Key Exchange We talk about symmetric keys here

Key Exchange • We talk about symmetric keys here • The problem is almost circular: • To establish an encrypted session, you need an encrypted means to exchange keys.

Key Exchange • Public Key cryptography can help ? ! • To see how, suppose S: (Sender) and R: (Receiver) want to derive a shared symmetric key, remember that S and R have their own keys and their each others public keys – S keys are (k. PR-S, k. PU-S) plus R’s public key – R keys are (k. PR-R, k. PU-R) plus S’s public key • Then, suppose that – S chooses any symmetric key K – S sends E(k. PR-S, K) to R – R takes S’s public key, removes the encryption, and obtains K • OOPS, any eavesdropper who can get S’s public key can also obtain K – let S send E(k. PU-R, K)to R. Then, only R can decrypt K • OOPS, R has no assurance that K came from S – The solution is for S to send to R: E(k. PU-R, E(k. PR-S, K))
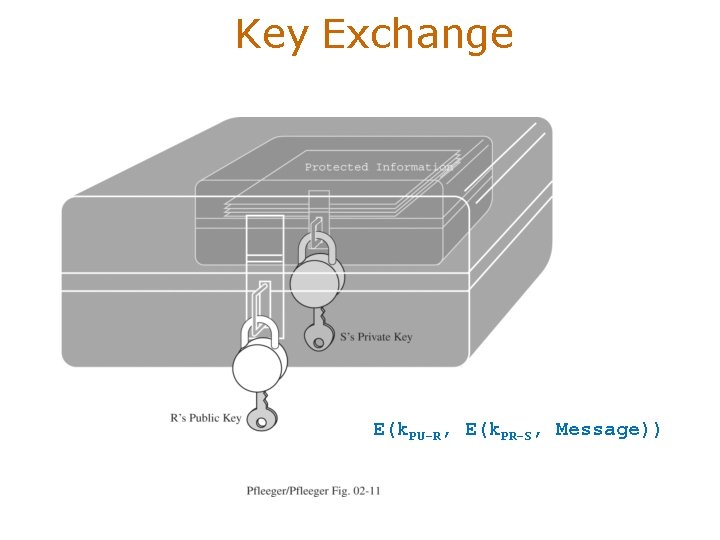
Key Exchange E(k. PU-R, E(k. PR-S, Message))

Digital Signatures

Electronic Record 1. Very easy to make copies 2. Very fast distribution 3. Easy archiving and retrieval 4. Copies are as good as original 5. Easily modifiable 6. Environmental Friendly Because of 4 & 5 together, these lack authenticity

