Lecture A 3 DNS Security r Domain Name



![First query: authoritative gslacks[pts/3]: ~> dig www. cse. ucsc. edu ; <<>> Di. G First query: authoritative gslacks[pts/3]: ~> dig www. cse. ucsc. edu ; <<>> Di. G](https://slidetodoc.com/presentation_image/cc88ecc5d82e9c00a6693155347da7dd/image-10.jpg)
![Second query: cached gslacks[pts/3]: ~> dig www. cse. ucsc. edu ; <<>> Di. G Second query: cached gslacks[pts/3]: ~> dig www. cse. ucsc. edu ; <<>> Di. G](https://slidetodoc.com/presentation_image/cc88ecc5d82e9c00a6693155347da7dd/image-11.jpg)





- Slides: 26

Lecture A. 3: DNS Security r Domain Name Service r Security Problems in DNS 1

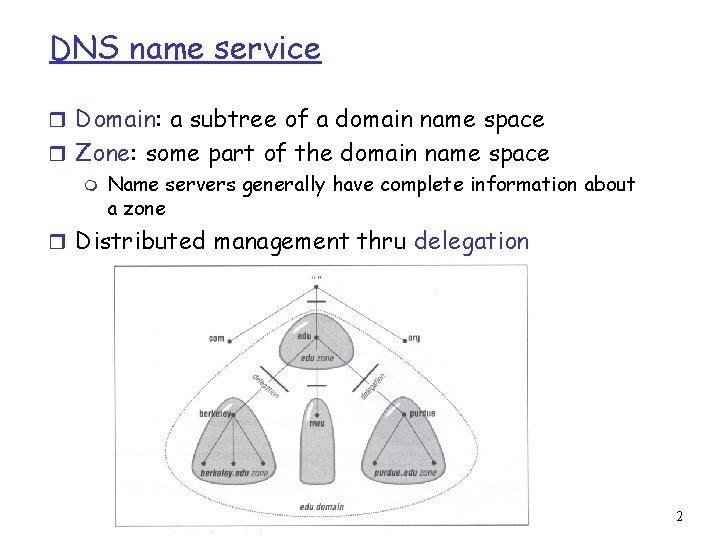
DNS name service r Domain: a subtree of a domain name space r Zone: some part of the domain name space m Name servers generally have complete information about a zone r Distributed management thru delegation 2

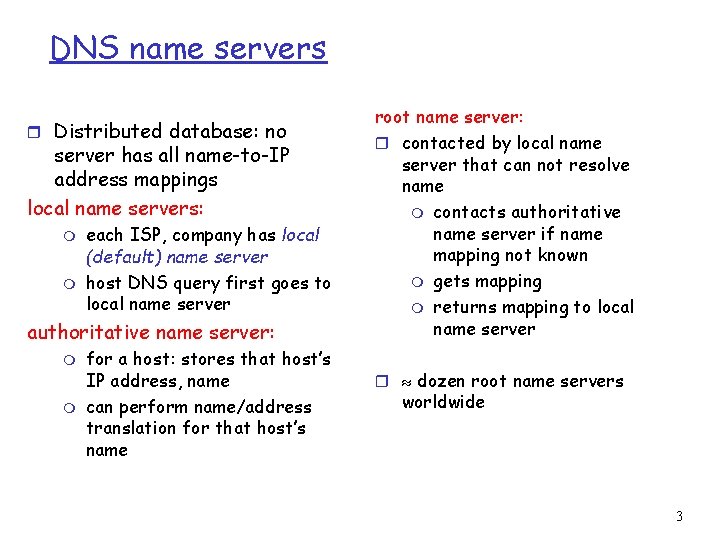
DNS name servers r Distributed database: no server has all name-to-IP address mappings local name servers: m m each ISP, company has local (default) name server host DNS query first goes to local name server authoritative name server: m m for a host: stores that host’s IP address, name can perform name/address translation for that host’s name root name server: r contacted by local name server that can not resolve name m contacts authoritative name server if name mapping not known m gets mapping m returns mapping to local name server r dozen root name servers worldwide 3

