Linux Memory Management How does the Linux kernel





- Slides: 16

Linux Memory Management How does the Linux kernel keep track of the Virtual Memory Areas that each process uses?

Hardware/Firmware/Software • The PC ‘s memory management system is a cooperative venture involving hardware, software, and firmware • The hardware and firmware would be the same no matter which Operating System we choose to run (i. e. , Linux or Windows) • An operating system utilizes the hardware (in its own unique way) to provide multiple processes with protected memory-spaces

The Linux/x 86 scheme • Let’s focus on the particular approach that Linux takes in utilizing the Intel x 86 CPU’s memory-addressing capabilities • There are two conceptual levels (because “processor independence” is a goal Linux strives for): much of the Linux ‘mm’ code runs on almost any CPU, yet there’s some code is (unavoidably) specific to the x 86

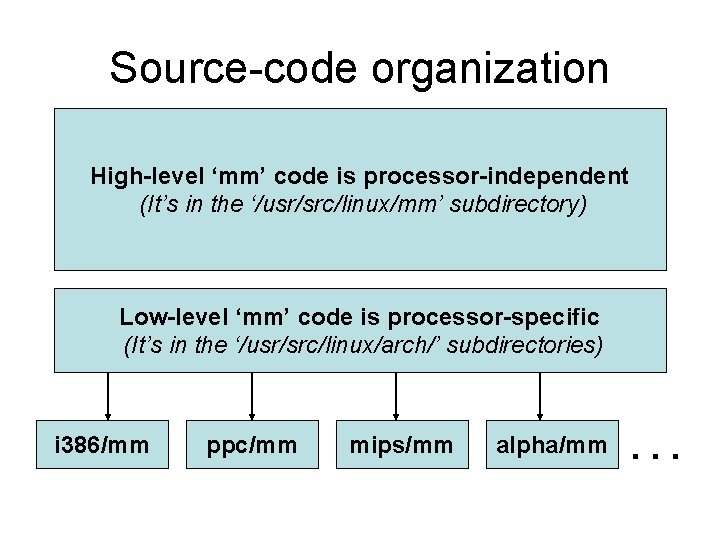
Source-code organization High-level ‘mm’ code is processor-independent (It’s in the ‘/usr/src/linux/mm’ subdirectory) Low-level ‘mm’ code is processor-specific (It’s in the ‘/usr/src/linux/arch/’ subdirectories) i 386/mm ppc/mm mips/mm alpha/mm . . .

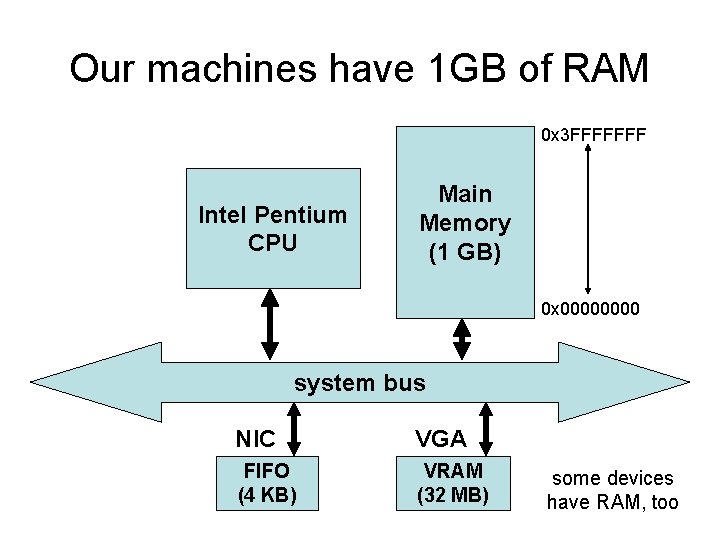
Our machines have 1 GB of RAM 0 x 3 FFFFFFF Intel Pentium CPU Main Memory (1 GB) 0 x 0000 system bus NIC VGA FIFO (4 KB) VRAM (32 MB) some devices have RAM, too

