Linux Operations and Administration Chapter Eight Network Communications







- Slides: 44

Linux Operations and Administration Chapter Eight Network Communications

Objectives • Identify the important protocols at each layer of the TCP/IP model • Describe IP addresses and the difference between the network and host portions of an IP address • Convert decimal IP addresses into binary numbers • Describe the five TCP/IP classes • Configure your Linux network interface card to work with TCP/IP, using the command line • Interact with network devices by using the ping command Linux Operations and Administration 2

Question • How do you connect to the internet? – Here? – At home? Linux Operations and Administration 3

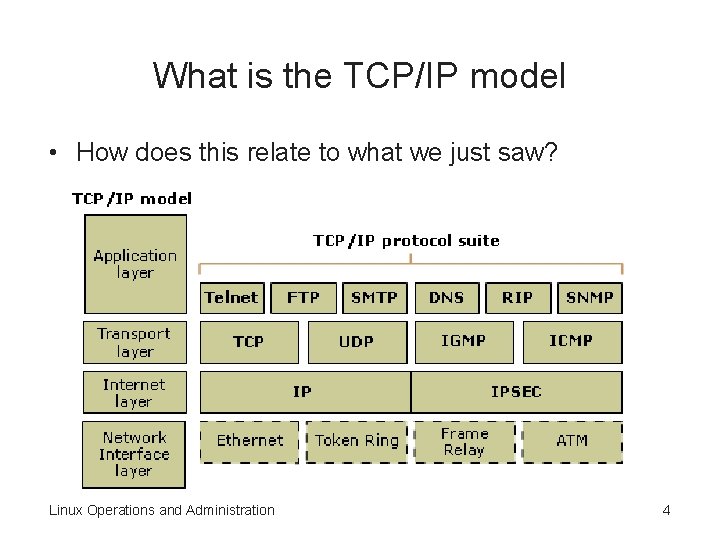
What is the TCP/IP model • How does this relate to what we just saw? Linux Operations and Administration 4

Introduction to TCP/IP (cont’d. ) • Two most important protocols in TCP/IP suite: – Transmission Control Protocol – Internet Protocol • Activity 8 -1: Researching the TCP/IP Protocol Suite – Learn about several protocols in the TCP/IP suite Linux Operations and Administration 5

Working with TCP/IP • Layers in the TCP/IP model: – Application layer • Receives packets from Transport layer • Opens packets to convert the message back to its original form – Transport layer • Responsible for delivering data from one location to another on the network – Internet layer • Receives packets and then routes them to the correct destination Linux Operations and Administration 6

Working with TCP/IP (cont’d. ) • Hardware layers: – Not part of the TCP/IP protocol suite – Data Link layer • Formats data as packets – Physical layer • Consists of cables or other connection media • Deals with data as bits traveling across a network medium Linux Operations and Administration 7

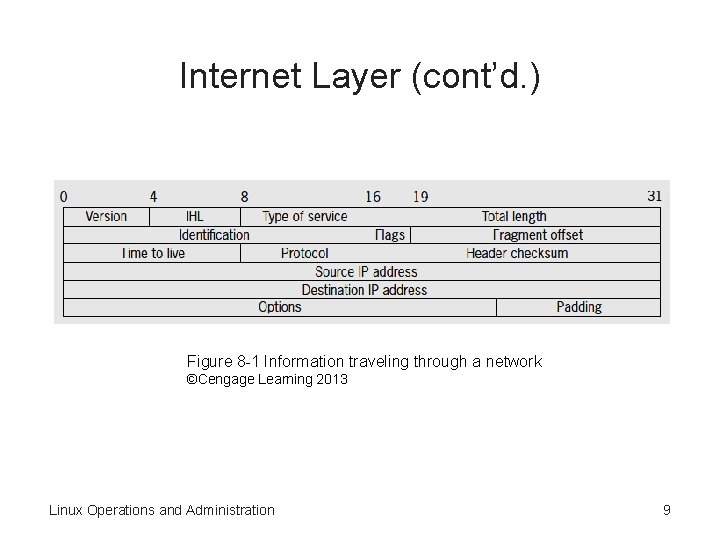
Internet Layer • Sends packets to their specified destinations • Adds an IP-specific header to the packet • Header contains information such as: – – – Source Destination Version Internet header length Protocol Other information about the data Linux Operations and Administration 8

Internet Layer (cont’d. ) Figure 8 -1 Information traveling through a network ©Cengage Learning 2013 Linux Operations and Administration 9

