Lecture 5 Introducing Network Design Concepts Designing and

- Slides: 36

Lecture 5: Introducing Network Design Concepts Designing and Supporting Computer Networks – Chapter 1 ITE I Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 1

Objectives § Explain how a hierarchical network design creates a stable, reliable, scalable network § Explain what factors need to be considered when the Core Layer of a network is designed and implemented § Explain which factors need to be considered when the Distribution Layer of a network is designed and implemented § Explain which factors need to be considered when the Access Layer of a network is designed and implemented § Describe the benefits and security implications of creating server farms § Describe the considerations of an implementation of a wireless network design § Describe the factors that affect the implementation of VPNs, including how remote workers can be supported ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 2

Explain How a Hierarchical Network Design Creates a Stable, Reliable, Scalable Network requirements: § Ease of management § Fast recovery § Application response time § Fast troubleshooting ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 3

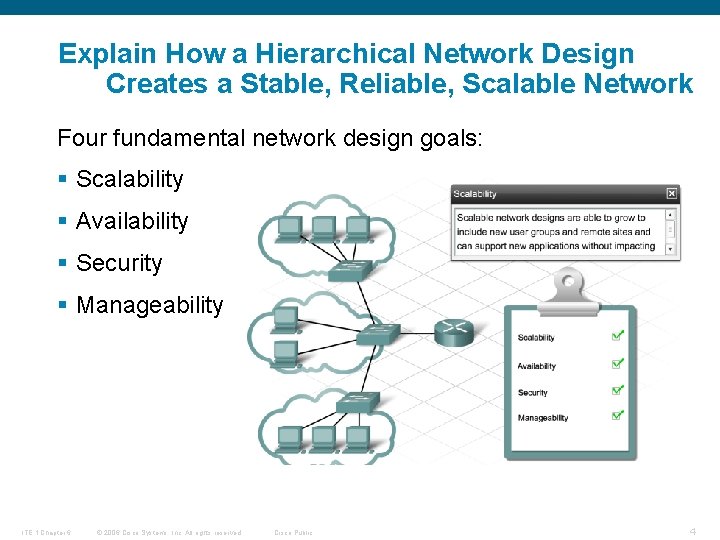
Explain How a Hierarchical Network Design Creates a Stable, Reliable, Scalable Network Four fundamental network design goals: § Scalability § Availability § Security § Manageability ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 4

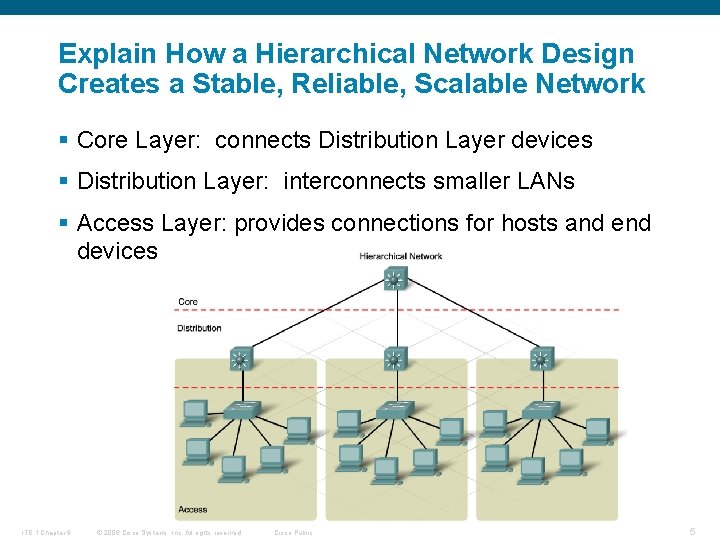
Explain How a Hierarchical Network Design Creates a Stable, Reliable, Scalable Network § Core Layer: connects Distribution Layer devices § Distribution Layer: interconnects smaller LANs § Access Layer: provides connections for hosts and end devices ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 5

Explain How a Hierarchical Network Design Creates a Stable, Reliable, Scalable Network Steps in network design projects: § Identify the network requirements § Characterize the existing network § Design the network topology and solutions ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 6

