Lecture 10 Buffer Overflows contd CS 105 Fall
Lecture 10: Buffer Overflows (cont'd) CS 105 Fall 2020
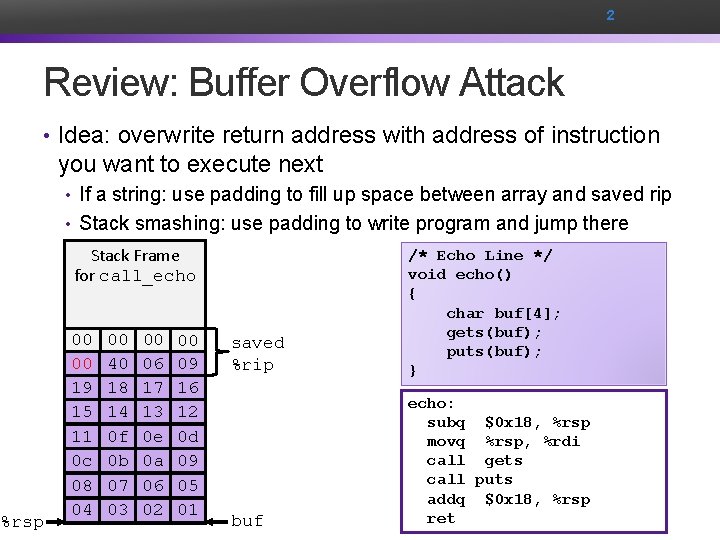
2 Review: Buffer Overflow Attack • Idea: overwrite return address with address of instruction you want to execute next • If a string: use padding to fill up space between array and saved rip • Stack smashing: use padding to write program and jump there Stack Frame for call_echo %rsp 00 Address 00 00 00 Return 40 bytes) 06 f 6 09 00 (8 19 18 17 16 15 14 13 12 Stack 11 0 f Frame 0 e 0 d 20 bytes unused for echo 0 c 0 b 0 a 09 08 07 06 05 04 [2] 03 [1] 02 [0] 01 [3] saved %rip /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); } buf echo: subq $0 x 18, %rsp movq %rsp, %rdi call gets call puts addq $0 x 18, %rsp ret

Review: Buffer Overflow Examples
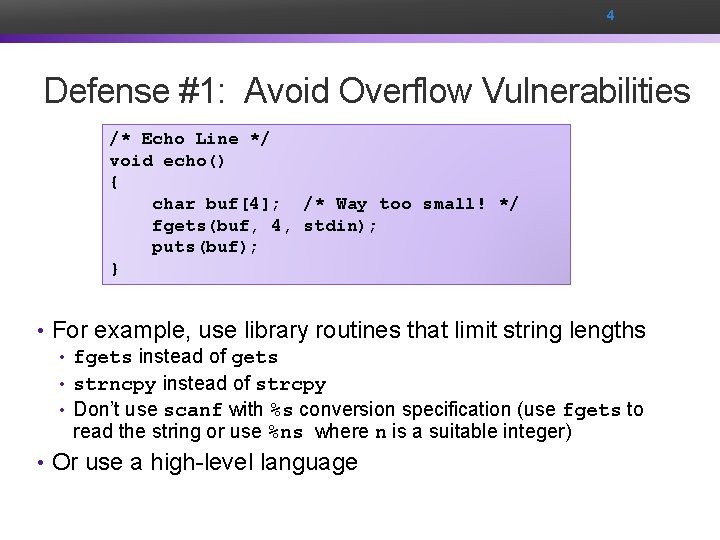
4 Defense #1: Avoid Overflow Vulnerabilities /* Echo Line */ void echo() { char buf[4]; /* Way too small! */ fgets(buf, 4, stdin); puts(buf); } • For example, use library routines that limit string lengths • fgets instead of gets • strncpy instead of strcpy • Don’t use scanf with %s conversion specification (use fgets to read the string or use %ns where n is a suitable integer) • Or use a high-level language
