Keywords User access levels Passwords Encryption Cipher Key



- Slides: 8

Keywords User access levels, Passwords, Encryption, Cipher, Key Systems Security Protecting Systems

Passwords Objectives BEGINNER: Understand how user access levels effect a system. ADVANCED: Explain how encryption works and how it can have a negative effect on law enforcement and investigations. EXPERT: Demonstrate a knowledge of a cypher and its’ key. 1. What are the benefits of encryption? 2. Why should passwords be kept secure?

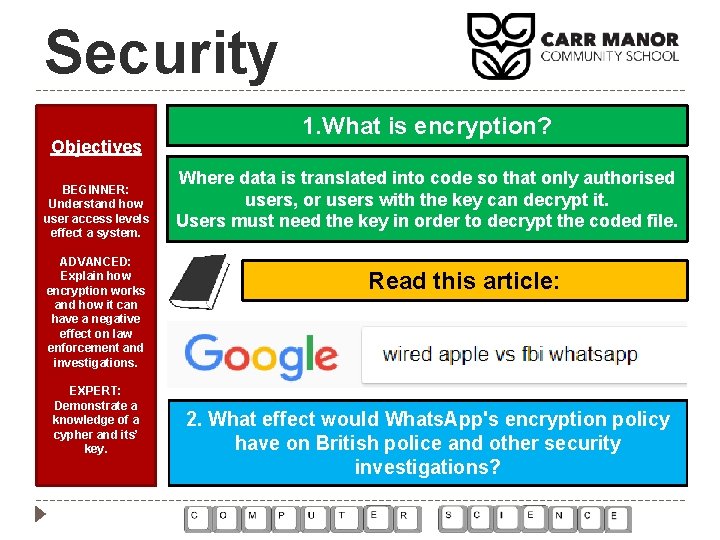
Security Objectives BEGINNER: Understand how user access levels effect a system. ADVANCED: Explain how encryption works and how it can have a negative effect on law enforcement and investigations. EXPERT: Demonstrate a knowledge of a cypher and its’ key. 1. What is encryption? Where data is translated into code so that only authorised users, or users with the key can decrypt it. Users must need the key in order to decrypt the coded file. Read this article: 2. What effect would Whats. App's encryption policy have on British police and other security investigations?

Security Objectives BEGINNER: Understand how user access levels effect a system. ADVANCED: Explain how encryption works and how it can have a negative effect on law enforcement and investigations. EXPERT: Demonstrate a knowledge of a cypher and its’ key. 1. What is Caesar cypher? Cipher invented by Julius Caesar. Designed to keep his messages secret. Works by encrypting messages through movement of each letter a certain number of places to the left in the alphabet. Key tells us how many places to the left the letters have been moved. Let’s say we received the message ABZOVMQBA with and the key was 3. A B Z O V M Q B A D E C R Y P T E D

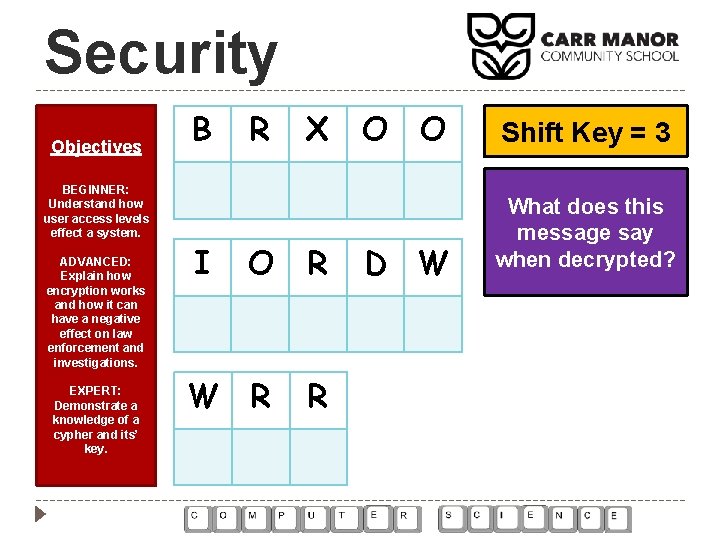
Security Objectives BEGINNER: Understand how user access levels effect a system. ADVANCED: Explain how encryption works and how it can have a negative effect on law enforcement and investigations. EXPERT: Demonstrate a knowledge of a cypher and its’ key. B I R X O R W R R O O D W Shift Key = 3 What does this message say when decrypted?

