Keamanan Sistem CS 4633 Information Security Controls Pertemuan




























- Slides: 32

Keamanan Sistem (CS 4633). . : : Information Security Controls : Pertemuan #8 05/10/2006 Fazmah Arif Yulianto 1

Types of Inf_Sec Controls • Physical • Technical (logical) • Administrative (personnel) • • • Preventive Detective Deterrent Corrective Recovery 2

Terminologies • Preventive controls attempt to avoid the occurrence of unwanted events • Detective controls attempt to identify unwanted events after they have occurred • Deterrent controls are intended to discourage individuals from intentionally violating information security policies or procedures • Corrective controls either remedy the circumstances that allowed the unauthorized activity or return conditions to what they were before the violation • Recovery controls restore lost computing resources or capabilities and help the organization recover monetary losses caused by a security violation 3

Physical Controls: Preventive • To prevent unauthorized personnel from entering computing facilities (i. e. , locations housing computing resources, supporting utilities, computer hard copy, and input data media) and to help protect against natural disasters. • Examples of these controls include: – – – Backup files and documentation, backup power Fences, Security guards, Badge systems. Double door systems, Locks and keys, Biometric access controls. Site selection. Fire extinguishers etc. 4

Physical Controls: Detective • Warn protective services personnel that physical security measures are being violated. • Examples of these controls include: – Motion detectors. – Smoke and fire detectors. – Closed-circuit television monitors. – Sensors and alarms etc. 5

Some types of Physical Security • Barriers: walls, fences, doors, gates etc. – Q: Who or what is the barrier intended to stop, and for how long? • Locks: day access locks, after-hours locks, emergency egress locks – Mechanical / electrical – door control system = authentication + door locking devices – Lock vs lockpicking • Alarms: primarily for letting us know if control is functioning properly — that is, has it been breached? – Q: who and what is it supposed to detect, and what is 6 the intended response?

Physical Security (cont’d) • Lights and cameras: best suited for assessing a situation — a tool to extend the eyes (and sometimes ears) of the guard force. – A common misuse of cameras is assuming that they will detect an intruder • Antitheft, Antitamper, and Inventory Controls – Antitamper devices control access to ensure the integrity of the protected asset – Antitheft devices and inventory controls are intended to limit movement to a confined area • … 7

Backup Files and Documentation • Backup files should be stored far enough away from the active data or documentation to avoid destruction by the same incident that destroyed the original. • Backup material should be stored in a secure location constructed of noncombustible materials, including twohour rated fire walls. • Backups of sensitive information should have the same level of protection as the active files of this information 8

Backup Power • Backup power is necessary to ensure that computer services are in a constant state of readiness and to help avoid damage to equipment if normal power is lost. • For short periods of power loss, backup power is usually provided by batteries. • In areas susceptible to outages of more than 15– 30 min. , diesel generators are usually recommended. 9

Fire extinguisher • Automatic water sprinkler: beware of the risk of water damage to computing equipments • Carbon dioxide extinguishing systems were developed: save for equipments, lethal for human • Halon extinguisher: usually harmless to equipment and less dangerous to personnel than carbon dioxide. – At a concentration of about 10%, Halon extinguishes fire and can be safely breathed by humans – High cost 10

Biometric Access Controls • Biometrics used for identification include fingerprints, handprints, voice patterns, signature samples, and retinal scans. • Because biometrics cannot be lost, stolen, or shared, they provide a higher level of security than badges. • Biometric identification is recommended for high-security, low-traffic entrance control. 11

More on biometrics • Every person has unique physiological, behavioral, and morphological characteristics that can be examined and quantified. • Biometrics is the use of these characteristics to provide positive personal identification. 12

Some Biometric Performances • Fingerprint Scan: False rejection rate = 9. 4%; False acceptance rate = 0; Average processing time = 7 seconds • Retinal scan: FRR = 1. 5%; FAR = 1. 5%; APT = 7 seconds • Palm scan: FRR = 0; FAR = 0. 00025%; APT = 2 -3 seconds • Hand geometry: FRR = 0. 1%; FAR = 0. 1%; ATP = 2 to 3 seconds • Facial recognition: ATP = 2 seconds • Voice verification: FRR = 8. 2%; FAR = 0. 4%; ATP = 2 to 3 seconds 13

