Lesson 9 Initial Response Initial Assessment Computer Forensics

























- Slides: 35

Lesson 9 Initial Response Initial Assessment Computer Forensics

Roesch on the Threat • “The propagation of automated tools for auto-hacking with the fact that less and less sophisticated attackers getting their hands on these tools is really going to cause big problems. ” • Martin Roesch CEO, Sourcefire SNORT Lead Developer UTSA IS 6353 Security Incident Response

Initial Response UTSA IS 6353 Security Incident Response

Off-scene Response • Freeze the Incident Scene • Verbally contain the scene with instructions such as: • “Take your hands off the keyboard and step away from the computer. ” • “Physically disconnect the computer from the network. ” • “What is your name, office and telephone number. ” • “What is the hardware and operating system? ” • “I’m going to fax you a set of instruction. What is your Fax number? ” UTSA IS 6353 Security Incident Response

Incident Response Checklist Date: Time: Name: Telephone Number: Version 1. 0 Nature of Incident: Time of Incident: How was the incident detected: Current Impact of Incident: Future Impact of incident: Description of the incident: Hardware/OS/Software involved: IP and network addresses of compromised systems: Network Type: Modem: Criticality of Information: Physical location: System Administrator Name and Number: Current status of machine: Description of Hacker Actions Ongoing activity: Source Address: Malicious program involved: Denial of Service Vandalism: Indication of insider or outsider:

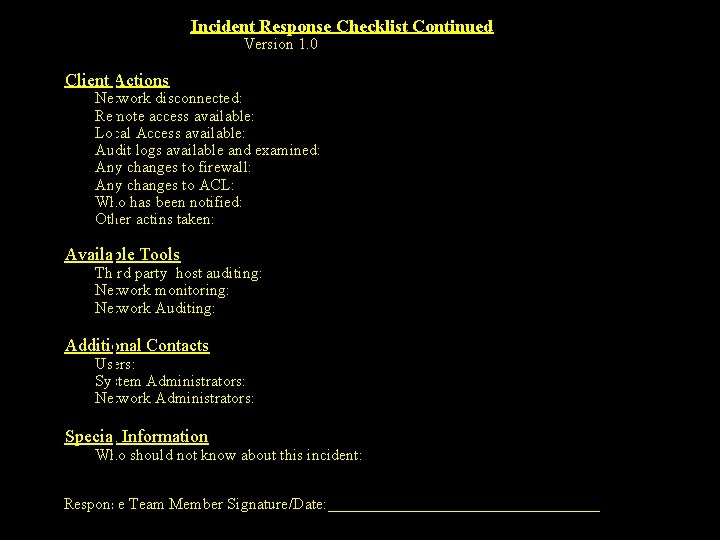
Incident Response Checklist Continued Version 1. 0 Client Actions Network disconnected: Remote access available: Local Access available: Audit logs available and examined: Any changes to firewall: Any changes to ACL: Who has been notified: Other actins taken: Available Tools Third party host auditing: Network monitoring: Network Auditing: Additional Contacts Users: System Administrators: Network Administrators: Special Information Who should not know about this incident: Response Team Member Signature/Date: _________________

