Lecture 17 Internet Network Layer Contents l Internet







- Slides: 38

Lecture #17: Internet Network Layer Contents l Internet Network layer l IPv 4 datagram format l IPv 4 addressing l Subnetting l Internet control protocols, ICMP l ARP, RARP & BOOTP, DHCP l IPv 6 1

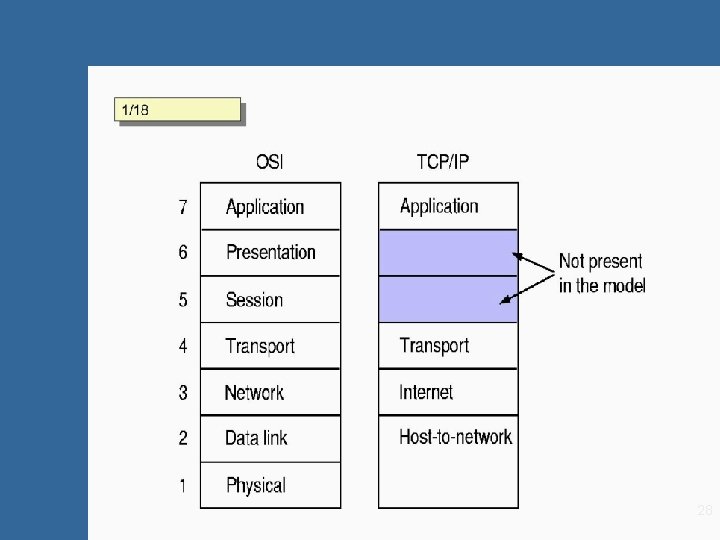
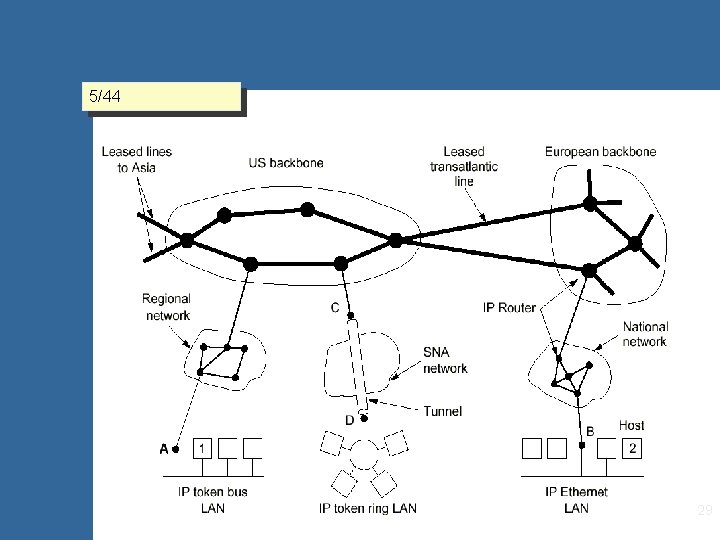
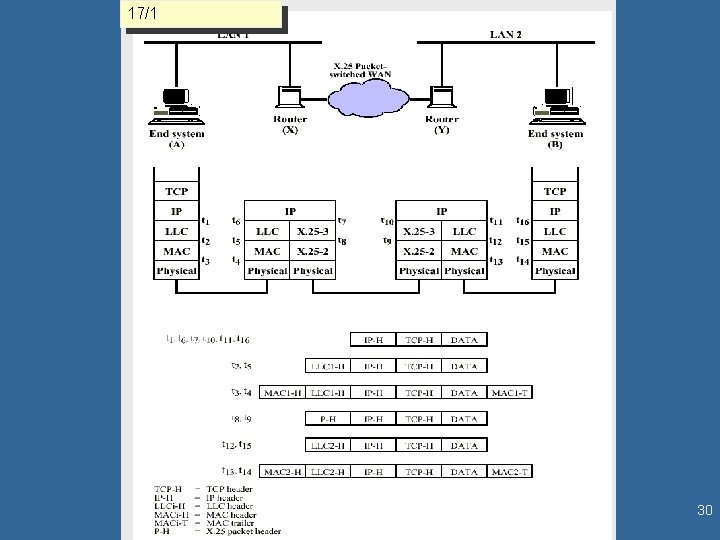
Internet Network Layer Network layer functions 1/18 • Connection control: establishment, maintaining and terminating network connections between source and destination open systems • Routing: considerations associated with hop-by-hop services transparent to the underlying resources such as data link connections. • Addressing: globally unique identification of a service access point of an end system (transparent to subnet technology (routers/LANs…) and topology (# of hops) including naming Internet architecture 5/44 17/1 • • • Ineternetwork of autonomous systems (AS) backbones: high-bandwidth connections and fast routers regional networks (midlevel) LANs and ISP systems internet protocol (IP) - transparent datagram exchange from-end 2 -to-end

