Lecture 2 Introduction to the concepts of IT












- Slides: 25

Lecture 2 Introduction to the concepts of IT auditing 1

Contents • • Architecture IT-function of an enterprise Enterprise risk management Computer fraud techniques Dept of Mathematics and Computer Science 2

Architecture (1) We distinguish EIS architecture and Enterprise Architecture. (We start with the first one. ) Architecture is used: 1. 2. 3. 4. 5. 6. 7. To understand a system To document a system To divide and conquer in the development To define and select components To test and integrate components To monitor the system when it is operational To modify the system Dept of Mathematics and Computer Science 3

Architecture (2) 4 Architecture: • The architecture of a system is a consistent set of views and rules of the system • Each view (model) consists of: – the set of components the system is made of – the external properties of the components – the relationships between the components • A rule is a constraint on a view or on a combination of views Often we have graphical models Dept of Mathematics and Computer Science

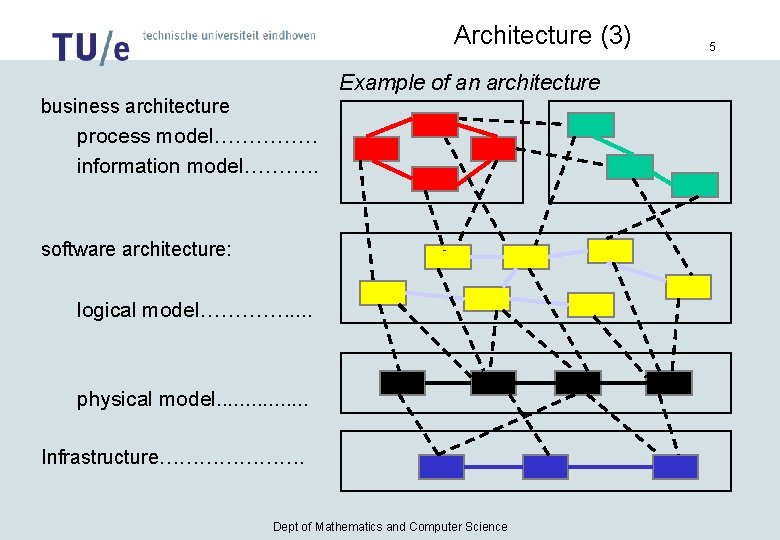
Architecture (3) Example of an architecture business architecture process model…………… information model………. . software architecture: logical model…………. . . physical model. . . . Infrastructure…………………. Dept of Mathematics and Computer Science 5

Architecture (4) • two types of relationships between components in one view: – interaction relations e. g. : “uses”, control flow, dataflow – structural relations e. g. : hierarchy, is-partof, is-specialization-of • many types of relationships between different views , e. g. is-realized-by, is-implemented-on Dept of Mathematics and Computer Science 6

Architecture (5) Architecture is more than views and rules: • • • architecture languages: modeling languages to described the views architecture patterns: standard solutions for generic problems architecture principles: in fact standard structural rules (to be adopted or modified in a specific architecture) Dept of Mathematics and Computer Science 7

Architecture (6) Architectural languages: • Distinguish: – – – • • component aspect data aspect, process aspect transformation aspect Component aspect: Rose. RT, Koala, SCA (SOA), hierachical Petri nets Data aspect: modeling languages like ER, relational model, functional model, UML class model, XML models (XSD) Dept of Mathematics and Computer Science 8

Architecture (7) • Process aspect: – Academic languages: • • • – • Transition systems (automaton, I/O automaton) Process algebra’s (CSP, CSS, ACP, Pi-calculus) Petri nets (classical P/T nets, colored Petri nets) Industrial languages, e. g. DFD, SADT, ECP, UML activity diagrams, UML state charts, BPEL, BPMN Transformation aspect: – – Specification languages such as Z, B, VDM Functional or logical (programming) languages Dept of Mathematics and Computer Science 9

Architecture (9) Enterprise Architecture: • An enterprise is itself a system, so it has an architecture • The components are Business Units (BU), • • • they can be nested (hierarchy). Each component is either atomic or composite Each BU has a Control Unit (CU) is concerned with – – Planning Control Coordination between the internal BU’s Reporting to surrounding BU or external stakeholders Dept of Mathematics and Computer Science 10