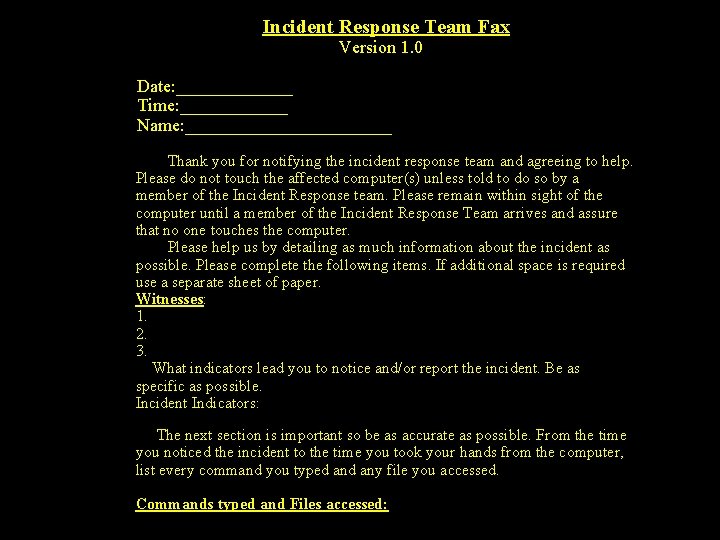
Incident Response Team Fax Version 1. 0 Date: _______ Time: ______ Name: ____________ Thank you for notifying the incident response team and agreeing to help. Please do not touch the affected computer(s) unless told to do so by a member of the Incident Response team. Please remain within sight of the computer until a member of the Incident Response Team arrives and assure that no one touches the computer. Please help us by detailing as much information about the incident as possible. Please complete the following items. If additional space is required use a separate sheet of paper. Witnesses: 1. 2. 3. What indicators lead you to notice and/or report the incident. Be as specific as possible. Incident Indicators: The next section is important so be as accurate as possible. From the time you noticed the incident to the time you took your hands from the computer, list every command you typed any file you accessed. Commands typed and Files accessed:

On-scene Response • Physically contain the scene • Two personnel, if possible, should immediately respond to the scene • Incident Scene Survey (1 st Member) • Use a portable tape recorder to: 1. Record the scene 2. Everyone present • Order everyone to leave the scene who is not directly involved in the incident 3. Interview the individual who reported the incident 4. Record, intermittently, the actions of the 2 nd individual 5. Assist the 2 nd Member UTSA IS 6353 Security Incident Response

On-Scene Response Continued • Contain the System (2 nd Member) • Ask the System Administrator to assist. • Back up the system. • Do this with forensic type tool that does bit-by-bit backup such as Safe. Back at http: //www. forensics-intl. com • Alternatively, remove the drive and seal it in a plastic bag with your notes and the notes of the individual who reported the incident • Attempt to identify the changed files through: • Tripwire http: //www. tripwire. org/ or alternatively • Expert Witness at http: //www. asrdata. com. UTSA IS 6353 Security Incident Response

Incident Investigation & Assessment

Knowing Architecture and Policies • Review Network Topology • External connectivity • Internet • Extranet • Dial-up • Remote Sites • Network Devices: Routers, Firewall, IDS • Broadcast domains • Review the Corporate Policies with regard to • Acceptable use policies • Network Monitoring • Computer Forensics UTSA IS 6353 Security Incident Response

Conducting Personnel Interviews • System administrator selected questions include: • Unusual Activity? • Administrative Access to System? . • Remote Access to Systems? • Logging Capabilities? • Current Security Precautions? • Managers selected questions include: • On-going Security tests? • Disgruntled employees? • Recently fired employee? • History of current employees? • Sensitive data or applications on the systems? • End users selected questions include: • Anomalous Behavior or Suspicious activity? UTSA IS 6353 Security Incident Response

Initial Assessment • Assess the potential security Incident • What are the incident symptoms? • Is it a security incident? • A system problem? • • • Power outage Faulty software Communication problems Procedural problem Training Problem UTSA IS 6353 Security Incident Response

Initial Evaluation • Evaluate the severity & scope of incident • • • What specifically happened? What was the entry point? What local computers/networks were affected? What remote computers/networks were affected? What information was affected? • What was its value to the organization? • What further can possibly occur? • Who else knows about the incident? • What are the estimated time/resources required to handle the incident. UTSA IS 6353 Security Incident Response

