Lecture3 Application Layer Chapter2 in textbook A note

Lecture#3 Application Layer Chapter#2 in textbook A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in Power. Point form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: v If you use these slides (e. g. , in a class) that you mention their source (after all, we’d like people to use our book!) v If you post any slides on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Thanks and enjoy! JFK/KWR Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 All material copyright 1996 -2012 J. F Kurose and K. W. Ross, All Rights Reserved 2 -1
Chapter 2: Application Layer Goals: v conceptual, implementation aspects of network application protocols § transport-layer service models § client-server paradigm § peer-to-peer paradigm v learn about protocols by examining popular application-level protocols § § v HTTP FTP SMTP / POP 3 / IMAP DNS programming network applications § socket API 2
Application Layer v v v The application layer is closest to the end user. Network applications enable users to send and receive data with ease. The application layer acts as interface between the applications and the underlying network. Application layer protocols help exchange data between programs running on the source and destination hosts. The TCP/IP application layer performs the functions of the upper three layers of the OSI model. Common application layer protocols include: HTTP, FTP, TFTP, DNS.
Presentation and Session Layer v The presentation layer has three primary functions: o Format data o Compress data o Encrypt data v v Common standards for video include Quick. Time and Motion Picture Experts Group (MPEG). Common graphic image formats are: • Graphics Interchange Format (GIF) • Joint Photographic Experts Group (JPEG) • Portable Network Graphics (PNG) format
Presentation and Session Layer (cont. ) v v The session layer creates and maintains dialogs between source and destination applications. The session layer handles the exchange of information to initiate dialogs, keep them active, and to restart sessions that are disrupted or idle for a long period of time.
TCP/IP Application Layer Protocols v v v TCP/IP application protocols specify the format and control information necessary for common Internet functions. Application layer protocols must be implemented in both the source and destination devices. Application layer protocols implemented on the source and destination host must be compatible to allow communication.

Some network apps v v v v e-mail web instant messaging remote login P 2 P file sharing multi-user network games streaming stored video clips v v social networks voice over IP real-time video conferencing grid computing 7
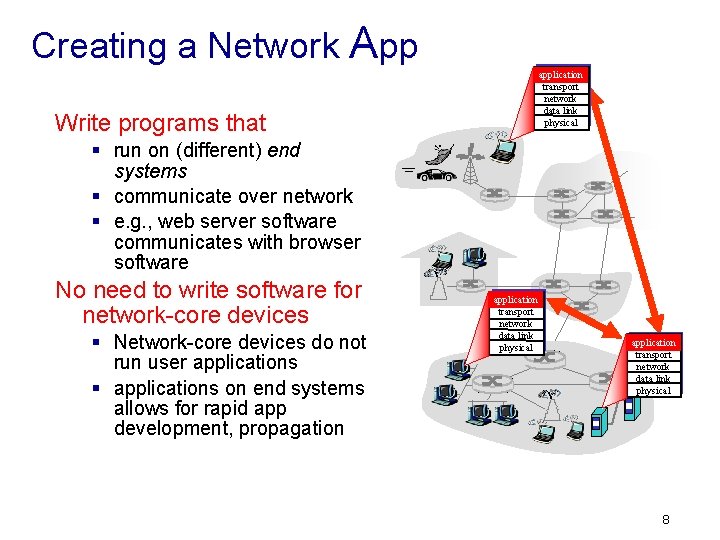
Creating a Network App application transport network data link physical Write programs that § run on (different) end systems § communicate over network § e. g. , web server software communicates with browser software No need to write software for network-core devices § Network-core devices do not run user applications § applications on end systems allows for rapid app development, propagation application transport network data link physical 8