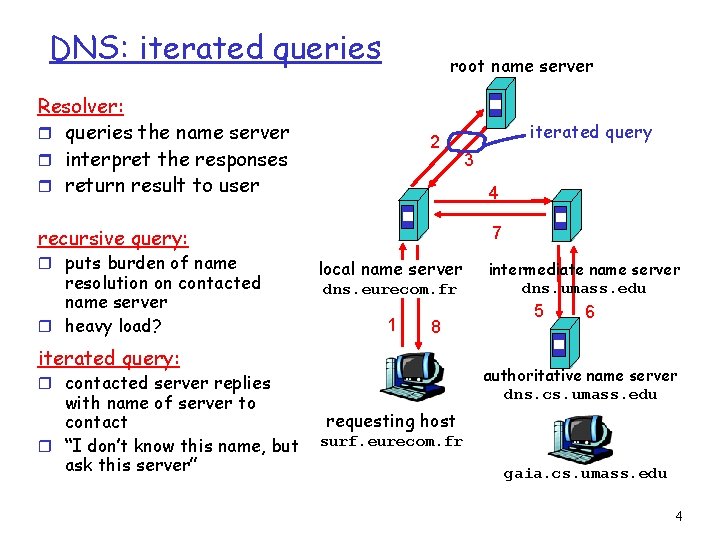
DNS: iterated queries root name server Resolver: r queries the name server r interpret the responses r return result to user 2 resolution on contacted name server r heavy load? 7 local name server dns. eurecom. fr 1 8 iterated query: intermediate name server dns. umass. edu 5 6 authoritative name server dns. cs. umass. edu r contacted server replies with name of server to contact r “I don’t know this name, but ask this server” 3 4 recursive query: r puts burden of name iterated query requesting host surf. eurecom. fr gaia. cs. umass. edu 4

DNS: caching and updating records r once (any) name server learns mapping, it caches mapping m cache entries timeout (disappear) after some time r update/notify mechanisms under design by IETF m RFC 2136 m http: //www. ietf. org/html. charters/dnsind-charter. html 5

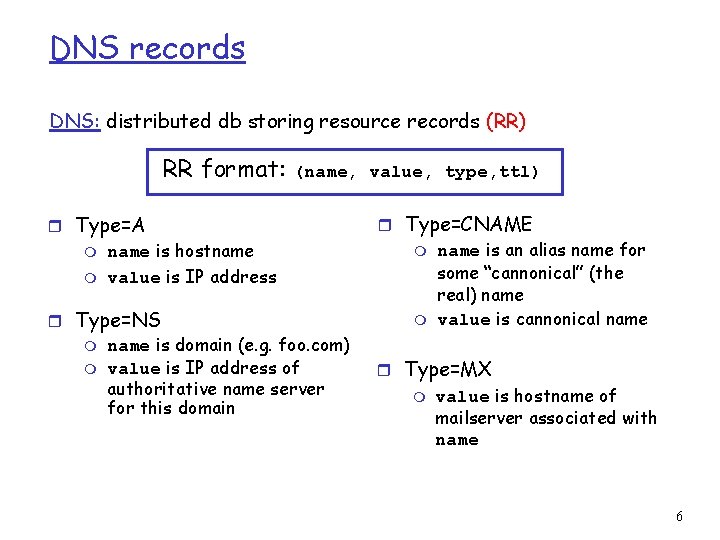
DNS records DNS: distributed db storing resource records (RR) RR format: (name, value, type, ttl) r Type=A m name is hostname m value is IP address r Type=NS m name is domain (e. g. foo. com) m value is IP address of authoritative name server for this domain r Type=CNAME m name is an alias name for some “cannonical” (the real) name m value is cannonical name r Type=MX m value is hostname of mailserver associated with name 6