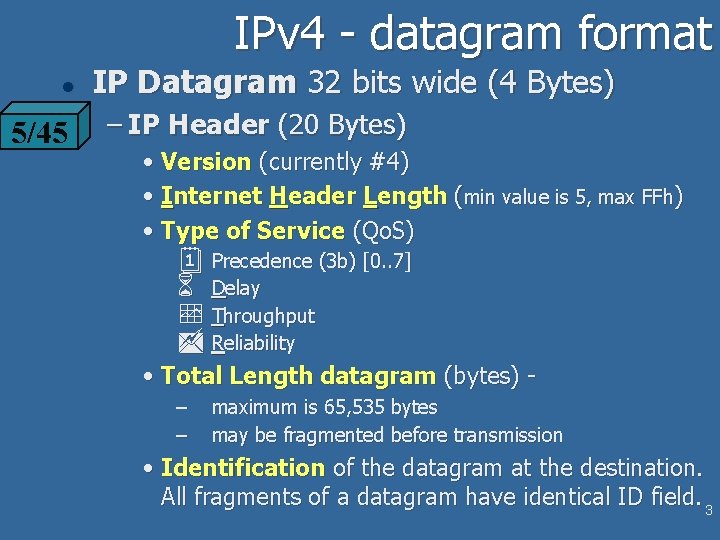
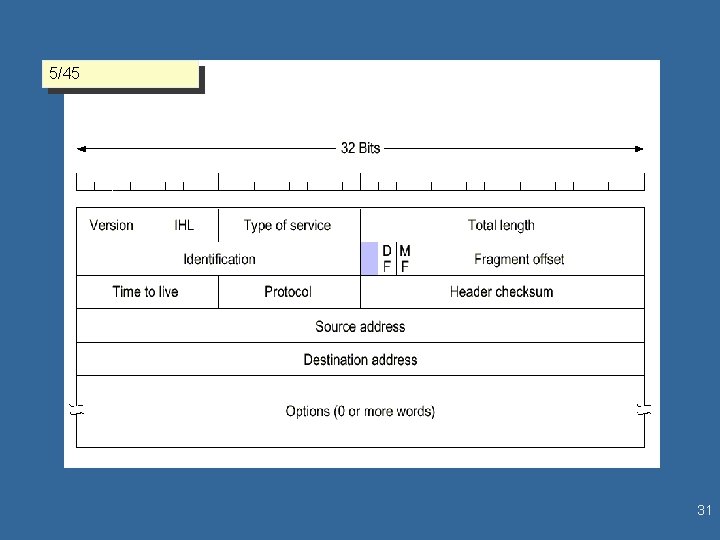
IPv 4 - datagram format l 5/45 IP Datagram 32 bits wide (4 Bytes) – IP Header (20 Bytes) • Version (currently #4) • Internet Header Length (min value is 5, max FFh) • Type of Service (Qo. S) ¦ Precedence (3 b) [0. . 7] 6 Delay Throughput Reliability • Total Length datagram (bytes) – – maximum is 65, 535 bytes may be fragmented before transmission • Identification of the datagram at the destination. All fragments of a datagram have identical ID field. 3

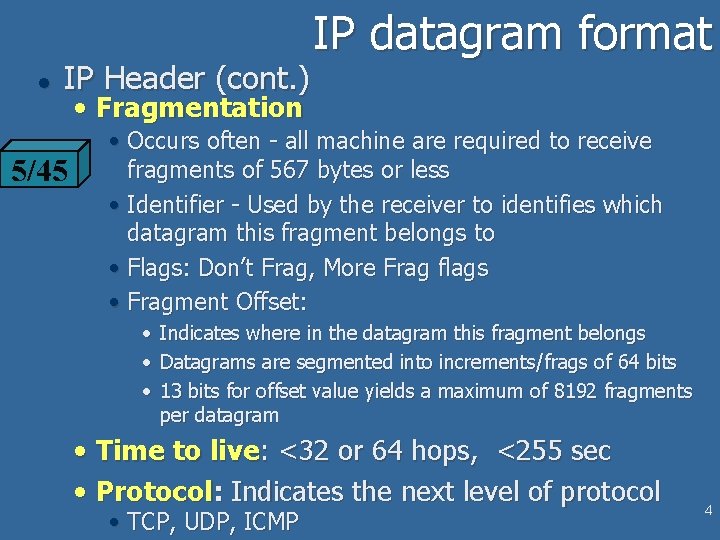
l IP Header (cont. ) 5/45 IP datagram format • Fragmentation • Occurs often - all machine are required to receive fragments of 567 bytes or less • Identifier - Used by the receiver to identifies which datagram this fragment belongs to • Flags: Don’t Frag, More Frag flags • Fragment Offset: • Indicates where in the datagram this fragment belongs • Datagrams are segmented into increments/frags of 64 bits • 13 bits for offset value yields a maximum of 8192 fragments per datagram • Time to live: <32 or 64 hops, <255 sec • Protocol: Indicates the next level of protocol • TCP, UDP, ICMP 4