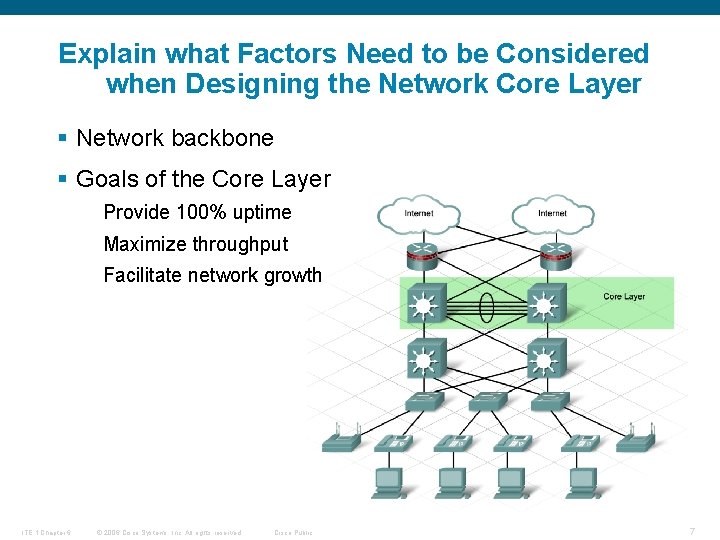
Explain what Factors Need to be Considered when Designing the Network Core Layer § Network backbone § Goals of the Core Layer Provide 100% uptime Maximize throughput Facilitate network growth ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 7

Explain what Factors Need to be Considered when Designing the Network Core Layer § Combining routing and switching in the same device § Redundancy and load balancing § High-speed and aggregate links § Quick convergence Network convergence refers to the coexistence of three networks within a single network: video transmission, a telephone network and data communication. It makes network stable and fully functional to work. ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 8

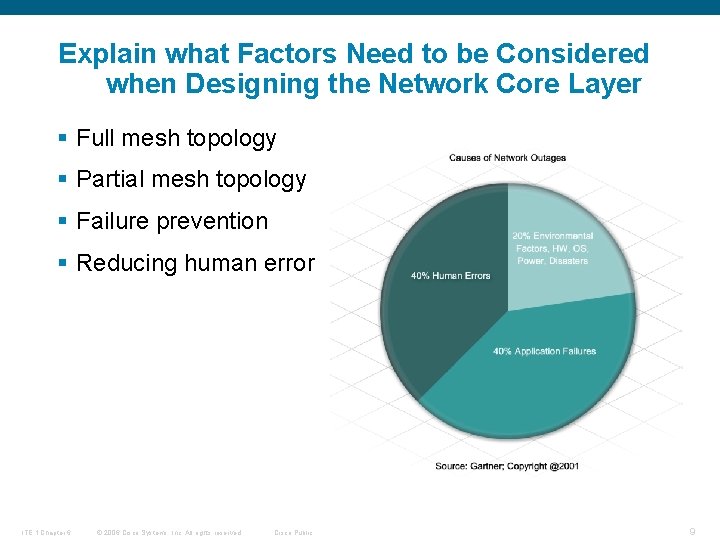
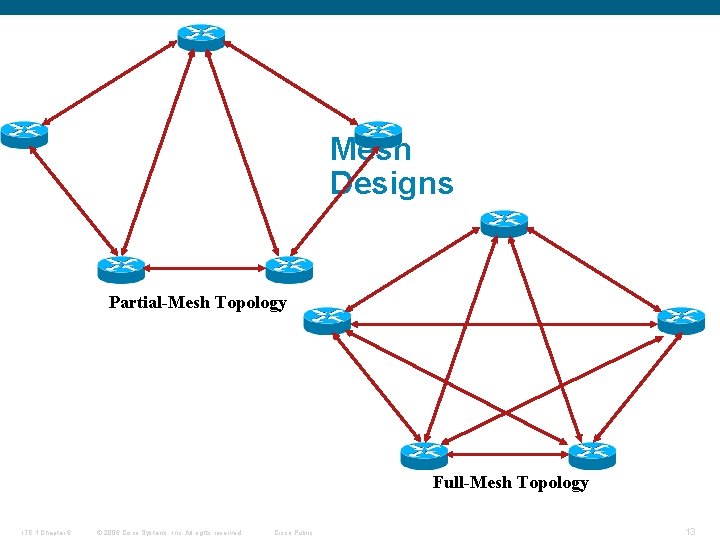
Explain what Factors Need to be Considered when Designing the Network Core Layer § Full mesh topology § Partial mesh topology § Failure prevention § Reducing human error ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 9

