Lecture 20 Firewalls and Intrusion Detection CS 551



























- Slides: 42

Lecture 20: Firewalls and Intrusion Detection CS 551: Security and Privacy David Evans University of Virginia CS 551 http: //www. cs. virginia. edu/~evans Computer Science

Menu • • Firewalls How to give a good project presentation Traditional Intrusion Detection Computer Immunology 11/2/2020 University of Virginia CS 551 2

Voting Challenge #1 • Why witness must observe opening Envelope A? – Your answer should be 6 words long – Or, your answer should cite government explanation 11/2/2020 University of Virginia CS 551 3

Voting Challenge #2 • Improved absentee ballot protocol – Must be as (or almost as) convenient as current procotol cannot require voter to use computer to vote – Should provide better integrity (my vote is counted right) and anonymity (no one can tell who I voted for) than current system 11/2/2020 University of Virginia CS 551 4

11/2/2020 University of Virginia CS 551 5

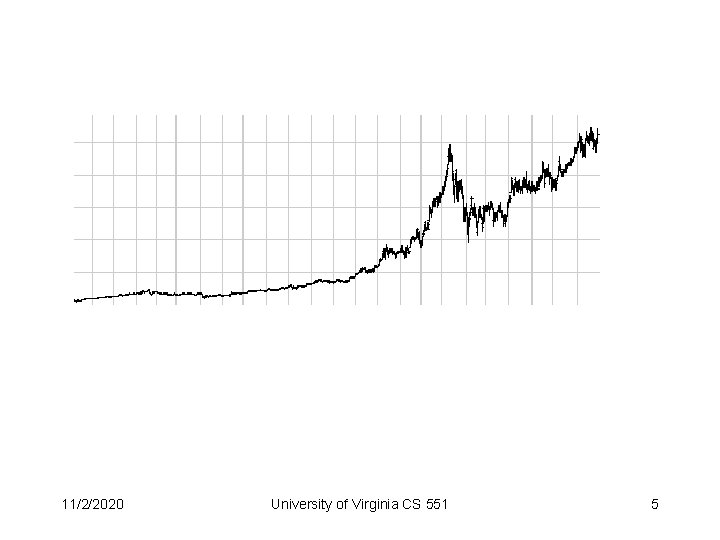
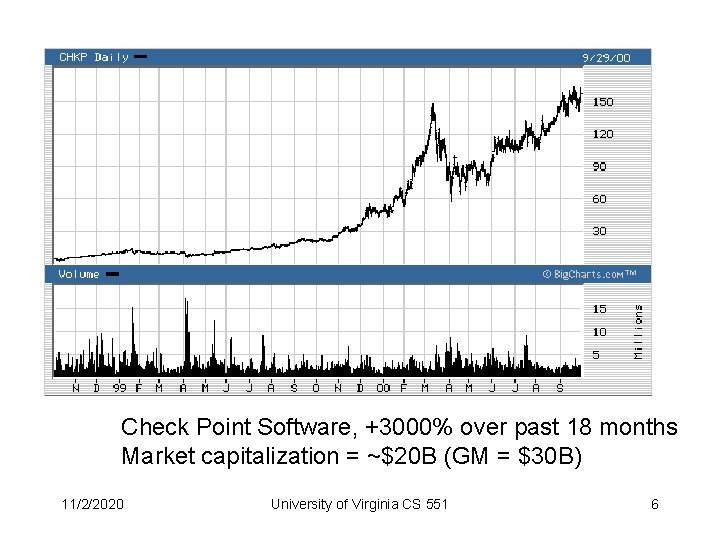
Check Point Software, +3000% over past 18 months Market capitalization = ~$20 B (GM = $30 B) 11/2/2020 University of Virginia CS 551 6