Internet Layer (cont’d. ) • Internet Protocol (IP) – Contains addressing information that enables packets to be routed – Two basic functions of IP are addressing and fragmentation • Internet Control Message Protocol (ICMP) – Used to generate IP error messages Linux Operations and Administration 10

Transport Layer • Responsible for delivering data from one location to another on the network • Transmission Control Protocol (TCP) – Connection-oriented protocol – Keeps track of packets and reassembles them into a single file after they’ve all arrived – Controls the flow of messages Linux Operations and Administration 11

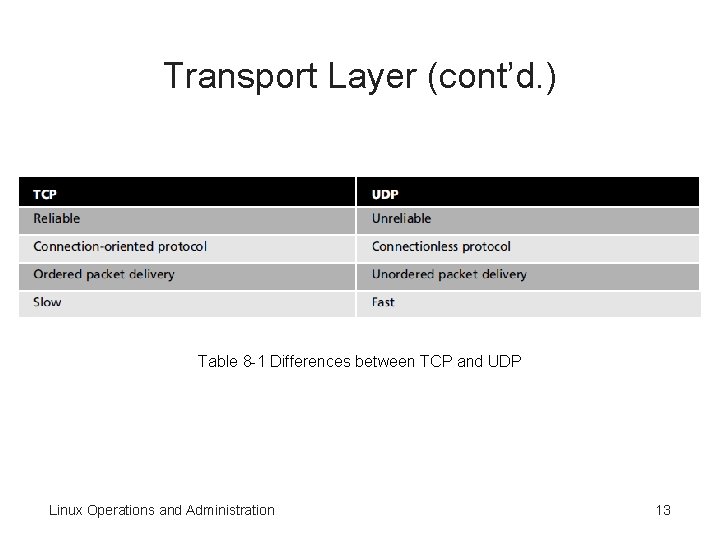
Transport Layer (cont’d. ) • User Datagram Protocol (UDP) – Connectionless protocol – Doesn’t perform error checking or acknowledge that messages were sent successfully • Table 8 -1 – Summarizes the differences between TCP and UDP Linux Operations and Administration 12

Transport Layer (cont’d. ) Table 8 -1 Differences between TCP and UDP Linux Operations and Administration 13

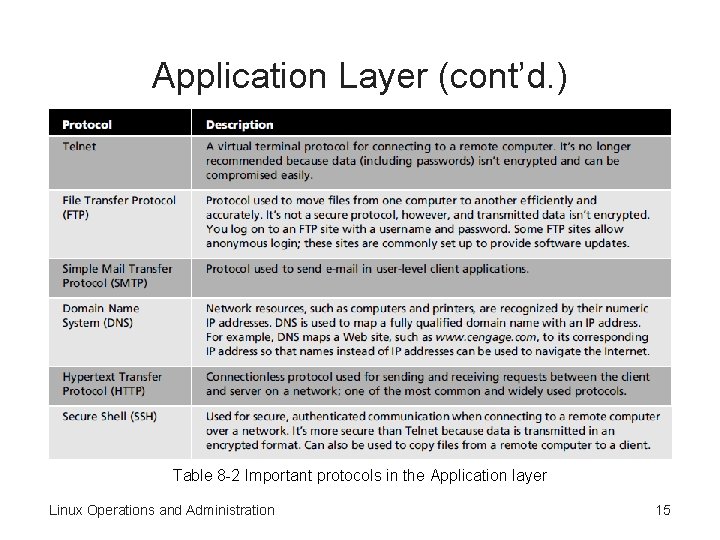
Application Layer • Sits at the top of the TCP/IP model • Contains the higher-level protocols used for network communication in the Transport layer • Table 8 -2 – Describes some important protocols in this layer Linux Operations and Administration 14

Application Layer (cont’d. ) Table 8 -2 Important protocols in the Application layer Linux Operations and Administration 15