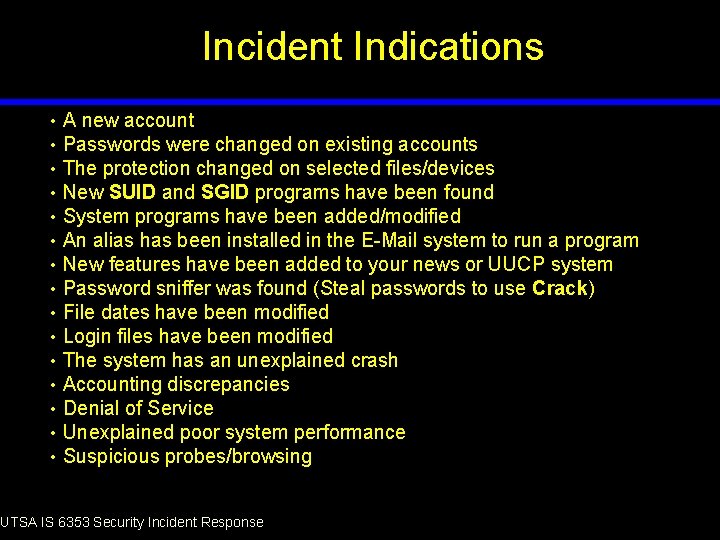
Incident Indications • • • • A new account Passwords were changed on existing accounts The protection changed on selected files/devices New SUID and SGID programs have been found System programs have been added/modified An alias has been installed in the E-Mail system to run a program New features have been added to your news or UUCP system Password sniffer was found (Steal passwords to use Crack) File dates have been modified Login files have been modified The system has an unexplained crash Accounting discrepancies Denial of Service Unexplained poor system performance Suspicious probes/browsing UTSA IS 6353 Security Incident Response

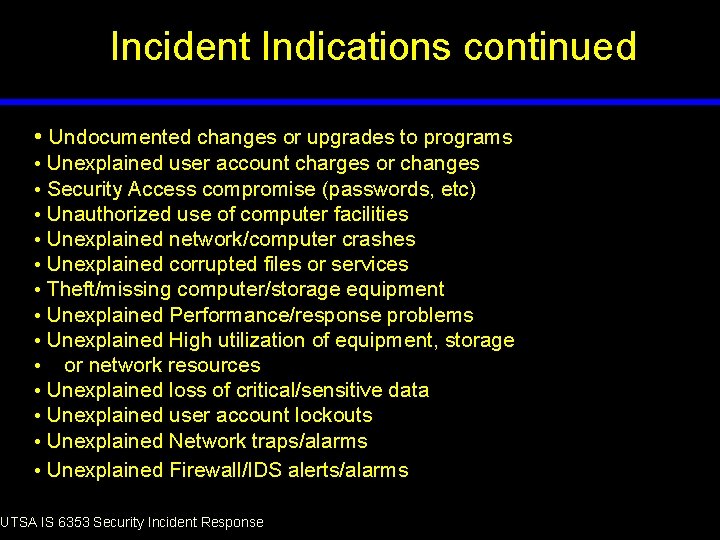
Incident Indications continued • Undocumented changes or upgrades to programs • Unexplained user account charges or changes • Security Access compromise (passwords, etc) • Unauthorized use of computer facilities • Unexplained network/computer crashes • Unexplained corrupted files or services • Theft/missing computer/storage equipment • Unexplained Performance/response problems • Unexplained High utilization of equipment, storage • or network resources • Unexplained loss of critical/sensitive data • Unexplained user account lockouts • Unexplained Network traps/alarms • Unexplained Firewall/IDS alerts/alarms UTSA IS 6353 Security Incident Response

Initial Steps • All systems/networks are suspect until the actual extent of the incident is known • Verify integrity of all site computers • Verify integrity of all site networks • Verify integrity of all files/directories (checksums) • Compare system files with backups or initial distributions • Compare software application with the baseline • Analyze the documentation, files and security logs Be careful not to contaminate the crime scene UTSA IS 6353 Security Incident Response

Computer Forensics

Pathways All data leaves a trail. The search for data leaves a trail. The erasure of data leaves a trail. The absence of data, under the right circumstances, can leave the clearest trail of all. “This Alien Shore”, C. S. Friedman (C) 1998 UTSA IS 6353 Security Incident Response

