LABORATORY MANAGEMENT SAFETY EBS 366 COMPUTER LABORATORY SECURITY

LABORATORY MANAGEMENT & SAFETY EBS 366

COMPUTER LABORATORY SECURITY MANAGEMENT Session Six (6)

COMPUTER SECURITY Computer security basically is the protection of computer systems and information from harm, theft, and unauthorized use. It is the process of preventing and detecting unauthorized use of your computer system

TYPES OF COMPUTER SECURITY Information security is securing information from unauthorized access, modification & deletion • Application Security is securing an application by building security features to prevent from Cyber Threats such as SQL injection, Do. S attacks, data breaches and etc.

TYPES OF COMPUTER SECURITY Computer Security means securing a standalone machine by keeping it updated and patched Network Security is by securing both the software and hardware technologies Cybersecurity is defined as protecting computer systems, which communicate over the computer networks
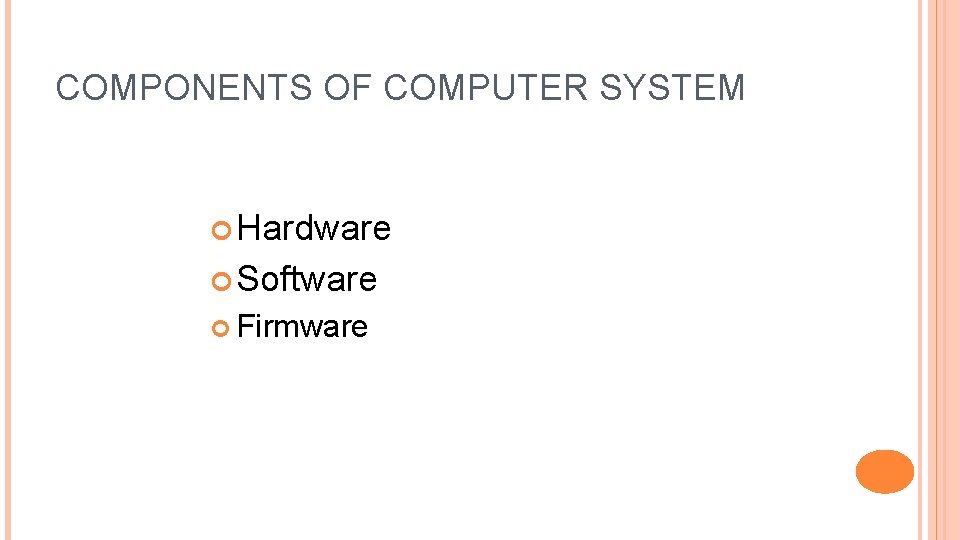
COMPONENTS OF COMPUTER SYSTEM Hardware Software Firmware
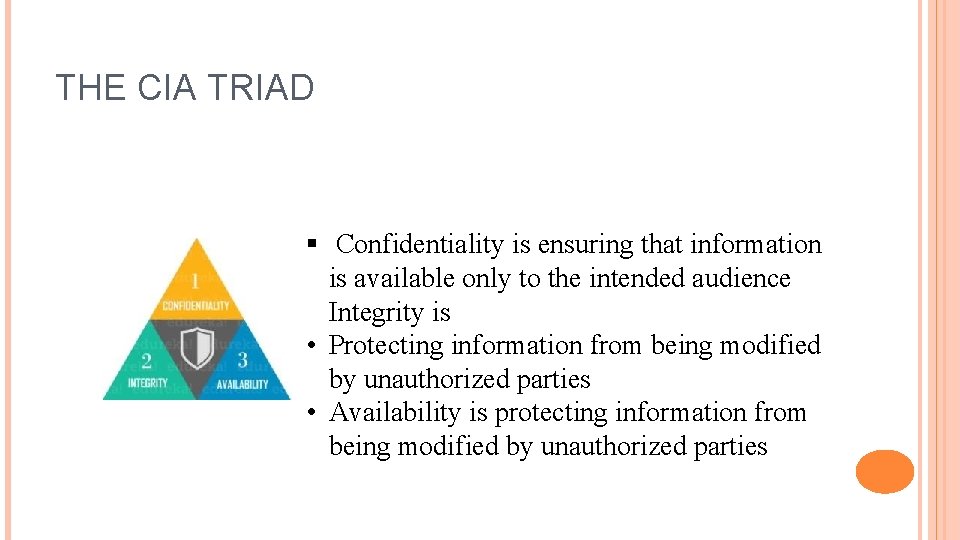
THE CIA TRIAD § Confidentiality is ensuring that information is available only to the intended audience Integrity is • Protecting information from being modified by unauthorized parties • Availability is protecting information from being modified by unauthorized parties

COMPUTER SECURITY THREATS Computer security threats are possible dangers that can possibly hamper the normal functioning of your computer. The most harmful types of computer security are: Viruses, Computer Worm, Phishing, Botnet, Rootkit, Keylogger, etc.

WHY COMPUTER SECURITY IMPORTANT In this digital era, we all want to keep our computers and our personal information secure and hence computer security is important to keep our personal information protected Improve system performance

COMPUTER LABORATORY RISKS Risks to laboratory security include: Theft or diversion of mission-critical or high-value equipment; Threats from activist groups or individuals; Sabotage or vandalism of high-value equipment; Loss or release of sensitive information; and Rogue work or unauthorized laboratory activities.

DOMAINS OF SECURITY Physical or architectural security- doors, walls, fences, locks, etc. Electronic security- alarm systems, password protection procedures, etc. Operational security- authorization procedures, background checks, etc. Information security- passwords, backup systems,

PHYSICAL AND ELECTRONIC SECURITY Door locks Video surveillance Other systems Eg. Glass-break alarms for windows and doors, Intrusion alarms, Hardware to prevent tampering with window and/or door locks, Lighting of areas where people may enter a secure area, etc.

SECURITY PLANS outline of elements that should be considered for any laboratory security plan Identify the leadership structure for security issues. • Secure the assets that are likely to be most vulnerable • Deter cyber sabotage, including unauthorized on-site or remote access to critical process controls. • Prevent diversion using secure shipping, receiving, and storage of target materials.

SECURITY PLANS outline of elements that should be considered for any laboratory security plan Identify the leadership structure for security issues. • Detect theft or diversion of target materials through inventory controls. • Establish a process for personnel surety, such as background checks, of laboratory personnel, visitors, and others with access to the laboratory. • Screen and control access to the facility using identification badges, electronic access controls, and security personnel.

SECURITY PLANS outline of elements that should be considered for any laboratory security plan Identify the leadership structure for security issues. • Train laboratory personnel on the security measures, response, and importance of compliance with security procedures. • • Monitor (detect) the security of those assets, such that a security breach would be noticed, and (for high-risk equipment) would prompt an immediate response Maintain monitoring, communication, and warning systems.

SECURITY PLANS Outline of elements that should be considered for any laboratory security plan Identify the leadership structure for security issues. • Investigate and track reports of security-related incidents. Document the incident reports, including findings and mitigation. • • Maintain records of compliance with the security plan. Develop a multilevel security plan that identifies appropriate security processes, procedures, and systems for normal security operations and increasing levels of security for periods of higher risk. .
THE END OF SESSION SIX THANK YOU
- Slides: 17