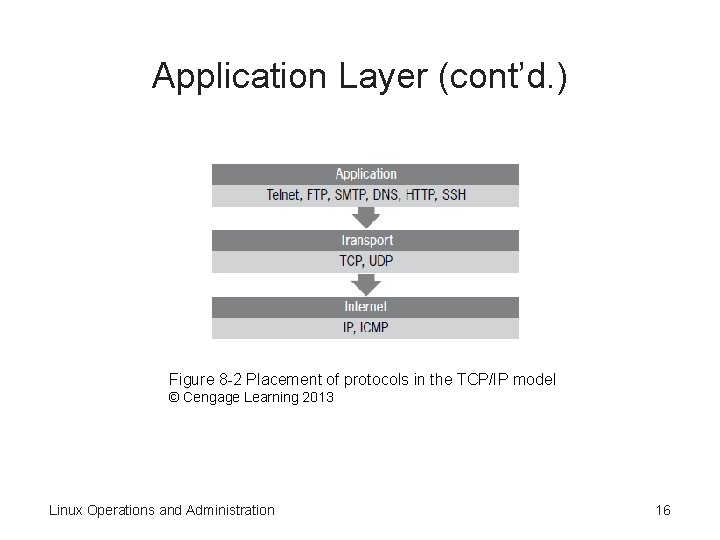
Application Layer (cont’d. ) Figure 8 -2 Placement of protocols in the TCP/IP model © Cengage Learning 2013 Linux Operations and Administration 16

Working with IP Addresses • IP address – A unique number that identifies a computer or device on a TCP/IP network – Format • Four numbers separated by periods • Example: 192. 168. 75. 136 – ifconfig command • Can be used to view a computer’s IP address and the current state of all its active network interfaces Linux Operations and Administration 17

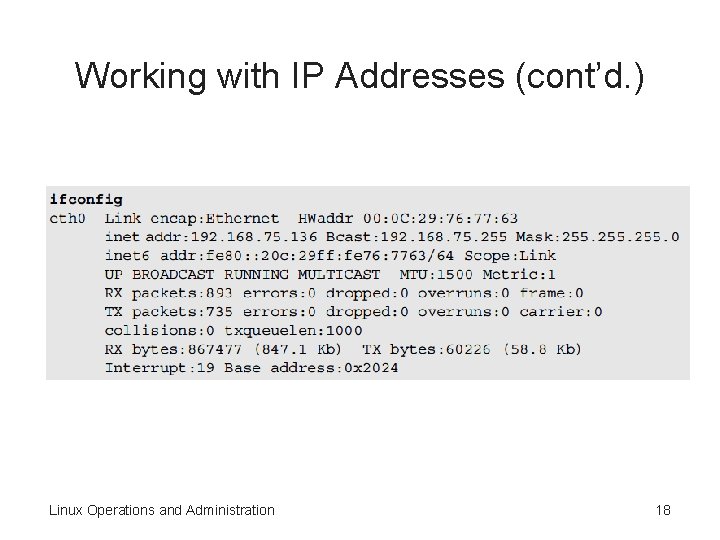
Working with IP Addresses (cont’d. ) Linux Operations and Administration 18

Binary and Decimal Numbering Systems • Decimal numbers – Used in IP addresses – Have 10 possible digits (0 to 9) • Binary numbering system – Uses only two digits (1 and 0) – Used in computers • Computers convert decimal IP addresses into binary numbers Linux Operations and Administration 19

Binary and Decimal Numbering Systems (cont’d. ) • Bit (also known as a binary digit) – Represents a single binary value • IP addresses – Decimal numbers divided into four octets – Each octet is 8 bits – An IP address has 32 bits Linux Operations and Administration 20

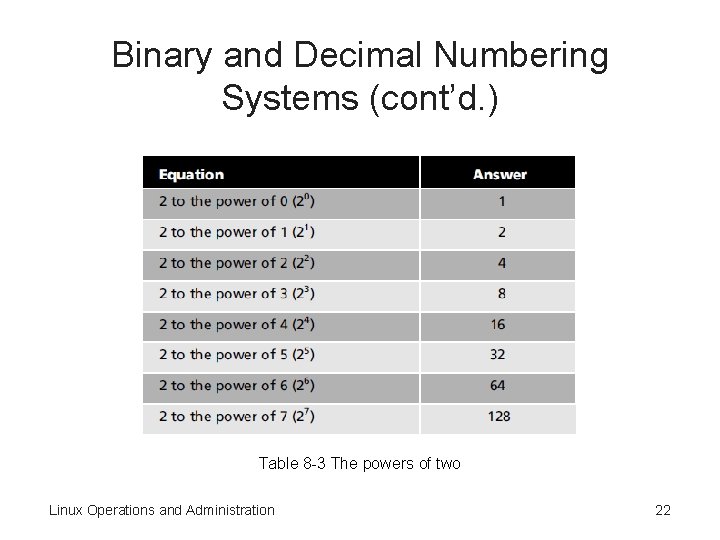
Binary and Decimal Numbering Systems (cont’d. ) • Table 8 -3 – Lists the powers of two from 0 to 7 • Decimal number 112 converts to binary number 01110000 • Activity 8 -2: Converting from Decimal to Binary – Convert a 32 -bit IP address into four 8 -bit binary octet Linux Operations and Administration 21