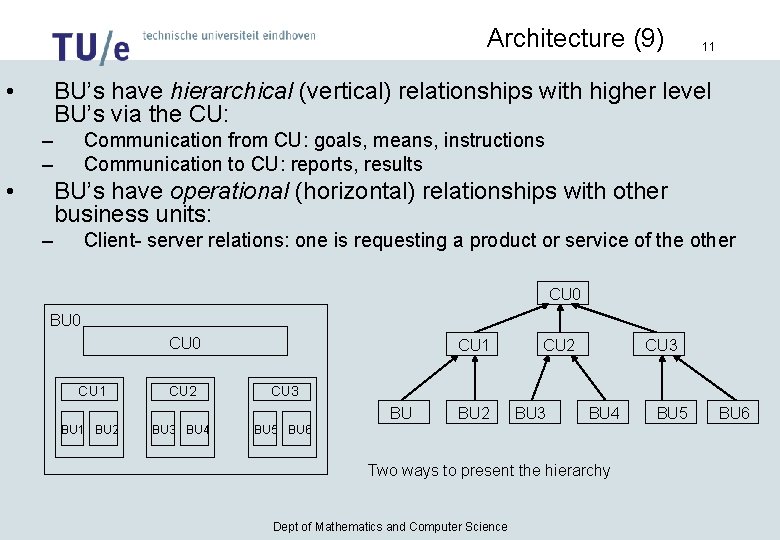
Architecture (9) • 11 BU’s have hierarchical (vertical) relationships with higher level BU’s via the CU: – – • Communication from CU: goals, means, instructions Communication to CU: reports, results BU’s have operational (horizontal) relationships with other business units: – Client- server relations: one is requesting a product or service of the other CU 0 BU 0 CU 1 CU 2 CU 1 BU 3 BU 4 CU 3 BU BU 1 BU 2 CU 2 BU 3 BU 4 BU 5 BU 6 Two ways to present the hierarchy Dept of Mathematics and Computer Science BU 5 BU 6

IT function of an enterprise (1) 12 • The IT function has three branches: – IT services (or ICT services), one business unit – Information management in each other BU – IT governance at the corporate level • The head of IT services reports to the CIO (chief information officer, member of the enterprise management team or even member of the executive board) • The information managers of the BU’s have two bosses: the hierachical boss of the BU they belong to and the CIO as functional boss • There is an IT governance board, to make the “laws”, chaired by the CIO Dept of Mathematics and Computer Science

IT function of an enterprise (2) 13 • Five main IT-resources: – Data: business data stored in files – Applications: enterprise specific programs and configuration files for software packages – Technology: computer hardware, network equipment, utility software such as operating system, database managers – Facilities: all resources to house and support EIS (e. g. building, power supply) – People: the experts and their knowledge Dept of Mathematics and Computer Science

IT function of an enterprise (3) IT-services organization A typical structure for the IT-services department with sub-departments: • Systems development – Business analysis and requirements engineering – Architecture and design – Application programming • Technical services – – Quality assurance Systems programming (infrastructure) Database administration Network control • Computer operations – – Data preparation/entry Server control and back up services Help desk PC/Lan administration Dept of Mathematics and Computer Science 14

IT function of an enterprise (4) Information management (at BU-level): • Goal: alignment of IT for the BU: the possible support of the business processes • Tasks: – – – – – Identification of required EIS-functions Reponsible in development for functionality Shared responsiblity for selection of COTS and suppliers Reponsible for acceptance testing Service level agreements (SLA’s) Functional management of the applications Deployment of systems in the BU Responsible for the correct use in the BU Definition of IT strategy of the BU Planning and bugetting of system development Dept of Mathematics and Computer Science 15

IT function of an enterprise (5) 16 IT governance (at corporate level): • Goal: – Take care that the investments in IT generate the best possible business value – Take care of the risks of IT • Tasks: – Setting the rules (e. g. for vendor selection) and standards (e. g. the use of an SDLC, hardware, interfacing) – Approval of plans from BU’s and IT services – Mediation in case of conflicts Note: governance is not about execution of BP’s, but setting the rules according to which others may or should do it! Dept of Mathematics and Computer Science

Enterprise risk management (1) • Management tasks: – Planning – Decision making – Control • Goals of control: – Assurance that the goals of the BP’s are achieved – Mitigate the risk that the enterprise will be exposed to harm, danger and loss; caused either by (physical) accidents or on purpose (fraud, sabotage)) – Assurance that the company will be in compliance with (external) legal and other regulatory obligations Dept of Mathematics and Computer Science 17

Enterprise risk management (2) 18 • Enterprise Risk Management (ERM) is the process to: – identify events that will affect the enterprise in negative sense – prevent or reduce the probability of the occurrence these events – compensate the effects of these events. • We will consider the risks of EIS and the business risks that can be controlled by EIS! • Definition of risk: the expected loss caused by a specific type of event (calamity); i. e. – Probability of number of occurrences N of an event type in a time frame t (e. g. a year): P[N (t)=n] – Expected cost to compensate the loss due to the ith event: E[Ci] – Risk= E[ i=1…N(t) Ci ]=E[N(t)]. E[Ci] (under some reasonable conditions) (mostly E[N(t)]=P[N(t)=1], since P[N(t)>1]~0) Dept of Mathematics and Computer Science

