Lecture 9 Hash House Harriers CS 551 Security








![IOU Protocol (Attempt 2) M EKA[H(M)] Bob Alice secret key KA Use Diffie-Hellman to IOU Protocol (Attempt 2) M EKA[H(M)] Bob Alice secret key KA Use Diffie-Hellman to](https://slidetodoc.com/presentation_image/9861dc94e87b98852bbc451ad891c7b4/image-13.jpg)
![IOU Protocol (Attempt 3) M EKRA[H(M)] Bob knows KUA Alice {KUA, KRA} 9/30/2020 M IOU Protocol (Attempt 3) M EKRA[H(M)] Bob knows KUA Alice {KUA, KRA} 9/30/2020 M](https://slidetodoc.com/presentation_image/9861dc94e87b98852bbc451ad891c7b4/image-14.jpg)
![Weak Collision Resistance • Suppose we use: H (char s[]) = (s[0] – ‘a’) Weak Collision Resistance • Suppose we use: H (char s[]) = (s[0] – ‘a’)](https://slidetodoc.com/presentation_image/9861dc94e87b98852bbc451ad891c7b4/image-15.jpg)





![IOU Request Protocol x EKRA[H(x)] Bob knows KUA Alice {KUA, KRA} y EKRA[H(x)] Bob IOU Request Protocol x EKRA[H(x)] Bob knows KUA Alice {KUA, KRA} y EKRA[H(x)] Bob](https://slidetodoc.com/presentation_image/9861dc94e87b98852bbc451ad891c7b4/image-23.jpg)










- Slides: 37

Lecture 9: Hash House Harriers CS 551: Security and Privacy David Evans University of Virginia CS 551 http: //www. cs. virginia. edu/~evans Computer Science

Menu • “Quiz” Results • Hashing 9/30/2020 University of Virginia CS 551 2

Quiz Results • Six people got everything right • Most common mistake: e * d 1 mod n should be: e * d (mod (p – 1)(q – 1)) Why is e * d 1 mod n a bad guess? • Little correlation between how well you said you understood RSA and correctness of answers 9/30/2020 University of Virginia CS 551 3

Selected Quiz Comments • “Wondering if we just have to understand the algorithms or do we have to memorize them. ” • “On both of the problem sets, I’ve felt like its the first time I’ve seen the material applied this way. ” • “I feel like we’ve hit the surface of many topics, but haven’t spent enough time to get really in depth in many of the topics. ” 9/30/2020 University of Virginia CS 551 4

Selected Quiz Comments • “Need TA’s” – Siddarth Dalai – Office hours on Tuesdays 3: 30 -4: 30 and Fridays 2: 00 -3: 00 in the CS department library or 113 g. – My office hours: Mondays 1: 30 -2: 30, Wednesdays after class. 9/30/2020 University of Virginia CS 551 5

Using RSA to Encrypt • Use 1024 -bit modulus (RSA recommends at least 768 bits) • Encrypt 1 M file • Why does no one use RSA like this? – About 100 -1000 times slower than DES – Can speed up encryption by choosing e that is an easy number to multiply by (e. g. , 3 or 216 + 1) 9/30/2020 University of Virginia CS 551 6

Alternatives • Use RSA to establish a shared secret key for symmetric cipher (DES, RC 6, . . . ) – Lose external authentication, nonrepudiation properties of public-key cryptosystems • Sign (encrypt with private key) a hash of the message – A short block that is associated with the message 9/30/2020 University of Virginia CS 551 7

