Juniper SoftwareDefined Secure Network Haitham Saif Market Situation



- Slides: 9

Juniper Software-Defined Secure Network Haitham Saif

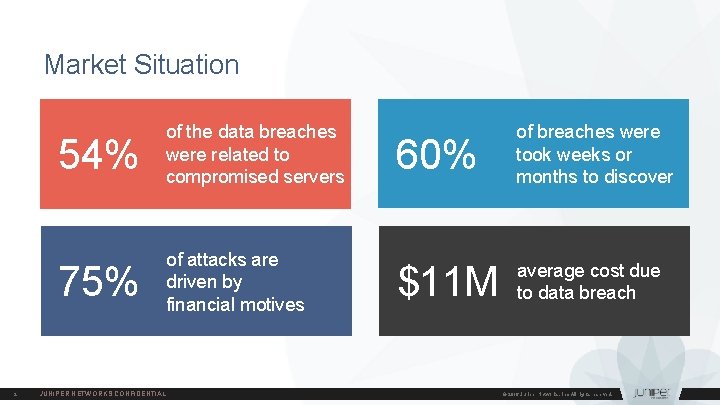
Market Situation 2 54% of the data breaches were related to compromised servers 60% of breaches were took weeks or months to discover 75% of attacks are driven by financial motives $11 M average cost due to data breach JUNIPER NETWORKS CONFIDENTIAL © 2016 Juniper Networks, Inc. All rights reserved.

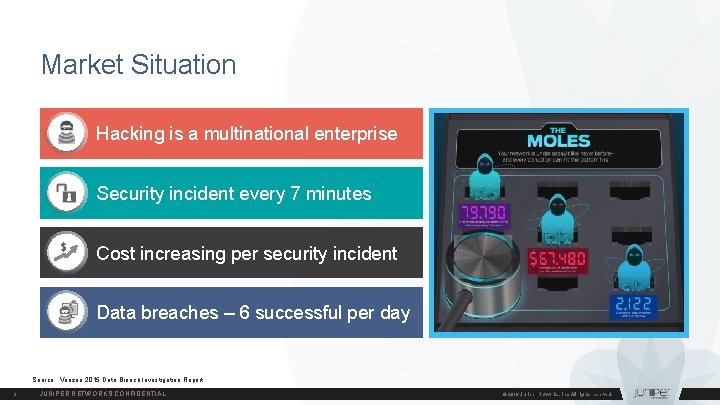
Market Situation Hacking is a multinational enterprise Security incident every 7 minutes $ Cost increasing per security incident Data breaches – 6 successful per day Source: Verizon 2015 Data Breach Investigation Report. 3 JUNIPER NETWORKS CONFIDENTIAL © 2016 Juniper Networks, Inc. All rights reserved.

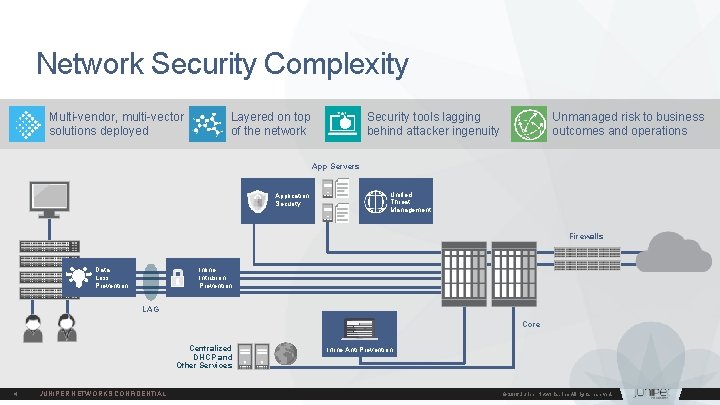
Network Security Complexity Multi-vendor, multi-vector solutions deployed Layered on top of the network Security tools lagging behind attacker ingenuity Unmanaged risk to business outcomes and operations App Servers Application Security Unified Threat Management Firewalls Data Loss Prevention Inline Intrusion Prevention LAG Core Centralized DHCP and Other Services 4 JUNIPER NETWORKS CONFIDENTIAL Inline Anti Prevention © 2016 Juniper Networks, Inc. All rights reserved.