Why Use a Hierarchical Model? § Reduces workload on network devices Avoids devices having to communicate with too many other devices (reduces “CPU adjacencies”) § Constrains broadcast domains § Enhances simplicity and understanding § Facilitates changes § Facilitates scaling to a larger size ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 10

Cisco’s Hierarchical Design Model § A core layer of high-end routers and switches that are optimized for availability and speed § A distribution layer of routers and switches that implement policies and segment traffic § An access layer that connects users via hubs, switches, and other devices ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 11

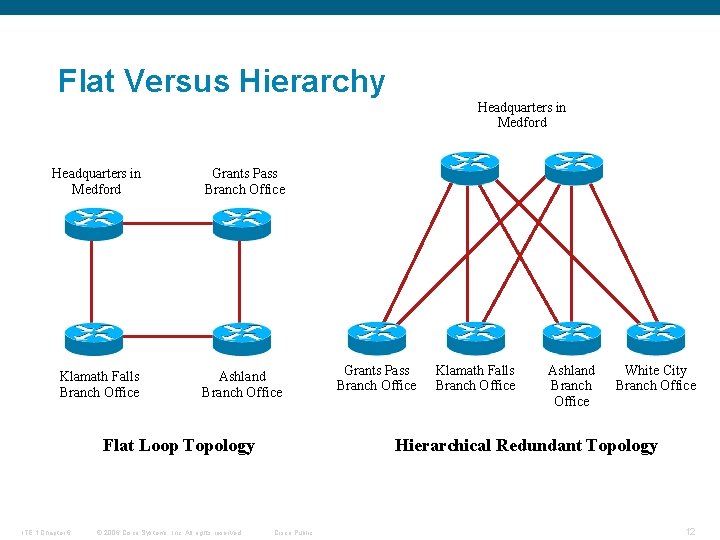
Flat Versus Hierarchy Headquarters in Medford Grants Pass Branch Office Klamath Falls Branch Office Ashland Branch Office Flat Loop Topology ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Grants Pass Branch Office Klamath Falls Branch Office Ashland Branch Office White City Branch Office Hierarchical Redundant Topology Cisco Public 12

Mesh Designs Partial-Mesh Topology Full-Mesh Topology ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 13

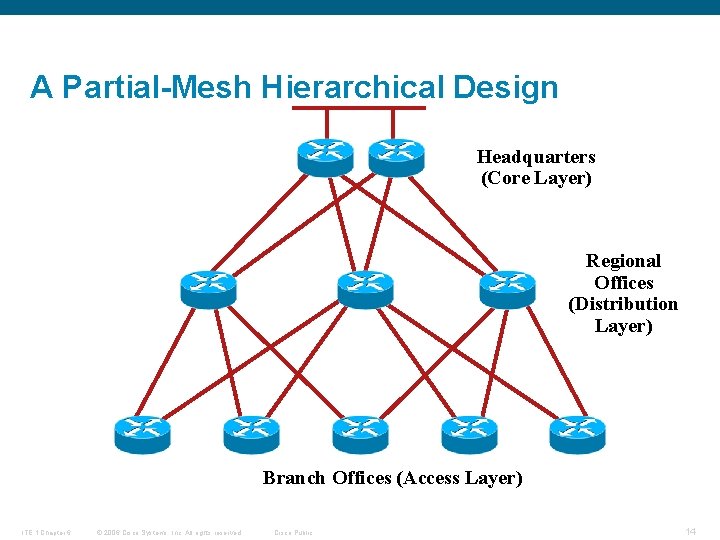
A Partial-Mesh Hierarchical Design Headquarters (Core Layer) Regional Offices (Distribution Layer) Branch Offices (Access Layer) ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 14

Explain which Factors Need to be Considered when Designing the Distribution Layer of a Network § Filtering and managing traffic flow § Access control policies § Route summarization § Isolating Core Layer from Access Layer failures § Routing between VLANs VLAN: is an emulation of a standard LAN that allows data transfer to take place without the traditional physical restraints placed on a network. ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 15

