Local Area Networks CSH 6 Chapter 25 Local
































- Slides: 38

Local Area Networks CSH 6 Chapter 25 “Local Area Networks” Gary C. Kessler & N. Todd Pritsky 1 Copyright © 2020 M. E. Kabay. All rights reserved.

Topics ØPolicy and Procedures ØPhysical Site Security ØPhysical Layer ØNetwork Operating System Issues Chapter 25 should be read in conjunction with Chapter 24 on Operating System Security. Chapter 25 includes commentary on operating systems commonly used on workstations configured on LANs. 2 Copyright © 2020 M. E. Kabay. All rights reserved.

Policy and Procedures Ø Without framework of policy and procedures, technology cannot be selected appropriately Ø Extensive list of suggestions available in many texts and online q. Many chapters in CSH 6 q. RFC 2196: Site Security Handbook http: //www. ietf. org/rfc 2196. txt 3 Copyright © 2020 M. E. Kabay. All rights reserved.

Physical Site Security Ø Physical access to LAN equipment is the single most dangerous vector for attack Ø Protect equipment and transmission media against physical damage q. Accident See CSH 6 q. Intentional attack Chapters 22 and 23 q. Denial of service Ø Business continuity planning & disaster recovery planning q. Require consideration of networks See CSH 6 Chapters 58 and 59 4 Copyright © 2020 M. E. Kabay. All rights reserved.

Physical Layer Issues ØISO OSI Model ØSniffers and Broadcast LANs ØAttacks on the Physical Plant ØModems, Dial-Up Servers, Telco ØWireless LANs 5 Copyright © 2020 M. E. Kabay. All rights reserved.

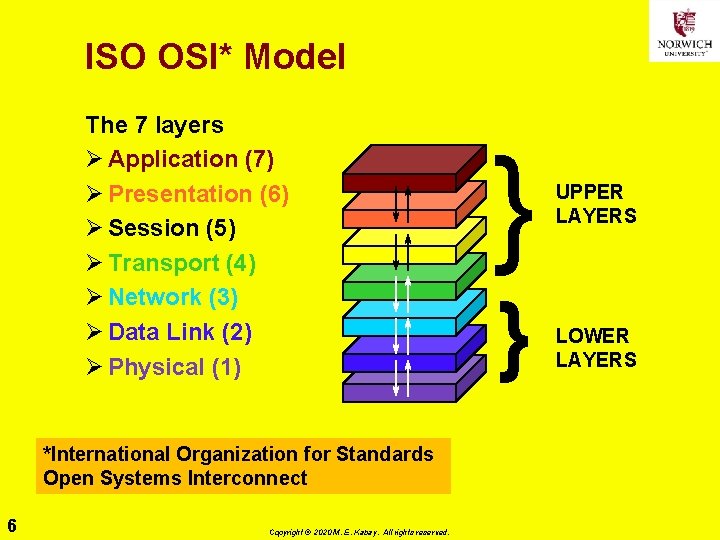
ISO OSI* Model The 7 layers Ø Application (7) Ø Presentation (6) Ø Session (5) Ø Transport (4) Ø Network (3) Ø Data Link (2) Ø Physical (1) *International Organization for Standards Open Systems Interconnect 6 Copyright © 2020 M. E. Kabay. All rights reserved. } } UPPER LAYERS LOWER LAYERS

OSI Data Transfer INPUT OUTPUT 7 Copyright © 2020 M. E. Kabay. All rights reserved.