Why Digital Signatures? • To provide Authenticity, Integrity and Non-repudiation to electronic Documents & Communicated Messages • To use the Internet as the safe and secure medium for e-Commerce and e-Governance
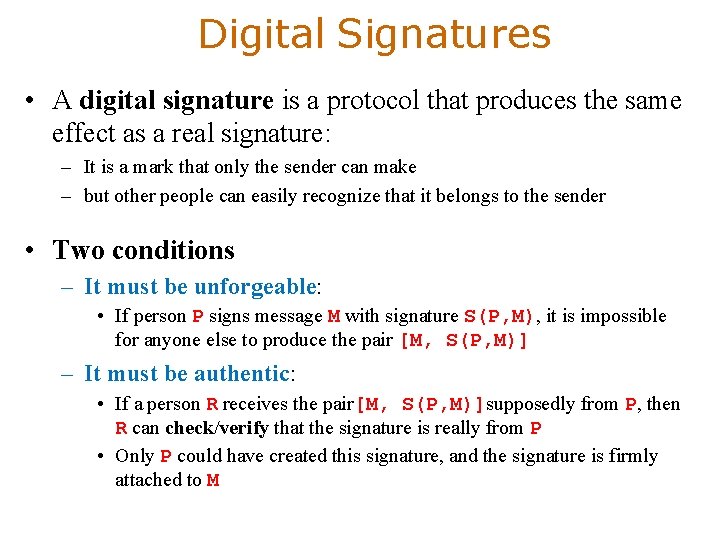
Digital Signatures • A digital signature is a protocol that produces the same effect as a real signature: – It is a mark that only the sender can make – but other people can easily recognize that it belongs to the sender • Two conditions – It must be unforgeable: • If person P signs message M with signature S(P, M), it is impossible for anyone else to produce the pair [M, S(P, M)] – It must be authentic: • If a person R receives the pair[M, S(P, M)]supposedly from P, then R can check/verify that the signature is really from P • Only P could have created this signature, and the signature is firmly attached to M
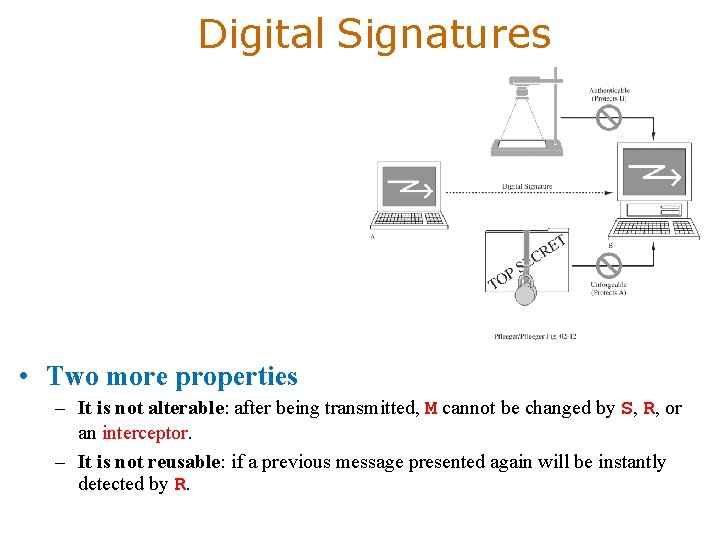
Digital Signatures • Two more properties – It is not alterable: after being transmitted, M cannot be changed by S, R, or an interceptor. – It is not reusable: if a previous message presented again will be instantly detected by R.

Digital Signatures I agree efcc 61 c 1 c 03 db 8 d 8 ea 8569545 c 073 c 814 a 0 ed 755 I am an Engineer. ea 0 ae 29 b 3 b 2 c 20 fc 018 aaca 45 c 3746 a 057 b 893 e 7 I am a Engineer. 01 f 1 d 8 abd 9 c 2 e 6130870842055 d 97 d 315 dff 1 ea 3 • These are digital signatures of the same person on different documents • Any message irrespective of its length can be compressed or shortened uniquely into a smaller length message called the Digest or the Hash. • Digital Signatures are numbers • They are document content dependent

What is Digital Signature? • Hash value of a message: • when encrypted with the private key of a person is his digital signature on that e-Document/Message – Digital Signature of a person therefore varies from document to document – thus ensuring authenticity of each word of that document. – As the public key of the signer is known, – anyone can verify the message and the digital signature