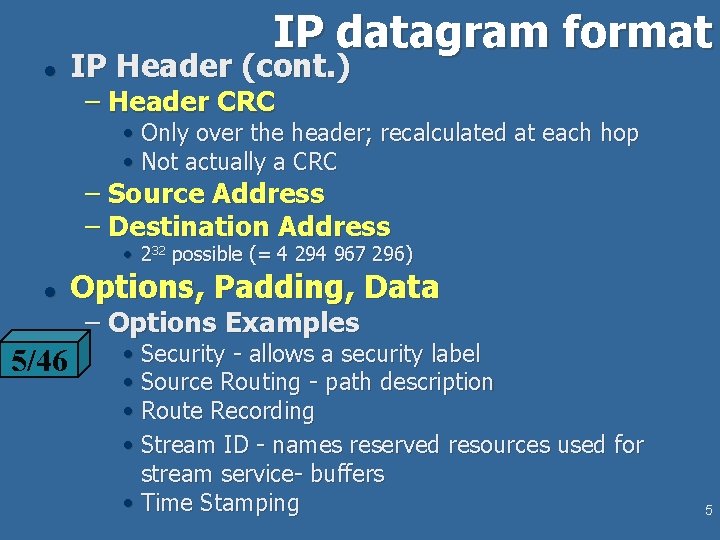
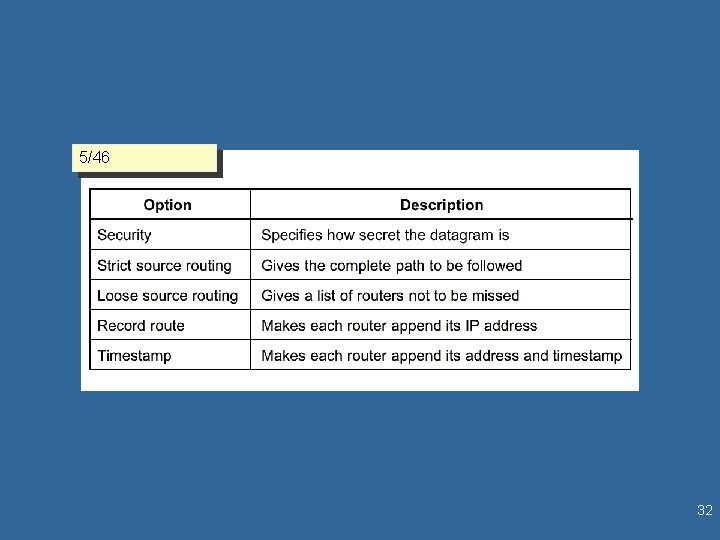
IP datagram format l IP Header (cont. ) – Header CRC • Only over the header; recalculated at each hop • Not actually a CRC – Source Address – Destination Address • 232 possible (= 4 294 967 296) l Options, Padding, Data – Options Examples 5/46 • Security - allows a security label • Source Routing - path description • Route Recording • Stream ID - names reserved resources used for stream service- buffers • Time Stamping 5

