Linux Networking Commands Commands Reviewed Ifconfig dmesg netstat


![ifconfig § Assign a IP Address to Network Interface § [root@tecmint ~]# ifconfig eth ifconfig § Assign a IP Address to Network Interface § [root@tecmint ~]# ifconfig eth](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-7.jpg)
![ifconfig § Change MTU for an Network Interface § [root@tecmint ~]# ifconfig eth 0 ifconfig § Change MTU for an Network Interface § [root@tecmint ~]# ifconfig eth 0](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-8.jpg)




![netstat -nr § § § § [root@localhost root]# netstat -nr Kernel IP routing table netstat -nr § § § § [root@localhost root]# netstat -nr Kernel IP routing table](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-18.jpg)

![arp -a § § [root@localhost root]# arp -a gatewayout. tcp-ip. ca (192. 168. 1. arp -a § § [root@localhost root]# arp -a gatewayout. tcp-ip. ca (192. 168. 1.](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-20.jpg)
![dig - supercharged nslookup § oroot@localhost root]# dig cs. senecac. on. ca § § dig - supercharged nslookup § oroot@localhost root]# dig cs. senecac. on. ca § §](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-21.jpg)


- Slides: 25

Linux Networking Commands

Commands Reviewed Ifconfig dmesg netstat ping route tcpdump wireshark traceroute nslookup arp dig

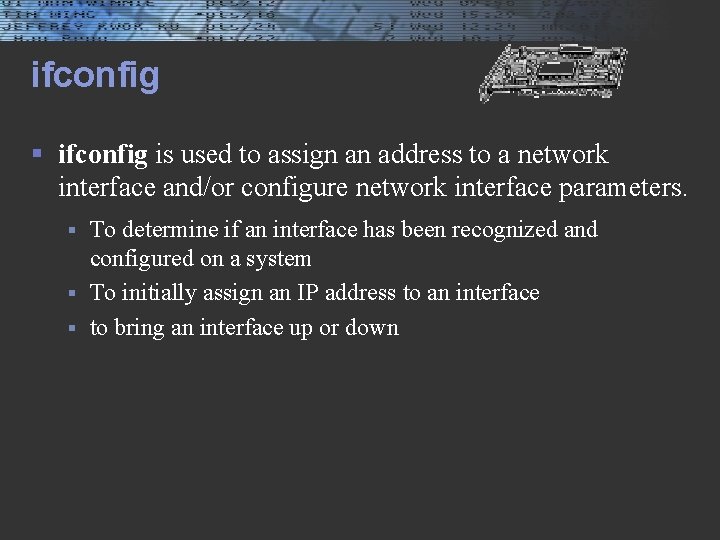
ifconfig § ifconfig is used to assign an address to a network interface and/or configure network interface parameters. To determine if an interface has been recognized and configured on a system § To initially assign an IP address to an interface § to bring an interface up or down §

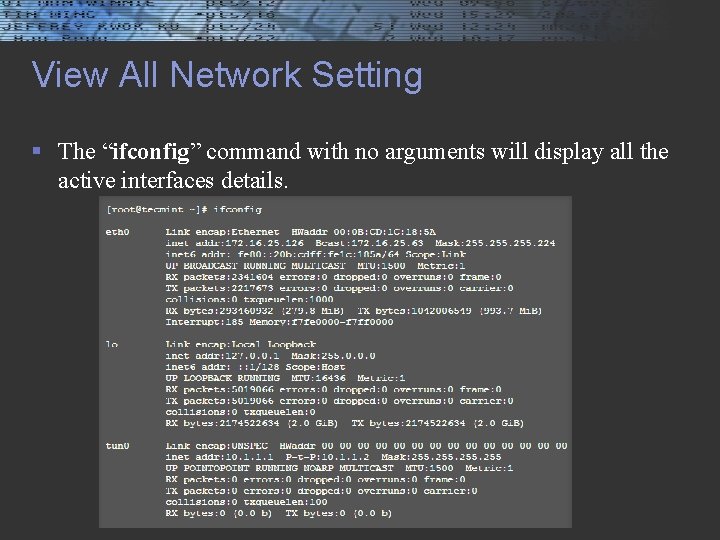
View All Network Setting § The “ifconfig” command with no arguments will display all the active interfaces details.