Digital Signatures Each individual generates his own key pair [Public key known to everyone & Private key only to the owner] Private Key – Used for making digital signature Public Key – Used to verify the digital signature
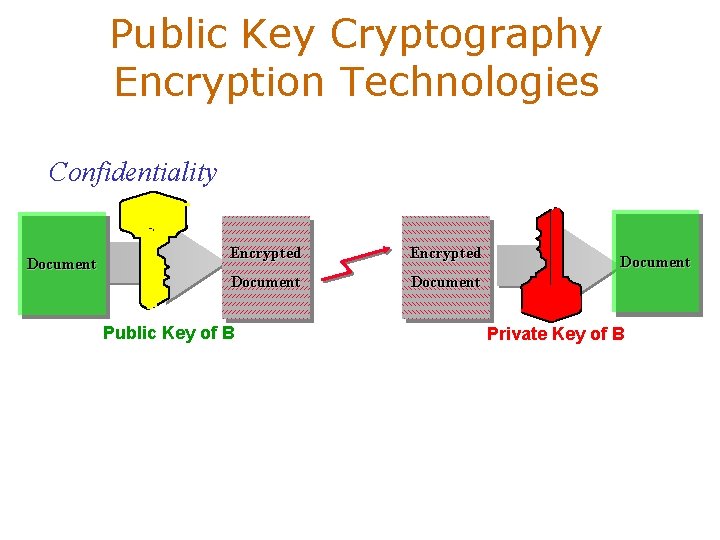
Public Key Cryptography Encryption Technologies Confidentiality Document Encrypted Document Public Key of B Document Private Key of B
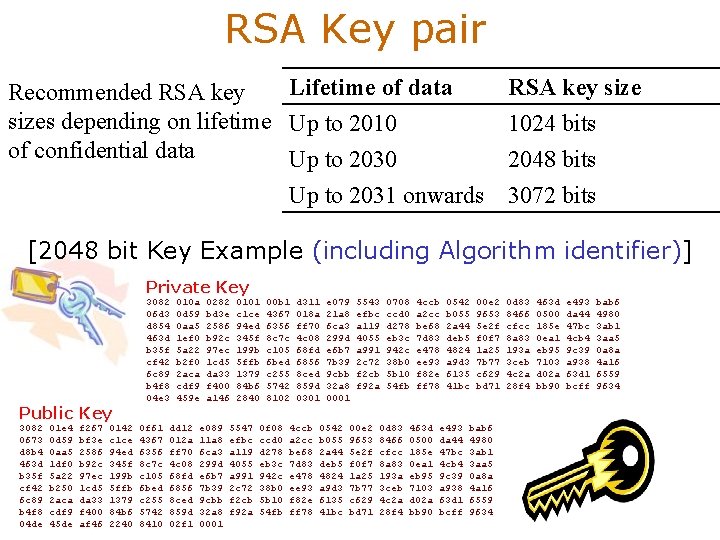
RSA Key pair Lifetime of data Recommended RSA key sizes depending on lifetime Up to 2010 of confidential data Up to 2030 Up to 2031 onwards RSA key size 1024 bits 2048 bits 3072 bits [2048 bit Key Example (including Algorithm identifier)] Private Key Public Key 3082 0673 d 8 b 4 463 d b 35 f cf 42 6 c 89 b 4 f 8 04 de 01 e 4 0 d 59 0 aa 5 1 df 0 5 a 22 b 250 2 aca cdf 9 45 de f 267 bf 3 e 2586 b 92 c 97 ec 1 cd 5 da 33 f 400 af 46 0142 c 1 ce 94 ed 345 f 199 b 5 ffb 1379 84 b 6 2240 3082 06 d 3 d 854 463 d b 35 f cf 42 6 c 89 b 4 f 8 04 e 3 0 f 61 4367 6356 8 c 7 c c 105 6 bed c 255 5742 8410 010 a 0 d 59 0 aa 5 1 ef 0 5 a 22 b 2 f 0 2 aca cdf 9 459 e dd 12 012 a ff 70 4 c 08 68 fd 6856 8 ced 859 d 02 f 1 0282 bd 3 e 2586 b 92 c 97 ec 1 cd 5 da 33 f 400 a 146 e 089 11 a 8 6 ca 3 299 d e 6 b 7 7 b 39 9 cbb 32 a 8 0001 0101 c 1 ce 94 ed 345 f 199 b 5 ffb 1379 84 b 6 2840 5547 efbc a 119 4055 a 991 2 c 72 f 2 cb f 92 a 00 b 1 4367 6356 8 c 7 c c 105 6 bed c 255 5742 8102 0 f 08 ccd 0 d 278 eb 3 c 942 c 38 b 0 5 b 10 54 fb d 311 018 a ff 70 4 c 08 68 fd 6856 8 