Binary and Decimal Numbering Systems (cont’d. ) Table 8 -3 The powers of two Linux Operations and Administration 22

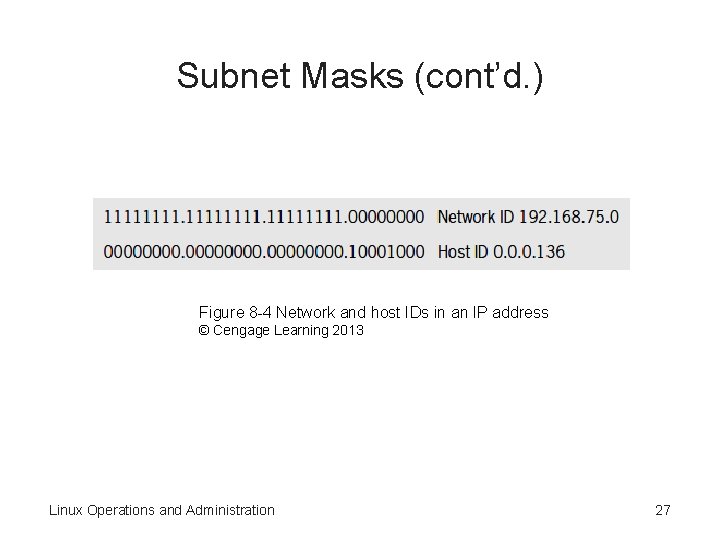
Network and Host Identifiers • An IP address is composed of two parts: – Network ID • Identifies the network where the host is located – Host ID • Identifies a computer or device on a network • Computers can communicate only with other computers on the same network – They must have the same network ID to exchange information Linux Operations and Administration 23

Network and Host Identifiers (cont’d. ) • Router – Used to connect networks and forward packets to their destinations – Needed to communicate with computers having different network IDs Linux Operations and Administration 24

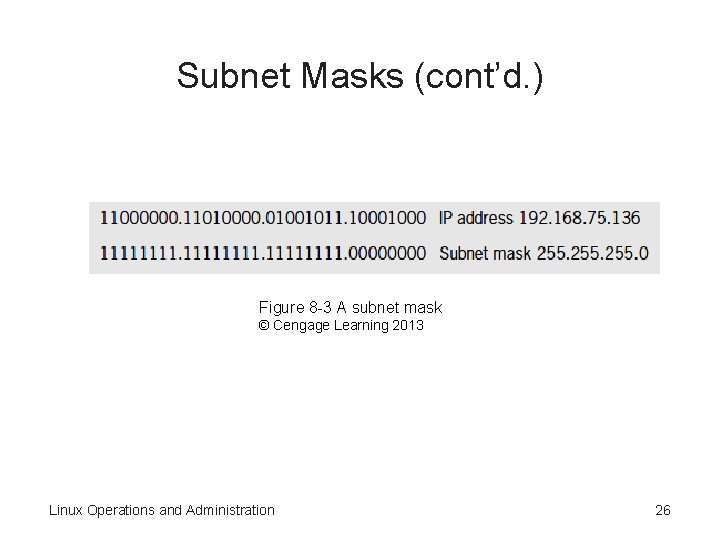
Subnet Masks • Subnet mask – Used to determine which part of an IP address is the network ID and which part is the host ID • A subnet mask is 32 bits • Example – When a computer reads the IP address 255. 0, it converts the decimal 255 to the binary 1111 Linux Operations and Administration 25

Subnet Masks (cont’d. ) Figure 8 -3 A subnet mask © Cengage Learning 2013 Linux Operations and Administration 26

Subnet Masks (cont’d. ) Figure 8 -4 Network and host IDs in an IP address © Cengage Learning 2013 Linux Operations and Administration 27