11/2/2020 University of Virginia CS 551 7

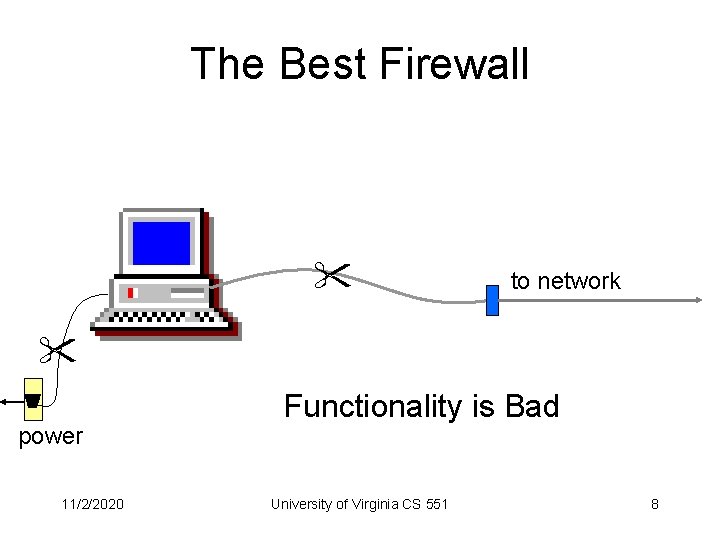
The Best Firewall to network power 11/2/2020 Functionality is Bad University of Virginia CS 551 8

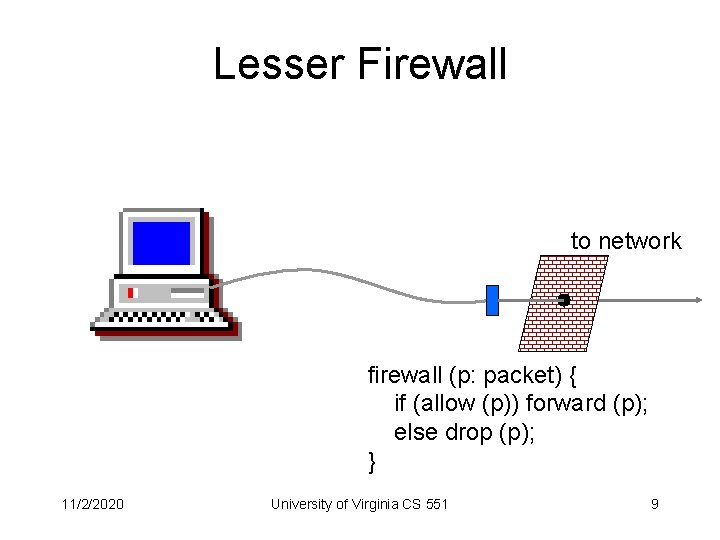
Lesser Firewall to network firewall (p: packet) { if (allow (p)) forward (p); else drop (p); } 11/2/2020 University of Virginia CS 551 9

