Lockheed Martin Counterintelligence Insider Threat Detection Dulles ISAC

















- Slides: 21

Lockheed Martin Counterintelligence & Insider Threat Detection Dulles ISAC February 24, 2016 Douglas D. Thomas Director, Counterintelligence Operations & Corporate Investigations

Introduction & Background • Douglas D. Thomas – Director, Lockheed Martin Counterintelligence Operations & Corporate Investigations – Chair, Intelligence & National Security Alliance (INSA), Insider Threat Subcommittee – 33 Years With The Air Force Office Of Special Investigations (AFOSI); Retired As Executive Director – 2 Years As The Principle Deputy Director Of The National Counterintelligence Executive (NCIX) 2

Why Counterintelligence? 3

Thoughts to Consider. . . • National Security Is Executed/Funded By USG; Built By Industry • Government Should Have Some Assurances Products & Services Are Delivered Uncompromised • There Is NO Difference Between National Security And Economic Security • MUST Think Beyond Classified Programs And Cleared People • War Room Board Room • “Adversaries” In The Government Might Be “Business Partners” In Industry 4

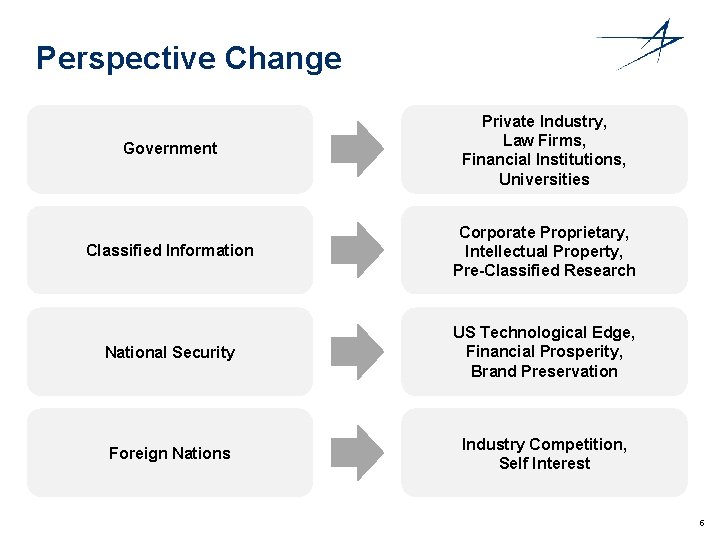
Perspective Change Government Private Industry, Law Firms, Financial Institutions, Universities Classified Information Corporate Proprietary, Intellectual Property, Pre-Classified Research National Security US Technological Edge, Financial Prosperity, Brand Preservation Foreign Nations Industry Competition, Self Interest 5

Trends • FBI Economic Espionage Caseload Increased 53% November 2014 November 2015 • Economic Espionage And Theft Of Trade Secrets Represent The Largest Growth Area Among The Traditional Espionage Cases Overseen By The FBI’s Counterespionage Section • Intelligence Information Reports (IIR) From Industry SCR Reporting; 660 In FY 2010 7, 292 In FY 2015 (+ 1, 005%) • Federal Investigations Or Operations From DSS Referrals; 202 In FY 2010 1, 020 In FY 2015 (+ 405%) • Narrowing Of Technology Gap Between The U. S. And Competing Nations 6

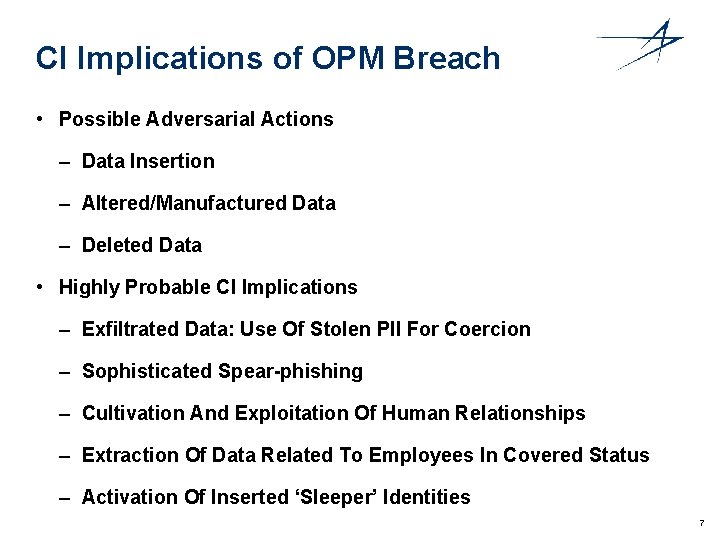
CI Implications of OPM Breach • Possible Adversarial Actions – Data Insertion – Altered/Manufactured Data – Deleted Data • Highly Probable CI Implications – Exfiltrated Data: Use Of Stolen PII For Coercion – Sophisticated Spear-phishing – Cultivation And Exploitation Of Human Relationships – Extraction Of Data Related To Employees In Covered Status – Activation Of Inserted ‘Sleeper’ Identities 7

