Lawful Intercept in Vo IP Networks Manohar Mahavadi


![LI – TDM_PKT_CONF_CHNL LI Model with Conferencing Courtesy: [4] January 23 -26, 2007 • LI – TDM_PKT_CONF_CHNL LI Model with Conferencing Courtesy: [4] January 23 -26, 2007 •](https://slidetodoc.com/presentation_image/121bba8e30874c198237606aaa6e7f14/image-17.jpg)

![References [1] Security Implications of Applying the Communications Assistance to Law Enforcement Act to References [1] Security Implications of Applying the Communications Assistance to Law Enforcement Act to](https://slidetodoc.com/presentation_image/121bba8e30874c198237606aaa6e7f14/image-22.jpg)
- Slides: 22


Lawful Intercept in Vo. IP Networks Manohar Mahavadi Vice President, Software Engineering Centillium Communications Inc. Fremont, California January 23 -26, 2007 • Ft. Lauderdale, Florida

Lawful Interception – Introduction • Omnibus Crime Prevention and Safe Streets Act of 1968 – Title III legalizes law enforcement wiretaps in criminal investigations • Foreign Intelligence Surveillance Act of 1978 (FISA) – Wiretapping in advance of a crime being perpetrated • The Electronic Communications Privacy Act of 1986 (ECPA) – Sets standards for access to cell phones, e-mail and other electronic communications and transactional records (subscriber identifying information, logs, toll records) • Communications Assistance for Law Enforcement Act of 1994 (CALEA) – Preserve law enforcement wiretapping capabilities by requiring telephone companies to design their systems to ensure a basic level of government access • H. R. 3162 (The PATRIOT Act of 2001) – Post 9/11 – Expands the scope of Title III wiretaps and FISA to include computer fraud, abuse, etc. January 23 -26, 2007 • Ft. Lauderdale, Florida

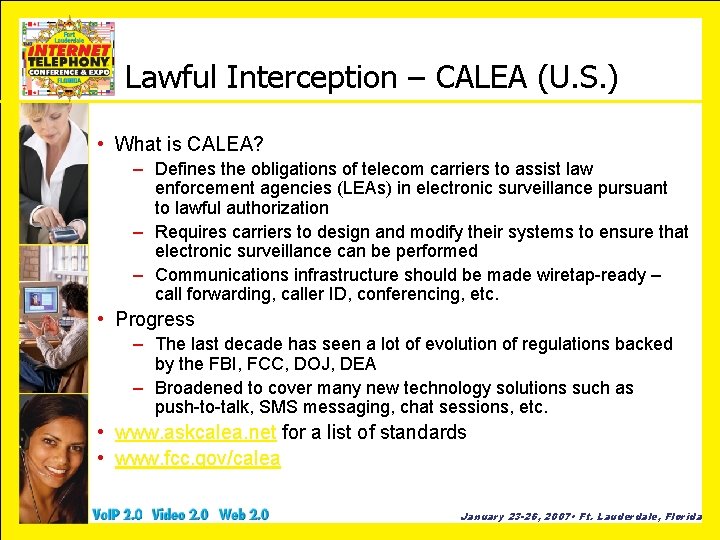
Lawful Interception – CALEA (U. S. ) • What is CALEA? – Defines the obligations of telecom carriers to assist law enforcement agencies (LEAs) in electronic surveillance pursuant to lawful authorization – Requires carriers to design and modify their systems to ensure that electronic surveillance can be performed – Communications infrastructure should be made wiretap-ready – call forwarding, caller ID, conferencing, etc. • Progress – The last decade has seen a lot of evolution of regulations backed by the FBI, FCC, DOJ, DEA – Broadened to cover many new technology solutions such as push-to-talk, SMS messaging, chat sessions, etc. • www. askcalea. net for a list of standards • www. fcc. gov/calea January 23 -26, 2007 • Ft. Lauderdale, Florida

