KMIP Hardware Security Modules MetaDataOnly MDO Keys Saikat








- Slides: 11

KMIP - Hardware Security Modules Meta-Data-Only (MDO) Keys Saikat Saha & Denis Pochuev Saikat. saha@safenet-inc. com denis. pochuev@safenet-inc. com Feb 2012

Purpose of HSM (Hardware Security Module) - Hardware based Key Storage Device - Provides High Assurance – FIPS 140 -2 Level 2 & 3 - Creates, Stores and manages various cryptographic objects ØSymmetric Keys ØAsymmetric Keys ØCertificates - Provides Crypto Acceleration and root of trust (trust anchor) - Available in PCI as well as Network Appliance versions with multiple partitions - NIST disapproves key material leaving the FIPS boundary 2

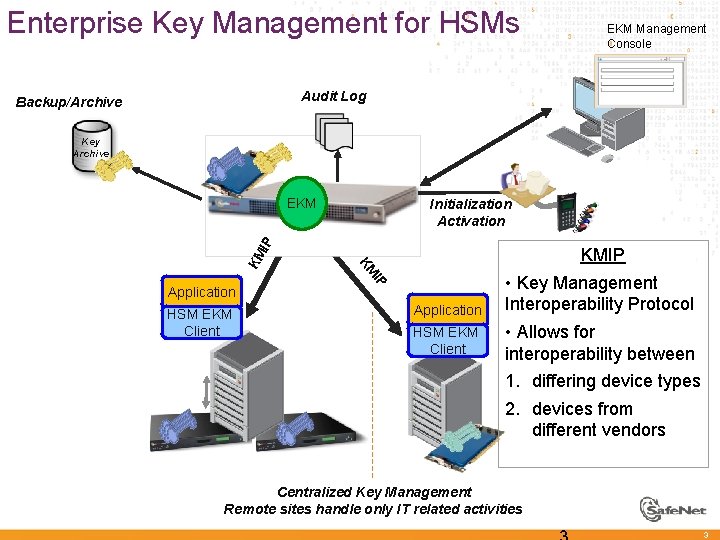
Enterprise Key Management for HSMs EKM Management Console Audit Log Backup/Archive Key Archive EKM HSM EKM Client IP Application KMIP KM KM IP Initialization Activation Application HSM EKM Client • Key Management Interoperability Protocol • Allows for interoperability between 1. differing device types 2. devices from different vendors Centralized Key Management Remote sites handle only IT related activities 3

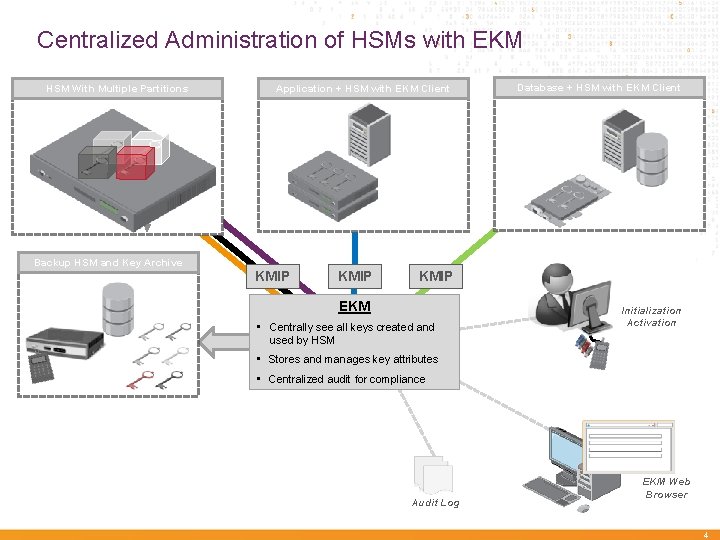
Centralized Administration of HSMs with EKM HSM With Multiple Partitions Application + HSM with EKM Client Database + HSM with EKM Client Backup HSM and Key Archive KMIP EKM • Centrally see all. K keys created and e S y used by HSMe Initialization Activation c urekey attributes • Stores and manages • Centralized audit for compliance Audit Log EKM Web Browser 4