ced 859 d 0301 4 ccb a 2 cc be 68 7 d 83 e 478 ee 93 f 82 e ff 78 e 079 21 a 8 6 ca 3 299 d e 6 b 7 7 b 39 9 cbb 32 a 8 0001 0542 b 055 2 a 44 deb 5 4824 a 9 d 3 6135 41 bc 5543 efbc a 119 4055 a 991 2 c 72 f 2 cb f 92 a 00 e 2 9653 5 e 2 f f 0 f 7 1 a 25 7 b 77 c 629 bd 71 0708 ccd 0 d 278 eb 3 c 942 c 38 b 0 5 b 10 54 fb 0 d 83 8466 cfcc 8 a 83 193 a 3 ceb 4 c 2 a 28 f 4 4 ccb a 2 cc be 68 7 d 83 e 478 ee 93 f 82 e ff 78 463 d 0500 185 e 0 ea 1 eb 95 7103 d 02 a bb 90 0542 b 055 2 a 44 deb 5 4824 a 9 d 3 6135 41 bc e 493 da 44 47 bc 4 cb 4 9 c 39 a 938 63 d 1 bcff 00 e 2 9653 5 e 2 f f 0 f 7 1 a 25 7 b 77 c 629 bd 71 bab 6 4980 3 ab 1 3 aa 5 0 a 8 a 4 a 16 6559 9634 0 d 83 8466 cfcc 8 a 83 193 a 3 ceb 4 c 2 a 28 f 4 463 d 0500 185 e 0 ea 1 eb 95 7103 d 02 a bb 90 e 493 da 44 47 bc 4 cb 4 9 c 39 a 938 63 d 1 bcff bab 6 4980 3 ab 1 3 aa 5 0 a 8 a 4 a 16 6559 9634
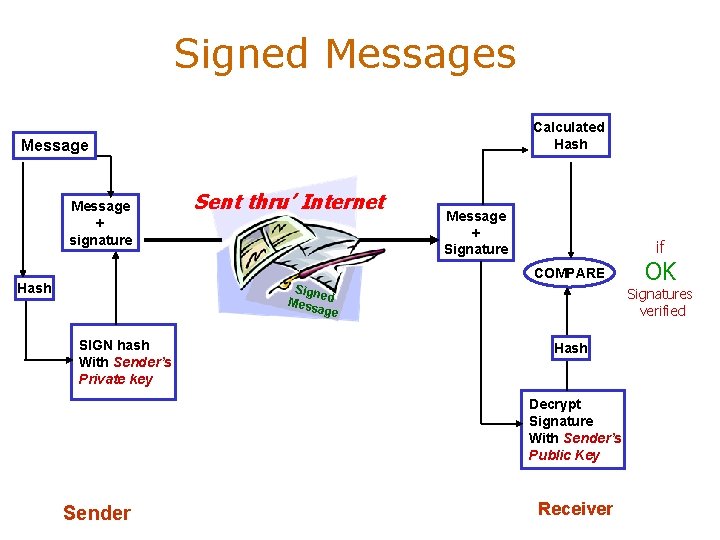
Signed Messages Calculated Hash Message + signature Sent thru’ Internet Message + Signature if COMPARE Hash Sign e Mess d age SIGN hash With Sender’s Private key Signatures verified Hash Decrypt Signature With Sender’s Public Key Sender OK Receiver
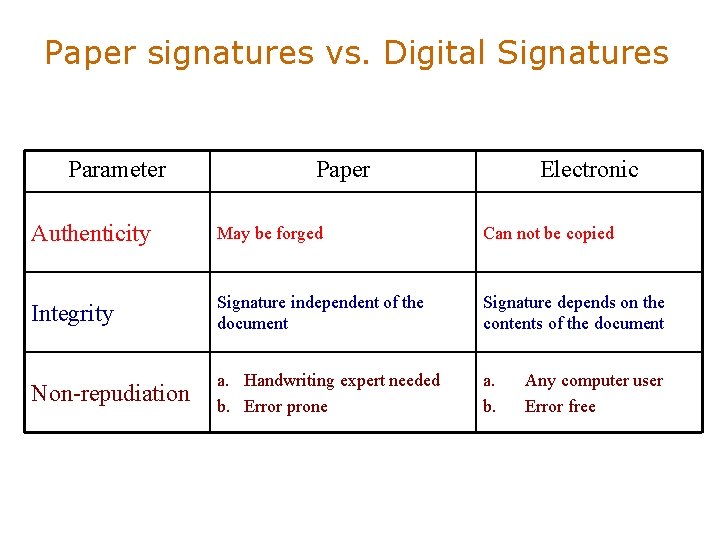
Paper signatures vs. Digital Signatures Parameter Paper Electronic Authenticity May be forged Can not be copied Integrity Signature independent of the document Signature depends on the contents of the document Non-repudiation a. Handwriting expert needed b. Error prone a. b. Any computer user Error free