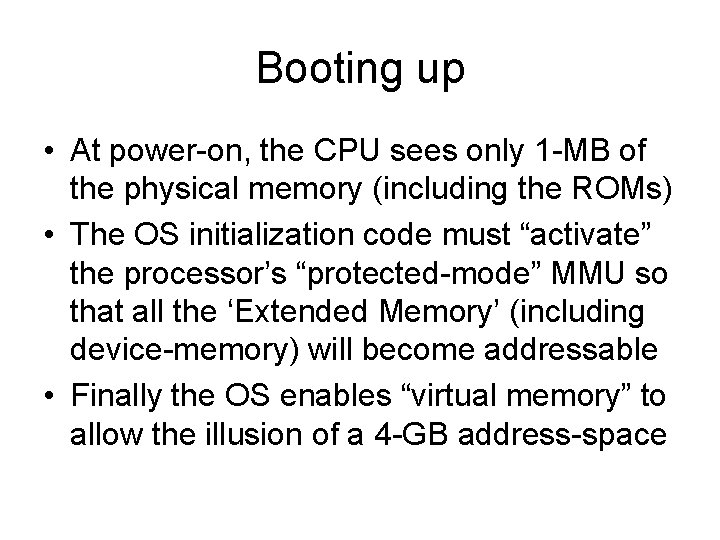
Booting up • At power-on, the CPU sees only 1 -MB of the physical memory (including the ROMs) • The OS initialization code must “activate” the processor’s “protected-mode” MMU so that all the ‘Extended Memory’ (including device-memory) will become addressable • Finally the OS enables “virtual memory” to allow the illusion of a 4 -GB address-space

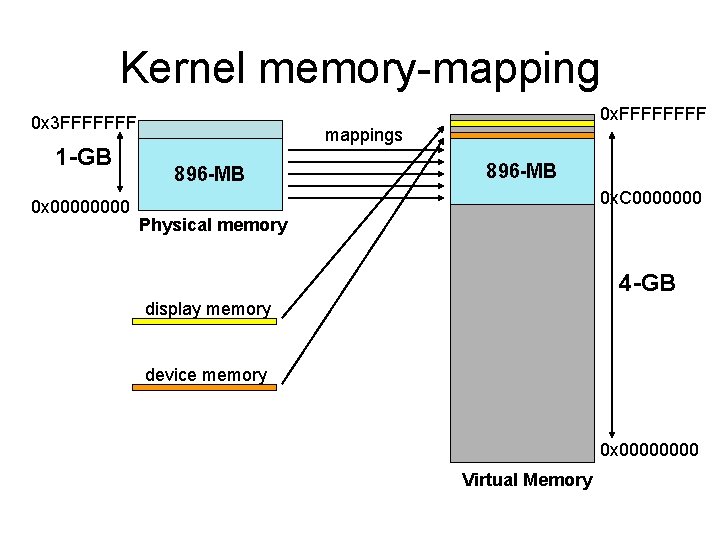
Kernel memory-mapping 0 x. FFFF 0 x 3 FFFFFFF 1 -GB 0 x 0000 mappings 896 -MB 0 x. C 0000000 Physical memory 4 -GB display memory device memory 0 x 0000 Virtual Memory

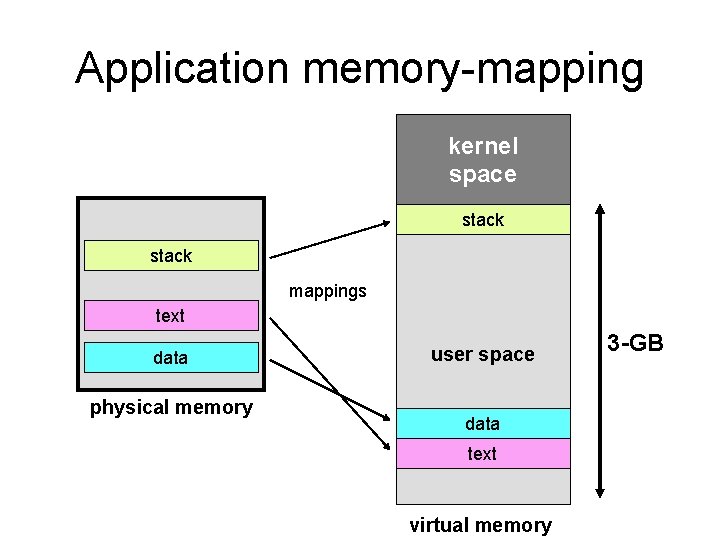
Application memory-mapping kernel space stack mappings text data physical memory user space data text virtual memory 3 -GB