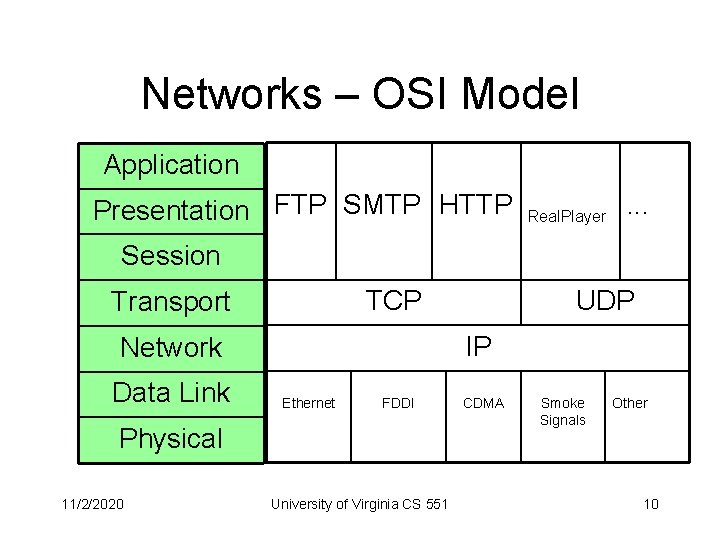
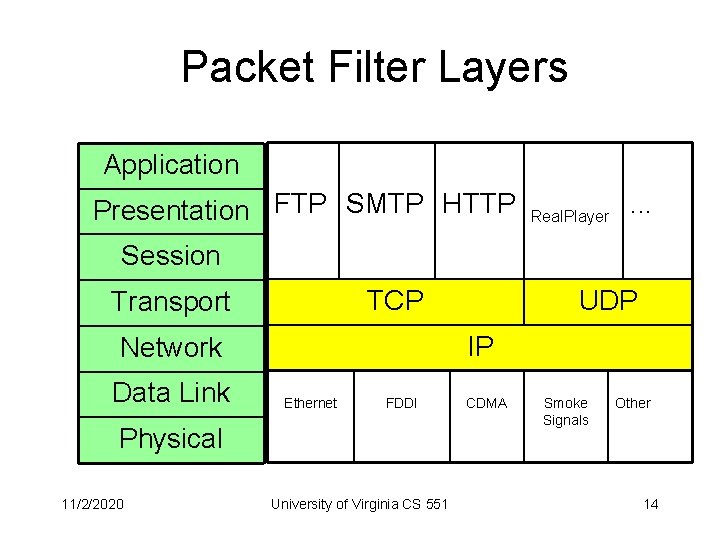
Networks – OSI Model Application Presentation FTP SMTP HTTP Real. Player . . . Session TCP Transport IP Network Data Link Ethernet FDDI Physical 11/2/2020 UDP University of Virginia CS 551 CDMA Smoke Signals Other 10

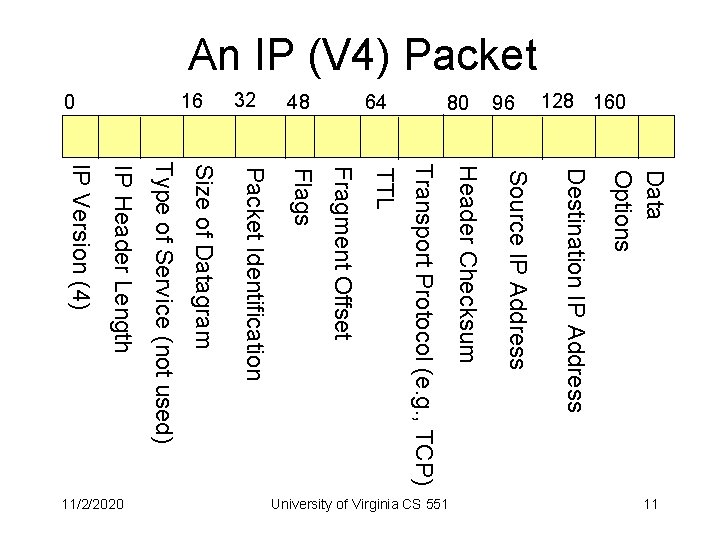
An IP (V 4) Packet Data Options Destination IP Address Source IP Address Header Checksum Transport Protocol (e. g. , TCP) TTL Fragment Offset Flags Packet Identification Size of Datagram Type of Service (not used) IP Header Length IP Version (4) 11 University of Virginia CS 551 11/2/2020 128 160 96 80 64 48 32 16 0

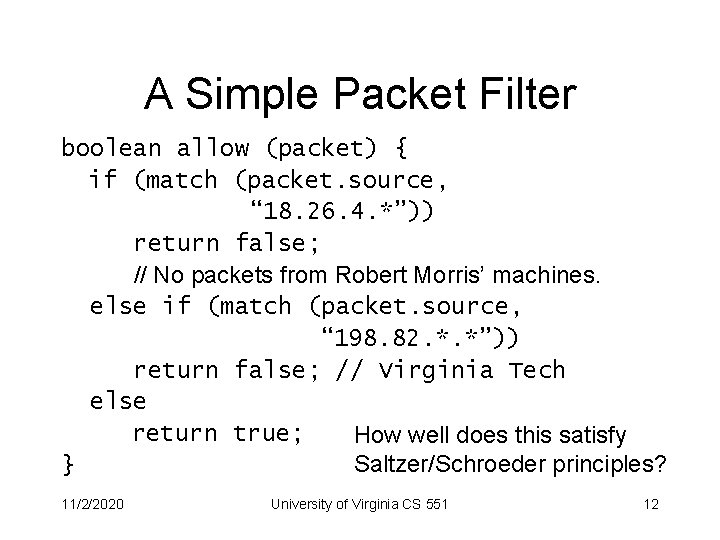
A Simple Packet Filter boolean allow (packet) { if (match (packet. source, “ 18. 26. 4. *”)) return false; // No packets from Robert Morris’ machines. else if (match (packet. source, “ 198. 82. *. *”)) return false; // Virginia Tech else return true; How well does this satisfy Saltzer/Schroeder principles? } 11/2/2020 University of Virginia CS 551 12