Private Key Protection • The Private key generated is to be protected and kept secret. – The responsibility of the secrecy of the key lies with the owner. • The key is secured using – PIN Protected soft token – Smart Cards – Hardware Tokens

PIN protected soft tokens • The Private key is encrypted and kept on the Hard Disk in a file, this file is password protected. • This forms the lowest level of security in protecting the key, as – The key is highly reachable. – PIN can be easily known or cracked. • Soft tokens are also not preferred because – The key becomes static and machine dependent. – The key is in known file format.

Smart Cards • The Private key is generated in the crypto module residing in the smart card. • The key is kept in the memory of the smart card. • The key is highly secured as it doesn’t leave the card, the message digest is sent inside the card for signing, and the signatures leave the card. • The card gives mobility to the key and signing can be done on any system. (Having smart card reader)

Hardware Tokens • They are similar to smart cards in functionality as – – • Key is generated inside the token. Key is highly secured as it doesn’t leave the token. Highly portable. Machine Independent. i. KEY is one of the most commonly used token as it doesn’t need a special reader and can be connected to the system using USB port.
Hardware Tokens i. Key Biometrics – adds another level of security to these tokens Smart Card

Public Key Deception • Impostor/Deceiver Claims to be a True Party – True party has a public and private key – Impostor/Deceiver also has a public and private key • Impostor sends impostor’s own public key to the verifier – Says, “This is the true party’s public key” – This is the critical step in the deception
Public Key Deception • If verifier accepts the impostor’s public key as the true party’s public key, – Impostor will be authenticated through any public key authentication method, because their private key will work – Impostor can also decrypt messages sent by the verifier if these messages are encrypted with the impostor’s public key

Public Key Deception • Moral: – Public key encryption for privacy, confidentiality, authentication, and message integrity only works if • The verifier gets the true party’s public key independently of the applicant, • From a trusted third party
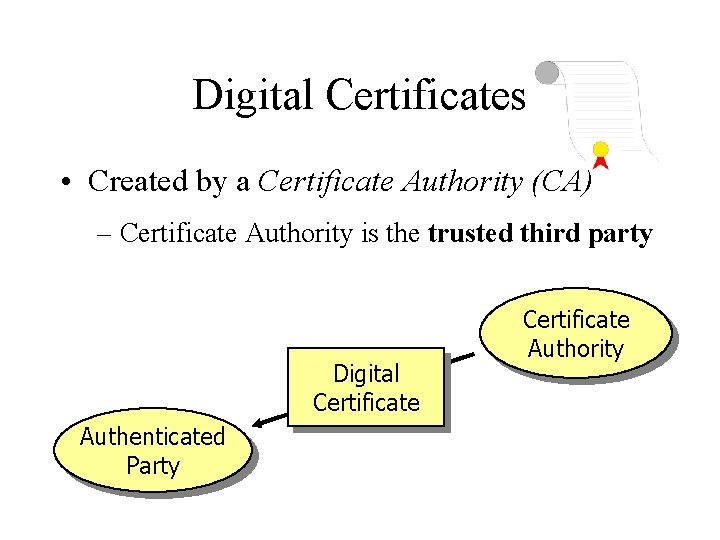
Digital Certificates • Created by a Certificate Authority (CA) – Certificate Authority is the trusted third party Digital Certificate Authenticated Party Certificate Authority

Public Key Infrastructure (PKI) • Some Trusted Agency is required which certifies the association of an individual with the key pair. Certifying Authority (CA) • This association is done by issuing a certificate to the user by the CA Public Key Certificate (PKC) • All public key certificates are digitally signed by the CA

Digital Certificates § A public key and user's identity are bound together in a certificate, which is then signed by someone called a Certificate Authority (CA) § Certifying the accuracy of the binding. § The algorithms to generate a matched pair of public and private keys are publicly known, and software that does it is widely available. § So if Alice wanted to use a public key cipher, she could generate her own pair of public and private keys, § keep the private key hidden, and publicize the public key. § But how can she publicize her public key— assert that it belongs to her—in such a way that other participants can be sure it really belongs to her?