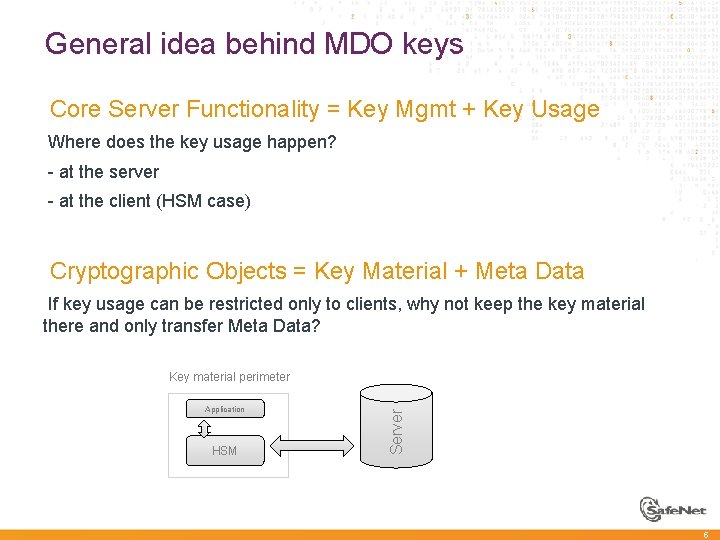
General idea behind MDO keys à Core Server Functionality = Key Mgmt + Key Usage Where does the key usage happen? à - at the server à - at the client (HSM case) à à Cryptographic Objects = Key Material + Meta Data If key usage can be restricted only to clients, why not keep the key material there and only transfer Meta Data? à Application HSM Server Key material perimeter 5

KMIP commands and MDO keys Supported KMIP Commands à Create Key Pair à Register à Locate à Get Attributes à Get Attribute List à Add Attribute à Modify Attribute à Delete Attribute à Destroy à Query à MDO KMIP Commands à Create Key Pair à Register à Locate à Get Attributes à Get Attribute List à Add Attribute à Modify Attribute à Delete Attribute à Destroy à Query à 6

KMIP Register operation in detail Regular KMIP Request à Request Message (0 x 420078) | 0 x 01 | 00000 | à Request Header (0 x 420077) | 0 x 01 | … à Batch Item (0 x 42000 f) | 0 x 01 | 00000 | à Operation (0 x 42005 c) | 0 x 05 | 0 x 00000004 | 0 x 00000003 à Unique Batch Item ID (0 x 420093) | 0 x 08 | 0 x 00000001 | 39 à Request Payload (0 x 420079) | 0 x 01 | 00000 | à Object Type (0 x 420057) | 0 x 05 | 0 x 00000004 | 0 x 00000002 à Template-Attribute (0 x 420091) | 0 x 01 | 00000 | à Attribute (0 x 420008) | 0 x 01 | 00000 | à Attribute Name (0 x 42000 a) | 0 x 07 | 0 x 00000018 | Cryptographic Usage Mask à Attribute Value (0 x 42000 b) | 0 x 02 | 0 x 00000004 | 0 x 00000007 à Attribute (0 x 420008) | 0 x 01 | 00000 | à Attribute Name (0 x 42000 a) | 0 x 07 | 0 x 00000004 | Name à Attribute Value (0 x 42000 b) | 0 x 01 | 00000 | à Name Value (0 x 420055) | 0 x 07 | 0 x 00000005 | mykey à Name Type (0 x 420054) | 0 x 05 | 0 x 00000004 | 0 x 00000001 à à Symmetric Key (0 x 42008 f) | 0 x 01 | 00000 | Key Block (0 x 420040) | 0 x 01 | 00000 | Meta-Data Registered Object à Key Format Type (0 x 420042) | 0 x 05 | 0 x 00000004 | 0 x 00000001 à Key Value (0 x 420045) | 0 x 01 | 00000 | à Key Material (0 x 420043) | 0 x 08 | 0 x 00000010 | 01 23 45 67 89 ab cd ef 01 23 45 67… à Cryptographic Algorithm (0 x 420028) | 0 x 05 | 0 x 00000004 | 0 x 00000003 à Cryptographic Length (0 x 42002 a) | 0 x 02 | 0 x 00000004 | 0 x 00000080 7

