Linux Operations and Administration Chapter Seven Managing Users














- Slides: 44

Linux Operations and Administration Chapter Seven Managing Users and Groups

Objectives • Identify key user account information in the /etc/passwd and /etc/shadow configuration files • Describe the default user and group information in the /etc/login. defs and /etc/default/useradd configuration files • Create and modify user accounts at the command line • Create and modify groups at the command line • Manage user and group accounts with the Ya. ST utility Linux Operations and Administration 2

Managing Users • Authentication – Process of verifying someone’s identity by checking his or her username and password against a central user database • Linux user database consists of two configuration files: – /etc/passwd – /etc/shadow Linux Operations and Administration 3

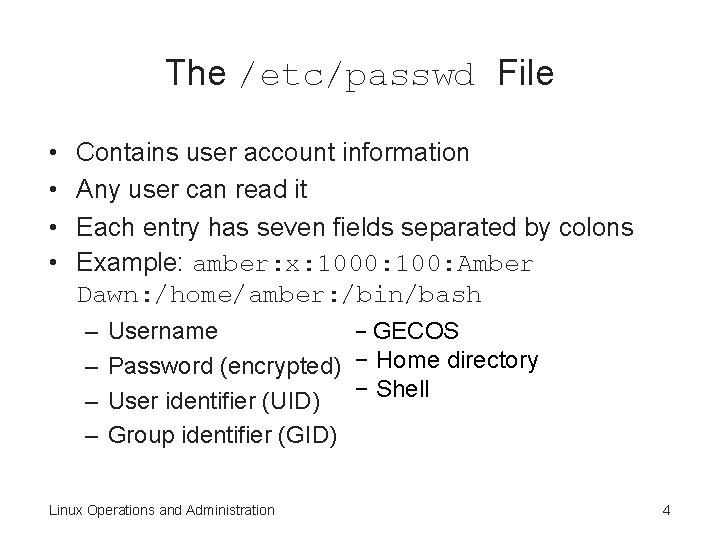
The /etc/passwd File • • Contains user account information Any user can read it Each entry has seven fields separated by colons Example: amber: x: 1000: 100: Amber Dawn: /home/amber: /bin/bash – – − GECOS Username Password (encrypted) − Home directory − Shell User identifier (UID) Group identifier (GID) Linux Operations and Administration 4

The /etc/shadow File • Configuration file containing passwords and password expiration information – For all user accounts • Can be read only by the root user • Example: chloe: $2 a$05$wa 7 x. VOq. OH 4 l. VOrh. qa 9 iv. SX 0 G 0 QUCFqbkll. YV 6: 14743: 0: 99999: 7: : : Linux Operations and Administration 5

The /etc/shadow File (cont’d. ) • Explanation of fields: – Username – Encrypted password – Last password change—number of days since January 1, 1970 that the password was last changed – Minimum—number of days before the password can be changed – Expiration—number of days before the password must be changed Linux Operations and Administration 6

The /etc/shadow File (cont’d. ) – Warning—number of days remaining until the password must be changed – Disabled—number of days after a password has expired until the user account is disabled – Disabled date—number of days since January 1, 1970 that the account has been disabled – Reserved Linux Operations and Administration 7

User Account Information • User information stored in two configuration files: – /etc/default/useradd – /etc/login. defs • Files contain: – – User’s PATH variable Password expiration information Default primary group Location of the home directory Linux Operations and Administration 8