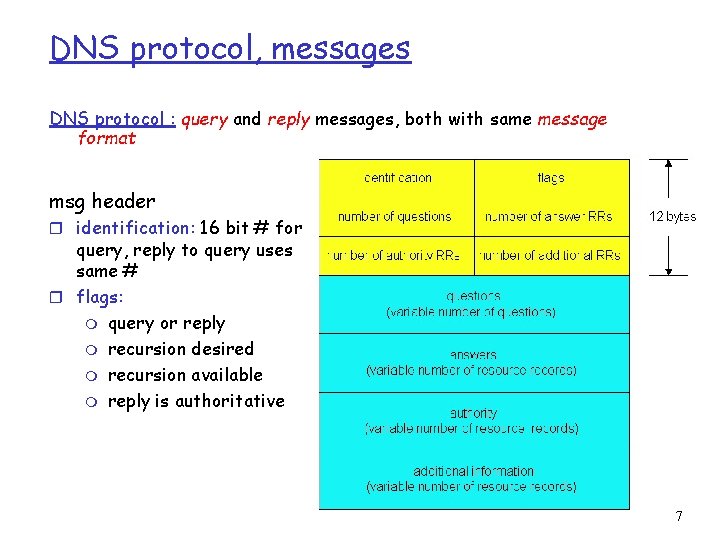
DNS protocol, messages DNS protocol : query and reply messages, both with same message format msg header r identification: 16 bit # for query, reply to query uses same # r flags: m query or reply m recursion desired m recursion available m reply is authoritative 7

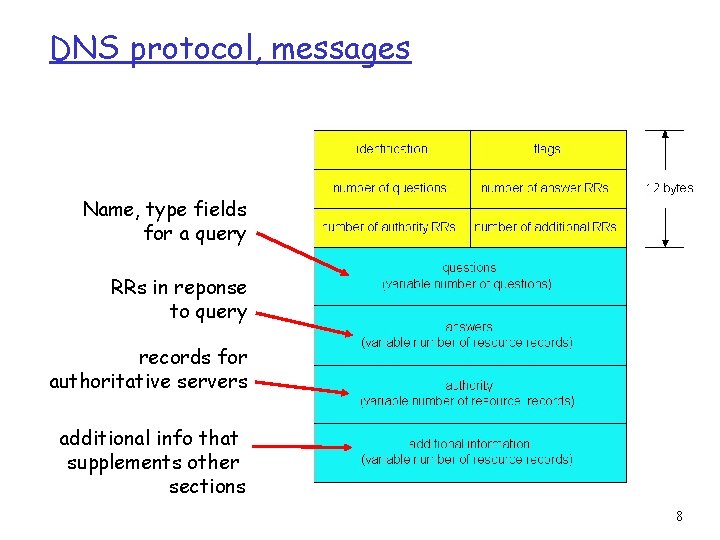
DNS protocol, messages Name, type fields for a query RRs in reponse to query records for authoritative servers additional info that supplements other sections 8