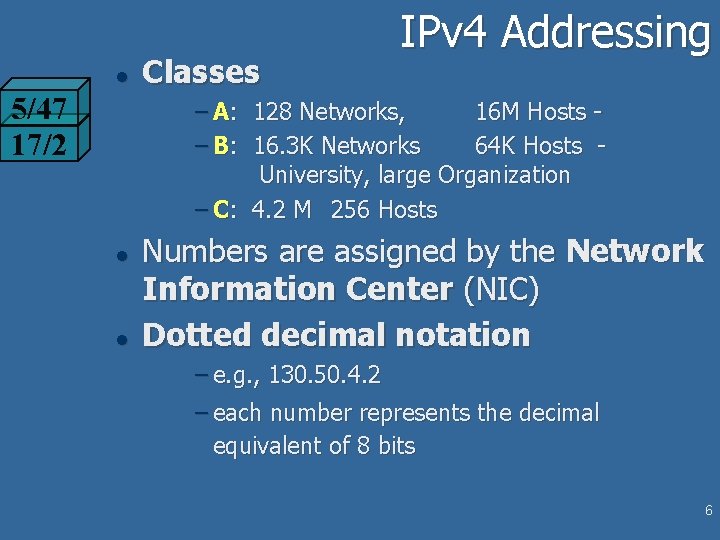
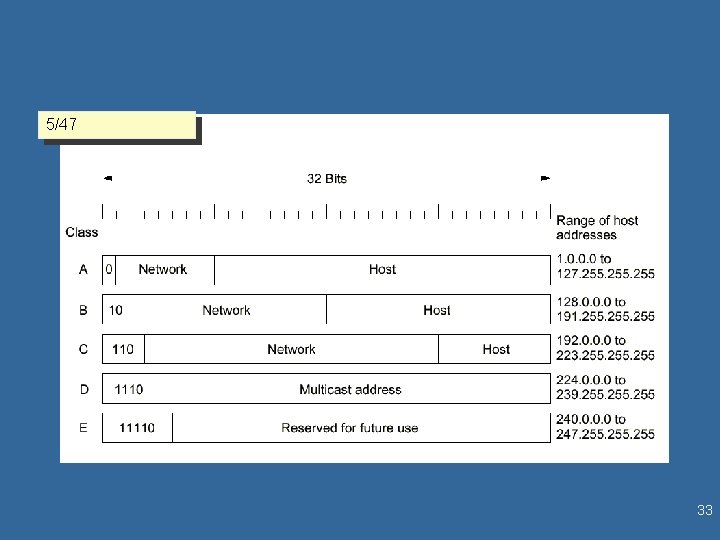
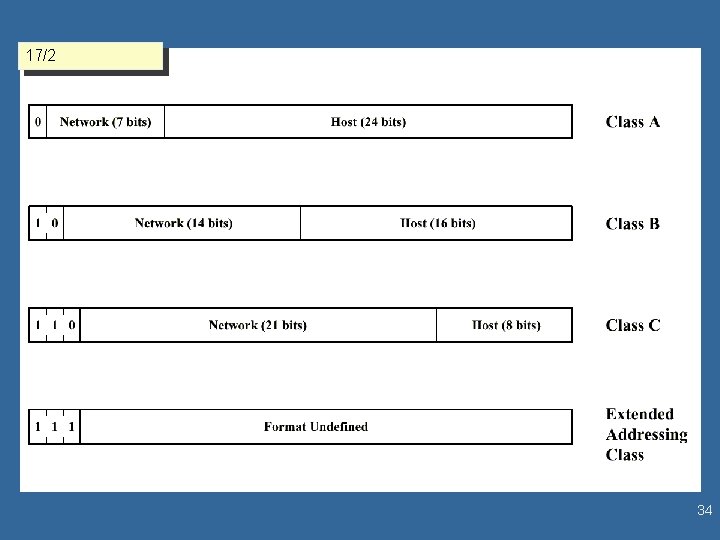
l 5/47 17/2 Classes IPv 4 Addressing – A: 128 Networks, 16 M Hosts – B: 16. 3 K Networks 64 K Hosts University, large Organization – C: 4. 2 M 256 Hosts l l Numbers are assigned by the Network Information Center (NIC) Dotted decimal notation – e. g. , 130. 50. 4. 2 – each number represents the decimal equivalent of 8 bits 6

IP Addressing l Special IP Addresses – All zeros: this host – All zeros network address: this (local) network – All ones: broadcast on this network l 5/49 Subnet Addressing (Subnet Masks) – In the above example, subnet address (6 bits) can formed from a (16 bit) host address, leaving 10 bits for host addresses – Results: 62 Subnets with 1022 hosts each 7

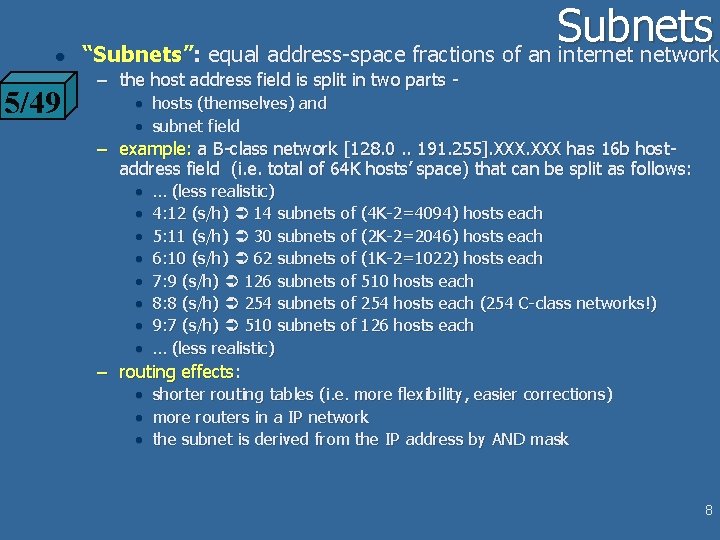
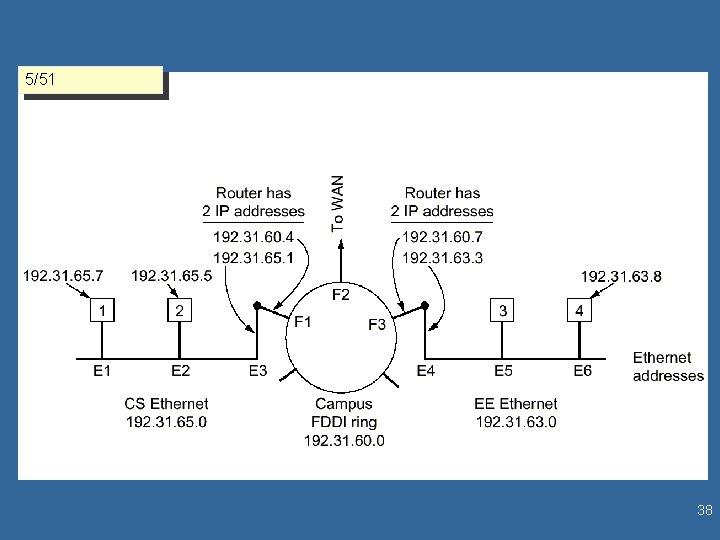
l 5/49 Subnets “Subnets”: equal address-space fractions of an internet network – the host address field is split in two parts • hosts (themselves) and • subnet field – example: a B-class network [128. 0. . 191. 255]. XXX has 16 b hostaddress field (i. e. total of 64 K hosts’ space) that can be split as follows: • … (less realistic) • 4: 12 (s/h) 14 subnets of (4 K-2=4094) hosts each • 5: 11 (s/h) 30 subnets of (2 K-2=2046) hosts each • 6: 10 (s/h) 62 subnets of (1 K-2=1022) hosts each • 7: 9 (s/h) 126 subnets of 510 hosts each • 8: 8 (s/h) 254 subnets of 254 hosts each (254 C-class networks!) • 9: 7 (s/h) 510 subnets of 126 hosts each • … (less realistic) – routing effects: • shorter routing tables (i. e. more flexibility, easier corrections) • more routers in a IP network • the subnet is derived from the IP address by AND mask 8