Topics v v Principles of network applications Web and HTTP FTP Electronic Mail § SMTP, POP 3, IMAP v DNS 9

Application architectures v Client-server (CS) § Including data centers / cloud computing v v Peer-to-peer (P 2 P) Hybrid of client-server and P 2 P 10
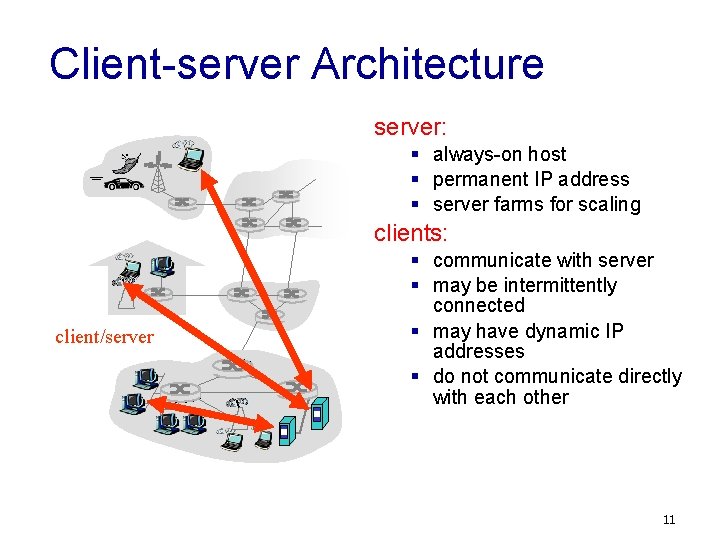
Client-server Architecture server: § always-on host § permanent IP address § server farms for scaling clients: client/server § communicate with server § may be intermittently connected § may have dynamic IP addresses § do not communicate directly with each other 11
Server Example - Google Data Centers v v v Estimated cost of data center: $600 M Google spent $2. 4 B in 2007 on new data centers Each data center uses 50 -100 megawatts of power 12
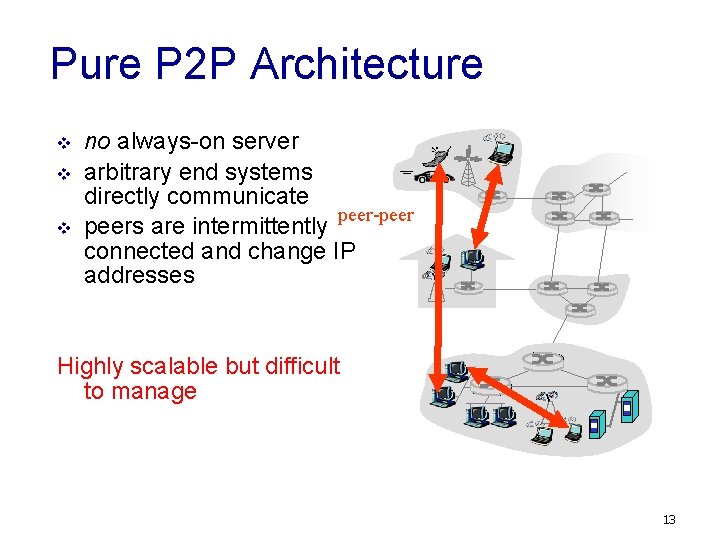
Pure P 2 P Architecture v v v no always-on server arbitrary end systems directly communicate peer-peers are intermittently connected and change IP addresses Highly scalable but difficult to manage 13
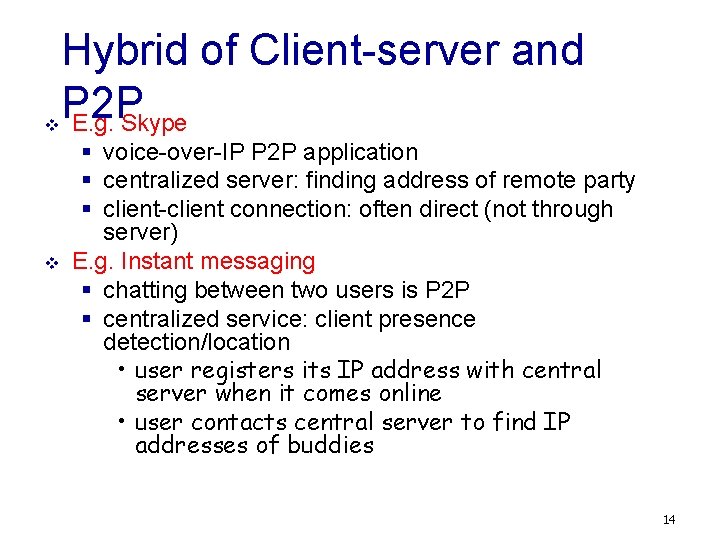
v v Hybrid of Client-server and P 2 P E. g. Skype § voice-over-IP P 2 P application § centralized server: finding address of remote party § client-client connection: often direct (not through server) E. g. Instant messaging § chatting between two users is P 2 P § centralized service: client presence detection/location • user registers its IP address with central server when it comes online • user contacts central server to find IP addresses of buddies 14
Processes Communicating Process: program running within a host. v Within same host, two processes communicate using inter-process communication (defined by OS). v Processes in different hosts communicate by exchanging messages Client process: process that initiates communication Server process: process that waits to be contacted • Note: applications with P 2 P architectures have client processes & server processes 15
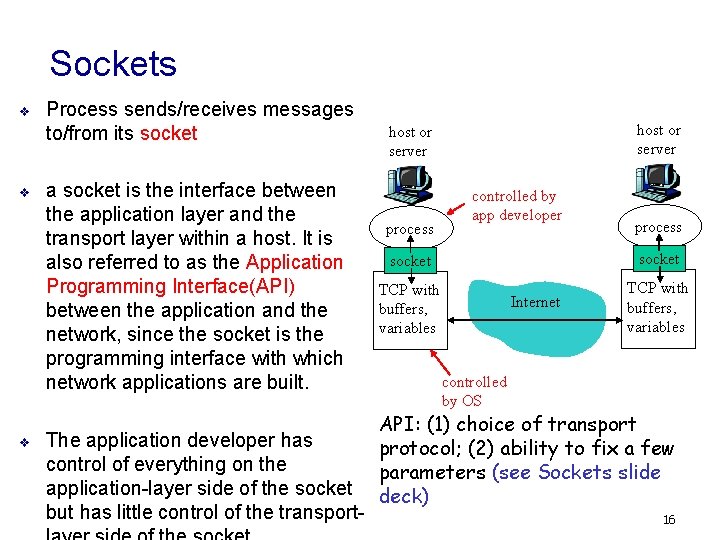
Sockets v v v Process sends/receives messages to/from its socket a socket is the interface between the application layer and the transport layer within a host. It is also referred to as the Application Programming Interface(API) between the application and the network, since the socket is the programming interface with which network applications are built. The application developer has control of everything on the application-layer side of the socket but has little control of the transport- host or server process controlled by app developer process socket TCP with buffers, variables Internet TCP with buffers, variables controlled by OS API: (1) choice of transport protocol; (2) ability to fix a few parameters (see Sockets slide deck) 16
