range of Customers • Security Operations • Security Engineering Intel 31% Civil 25% Int’l Defense 6% 38% • Security R&D • Across All Domains • Policy Support • Security Planning • Defense in Depth • Unique Solutions INFORMATION SYSTEMS & GLOBAL SERVICES
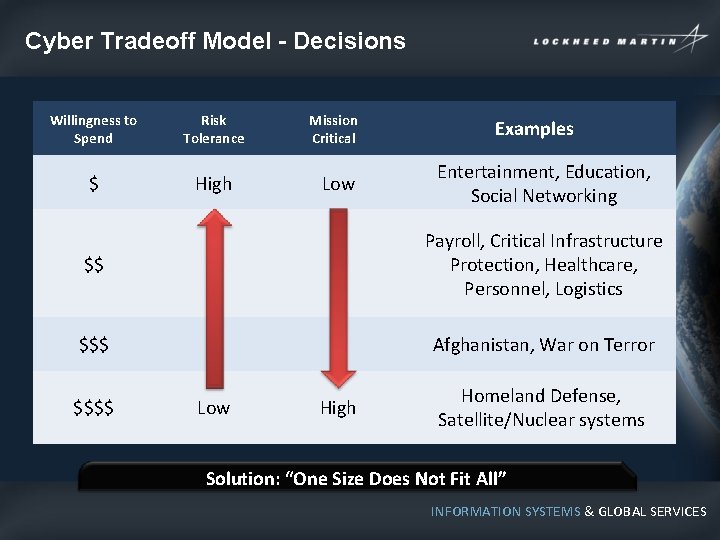
Cyber Tradeoff Model - Decisions Willingness to Spend Risk Tolerance $ High Mission Critical Low Examples Entertainment, Education, Social Networking $$ Payroll, Critical Infrastructure Protection, Healthcare, Personnel, Logistics $$$ Afghanistan, War on Terror $$$$ Low High Homeland Defense, Satellite/Nuclear systems Solution: “One Size Does Not Fit All” INFORMATION SYSTEMS & GLOBAL SERVICES
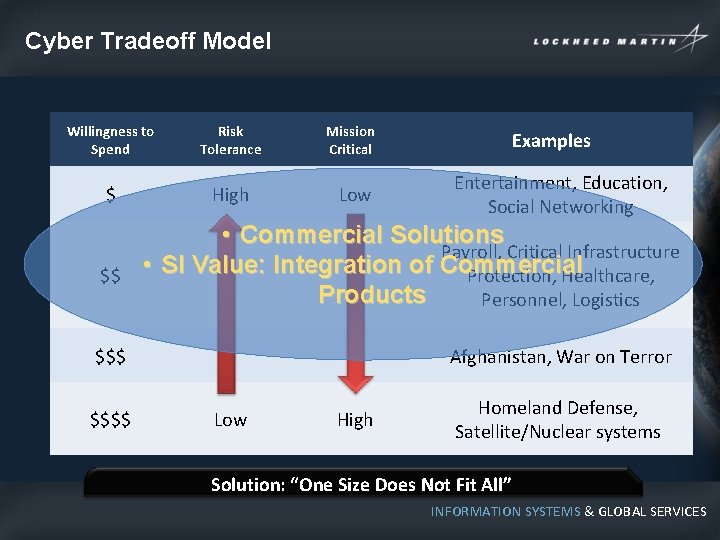
Cyber Tradeoff Model Willingness to Spend Risk Tolerance $ High $$ Mission Critical Low Entertainment, Education, Social Networking • Commercial Solutions Payroll, Critical Infrastructure • SI Value: Integration of Commercial Protection, Healthcare, Products Personnel, Logistics $$$$ Examples Afghanistan, War on Terror Low High Homeland Defense, Satellite/Nuclear systems Solution: “One Size Does Not Fit All” INFORMATION SYSTEMS & GLOBAL SERVICES
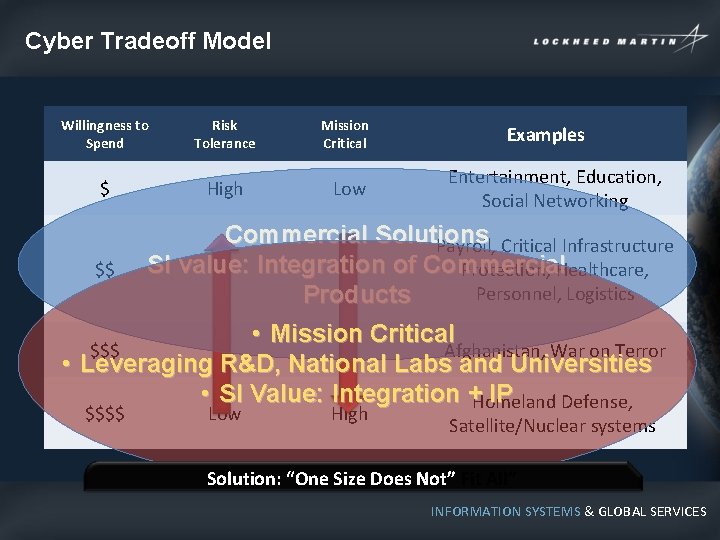
Cyber Tradeoff Model Willingness to Spend Risk Tolerance $ High $$ Mission Critical Low Examples Entertainment, Education, Social Networking Commercial Solutions Payroll, Critical Infrastructure SI value: Integration of Commercial Protection, Healthcare, Personnel, Logistics Products • Mission Critical $$$ Afghanistan, War on Terror • Leveraging R&D, National Labs and Universities • SI Value: Integration +Homeland IP Defense, $$$$ Low High Satellite/Nuclear systems Solution: “One Size Does Not” Fit All” INFORMATION SYSTEMS & GLOBAL SERVICES
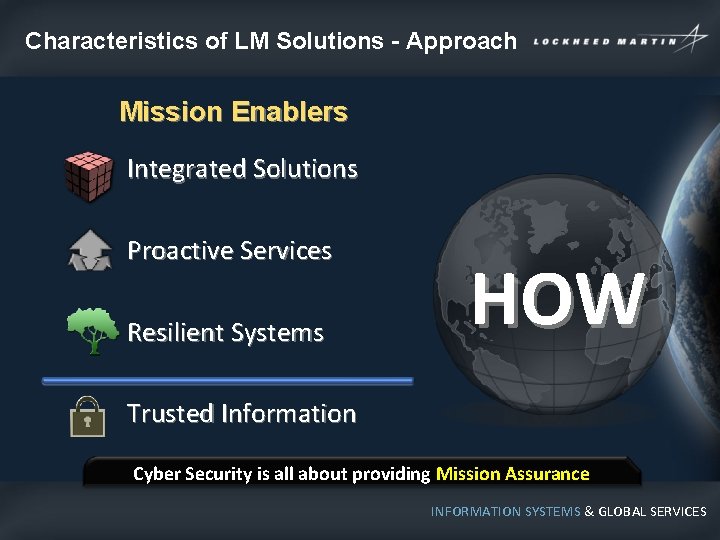
Characteristics of LM Solutions - Approach Mission Enablers Integrated Solutions Proactive Services Resilient Systems HOW Trusted Information Cyber Security is all about providing Mission Assurance INFORMATION SYSTEMS & GLOBAL SERVICES
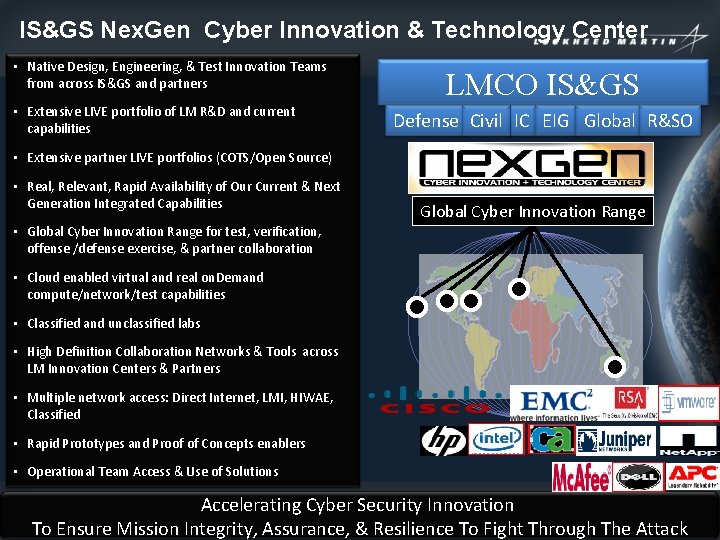
IS&GS Nex. Gen Cyber Innovation & Technology Center • Native Design, Engineering, & Test Innovation Teams from across IS&GS and partners • Extensive LIVE portfolio of LM R&D and current capabilities LMCO IS&GS Defense Civil IC EIG Global R&SO • Extensive partner LIVE portfolios (COTS/Open Source) • Real, Relevant, Rapid Availability of Our Current & Next Generation Integrated Capabilities Global Cyber Innovation Range • Global Cyber Innovation Range for test, verification, offense /defense exercise, & partner collaboration • Cloud enabled virtual and real on. Demand compute/network/test capabilities • Classified and unclassified labs • High Definition Collaboration Networks & Tools across LM Innovation Centers & Partners • Multiple network access: Direct Internet, LMI, HIWAE, Classified • Rapid Prototypes and Proof of Concepts enablers • Operational Team Access & Use of Solutions Accelerating Cyber Security Innovation INFORMATION SYSTEMS & GLOBAL SERVICES To Ensure Mission Integrity, Assurance, & Resilience To Fight Through The Attack