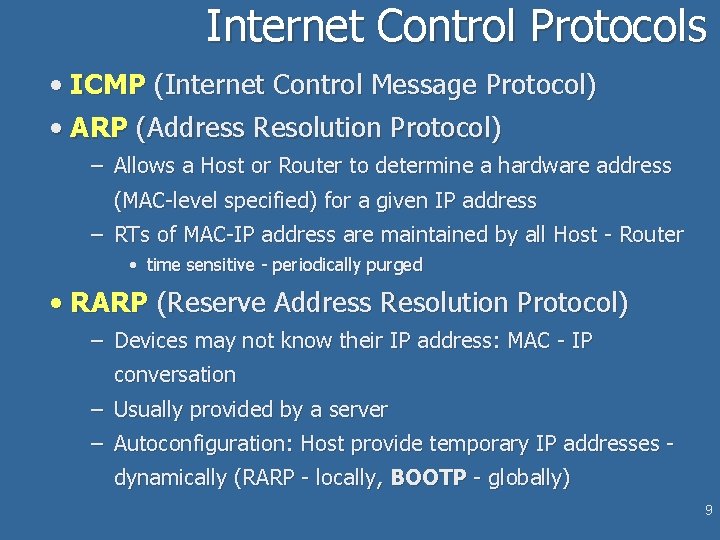
Internet Control Protocols • ICMP (Internet Control Message Protocol) • ARP (Address Resolution Protocol) – Allows a Host or Router to determine a hardware address (MAC-level specified) for a given IP address – RTs of MAC-IP address are maintained by all Host - Router • time sensitive - periodically purged • RARP (Reserve Address Resolution Protocol) – Devices may not know their IP address: MAC - IP conversation – Usually provided by a server – Autoconfiguration: Host provide temporary IP addresses dynamically (RARP - locally, BOOTP - globally) 9