IBM's TCP/IP Redbook http: //www. redbooks. ibm. com/pubs/pdfs/redbooks/gg 243 376. pdf Part I. Core TCP/IP protocols Ø Chapter 1. Architecture, history, standards, and trends Ø Chapter 2. Network interfaces Ø Chapter 3. Internetworking protocols Ø Chapter 4. Routing protocols Ø Chapter 5. Transport layer protocols Ø Chapter 6. IP multicast Part 2. TCP/IP application protocols Ø Chapter 7. Application structure and programming interfaces Ø Chapter 8. Directory and naming protocols Ø Chapter 9. Remote execution and distributed computing Ø Chapter 10. File related protocols 8 Ø Ø Chapter 11. Mail applications Chapter 12. The World Wide Web Chapter 13. Multimedia protocols Chapter 14. Wireless Application Protocol (WAP) Ø Chapter 15. Network management Ø Chapter 16. Utilities Part 3. Advanced concepts and new technologies Ø Chapter 17. IP Version 6 Ø Chapter 18. Multiprotocol Label Switching (MPLS) Ø Chapter 19. Mobile IP Ø Chapter 20. Integrating other protocols with TCP/IP Ø Chapter 21. TCP/IP security Ø Chapter 22. Quality of Service Ø Chapter 23. Availability, scalability, and load balancing Copyright © 2020 M. E. Kabay. All rights reserved.

Sniffers and Broadcast LANs 9 Ø Most LANs use broadcast packets / frames Ø Normally nodes read only designated packets / frames by destination address Ø Nodes in promiscuous mode read all frames Ø Sniffers capture and analyze all packets q. Older models were hardware – obvious q. Software sniffers practically invisible on network Ø Countermeasures q. Cryptography the most obvious: IPSec, SSH q. Can put servers on switches to avoid broadcasts q. Special software can test timing of networks to detect sniffers Copyright © 2020 M. E. Kabay. All rights reserved.

TCP/IP Sniffers Ø BUTTsniffer (Windows NT) Ø Ethereal (Windows, Unix) Ø Network Monitor (free with, and for, Windows NT) Ø Sniffit (Linux, Sun. OS, Solaris, Free. BSD, Irix) Ø snort (Unix) Ø Solsniff (Solaris) Ø tcpdump (Unix) Ø Win. Dump (Windows 9 x/NT) Image used with kind permission of IXXAT, Inc. http: //www. ixxat. com/introduction_tcp_ip_en. html 10 Copyright © 2020 M. E. Kabay. All rights reserved.

Sniffer Detectors: Anti. Sniff® Ø L 0 pht Heavy Industries – hackers Ø Released Anti. Sniff in 1999 q. Notes below from Nomad review at http: //www. nmrc. org/pub/review/antisniffb 2. html Ø Pro q. Accurate detection of promiscuous mode Ethernet cards q. Alerts sent via email – also includes visual and audio alerts q. Anti. Sniff sessions can be stored for later use/analysis 11 Copyright © 2020 M. E. Kabay. All rights reserved.

Limitations of Anti. Sniff® Comments from Nomad: Ø NT version runs at high priority and is resource-intensive – need dedicated machine Ø Can only work properly checking Ethernet cards on the same segment as the system running Anti. Sniff q. Again, this is not a flaw, but due to the nature of networking in general. q. It will work in a switched environment with a smart hub Ø No SNMP support 12 Copyright © 2020 M. E. Kabay. All rights reserved.

Attacks on the Physical Plant Ø Wiretapping cables (use shielding, testing) Ø Van Eck phreaking (use TEMPEST standard for shielding or obfuscation) Ø Removal of end-of-cable resistors (causes noise and Do. S) Ø Twisted-pair LANs (10 Base. T Ethernet) susceptible to tapping at punch-down junction boxes Ø Generally protect cabling against tampering Ø Protect servers against unauthorized physical access 13 Copyright © 2020 M. E. Kabay. All rights reserved.

Modems, Dial-Up Servers, Telco Ø Modems can bypass perimeter protection q. May be installed without authorization q. Users often have modems on laptops linked into network q. Bypass firewalls etc. q. Allow easy outbound a ccess Ø Auto-answer modems allow inbound access across firewalls 300 baud modem c. 1980 Ø Dial-up servers allow centralized control of modem communications Ø Modems becoming less important today because of high-speed Internet connectivity 14 Copyright © 2020 M. E. Kabay. All rights reserved.

Wireless LANs Ø Overview of Wireless LANs Ø Wired Equivalent Privacy (WEP) Ø Web for Authentication 15 Copyright © 2020 M. E. Kabay. All rights reserved.