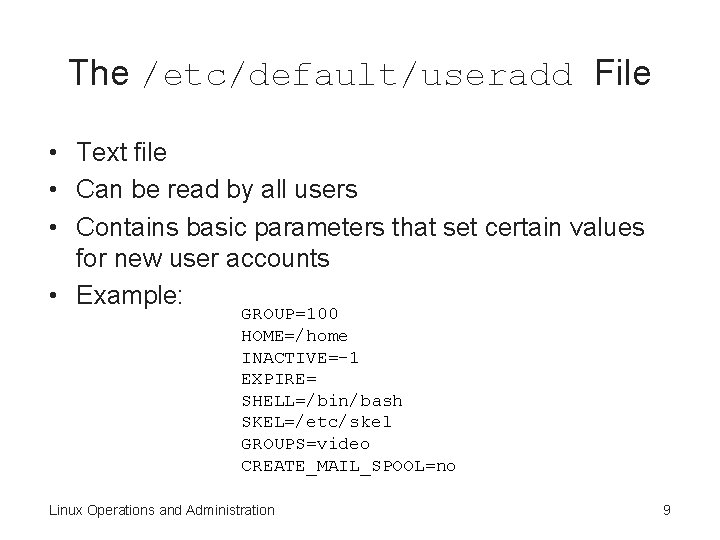
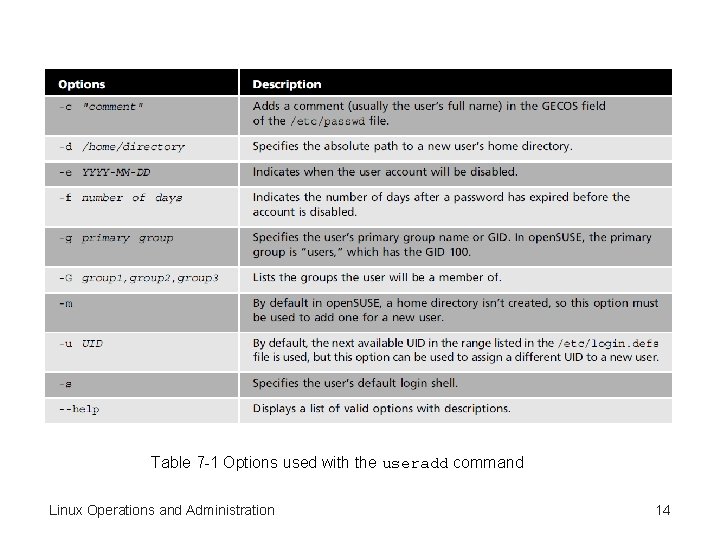
The /etc/default/useradd File • Text file • Can be read by all users • Contains basic parameters that set certain values for new user accounts • Example: GROUP=100 HOME=/home INACTIVE=-1 EXPIRE= SHELL=/bin/bash SKEL=/etc/skel GROUPS=video CREATE_MAIL_SPOOL=no Linux Operations and Administration 9

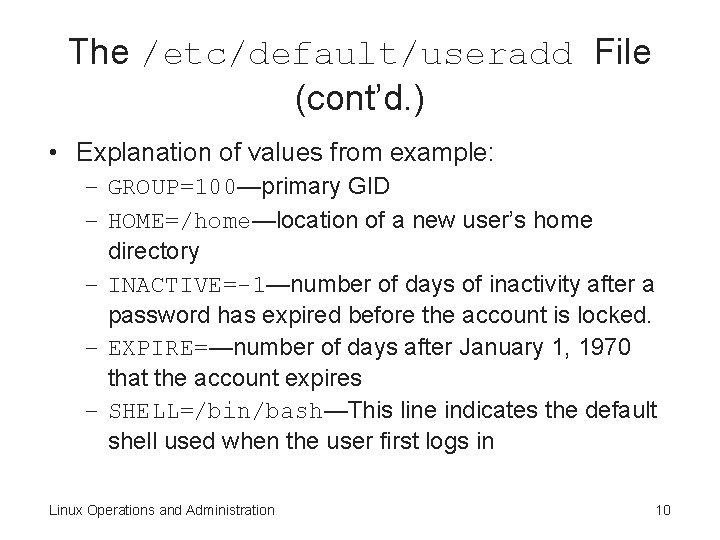
The /etc/default/useradd File (cont’d. ) • Explanation of values from example: – GROUP=100—primary GID – HOME=/home—location of a new user’s home directory – INACTIVE=-1—number of days of inactivity after a password has expired before the account is locked. – EXPIRE=—number of days after January 1, 1970 that the account expires – SHELL=/bin/bash—This line indicates the default shell used when the user first logs in Linux Operations and Administration 10