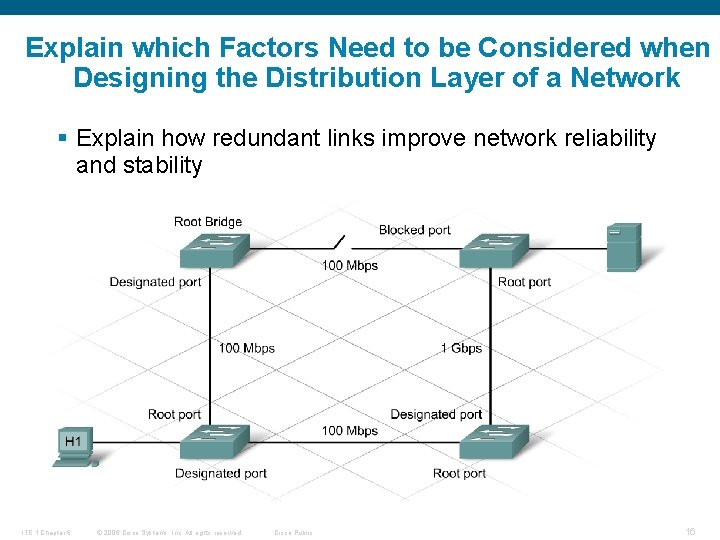
Explain which Factors Need to be Considered when Designing the Distribution Layer of a Network § Explain how redundant links improve network reliability and stability ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 16

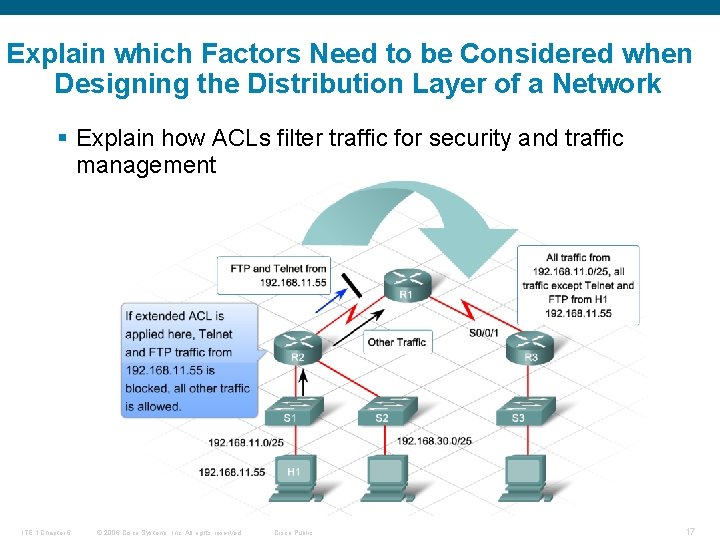
Explain which Factors Need to be Considered when Designing the Distribution Layer of a Network § Explain how ACLs filter traffic for security and traffic management ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 17

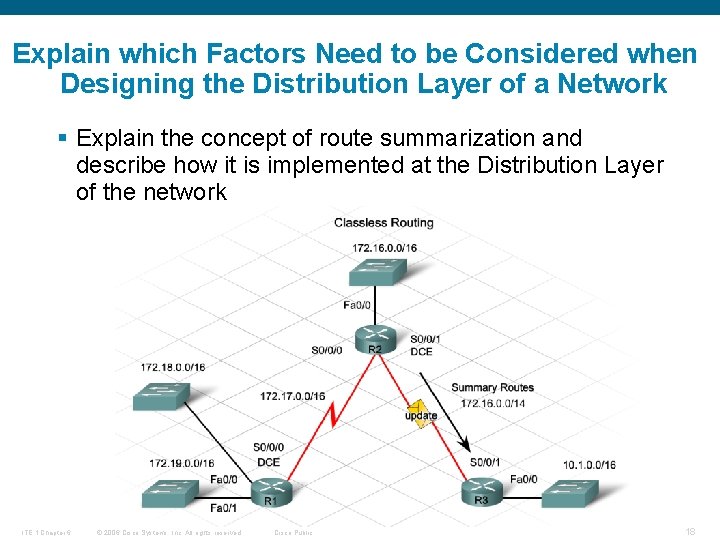
Explain which Factors Need to be Considered when Designing the Distribution Layer of a Network § Explain the concept of route summarization and describe how it is implemented at the Distribution Layer of the network ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 18

