Linux Kernel Development Chap 5 System Calls Bai

Linux Kernel Development Chap. 5 System Calls Bai, Peng WMN Lab 2007. 03. 29 1

What should we learn from this Chapter? Ø What are system calls? Ø How do they relate to library calls and API? Ø How does linux kernel implement system calls and the chain of events required to execute a system call? Ø How to add new system calls? Ø What are pros and cons of implementing system calls? 2
5. 1 API, POSIX, and the C Library Ø System calls provide a layer between the hardware and user-space processes. Ø Why we need this layer? Ø provides a hardware interface for user-space. Ø ensure system security and stability. Ø this layer allows for the virtualized system provided to processes. Ø In Linux, system calls are the only legal entry userspace has of interfacing with the kernel. 3

5. 1 API, POSIX, and the C Library Ø API is Application Programming Interface Ø Applications are programmed against an API, not directly to system calls. Ø An API defines a set of programming interfaces used by applications. Ø One of the more common application programming interfaces in the Unix world is based on the POSIX standard. Linux is compatible with POSIX. Ø The system call interface in Linux, as with most Unix systems, is provided in part by the C library. 4

5. 1 API, POSIX, and the C Library Figure 5. 1. The relationship between applications, the C library, and the kernel with a call to printf(). 5

5. 2 Syscalls Ø System calls (syscalls in Linux) are accessed via function calls. System calls need inputs and also provide a return value (long) signifies success or error. Ø System calls have a defined behavior. Ø In Linux, each system call is assigned a syscall number. This is a unique number that is used to reference a specific system call. Ø When the syscall number is assigned, it cannot change or be recycled. Ø System calls in Linux are faster than in many other operating systems. (such as fast context switch times) 6

5. 3 System Call Handler Ø Because it is not possible for user-space applications to execute kernel code directly, applications must signal the kernel that they want to execute a system call and have the system switch to kernel mode. Ø The mechanism to signal the kernel is a software interrupt: Incur an exception and then the system will switch to kernel mode and execute the exception handler system call handler. Ø The defined software interrupt on x 86 is function system_call(). Ø x 86 processors added a feature known as sysenter. 7
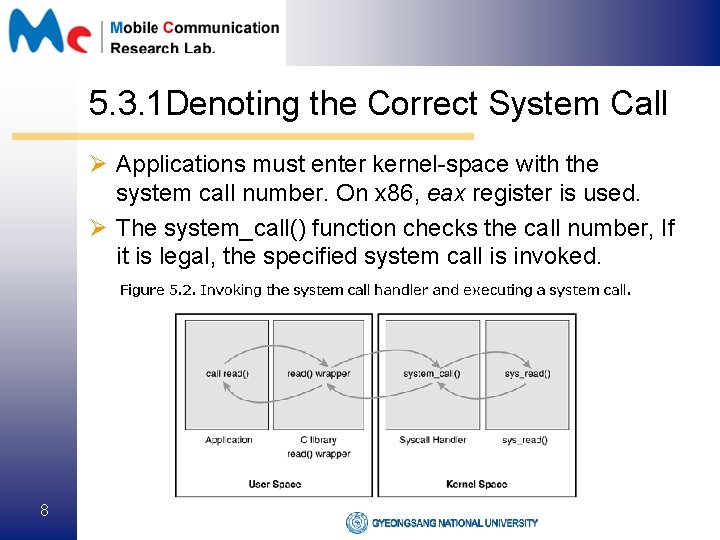
5. 3. 1 Denoting the Correct System Call Ø Applications must enter kernel-space with the system call number. On x 86, eax register is used. Ø The system_call() function checks the call number, If it is legal, the specified system call is invoked. 8

5. 4 System Call Implementation Ø The implementation of a system call does not need to concern itself with the behavior of the system call handler. Adding a new system call to Linux is easy. The hard work is designing and implementing the system call. Ø How to involved a new system call for Linux? Ø Ø 9 defining system call’s purpose. system call's arguments, return value, and error codes. designing the interface with an eye toward the future. realizing the need for portability and robustness, not just today but in the future.

5. 4 System Call Implementation Ø Verifying the Parameters Ø System calls must make sure all of their parameters are valid and legal. Such as access permission. Ø Two methods for performing the requisite checks and the desired copy to and from user-space: Ø For writing into user-space, the method copy_to_user(destination memory address , source pointer , size of the data to copy ) is provided. Ø For reading from user-space, the method copy_from_user(destination memory address , source pointer, the number from the second parameter reading into the first parameter) is used. Ø The possible check is for valid permission. Ø suser() and capable() 10

5. 5 System Call Context Ø Final Steps in Binding a System Call Ø First, add an entry to the end of the system call table. Ø For each architecture supported, the syscall number needs to be defined in <asm/unistd. h>. Ø The syscall needs to be compiled into the kernel image. Ø Accessing the System Call from User-Space Ø Linux provides a set of macros for wrapping access to system calls. It sets up the register contents and issues the trap instructions. These macros are named _syscalln(), where n is between 0 and 6. Ø The macro also can use system call without library support. 11

5. 5 System Call Context Ø Why Not to Implement a System Call? Ø Be care of adding new syscalls. Often, much more viable alternatives to providing a new system call are available. Ø The pros of implementing a new interface as a syscall are as follows: Ø System calls are simple to implement and easy to use. Ø System call performance on Linux is blindingly fast. Ø The cons: Ø The syscall number needs to be officially assigned to you. Ø After the system call is in a stable series kernel, the interface cannot change without breaking user-space applications. Ø Each architecture needs to separately register the system call and support it. Ø System calls are not easily used from scripts and cannot be accessed directly from the filesystem. Ø For simple exchanges of information, a system call is overkill. Ø Still some alternatives 12
- Slides: 12