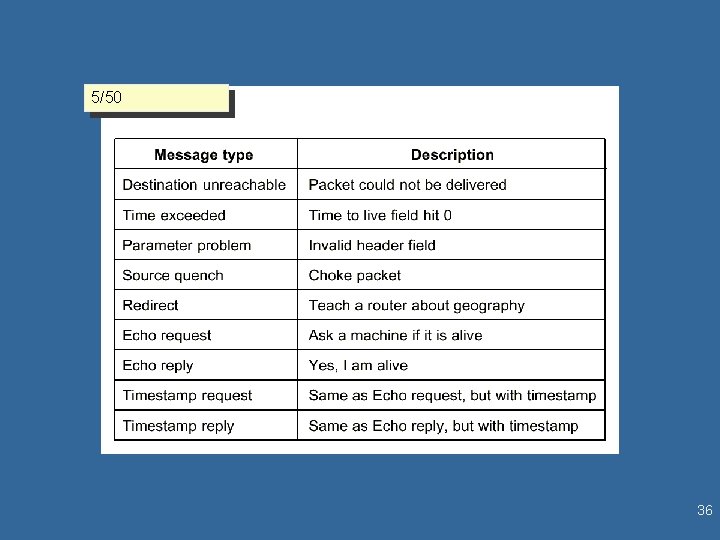
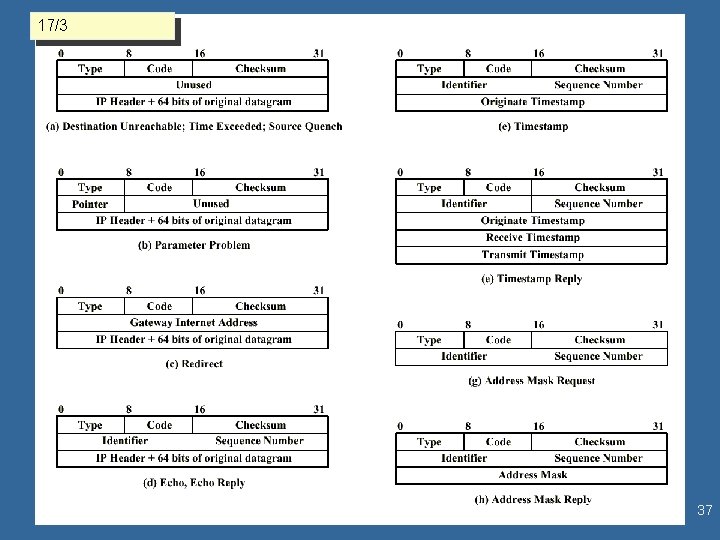
ICMP is the primary supervisory protocol in TCP/IP ICMP • Lets the Host and Routers know of the status of the network around them - problems with routers, congestion • Network Status information provided to Hosts/Routers via – – Error messages Queries from hosts (e. g. , ping) Flow Control information (source squelch is implemented this way) Routing (redirecting paths) • Message Types 5/50 17/3 ° Destination Unreachable - informs host that destination is either physically or logically unreachable. ° Time Exceeded, Parameter - datagram lifetime expires (reassemble deadlock) ° Parameter Problem (rcvd an incorrect argument for a parameter), syntax or semantics ° Redirect, Echo/reply - Test for different route ° Source Squelch - sent by either destination Host (flow control) or Router (Congestion Control) ° Timestamp request/reply - Test for delay characteristics ° Information request/reply ° Address Mask - To address subnet more directly • ICMP uses IP datagrams modified with a 64 -bit header 10

ARP • ARP = Address Resolution Protocol • Maps IP addresses to MAC-specified addresses (e. g. Ethernet 6 byte address) 5/51 • RTs of MAC-IP address are maintained by all Host Router – better and more flexible than static configuration map – time sensitive - periodically purged – cashing the map information avoids frequent repetition of the broadcasting – host initiated broadcasting on boot up (- avoiding duplication of IP addresses) • ARP/RARP has its own protocol frame structure 11

RARP & BOOTP • RARP = Reverse Address Resolution Protocol • Maps MAC-specified addresses to IP addresses e. g. by booting diskless station • RARP server keeps configuration table of mapping • RARP server is needed for each network because it is reachable only by broadcast IP address (of all ones) • BOOTP (bootstrap protocol) provides same functionality by UDP (datagram) messages that travel over routers. Beside the local IP address it provides • IP address of the booting station • IP address of the default router • the subnet mask 12

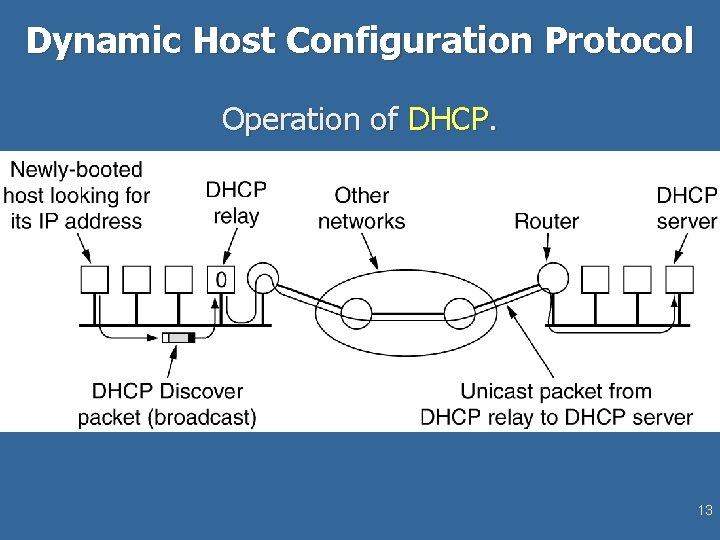
Dynamic Host Configuration Protocol Operation of DHCP. 13

The new IP version 6 (IPv 6) l Motivation: Ø The threat of exhausting of the 32 -bit IPv 4 addess space. (Original estimates for when the world would run out of IPv 4 numbers varied from 2000 to 2008. ) Ø Fixing issues and problems in the existing IPv 4 implementation Ø Optimizing the network layer operation Ø Introducing new network services 14

IPv 6 history l l 1995 - Experimental deployment December, 1995 - specifications of the basic protocols, RFC 1883 l 1996 - more specifications l 1998 - RFC 2460 obsoletes RFC 1883. l l 2000 - Production quality support in all major OS and routers. 26. 10. 2007 - The RIPE community issued a ‘Resolution on IPv 4 Depletion and Deployment of IPv 6’ 15

IPv 6 Support Requirements l l l Routers must support IPv 6 Switches do not require upgrades to support IPv 6 Unicast but will require upgrades to support IPv 6 Multicast (MLDv 2 snooping). DNS management software must support IPv 6. 16