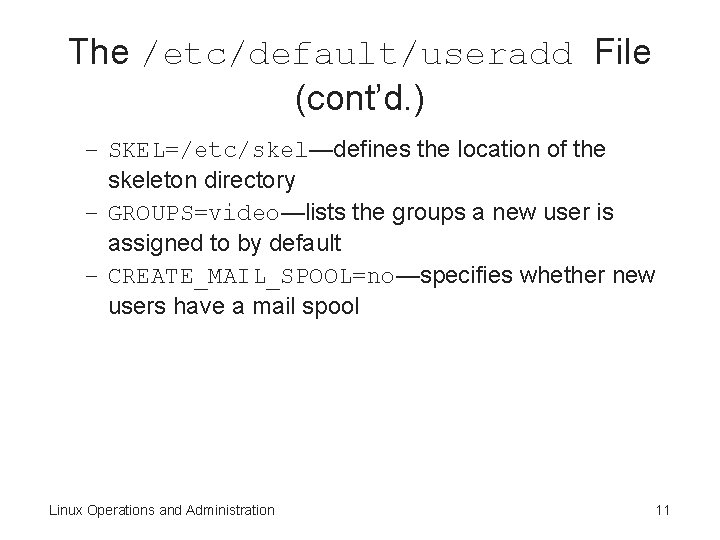
The /etc/default/useradd File (cont’d. ) – SKEL=/etc/skel—defines the location of the skeleton directory – GROUPS=video—lists the groups a new user is assigned to by default – CREATE_MAIL_SPOOL=no—specifies whether new users have a mail spool Linux Operations and Administration 11

The /etc/login. defs File • Text file • Can be read by all users • Contains parameters that set certain values for new user accounts: – Default PATH settings – Maximum and minimum number of days between password changes – Range of UIDs and GIDs that can be allocated to user and group accounts Linux Operations and Administration 12

Creating User Accounts • useradd command – Create user accounts – Update default information for new users • Table 7 -1 – Options for useradd Linux Operations and Administration 13

Table 7 -1 Options used with the useradd command Linux Operations and Administration 14

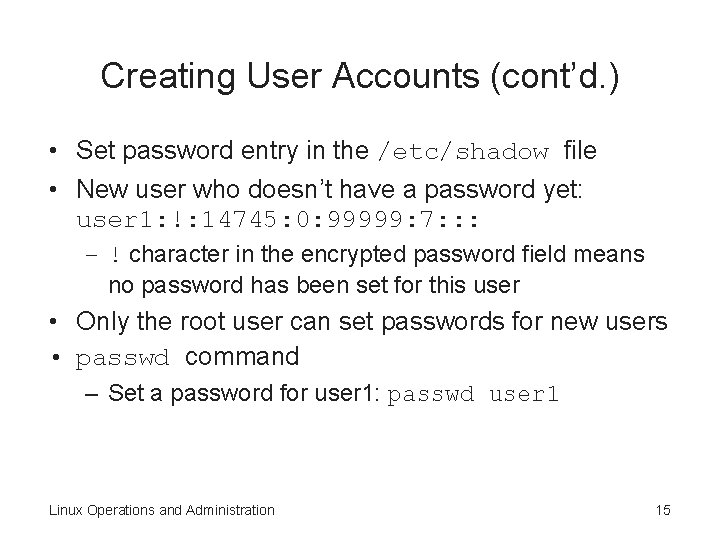
Creating User Accounts (cont’d. ) • Set password entry in the /etc/shadow file • New user who doesn’t have a password yet: user 1: !: 14745: 0: 99999: 7: : : – ! character in the encrypted password field means no password has been set for this user • Only the root user can set passwords for new users • passwd command – Set a password for user 1: passwd user 1 Linux Operations and Administration 15

Creating User Accounts (cont’d. ) • passwd command – Enter a new password and then enter it again to confirm • After the password has been set: user 1: $2 a$10$79 rygmrg 39 tt. n. PM 5 ls. Lh. w. ZWEJK 3 a. YWqaq. G 6 p 6 l. LNKYp. FMMHNG. O: 14745: 0: 99999: 7: : : • Activity 7 -1: Creating Users – Create users with the useradd command user database files Linux Operations and Administration 16