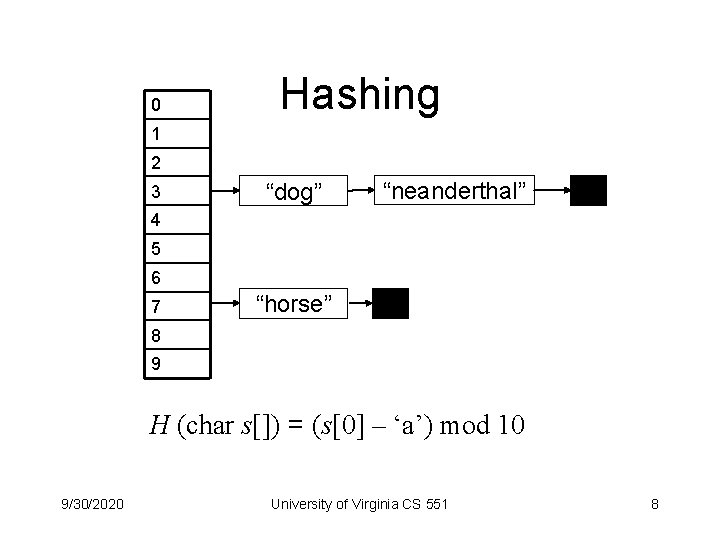
0 Hashing 1 2 3 “dog” “neanderthal” 4 5 6 7 “horse” 8 9 H (char s[]) = (s[0] – ‘a’) mod 10 9/30/2020 University of Virginia CS 551 8

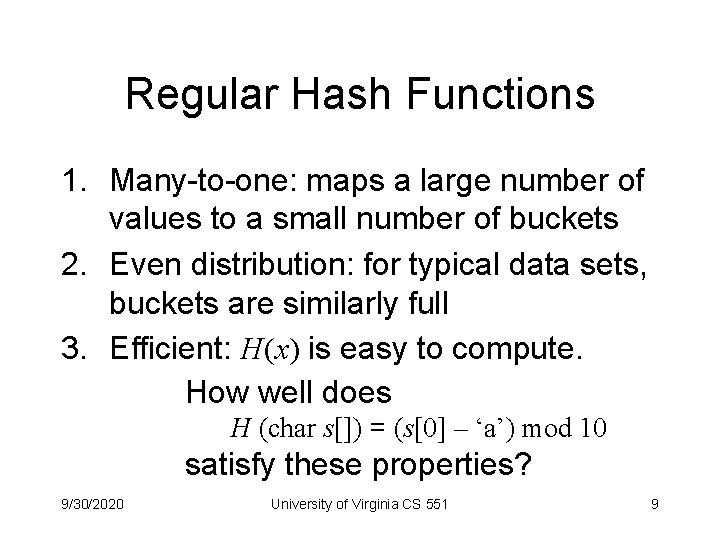
Regular Hash Functions 1. Many-to-one: maps a large number of values to a small number of buckets 2. Even distribution: for typical data sets, buckets are similarly full 3. Efficient: H(x) is easy to compute. How well does H (char s[]) = (s[0] – ‘a’) mod 10 satisfy these properties? 9/30/2020 University of Virginia CS 551 9

Cryptographic Hash Functions 4. One-way: for given h, it is hard to find x such that H(x) = h. 5. Collision resistance: Weak collision resistance: given x, it is hard to find y x such that H(y) = H(x). Strong collision resistance: it is hard to find any x and y x such that H(y) = H(x). 9/30/2020 University of Virginia CS 551 10

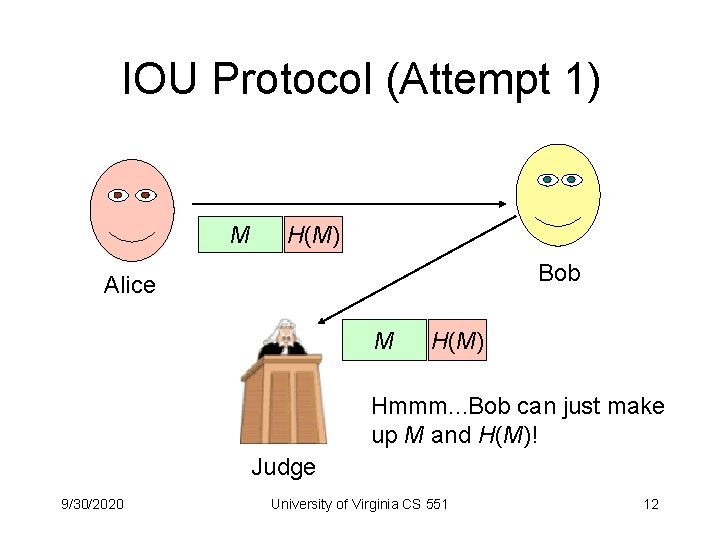
Using Hashes • Alice wants to send Bob and “I owe you” message. • Bob should be able to show the message to a judge to compel Alice to pay up. • Bob should not be able to make his own “I owe you” from Alice, or change the contents of the one she sent him. 9/30/2020 University of Virginia CS 551 11