14

A basic role of physical security to keep unwanted people / things out, and to keep “insiders” honest 15

Technical Controls: Preventive • To prevent unauthorized personnel or programs from gaining remote access to computing resources. • Examples of these controls include: – – – – Access control software. Antivirus software. Library control systems. Passwords. Smart cards. Encryption. Dial-up access control and callback systems. etc. 16

Technical Controls: Detective • Warn personnel of violations or attempted violations of preventive technical controls. • Examples of these include: – Audit trails – Intrusion detection expert systems 17

Access Control Software • To control sharing of data and programs between users. • In many computer systems, access to data and programs is implemented by access control lists that designate which users are allowed access. • Access control software provides the ability to control access to the system by establishing that only registered users with an authorized log-on ID and password can gain access to the computer system. • After access to the system has been granted, the next step is to control access to the data and programs residing in the system. • The data or program owner can establish rules that designate who is authorized to use the data or program 18

Access Controls • One among central issues in security • Specify what users can do, what resources they can access, and what operations they can perform on a system • The effectiveness of access control rests on the proper user authentication and on the correctness of the authorizations 19

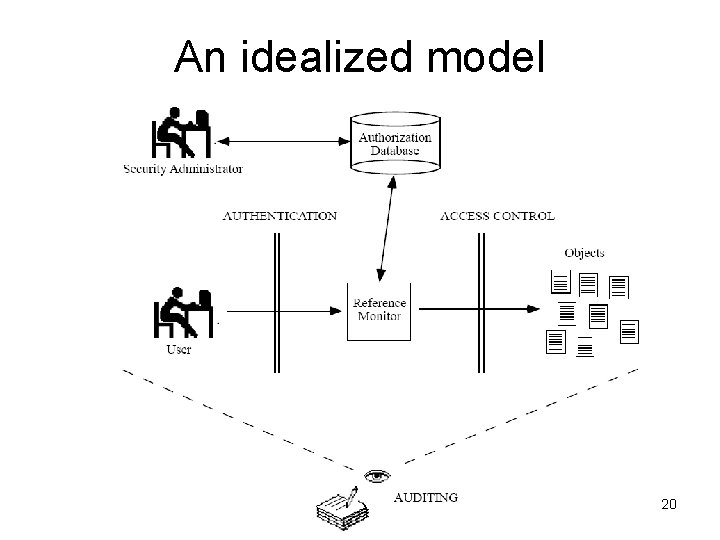
An idealized model 20

Audit Control • Concern a posteriori analysis of all the request and activities of users in the system requires logging • Useful as/to: – Deterrent/pencegah – Find out about possible attempted or actual violations – Determining possible flaws in the system – Hold users accountable for their actions 21

Control over access • More security is not necessarily less access. That is, controlled access does not equal denied access • Practically all controls fall somewhere in between providing complete access and total denial. Thus, it is the level of control over access — not the amount of access — that provides security. 22

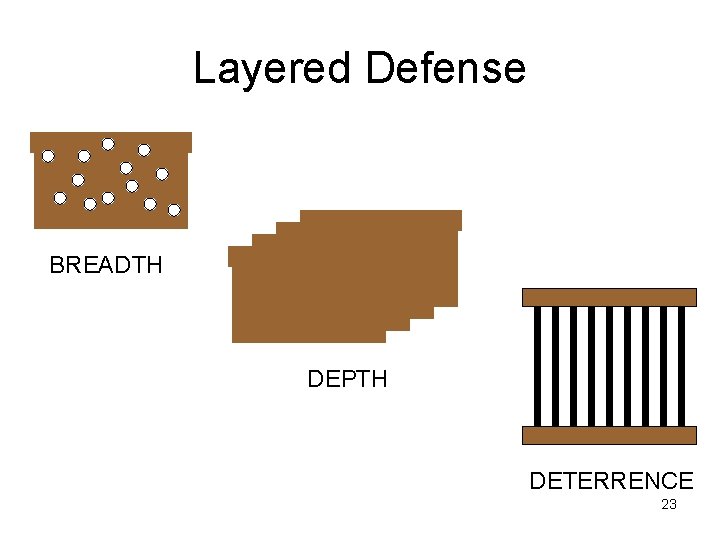
Layered Defense BREADTH DEPTH DETERRENCE 23