DNS query r Troubleshooting tools for DNS m nslookup m dig (domain information gopher) dig cic. ulsan. ac. kr ; looks up A records for ; cic. ulsan. ac. kr dig mail. ulsan. ac. kr mx ; looks up MX records for ; mail. ulsan. ac. kr dig @a. root-servers. net ns. ; queries a. root-servers. net ; for NS records for. domain 9
![First query authoritative gslackspts3 dig www cse ucsc edu Di G First query: authoritative gslacks[pts/3]: ~> dig www. cse. ucsc. edu ; <<>> Di. G](https://slidetodoc.com/presentation_image/cc88ecc5d82e9c00a6693155347da7dd/image-10.jpg)
First query: authoritative gslacks[pts/3]: ~> dig www. cse. ucsc. edu ; <<>> Di. G 8. 2 <<>> www. cse. ucsc. edu ; ; res options: init recurs defnam dnsrch ; ; got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4 ; ; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 2 ; ; QUERY SECTION: qr: query packet ; ; www. cse. ucsc. edu, type = A, class = IN ; ; ANSWER SECTION: www. cse. ucsc. edu. ftp. cse. ucsc. edu. 1 D IN CNAME 1 D IN A ftp. cse. ucsc. edu. 128. 114. 48. 173 ; ; AUTHORITY SECTION: cse. ucsc. edu. 1 D IN NS services. cse. ucsc. edu. fs 1. cse. ucsc. edu. ; ; ADDITIONAL SECTION: services. cse. ucsc. edu. fs 1. cse. ucsc. edu. 1 D IN A 128. 114. 48. 10 128. 114. 48. 11 ; ; ; ; Total query time: 89 msec FROM: gslacks. cs. umass. edu to SERVER: default -- 128. 119. 240. 1 WHEN: Thu Apr 12 08: 25: 04 2001 MSG SIZE sent: 34 rcvd: 153 aa: authoritative answer rd: recursion desired ra: recursion available 10
![Second query cached gslackspts3 dig www cse ucsc edu Di G Second query: cached gslacks[pts/3]: ~> dig www. cse. ucsc. edu ; <<>> Di. G](https://slidetodoc.com/presentation_image/cc88ecc5d82e9c00a6693155347da7dd/image-11.jpg)
Second query: cached gslacks[pts/3]: ~> dig www. cse. ucsc. edu ; <<>> Di. G 8. 2 <<>> www. cse. ucsc. edu ; ; res options: init recurs defnam dnsrch ; ; got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4 ; ; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 2 ; ; QUERY SECTION: ; ; www. cse. ucsc. edu, type = A, class = IN ; ; ANSWER SECTION: www. cse. ucsc. edu. ftp. cse. ucsc. edu. 23 h 59 m 57 s IN CNAME ftp. cse. ucsc. edu. 23 h 59 m 57 s IN A 128. 114. 48. 173 ; ; AUTHORITY SECTION: cse. ucsc. edu. 15 h 54 m 19 s IN NS ; ; ADDITIONAL SECTION: services. cse. ucsc. edu. fs 1. cse. ucsc. edu. 15 h 54 m 19 s IN A services. cse. ucsc. edu. fs 1. cse. ucsc. edu. 128. 114. 48. 10 128. 114. 48. 11 ; ; Total query time: 1 msec ; ; FROM: gslacks. cs. umass. edu to SERVER: default -- 128. 119. 240. 1 ; ; WHEN: Thu Apr 12 08: 25: 07 2001 11

Zone transfer r Name servers for a zone m Primary master name server: reads zone data from a file on its host m Secondary master (slave) name server: gets zone data from another name server that is authoritative for the zone r Zone transfer: When a slave name server starts up, it contacts its master server and pulls the zone data over 12

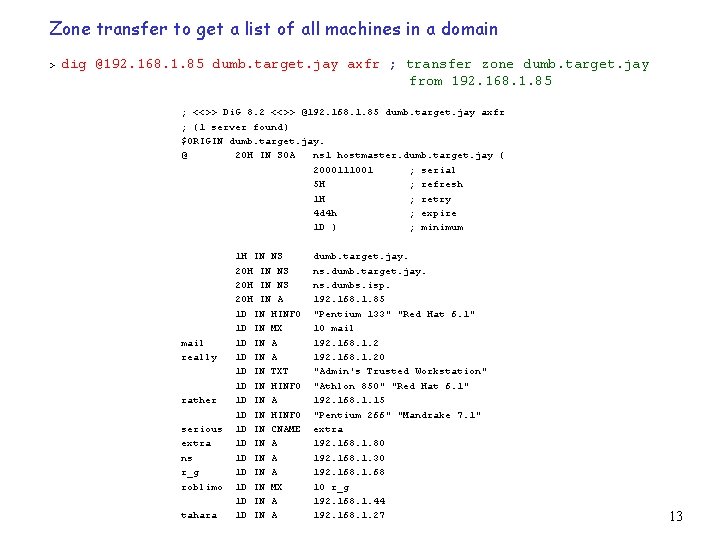
Zone transfer to get a list of all machines in a domain > dig @192. 168. 1. 85 dumb. target. jay axfr ; transfer zone dumb. target. jay from 192. 168. 1. 85 ; <<>> Di. G 8. 2 <<>> @192. 168. 1. 85 dumb. target. jay axfr ; (1 server found) $ORIGIN dumb. target. jay. @ 20 H IN SOA ns 1 hostmaster. dumb. target. jay ( 2000111001 ; serial 5 H ; refresh 1 H ; retry 4 d 4 h ; expire 1 D ) ; minimum mail really rather serious extra ns r_g roblimo tahara 1 H IN NS 20 H IN A 1 D IN HINFO 1 D IN MX 1 D IN A 1 D IN TXT 1 D IN HINFO 1 D IN A 1 D IN HINFO 1 D IN CNAME 1 D IN A 1 D IN MX 1 D IN A dumb. target. jay. ns. dumbs. isp. 192. 168. 1. 85 "Pentium 133" "Red Hat 6. 1" 10 mail 192. 168. 1. 20 "Admin's Trusted Workstation" "Athlon 850" "Red Hat 6. 1" 192. 168. 1. 15 "Pentium 266" "Mandrake 7. 1" extra 192. 168. 1. 80 192. 168. 1. 30 192. 168. 1. 68 10 r_g 192. 168. 1. 44 192. 168. 1. 27 13