Overview of Wireless LANs Ø Data carried on radio-frequency radiation more easily intercepted than data on physical wires q. Typical range measured in meters or more q. Infrared transmission doesn’t go through walls Ø IEEE 802. 11 Standards for Wireless Networking q. Direct-Sequence Spread Spectrum (DSSS) q. Frequency-Hopping Spread Spectrum See CSH 6 Chapter 5 (FHSS) q. Without codes/patterns, seems like noise to eavesdropper 16 Copyright © 2020 M. E. Kabay. All rights reserved.

Wired Equivalent Privacy Ø Optional encryption q 40 -bit RC 4 by default (inadequate today) q 128 -bit version available for some products Ø Vendors have defined additional encryption similar to virtual private networks (VPNs) q Use public key cryptography (PKC) & support public key infrastructure (PKI) q E. g. , MS Point-to-Point Encryption used in Point-to-Point Tunneling Protocol (PPTP) Ø Some provide authentication q E. g. , RADIUS (Remote Access Dial-In User Service) q Not generally interoperable 17 Copyright © 2020 M. E. Kabay. All rights reserved.

WEP for Authentication Ø Adds extra layer to user. ID/password normally used Ø Wireless device must have same encryption key as LAN’s access point Ø Wireless access points (WAPs) usually also able to q. Define access control lists (ACLs) based on q. Media access control (MAC) addresses 18 Copyright © 2020 M. E. Kabay. All rights reserved.

Network Operating System Issues ØOverview of Network OS Topics ØWindows 9 x ØNT/2000, XP, Vista, 7 ØUNIX ØMac. OS 19 Copyright © 2020 M. E. Kabay. All rights reserved.

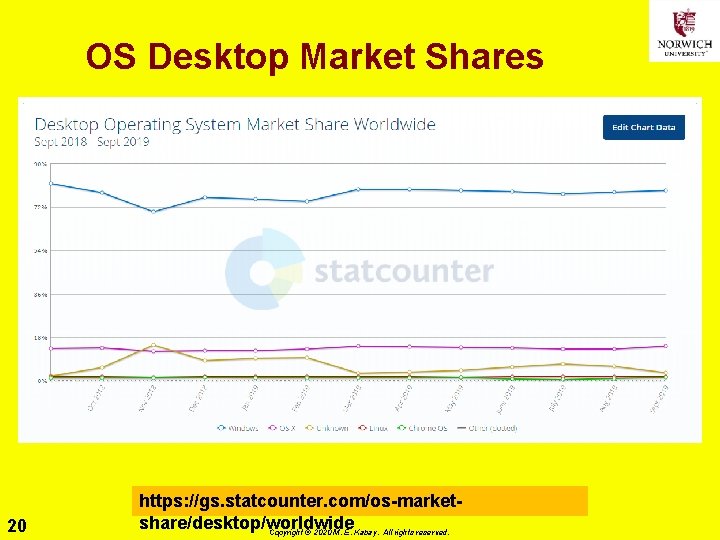
OS Desktop Market Shares 20 https: //gs. statcounter. com/os-marketshare/desktop/worldwide Copyright © 2020 M. E. Kabay. All rights reserved.

OS Mobile Device Market Shares https: //gs. statcounter. com/os-market -share 21 Copyright © 2020 M. E. Kabay. All rights reserved.

Overview of Network OS Topics Ø LAN environment has changed since 1990 s q. At that time, desktops ran applications under Windows q. Network ran Novell Netware for file sharing Ø By late 2000 s, networking commonplace for all desktop OSs (Windows, *nix, Mac. OS…) 22 Copyright © 2020 M. E. Kabay. All rights reserved.

General Considerations for NW Security (1) 1. 2. 3. 4. 5. 6. 7. 8. 9. 23 Strong passwords & effective password policies Disable/uninstall unused services I Keep OS up to date by version & patches II Define users, groups, domain trust III relations IV Secure running applications V Limit use of root logon to need – and local only. VI VII Limit guest, demo, anonymous accounts VIII Put boot/system files on separate IX partitions, drives, I/O controllers from application programs and data Audit servers Copyright © 2020 M. E. Kabay. All rights reserved.

