KMIP PKCS12 February 2014 Tim Hudson tjhcryptsoft com

KMIP PKCS#12 February 2014 Tim Hudson – tjh@cryptsoft. com 1

Context PKCS#12 is used as the general protected import/export of credentials (private key, certificate chains) all password protected. Supporting this usage within KMIP is desirable as many vendors use this as the primary format for loading in client credentials or for providing server generated client credentials. 2

Challenges PKCS#12 • Complex format • Contains arbitrary buckets of keys and certificates • Simple usage is common – private key, certificate, CA certificates (with possible intermediate chain) 3

Example PKCS#8 Register 4

Map as Key Wrapping Format • Add PKCS 12 as a Key Format Type (to match PKCS#1, PKCS#8 existing usage) is simple • Adding PKCS 12 as a Key Wrapping approach is less straight forward • Where does the password/passphrase go? • Same issue for PKCS#8 as for PKCS#12 5
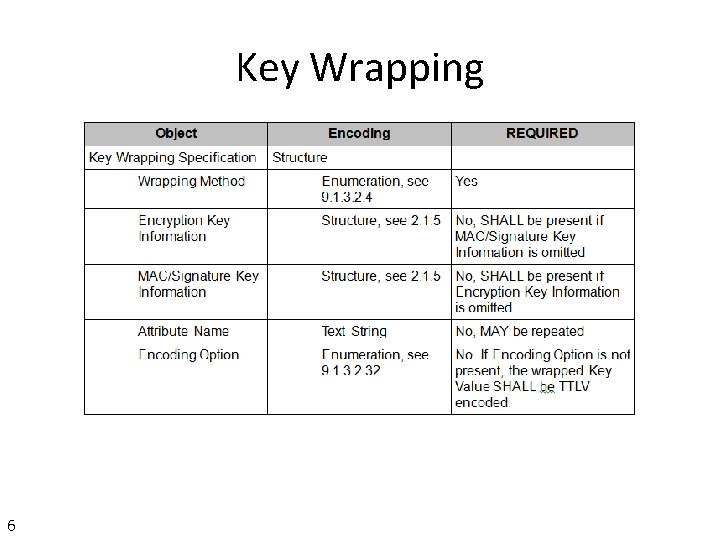
Key Wrapping 6
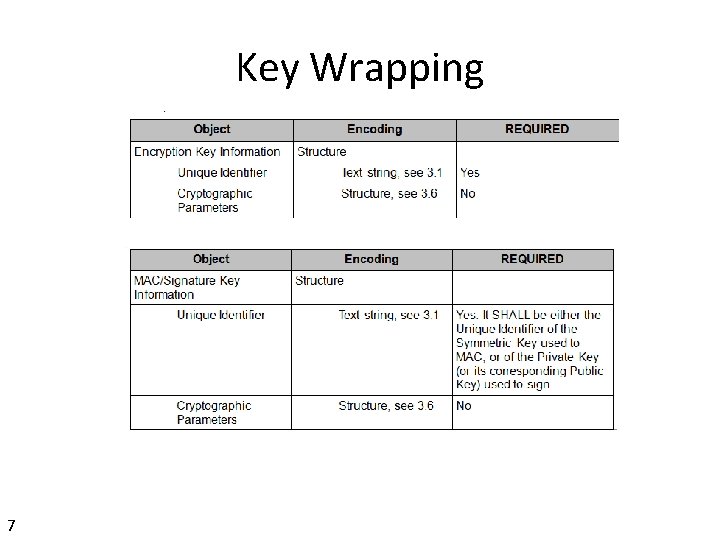
Key Wrapping 7
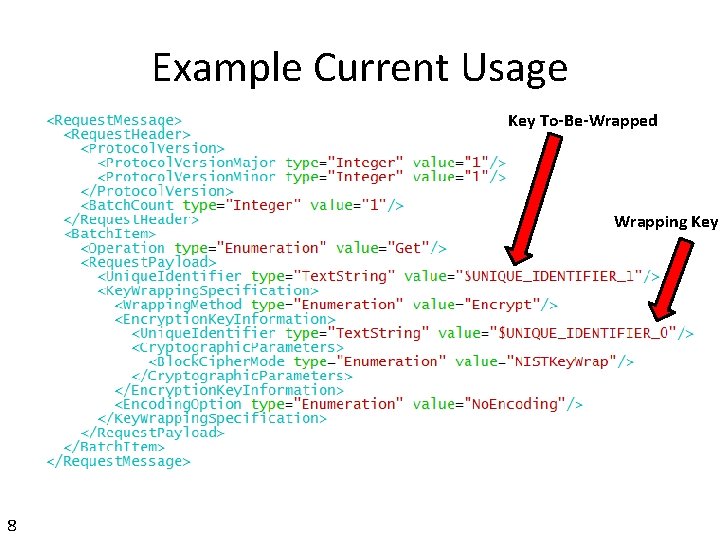
Example Current Usage Key To-Be-Wrapped Wrapping Key 8
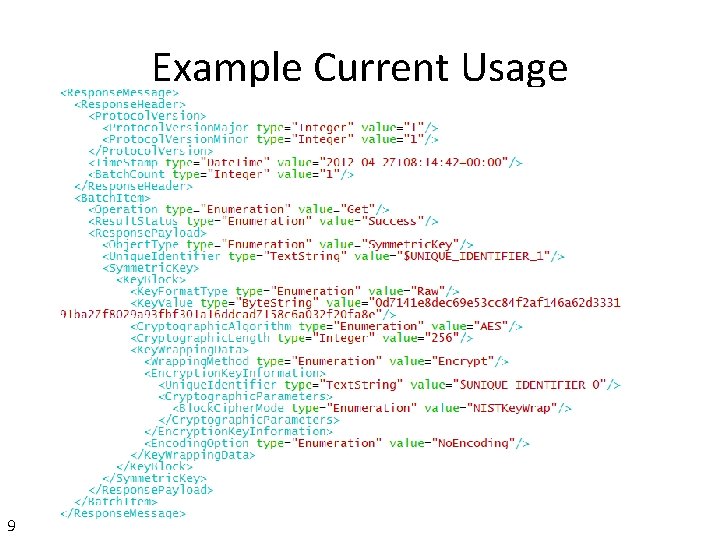
Example Current Usage 9

Map as Key Wrapping Format • If PKCS#12 (and PKCS#8) are allowed as Key Wrapping Format values then – Which managed objects get packaged? – Which managed objects can this be used against? – PKCS#12 is used for both protected private key transport and bucketof-certificates transport (trust chains) • Follow the links? – Works for Private Key and Public Key to Certificate – Doesn’t work for the chain – unless we add in the links using the new link types … • Reference a Secret Data managed object for the passphrase? 10
- Slides: 10