Security Objectives BEGINNER: Understand how user access levels effect a system. ADVANCED: Explain how encryption works and how it can have a negative effect on law enforcement and investigations. EXPERT: Demonstrate a knowledge of a cypher and its’ key. B R X O O Y O U L L I O R D W F L O A W R R T O O T Shift Key = 3

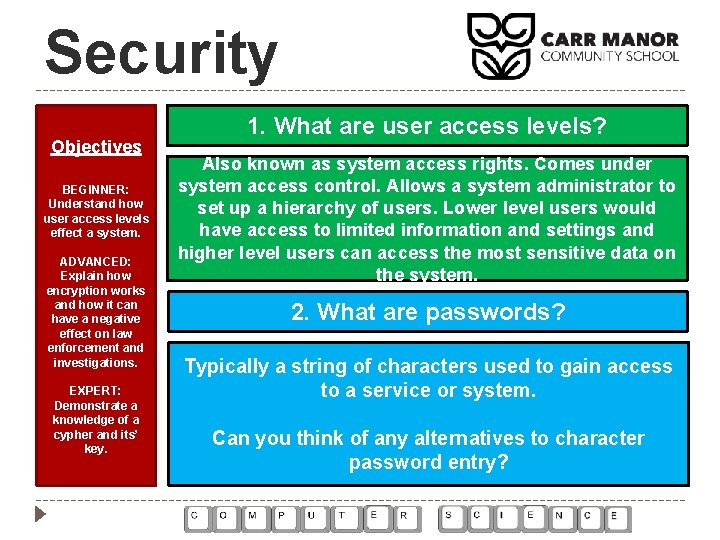
Security Objectives BEGINNER: Understand how user access levels effect a system. ADVANCED: Explain how encryption works and how it can have a negative effect on law enforcement and investigations. EXPERT: Demonstrate a knowledge of a cypher and its’ key. 1. What are user access levels? Also known as system access rights. Comes under system access control. Allows a system administrator to set up a hierarchy of users. Lower level users would have access to limited information and settings and higher level users can access the most sensitive data on the system. 2. What are passwords? Typically a string of characters used to gain access to a service or system. Can you think of any alternatives to character password entry?

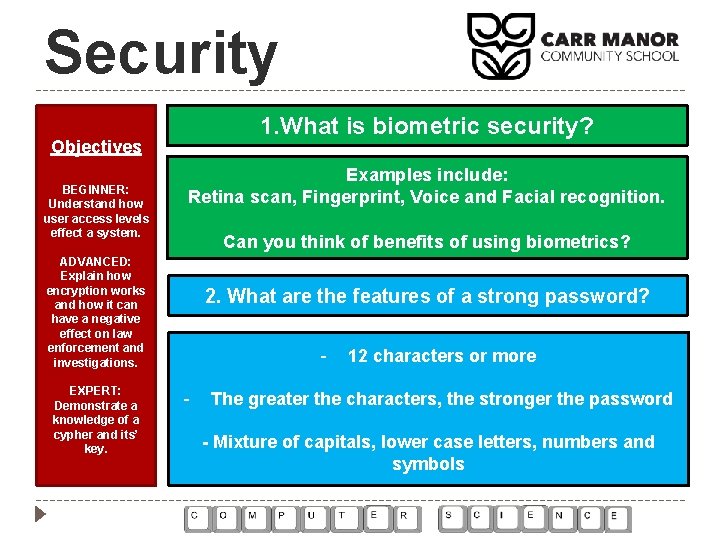
Security 1. What is biometric security? Objectives BEGINNER: Understand how user access levels effect a system. Examples include: Retina scan, Fingerprint, Voice and Facial recognition. Can you think of benefits of using biometrics? ADVANCED: Explain how encryption works and how it can have a negative effect on law enforcement and investigations. EXPERT: Demonstrate a knowledge of a cypher and its’ key. 2. What are the features of a strong password? - 12 characters or more The greater the characters, the stronger the password - Mixture of capitals, lower case letters, numbers and symbols