Lecture 14 Crime Criminal Law Even though there





















- Slides: 23

Lecture 14: Crime

Criminal Law • Even though there is a victim, the injury is to “society, ” so the government prosecutes: • Unauthorized access • Theft of services • Denial of service • Alteration/destruction of data • Trafficking in passwords • Computer fraud • Password trafficking • Email bombing, spamming • Video piracy, software piracy • Gambling

Criminal Jurisdiction • When can a state exercise criminal jurisdiction? – Conduct in the state that is an element of the offense – Conduct outside that is an attempt to commit inside – Conduct outside that is conspiracy to commit inside the state + an overt act in the state – Omission to perform a legal duty imposed by the state – Offense is based on a state statute that prohibits conduct outside the state that bears a reasonable relation to a legitimate interest of the state and the actor knows or should know that his conduct is likely to affect that interest. 18 Pa. C. S. § 102

Strict Construction • Problem: criminal statutes are “strictly construed. ” • If the act is not expressly made criminal by statute, it is not criminal (exception: “common law crimes, ” like murder) • The words of a criminal statute are not expanded to cover related or analogous behavior.

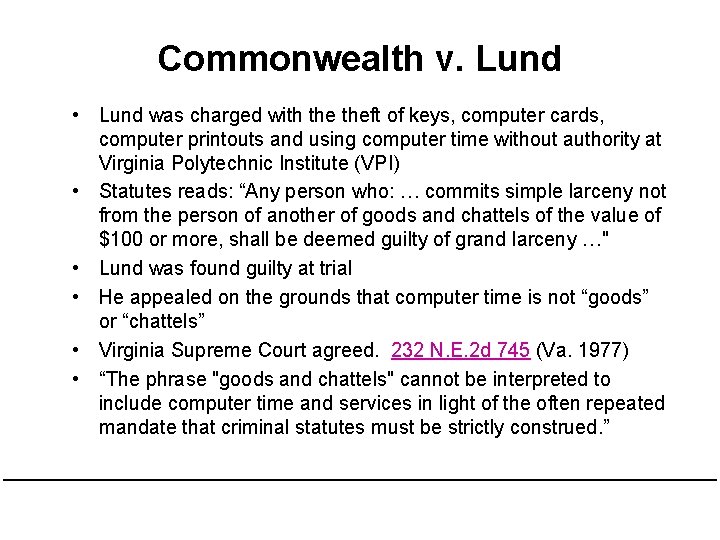
Commonwealth v. Lund • Lund was charged with theft of keys, computer cards, computer printouts and using computer time without authority at Virginia Polytechnic Institute (VPI) • Statutes reads: “Any person who: … commits simple larceny not from the person of another of goods and chattels of the value of $100 or more, shall be deemed guilty of grand larceny …" • Lund was found guilty at trial • He appealed on the grounds that computer time is not “goods” or “chattels” • Virginia Supreme Court agreed. 232 N. E. 2 d 745 (Va. 1977) • “The phrase "goods and chattels" cannot be interpreted to include computer time and services in light of the often repeated mandate that criminal statutes must be strictly construed. ”

What’s a Commonwealth? • Commonwealth means “free state, ” not controlled by a king (Oliver Cromwell, 1649); in the U. S. , synonymous with “state. ” • Among the U. S. states, 4 are called Commonwealths: – Pennsylvania – Massachusetts – Virginia – Kentucky • The first three were among the original 13 colonies when the U. S. was formed • Kentucky was part of Virginia but split in 1792 as the 15 th state • Also, “a political unit having local autonomy but voluntarily united with the U. S. ” Puerto Rico, Northern Marianas Islands.