IOU Protocol (Attempt 1) M H(M) Bob Alice M H(M) Hmmm. . . Bob can just make up M and H(M)! Judge 9/30/2020 University of Virginia CS 551 12
![IOU Protocol Attempt 2 M EKAHM Bob Alice secret key KA Use DiffieHellman to IOU Protocol (Attempt 2) M EKA[H(M)] Bob Alice secret key KA Use Diffie-Hellman to](https://slidetodoc.com/presentation_image/9861dc94e87b98852bbc451ad891c7b4/image-13.jpg)
IOU Protocol (Attempt 2) M EKA[H(M)] Bob Alice secret key KA Use Diffie-Hellman to establish shared secret KA 9/30/2020 M Judge knows KA EKA[H(M)] Can Bob cheat? Can Alice cheat? Yes, send Bob: M, junk. Judge will think Bob cheated! University of Virginia CS 551 13
![IOU Protocol Attempt 3 M EKRAHM Bob knows KUA Alice KUA KRA 9302020 M IOU Protocol (Attempt 3) M EKRA[H(M)] Bob knows KUA Alice {KUA, KRA} 9/30/2020 M](https://slidetodoc.com/presentation_image/9861dc94e87b98852bbc451ad891c7b4/image-14.jpg)
IOU Protocol (Attempt 3) M EKRA[H(M)] Bob knows KUA Alice {KUA, KRA} 9/30/2020 M Judge knows KUA EKRA[H(M)] Bob can verify H(M) by decrypting, but cannot forge M, EKRA[H(M)] pair without knowing KRA. University of Virginia CS 551 14
![Weak Collision Resistance Suppose we use H char s s0 a Weak Collision Resistance • Suppose we use: H (char s[]) = (s[0] – ‘a’)](https://slidetodoc.com/presentation_image/9861dc94e87b98852bbc451ad891c7b4/image-15.jpg)
Weak Collision Resistance • Suppose we use: H (char s[]) = (s[0] – ‘a’) mod 10 • Alice sends Bob: “I, Alice, owe Bob $2. ”, EKRA[H (M)] • Bob sends Judge: “I, Alice, owe Bob $200000000. ”, EKRA[H (M)] • Judge validates EKUA [ EKRA[H (M)]] = H(“I, Alice, owe Bob $200000000. ”) and makes Alice pay. 9/30/2020 University of Virginia CS 551 15

Weak Collision Resistance • Given x, it should be hard to find y x such that H(y) = H(x). • Similar to a block cipher except no need for secret key: – Changing any bit of x should change most of H(x). – The mapping between x and H(x) should be confusing (complex and non-linear). 9/30/2020 University of Virginia CS 551 16

A Better Hash Function? • H(x) = DES (x, 0) • Weak collision resistance? – Given x, it should be hard to find y x such that H(y) = H(x). – Yes – DES is one-to-one. (These is no such y. ) • A good hash function? – No, its output is as big as the message! 9/30/2020 University of Virginia CS 551 17

What we need: • Produce small number of bits (say 64) that depend on the whole message in a confusing, non-linear way. • Have we seen anything like this? 9/30/2020 University of Virginia CS 551 18