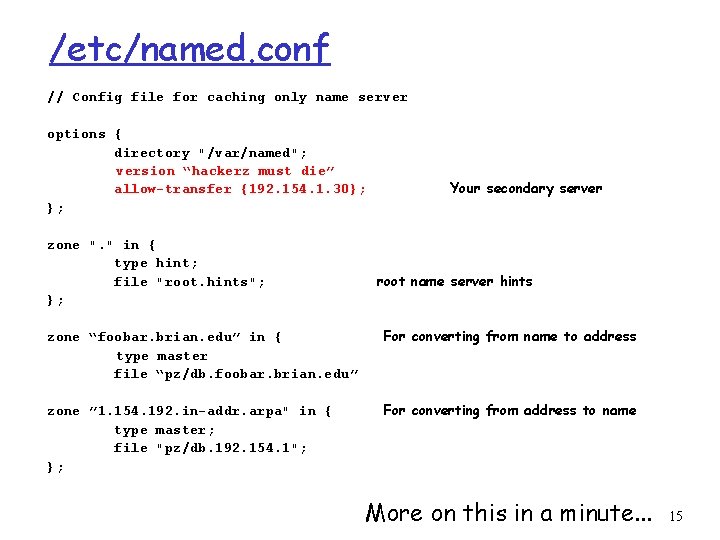
BIND r Be careful not announce what version of bind you are running when answering queries <- security by obscurity. r In unix, DNS is handled by the BIND package, and a program called “named” r Configuration of the daemon is kept in /etc/named. conf 14

/etc/named. conf // Config file for caching only name server options { directory "/var/named"; version “hackerz must die” allow-transfer {192. 154. 1. 30}; }; zone ". " in { type hint; file "root. hints"; }; Your secondary server root name server hints zone “foobar. brian. edu” in { type master file “pz/db. foobar. brian. edu” For converting from name to address zone ” 1. 154. 192. in-addr. arpa" in { type master; file "pz/db. 192. 154. 1"; }; For converting from address to name More on this in a minute. . . 15

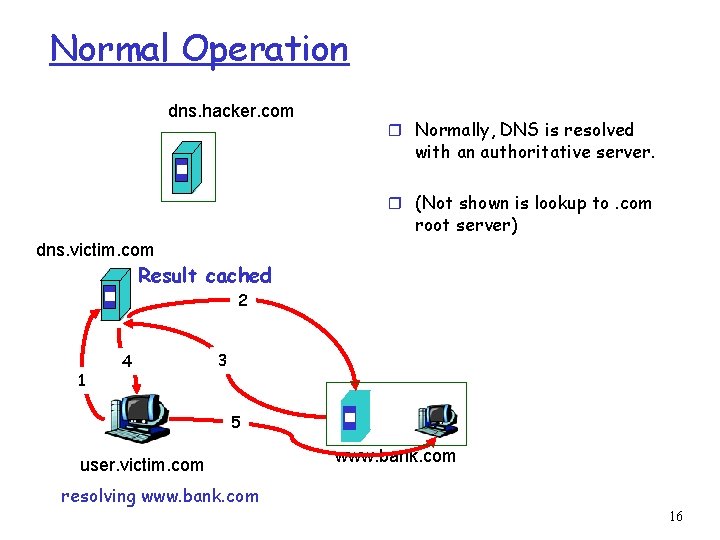
Normal Operation dns. hacker. com r Normally, DNS is resolved with an authoritative server. r (Not shown is lookup to. com root server) dns. victim. com Result cached 2 1 4 3 5 user. victim. com www. bank. com resolving www. bank. com 16