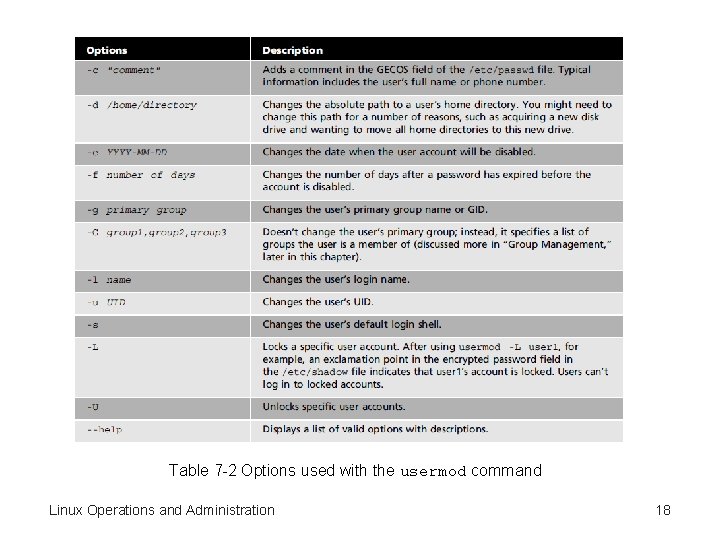
Modifying User Accounts • usermod command – Change user account information – Only the root user can issue this command • For a currently logged in user, cannot change: – Name – UID – Home directory • Table 7 -2 – Common options used with the usermod command Linux Operations and Administration 17

Table 7 -2 Options used with the usermod command Linux Operations and Administration 18

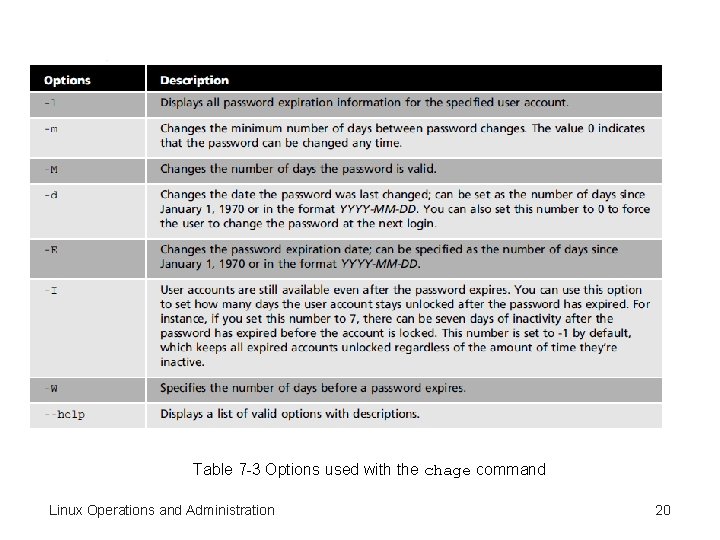
Modifying User Accounts (cont’d. ) • chage command – Only root user can issue – Modify information • Number of days between allowed and required password changes • Expiration date • Warning information • Table 7 -3 – Options used with chage command Linux Operations and Administration 19

Table 7 -3 Options used with the chage command Linux Operations and Administration 20

Modifying User Accounts (cont’d. ) • chage command used without options – Interactive mode chage elijah Changing aging information for elijah. Minimum Password Age [0]: • Activity 7 -2: Modifying User Accounts – Modify user accounts with the usermod and chage commands Linux Operations and Administration 21

Deleting User Accounts • userdel command – Delete user accounts – Remove all entries from user database files – Doesn’t remove the user’s home directory • -r option – Remove user’s home directory • When a user is deleted – All files he or she owned are then owned by the UID – If new user created with same UID, new user owns files Linux Operations and Administration 22

Managing Groups • Groups – Helpful for streamlining the process of designating which users can perform certain tasks • Every user is a member of at least one group – Called the primary group • Root user can assign an unlimited number of additional groups – Called secondary groups • /etc/group – Group database configuration file Linux Operations and Administration 23

Managing Groups (cont’d. ) • id command – View all the groups you belong to and their corresponding GIDs • Example results: id uid=1000(isaiah) gid=100(users) groups=33(video), 1000(ftp) – Users is the primary group – All other groups are secondary groups and are separated by commas Linux Operations and Administration 24

The /etc/group File • Configuration file that stores group information • Can be read by everyone on the system • Example: video: x: 33: dustin, student 1 – – Group name Password Group identifier (GID) List of members Linux Operations and Administration 25