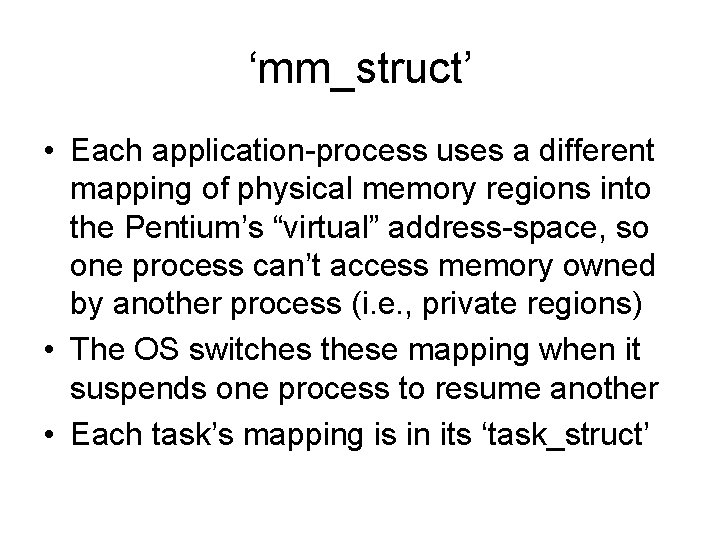
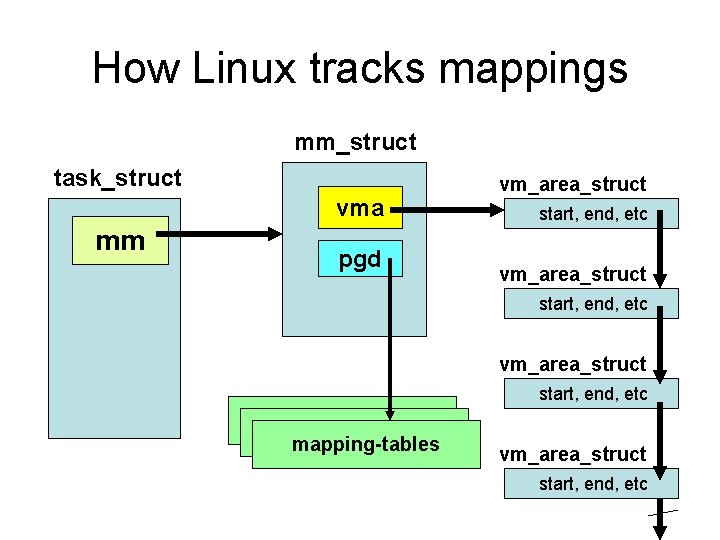
‘mm_struct’ • Each application-process uses a different mapping of physical memory regions into the Pentium’s “virtual” address-space, so one process can’t access memory owned by another process (i. e. , private regions) • The OS switches these mapping when it suspends one process to resume another • Each task’s mapping is in its ‘task_struct’

How Linux tracks mappings mm_struct task_struct vma mm pgd vm_area_struct start, end, etc mapping-tables vm_area_struct start, end, etc

What does ‘malloc()’ do? • The standard C runtime environment lets a user program allocate additional memory void *malloc( unsigned long nbytes ); • This memory is released after being used void free( void *vaddr ); • Using suitable kernel modules we can see how the kernel keeps track of this memory

