Lecture 3 Basic Cryptography part 2 Digital Signatures

Lecture 3: Basic Cryptography (part 2) Digital Signatures Decentralized Identity Management Putting together a cryptocurrency Reference: Chapter 1. 4, 1. 5. Princeton University Press book

Digital Signatures Key generation Signature (secretkey, publickey) = Generatekeys(keysize) Sig = sign(secretkey, message) Randomized function Verification verify(publickey, Sig, message)

Unforgeable Signatures Unforgeable ECDSA Computationally hard to generate a verifiable signature without knowing the secret key Elliptic Curve Digital Signature Algorithms Cryptographicaly secure against an adaptive adversary
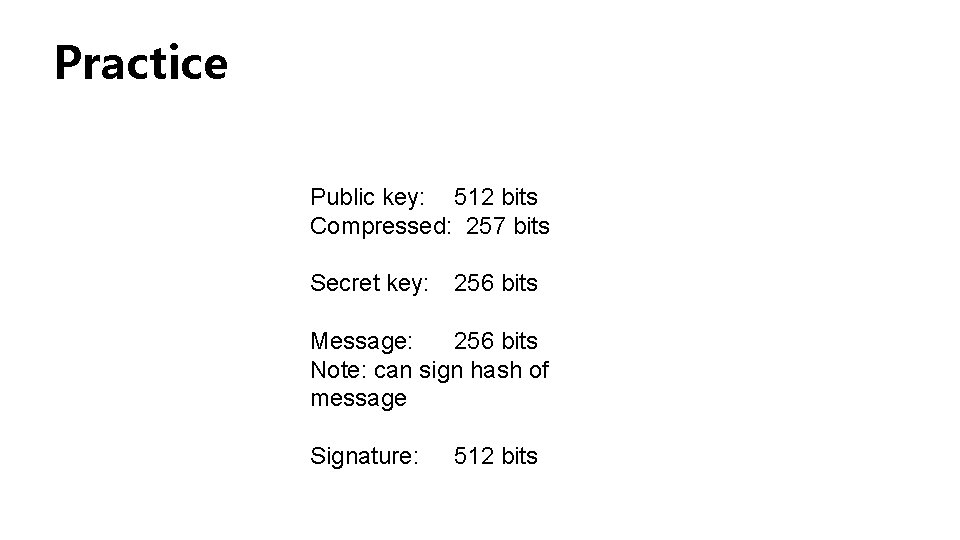
Practice Public key: 512 bits Compressed: 257 bits Secret key: 256 bits Message: 256 bits Note: can sign hash of message Signature: 512 bits

Decentralized Identity Management Public keys are your identity address in Bitcoin terminology Can create multiple identities (publickey, secretkey) pairs publish publickey sign using secretkey Can create oneself verifiable by others

Putting Together: Basic Cryptocurrencies Attempt 1: Goofycoin Transaction: Coin: (coin. ID, signature of Goofy) Goofy creates coins This: hash pointer to coin Alice: publickey of Alice Transaction: Transfer of coin ownership Signed by owner of coin Pay this to Alice
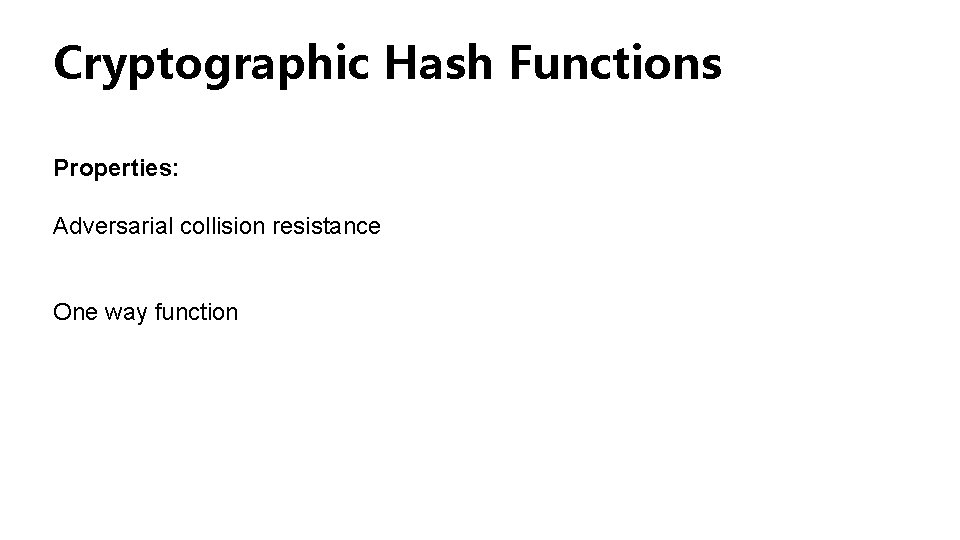
Cryptographic Hash Functions Properties: Adversarial collision resistance One way function