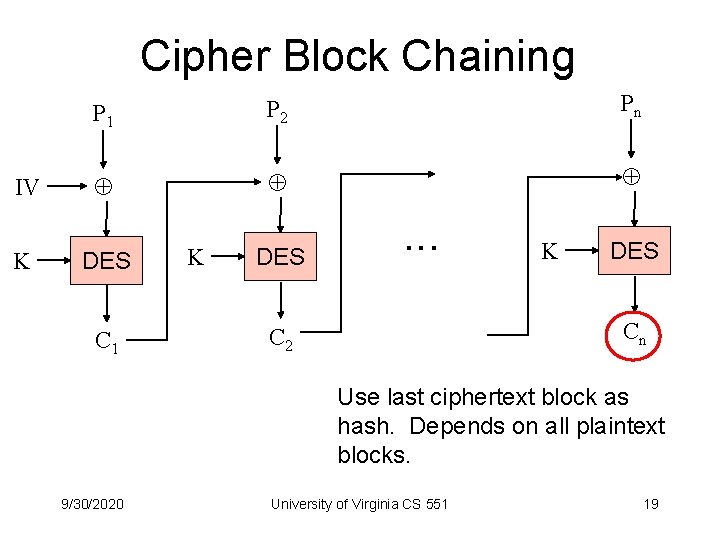
Cipher Block Chaining IV K P 1 P 2 Pn DES C 1 K DES . . . K DES Cn C 2 Use last ciphertext block as hash. Depends on all plaintext blocks. 9/30/2020 University of Virginia CS 551 19

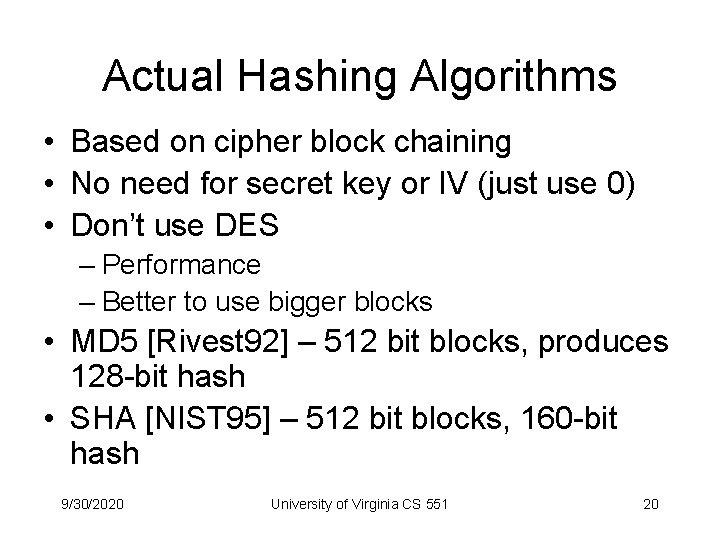
Actual Hashing Algorithms • Based on cipher block chaining • No need for secret key or IV (just use 0) • Don’t use DES – Performance – Better to use bigger blocks • MD 5 [Rivest 92] – 512 bit blocks, produces 128 -bit hash • SHA [NIST 95] – 512 bit blocks, 160 -bit hash 9/30/2020 University of Virginia CS 551 20

Why big hashes? • 3 DES is (probably) secure with 64 -bit blocks, why do secure hash functions need at least 128 bit digests? • 64 bits is fine for weak collision resistance, but we need strong collision resistance too. 9/30/2020 University of Virginia CS 551 21

Strong Collision Resistance • It is hard to find any x and y x such that H(y) = H(x). • Difference from weak: – Attacker gets to choose both x and y, not just y. • Scenario: – Suppose Bob gets to write IOU message, send it to Alice, and she signs it. 9/30/2020 University of Virginia CS 551 22
![IOU Request Protocol x EKRAHx Bob knows KUA Alice KUA KRA y EKRAHx Bob IOU Request Protocol x EKRA[H(x)] Bob knows KUA Alice {KUA, KRA} y EKRA[H(x)] Bob](https://slidetodoc.com/presentation_image/9861dc94e87b98852bbc451ad891c7b4/image-23.jpg)
IOU Request Protocol x EKRA[H(x)] Bob knows KUA Alice {KUA, KRA} y EKRA[H(x)] Bob picks x and y such that H(x) = H(y). 9/30/2020 Judge knows KUA University of Virginia CS 551 23

Finding x and y Bob generates 210 different agreeable (to Alice) xi messages: I, { Alice | Alice Hacker | Alice P. Hacker | Ms. A. Hacker }, { owe | agree to pay } Bob { the sum of | the amount of } { $2 | $2. 00 | 2 dollars | two dollars } { by | before } { January 1 st | 1 Jan | 1/1 | 1 -1 } { 2001 | 2001 AD}. 9/30/2020 University of Virginia CS 551 24