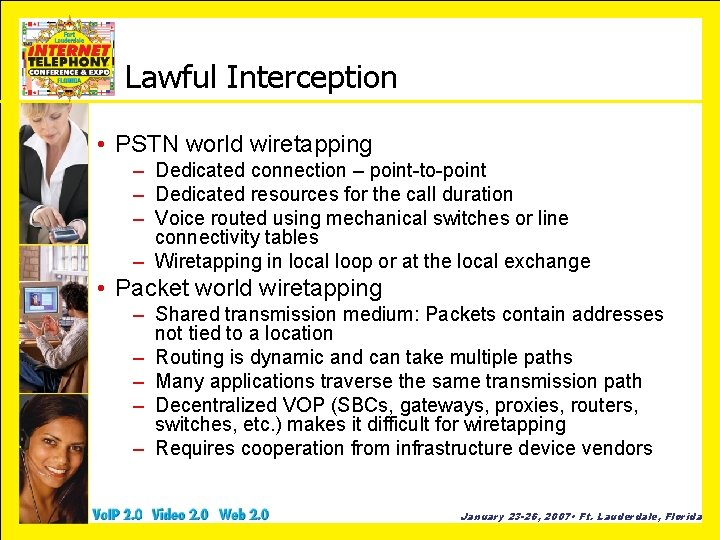
Lawful Interception • PSTN world wiretapping – Dedicated connection – point-to-point – Dedicated resources for the call duration – Voice routed using mechanical switches or line connectivity tables – Wiretapping in local loop or at the local exchange • Packet world wiretapping – Shared transmission medium: Packets contain addresses not tied to a location – Routing is dynamic and can take multiple paths – Many applications traverse the same transmission path – Decentralized VOP (SBCs, gateways, proxies, routers, switches, etc. ) makes it difficult for wiretapping – Requires cooperation from infrastructure device vendors January 23 -26, 2007 • Ft. Lauderdale, Florida

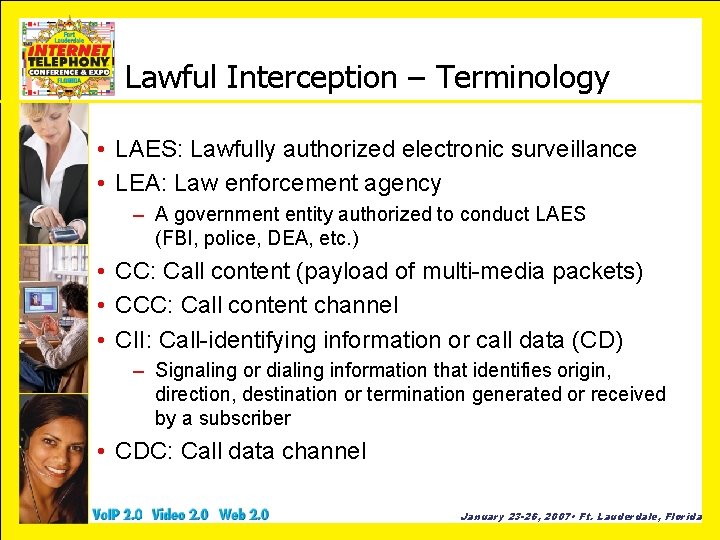
Lawful Interception – Terminology • LAES: Lawfully authorized electronic surveillance • LEA: Law enforcement agency – A government entity authorized to conduct LAES (FBI, police, DEA, etc. ) • CC: Call content (payload of multi-media packets) • CCC: Call content channel • CII: Call-identifying information or call data (CD) – Signaling or dialing information that identifies origin, direction, destination or termination generated or received by a subscriber • CDC: Call data channel January 23 -26, 2007 • Ft. Lauderdale, Florida

