Linux and UNIX Overview 1 Linux and UNIX





























- Slides: 47

Linux and UNIX Overview 1

Linux and UNIX q Linux and UNIX OSs are… o Often targets for attacks o Often used for launching attacks q So we need to understand basics Linux and UNIX Overview 2

UNIX q. A o o “beautiful but strange beast” Developed as research project by AT&T More than 35 years old Internet was built on UNIX Recently, popular for desktops, etc. Linux and UNIX Overview 3

UNIX q It’s beautiful because… o It’s powerful o o § Millions of people have worked on it Huge numbers of useful tools “Been around the block” more than once Closely associated with open source Admins can find lots of useful tools Linux and UNIX Overview 4

UNIX Strange because so many UNIX OSs q Popular variants include q o o o o Solaris by Sun Mac. OS by Apple HP-UX by HP IRIX by sgi AIX by IBM Free. BSD, free open source Open. BSD, “the #1 most secure” OS Linux and UNIX Overview 5

UNIX q Differences between UNIX variants o File systems organization o System calls, command options, etc. q Two main “lines” of UNIX o AT&T and BSD q But some UNIXs are combinations Linux and UNIX Overview 6

Linux q Developed by Linus Torvalds o Technically, not a variant of UNIX o Created without using any of the underlying UNIX code o A “UNIX-like environment” o Strictly speaking, “Linux” is just the kernel o Many Linux “distros”: Debian, Gentoo, Mandrake, Red Hat, Slackware, Su. SE, etc. Linux and UNIX Overview 7

UNIX q Here, generic UNIX/Linux concepts o Things that apply to most UNIX/Linux q UNIX also strange because o Not designed for ease of use o Think command line, not GUI o Ironically, much simpler than Windows… If you think Windows is easier, you don’t know Linux… q …and you don’t know Windows q Linux and UNIX Overview 8

UNIX q Here, we focus on generic “UNIX” o Things that apply to most variants Book use “UNIX”, “Linux” interchangeably q Here, we only scratch the surface q For more info q o Linux Administration Handbook, by Nemeth o Man pages Linux and UNIX Overview 9

Architecture q File system o Like traveling thru a city… o Directories are like signs leading you to “buildings” (files) q Many things treated as files o Devices, elements of processes, files Linux and UNIX Overview 10

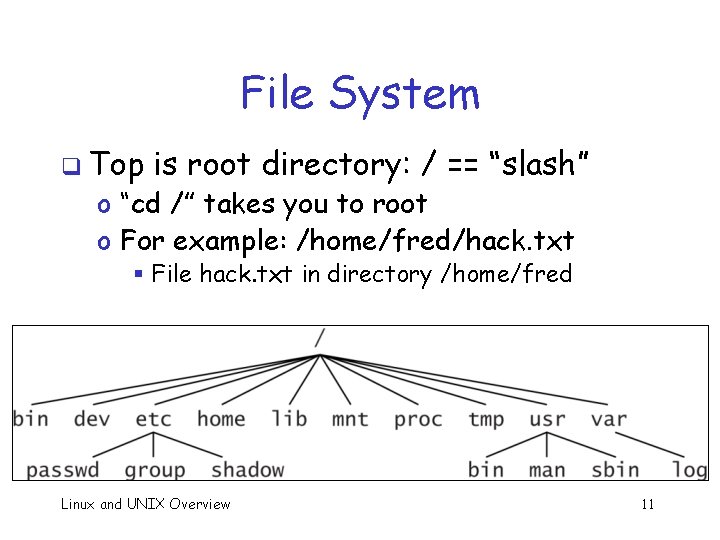
File System q Top is root directory: / == “slash” o “cd /” takes you to root o For example: /home/fred/hack. txt § File hack. txt in directory /home/fred Linux and UNIX Overview 11

Important Directories q/ == root (top level), called “slash” q /bin, /sbin == critical system exe’s q /dev == devices, terminal, CD, etc. q /etc == system config files o Accounts, pwds, network addresses, etc. q /home == user directories Linux and UNIX Overview 12

Important Directories q q q /lib == shared libraries for programs /mnt == exported file systems temporarily mounted, removable devices (e. g. , USB) /proc == images/data of current processes o Not on hard drive---can see what kernel is doing q q q /tmp == temporary files /usr == critical system files (utilities, man pages, …) /var == stores various types of files, often for administration (log files) Linux and UNIX Overview 13