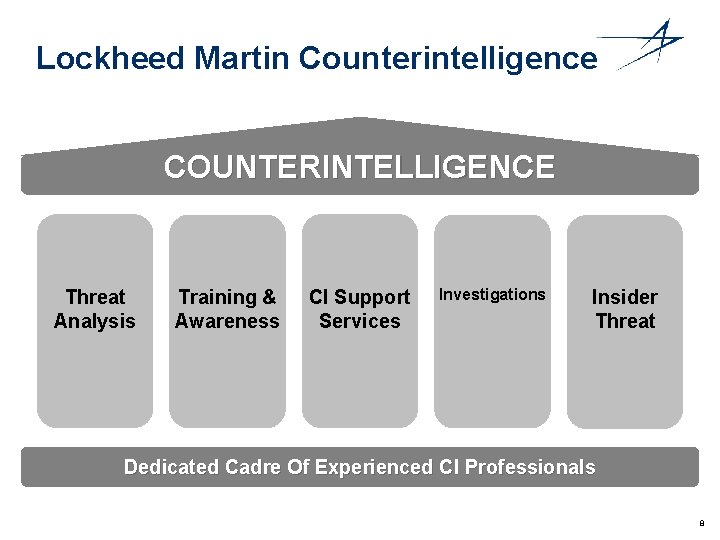
Lockheed Martin Counterintelligence COUNTERINTELLIGENCE Threat Analysis Training & Awareness CI Support Services Investigations Insider Threat Dedicated Cadre Of Experienced CI Professionals 8

Insider Threat Detection 9

Increase in Insider Threat • The Incidence Of Employee Financial Hardships During Economic Downturns • Employer Affordability Initiatives – Reduction Of Benefits And Pension Plans, Lay-offs, Etc. • The Global Economic Crisis – Foreign Nations More Eager To Acquire New Technologies, R&D – Mergers, Acquisitions, Divestitures, Joint Ventures • Ease Of Stealing Anything Stored Electronically • Increasing Exposure To Foreign Intelligence Entities (FIE) Presented By The Reality Of Global Business • Increase In FIE Recruitment Of Students • OPM Breach 10

LMCO Insider Threat Program Planning Development Implementation Steering Committee Selling Leadership • • Shifting Landscape Trends Cost Considerations Peer Benchmarking Tool Procurement / Development Challenges/Successes Population Size Privacy Considerations Program Governance Budget Live Analyst Support Data Ingestion And Tool Calibration Establish Potential Risk Indicators • Determine Appropriate Weights And Aging • Transparency In Objective • Reinforcement Of Leadership Support • Proper Vehicles For Voicing Concerns Identify Stakeholders • HR, Legal, Privacy, Information Security, Communications, Ethics • CONOPS • Codification Of Policy • Communications Plan • Security, Legal, HR, Ethics, Information Security • Receive Quarterly Briefings On Results • Manage Policy Updates Roll-out Message To Employees Peer Benchmarking • • • Governance Identification Of Required Data Sets • Agreements With Data Owners Incident Management • Conducting Inquires • Opening Investigations • Coordination With Law Enforcement Agencies Metrics • Tool Analysis • Employee Surveys Red Team Internal Audit Risk And Compliance Committee Board Of Directors 11

Privacy Considerations • Communications Plan To Properly Introduce Program To Employees • Ingestion Of Only Data Already Collected By Existing Corporate Initiatives • Proper Adoption Of Local Restrictions Applicable To Foreign And Expatriated Employees • Access To Automated Tool Heavily Restricted • “Red Team” Exercises To Ensure Highest Level Of System Defenses • Continual Coordination With Corporate Privacy General Counsel • Member Of CI Team Privacy Certified Through International Association Of Privacy Professionals (IAPP) – (In Progress) • No Profiling 12