Hash Pointer to location of information + hash of the information Regular pointer: retrieve information Hash pointer: retrieve information and verify the information has not changed

Goofy Coin Good news: Validity and ownership of coins Bad news: double spending
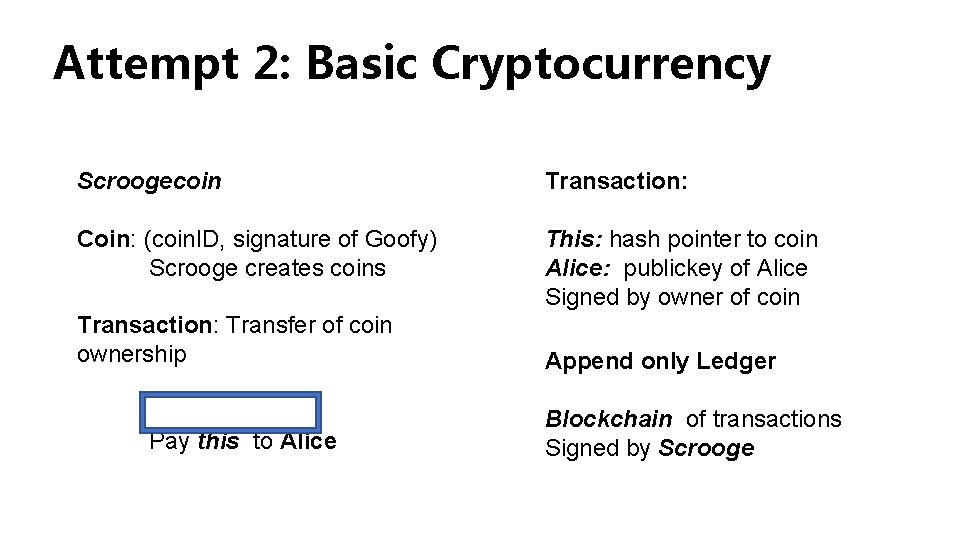
Attempt 2: Basic Cryptocurrency Scroogecoin Transaction: Coin: (coin. ID, signature of Goofy) Scrooge creates coins This: hash pointer to coin Alice: publickey of Alice Signed by owner of coin Transaction: Transfer of coin ownership Pay this to Alice Append only Ledger Blockchain of transactions Signed by Scrooge

Blockchain: a linked list via hash pointers Block: Header + Data Header: Pointer to location of previous block + hash of the previous block Data: information specific to the block Application: tamper evident information log Head of the chain being known is enough to find tamper evidence in any internal block Hence the phrase: block chain blockchain
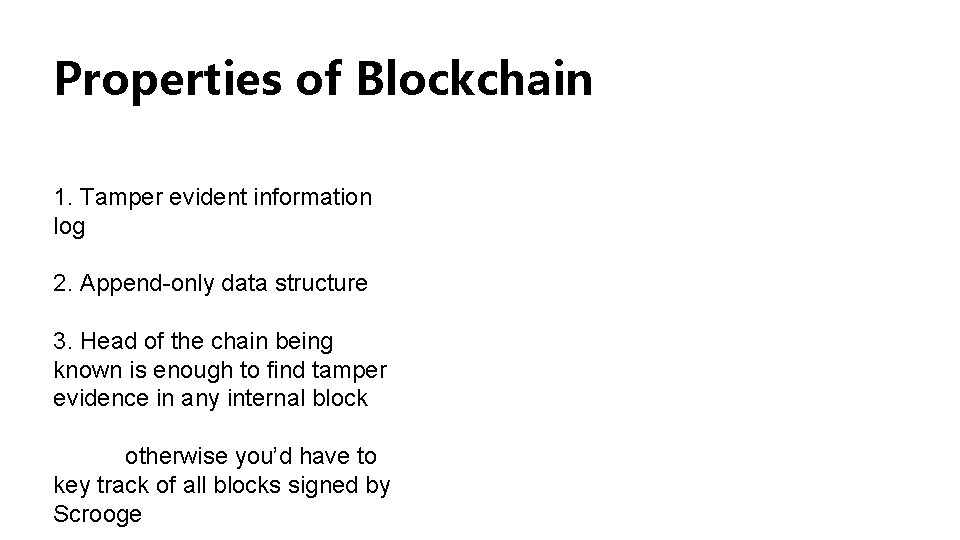
Properties of Blockchain 1. Tamper evident information log 2. Append-only data structure 3. Head of the chain being known is enough to find tamper evidence in any internal block otherwise you’d have to key track of all blocks signed by Scrooge
Scrooge. Coin Createcoins can only be created by Scrooge multiple coins created at the same time each coin has a recipient (identified via public key) Paycoins Overall block signed by Scrooge consumed coins (list) coins created (list) Total wealth consumed = total wealth created
- Slides: 13