Lecturer 2 Classical Cryptography Substitution Cipher Newroz N

Lecturer 2: Classical Cryptography Substitution Cipher Newroz N. Abdulrazaq Science College- Department of Computer Science & I. T. newroz. abudlrazaq@su. edu. kurd Mobile: 07504052680 1
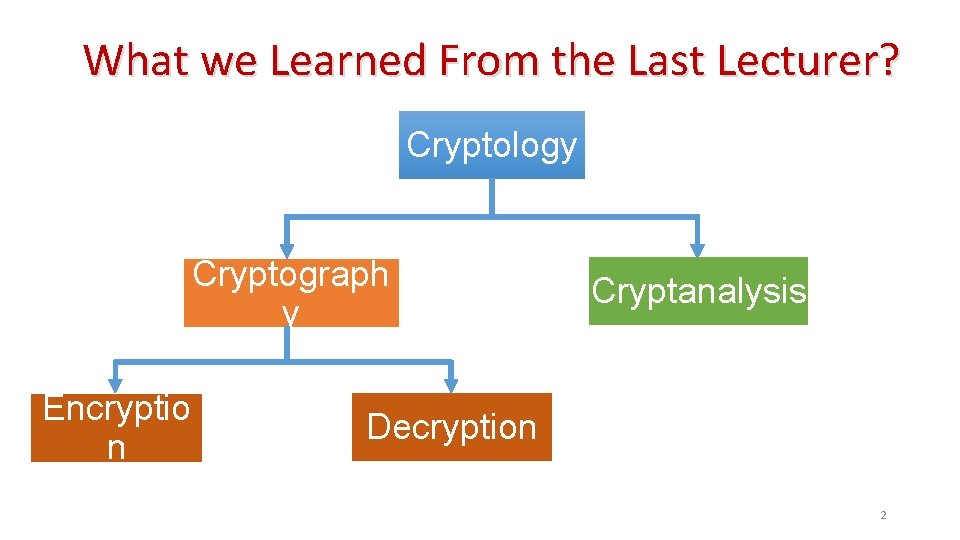
What we Learned From the Last Lecturer? Cryptology Cryptograph y Encryptio n Cryptanalysis Decryption 2

Today Lecturer Outlines ü Types of Cryptography. ü Types of Classical Cryptography. ü Substitution Cipher. ü Caesar Cipher. 3

Types of Cryptography Classical Cipher: is a type of cipher that was used historically but now has fallen. is Modern cryptography: the cornerstone of computer and communications security. Its foundation is based on various concepts of mathematics such as number theory, and probability theory. 4

Before Computer Era v Substitution Cipher. v Caesar Cipher. v Atbash Cipher. v Transposition Cipher v Columnar Cipher. v Route Cipher. 5
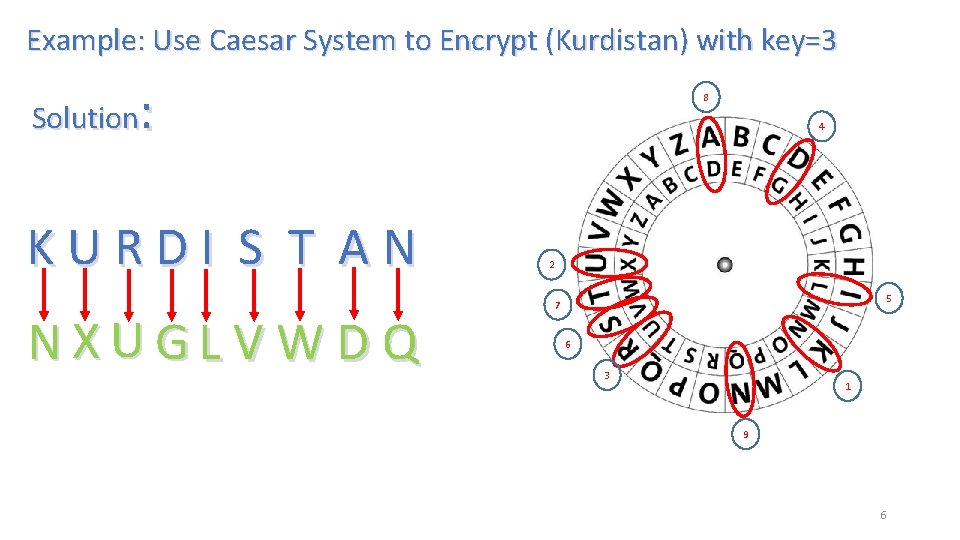
Example: Use Caesar System to Encrypt (Kurdistan) with key=3 : 8 Solution KURDI S T AN NXUGL V W D Q 4 2 5 7 6 3 1 9 6
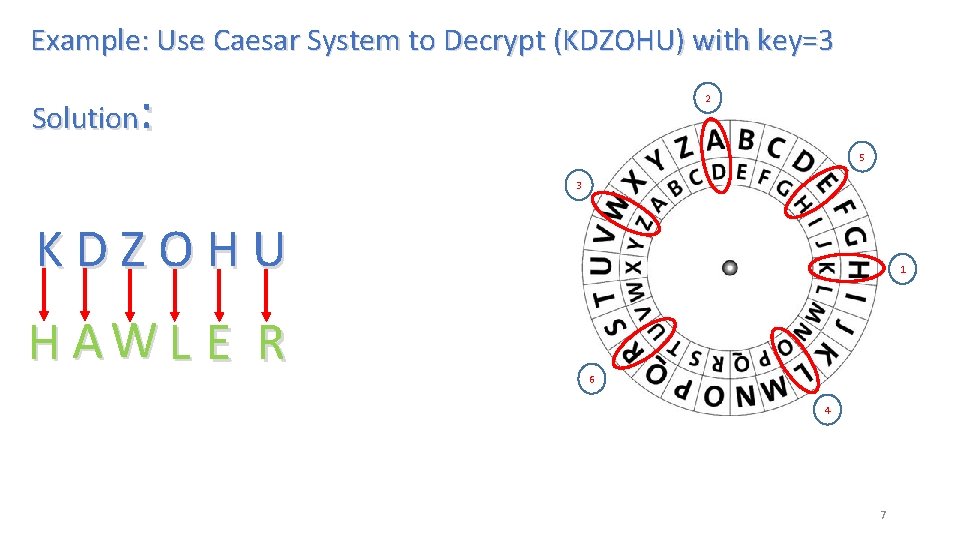
Example: Use Caesar System to Decrypt (KDZOHU) with key=3 : 2 Solution 5 3 KDZOHU H AW L E R 1 6 4 7

Conclusion Security objectives addressed by cryptography: ü Confidentiality: Cryptography. ü Classical Ciphers have been Fallen. ü Modern Cipher is a Cornerstone of Computer Era. ü Caesar Cipher: Shifting Letters. 8

References ü William J. Buchanan, Cryptography, River Publishers, Denmark 2017. ü Hans Delfs, Helmut Knebl, Introduction to Cryptography Principles and Applications, 3 rd ed. , Springer, 2016. ü Wade Trappe, Lawrence Washington, Introduction to Cryptography with Coding Theory, 2 nd ed. , USA Pearson, 2006. 9

Home Work ü Use Caesar System to Encrypt the Word “Sulaimania” with key=19? ü Use Caesar System to Decrypt the Word “KZNCHVMBV” with key=5? ü What is the difference between Cryptography & Cryptanalysis? 10

Next Lecture ü Transposition Cipher. ü Methods that Use Transposition Cipher: üColumnar Cipher. üRoute Cipher. 11

12
- Slides: 12