General Considerations for NW Security (2) 10. Monitor log files 11. Remove floppy, CD, DVD drives from servers after use 12. Implement industry best practices for securing OS 13. Use vulnerability assessment tools regularly 14. Use intrusion detection tools 15. When using SNMP, block external access to SNMP 16. Don’t make your OS version & processor type public info 24 Copyright © 2020 M. E. Kabay. All rights reserved. X XI XIII XIV XV XVI

Windows 9 x Ø Windows OSs susceptible to q Exploitation of NETBIOS file & print sharing q Abuse of resource sharing through TCP/IP when network has Internet access Ø Windows challenge-handshake authentication protocol (CHAP) q Used for sending passwords q But same challenge used for 15 minutes q Thus possible capture/replay by intruder with physical access & sniffer Ø Back. Orifice & Net. Bus: remote-control tools Ø Password crackers can break. PWL password files Ø PW-protected screensaver? Reboot! Ø Use 3 rd party secure bootlocks 25 Copyright © 2020 M. E. Kabay. All rights reserved.

NT/2000 Ø Windows 2000 Millennium Edition has same weaknesses as 9 x Ø Stronger: q. Windows NT Server q. NT Workstation q 2000 Server Ø Many hacking tools available for these versions as well Ø Vulnerabilities in Internet Explorer (IE) & Office products weaken OS Ø Ideally, disable all Active Scripting and Active. X options in Restricted Sites Zone of IE 26 Copyright © 2020 M. E. Kabay. All rights reserved.

NT/2000 (2) Ø NT/2000: Simple recommendations for basic security q Format drives using NTFS, not FAT q Use long file names & disable DOS 8. 3 naming q Disable Everyone group q Rename administrator account q Turn auditing on (off by default) Ø W 2 K: Enable Encrypting File System (EFS) q Automatic encryption of disk data q Should enable recovery of keys 27 Copyright © 2020 M. E. Kabay. All rights reserved.

Windows NT Audit Tools (1) Ø netstat examines open ports Ø Event Viewer examines application, security, and system logs. Ø net start, net user, net group, net local group display running services, users, groups, and local groups Ø dumpel converts Event Viewer logs to ASCII files Ø Net. Mon displays network traffic Ø netsvc displays local and remote running services and drivers Ø addusers displays users and groups Ø findgrp displays local and domain groups for a user 28 Copyright © 2020 M. E. Kabay. All rights reserved.

Windows NT Audit Tools (2) Ø local and global show all members of specific local or global groups Ø dommon displays trusted domains Ø xcacls examines the file Access Control Lists (ACL) Ø perms examines the ACLs associated with a user Ø sysdiff displays changes in the Registry and file system Ø regdmp creates an ASCII version of the Registry Ø ralists a domain's Remote Access Servers (RAS) Ø rasusers lists users authorized for dial-in access 29 Copyright © 2020 M. E. Kabay. All rights reserved.

Windows XP: Better Security Ø EFS, firewall, Data Execution Prevention Ø But original release included raw sockets q Permits program to manipulate TCP/IP communications directly q Without use of normal application program interfaces (APIs) that apply security Steve Gibson http: //www. grc. com q Allowed external control q Steve Gibson warned (2001) of serious risk from script kiddies for denial of service applications q See http: //www. informit. com/articles/article. aspx? p=272 89 Ø MS removed raw sockets in Service Pack 2 (SP 2) 30 Copyright © 2020 M. E. Kabay. All rights reserved.

Vista: Child of Trustworthy Computing Initiative Ø Vista released Jan 2007; but by end of July 2009, q 22% market share (360 M users) q 70% market share for Windows XP (1. 1 B users) Ø Major security change is User Account Control (UAC) Ø Requires user response to allow action requiring admin privileges q Run as admin q Changing files in root and program files folders q [Un]Installing apps, drivers, Active. X q Changing settings for Firewall, UAC, Update, user accounts, Parental Controls, Task Scheduler q Restoring system files from backups q Viewing or changing other user’s data 31 Copyright © 2020 M. E. Kabay. All rights reserved.