KMIP Register operation in detail Regular KMIP Request à Request Message (0 x 420078) | 0 x 01 | 00000 | MDO KMIP Request à Request Message (0 x 420078) | 0 x 01 | 0 x 00000180 | à Request Header (0 x 420077) | 0 x 01 | … à Batch Item (0 x 42000 f) | 0 x 01 | 00000 | à Batch Item (0 x 42000 f) | 0 x 01 | 0 x 00000128 | Re à Operation (0 x 42005 c) | 0 x 05 | 0 x 00000004 | 0 x 00000003 à Unique Batch Item ID (0 x 420093) | 0 x 08 | 0 x 00000001 | 39 à Unique Batch Item ID (0 x 420093) | 0 x 08 | 0 x 00000001 | 30 à Request Payload (0 x 420079) | 0 x 01 | 00000 | à Request Payload (0 x 420079) | 0 x 01 | 0 x 00000100 | à Object Type (0 x 420057) | 0 x 05 | 0 x 00000004 | 0 x 00000002 à Template-Attribute (0 x 420091) | 0 x 01 | 00000 | à Template-Attribute (0 x 420091) | 0 x 01 | 0 x 000000 e 8 | à Attribute (0 x 420008) | 0 x 01 | 00000 | à Attribute (0 x 420008) | 0 x 01 | 0 x 00000030 | à Attribute Name (0 x 42000 a) | 0 x 07 | 0 x 00000018 | Cryptographic Usage Mask à Attribute Name (0 x 42000 a) | 0 x 07 | 0 x 00000017 | Cryptographic Algorithm à Attribute Value (0 x 42000 b) | 0 x 02 | 0 x 00000004 | 0 x 00000007 à Attribute Value (0 x 42000 b) | 0 x 05 | 0 x 00000004 | 0 x 00000003 à Attribute (0 x 420008) | 0 x 01 | 00000 | à Attribute (0 x 420008) | 0 x 01 | 0 x 00000030 | à Attribute Name (0 x 42000 a) | 0 x 07 | 0 x 00000004 | Name à Attribute Name (0 x 42000 a) | 0 x 07 | 0 x 00000014 | Cryptographic Length à Attribute Value (0 x 42000 b) | 0 x 01 | 00000 | à Attribute Value (0 x 42000 b) | 0 x 02 | 0 x 00000004 | 0 x 00000080 à Name Value (0 x 420055) | 0 x 07 | 0 x 00000005 | mykey à à Name Type (0 x 420054) | 0 x 05 | 0 x 00000004 | 0 x 00000001 à Attribute Name (0 x 42000 a) | 0 x 07 | 0 x 00000018 | Cryptographic Usage Mask à Attribute Value (0 x 42000 b) | 0 x 02 | 0 x 00000004 | 0 x 00000007 à à Symmetric Key (0 x 42008 f) | 0 x 01 | 00000 | Key Block (0 x 420040) | 0 x 01 | 00000 | à Attribute (0 x 420008) | 0 x 01 | 0 x 00000030 | Attribute (0 x 420008) | 0 x 01 | 0 x 00000038 | à Key Format Type (0 x 420042) | 0 x 05 | 0 x 00000004 | 0 x 00000001 à Attribute Name (0 x 42000 a) | 0 x 07 | 0 x 00000004 | Name à Key Value (0 x 420045) | 0 x 01 | 00000 | à Attribute Value (0 x 42000 b) | 0 x 01 | 0 x 00000020 | à Key Material (0 x 420043) | 0 x 08 | 0 x 00000010 | 01 23 45 67 89 ab cd ef 01 23 45 67… à Cryptographic Algorithm (0 x 420028) | 0 x 05 | 0 x 00000004 | 0 x 00000003 à Cryptographic Length (0 x 42002 a) | 0 x 02 | 0 x 00000004 | 0 x 00000080 à Name Value (0 x 420055) | 0 x 07 | 0 x 00000005 | mykey à Name Type (0 x 420054) | 0 x 05 | 0 x 00000004 | 0 x 00000001 8

New key format à What happened to Key Format in previous request? - Key Format is not a full-fledged attribute à - Absence of the object => custom key format à - Key Format is purely internal à 9

KMIP Updates for MDO keys à Crypto Domain Parameters o Crypto parameters need to be a part of the Register command, not only Create Key Pair à ECC Enumeration o Need a broader set of supported curves 10

Questions? à Thank you. 11