Important Directories q “. ” is current directory q “. . ” is parent directory o One level up q “ls” lists all files in directory q “ls -a” lists “. ” and “. . ” too Linux and UNIX Overview 14

Kernel q UNIX and Linux are modular q The core is the kernel o Heart and brains of OS o Deals with critical system functions o E. g. , hardware interactions, resource allocation, … o Programs call on kernel for these things Linux and UNIX Overview 15

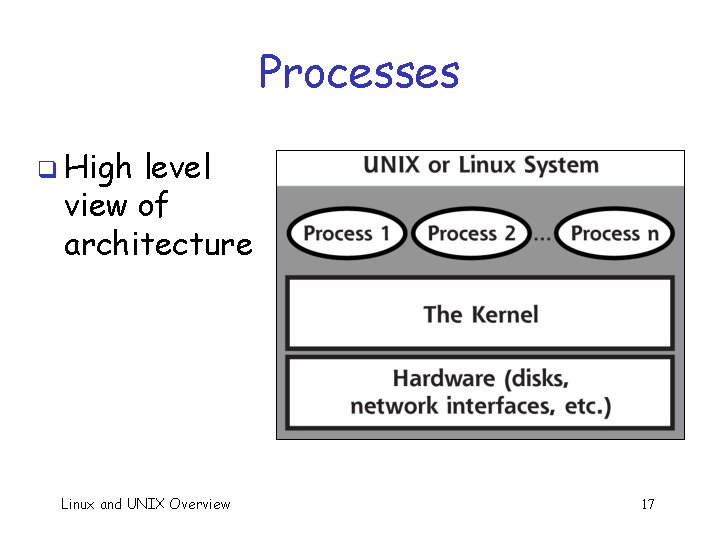
Processes q For program, kernel starts a process o Process is like a “bubble that contains the guts of a running program” o Kernel creates bubble, inflates it and tries to keep bubbles from popping each other q User programs, admin tools, services (e. g. , Web, email) are processes o May be 100 s to 1000 s of active processes o Kernel juggles these into CPU, manages memory Linux and UNIX Overview 16

Processes q High level view of architecture Linux and UNIX Overview 17

Processes q Many processes run in background q Perform system-critical functions o Printing, network activity, etc. q Known as “daemons” o Pronounced “day-muns” or “dee-muns” o Named based on their function o E. g. , SSH daemon is sshd Linux and UNIX Overview 18

Automatic Processes q Booting: kernel starts init daemon o Finishes boot process q Init o o starts many network processes Httpd --- Web server, for http/https Sshd --- SSH service Sendmail --- common UNIX email server NFS --- Network File System for sharing files between UNIX systems Linux and UNIX Overview 19

Network Services q Network service listens to network o Web server listens on TCP port 80 o Email server listens on TCP port 25 q Wait for incoming traffic q Lots of email/Web traffic, so they listen constantly q What about, say, FTP? Linux and UNIX Overview 20

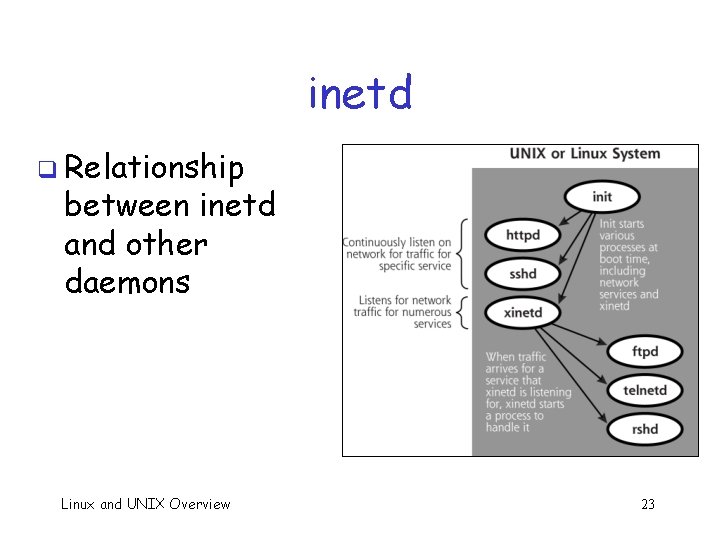
Network Services To improve efficiency… q “Internet daemon” listens for uncommon services q o inetd (“I-Net-D”) or xinetd When traffic arrives, inetd activates appropriate service q Uncommon services: echo, chargen, ftpd, telnetd, rsh, rlogin, TFTP, … q Linux and UNIX Overview 21

inetd q File /etc/inetd. conf tells inted what services to listen for: must specify o Service name --- e. g. , telnet (defined in /etc/services) o Socket type --- type of connection? o Protocol --- usually tcp or udp o Wait status --- process handles multiple connection or not o User Name --- name services should run as o Server program and arguments q inetd. conf is target of attacks Linux and UNIX Overview 22

inetd q Relationship between inetd and other daemons Linux and UNIX Overview 23

cron q Cron daemon o Schedule programs to run at predetermined times o For example, backup files at 3 am q Attackers also like cron o E. g. , shut down critical service at a particular time as part of back door Linux and UNIX Overview 24