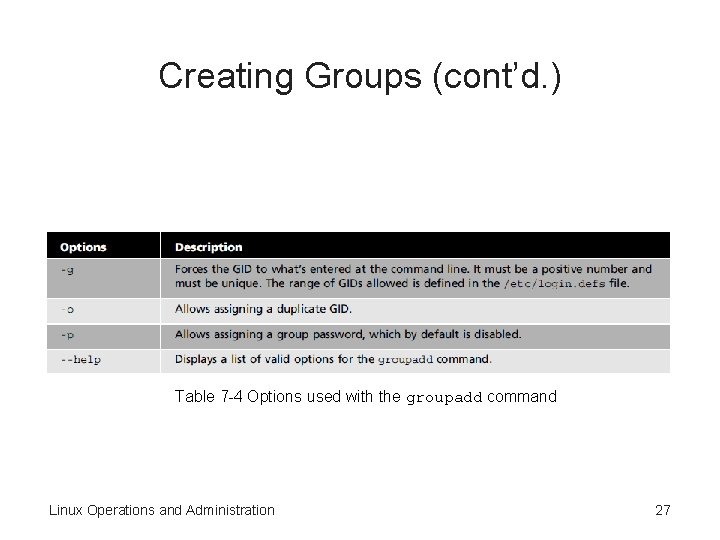
Creating Groups • groupadd command – Add a group account – Only the root user has permission to use this command • Table 7 -4 – Options for groupadd command • newgrp command – Change a user’s primary group temporarily – Stays in effect until the user logs out Linux Operations and Administration 26

Creating Groups (cont’d. ) Table 7 -4 Options used with the groupadd command Linux Operations and Administration 27

Creating Groups (cont’d. ) • newgrp command – Opens a new instance of the BASH shell – Changes the user’s primary group from users to video newgrp projects id uid=1002(student 1) gid=1000(projects) groups=100(users), 1000(video) Linux Operations and Administration 28

Modifying Groups • groupmod command – Modify existing groups – Only the root user has permission to use this command • Table 7 -5 – Options for groupmod command • Activity 7 -3: Working with Groups – Create and modify groups with the groupadd, groupmod, and newgrp commands Linux Operations and Administration 29

Managing User and Group Accounts with Ya. ST • Ya. ST User and Group Management – Part of Open. SUSE – Graphical utility for centrally managing users and groups • yast 2 users command – Start utility Linux Operations and Administration 30

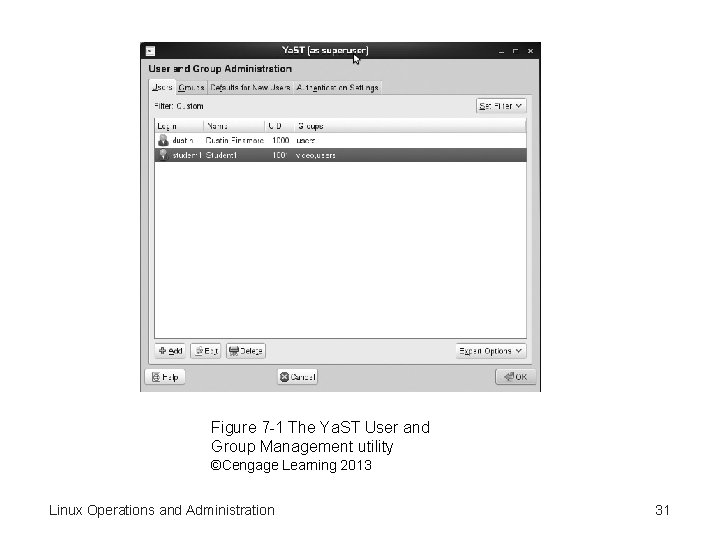
Figure 7 -1 The Ya. ST User and Group Management utility ©Cengage Learning 2013 Linux Operations and Administration 31

Managing User and Group Accounts with Ya. ST (cont’d. ) • Users and Groups tabs – Add, edit, and delete user and group accounts • Ya. ST filters user accounts – See only local users by default – Click the Set Filter button to see Options • Expert Options button – Edit advanced settings, such as password encryption type and automatic logins Linux Operations and Administration 32