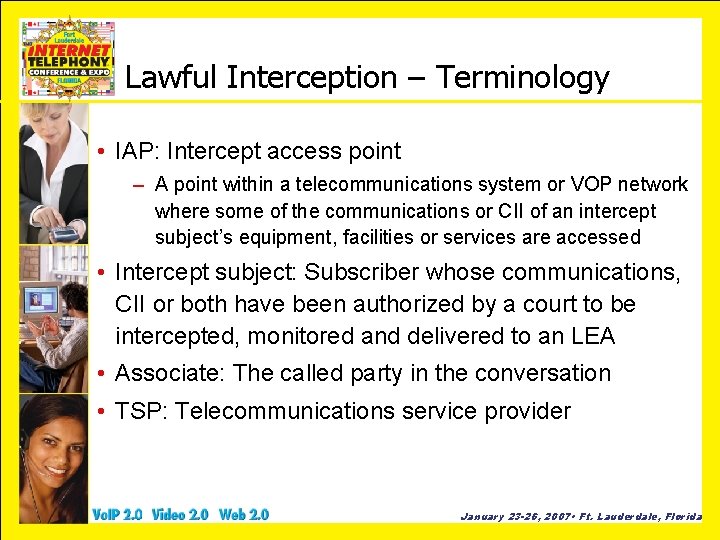
Lawful Interception – Terminology • IAP: Intercept access point – A point within a telecommunications system or VOP network where some of the communications or CII of an intercept subject’s equipment, facilities or services are accessed • Intercept subject: Subscriber whose communications, CII or both have been authorized by a court to be intercepted, monitored and delivered to an LEA • Associate: The called party in the conversation • TSP: Telecommunications service provider January 23 -26, 2007 • Ft. Lauderdale, Florida

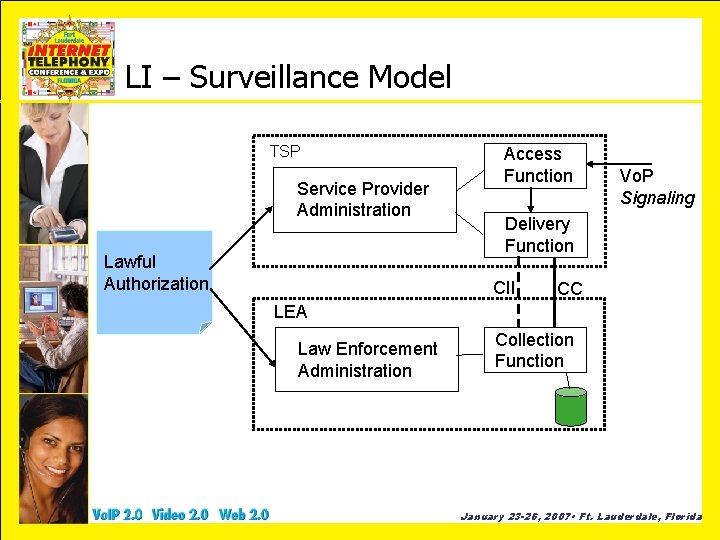
LI – Surveillance Model TSP Service Provider Administration Lawful Authorization Access Function Vo. P Signaling Delivery Function CII CC LEA Law Enforcement Administration Collection Function January 23 -26, 2007 • Ft. Lauderdale, Florida

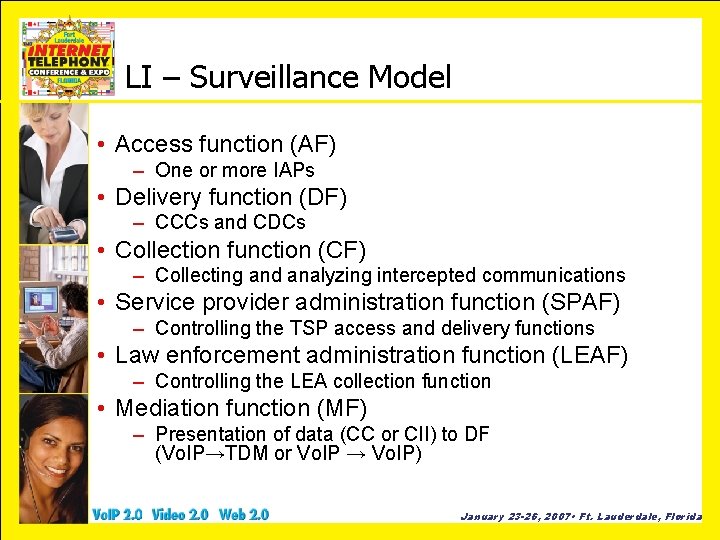
LI – Surveillance Model • Access function (AF) – One or more IAPs • Delivery function (DF) – CCCs and CDCs • Collection function (CF) – Collecting and analyzing intercepted communications • Service provider administration function (SPAF) – Controlling the TSP access and delivery functions • Law enforcement administration function (LEAF) – Controlling the LEA collection function • Mediation function (MF) – Presentation of data (CC or CII) to DF (Vo. IP→TDM or Vo. IP → Vo. IP) January 23 -26, 2007 • Ft. Lauderdale, Florida

