KS 3 Computer Science Ethical and Cultural Issues











- Slides: 15

KS 3 Computer Science: Ethical and Cultural Issues Topics Covered: Laws - Network Security Threats - Censorship Surveillance - Online Privacy - Social Media

Objectives • Consider the ethical and cultural issues related to computer science technologies • Consider privacy issues • Consider the environmental impact of computer science Keywords ethical - moral - computer - environmental - cultural - future - security data - networks - responsibility - privacy - surveillance - censorship legislation - cybercrime - threats - misuse

Ethical, Moral, Cultural and Environmental issues in Computer Science

Ethics v Morals There are laws that govern how we use computers. There also ethical concerns about issues such as piracy, hacking and the environment. Ethics refer to rules provided by an external source eg workplace or religion. Morals refer to an individuals own principles regarding right and wrong.

Privacy What information can we consider to be private and who owns data? For example, photographs that are uploaded to social networks often legally become the property of the website. Think: At what stage can private information like this be used and for what purposes?

Privacy Computer systems store lots of personal details, and personal data can be very valuable. The Data Protection Act protects us. Breaches of data protection are often in the news. For example, NHS Surrey was fined £ 200, 000 for selling a computer that contained patients' personal records without first destroying the data on the hard drive.

Sharing Data Whilst using the internet, users often upload information such as birthdays, passwords and banking details. As we use browsers and web applications , we create a record about our interests. Information like this can be valuable to companies, eg advertising companies spend a lot of money seeking better ways to target adverts at the right users.

Sharing Resources There are piracy laws protecting the distribution of films and other media. It is illegal to rip a copyrighted DVD or CD and distribute it online. Can you remember the name of the Act?

Sharing Resources However, peer-to-peer (P 2 P) filesharing networks and hosting websites mean it is easy to share files with anyone in the world. Think: At which point does sharing a film with others become piracy?

Tracking Online Activity A person's online activity can be tracked through their IP address. Like a postal address, an IP address identifies a computer and its physical location on the network. All online activity can be tracked using an IP address. This is a method used to detect criminals on the internet and can be used to trace malicious comments made online.

Cyber Bullying As the use and importance of computer systems in society has increased, the opportunities to misuse them have also increased. In the UK there is a legal Can you remember framework that governs the name of the use of computers. Act?

Cyber Bullying The ease of communication that comes with social networking sites, email and mobile phones means that it is also easier to be unpleasant to other people. Cyberbullying involves abuse of another person using threats, insults and hurtful remarks and messages over the internet. There have been numerous reports of people who have been driven to suicide by persistent cyberbullying. Internet trolls post messages and comments that try to evoke an emotional response from other people. BBC presenter Richard Bacon and other celebrities have spoken about being victims of trolls.

Digital Divide A society which is dependent on technology can create inequality. The gap between those who have access to the latest technology and those who do not is called the 'digital

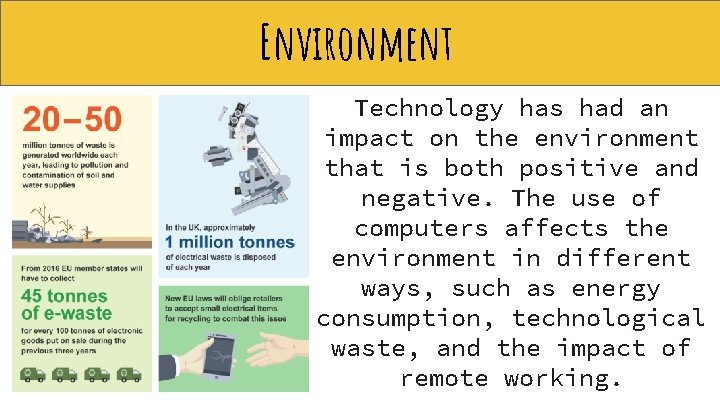
Environment Technology has had an impact on the environment that is both positive and negative. The use of computers affects the environment in different ways, such as energy consumption, technological waste, and the impact of remote working.

Complete the Recall Quiz Complete the recall question document.