IPv 6 details l l l IPv 6 was designed to work together with IPv 4 (“Dual Stack”, “Dual Stack Strategy”) During the transition period most hosts will have both an IPv 4 and an IPv 6 number. The transition period is expected to last many years (The wide use of NAT will slow down this proccess). 17

IPv 6 technical l l A 128 bit address space (about 3. 4× 1038 unique addresses comparing to 4. 3× 109 in IPv 4 !!!) The addresses are divided into 4 categories: – – l Unicast (corresponds to exactly one interface) Multicast (group address) Anycast (corresponds to more than one interface) Special addresses Examples (IPv 6 uses CIDR notation): 2001: 4 b 58: acad: : 107/64 (a global unicast addr. ) fe 80: : 208: a 1 ff: fe 7 d: 57 df/64 (a link-local or autoconfiguration addr. ) : : 1/128 (the loopback address) 18

IPv 6 technical (2) Ø Ø Stateless autoconfiguration of hosts Multicast - part of the base specifications in IPv 6, unlike IPv 4, where it was introduced later. Ø Link-local addresses Ø Jumbograms – datagrams over the 64 KB IPv 4 limit. Ø Ø Ø Network-layer security - IPsec is an integral part of the base protocol suite in IPv 6. Mobility support Lack of a checksum - It is believed that errors are very rare in today's network. For this reason, IPv 6 has no error checking in its protocol but instead relies on link layer protocols to perform error checking. 19

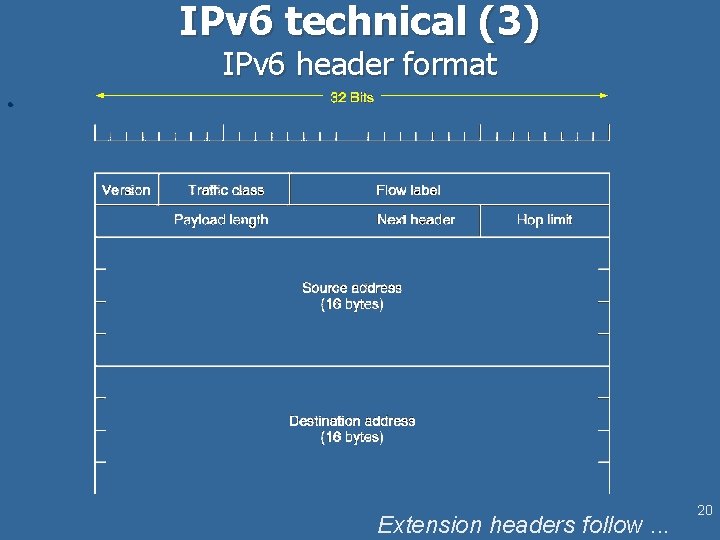
IPv 6 technical (3) IPv 6 header format l Extension headers follow. . . 20

IPv 6 - Transition mechanisms l Dual stack l Tunneling - Automatic or Configured l Proxying and translation 21

Barriers to implementing IPv 6 l The support in the wide used PC Operating systems – All three major OS (Linux, Mac OS X, MS Windows) have full support for IPv 6 now. l The support in the wide used routers –The major router vendors support IPv 6 l IPv 6 has been implemented more widely in Europe and Asia than in the USA. Some statistics next. . . 22

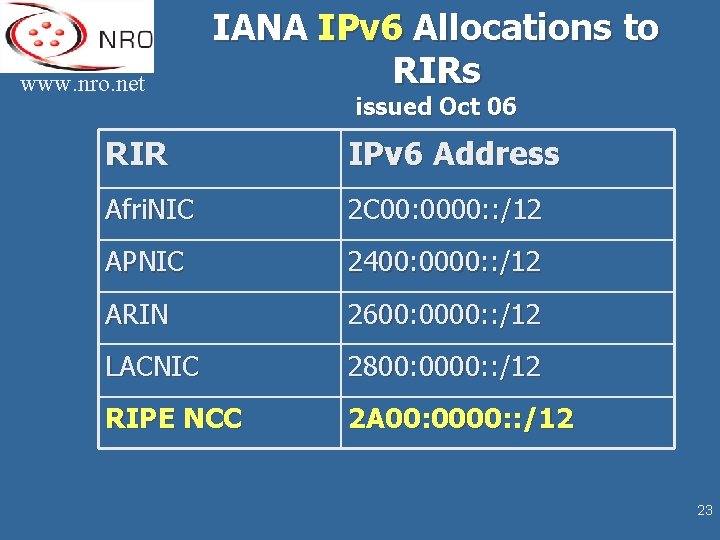
www. nro. net IANA IPv 6 Allocations to RIRs issued Oct 06 RIR IPv 6 Address Afri. NIC 2 C 00: 0000: : /12 APNIC 2400: 0000: : /12 ARIN 2600: 0000: : /12 LACNIC 2800: 0000: : /12 RIPE NCC 2 A 00: 0000: : /12 23