Vista: Stepchild of the NSA? !? Ø Alec Klein & Ellen Nakashima q Washington Post (January 9, 2007) q NSA “participated” in creation of Vista security elements Ø Unclear extent of involvement Ø NSA acknowledged helping to protect OS against “worms, Trojan horses and other insidious computer attackers…. ” Ø Microsoft made NSA involvement public Ø Authors Kessler & Pritsky comment, “It is left as an exercise for the reader to decide whether having a spy agency working on a premier OS is a good thing or not. ” Ø What do you think? 32 Copyright © 2020 M. E. Kabay. All rights reserved.

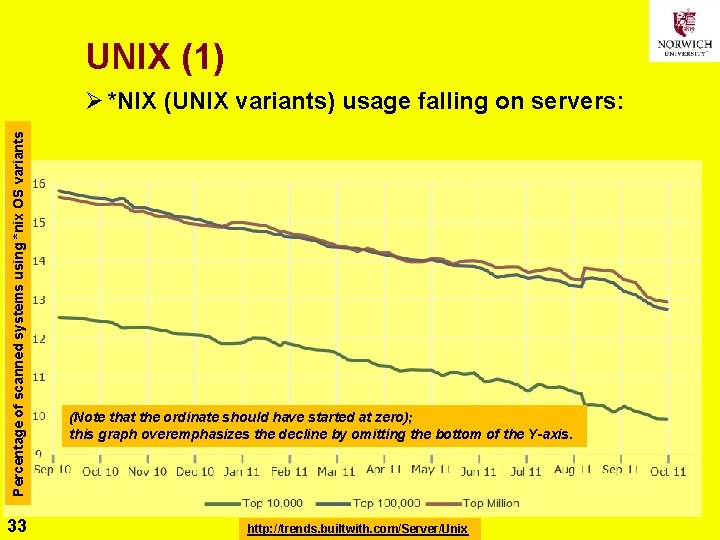
UNIX (1) Percentage of scanned systems using *nix OS variants Ø *NIX (UNIX variants) usage falling on servers: 33 (Note that the ordinate should have started at zero); this graph overemphasizes the decline by omitting the bottom of the Y-axis. http: //trends. builtwith. com/Server/Unix Copyright © 2020 M. E. Kabay. All rights reserved.

UNIX (2) Ø UNIX security architecture q. Developed originally for use in trusted community – security not paramount q. Usual list of normal security functions q. Enormous list of services Ø Extensive literature on *NIX security Ø Apply proper security audits, vulnerability assessment to *NIX systems 34 Copyright © 2020 M. E. Kabay. All rights reserved.

Mac. OS (1) Ø Mac OS originally designed with little concern for security Ø Every user is admin Ø Sharing capabilities more complex than on Windows q. Therefore more risk of naïve user error Ø Little user-level protection q. No default requirement for password at logon q. No standard password-equipped screen saver 35 Copyright © 2020 M. E. Kabay. All rights reserved.

Mac. OS (2) Ø Malware attacks fewer q. But MS Office malware works q. Do. S attacks work q. Use anti-malware package! Ø Other tools q. Disk. Locker: passwordprotection of entire HD q. File. Lock: locks on individual files q. Empower: applications & files q. Mac. Password, Sesame: multilevel passwords 36 Copyright © 2020 M. E. Kabay. All rights reserved.

Mac. OS (3) Ø Mac-oriented security tools for networking include q Intermapper: SNMP tool for Apple. Talk & IP q Mac. Radius: RADIUS for dial-in servers q Net. Lock: encryption for sessions, passwords, logins q Network Security Guard: vulnerability scanner Ø Update versions and apply patches promptly Ø Criminal hackers still not as frequently attacking Macs q Fewer targets, less familiarity 37 Copyright © 2020 M. E. Kabay. All rights reserved.

Now go and study 38 Copyright © 2020 M. E. Kabay. All rights reserved.