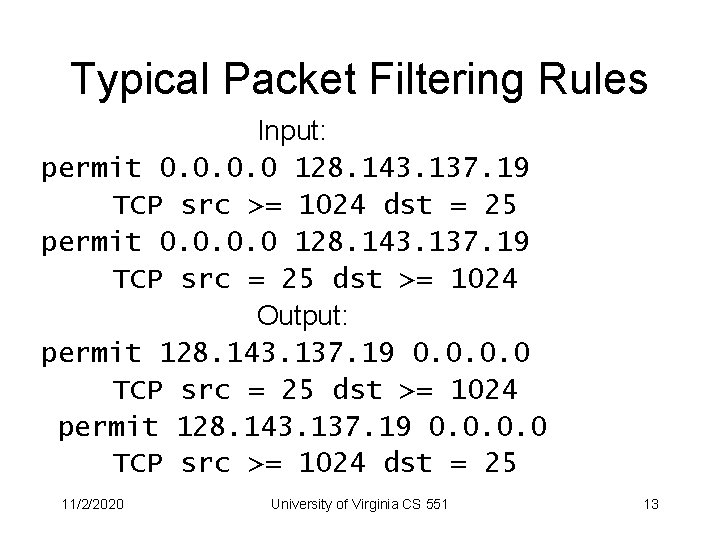
Typical Packet Filtering Rules Input: permit 0. 0 128. 143. 137. 19 TCP src >= 1024 dst = 25 permit 0. 0 128. 143. 137. 19 TCP src = 25 dst >= 1024 Output: permit 128. 143. 137. 19 0. 0 TCP src = 25 dst >= 1024 permit 128. 143. 137. 19 0. 0 TCP src >= 1024 dst = 25 11/2/2020 University of Virginia CS 551 13

Packet Filter Layers Application Presentation FTP SMTP HTTP Real. Player . . . Session TCP Transport IP Network Data Link Ethernet FDDI Physical 11/2/2020 UDP University of Virginia CS 551 CDMA Smoke Signals Other 14

Application-Layer Gateways • Analyze communication at application layer • All communication must go through a proxy that knows about application • Poor scalability, performance 11/2/2020 University of Virginia CS 551 15

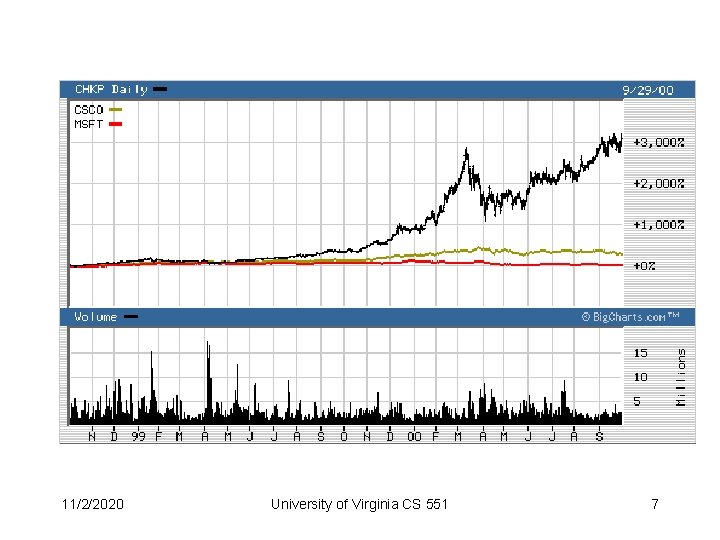
Why is a little Israeli firewall company worth $20 B? • Stateful Inspection – Intercept packets at network layer, but analyze at all communications layers – Maintain application-specific state • e. g. , Save PORT command of outgoing FTP session, compare with incoming FTP data – Programmable filters and manipulators – Provide a graphical front end for programming filters and monitoring activity 11/2/2020 University of Virginia CS 551 16