Addressing Processes v In the Internet, the host is identified by its IP address v In addition to knowing the address of the host to which a message is destined, the sending process must also identify the receiving process (more specifically, the receiving socket) running in the host. This information is needed because in general a host could be running many network applications. § Recall: the application at the sending side pushes messages through the socket. At the other side of the socket, the transport-layer protocol has the responsibility of getting the messages to the socket of the receiving process. v A destination port number serves this purpose. Popular applications have been assigned specific port numbers. v Example port numbers: v § HTTP server: 80 § Mail server: 25 Identifier includes both IP address and port numbers associated with process on host. 17
App-layer Protocol Defines v Types of messages exchanged, § e. g. , request, response v Message syntax: § what fields in messages & how fields are delineated v Message semantics § meaning of information in fields v Public-domain protocols: v Defined in RFCs v allows for interoperability v e. g. , HTTP, SMTP, Bit. Torrent Proprietary protocols: v e. g. , Skype, ppstream Rules for when and how processes send & respond to messages 18
What Transport Service Does an App Need? Throughput Data loss v some apps (e. g. , audio) can • some apps (e. g. , multimedia) require tolerate some loss minimum amount of v other apps (e. g. , file throughput to be “effective” transfer, telnet) require • Ex: real-time audio/video 100% reliable data transfer Timing v some apps (e. g. , Internet telephony, interactive games) require low delay to be “effective” • other apps (“elastic apps”) make use of whatever throughput they get • Ex: Electronic mail, file transfer, and Web transfers. . Security 19
Internet Transport Protocols Services TCP service: v v v connection-oriented: setup required between client and server processes reliable transport between sending and receiving process flow control: sender won’t overwhelm receiver congestion control: throttle sender when network overloaded does not provide: timing, minimum throughput guarantees, security UDP service: v v unreliable data transfer between sending and receiving process does not provide: connection setup, reliability, flow control, congestion control, timing, throughput guarantee, or security Q: why bother? Why is there a UDP? note : more details will be given in the next lecture. 20
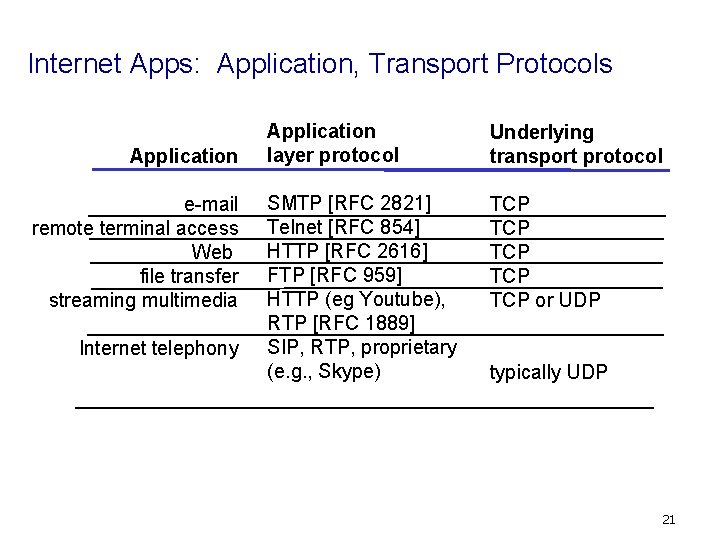
Internet Apps: Application, Transport Protocols Application e-mail remote terminal access Web file transfer streaming multimedia Internet telephony Application layer protocol Underlying transport protocol SMTP [RFC 2821] Telnet [RFC 854] HTTP [RFC 2616] FTP [RFC 959] HTTP (eg Youtube), RTP [RFC 1889] SIP, RTP, proprietary (e. g. , Skype) TCP TCP TCP or UDP typically UDP 21
Topices v v Principles of network applications Web and HTTP FTP Electronic Mail § SMTP, POP 3, IMAP v v P 2 P applications Socket programming with UDP Socket programming with TCP DNS 22