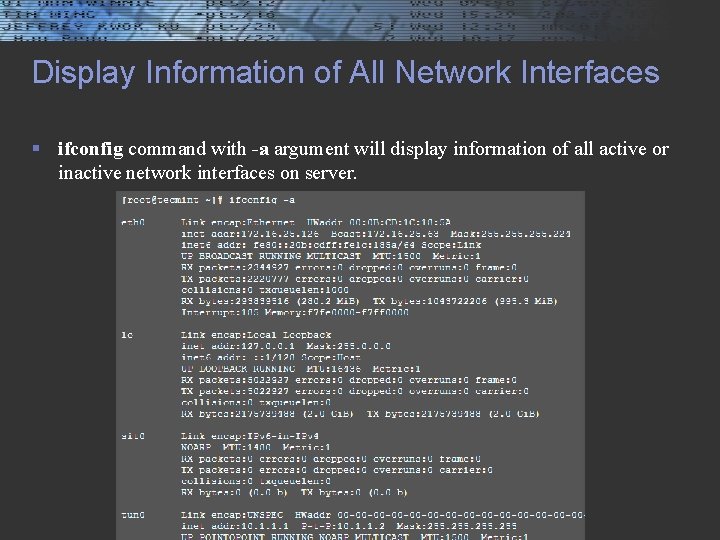
Display Information of All Network Interfaces § ifconfig command with -a argument will display information of all active or inactive network interfaces on server.

ifconfig § View Network Settings of Specific Interface § Enable an Network Interface
![ifconfig Assign a IP Address to Network Interface roottecmint ifconfig eth ifconfig § Assign a IP Address to Network Interface § [root@tecmint ~]# ifconfig eth](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-7.jpg)
ifconfig § Assign a IP Address to Network Interface § [root@tecmint ~]# ifconfig eth 0 172. 16. 25. 125 § Assign a netmask to Network Interface § [root@tecmint ~]# ifconfig eth 0 netmask 255. 224 § Assign a Broadcast to Network Interface § [root@tecmint ~]# ifconfig eth 0 broadcast 172. 16. 25. 63 § Assign all in one command § [root@tecmint ~]# ifconfig eth 0 172. 16. 25. 125 netmask 255. 224 broadcast 172. 16. 25. 63 § Change the MAC address of Network Interface § [root@tecmint ~]# ifconfig eth 0 hw ether AA: BB: CC: DD: EE: FF
![ifconfig Change MTU for an Network Interface roottecmint ifconfig eth 0 ifconfig § Change MTU for an Network Interface § [root@tecmint ~]# ifconfig eth 0](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-8.jpg)
ifconfig § Change MTU for an Network Interface § [root@tecmint ~]# ifconfig eth 0 mtu 1000 § Enable and disable. Promiscuous Mode [root@tecmint ~]# ifconfig eth 0 promisc § [root@tecmint ~]# ifconfig eth 0 –promisc § § Add or remove New Alias to Network Interface [root@tecmint ~]# ifconfig eth 0: 0 172. 16. 25. 127 § [root@tecmint ~]# ifconfig eth 0: 0 down § § Verify the newly created alias network interface address [root@tecmint ~]# ifconfig eth 0: 0 Link encap: Ethernet HWaddr 00: 01: 6 C: 99: 14: 68 inet addr: 172. 16. 25. 123 Bcast: 172. 16. 25. 63 Mask: 255. 240 UP BROADCAST RUNNING MULTICAST MTU: 1500 Metric: 1 Interrupt: 17 §

See if the device has been found - use dmesg § The command 'dmesg', which is used to print kernel messages, is very useful in determining if a piece of hardware has been found, and if so, what the system is referring to it as. § Examples: § dmesg | grep -i eth 0 § dmesg | grep -i usb § dmesg | grep -i Memory § dmesg | grep -i bluetooth § dmesg | grep -i tty § dmesg –c clear dmesg logs from boot time to till that time

ping § Confirm that a remote host is online and responding. § ping is intended for use in network testing, measurement, and management. § It is unwise to use ping during normal operations or from automated scripts.

§ Decrease /Increase Ping Time Interval $ ping -i 5 IP § # ping -i 0. 1 IP § § Note: Only super user can specify interval less than 0. 2 seconds. § Check local interface $ ping 0 § $ ping localhost § $ ping 127. 0. 0. 1 § § Send n packets and stop: § $ ping -c 5 google. com § Display the current version of ping program § $ ping -V

Ping § 5. Flood the network § # ping -f localhost § Audible ping: § $ ping -a IP § Change Ping Packet Size § $ ping -s 100 localhost § Specify path for ping to send the packet § $ ping 192. 168. 3. 33 192. 168. 7. 1 192. 168. 4. 45 § Record and print route of how ECHO_REQUEST sent and ECHO_REPLY received § $ ping -R 192. 168. 1. 63

Route command § Display Existing Routes § if the destination is within the network range 192. 168. 1. 0 – 192. 168. 1. 255, then the gateway is *, which is 0. 0. § By default route command displays the host name in its output. We can request it to display the numerical IP address using -n option as shown below.