Computer Fraud and Abuse Act • Prohibits certain acts against “protected computers” that affect interstate commerce. 18 U. S. C. § 1030. • ''protected computer'' means a computer – exclusively for the use of a financial institution or the United States Government … ; or – which is used in interstate or foreign commerce or communication • including a computer located outside the United States that is used in a manner that affects interstate or foreign commerce or communication of the United States • Provides for a civil action (private lawsuit) by anyone injured by a violation

Computer Fraud and Abuse Act • intentionally accessing a computer without authorization or exceeding authorized access, to obtain – information in a financial record of a financial institution, or of a card issuer or consumer reporting agency on a consumer – information from any department or agency of the United States; or – information from any protected computer if the conduct involved an interstate or foreign communication • knowingly and with intent to defraud, accesses a protected computer without authorization, or exceeds authorized access, and … obtains anything of value

Computer Fraud and Abuse Act Fraud in connection with access devices. 18 U. S. C. § 1029. • “access device” means any card, plate, code, account number, electronic serial number, mobile identification number, PIN, or other … identifier or other means of account access that can be used … to obtain money, goods, services, or any other thing of value, or that can be used to initiate a transfer of funds · • Prohibits use or trafficking in counterfeit access devices • trafficking in passwords

Computer Fraud and Abuse Act • knowingly transmitting a program, information, code, or command, and … intentionally causing damage without authorization, to a protected computer • intentionally accessing a protected computer without authorization, and … causing damage • 'damage' means any impairment to the integrity or availability of data, a program, a system, or information (covers denial of service) • extortion by threat to a computer • crimes investigated by FBI and Secret Service • PA: “Unlawful use of computer” 18 Pa. C. S. § 3933

AOL, Inc. v. LCGM, Inc. • LCGM is a porno site • LCGM became an AOL customer and harvested email addresses from AOL chat rooms • LCGM spammed users through AOL (300, 000 emails per day) • Bulk emails violate AOL’s Terms of Service • LCGM was sued for violating the Computer Fraud and Abuse Act • Held, LCGM’s use of AOL was unauthorized; LCGM obtained value (use of AOL mailing services) and information (email addresses)

No Electronic Theft Act • Any person who infringes a copyright willfully either – for purposes of commercial advantage or private financial gain, or – by the reproduction or distribution, including by electronic means, during any 180 -day period, of 1 or more copies or phonorecords of 1 or more copyrighted works, which have a total retail value of more than $1, 000. 17 U. S. C. 506 • First offense, less than 10 copies: 1 year + $100, 000 • First offense, 10 or more copies: 5 years + $250, 000 • Second offense, 10 or more: 10 years + $250, 000 • “financial gain” includes receipt, or expectation of receipt, of anything of value, including the receipt of other copyrighted works.

People ex rel. Vacco v. World Interactive Gaming Corp. et al. • “ex rel. ” (ex relatione, upon relation) means “acting through. ” Vacco was the NY Attorney General • no lottery or … book-making, or any other kind of gambling, … except pari-mutuel betting on horse races as may be prescribed by the legislature … shall hereafter be authorized or allowed within this state. NY Const. Art. 1, Sec. 9 • World Interactive Gaming Corp. (WIGC) is a Delaware corp. with offices in NY. • Golden Chips Casino, Inc. (GCC) is an Antigua corp. wholly owned by WIGC. • GCC operated an Internet casino using servers in Antigua. • GCC advertised in the US; ads were seen in NY

Antigua

People ex rel. Vacco v. World Interactive Gaming Corp. et al. • Users had to enter a home address; GCC checked for Nevada • Users transferred money to a bank in Antigua. They could gamble. Gambling is legal in Antigua. • New Yorkers could gamble by lying about their address • NY Attorney General sought an injunction against WIGC, GCC to stop their activities • GCC argued • Held, NY has jurisdiction. When New Yorkers transfer money to GCC, they are gambling in NY. Doesn’t matter where GCC is • Injunction issued

Cyberstalking • “It is the intent of this act to clarify that electronic communications are included in the actions that can constitute the crimes of harassment and stalking. ” • Cal. Penal Code 646. 9. (a) Any person who willfully, maliciously, and repeatedly follows or harasses another person and who makes a credible threat with the intent to place that person in reasonable fear for his or her safety, or the safety of his or her immediate family, is guilty of the crime of stalking, punishable by imprisonment in a county jail for not more than one year or by a fine of not more than one thousand dollars ($1, 000), or by both that fine and imprisonment.