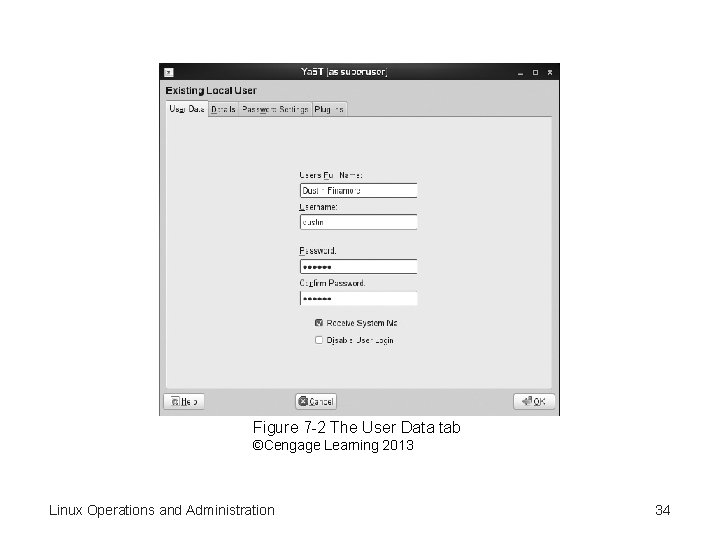
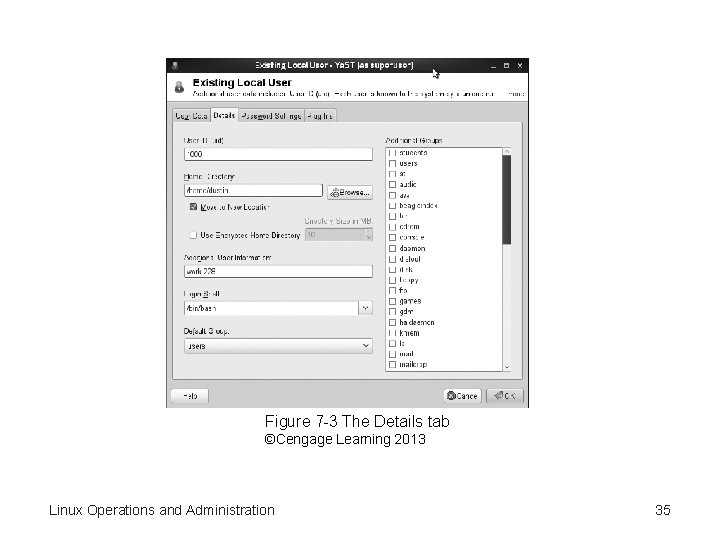
Adding or Editing User Accounts • Four tabs to add or change information – User Data—enter the user’s full name, username, and password – Details—assign a UID, home directory, login shell, default group, and additional user information Linux Operations and Administration 33

Figure 7 -2 The User Data tab ©Cengage Learning 2013 Linux Operations and Administration 34

Figure 7 -3 The Details tab ©Cengage Learning 2013 Linux Operations and Administration 35