Computer Forensics Basic Principles • Principle 1 - Preserve the evidence in an unchanged state • Principle 2 - Document the investigative process…thoroughly and completely Investigate as if LE will be called in and the attackers will be prosecuted UTSA IS 6353 Security Incident Response

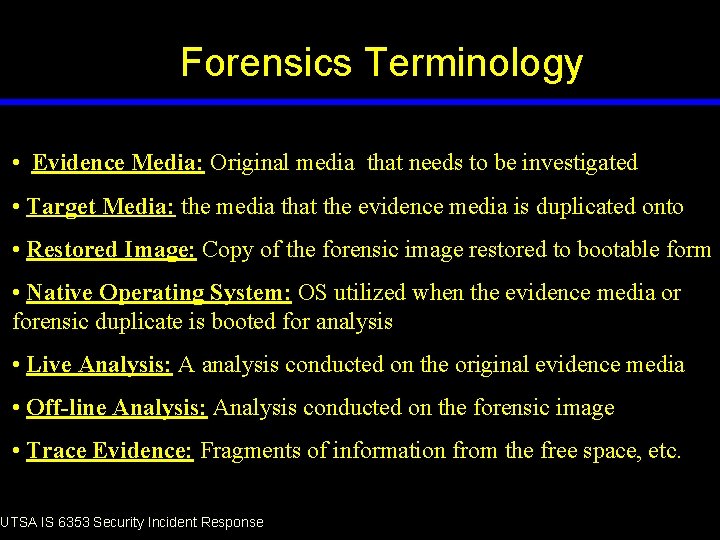
Forensics Terminology • Evidence Media: Original media that needs to be investigated • Target Media: the media that the evidence media is duplicated onto • Restored Image: Copy of the forensic image restored to bootable form • Native Operating System: OS utilized when the evidence media or forensic duplicate is booted for analysis • Live Analysis: A analysis conducted on the original evidence media • Off-line Analysis: Analysis conducted on the forensic image • Trace Evidence: Fragments of information from the free space, etc. UTSA IS 6353 Security Incident Response

Best Evidence Rule • Common Mistakes include: • Altering time and date stamps • Killing rogue processes • Patching the system before the investigation • Not recording commands executed on the system • Using un-trusted commands and binaries • Writing over potential evidence: • Installing software on the evidence media • Running program that store output on evidence media. UTSA IS 6353 Security Incident Response • FRE 1001(3) ". . . if data are stored on a computer or similar device, any printout or other output readable by sight, shown to reflect the data accurately, is an 'Original. '"

Evidence Chain of Custody • Prosecution is responsible for proving that which is presented in court is that which was originally collected. An Evidence Chain of Custody must be maintained • Create an Evidence Tag at the time of collection • A designated Evidence Custodian with a Laptop to generate the Evidence Tags • Date and Time • Case Number • Evidence Tag number • Evidence Description • Individual receiving the evidence and Date • Each time the evidence moves from one person to another or from one media to another must be recorded UTSA IS 6353 Security Incident Response