Project Presentations Tell a story, don’t read a list. 11/2/2020 University of Virginia CS 551 17

All Good Talks Tell a Story • Introduce characters (rabbit, fox) • Describe an important problem (fox wants to eat rabbit) • Relate events that resolve the problem (rabbit tells fox about thesis) • A few examples (rabbit tells wolf, . . . ) • Draw a general conclusion that is supported by your story (thesis doesn’t matter, only advisor) 11/2/2020 University of Virginia CS 551 18

Introduction • Introduce characters: motivate your work – Convey why the problem you are solving is interesting, important and exciting – Place your work in context: how is it different from what others have done • Teaser for your results – why should we listen to the rest of the talk? – Don’t need a full outline, but let audience know enough so they want to listen to the rest – Unlike Rabbit story, suspense is not good 11/2/2020 University of Virginia CS 551 19

Guts • Explain what you did – Don’t be comprehensive – convey the big picture – Use pictures, 1 -2 examples, etc. • Convey one technical nugget – Show one neat concrete thing that came out of your work. • Analysis – Did your work solve the problem? – What are the important results of your work 11/2/2020 University of Virginia CS 551 20

Conclusion Summarize your project with one key point. If your audience remembers one thing from your talk, you have succeeded. 11/2/2020 University of Virginia CS 551 21

Some Specific Advice • Average 2 minutes per slide • Your target audience is the other students in the class – Assume they know as much security as has been covered in the class • Use Pictures • Use Humor (but only if its relevant) • Don’t put this much text on any of your slides! 11/2/2020 University of Virginia CS 551 22

Can you do all this in 13 minutes? • Advertisers pay $2. 5 M for 30 seconds during Superbowl – they must be pretty sure they can tell a compelling story in that time • Seinfeld episode is 22 minutes long • Make your points directly, avoid unnecessary details • Organize your presentation 11/2/2020 University of Virginia CS 551 23

Practice! • Without an audience • In front of your teammates • In front of friends not familiar with your project • I will listen to any group that wants to practice their talk Tuesday Nov 28 th (email your preferred time 9 pm-midnight) and Sunday Dec 3 rd (after 7 pm) 11/2/2020 University of Virginia CS 551 24

Intrusion Detection 11/2/2020 University of Virginia CS 551 25

Why Detect Intruders? • Catch them before they cause damage and plug holes • Identify damage • Collect evidence for prosecution • Deterrent 11/2/2020 University of Virginia CS 551 26

Behavior Obviously Normal 11/2/2020 Obviously Malicious University of Virginia CS 551 27

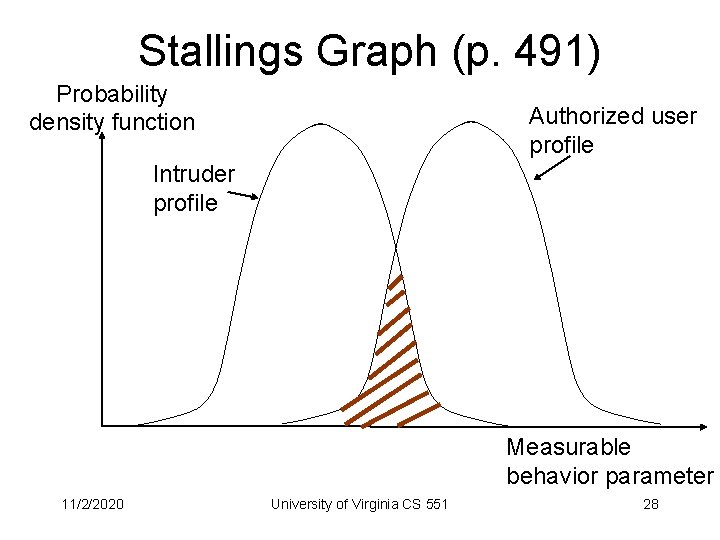
Stallings Graph (p. 491) Probability density function Authorized user profile Intruder profile Measurable behavior parameter 11/2/2020 University of Virginia CS 551 28