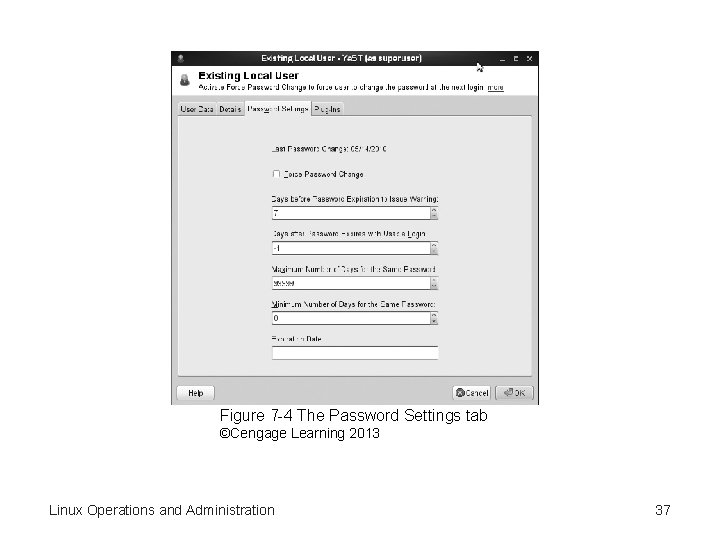
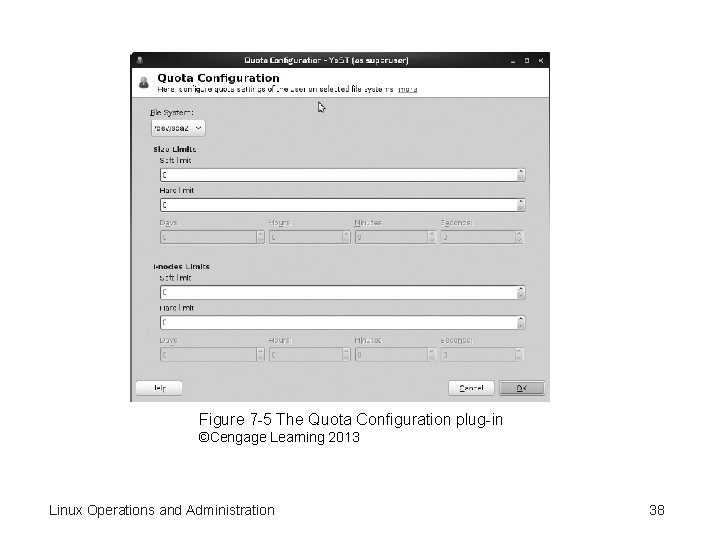
Adding or Editing User Accounts (cont’d. ) – Password Settings—displays password expiration information, like /etc/login. defs configuration file – Plug-Ins—displays a list of plug-ins for user and group configuration. The default plug-in for open. SUSE users is Manage User Quotas Linux Operations and Administration 36

Figure 7 -4 The Password Settings tab ©Cengage Learning 2013 Linux Operations and Administration 37

Figure 7 -5 The Quota Configuration plug-in ©Cengage Learning 2013 Linux Operations and Administration 38

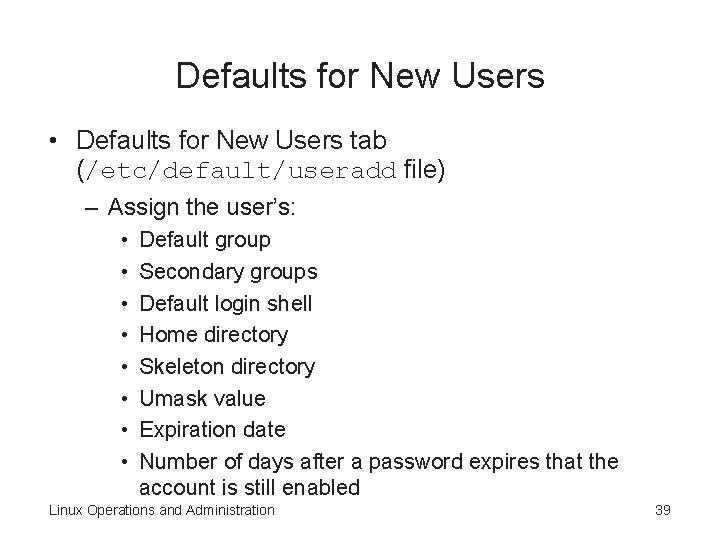
Defaults for New Users • Defaults for New Users tab (/etc/default/useradd file) – Assign the user’s: • • Default group Secondary groups Default login shell Home directory Skeleton directory Umask value Expiration date Number of days after a password expires that the account is still enabled Linux Operations and Administration 39

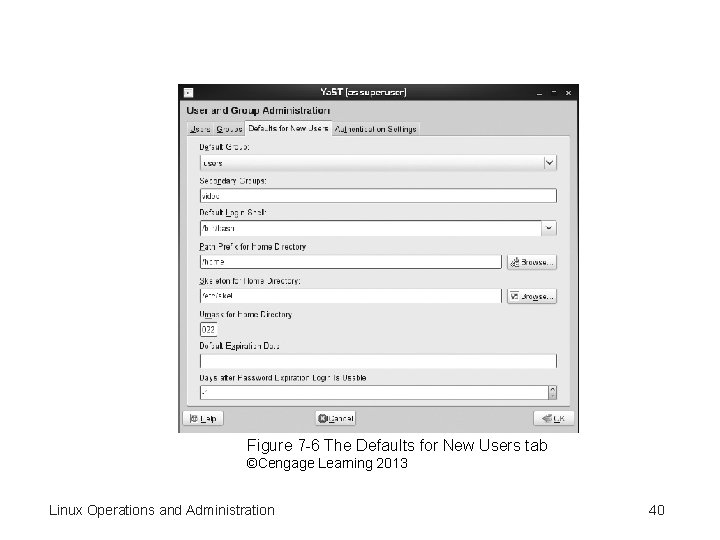
Figure 7 -6 The Defaults for New Users tab ©Cengage Learning 2013 Linux Operations and Administration 40