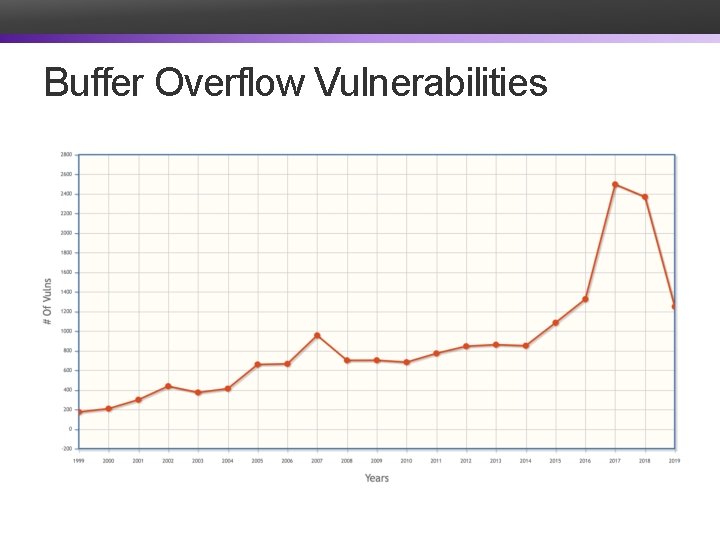
Buffer Overflow Vulnerabilities
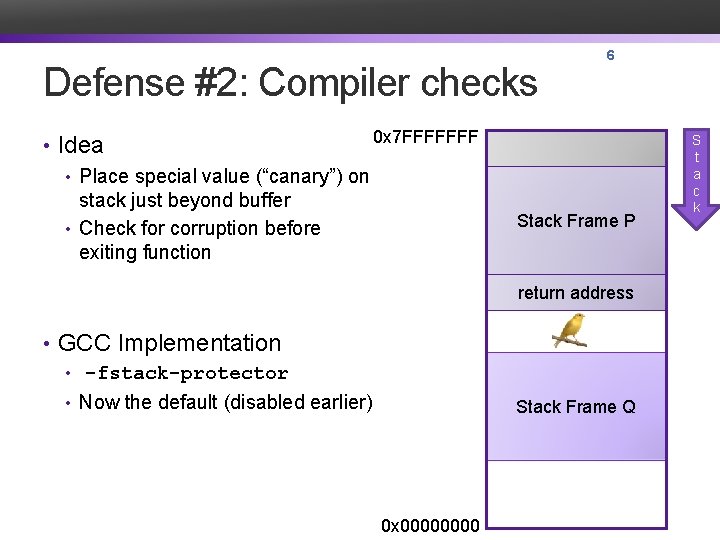
Defense #2: Compiler checks 0 x 7 FFFFFFF • Idea • Place special value (“canary”) on stack just beyond buffer • Check for corruption before exiting function 6 Stack Frame P return address • GCC Implementation • -fstack-protector • Now the default (disabled earlier) Stack Frame Q 0 x 0000 S t a c k
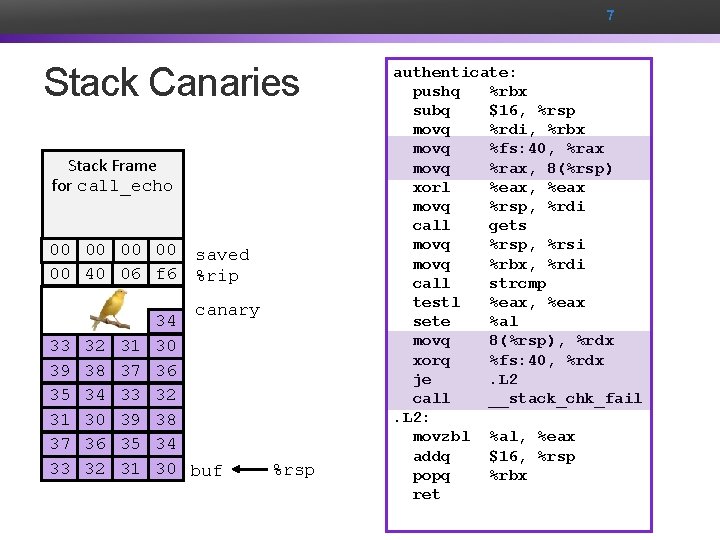
7 Stack Canaries Stack Frame for call_echo 00 Address 00 00 00 Return 00 (8 40 bytes) 06 f 6 Stack Frame for echo 34 33 32 31 30 39 38 37 36 Stack 35 34 Frame 33 32 20 bytes unused for echo 31 30 39 38 37 36 35 34 33 [2] 32 [1] 31 [0] 30 [3] saved %rip canary buf %rsp authenticate: pushq %rbx subq $16, %rsp movq %rdi, %rbx movq %fs: 40, %rax movq %rax, 8(%rsp) xorl %eax, %eax movq %rsp, %rdi call gets movq %rsp, %rsi movq %rbx, %rdi call strcmp testl %eax, %eax sete %al movq 8(%rsp), %rdx xorq %fs: 40, %rdx je. L 2 call __stack_chk_fail. L 2: movzbl %al, %eax addq $16, %rsp popq %rbx ret