Web and HTTP First some jargon v Web page consists of objects v Object can be HTML file, JPEG image, Java applet, audio file, … v Web page consists of base HTML-file which includes several referenced objects v Each object is addressable by a URL v Example URL: www. someschool. edu/some. Dept/pic. gif host name path name 23
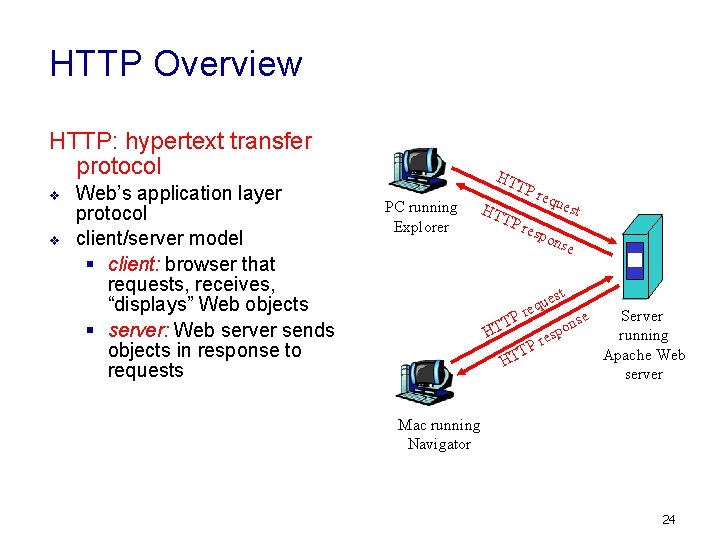
HTTP Overview HTTP: hypertext transfer protocol v v Web’s application layer protocol client/server model § client: browser that requests, receives, “displays” Web objects § server: Web server sends objects in response to requests HT TP PC running Explorer HT TP req ues resp ons t e t P T HT ues q e r e HT r TP e ns spo Server running Apache Web server Mac running Navigator 24
HTTP Overview (continued) Uses TCP: v v v client initiates TCP connection (creates socket) to server, port 80 server accepts TCP connection from client HTTP messages (application-layer protocol messages) exchanged between browser (HTTP client) and Web server (HTTP server) TCP connection closed HTTP need not worry about lost data or the details of how TCP recovers from loss or reordering of data within the network. That is the job of TCP and the protocols in the lower layers of the protocol stack. 25
HTTP connections Nonpersistent HTTP v At most one object is sent over a TCP connection. Persistent HTTP v Multiple objects can be sent over single TCP connection between client and server. 26
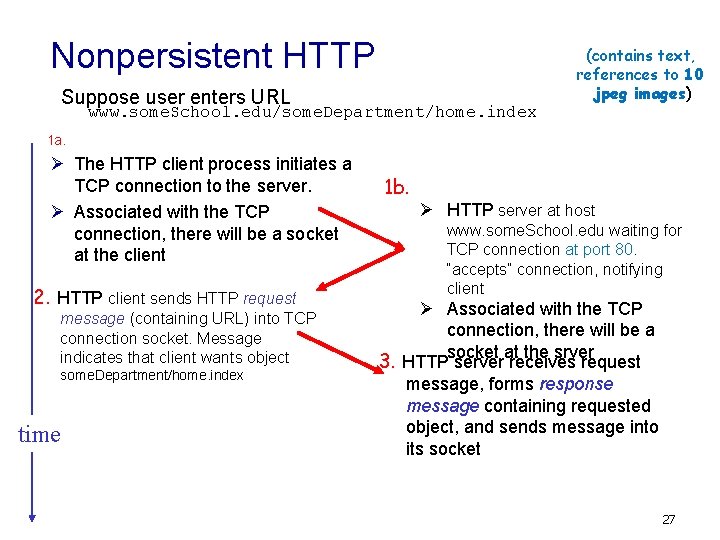
Nonpersistent HTTP Suppose user enters URL www. some. School. edu/some. Department/home. index (contains text, references to 10 jpeg images) 1 a. Ø The HTTP client process initiates a TCP connection to the server. Ø Associated with the TCP connection, there will be a socket at the client 2. HTTP client sends HTTP request message (containing URL) into TCP connection socket. Message indicates that client wants object some. Department/home. index time 1 b. Ø HTTP server at host www. some. School. edu waiting for TCP connection at port 80. “accepts” connection, notifying client Ø Associated with the TCP connection, there will be a at the srver 3. HTTPsocket server receives request message, forms response message containing requested object, and sends message into its socket 27
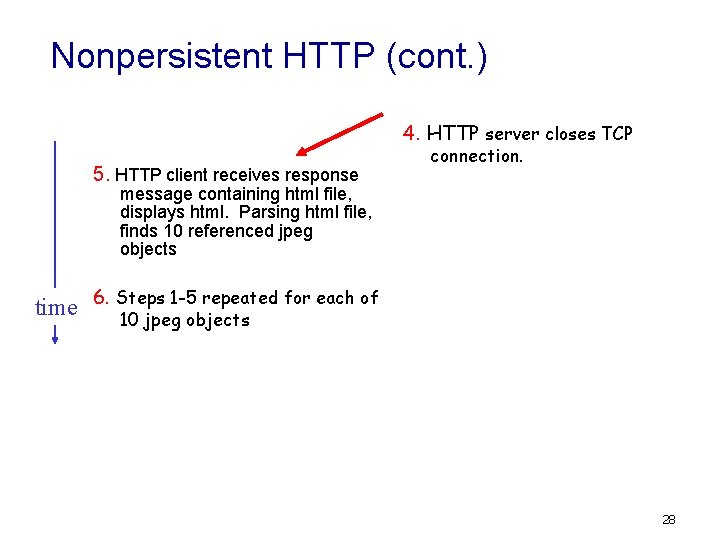
Nonpersistent HTTP (cont. ) 4. HTTP server closes TCP 5. HTTP client receives response connection. message containing html file, displays html. Parsing html file, finds 10 referenced jpeg objects 1 -5 repeated for each of time 6. Steps 10 jpeg objects 28
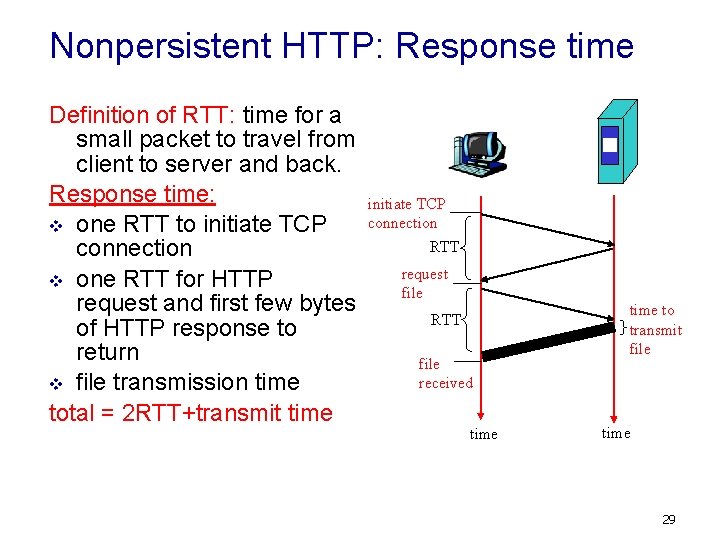
Nonpersistent HTTP: Response time Definition of RTT: time for a small packet to travel from client to server and back. Response time: v one RTT to initiate TCP connection v one RTT for HTTP request and first few bytes of HTTP response to return v file transmission time total = 2 RTT+transmit time initiate TCP connection RTT request file RTT file received time to transmit file time 29
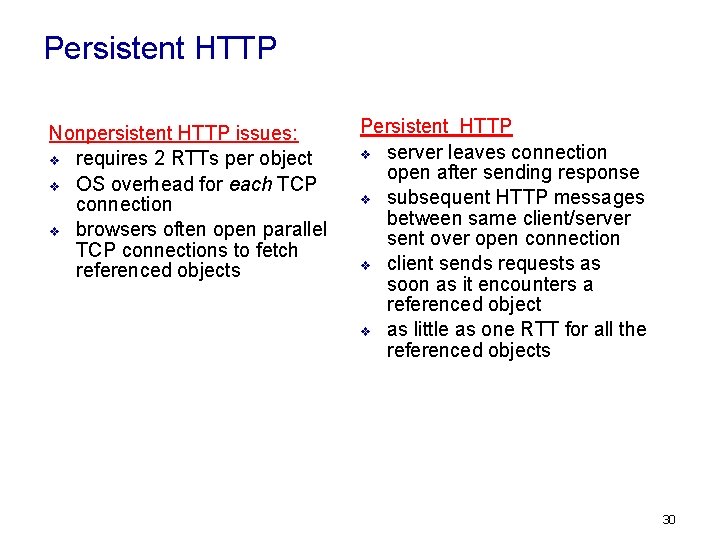