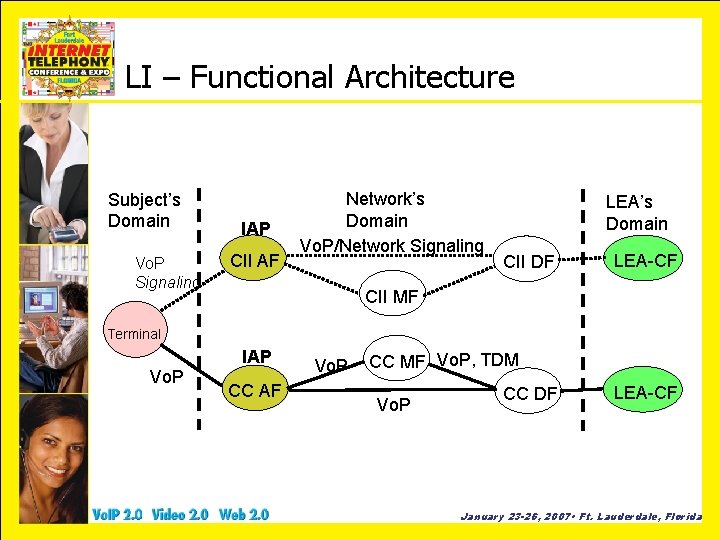
LI – Functional Architecture Subject’s Domain Vo. P Signaling IAP CII AF Network’s Domain Vo. P/Network Signaling LEA’s Domain CII DF LEA-CF CII MF Terminal Vo. P IAP CC AF Vo. P CC MF Vo. P, TDM Vo. P CC DF LEA-CF January 23 -26, 2007 • Ft. Lauderdale, Florida

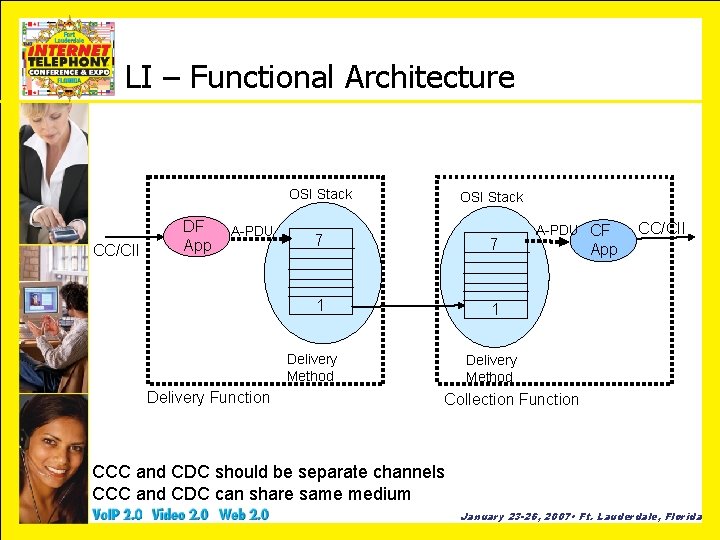
LI – Functional Architecture OSI Stack CC/CII DF App A-PDU OSI Stack 7 7 1 1 Delivery Method Delivery Function A-PDU CF CC/CII App Delivery Method Collection Function CCC and CDC should be separate channels CCC and CDC can share same medium January 23 -26, 2007 • Ft. Lauderdale, Florida