Digital Certificates • A complete scheme for certifying bindings between public keys and identities— what key belongs to who—is called a Public Key Infrastructure (PKI). • A PKI starts with the ability to verify identities and bind them to keys out of band. By “out of band, ” we mean something outside the network and the computers that comprise it, such as in the following scenarios. • Himmm, if Alice and Bob are individuals who know each other, then they could get together in the same room and Alice could give her public key to Bob directly, perhaps on a business card. • If Bob is an organization, Alice the individual could present conventional identification, perhaps involving a photograph or fingerprints. • If Alice and Bob are computers owned by the same company, then a system administrator could configure Bob with Alice’s public key. • A digitally signed statement of a public key binding is called a public key certificate, or simply a Certificate

Digital Certificates • One of the major standards for certificates is known as X. 509. This standard leaves a lot of details open, but specifies a basic structure. • A certificate clearly must include: – – – the identity of the entity being certified the public key of the entity being certified the identity of the signer the digital signature algorithm identifier • (which cryptographic hash and which cipher)
Certificates: Paper vs. Electronic Paper Electronic

Certificate Authorities • Unfortunately, certificate authorities are not regulated • You must only use certificate authorities you trust • Company can be its own certificate authority for internal authentication among its hardware and software systems

Certification Authorities • A certification authority or certificate authority (CA) is an entity claimed (by someone) to be trustworthy for verifying identities and issuing public key certificates. • There are commercial CAs, governmental CAs, and even free CAs. • To use a CA, you must know its own key. You can learn that CA’s key, however, if you can obtain a chain of CA-signed certificates that starts with a CA whose key you already know. • Then you can believe any certificate signed by that new CA

Certifying Authority • Must be widely known and trusted • Must have well defined Identification process before issuing the certificate • Provides online access to all the certificates issued • Provides online access to the list of certificates revoked • Displays online the license issued by the Controller • Displays online approved Certification Practice Statement (CPS) • Must adhere to IT Act/Rules/Regulations and Guidelines
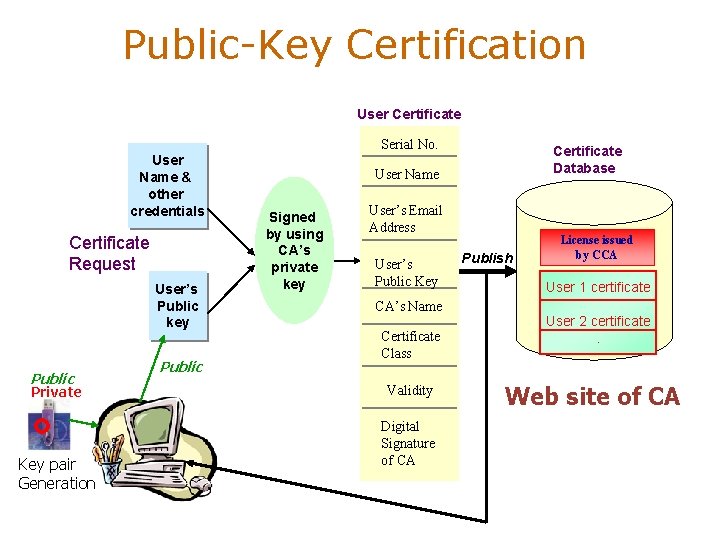
Public-Key Certification User Certificate Serial No. User Name & other credentials Certificate Request User’s Public key Public Private Key pair Generation Public Certificate Database User Name Signed by using CA’s private key User’s Email Address User’s Public Key CA’s Name Certificate Class Validity Digital Signature of CA Publish License issued by CCA User 1 certificate User 2 certificate. Web site of CA