Layered Defense: Breadth A single type of control rarely eliminates all vulnerabilities – suppose one decides to control read access to data by using a log-on password. But the log-on password does not afford protection if one sends the data over the Internet. A different type of control (i. e. , encryption) would therefore provide the additional coverage needed. 24

Layered Defense: Depth • To be realistic with security, one must believe in failure Any given control is not perfect and will fail, sooner or later. • Adds layers of additional access controls as a backstop measure. • Example: The password will not stay secret forever embrace the common dictum, “something you have, something you know, and something you are. ” (password, smartcard, fingerprint) 25

Layered Defense: Deterrence • Simply putting enough controls in place that the cost or feasibility of defeating them without getting caught is more than the prize is worth. • Examples: surveillance cameras, activity logging 26

Password • Passwords are used to verify that the user of an ID is the owner of the ID. • Fixed passwords that are used for a defined period of time are often easy for hackers to compromise • Choosing ‘good’ passwords? • One-time password: – Time-synchronized type – Challenge type 27

28

Administrative Controls: Preventive • Personnel-oriented techniques for controlling people’s behavior to ensure the confidentiality, integrity, and availability of computing data and programs. • Examples of preventive administrative controls include: – – – – Security awareness and technical training. Separation of duties. Procedures for recruiting and terminating employees. Security policies and procedures. Supervision. Disaster recovery, contingency, and emergency plans. User registration for computer access. 29

Administrative Controls: Detective • To determine how well security policies and procedures are complied with, to detect fraud, and to avoid employing persons that represent an unacceptable security risk. • This type of control includes: – – – Security reviews and audits. Performance evaluations. Required vacations. Background investigations. Rotation of duties 30

31

References • Harold F. Tipton, Types of Information Security Controls, Information Security Management Handbook, 5 th ed. , Harold F. Tipton & Micki Krause (editor), 2004, pp. 113 -135 • Ravi S. Sandhu & Pierangela Samarati, Access Control: Principles and Practice 32
 General controls vs application controls
General controls vs application controls He who controls the past controls the future
He who controls the past controls the future Private security
Private security Physical security adalah
Physical security adalah Security hole adalah salah satu faktor evaluasi keamanan
Security hole adalah salah satu faktor evaluasi keamanan Visa international security model
Visa international security model Information security
Information security Cissp control types
Cissp control types Critical security controls framework
Critical security controls framework Paranoid policy
Paranoid policy Latar belakang sistem operasi
Latar belakang sistem operasi Ancaman keamanan sistem informasi
Ancaman keamanan sistem informasi Jenis ancaman sistem keamanan komputer
Jenis ancaman sistem keamanan komputer Sistem keamanan pintu menggunakan sidik jari
Sistem keamanan pintu menggunakan sidik jari Peta konsep jaringan komputer
Peta konsep jaringan komputer Mata kuliah keamanan sistem informasi
Mata kuliah keamanan sistem informasi Peta konsep peralatan kantor
Peta konsep peralatan kantor Keamanan sistem operasi windows
Keamanan sistem operasi windows Materi keamanan komputer
Materi keamanan komputer Mengapa keamanan sistem informasi diperlukan
Mengapa keamanan sistem informasi diperlukan Mata kuliah keamanan sistem informasi
Mata kuliah keamanan sistem informasi Tugas pertemuan 9 metode perancangan program
Tugas pertemuan 9 metode perancangan program Definition
Definition 4 pendekatan pendidikan multikultural
4 pendekatan pendidikan multikultural Pertemuan multikultural
Pertemuan multikultural Denah ruang pertemuan
Denah ruang pertemuan Majas pleonasme adalah
Majas pleonasme adalah Creat by
Creat by Pada pertemuan kali ini kita
Pada pertemuan kali ini kita Pertemuan ini
Pertemuan ini Pertemuan 9
Pertemuan 9 Pertemuan awal pkh adalah
Pertemuan awal pkh adalah Dari gambar ini notasi infix yang dihasilkan adalah
Dari gambar ini notasi infix yang dihasilkan adalah