Explain which Factors Need to be Considered when Designing the Access Layer of a Network § Physical location of equipment § Wiring closets § Converged networking § Availability ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 19

Explain which Factors Need to be Considered when Designing the Access Layer of a Network § Naming structures § VLAN architecture § Traffic patterns § Prioritization strategies ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 20

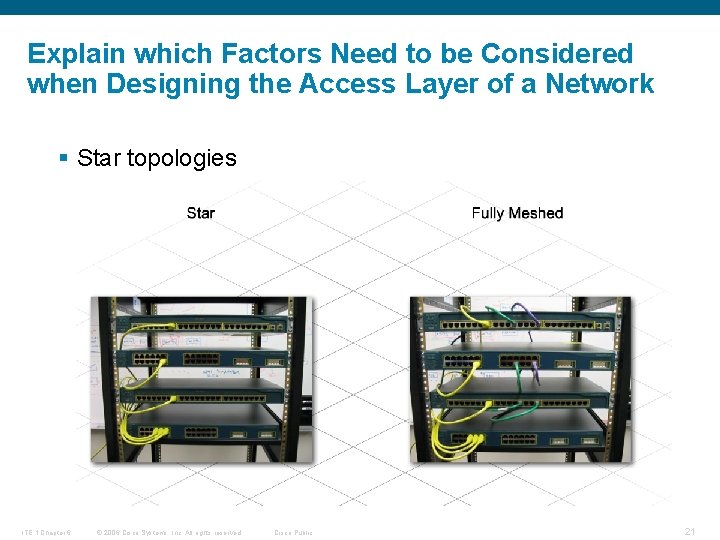
Explain which Factors Need to be Considered when Designing the Access Layer of a Network § Star topologies ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 21

Explain which Factors Need to be Considered when Designing the Access Layer of a Network Functions of VLANs: § Separate and classify traffic § Control broadcasts § Contain VLANs within a single wiring closet ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 22

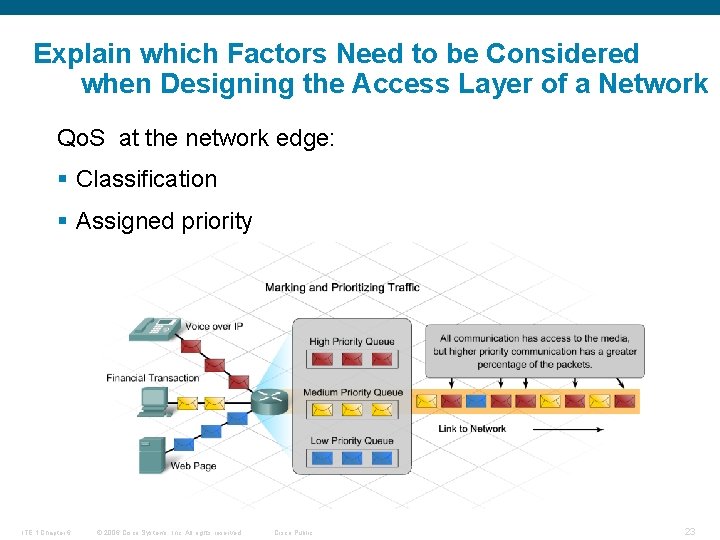
Explain which Factors Need to be Considered when Designing the Access Layer of a Network Qo. S at the network edge: § Classification § Assigned priority ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 23

Explain which Factors Need to be Considered when Designing the Access Layer of a Network Security risks at the network edge: § Authentication § Wireless security ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 24

Explain which Factors Need to be Considered when Designing the Access Layer of a Network Security measures at the Access Layer: § Physical security § Strong passwords § SSH (Secure Shell Protocol) A protocol for that offers encrypted remote access for devices § Disabling unused ports § Security policy ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 25