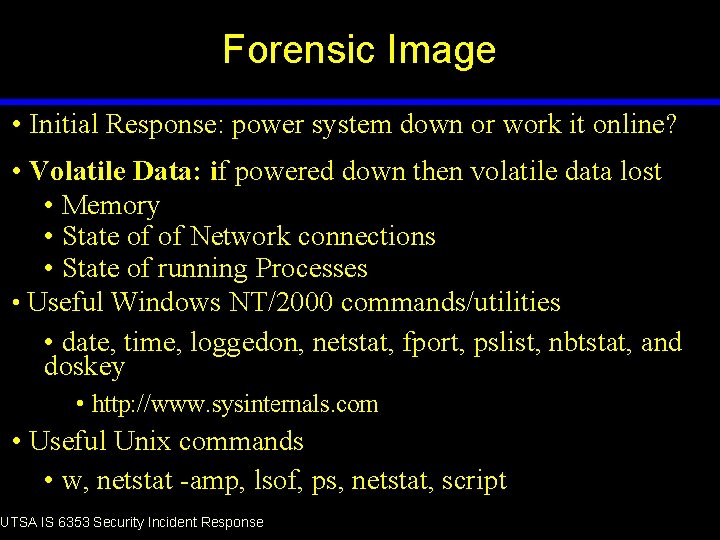
Forensic Image • Initial Response: power system down or work it online? • Volatile Data: if powered down then volatile data lost • Memory • State of of Network connections • State of running Processes • Useful Windows NT/2000 commands/utilities • date, time, loggedon, netstat, fport, pslist, nbtstat, and doskey • http: //www. sysinternals. com • Useful Unix commands • w, netstat -amp, lsof, ps, netstat, script UTSA IS 6353 Security Incident Response

BIOS Review • Review the Basic Input/Output System (BIOS) before beginning a duplication to determine: • Basic geometry of the hard drive on the target System • Document the hard drive setting to include maximum capacity, cylinders, heads, and sectors • For proper recovery by the original OS the partitions should be aligned on the cylinder boundaries • Determine the Boot Sequence on the target System - Floppy drives - Network - PCMCIA Card - CD-Rom - Hard Drive Throughout the forensics process do not forget the basics…assume nothing. UTSA IS 6353 Security Incident Response

Forensic Duplication • Three Forensic Duplication Approaches 1. Remove the storage media and connect it to a Forensics Workstation • Document the system details to include serial number, jumper settings, visible damage, etc • Remove media from target system and connect it to the forensics workstation • Image the media using Safeback, the Unix dd utility or En. Case Forensics Workstations Safeback En. Case Disk. Pro UTSA IS 6353 Security Incident Response http: //www. computer-forensics. com http: //www. forensics-intl. com/safeback. html http: //guidancesoftware. com http: //www. e-mart. com/www/cnr. html

Forensic Duplication Continued 2. Attach a hard drive to the Target Computer • Make sure the target computer works as expected 3. Image the storage media by transmitting the disk image over a closed network to the forensics Workstation • Establish a point-to-point interface from evidence system to forensics workstation using an Ethernet Switch of Ethernet cross-connect cable • Perform MD 5 computation on both the original and target system Don’t forget to document the process you used UTSA IS 6353 Security Incident Response

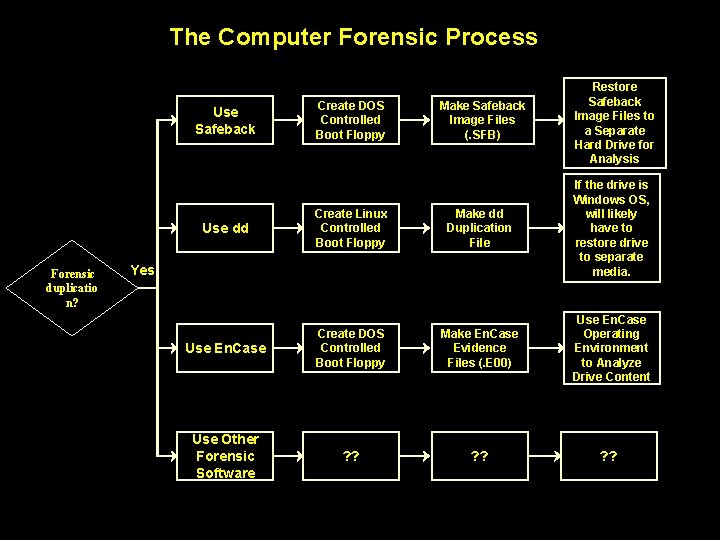
The Computer Forensic Process Make Safeback Image Files (. SFB) Restore Safeback Image Files to a Separate Hard Drive for Analysis Make dd Duplication File If the drive is Windows OS, will likely have to restore drive to separate media. Use En. Case Create DOS Controlled Boot Floppy Make En. Case Evidence Files (. E 00) Use En. Case Operating Environment to Analyze Drive Content Use Other Forensic Software ? ? Use Safeback Use dd Forensic duplicatio n? Create DOS Controlled Boot Floppy Create Linux Controlled Boot Floppy Yes