Communications Strategy • Proper Introduction To Employees – IMPERATIVE! • Absolute Transparency In Purpose And Objective • Communication Of Adherence To Corporate Value Structure • Joint Strategy Development (HR, Communications, Public Relations) • Executive Review • Multi-pronged Approach • Deployment Of Various Modalities 13

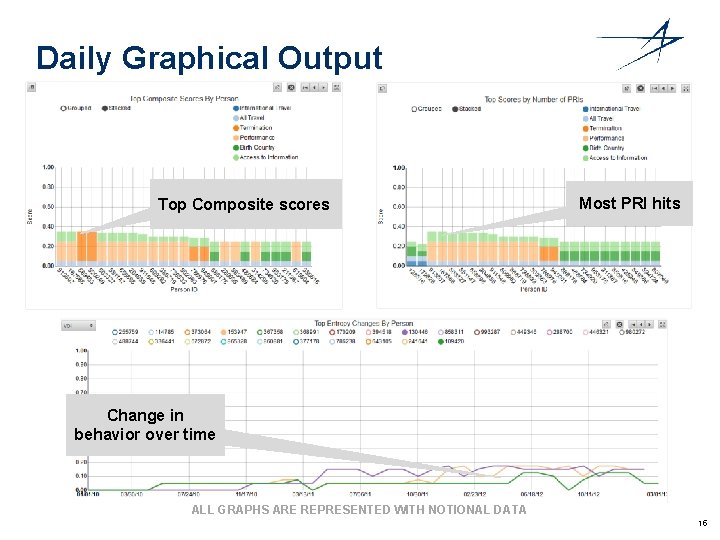
LM Wisdom ITI™ • Evaluation Of Employee Attributes, Behaviors And Actions According To Analyst-defined Models • Digital And Behavioral Baseline • Lead Generation And Triage From Three Graphical Outputs • Automated Link Analysis • Analyst Defined Categories And Attributes Of Interest • Categories And Attributes Are Assigned Weights • Models Run Against An Entire Population Or Subsets • Based On Big Data Technologies (Petabyte+) • Notifications And Alerts • Data Encryption 14

Daily Graphical Output Top Composite scores Most PRI hits Change in behavior over time ALL GRAPHS ARE REPRESENTED WITH NOTIONAL DATA 15

Intelligence Threats to Supply Chain 16

Intelligence Threats to Supply Chain • CI & Security Issue With National Attention – Director, NCIX, Dubbed 2013 “Year Of The Supply Chain” – National Counterintelligence Strategy Lists “Assure The Supply Chain” As One Of Four Strategic Objectives • Soft Underbelly Vulnerability • Applicable To Classified & Unclassified Technologies • Very Difficult To Detect • Vulnerabilities Exist At All Stages Of The Process • Vendors Are Likely The Softest Target For Exploitation • Decision Makers Often Focused Solely On Cost & Schedule 17

Implications of Compromise • Theft Of Lockheed Martin Technology • Counterfeiting – Potential For Sub-par Components And Lawsuits • Sabotage – Potential To Insert Components Which May Be Designed To Fail Or Malfunction Immediately Or At Some Point In The Future • Acquisition Of Program/System Intelligence – Sensitive Program Information Could Potentially Yield Engineering Of Defense & Weaponry Countermeasures – System Limitation Information Could Allow For Engineering Of Offensive Measures • Severe Damage To Reputation 18

Mitigation Recommendations • KNOW Your Supply Chain! • Thoroughly And Continuously Vet Your Vendors • Stay Apprised Of Vendor Ownership Changes • Practice “Need To Know” With Vendors • Use Trusted US Manufacturers, Builders & Installers Where Possible • Consistently Use Anti-tamper & Tracking Technology • Educate Your Workforce & Vendors On The Importance Of Reporting Suspicious Anomalies • Know Who’s Touching Your Materials/Shipments • Periodically Change Procedures • Investigate Suspicious Anomalies • Limit Access To Critical Systems • Educate Yourself On How Vendors Protect Your Data On Their Networks 19

Questions? 20