Digital Certificates • Each digital certificate has its own digital signature, signed (encrypted) by the private key of the certificate authority – Provides message integrity so that an impostor cannot change the name field in the digital certificate to its own

Digital Certificates • Certificate authorities may revoke digital certificates before the expiration date listed in the digital certificate – Revoked certificate ID numbers are placed in a Certificate Revocation List (CRL) – Verifier must check with the certificate authority to determine if a digital certificate is on the CRL • Without the CRL check, digital certificates do not support authentication

Digital Certificates • Recap – A digital signature gives the public key of a named party – This is needed for public key authentication, to prevent public key deception – However, a digital certificate alone does NOT provide authentication

Public Key Infrastructures (PKIs) Private key creation and distribution Digital certificate creation and distribution Certificate Revocation List checking
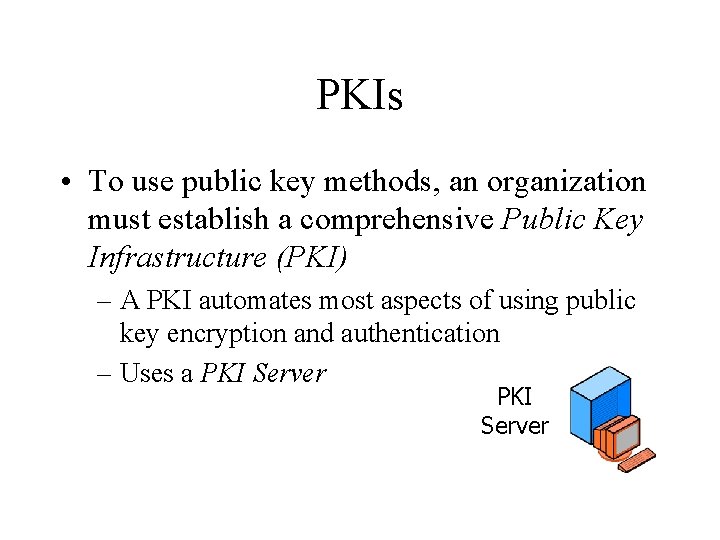
PKIs • To use public key methods, an organization must establish a comprehensive Public Key Infrastructure (PKI) – A PKI automates most aspects of using public key encryption and authentication – Uses a PKI Server
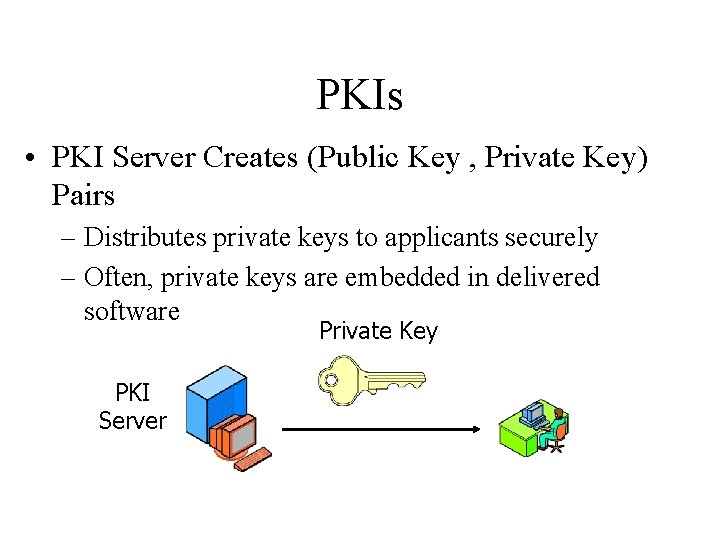
PKIs • PKI Server Creates (Public Key , Private Key) Pairs – Distributes private keys to applicants securely – Often, private keys are embedded in delivered software Private Key PKI Server
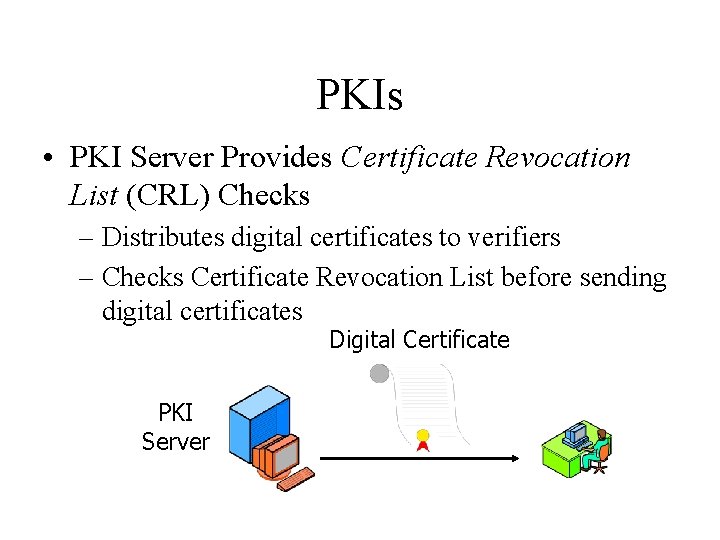
PKIs • PKI Server Provides Certificate Revocation List (CRL) Checks – Distributes digital certificates to verifiers – Checks Certificate Revocation List before sending digital certificates Digital Certificate PKI Server
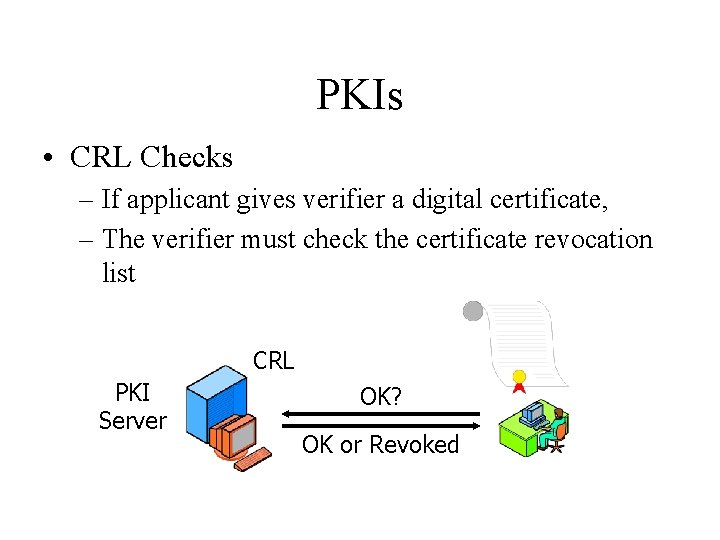
PKIs • CRL Checks – If applicant gives verifier a digital certificate, – The verifier must check the certificate revocation list CRL PKI Server OK? OK or Revoked