Forensic Analysis • Physical Analysis--performed on the forensic image only! • Perform a String Search • Sting Search http: //www. maresware. com/maresware/forensic 1. htm • Perform a Search and Extract • Looks for file types • File Formats http: //www. wotsit. org/ • Extract File slack and/Free Space • Free Space: Hard Drive space not allocated to a file and deleted file fragments. • Slack Space: Space left when a minimum block size is not filled by a write operation. • NTI Tool Suite http: //www. forensics-intl. com/ UTSA IS 6353 Security Incident Response

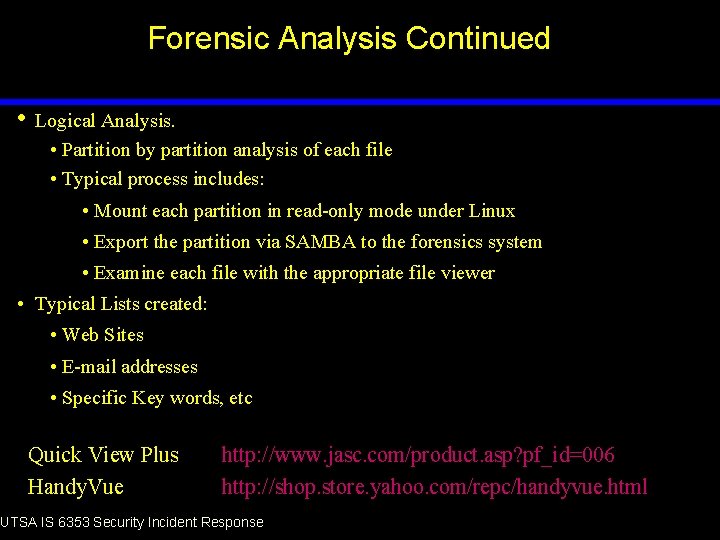
Forensic Analysis Continued • Logical Analysis. • Partition by partition analysis of each file • Typical process includes: • Mount each partition in read-only mode under Linux • Export the partition via SAMBA to the forensics system • Examine each file with the appropriate file viewer • Typical Lists created: • Web Sites • E-mail addresses • Specific Key words, etc Quick View Plus Handy. Vue http: //www. jasc. com/product. asp? pf_id=006 http: //shop. store. yahoo. com/repc/handyvue. html UTSA IS 6353 Security Incident Response

Common Forensics Mistakes • Failure to Maintain through complete documentation • Failure to control access to digital information • Underestimate the scope of the incident • Failure to report the incident in a timely manner • Failure to provide accurate information • No incident response plan Plan, control, document, report UTSA IS 6353 Security Incident Response