Exercise 1: Stack Canaries • Which of the following would make a good stack canary? 1. A secret, constant value 2. A fixed sequence of common terminators (�, EOF, etc. ) 3. A random number chosen each time the program is run
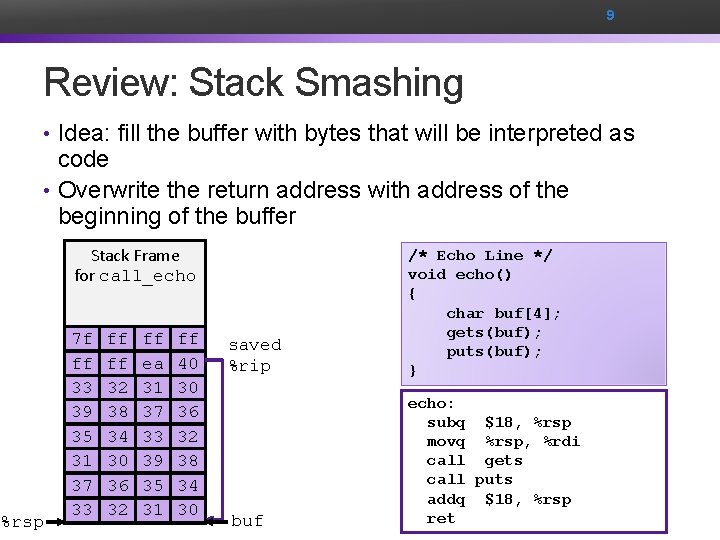
9 Review: Stack Smashing • Idea: fill the buffer with bytes that will be interpreted as code • Overwrite the return address with address of the beginning of the buffer Stack Frame for call_echo %rsp 7 f ff ff ff 00 Address 00 00 00 Return ff ff ea 00 (8 40 bytes) 06 40 f 6 33 32 31 30 39 38 37 36 Stack 35 34 Frame 33 32 20 bytes unused for echo 31 30 39 38 37 36 35 34 33 [2] 32 [1] 31 [0] 30 [3] saved %rip /* Echo Line */ void echo() { char buf[4]; gets(buf); puts(buf); } buf echo: subq $18, %rsp movq %rsp, %rdi call gets call puts addq $18, %rsp ret
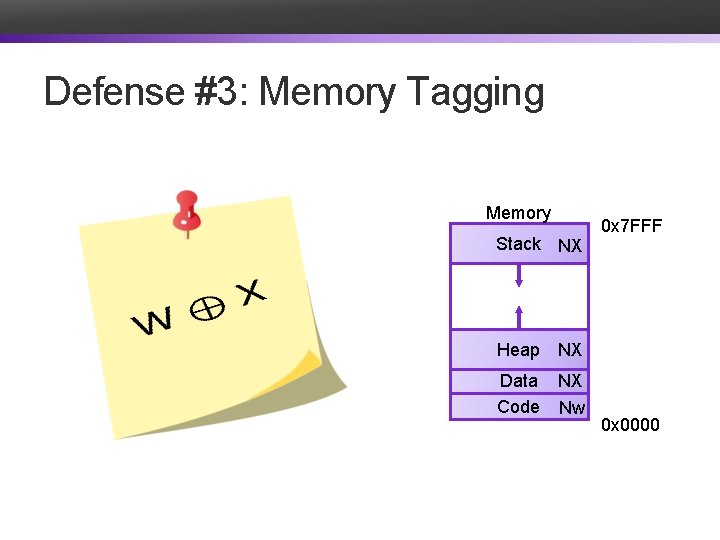
Defense #3: Memory Tagging Memory Stack NX 0 x 7 FFF Heap NX Data NX Code Nw 0 x 0000