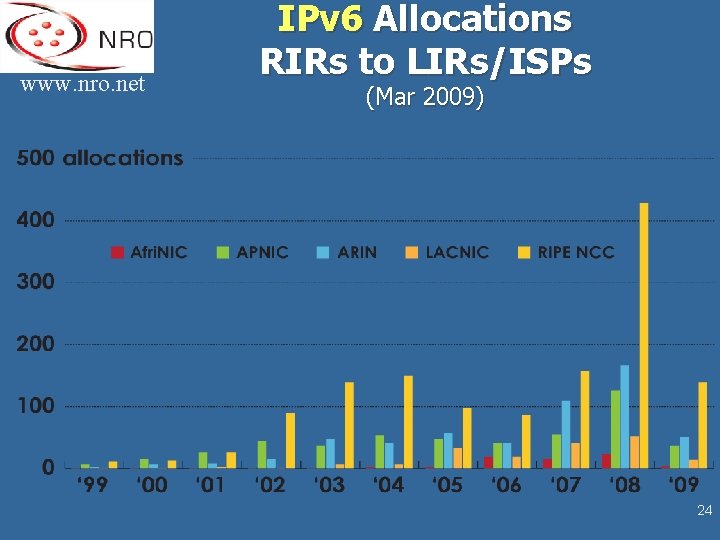
www. nro. net IPv 6 Allocations RIRs to LIRs/ISPs (Mar 2009) 24

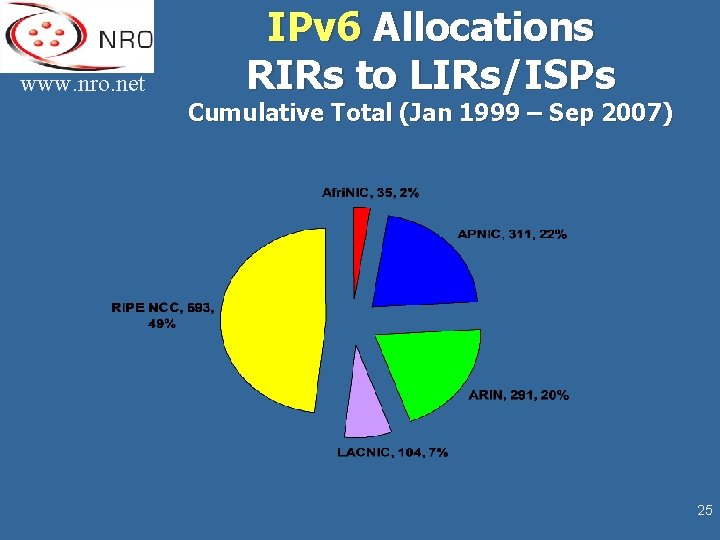
www. nro. net IPv 6 Allocations RIRs to LIRs/ISPs Cumulative Total (Jan 1999 – Sep 2007) 25

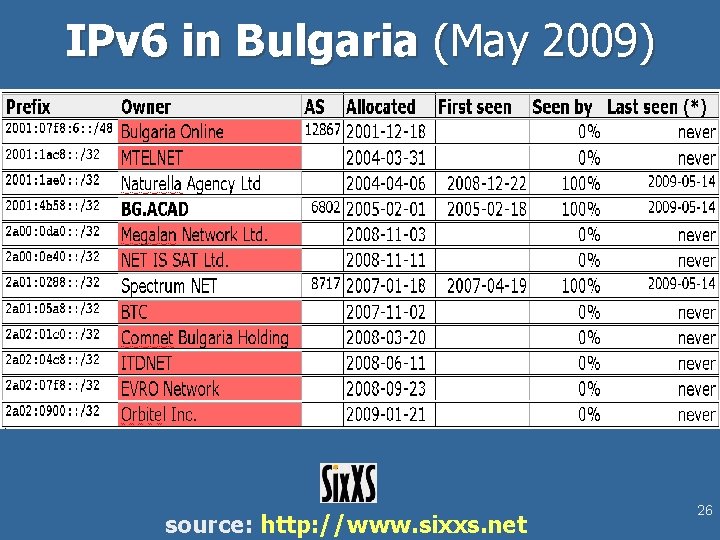
IPv 6 in Bulgaria (May 2009) source: http: //www. sixxs. net 26

IPv 6 deployment in BREN’s network (some pride ; -) l l The central node at IPP-BAS is fully IPv 6 enabled, including the NOC and part of the LAN of IPP-BAS (the most of the internal traffic is actually IPv 6) IPv 6 traffic is also carried over four major links in the BREN internal backbone: • • Sofia – Veliko Tarnovo Sofia – Plovdiv Sofia – Pleven Sofia – Varna 27

28

5/44 29

17/1 30

5/45 31

5/46 32

5/47 33

17/2 34

5/48 5/49 35

5/50 36

17/3 37

5/51 38