Persistent HTTP Nonpersistent HTTP issues: v requires 2 RTTs per object v OS overhead for each TCP connection v browsers often open parallel TCP connections to fetch referenced objects Persistent HTTP v server leaves connection open after sending response v subsequent HTTP messages between same client/server sent over open connection v client sends requests as soon as it encounters a referenced object v as little as one RTT for all the referenced objects 30

HTTP request message v v two types of HTTP messages: request, response HTTP request message: § ASCII (human-readable format) request line (GET, POST, HEAD commands) GET /somedir/page. html HTTP/1. 1 Host: www. someschool. edu User-agent: Mozilla/4. 0 header Connection: close lines Accept-language: fr Carriage return, line feed indicates end of message (extra carriage return, line feed) 31
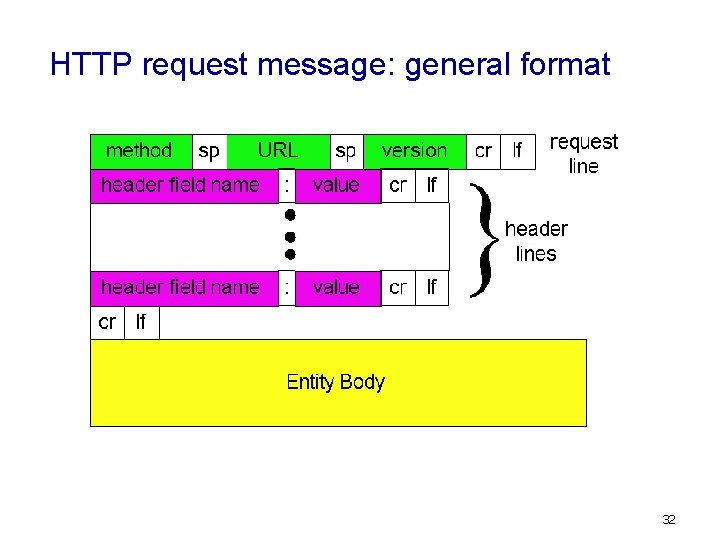
HTTP request message: general format 32
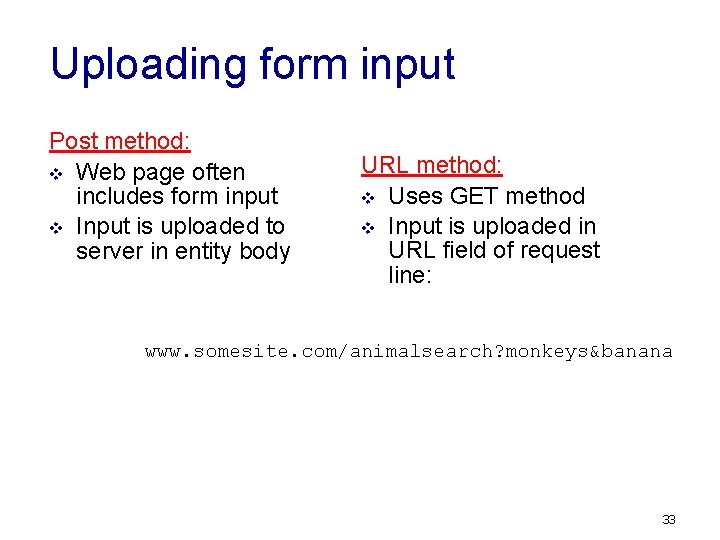
Uploading form input Post method: v Web page often includes form input v Input is uploaded to server in entity body URL method: v Uses GET method v Input is uploaded in URL field of request line: www. somesite. com/animalsearch? monkeys&banana 33
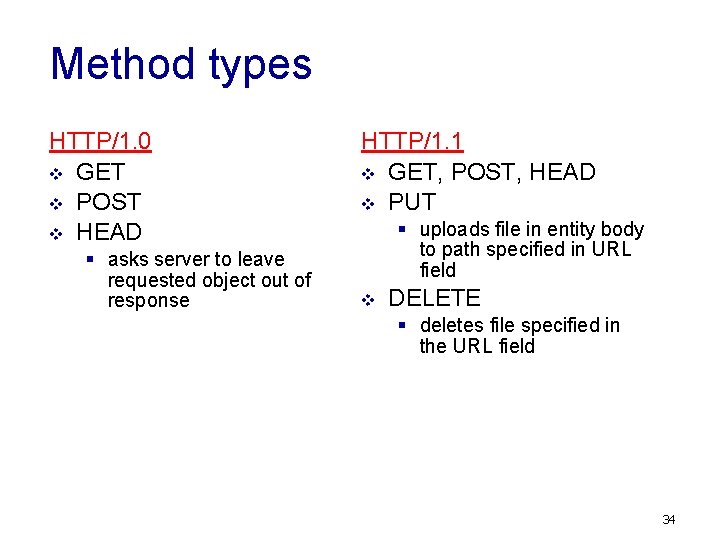
Method types HTTP/1. 0 v GET v POST v HEAD § asks server to leave requested object out of response HTTP/1. 1 v GET, POST, HEAD v PUT § uploads file in entity body to path specified in URL field v DELETE § deletes file specified in the URL field 34
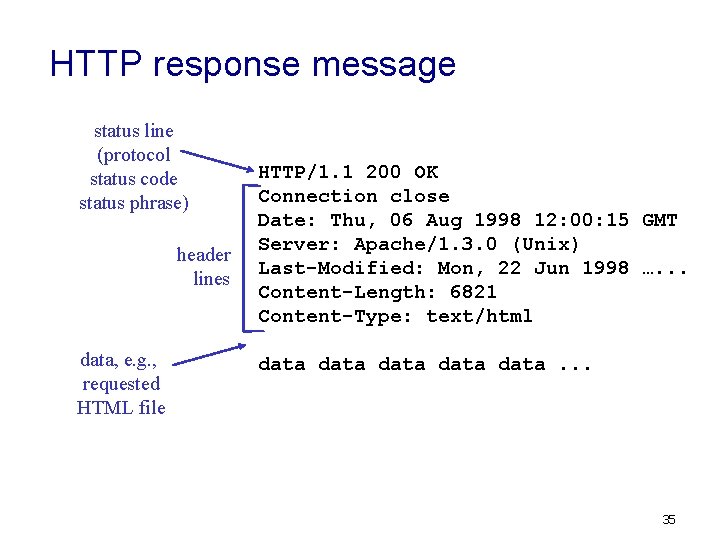
HTTP response message status line (protocol status code status phrase) header lines data, e. g. , requested HTML file HTTP/1. 1 200 OK Connection close Date: Thu, 06 Aug 1998 12: 00: 15 GMT Server: Apache/1. 3. 0 (Unix) Last-Modified: Mon, 22 Jun 1998 …. . . Content-Length: 6821 Content-Type: text/html data data. . . 35
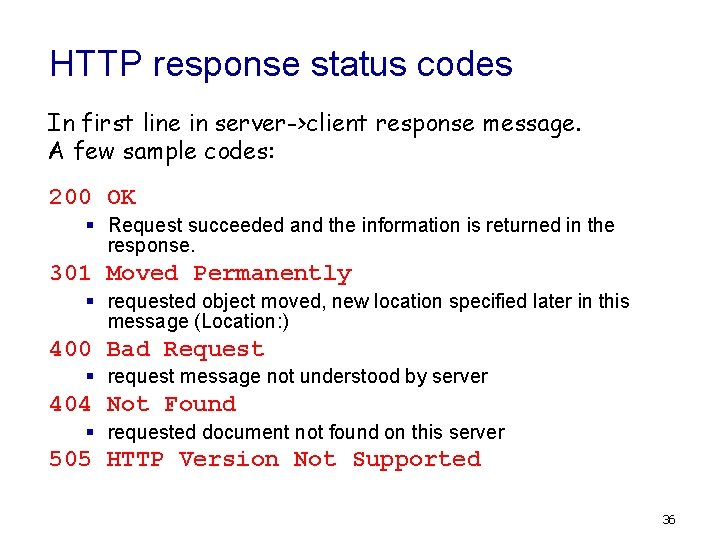
HTTP response status codes In first line in server->client response message. A few sample codes: 200 OK § Request succeeded and the information is returned in the response. 301 Moved Permanently § requested object moved, new location specified later in this message (Location: ) 400 Bad Request § request message not understood by server 404 Not Found § requested document not found on this server 505 HTTP Version Not Supported 36

User-server State: Cookies Example: Many major Web sites use v Susan always access cookies Internet always from PC Four components: v visits specific e-commerce 1) cookie header line of site for first time HTTP response message v when initial HTTP 2) cookie header line in requests arrives at site, HTTP request message site creates: 3) cookie file kept on user’s § unique ID host, managed by user’s browser § entry in backend 4) back-end database at database for ID Web site 37
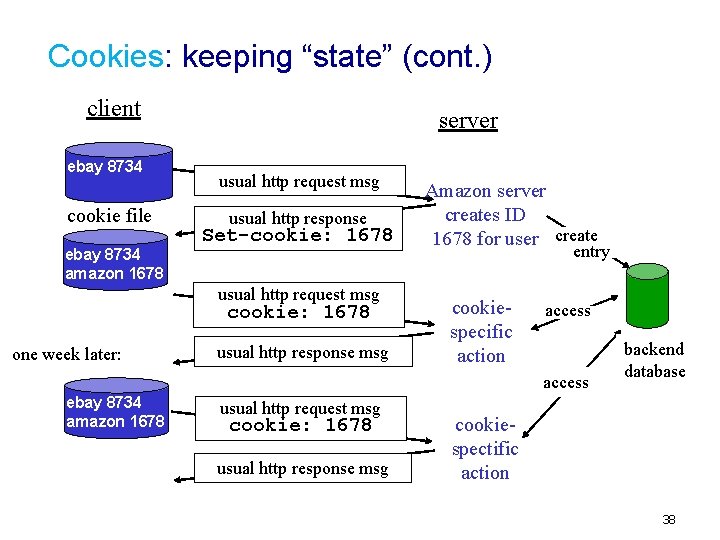
Cookies: keeping “state” (cont. ) client ebay 8734 cookie file ebay 8734 amazon 1678 server usual http request msg usual http response Set-cookie: 1678 usual http request msg cookie: 1678 one week later: usual http response msg Amazon server creates ID 1678 for user create entry cookiespecific action access ebay 8734 amazon 1678 usual http request msg cookie: 1678 usual http response msg backend database cookiespectific action 38