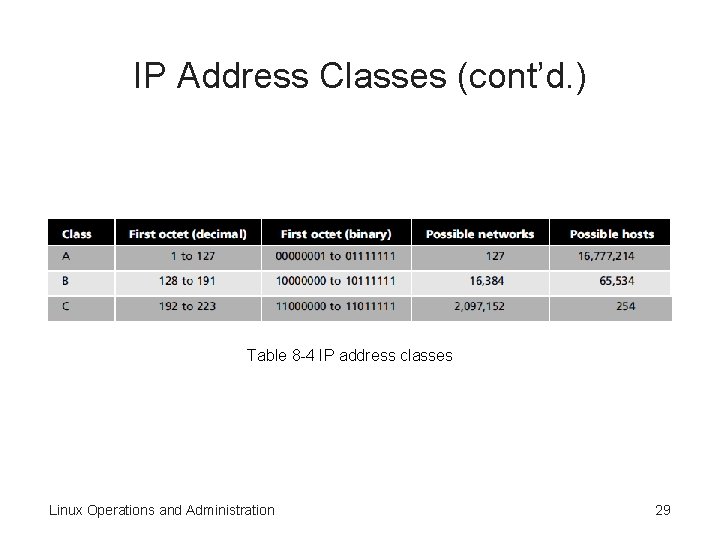
IP Address Classes • IP addresses are divided into five classes to accommodate varying network sizes – Class A, Class B, and Class C: most common classes – Class D and E networks are for multicasting and experimentation • Table 8 -4 – Describes the different IP address classes Linux Operations and Administration 28

IP Address Classes (cont’d. ) Table 8 -4 IP address classes Linux Operations and Administration 29

Class A Networks • Their subnet mask is 255. 0. 0. 0 • The first bit is always 0 • There can be only 127 Class A networks on the entire Internet – Allows 16, 777, 214 hosts per network • Assigned to ISPs or very large companies Linux Operations and Administration 30

Class B Networks • Their subnet mask is 255. 0. 0 • The first two bits are always 10 • Assigned to large organizations – Such as government agencies, universities, and typical companies Linux Operations and Administration 31

Class C Networks • Their subnet mask is 255. 0 • The first three bits are always 110 • More than 2 million Class C networks are possible – Each network can have only 254 hosts • Assigned to small organizations Linux Operations and Administration 32

Configuring Network Interface Cards • Open. SUSE includes tools and utilities to configure many hardware devices – Such as printers, network cards, modems, etc. • Linux provides commands such as ifconfig for configuring a network interface card (NIC) Linux Operations and Administration 33

Using the ifconfig Command • ifconfig command is used to: – View a computer’s IP address and the current state of all active network interfaces on it – Configure NICs Linux Operations and Administration 34

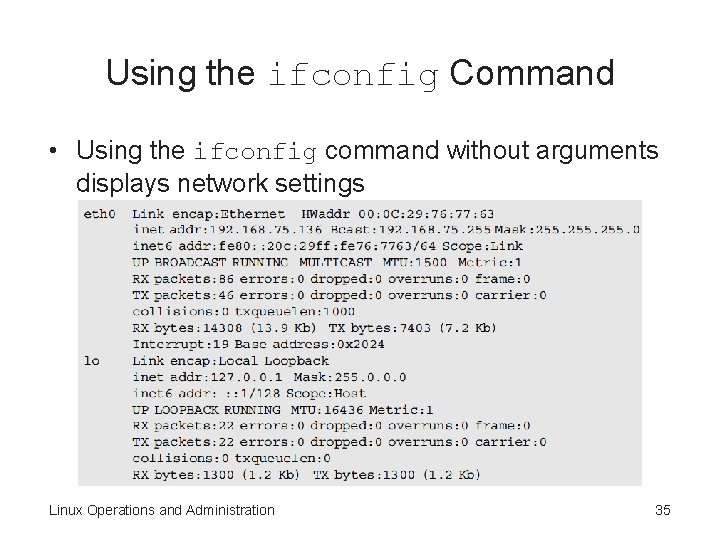
Using the ifconfig Command • Using the ifconfig command without arguments displays network settings Linux Operations and Administration 35

Using the ifconfig Command (cont’d. ) • Output description – Link encap—specifies the type of interface – HWaddr—specifies the hardware address (also known as the MAC address) of a NIC – inet addr—specifies the IP address as well as the broadcast address (Bcast) and the netmask (Mask) – RX packets—specifies the number of packets received (RX) • Also shows the number of errors and dropped packets and how many packets were too long Linux Operations and Administration 36

Using the ifconfig Command (cont’d. ) – TX packets—displays packets transmitted from the computer over the network • Shows error information – Interrupt—displays the computer’s configuration settings • If you have only one NIC, it’s labeled eth 0 – All other NICs are labeled eth 1, eth 2, etc. • The lo represents the loopback adapter with an IP address of 127. 0. 0. 1 • All devices using TCP/IP require the loopback address Linux Operations and Administration 37