Processes q Can also start processes manually q “path” is searched for command q To see path: echo $path o Dangerous to have “. ” in path o Why? Linux and UNIX Overview 25

Interacting with Processes q Each process has process ID (PID) q To get info on current processes o “ps -aux” (all running processes) o “lsof” (list of open files) q Can send a signal to a process o TERM to terminate, HUP to “hang up” (often rereads config), killall, etc. Linux and UNIX Overview 26

Accounts q Need an account to log in q A process runs with permissions of a given account q /etc/passwd file o One line for every account, e. g. , o sshd: *: 75: sshd Privilege separation: /var/empty: /usr/bin/false Linux and UNIX Overview 27

Passwd File q Each line contains o Login name o Hashed/encrypted password o UID number --- number assigned to account, used to determine permissions of processes o Default GID --- default group number o GECOS info --- not used by system, names, etc. o Home directory --- directory after login o Login shell --- sh, bash, csh, ksh, or another program Linux and UNIX Overview 28

Passwd File q Passwd file is world readable o Attackers like to know hashed passwords o Used for password guessing q Most modern UNIX systems do not include hashed passwords in passwd file o Instead, in “shadow” passwd file, /etc/shadow o Requires super-user privilege to access q So passwd file contains no passwords… Linux and UNIX Overview 29

Password File q After much searching… q Found my OS X hashed password is o 0 x 3 BBC 2 A 94 D 59 EB 1 D 5 D 3452 EA 6 FA 47399 B 2 A 25664 C q Where SHA 1 hash is used, with salt o 0 x 8429 A 223 q Extra credit: Find my password! Linux and UNIX Overview 30

Groups Group users together q Assign permission to the group q Stored in file /etc/group, format is q o Group name o Hashed group password --- never used o GID number --- used by the system instead of group name o Group members --- by login names Linux and UNIX Overview 31

Root account is all-powerful user q Maximum privilege --- can read, write any file q Root == superuser or “God” q UID == 0 q o “root” could be called anything, provided UID is 0 o Can be multiple root accounts Linux and UNIX Overview 32

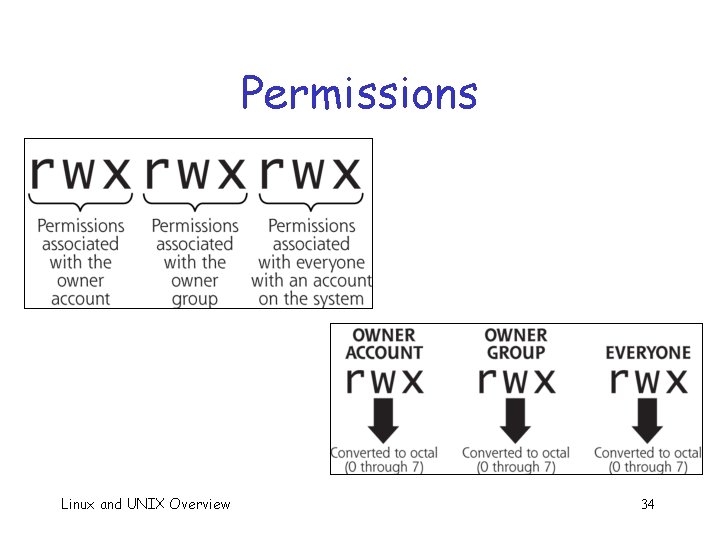
Permissions Every file has an owner and group q Owner (or root) sets permissions q o Permissions: owner, group, everybody o For each of the 3, read, write, execute o Use “ls -l” to see permissions -rw-r--r-- 1 markstam 767 Feb 6 19: 31 cs 286. txt drwxr-xr-x 40 markstam 1360 Jan 25 17: 33 docs Linux and UNIX Overview 33