Code Reuse Attacks • Key idea: execute instructions that already exist • Defeats memory tagging defenses • Examples: 1. return to a function or line in the current program 2. return to a library function (e. g. , return-into-libc) 3. return to some other instruction (return-oriented programming)
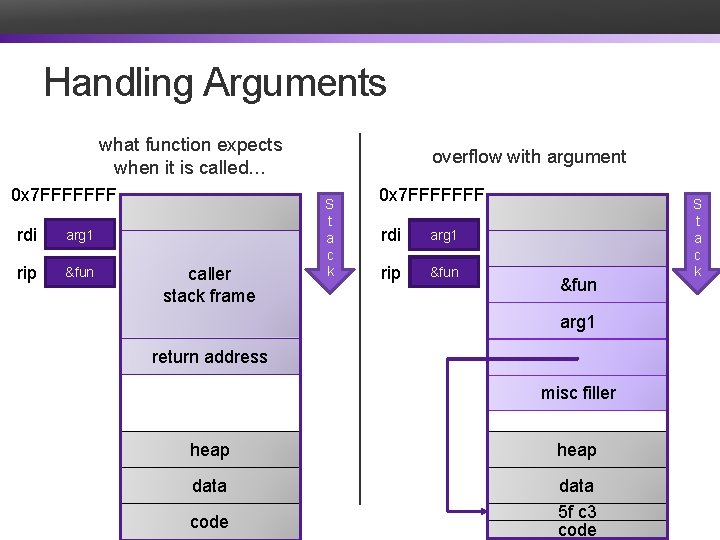
Handling Arguments what function expects when it is called… 0 x 7 FFFFFFF rdi arg 1 rip &fun caller stack frame overflow with argument S t a c k 0 x 7 FFFFFFF rdi ? arg 1 rip pc 0+4 pc 0 c 3) &fun &(c 3) &(5 f caller stack &fun frame arg 1 return address callee stack frame misc filler buffer heap data 5 f c 3 code S t a c k
Return-into-libc
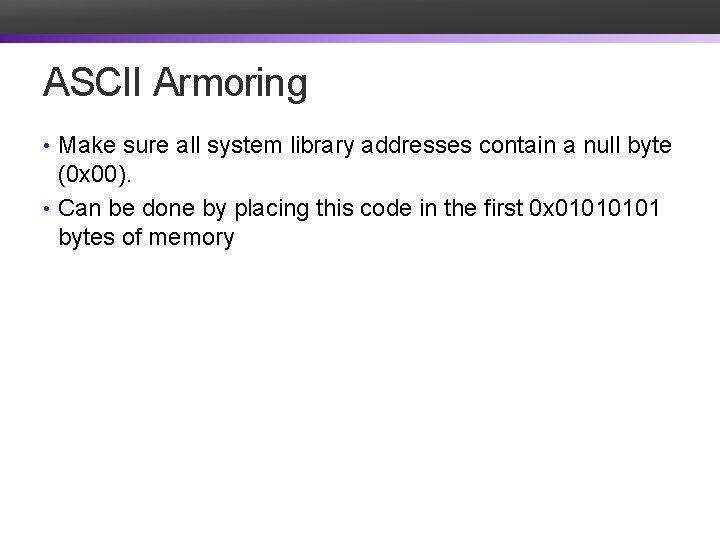
ASCII Armoring • Make sure all system library addresses contain a null byte (0 x 00). • Can be done by placing this code in the first 0 x 0101 bytes of memory

Properties of x 86 Assembly • lots of instructions • variable length instructions • not word aligned • dense instruction set
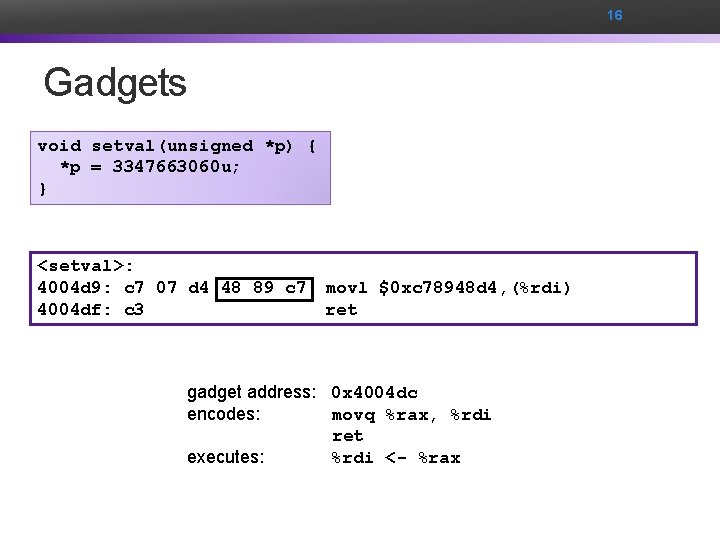
16 Gadgets void setval(unsigned *p) { *p = 3347663060 u; } <setval>: 4004 d 9: c 7 07 d 4 48 89 c 7 movl $0 xc 78948 d 4, (%rdi) 4004 df: c 3 ret gadget address: 0 x 4004 dc encodes: movq %rax, %rdi ret executes: %rdi <- %rax