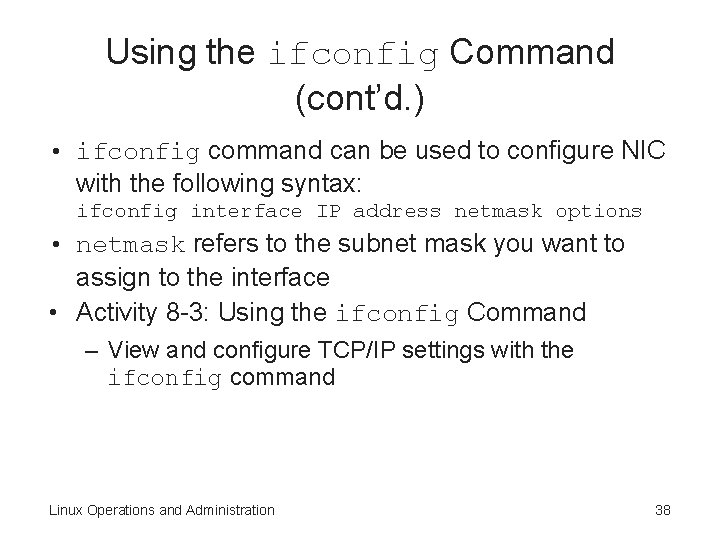
Using the ifconfig Command (cont’d. ) • ifconfig command can be used to configure NIC with the following syntax: ifconfig interface IP address netmask options • netmask refers to the subnet mask you want to assign to the interface • Activity 8 -3: Using the ifconfig Command – View and configure TCP/IP settings with the ifconfig command Linux Operations and Administration 38

The ping Command • Uses ICMP to send an Echo Request packet to a specified network device on the network and waits for a reply • Used by administrators in network testing, measurement, and management • Example: ping 192. 168. 0. 6 Linux Operations and Administration 39

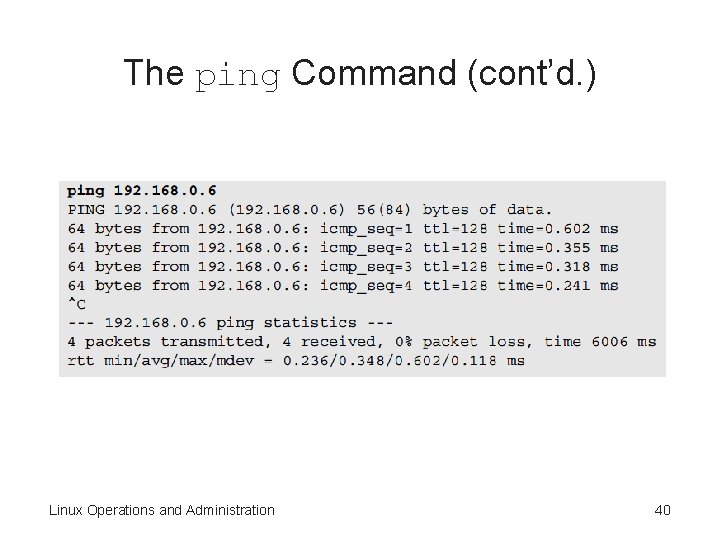
The ping Command (cont’d. ) Linux Operations and Administration 40

The ping Command (cont’d. ) • Each ping request produces a result, including: – icmp_seq – Time to live (ttl) – Packet request’s round-trip time • Table 8 -5 – Describes the options you can use with the ping command • Activity 8 -4: Using the ping Command – Test your TCP/IP configuration with the ping command Linux Operations and Administration 41

The ping Command (cont’d. ) Table 8 -5 Options used with the ping command Linux Operations and Administration 42

Summary • TCP/IP – A suite of networking protocols – Three layers: Application, Transport, and Internet • IP and ICMP: major protocols at Internet layer – IP contains addressing information – ICMP is used to generate IP error messages • TCP and UDP: major protocols at Transport layer – TCP is a connection-oriented protocol – UDP is a connectionless protocol Linux Operations and Administration 43

Summary (cont’d. ) • FTP and HTTP: protocols at Application layer • IP address – Two-part (network ID and host ID) unique number that identifies a device on a TCP/IP network – Decimal IP addresses are converted into binary numbers – IP addresses are divided into classes • ifconfig command is used to view and modify TCP/IP configuration settings • ping command is used in network testing, measurement, and management Linux Operations and Administration 44