Finding x and y Bob generates 210 different agreeable (to Bob) yi messages: I, { Alice | Alice Hacker | Alice P. Hacker | Ms. A. Hacker }, { owe | agree to pay } Bob { the sum of | the amount of } { $2 quadrillion | $200000000 | 2 quadrillion dollars | two quadrillion dollars } { by | before } { January 1 st | 1 Jan | 1/1 | 11 } { 2001 | 2001 AD}. 9/30/2020 University of Virginia CS 551 25

Bob the Quadrillionaire!? • For each message xi and yi, Bob computes hxi = H(xi) and hyi = H(yi). • If hxi = hyj for some i and j, Bob sends Alice xi, gets EKRA[H(x)] back. • Bob sends the judge yj and EKRA[H(x)]. 9/30/2020 University of Virginia CS 551 26

Chances of Success • Hash function generate 64 -bit digest (n = 264) • Hash function is good (randomly distributed and diffuse) • Chance a randomly chosen message maps to a given hash value: 1 in n = 2 -64 • By hashing m good messages, chance that a randomly chosen message maps to one of the m different hash values: m * 2 -64 • By hashing m good messages and m bad messages: m * 2 -64 9/30/2020 University of Virginia CS 551 27

Is Bob a Quadrillionaire? • • • m = 210 * 2 -64 = 2 -44 (doesn’t look good. . . ) Try m = 232 * 2 -64 = 20 = 1 (yippee!) Flaw: some of the messages might hash to the same value, might need more than 232 to find match. 9/30/2020 University of Virginia CS 551 28

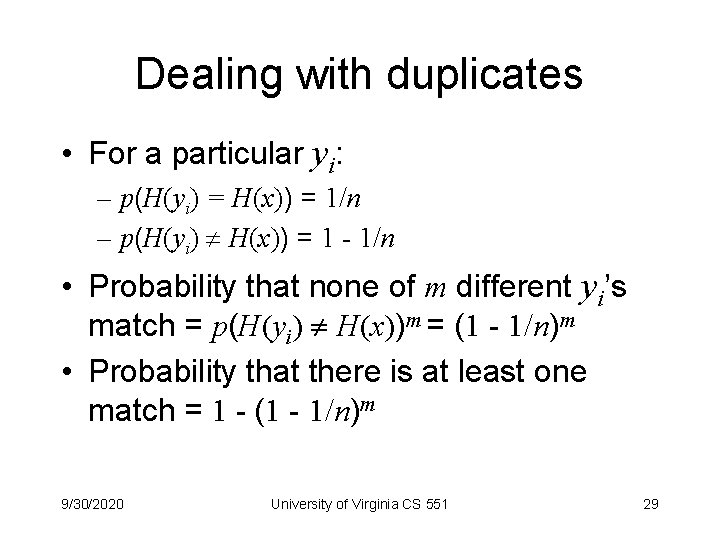
Dealing with duplicates • For a particular yi: – p(H(yi) = H(x)) = 1/n – p(H(yi) H(x)) = 1 - 1/n • Probability that none of m different yi’s match = p(H(yi) H(x))m = (1 - 1/n)m • Probability that there is at least one match = 1 - (1 - 1/n)m 9/30/2020 University of Virginia CS 551 29

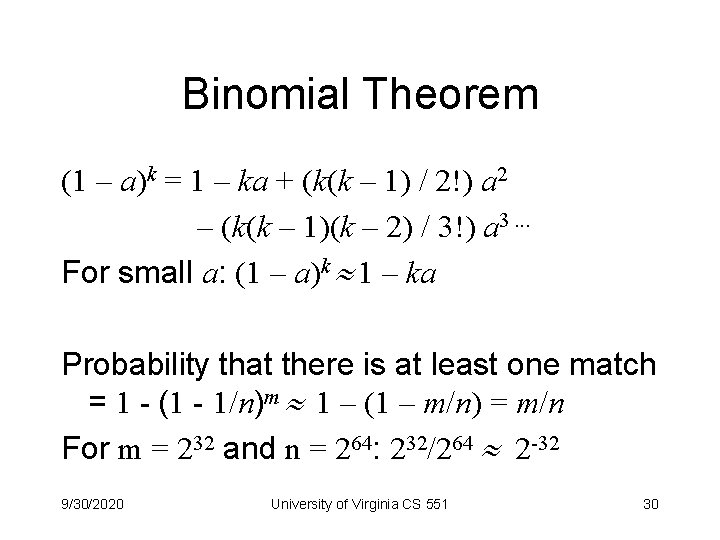
Binomial Theorem (1 – a)k = 1 – ka + (k(k – 1) / 2!) a 2 – (k(k – 1)(k – 2) / 3!) a 3. . . For small a: (1 – a)k 1 – ka Probability that there is at least one match = 1 - (1 - 1/n)m 1 – (1 – m/n) = m/n For m = 232 and n = 264: 232/264 2 -32 9/30/2020 University of Virginia CS 551 30