DNS Cache Poisoning r URL spoofing attack: m register a similar name of someone you are attacking m e. g. , www. ibn. com, … r Cache poisoning is a more sophisticated version of the same idea. r The two key ideas we will take advantage of are: m The query number (and reply id) are often predictable if you can learn earlier IDs. m DNS caches previous results 17

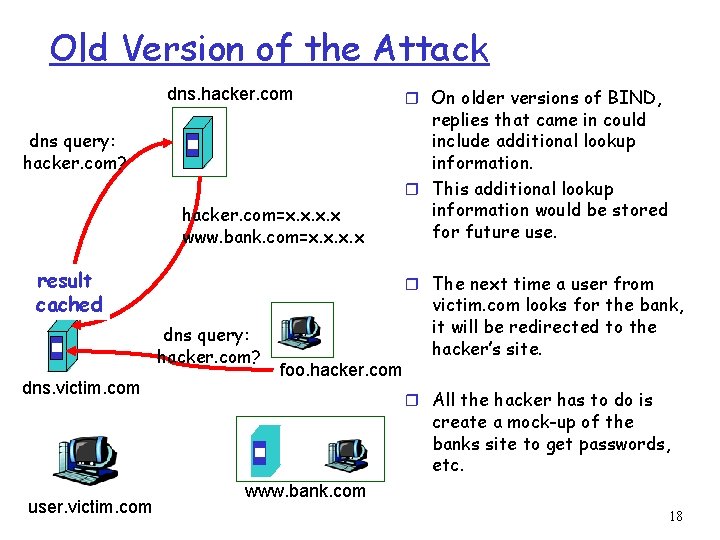
Old Version of the Attack dns. hacker. com dns query: hacker. com? hacker. com=x. x www. bank. com=x. x result cached replies that came in could include additional lookup information. r This additional lookup information would be stored for future use. r The next time a user from dns query: hacker. com? dns. victim. com r On older versions of BIND, victim. com looks for the bank, it will be redirected to the hacker’s site. foo. hacker. com r All the hacker has to do is create a mock-up of the banks site to get passwords, etc. user. victim. com www. bank. com 18

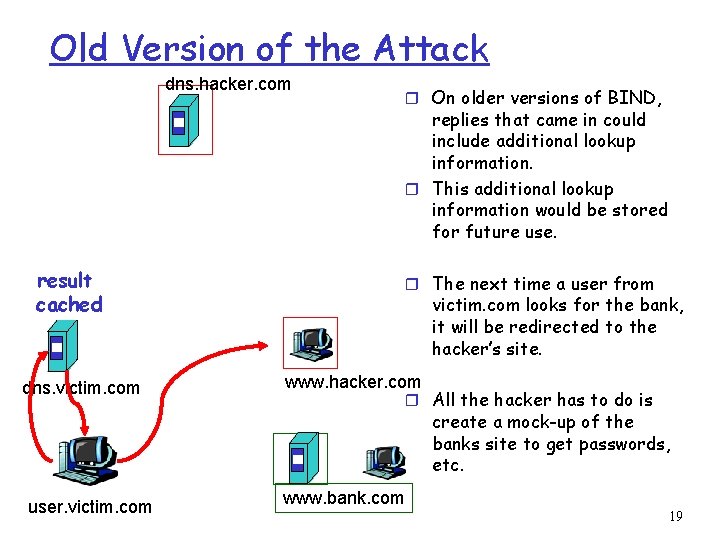
Old Version of the Attack dns. hacker. com r On older versions of BIND, replies that came in could include additional lookup information. r This additional lookup information would be stored for future use. result cached dns. victim. com r The next time a user from victim. com looks for the bank, it will be redirected to the hacker’s site. www. hacker. com r All the hacker has to do is create a mock-up of the banks site to get passwords, etc. user. victim. com www. bank. com 19