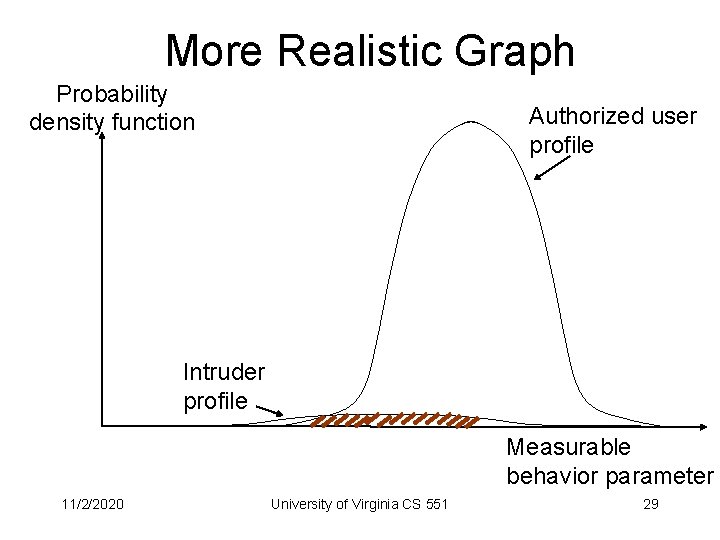
More Realistic Graph Probability density function Authorized user profile Intruder profile Measurable behavior parameter 11/2/2020 University of Virginia CS 551 29

False Positives Dilemma • Doctor invents a new, inexpensive test for a deadly disease that is 95% accurate • Assume 1 in 1000 people have deadly disease (but don’t know it yet) • Should everyone get the test? – – 1000 people tested Expect. 95 + (999 *. 05) positives 50 people will be told they have disease If you test positive, there is a 1/50 chance you have disease 11/2/2020 University of Virginia CS 551 30

Intrusion Detection Approaches • Statistical Anomaly Detection – Produce a profile of the normal behavior of each user (or independent of user) – Notice statistical deviations from that behavior • Rule-based Detection – Think really hard and make up rules that describe intruder behavior. – Hope intruders can’t read and figure out the rules also. 11/2/2020 University of Virginia CS 551 31

Detect an Intrusion • • Do nothing Email system administrator Page system administrator Shut down system 11/2/2020 University of Virginia CS 551 32

Network Intrusion Detection • Monitor activity on many hosts • Aggregate audit records to detect anomalous behavior • Managed Security Monitoring (Counterpane, Inc. ) – $12, 000/month 11/2/2020 University of Virginia CS 551 33

Challenges in Intrusion Detection • The first thing a smart intruder will do is tamper with the Intrusion Detection system! • Few activities are either obviously normal or obviously malicious • False positives dilemma 11/2/2020 University of Virginia CS 551 34

Immunology 11/2/2020 University of Virginia CS 551 35

Biological Inspiration • Biological systems are incredibly resilient • Most humans survive ~80 years • Before medical advances, most still would survive ~30 years • Operate in a hostile, unpredictable environment • No way to reboot, reinstall operating system, upgrade software, etc. • Human genome: 3 Billion base pairs = 6 Gb = 750 MB (Human genome project says 3 GB ? ? ) 11/2/2020 University of Virginia CS 551 36