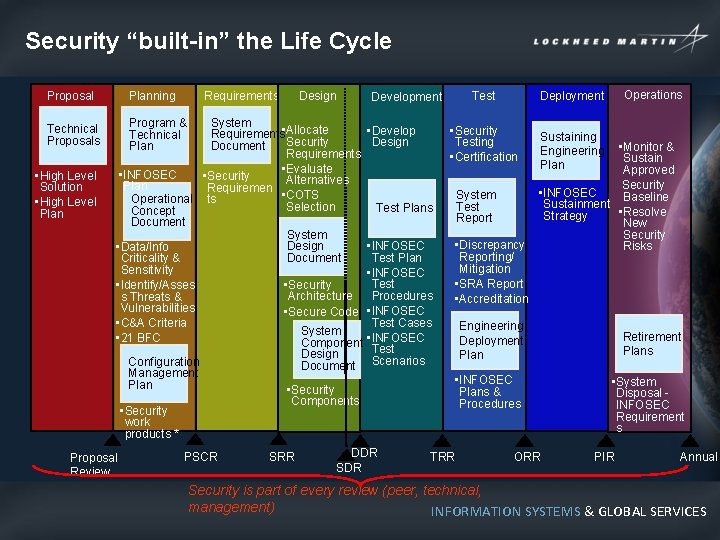
Security “built-in” the Life Cycle Proposal Technical Proposals • High Level Solution • High Level Planning Requirements Design System • Develop Requirements • Allocate Security Design Document Requirements • Evaluate • INFOSEC • Security Alternatives Plan Requiremen • COTS Operational ts Selection Test Plans Concept Document System Design • INFOSEC • Data/Info Document Test Plan Criticality & Sensitivity • INFOSEC Test • Security • Identify/Asses Procedures Architecture s Threats & Vulnerabilities • Secure Code • INFOSEC Test Cases • C&A Criteria System • 21 BFC Component • INFOSEC Test Design Configuration Document Scenarios Management Plan • Security Components • Security work products * Proposal Review Program & Technical Plan PSCR SRR DDR SDR Operations Deployment Test Development • Security Testing • Certification System Test Report • Discrepancy Reporting/ Mitigation • SRA Report • Accreditation Sustaining Engineering Plan • Monitor & Sustain Approved Security • INFOSEC Baseline Sustainment • Resolve Strategy New Security Risks Engineering Deployment Plan • INFOSEC Plans & Procedures TRR ORR Retirement Plans • System Disposal INFOSEC Requirement s PIR Annual Security is part of every review (peer, technical, management) INFORMATION SYSTEMS & GLOBAL SERVICES

INFORMATION SYSTEMS & GLOBAL SERVICES
- Slides: 11