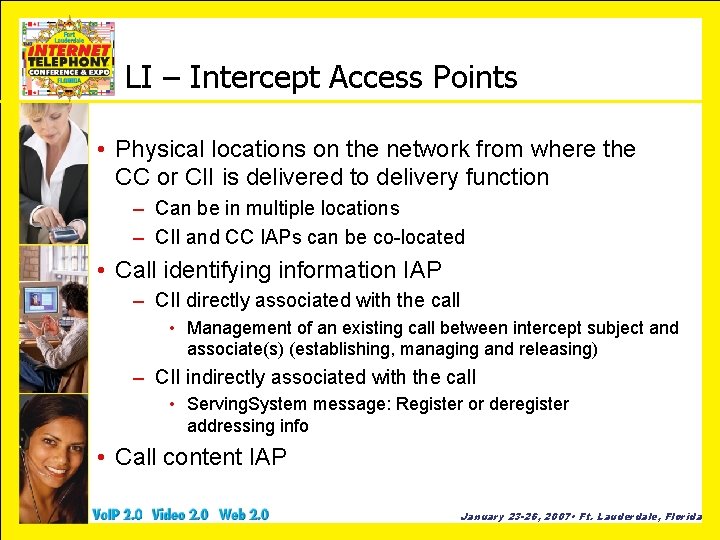
LI – Intercept Access Points • Physical locations on the network from where the CC or CII is delivered to delivery function – Can be in multiple locations – CII and CC IAPs can be co-located • Call identifying information IAP – CII directly associated with the call • Management of an existing call between intercept subject and associate(s) (establishing, managing and releasing) – CII indirectly associated with the call • Serving. System message: Register or deregister addressing info • Call content IAP January 23 -26, 2007 • Ft. Lauderdale, Florida

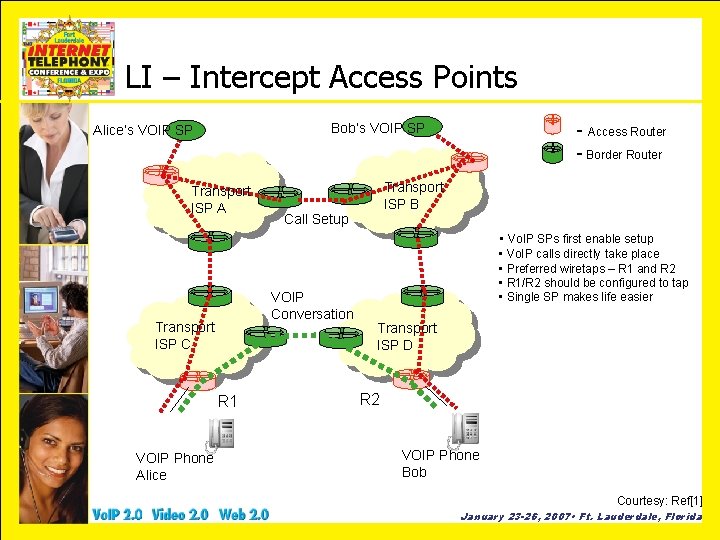
LI – Intercept Access Points - Access Router - Border Router Bob’s VOIP SP Alice’s VOIP SP Transport ISP A Transport ISP B Call Setup • Vo. IP SPs first enable setup VOIP Conversation Transport ISP C R 1 VOIP Phone Alice • Vo. IP calls directly take place • Preferred wiretaps – R 1 and R 2 • R 1/R 2 should be configured to tap • Single SP makes life easier Transport ISP D R 2 VOIP Phone Bob Courtesy: Ref[1] January 23 -26, 2007 • Ft. Lauderdale, Florida