§ Adding a Default Gateway § $ route add default gw 192. 168. 1. 10 § List Kernel’s Routing Cache Information § Reject Routing to a Particular Host or Network § route add -host 192. 168. 1. 51 reject

traceroute § traceroute attempts tracing by launching UDP probe packets with a small TTL (time to live), then listening for an ICMP "time exceeded" reply from a gateway. § host is the destination hostname or the IP number of host to reach. § packetsize is the packet size in bytes of the probe datagram. Default is 38 bytes. Note Traceroute has lost some of its effectiveness since most ISP’s disallow it from running on their networks

netstat § List out all connections § $ netstat –a § List only TCP or UDP connections $ netstat –at § $ netstat –au § § Disable reverse dns lookup for faster output: By default, the netstat command tries to find out the hostname of each ip address in the connection by doing a reverse dns lookup. This slows down the output. § $ netstat -ant

netstat § Print statistic § $ netstat -s § List out only listening connections § $ netstat –tnl § Get process name/pid and user id § $ sudo netstat –nlpt § Use the e option along with the p option to get the username too. § $ sudo netstat -ltpe
![netstat nr rootlocalhost root netstat nr Kernel IP routing table netstat -nr § § § § [root@localhost root]# netstat -nr Kernel IP routing table](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-18.jpg)
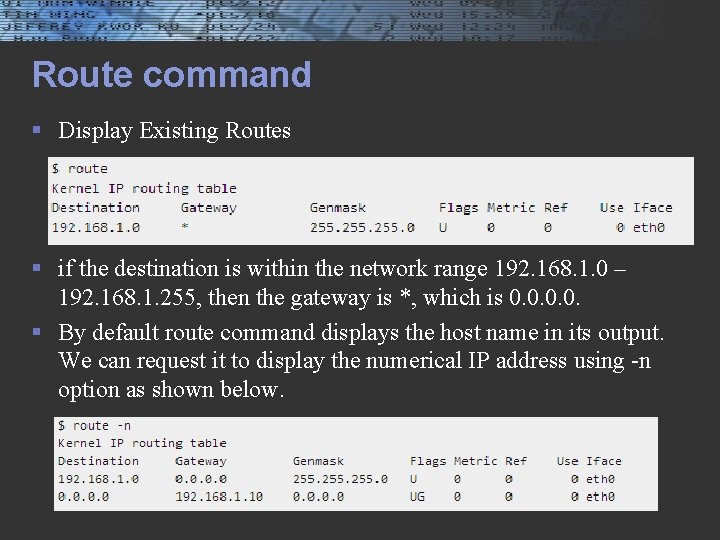
netstat -nr § § § § [root@localhost root]# netstat -nr Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface 192. 168. 2. 0 0. 0 255. 0 U 40 0 0 eth 0 192. 168. 1. 0 0. 0 255. 0 U 40 0 0 eth 1 127. 0. 0. 0 255. 0. 0. 0 U 40 0 0 lo 0. 0 192. 168. 1. 1 0. 0 UG 40 0 0 eth 1

nslookup § Query Internet domain name servers. § $ nslookup redhat. com § $ nslookup -query=mx redhat. com § nslookup -type=ns redhat. com § Query the SOA Record using -query=soa § provides the authoritative information about the domain, the e-mail address of the domain admin, the domain serial number, etc… § $ nslookup -type=soa redhat. com § View available DNS records using -query=any § $ nslookup -type=any google. com § Reverse DNS lookup § $ nslookup redhat. com ns 1. redhat. com
![arp a rootlocalhost root arp a gatewayout tcpip ca 192 168 1 arp -a § § [root@localhost root]# arp -a gatewayout. tcp-ip. ca (192. 168. 1.](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-20.jpg)
arp -a § § [root@localhost root]# arp -a gatewayout. tcp-ip. ca (192. 168. 1. 1) at 00: 04: 5 A: DB: A 1: C 5 [ether] on eth 1 basement. tcp-ip. ca (192. 168. 2. 75) at 00: 10: E 0: 04: 61: 84 [ether] on eth 0 just_a_node. tcp-ip. ca (192. 168. 1. 101) at 00: 09: B 7: 13: AA: 13 [ether] on eth 1
![dig supercharged nslookup orootlocalhost root dig cs senecac on ca dig - supercharged nslookup § oroot@localhost root]# dig cs. senecac. on. ca § §](https://slidetodoc.com/presentation_image_h/c5a7ba065fc6a1b04e5d450b3affa830/image-21.jpg)
dig - supercharged nslookup § oroot@localhost root]# dig cs. senecac. on. ca § § § ; <<>> Di. G 9. 1. 3 <<>> cs. senecac. on. ca ; ; global options: printcmd ; ; Got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10483 ; ; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 6, ADDITIONAL: 4 § § ; ; QUESTION SECTION: ; cs. senecac. on. ca. IN A § § ; ; ANSWER SECTION: cs. senecac. on. ca. 86400 IN A 142. 204. 57. 48