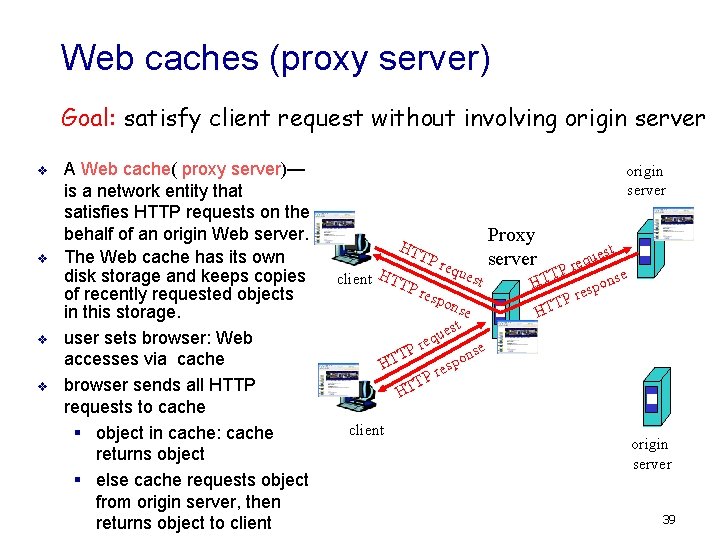
Web caches (proxy server) Goal: satisfy client request without involving origin server v v A Web cache( proxy server)— is a network entity that satisfies HTTP requests on the behalf of an origin Web server. The Web cache has its own disk storage and keeps copies of recently requested objects in this storage. user sets browser: Web accesses via cache browser sends all HTTP requests to cache § object in cache: cache returns object § else cache requests object from origin server, then returns object to client origin server HT TP client HTTP req resp Proxy server ues t ons e t ues q e Pr se n T o T p H res P T HT client est u q re P T e HT ons p s re P T HT origin server 39
Topics v v Principles of network applications Web and HTTP FTP Electronic Mail § SMTP, POP 3, IMAP v DNS 40
Email Protocols v v v Email is a store-and-forward method of sending, storing, and retrieving electronic messages. Email messages are stored in databases on mail servers. Email clients communicate with mail servers to send and receive email. Mail servers communicate with other mail servers to transport messages from one domain to another. Email clients do not communicate directly when sending email. Email relies on three separate protocols for operation: SMTP (sending), POP (retrieving), IMAP (retrieving).
SMTP Operation v v v SMTP message formats require a message header and body. An SMTP client sends an email by connecting to a SMTP server on port 25. The server receives the message and stores it message in a local mailbox or relays the message to another mail server. Users use email clients to retrieve messages stored on the server. IMAP and POP are two protocols commonly used by email clients to retrieve messages.
POP Operation v v v v Messages are downloaded from the server to the client. The server listens on port 110 TCP for client requests. Email clients direct their POP requests to mail servers on port TCP 110. The POP client and server exchange commands and responses until the connection is closed or aborted. POP allows for email messages to be downloaded to the client’s device (computer or phone) and removed from the server. There is no centralized location where email messages are kept. A downloaded message resides on the device that triggered the download.
IMAP Operation v v v v IMAP is another protocol used to retrieve email messages. Allows for messages to be displayed to the user rather than downloaded. The original messages reside on the server until manually deleted by the user. Users view copies of the messages in their email client software. Users can create a folder hierarchy on the server to organize and store mail. That file structure is displayed on the email client. When a user decides to delete a message, the server synchronizes that action and deletes the message from the server.