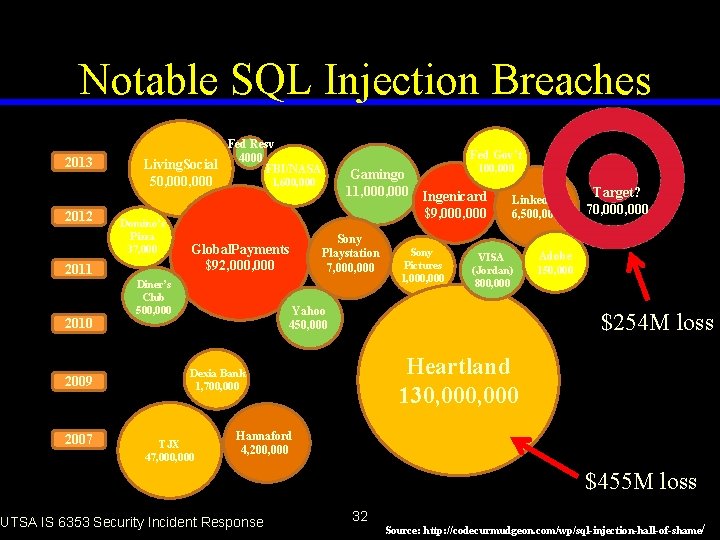
Notable SQL Injection Breaches 2013 Fed Resv 4000 Living. Social FBI/NASA 50, 000 2012 Domino’s Pizza 37, 000 2011 2010 2009 2007 Fed Gov’t 100, 000 Gamingo 11, 000 Ingenicard $9, 000 1, 600, 000 Global. Payments $92, 000 Diner’s Club 500, 000 Sony Playstation 7, 000 Sony Pictures 1, 000 Linked. In 6, 500, 000 VISA (Jordan) 800, 000 Yahoo 450, 000 Adobe 150, 000 $254 M loss Heartland 130, 000 Dexia Bank 1, 700, 000 TJX 47, 000 Target? 70, 000 Hannaford 4, 200, 000 $455 M loss UTSA IS 6353 Security Incident Response 32 Source: http: //codecurmudgeon. com/wp/sql-injection-hall-of-shame/

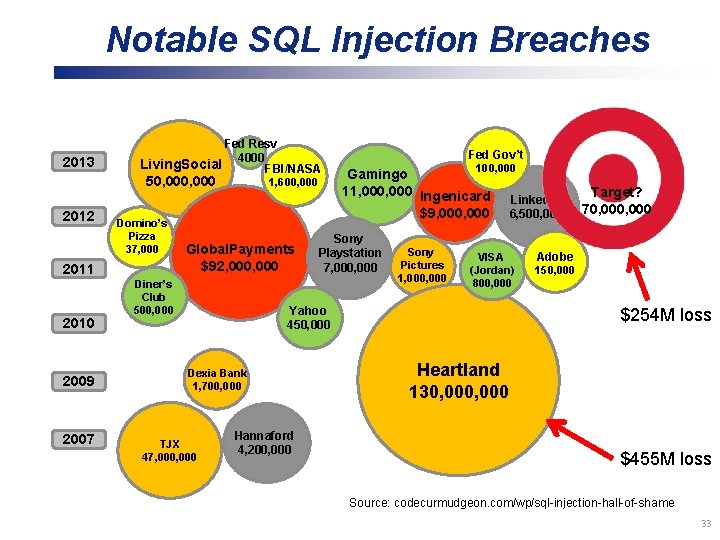
Notable SQL Injection Breaches 2013 Fed Resv 4000 Living. Social FBI/NASA 50, 000 2012 Domino’s Pizza 37, 000 2011 2010 2009 2007 1, 600, 000 Global. Payments $92, 000 Diner’s Club 500, 000 Fed Gov’t 100, 000 Gamingo 11, 000 Ingenicard $9, 000 Sony Playstation 7, 000 Sony Pictures 1, 000 VISA (Jordan) 800, 000 Yahoo 450, 000 Dexia Bank 1, 700, 000 TJX 47, 000 Linked. In 6, 500, 000 Target? 70, 000 Adobe 150, 000 $254 M loss Heartland 130, 000 Hannaford 4, 200, 000 $455 M loss Source: http: //codecurmudgeon. com/wp/sql-injection-hall-of-shame/ Source: codecurmudgeon. com/wp/sql-injection-hall-of-shame 33

Closing Thought • “If an organization is going to make the effort to secure its systems it must make every effort to respond to security breaches…the only failure to good security planning is to fail to plan a response action for a breach in that security. ” • Rob Kaufman UTSA IS 6353 Security Incident Response

Summary • • Prepare for incidents Perform initial assessment Evaluate crime scene Conduct forensics--D 3 UTSA IS 6353 Security Incident Response