dig - better than nslookup § § § § ; ; AUTHORITY SECTION: senecac. on. ca. 86400 IN NS ns. onet. on. ca. senecac. on. ca. 86400 IN NS ns 2. senecac. on. ca. 86400 IN NS hades. senecac. on. ca. 86400 IN NS ittads. senecac. on. ca. 86400 IN NS pulsar. senecac. on. ca. 86400 IN NS nsprime. senecac. on. ca. § § § ; ; ADDITIONAL SECTION: ns 2. senecac. on. ca. 86400 IN A 142. 204. 100 hades. senecac. on. ca. 86400 IN A 142. 204. 57. 15 ittads. senecac. on. ca. 86400 IN A 142. 204. 6. 57 pulsar. senecac. on. ca. 86400 IN A 142. 204. 119. 97 § § ; ; Query time: 2202 msec ; ; SERVER: 127. 0. 0. 1#53(127. 0. 0. 1) ; ; WHEN: Sun Sep 29 16: 38: 20 2002 ; ; MSG SIZE rcvd: 238

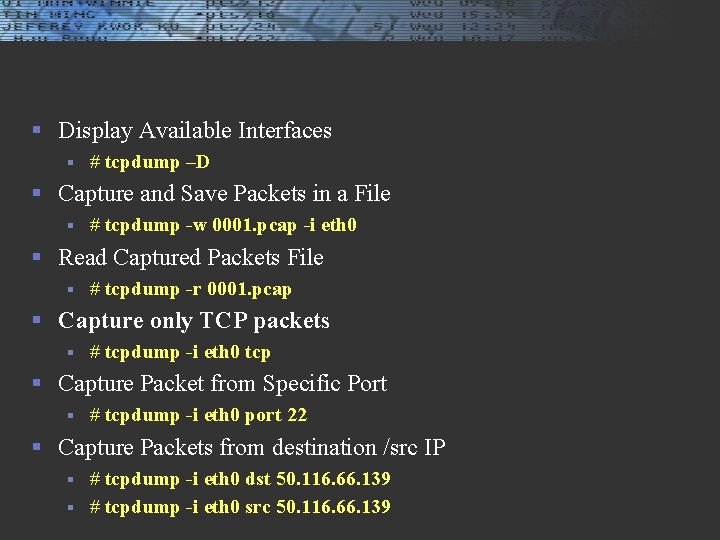
tcpdump § tcpdump is a most powerful and widely used command-line packets sniffer or package analyzer tool which is used to capture or filter TCP/IP packets that received or transferred over a network on a specific interface. # yum install tcpdump § $ apt-get install tcpdump § § Capture Packets from Specific Interface § # tcpdump -i eth 0 § Capture Only N Number of Packets § # tcpdump -c 5 -i eth 0

§ Display Available Interfaces § # tcpdump –D § Capture and Save Packets in a File § # tcpdump -w 0001. pcap -i eth 0 § Read Captured Packets File § # tcpdump -r 0001. pcap § Capture only TCP packets § # tcpdump -i eth 0 tcp § Capture Packet from Specific Port § # tcpdump -i eth 0 port 22 § Capture Packets from destination /src IP # tcpdump -i eth 0 dst 50. 116. 66. 139 § # tcpdump -i eth 0 src 50. 116. 66. 139 §

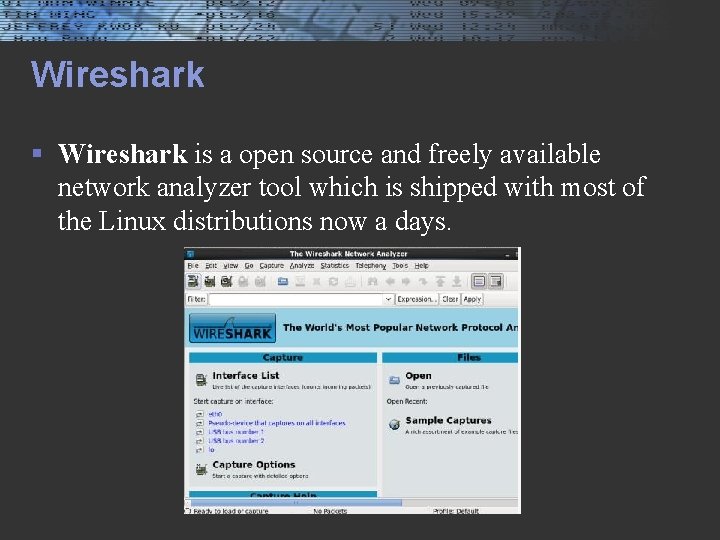
Wireshark § Wireshark is a open source and freely available network analyzer tool which is shipped with most of the Linux distributions now a days.