Topics v v Principles of network applications Web and HTTP FTP Electronic Mail § SMTP, POP 3, IMAP v DNS 45
Domain Name Service v v While IP addresses are crucial for network communication, they are not easy to memorize. Domain names are created to make server addresses more userfriendly. Domain names such as www. google. com are user-friendly addresses associated with the IP address of a specific server. However, computers still need the actual numeric address before they can communicate. two ways to identify a host: by a hostname and by an IP address
Domain Name Service (cont. ) v v The DNS protocol allows for the dynamic translation of a domain name into the correct IP address. The DNS protocol communications using a single format called a message.
domain name system (DNS) (1) v v v Domain Name System: § distributed database implemented in hierarchy of many name servers an application-layer protocol that allows hosts to query the distributed database. The DNS servers are often UNIX machines running the Berkeley Internet Name Domain (BIND) software [BIND 2012]. The DNS protocol runs over UDP and uses port 53. DNS is commonly employed by other application-layer protocols— including HTTP, SMTP, and FTP—to translate user-supplied hostnames to IP addresses.
domain name system (DNS) (2) v As an example, consider what happens when a browser (that is, an HTTP client), running on some user’s host, requests the URL www. someschool. edu/index. html. In order for the user’s host to be able to send an HTTP request message to the Web server www. someschool. edu, the user’s host must first obtain the IP address of www. someschool. edu. This is done as follows. 1. The same user machine runs the client side of the DNS application. 2. The browser extracts the hostname, www. someschool. edu, from the URLand passes the hostname to the client side of the DNS application. 3. The DNS client sends a query containing the hostname to a DNS server. 4. The DNS client eventually receives a reply, which includes the IP address forthe hostname. 5. Once the browser receives the IP address from DNS, it can initiate a TCP connection to the HTTP server process located at port
DNS services v v v 3. Mail server aliasing. 1. translating hostnames to IP addresses: § DNS can be invoked by a mail application to obtain the 2. Host aliasing. A host with a canonical hostname for a complicated hostname can have supplied alias hostname as one or more alias names. well as the IP address of the § For example, a hostname such host. as relay 1. west-coast. enterprise. v 4. Load distribution. DNS is also com could have, say, two used to perform load distribution aliases such as enterprise. com among replicated servers, such and www. enterprise. com. as replicated Web servers. § In this case, the hostname Why not centralize DNS? relay 1. westcoast. v single point of failure enterprise. com is said to be a v traffic volume canonical hostname. v distant centralized database § Alias hostnames, when v Maintenance present, are typically more mnemonic than canonical doesn’t scale! hostnames. 50
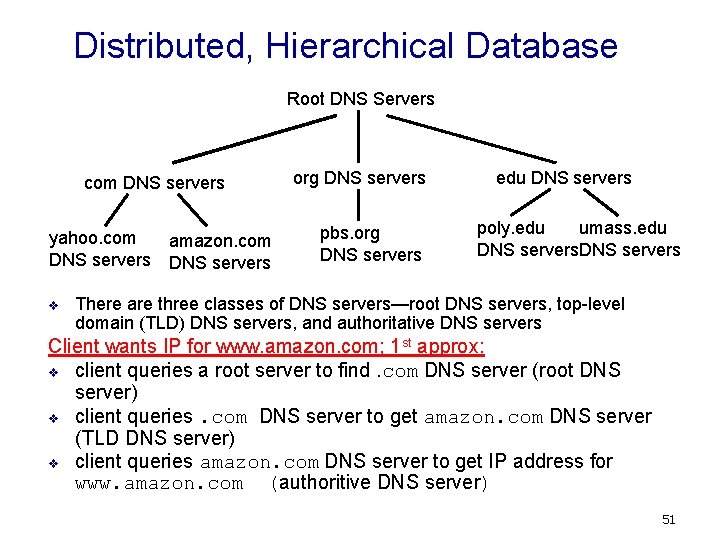
Distributed, Hierarchical Database Root DNS Servers com DNS servers yahoo. com amazon. com DNS servers v org DNS servers pbs. org DNS servers edu DNS servers poly. edu umass. edu DNS servers There are three classes of DNS servers—root DNS servers, top-level domain (TLD) DNS servers, and authoritative DNS servers Client wants IP for www. amazon. com; 1 st approx: v client queries a root server to find. com DNS server (root DNS server) v client queries. com DNS server to get amazon. com DNS server (TLD DNS server) v client queries amazon. com DNS server to get IP address for www. amazon. com (authoritive DNS server) 51
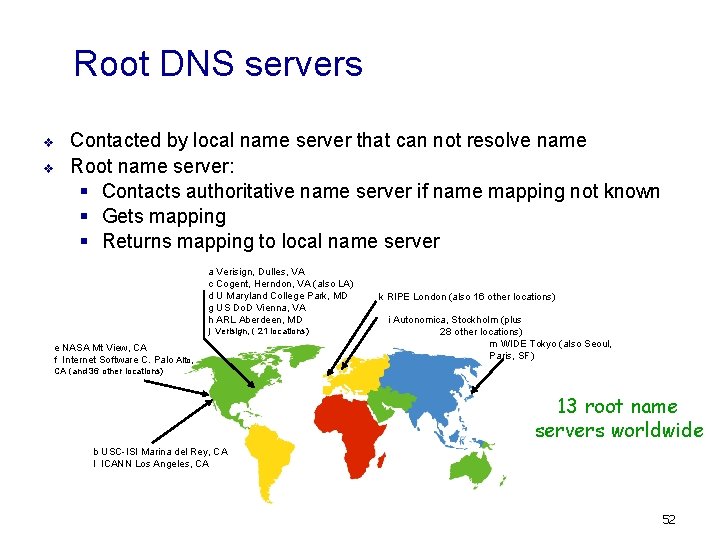