LI – Intercept Access Points • Media gateways • Session border controllers • Access routers • Signaling proxies • CII and CC are typically delivered over secure channels to LEA January 23 -26, 2007 • Ft. Lauderdale, Florida

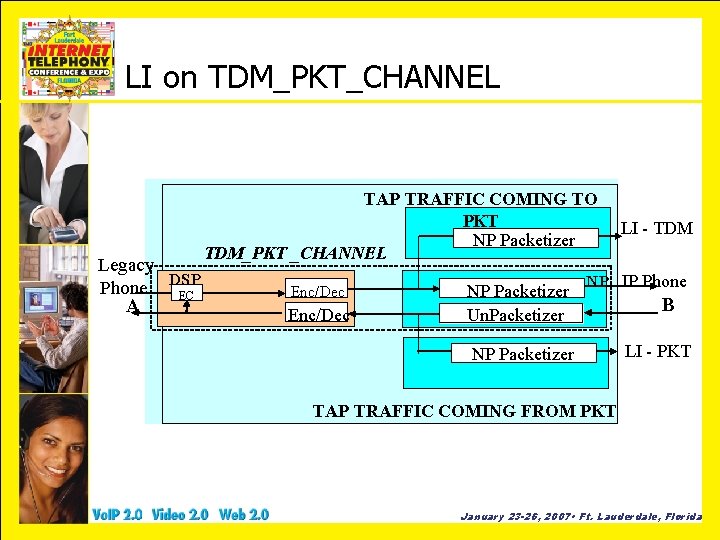
LI on TDM_PKT_CHANNEL Legacy DSP Phone EC A TAP TRAFFIC COMING TO PKT NP Packetizer TDM_PKT _CHANNEL Enc/Dec NP Packetizer Un. Packetizer LI - TDM NP IP Phone NP Packetizer B LI - PKT TAP TRAFFIC COMING FROM PKT January 23 -26, 2007 • Ft. Lauderdale, Florida

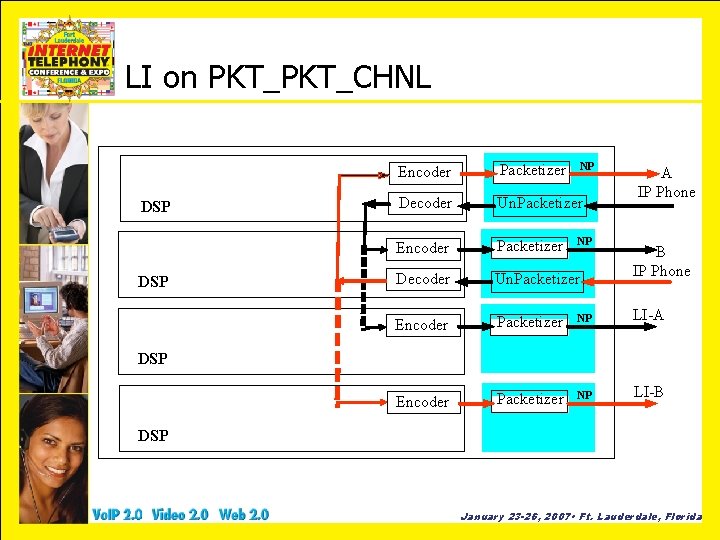
LI on PKT_CHNL DSP NP Encoder Packetizer Decoder Un. Packetizer Encoder Packetizer NP LI-A Encoder Packetizer NP LI-B NP A IP Phone B IP Phone DSP January 23 -26, 2007 • Ft. Lauderdale, Florida
![LI TDMPKTCONFCHNL LI Model with Conferencing Courtesy 4 January 23 26 2007 LI – TDM_PKT_CONF_CHNL LI Model with Conferencing Courtesy: [4] January 23 -26, 2007 •](https://slidetodoc.com/presentation_image/121bba8e30874c198237606aaa6e7f14/image-17.jpg)
LI – TDM_PKT_CONF_CHNL LI Model with Conferencing Courtesy: [4] January 23 -26, 2007 • Ft. Lauderdale, Florida