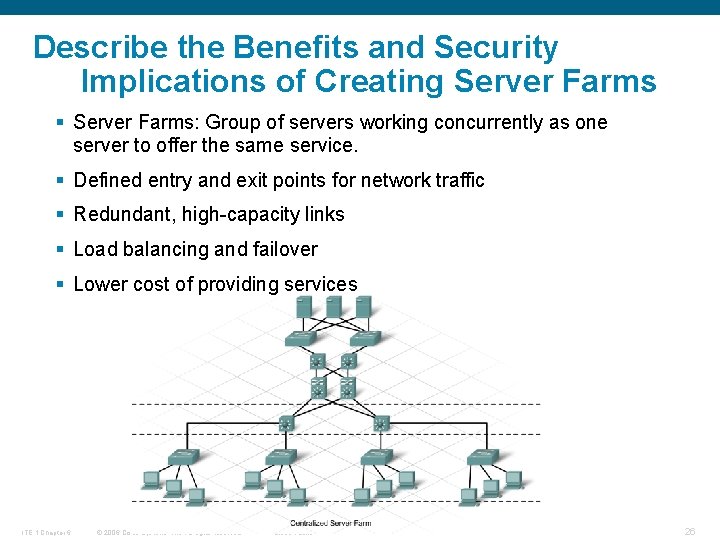
Describe the Benefits and Security Implications of Creating Server Farms § Server Farms: Group of servers working concurrently as one server to offer the same service. § Defined entry and exit points for network traffic § Redundant, high-capacity links § Load balancing and failover § Lower cost of providing services ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 26

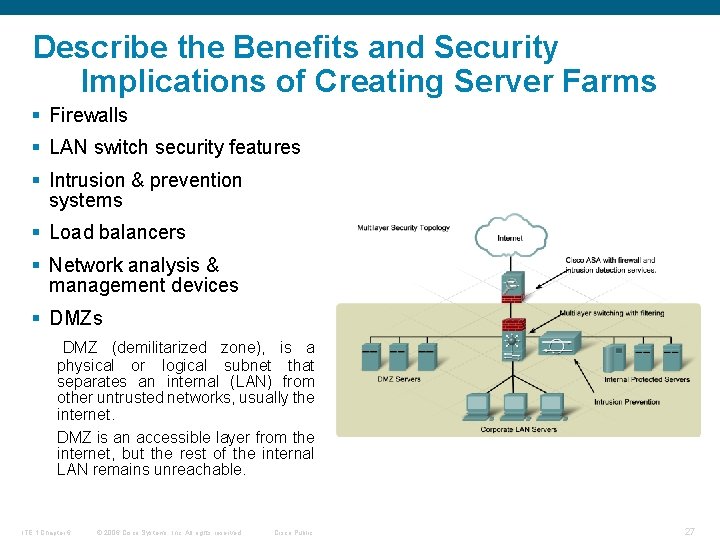
Describe the Benefits and Security Implications of Creating Server Farms § Firewalls § LAN switch security features § Intrusion & prevention systems § Load balancers § Network analysis & management devices § DMZs DMZ (demilitarized zone), is a physical or logical subnet that separates an internal (LAN) from other untrusted networks, usually the internet. DMZ is an accessible layer from the internet, but the rest of the internal LAN remains unreachable. ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 27

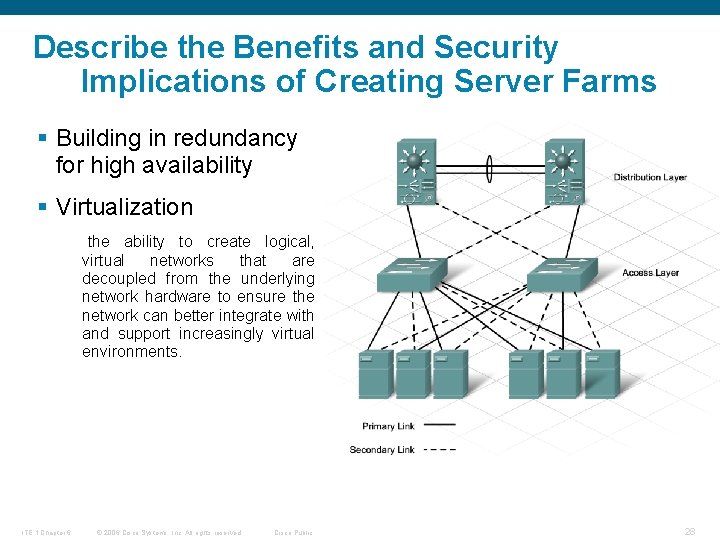
Describe the Benefits and Security Implications of Creating Server Farms § Building in redundancy for high availability § Virtualization the ability to create logical, virtual networks that are decoupled from the underlying network hardware to ensure the network can better integrate with and support increasingly virtual environments. ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 28