Root DNS servers v v Contacted by local name server that can not resolve name Root name server: § Contacts authoritative name server if name mapping not known § Gets mapping § Returns mapping to local name server a Verisign, Dulles, VA c Cogent, Herndon, VA (also LA) d U Maryland College Park, MD g US Do. D Vienna, VA h ARL Aberdeen, MD j Verisign, ( 21 locations) e NASA Mt View, CA f Internet Software C. Palo Alto, k RIPE London (also 16 other locations) i Autonomica, Stockholm (plus 28 other locations) m WIDE Tokyo (also Seoul, Paris, SF) CA (and 36 other locations) 13 root name servers worldwide b USC-ISI Marina del Rey, CA l ICANN Los Angeles, CA 52
TLD and Authoritative Servers v Top-level domain (TLD) servers: § Responsible for com, org, net, edu, etc, and all top-level country domains uk, fr, ca, jp § Network Solutions maintains servers for com TLD § Educause for edu TLD v Authoritative DNS servers: § Organization’s DNS servers, providing authoritative hostname to IP mappings for organization’s servers (e. g. , Web, mail). § Can be maintained by organization or service provider 53

Local Name Server v v Does not strictly belong to hierarchy Each ISP (residential ISP, company, university) has one § Also called “default name server” § You can run one in your home/dorm! v When host makes DNS query, query is sent to its local DNS server § Acts as proxy, forwards query into hierarchy 54
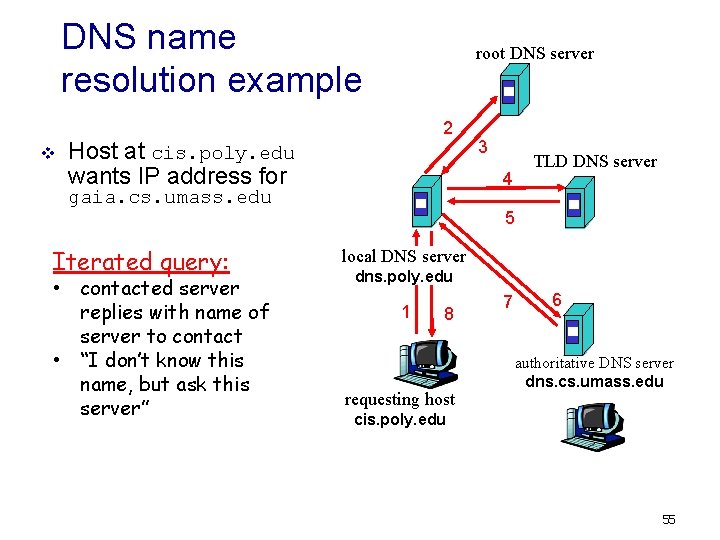
DNS name resolution example v root DNS server 2 Host at cis. poly. edu wants IP address for • contacted server replies with name of server to contact • “I don’t know this name, but ask this server” TLD DNS server 4 gaia. cs. umass. edu Iterated query: 3 5 local DNS server dns. poly. edu 1 8 requesting host 7 6 authoritative DNS server dns. cs. umass. edu cis. poly. edu 55
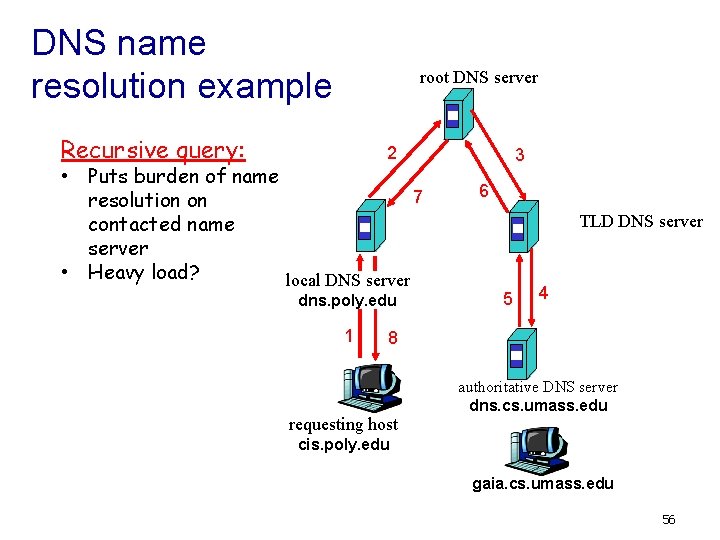
DNS name resolution example root DNS server Recursive query: 2 • Puts burden of name 7 resolution on contacted name server • Heavy load? local DNS server dns. poly. edu 1 3 6 TLD DNS server 5 4 8 requesting host authoritative DNS server dns. cs. umass. edu cis. poly. edu gaia. cs. umass. edu 56

DNS: caching and updating records v Once (any) name server learns mapping, it caches mapping § Cache entries timeout (disappear) after some time § TLD servers typically cached in local name servers • Thus root name servers not visited often v Originally thought DNS names quite static, but increasingly not so update/notify mechanisms under design by IETF § RFC 2136: http: //www. ietf. org/rfc 2136. txt 57
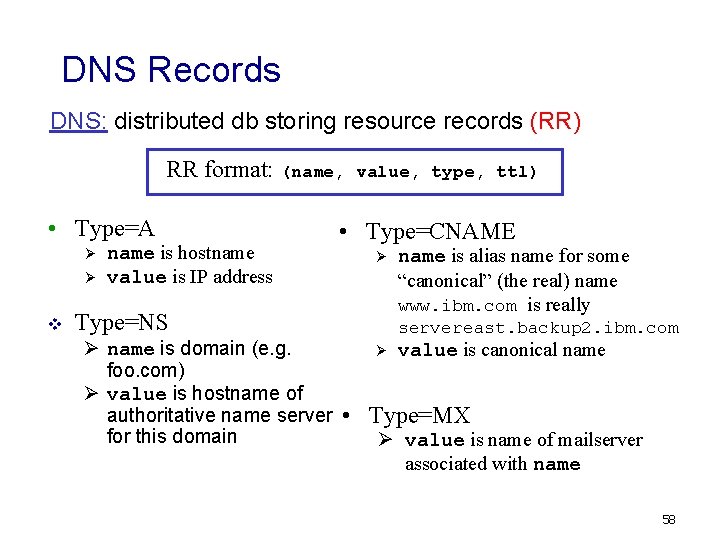
DNS Records DNS: distributed db storing resource records (RR) RR format: (name, • Type=A Ø Ø v name is hostname value is IP address Type=NS value, type, ttl) • Type=CNAME Ø name is alias name for some “canonical” (the real) name www. ibm. com is really servereast. backup 2. ibm. com Ø name is domain (e. g. Ø value is canonical name foo. com) Ø value is hostname of authoritative name server • Type=MX for this domain Ø value is name of mailserver associated with name 58
Inserting records into DNS v Example: new startup “Network Utopia” § How do people get IP address of your Web site? § How do they send you email? v Register name networkuptopia. com at DNS registrar (e. g. , Network Solutions) § provide names, IP addresses of authoritative name server (primary and secondary) § registrar inserts two RRs into. com TLD server: (networkutopia. com, dns 1. networkutopia. com, NS) (dns 1. networkutopia. com, 212. 1, A) v Create authoritative server Type A record for www. networkuptopia. com; Type MX record for networkutopia. com for mail 59
Chapter 2: Summary Study of network apps now complete! v Application architectures § client-server § P 2 P § hybrid v Application service requirements: • specific protocols: - HTTP DNS P 2 P: Bit. Torrent, Skype • socket programming § reliability, bandwidth, delay v Internet transport service model § connection-oriented, reliable: TCP § unreliable, datagrams: UDP 60
- Slides: 60