More attacks r The old attack no longer work since BIND was patched to ignore additional information provided in the reply. r However, a more complex version of the attack still works. 20

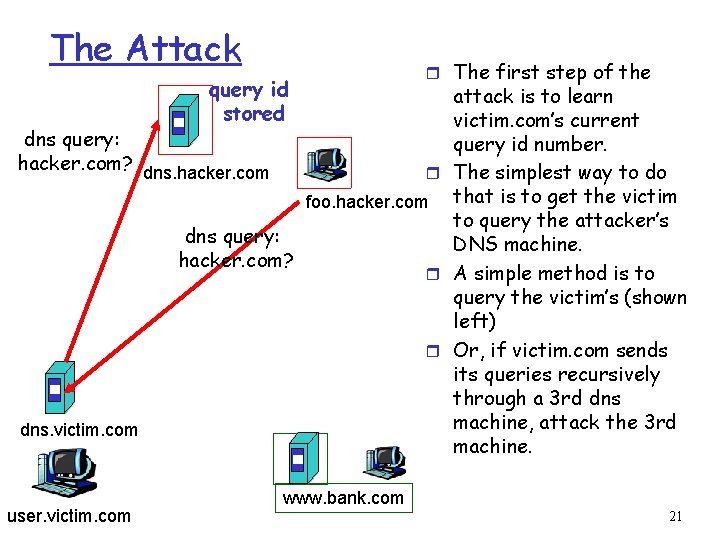
The Attack query id stored r The first step of the attack is to learn victim. com’s current dns query: query id number. hacker. com? dns. hacker. com r The simplest way to do foo. hacker. com that is to get the victim to query the attacker’s dns query: DNS machine. hacker. com? r A simple method is to query the victim’s (shown left) r Or, if victim. com sends its queries recursively through a 3 rd dns machine, attack the 3 rd dns. victim. com machine. user. victim. com www. bank. com 21

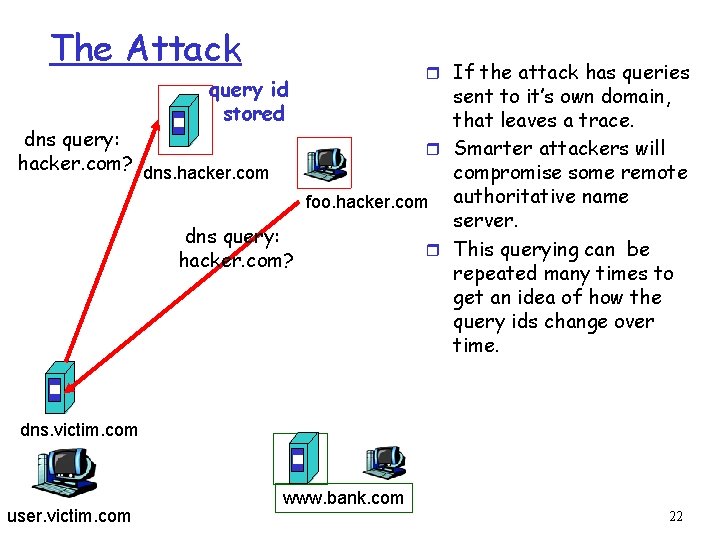
The Attack query id stored r If the attack has queries sent to it’s own domain, that leaves a trace. dns query: r Smarter attackers will hacker. com? dns. hacker. compromise some remote foo. hacker. com authoritative name server. dns query: r This querying can be hacker. com? repeated many times to get an idea of how the query ids change over time. dns. victim. com user. victim. com www. bank. com 22