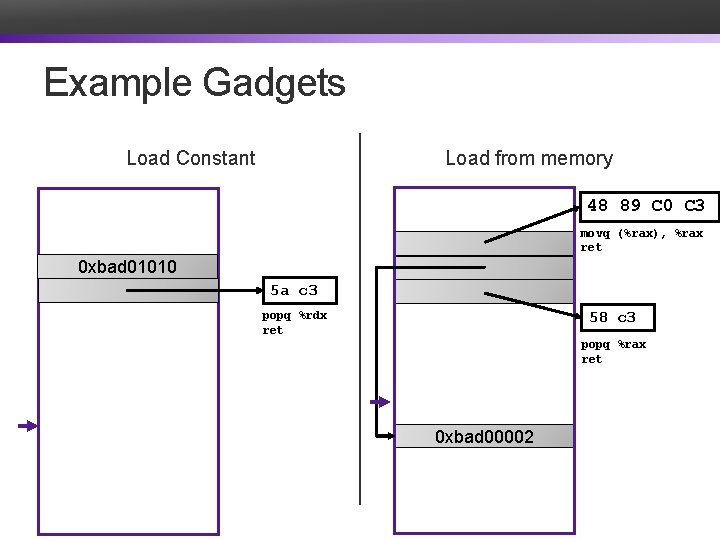
Example Gadgets Load Constant Load from memory 48 89 C 0 C 3 movq (%rax), %rax ret 0 xbad 01010 return addr 5 a c 3 Return addr 58 c 3 popq %rdx ret popq %rax ret 0 xbad 00002

Return-oriented Programming
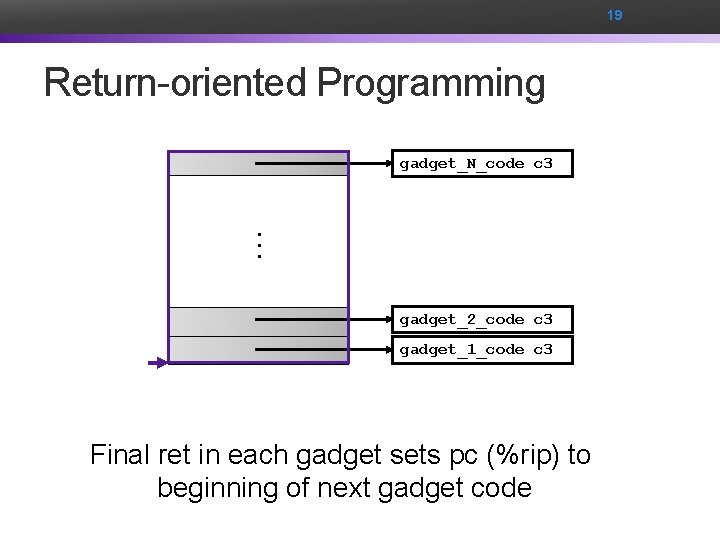
19 Return-oriented Programming … gadget_N_code c 3 gadget_2_code c 3 gadget_1_code c 3 Final ret in each gadget sets pc (%rip) to beginning of next gadget code
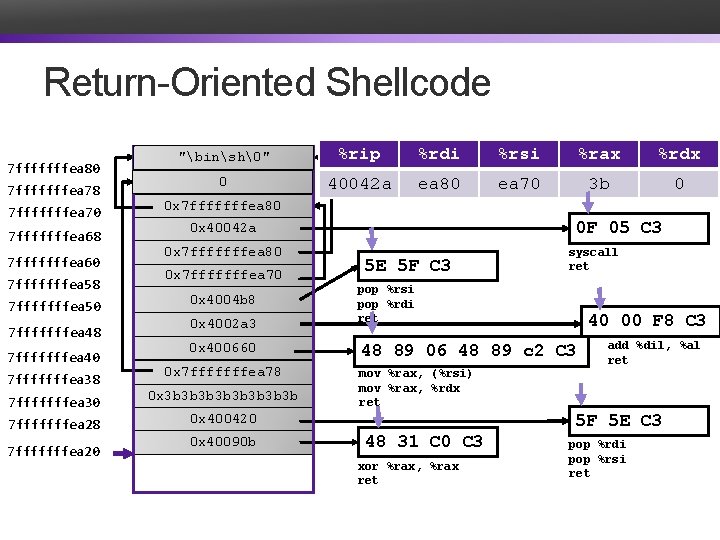
Return-Oriented Shellcode 7 fffffffea 80 7 fffffffea 78 7 fffffffea 70 7 fffffffea 68 7 fffffffea 60 7 fffffffea 58 7 fffffffea 50 7 fffffffea 48 7 fffffffea 40 "binsh�" 0 0 x 1122334455667788 %rdi 400666 400663 400660 40090 b 3 b 3 b 3 b 4004 b 8 400420 40090 e 4002 a 6 4002 a 3 400421 4004 b 9 ea 80 40042 a %rsi %rax %rdx ea 78 ea 70 00 3 b 0 0 x 7 fffffffea 80 0 F 05 C 3 0 x 40042 a 0 x 7 fffffffea 80 0 x 7 fffffffea 70 0 x 4004 b 8 0 x 4002 a 3 0 x 400660 7 fffffffea 38 0 x 7 fffffffea 78 7 fffffffea 