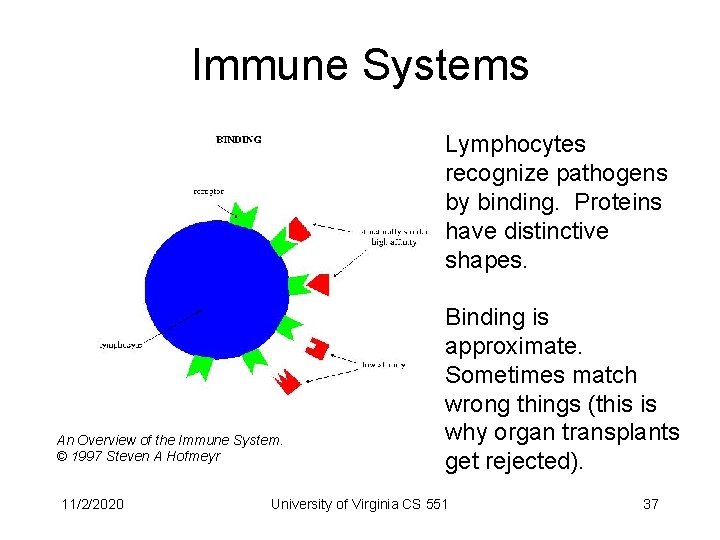
Immune Systems Lymphocytes recognize pathogens by binding. Proteins have distinctive shapes. An Overview of the Immune System. © 1997 Steven A Hofmeyr 11/2/2020 Binding is approximate. Sometimes match wrong things (this is why organ transplants get rejected). University of Virginia CS 551 37

Receptor Diversity • Need to recognize all foreign intruders, but DNA can’t know about all possible intruders • Gene segments are randomly combined to form different receptors – About 108 – 1012 different receptors 11/2/2020 University of Virginia CS 551 38

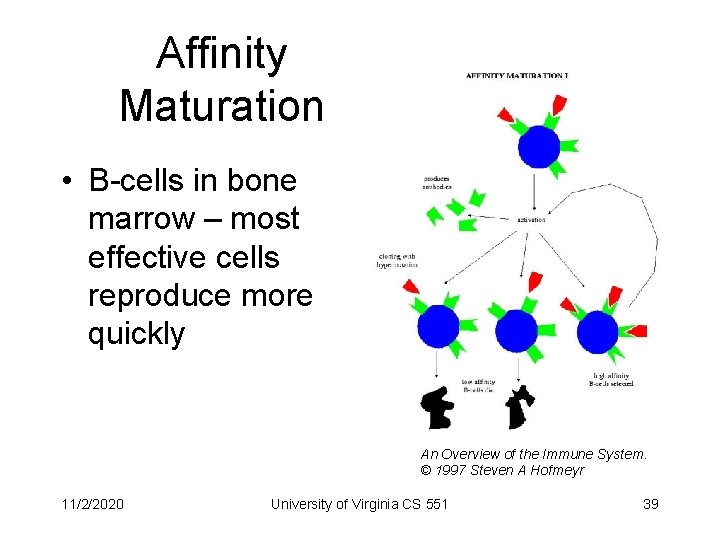
Affinity Maturation • B-cells in bone marrow – most effective cells reproduce more quickly An Overview of the Immune System. © 1997 Steven A Hofmeyr 11/2/2020 University of Virginia CS 551 39

Can computers do this? • Programs identified by sequences of system calls • Build a database of normal patterns (how? ) • Receptors recognize unusual patterns • Enough unusual patterns is considered an intrusion 11/2/2020 University of Virginia CS 551 40

Fatal Flaw? • Might work okay if no one important is using it. • Will it work if an attacker knows about it and is deliberately constructing an attack to avoid detection? – Do biological viruses evolve to mimic host proteins? 11/2/2020 University of Virginia CS 551 41

Charge • Next time – pick one: – Denial of service attacks and countermeasures – Law/Politics: Carnivore, Encryption Policy, Digital Signatures – Security Policies: MAC/DAC, Chinese Wall, Orange Book – Other? • Send email/tell me your suggestions before Wednesday (if I don’t get any, I’ll talk about formal logics for analyzing security protocols) 11/2/2020 University of Virginia CS 551 42