• Role of controller • Controller of Certifying Authorities as the “Root” Authority certifies the technologies, infrastructure and practices of all the Certifying Authorities licensed to issue Digital Signature Certificates

Summary • Each individual has a pair of keys • Public key of each individual is certified by a CA (Certifying Authority) • Public keys of CAs are certified by the Controller • Public key of the Controller is self certified • Public keys of everyone are known to all concerned and are also available on the web • Certification Practice Statement is displayed on the web site
![• Key Generation – True Random Numbers – RSA Key Pair [Private/Public Key] • Key Generation – True Random Numbers – RSA Key Pair [Private/Public Key]](http://slidetodoc.com/presentation_image_h2/5ba8f50c955722d433dddb5cdf086554/image-44.jpg)
• Key Generation – True Random Numbers – RSA Key Pair [Private/Public Key] • i. e. 128 -bits for symmetric key algorithms • i. e. at least 2048 -bits for public-key algorithms. • Digital Signature – Generate Message Digest [i. e. SHA 1] – Encrypting Digest using Private Key [Signatures] – Attaching the Signatures to the message. • Verification of Signatures – Run the test for Authentication, Integrity and Non-repudiation. • Digital Signature Certificate – i. e. ITU X. 509 v 3 – A digital certificate is necessary for a digital signature because it provides the public key that can be used to validate the private key that is associated with a digital signature. – Digital certificates make it possible for digital signatures to be used as a way to authenticate digital information.
- Slides: 44