Permissions Linux and UNIX Overview 34

Permissions q Change permissions using chmod o “change modes” q Give new permissions in octal o For example: chmod 745 foo o This corresponds to: rwxr--r-x Linux and UNIX Overview 35

Set. UID q Sometimes user needs to access file and they do not have permissions o Example: to change password (assuming hashes stored in shadow file) Set. UID == Set User ID q Use this so program will execute with permission of it’s owner q o As opposed to permission of user executing it o Password changing program: Set. UID root Linux and UNIX Overview 36

Set. UID q Gives “common” users lots of power o OK if used in controlled way for specific tasks q Set. UID permissions appear before 9 standard permission bits o In fact, 3 additional bits o Set. UID, Set. GID, “sticky bit” o For example: chmod 4745 foo o Shows up in “ls -l” as an s: -r-sr-xr-x 1 root wheel 75636 Jan 11 2007 /usr/bin/passwd Linux and UNIX Overview 37

Set. UID q Attackers like Set. UID programs o May be possible to exploit flaws in code (buffer overflow) to elevate privilege q New/modified Set. UID programs may be evidence of attack Linux and UNIX Overview 38

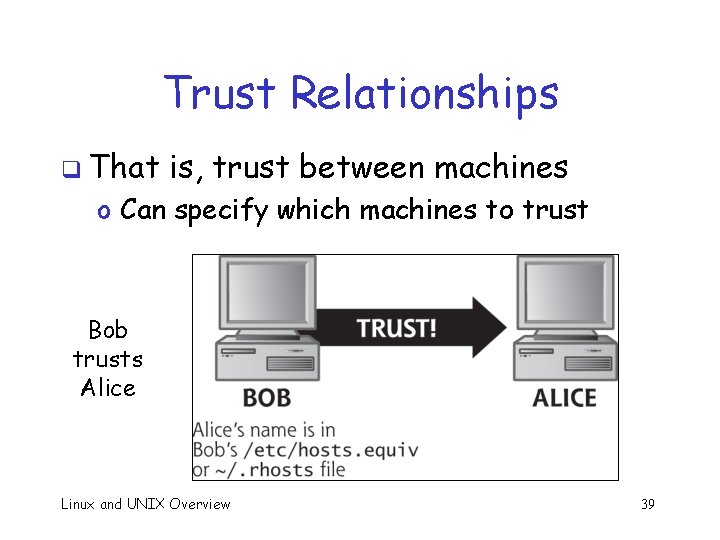
Trust Relationships q That is, trust between machines o Can specify which machines to trust Bob trusts Alice Linux and UNIX Overview 39

Trust Relationships q Unauthenticated access by users from trusted machine o Since trusted machine (presumably) already authenticated the user q If trusted, the r-commands (rlogin, rsh, rcp) require no password o Also, r-commands do not encrypt q How does Bob know trusted Alice is Alice? Linux and UNIX Overview 40

Logs and Audit q Created by syslog daemon (syslogd) q Typical log files o Secure --- logins, successful and failed o Message --- catch-all system log o Individual app logs --- for specific apps Linux and UNIX Overview 41

Logs and Audit q Forensic info also logged q Attackers like to cover their tracks q To do so, may need to manipulate… o utmp --- who is logged in o wtmp --- record of all logins and logouts o lastlog --- time and location of each user’s most recent login Linux and UNIX Overview 42

Common Network Services q Telnet --- command line remote access o No encryption, session can be hijacked, … q FTP --- file transfer o Insecure, like telnet q SSH --- encrypted “tunnel” o Then safe to use unsafe services o SSH version 1 insecure, version 2 is good Linux and UNIX Overview 43

Common Network Services q HTTP --- Web o Source of many attacks Email --- sendmail, several security issues q r-commands --- rlogin, rsh, rcp q o Considered very insecure q DNS --- domain names to IP addresses o Critical service, good one for attackers… Linux and UNIX Overview 44

Common Network Services q NFS --- transparently access files across network o NFS server “exports” directory info o Local machine can “mount” these, so files appear to be locally accessible o Like FTP without all of the trouble of FTP-ing o Of course, exporting too much may be bad q X-Window System --- X 11 (or just “X”) o The underlying GUI service in UNIX o X server controls screen, provides service o Must limit who can display/access your screen Linux and UNIX Overview 45

Conclusion UNIX/Linux q Popular OSs q More than 30 years old q Fundamental part of Internet q Widely used OSs q Platform of choice for many attackers q Linux and UNIX Overview 46

Summary Linux and UNIX Overview 47