Birthday “Paradox” • What is the probability that a group of k people have 2 with the same birthday? 9/30/2020 University of Virginia CS 551 31

Birthday Paradox Ways to assign k different birthdays without duplicates: N = 365 * 364 *. . . * (365 – k + 1) = 365! / (365 – k)! Ways to assign k different birthdays with possible duplicates: D = 365 *. . . * 365 = 365 k 9/30/2020 University of Virginia CS 551 32

Birthday “Paradox” Assuming real birthdays assigned randomly: N/D = probability there are no duplicates 1 - N/D = probability there is a duplicates = 1 – 365! / ((365 – k!)(365)k ) For k = 48: > 95% 9/30/2020 University of Virginia CS 551 33

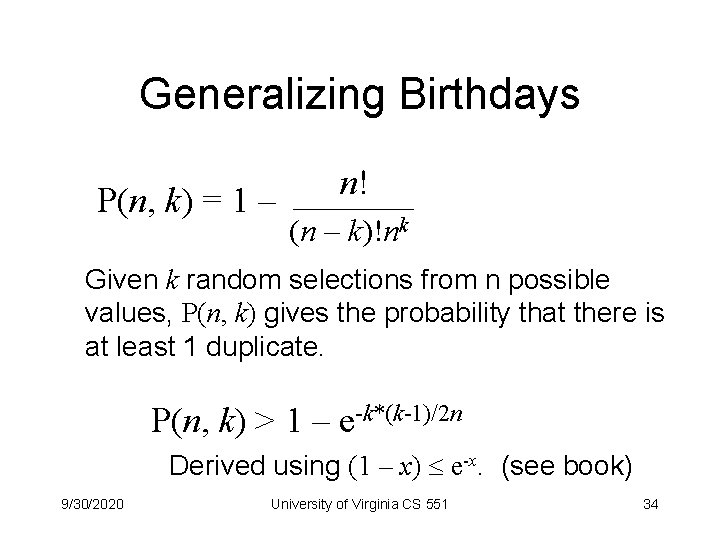
Generalizing Birthdays P(n, k) = 1 – n! (n – k)!nk Given k random selections from n possible values, P(n, k) gives the probability that there is at least 1 duplicate. P(n, k) > 1 – e-k*(k-1)/2 n Derived using (1 – x) e-x. (see book) 9/30/2020 University of Virginia CS 551 34

Applying Birthdays P(n, k) > 1 – e-k*(k-1)/2 n • For n = 365, k = 48: • • P(365, 48) > 1 – e-48*(47)/2*365 P(365, 48) >. 954 For n = 264, k = 232: P (264, 232) >. 39 For n = 264, k = 233: P (264, 233) >. 86 For n = 264, k = 234: P (264, 234) >. 9996 For n = 2128, k = 240: P (2128, 240) > 10 -15 9/30/2020 University of Virginia CS 551 35

Conclusion • If you’re Alice, don’t sign a hash for an IOU from Bob, unless the hash is at least 128 bits. 9/30/2020 University of Virginia CS 551 36

Charge • Full Project Proposals due Oct 4 • Next time: $$$$ KUA chainmailinc. com Guest lecture C = E A KRchainmail[Time 1, IDA, KUA] Paco Hope, chainmailinc. com Alice 9/30/2020 University of Virginia CS 551 37