Enterprise risk management (3) 19 • Internal Control (IC) is a system of people, structure, processes (or procedures) and systems to: – Safeguard assets – Check accuracy and reliability of financial statements – Promote operational efficiency – Check the application of rules and policies • In fact ERM is an extension of IC: to incorporate all risks while IC was mainly focussed on financial (reporting) risks • Governance and IC are different: Governance is defining the rules, IC is about checking the application of them. (Distinguish corporate governance and IT governance) Dept of Mathematics and Computer Science

Enterprise risk management (4) • • 20 Two laws to be in compliance with: SOX and Basel II Sarbane-Oxley Act (SOX) is a law that requires enterprises to be transparent and responsible. This includes for a public enterprise: – That it should report quarterly in public about the state of affairs (mainly financials), approved by independent auditors – That executives are responsible for the correctness of these statements – US companies should have an internal audit function that is certified by an external auditor – Transparancy about the compensation (salary etc) of the Chief Eexecutive Officer (CEO) and Chief Financial Officer (CFO) Dept of Mathematics and Computer Science

Enterprise risk management (5) • 21 New Basel Capital Accord (Basel II) specifically important for financial service industry, it: – specifies minimal capital reserves for: • • • credit risks: client does not pay back market risks: value of shares is falling down operational risks: errors and fraud that cause losses – requires financial institutions to assess their risks periodically and to take action if reserves are too low – requires to publish their financial risks (transparency) Dept of Mathematics and Computer Science

Computer fraud techniques (1) 22 1. Adware: collect web-surfing data and sell it to an advertisement company 2. Data diddling: changing data, before, during or after storage 3. Data leakage: copying files without permission 4. Denial-of-service attack: sending thousands of emails from fake addresses to overload an e-mail server 5. Dictionary attack: guess company address and send blank emails. Unreturned messages are probably real addresses and can be used for spamming 6. Eavesdropping: listening to private voice or data transmission, often using a wire tap 7. E-mail spoofing: sending e-mails as if sent by some else Dept of Mathematics and Computer Science

Computer fraud techniques (2) 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. 23 Hacking: accessing and using computers without permission Hijacking: gaining control of someone's system to perform actions (like spamming) without the user is knowing Identity theft: using someone’s identity (e. g. soc security) Internet misinformation: using internet to spread false or misleading infomation about a person Internet terrorism: using internet to disrupt e-commerce and destroy business and personal communication Key logger: using spywar to record user’s keystrokes, e-mails and chat sessions Logic time bomb: sabbotage by a program that becomes active at certain time or event, and then it destroys programs or data Masquerading: accessing a system by pretending an authorized user. Packet snifting: find users name and password while s/he is active on the net Password cracking: penetrating a system, stealing passwords, decrypting them and (mis) use Phising: sending e-mails as if a legitimate company, requesting the user to go to a web page and verify or fill in data. Dept of Mathematics and Computer Science

Computer fraud techniques (3) 24 19. Phreaking: attacking phone system and using telephone line to distribute viruses, to access and steal or destroy data 20. Piggybacking: tapping into a telcom line and latching on to a legitimate before s/he logs in, perpetrator gets unseen access 21. Round-down: rounding all interest rates to two decimals. Remaining fraction of a cent is placed in account of perpetrator 22. Salami technique: stealing thin slices of money over a period of time. Expenses are increased by a fraction of a percent. Increments are put into an account of the perpetrator 23. Scavenging: gaining access to confidential information by searching corporate records, by searching trashcans for printouts or copies 24. Shoulder surfing: watching people entering telephone calling or credit card numbers or listening if they say these numbers 25. Social engineering: tricking an employee into providing the needed information Dept of Mathematics and Computer Science

Computer fraud techniques (4) 25 26. Software piracy: copying software without publisher’s permission 27. Spamming: mail the same message to many people at the same time, often with the intension to sell something 28. Spyware: using software to monitor computing habits and sending that data to someone else, without permission 29. Superzapping: bypass the regular system controls to perform illegal actions using special system programs 30. Trap door: entering the system through a “back door” by bypassing the regular controls. These back doors are in the system software. 31. Trojan horse: program that comes undiscovered with another program installed by the user. It gives access to others (it creates a back door). It does not damage files itself and it does not distributes to other systems 32. Virus: code attached to other programs that come with other software installations. They are activated by human action. They settle in the system, they destroy data or copy it and the may replicate themselves to e. g. computers in the address book 33. War dialing: trying thousands of telephone numbers automatically until an idle modem is found. For wire less networks it is called war driving 34. Worm: similar to a virus, but it is a stand-alone program. They can replicate themselves without human actions. Dept of Mathematics and Computer Science