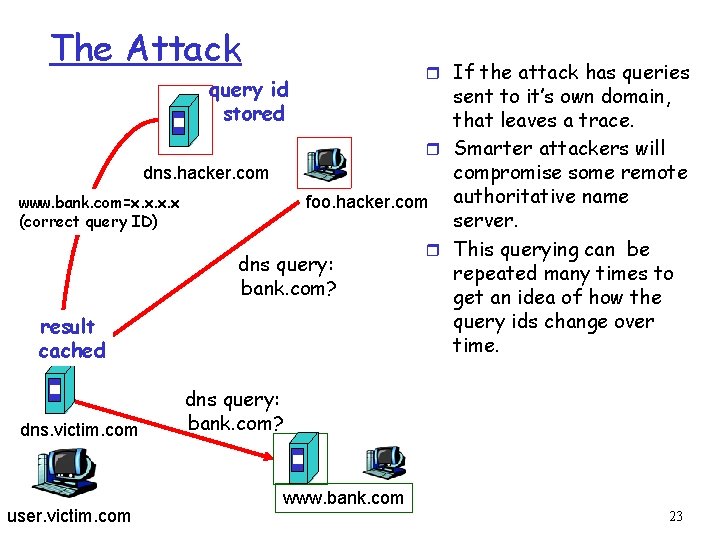
The Attack query id stored r If the attack has queries sent to it’s own domain, that leaves a trace. r Smarter attackers will dns. hacker. compromise some remote www. bank. com=x. x foo. hacker. com authoritative name (correct query ID) server. r This querying can be dns query: repeated many times to bank. com? get an idea of how the query ids change over result time. cached dns. victim. com user. victim. com dns query: bank. com? www. bank. com 23

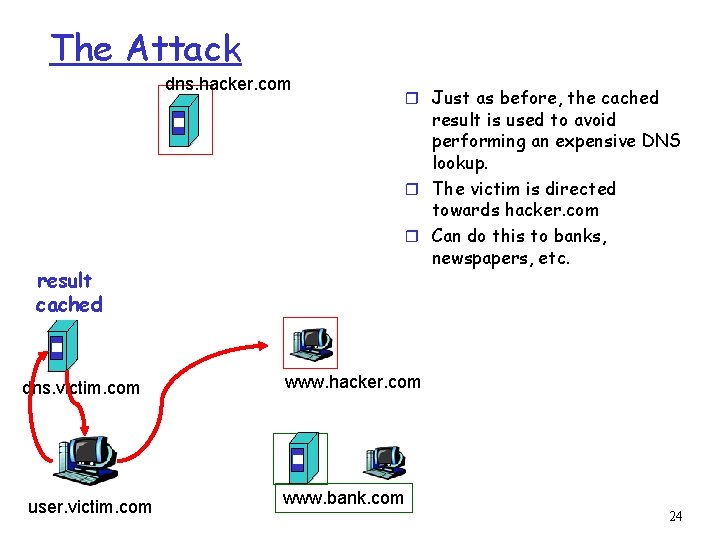
The Attack dns. hacker. com result is used to avoid performing an expensive DNS lookup. r The victim is directed towards hacker. com r Can do this to banks, newspapers, etc. result cached dns. victim. com user. victim. com r Just as before, the cached www. hacker. com www. bank. com 24

Defenses r New versions of BIND have harder to predict query IDs. r DNSSEC (RFC 2535) is a secure version of DNS with RSA signed DNS records. r You could use a secure connection to your bank. r Split-split defense: m m m One DNS server for resolving names for users inside your domain; this server doesn’t respond to outside queries at all. Another separate DNS server is setup for responding to queries from outsiders. The two never exchange information. Your users never are subject to poisoned information. 25

Defenses in /etc/named. conf // Config file for caching only name server options { directory "/var/named"; version “hackerz must die” allow-transfer {192. 154. 1. 30}; allow-query { any; }; allow-recursion { 192. 154. 1. 0/24; }; }; zone “foobar. brian. edu” in { type master file “pz/db. foobar. brian. edu” allow-query { 192. 154. 1. 0/24; } }; zone ” 1. 154. 192. in-addr. arpa" in { type master; file "pz/db. 192. 154. 1"; allow-query { 192. 154. 1. 0/24; } }; Global access control list (ACL): Only this subnet can query us Zone specific ACL: take precedence over a global ACL 26