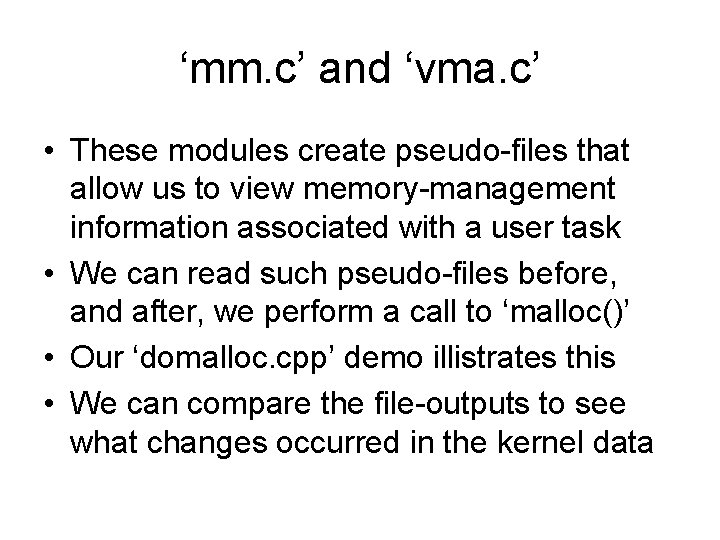
‘mm. c’ and ‘vma. c’ • These modules create pseudo-files that allow us to view memory-management information associated with a user task • We can read such pseudo-files before, and after, we perform a call to ‘malloc()’ • Our ‘domalloc. cpp’ demo illistrates this • We can compare the file-outputs to see what changes occurred in the kernel data

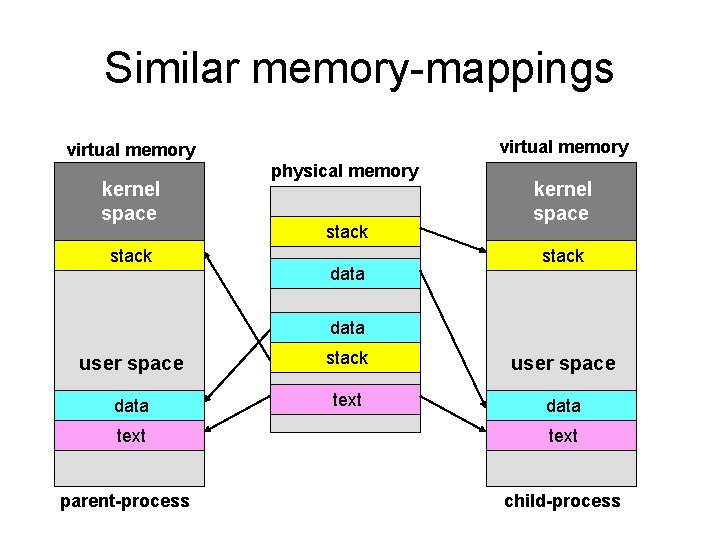
When a program ‘forks()’ • We already know how new processes get created in the UNIX/Linux environment (i. e. , via the ‘fork()’ function or system-call) • A child-process gets constructed using the same code and data as its parent-process • Yet each task’s memory-regions are kept ‘private’ (i. e. , accessible to it alone) • So how exactly is this feat achieved?

Similar memory-mappings virtual memory kernel space stack physical memory stack data kernel space stack data user space stack user space data text parent-process text child-process

Another demo • You could write a program, similar to our ‘domalloc. cpp’ demo, that would let a user compare the list of memory-regions which a parent-process owns and the list that its child-process has inherited

In-class exercise • Write an application program that allows a user to compare BOTH the ‘mm_struct’ and the ‘vm_area_struct’ information that belong to a parent-process and to its child • You can use our ‘mm. c’ and ‘vma. c’ Linux kernel modules, and you can imitate the programming ideas used in ‘domalloc. cpp’ • TURN IN printouts of your code and output