Describe the Considerations of an Implementation of a Wireless Network Design Customer requirements: § Roaming § Authentication § Services and applications § Encryption § Coverage and number of users ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 29

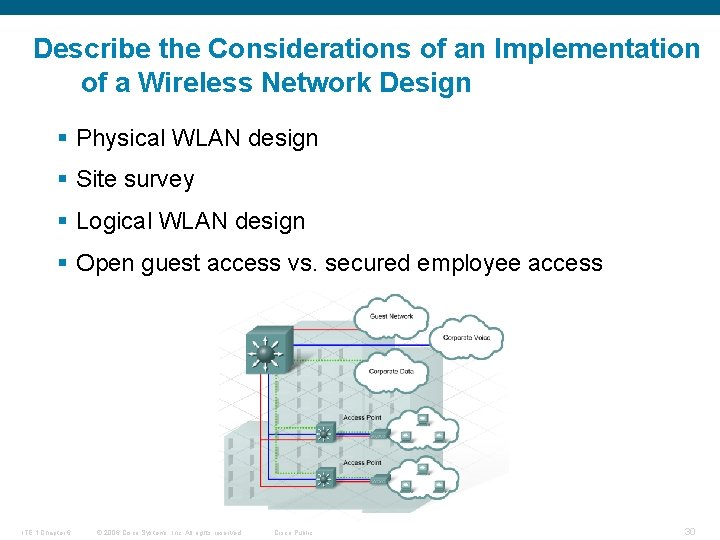
Describe the Considerations of an Implementation of a Wireless Network Design § Physical WLAN design § Site survey § Logical WLAN design § Open guest access vs. secured employee access ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 30

Describe the Factors that Affect the Implementation of VPNs § Cost of bandwidth § Qo. S § Security § Remote access ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 31

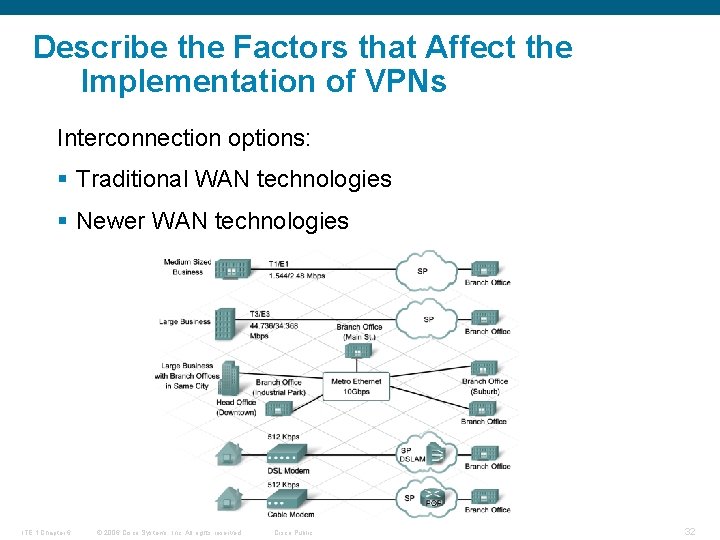
Describe the Factors that Affect the Implementation of VPNs Interconnection options: § Traditional WAN technologies § Newer WAN technologies ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 32

Describe the Factors that Affect the Implementation of VPNs § Explain ways to provide redundant connectivity to remote sites ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 33

How Can You Tell When You Have a Good Design? § When you already know how to add a new building, floor, WAN link, remote site, ecommerce service, and so on § When new additions cause only local change, to the directly connected devices § When your network can double or triple in size without major design changes § When troubleshooting is easy because there are no complex protocol interactions to disturb you. ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 34

Summary § The four fundamental technical requirements of network design are scalability, availability, security and manageability. § Network projects involve identifying the requirements, characterizing the existing network, and designing the network topology and solutions. § Redundancy at the Core Layer keeps the network functioning even when a device or link fails. § Routing efficiency at the Distribution Layer isolates the Core from Access Layer failures. § Using VLANs and IP subnets is the most common way to segregate user groups and traffic within the Access Layer. ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 35

ITE 1 Chapter 6 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 36