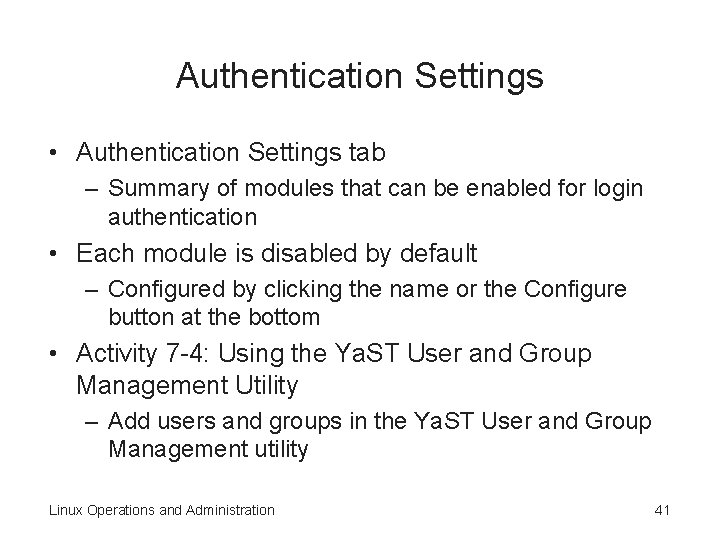
Authentication Settings • Authentication Settings tab – Summary of modules that can be enabled for login authentication • Each module is disabled by default – Configured by clicking the name or the Configure button at the bottom • Activity 7 -4: Using the Ya. ST User and Group Management Utility – Add users and groups in the Ya. ST User and Group Management utility Linux Operations and Administration 41

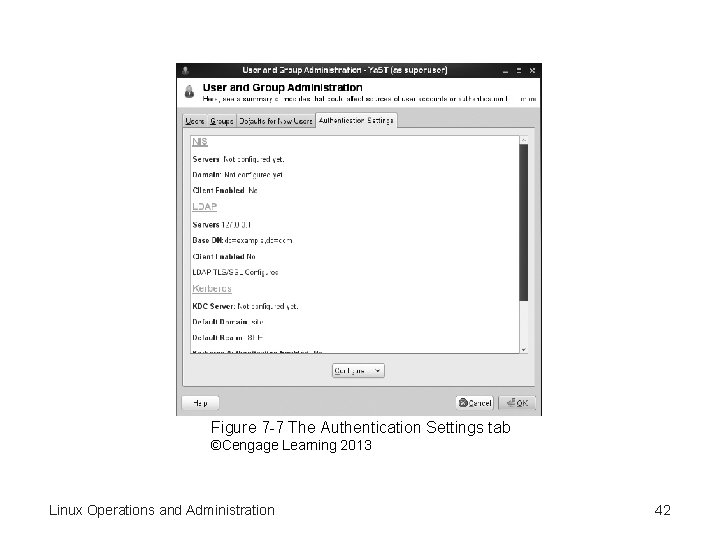
Figure 7 -7 The Authentication Settings tab ©Cengage Learning 2013 Linux Operations and Administration 42

Summary • User account information stored in two database configuration files: /etc/passwd and /etc/shadow • User account parameters specified in the /etc/default/useradd and /etc/login. defs configuration files • useradd command – Create user accounts Linux Operations and Administration 43

Summary (cont’d. ) • passwd command sets passwords for users • usermod and chage commands modify user accounts • userdel command – Delete user accounts • groupadd and groupmod commands – Create groups and change groups • Open. SUSE Ya. ST User and Group Management – GUI utility for adding, editing, and removing users and groups Linux Operations and Administration 44