30 0 x 3 b 3 b 7 fffffffea 28 0 x 400420 7 fffffffea 20 %rip 0 x 40090 b 5 E 5 F C 3 syscall ret pop %rsi pop %rdi ret 40 00 F 8 C 3 48 89 06 48 89 c 2 C 3 add %dil, %al ret mov %rax, (%rsi) mov %rax, %rdx ret 5 F 5 E C 3 48 31 C 0 C 3 xor %rax, %rax ret pop %rdi pop %rsi ret
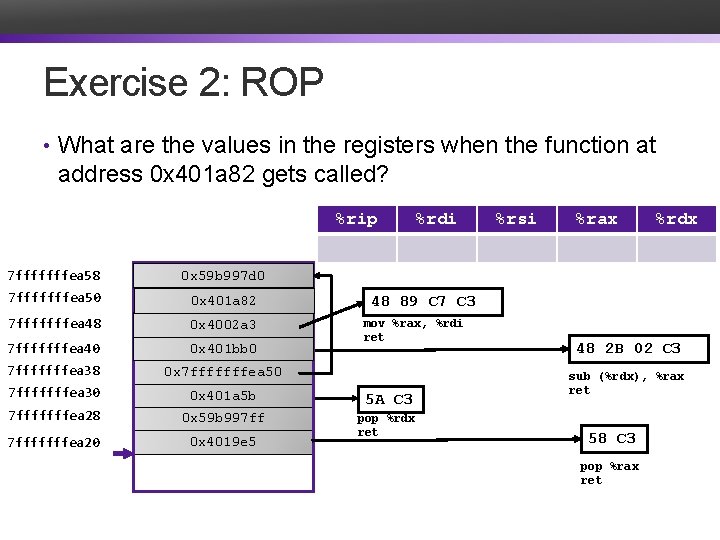
Exercise 2: ROP • What are the values in the registers when the function at address 0 x 401 a 82 gets called? %rip %rdi 7 fffffffea 58 0 x 59 b 997 d 0 7 fffffffea 50 0 x 401 a 82 7 fffffffea 48 0 x 4002 a 3 7 fffffffea 40 0 x 401 bb 0 7 fffffffea 38 0 x 7 fffffffea 50 7 fffffffea 30 0 x 401 a 5 b 7 fffffffea 28 5 A C 3 0 x 59 b 997 ff 7 fffffffea 20 0 x 4019 e 5 pop %rdx ret %rsi %rax %rdx 48 89 C 7 C 3 mov %rax, %rdi ret 48 2 B 02 C 3 sub (%rdx), %rax ret 58 C 3 pop %rax ret
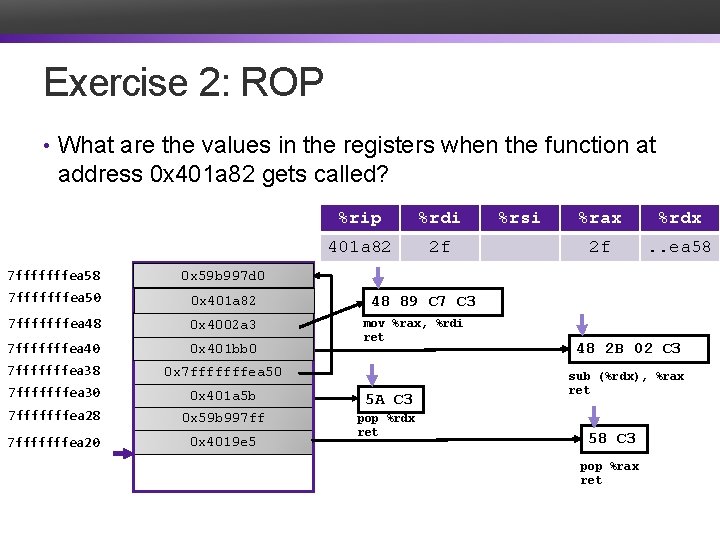
Exercise 2: ROP • What are the values in the registers when the function at address 0 x 401 a 82 gets called? %rip 401 a 5 c 401 bb 0 401 a 5 b 4002 a 3 4019 e 6 4019 e 5 401 a 82 401 bb 3 %rdi 7 fffffffea 58 0 x 59 b 997 d 0 7 fffffffea 50 0 x 401 a 82 7 fffffffea 48 0 x 4002 a 3 7 fffffffea 40 0 x 401 bb 0 7 fffffffea 38 0 x 7 fffffffea 50 7 fffffffea 30 0 x 401 a 5 b 7 fffffffea 28 5 A C 3 0 x 59 b 997 ff 7 fffffffea 20 0 x 4019 e 5 pop %rdx ret 2 f %rsi %rax %rdx. . 97 ff. . ea 58 2 f. . ea 58 48 89 C 7 C 3 mov %rax, %rdi ret 48 2 B 02 C 3 sub (%rdx), %rax ret 58 C 3 pop %rax ret
Address Space Layout Randomization
Other defenses Gadget Elimination Control Flow Integrity Code
The state of the world Defenses: • high-level languages • Stack Canaries • Memory tagging • ASLR • continuing research and development… But all they aren't perfect!
26 Exercise 3: Feedback 1. Rate how well you think this recorded lecture worked 1. Better than an in-person class 2. About as well as an in-person class 3. Less well than an in-person class, but you still learned something 4. Total waste of time, you didn't learn anything 2. How much time did you spend on this video lecture (including time spent on exercises)? 3. Do you have any questions that you would like me to address in this week's problem session? 4. Do you have any other comments or feedback?
- Slides: 26