LI – Surveillance Events • Information events – Call-control related events • • Answer: Call accepted Origination: Subject initiated a Vo. P session Release: Session released along with resources Termination attempt: Session termination requested – Signaling events • Dialed digit extraction: Digits dialed after a call is connected • Direct signal reporting: Signaling from and to intercept subject • Network signal: Tone or message indicating CII (busy, ringing, etc. ) • Subject signal: Call waiting, forwarding, etc. January 23 -26, 2007 • Ft. Lauderdale, Florida

LI – Surveillance Events • Information events – Feature use events • • Change Connection break Redirection – Registration events • Address registration • Content events – – CCChange: Media characteristics established or modified CCClose: CC delivery is disabled CCOpen: CC delivery is enabled CCUnavailable: Network loses access for the call under interception January 23 -26, 2007 • Ft. Lauderdale, Florida

LI Challenges • Security vs. CALEA requirements – Security ensures privacy, packet integrity, authenticity and non-repudiation – CALEA requires intercepted packets are not secured – SRTP and secured SIP with end-to-end security poses challenge – Peer-to-peer Vo. IP communication with security enabled prevents interception – Secured traffic needs to be decrypted and re-encrypted for interception • Security Association termination and re-initiation – Key distribution or sharing with LEA January 23 -26, 2007 • Ft. Lauderdale, Florida

LI Challenges • Channel capacity affected if channel duplication is required • Design should consider requirements for extra performance • Should support all call models like Forking, Handoff, etc. • Should support all codecs in use • Requires additional interface support January 23 -26, 2007 • Ft. Lauderdale, Florida
![References 1 Security Implications of Applying the Communications Assistance to Law Enforcement Act to References [1] Security Implications of Applying the Communications Assistance to Law Enforcement Act to](https://slidetodoc.com/presentation_image/121bba8e30874c198237606aaa6e7f14/image-22.jpg)
References [1] Security Implications of Applying the Communications Assistance to Law Enforcement Act to Voice over IP, Steve Bellovin, et al, June 13, 2006 [2] Electronics Surveillance Needs for Carrier-Grade Voice Over Packet (CGVo. P) Service, FBI Document for CALEA [3] Lawfully Authorized Electronic Surveillance (LAES) for voice over Packet Technologies in Wireline Telecommunications Networks ANSI T 1. 678. xxxx [4] 05/2000, TIA/EIA/J-STD-025 Lawfully Authorized Electronic Surveillance, revision A: updated [5] 09/200, TIA/EIA/J-STD-025 Lawfully Authorized Electronic Surveillance, updated [6] www. askcalea. net [7] www. fcc. gov/calea January 23 -26, 2007 • Ft. Lauderdale, Florida
 Manohar mahavadi
Manohar mahavadi Manohar mahavadi
Manohar mahavadi Lawful intercept cisco
Lawful intercept cisco X intercept and y intercept
X intercept and y intercept X intercept form
X intercept form Axinometric
Axinometric Lawful object
Lawful object Explain virtual circuit and datagram network
Explain virtual circuit and datagram network Basestore iptv
Basestore iptv Tacheometry
Tacheometry Slope intercept form story problems
Slope intercept form story problems Converting linear equations to slope intercept form
Converting linear equations to slope intercept form X intercept method
X intercept method Brant & associates tulsa ok
Brant & associates tulsa ok Intercept problems
Intercept problems How to tell if graph opens up or down
How to tell if graph opens up or down Using transformations to graph quadratic functions
Using transformations to graph quadratic functions Converting to slope intercept form
Converting to slope intercept form Graphing lines in slope intercept form
Graphing lines in slope intercept form Lesson 4-6 slope intercept form answer key
Lesson 4-6 slope intercept form answer key Find y intercept
Find y intercept 1-4 writing linear equations
1-4 writing linear equations Metode lit
Metode lit