Cyberstalking • Cal. Penal Code § 653 m. (a) Every person who, with intent to annoy, telephones or makes contact by means of an electronic communication device with another and addresses to or about the other person any obscene language or addresses to the other person any threat to inflict injury to the person or property of the person addressed or any member of his or her family, is guilty of a misdemeanor. Nothing in this subdivision shall apply to telephone calls or electronic contacts made in good faith.

Pornography • Federal statute, 18 U. S. C. § 2252: Applies to any person who - (1) knowingly transports, ships, receives or distributes in interstate or foreign commerce by any means including by computer or mails, any visual depiction of a minor engaging in sexually explicit conduct. • U. S. v. Hockings, No. 97 -50018 (9 th Cir. 11/21/97): Computer graphic interchange files (GIFs) in binary format fall within the definition of “visual depictions” in 18 U. S. C. §§ 2252(a)(1) and (4)(B). The fact that such files require the use of personal computer hardware and software to depict images of child pornography does not put them outside the statute, the court held, analogizing to an earlier case in which undeveloped film was also held to constitute a "visual depiction" under the statute.

Other e. Commerce Crimes • • • Securities fraud Money laundering, FINCEN, USA Patriot Act Auctions Pyramid schemes Justice Dept Computer Crime and Intellectual Property Section • How to report cybercrime

Council of Europe Convention on Cybercrime • Signed by the US on Nov. 23, 2001; not yet ratified by the US Senate • Requires signatories to make certain acts illegal • Provides for – – – jurisdiction cooperation extradition 24/7 information network compel ISPs to record traffic data

Crimes Under the Convention • • • Unauthorized access Interception of data, including “electronic emissions” Data interference System interference Misuse or possession of devices, including programs, for committing offenses Computer forgery Computer fraud Child pornography Copyright infringement

Current International Cases • France v. Yahoo, Inc. ; Timothy Koogle, filed 2002). A French criminal court plans to try Yahoo and Timothy Koogle, its former CEO, for allowing Nazi memorabilia to be sold on the Yahoo auction site. It is illegal under French law to exhibit or sell objects with racist overtones. The court stated it would hear allegations that Yahoo incited racial hatred by allowing French Internet users to buy Nazi memorabilia on its site. • Norway v. Tvedt, Asker and Baerum District Court (Norway, 2002). A Norwegian court sentenced Tvedt to jail for posting racist material on a web site. Tvedt posted material that mixed neo-Nazism, racial hatred, and religion on a served based in the United States.

Q&A 46 -840 ECOMMERCE LAW AND REGULATION SPRING 2003 COPYRIGHT © 2003 MICHAEL I. SHAMOS
 However but although
However but although Even though contrast
Even though contrast Even though beowulf was originally dgp
Even though beowulf was originally dgp Bryanna and charles are in a dancing competition
Bryanna and charles are in a dancing competition Though i walk
Though i walk Even though we walk in the flesh
Even though we walk in the flesh Oh no you never let go
Oh no you never let go Difference between civil law and criminal law
Difference between civil law and criminal law Criminal law plaintiff
Criminal law plaintiff Task 1 match the words
Task 1 match the words Regular expression recursive definition
Regular expression recursive definition Regular expression of even even language
Regular expression of even even language 01:640:244 lecture notes - lecture 15: plat, idah, farad
01:640:244 lecture notes - lecture 15: plat, idah, farad Types of computer misuse
Types of computer misuse Mala prohibita
Mala prohibita Taser 7 nomenclature
Taser 7 nomenclature Chapter 11 basic concepts street law
Chapter 11 basic concepts street law Types of criminal law
Types of criminal law Criminal law samaha 9th
Criminal law samaha 9th Difference between civil and criminal law table
Difference between civil and criminal law table Difference between civil and criminal law table
Difference between civil and criminal law table Define substantive criminal law
Define substantive criminal law Involuntary manslaughter examples
Involuntary manslaughter examples Causation in criminal law
Causation in criminal law