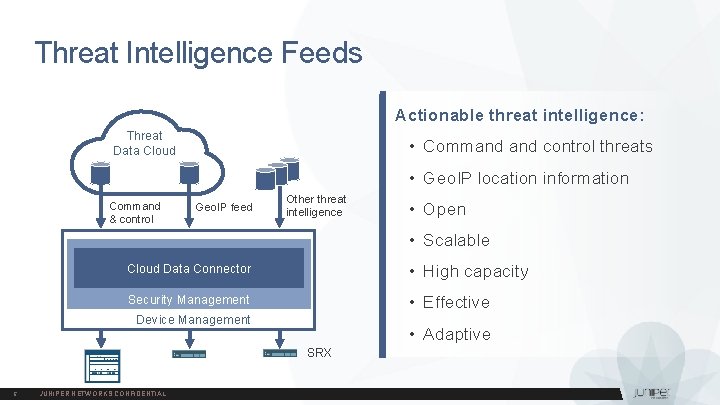
Threat Intelligence Feeds Actionable threat intelligence: Threat Data Cloud • Command control threats • Geo. IP location information Command & control Geo. IP feed Other threat intelligence • Open • Scalable Cloud Data Connector • High capacity Security Management • Effective Device Management • Adaptive SRX 5 JUNIPER NETWORKS CONFIDENTIAL

A Change in Mindset Realize threats are everywhere. They are already inside. They walked in your front door Recognize perimeter security isn’t enough Detection and Enforcement should be enabled anywhere Acknowledge security is everyone’s problem – horizontal and vertical 6 Copyright © 2014 Juniper Networks, Inc.

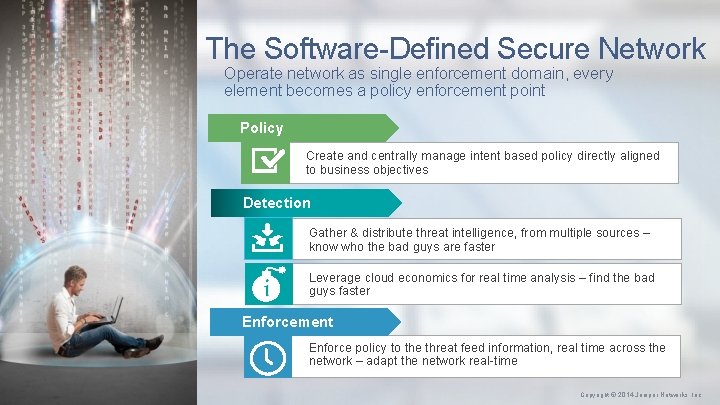
The Software-Defined Secure Network Operate network as single enforcement domain, every element becomes a policy enforcement point Policy Create and centrally manage intent based policy directly aligned to business objectives Detection Gather & distribute threat intelligence, from multiple sources – know who the bad guys are faster Leverage cloud economics for real time analysis – find the bad guys faster Enforcement Enforce policy to the threat feed information, real time across the network – adapt the network real-time 7 Copyright © 2014 Juniper Networks, Inc.

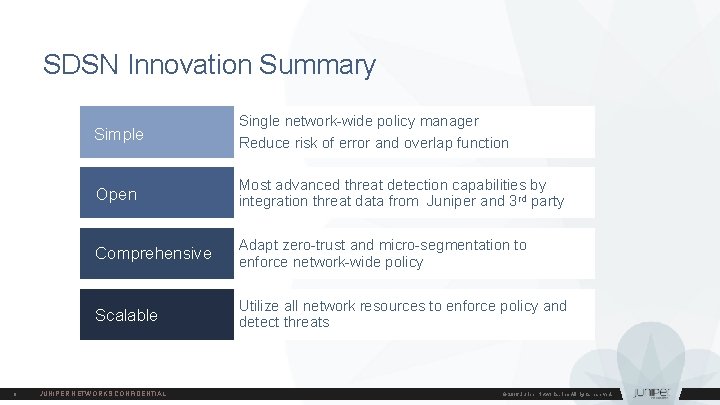
SDSN Innovation Summary 8 Simple Single network-wide policy manager Reduce risk of error and overlap function Open Most advanced threat detection capabilities by integration threat data from Juniper and 3 rd party Comprehensive Adapt zero-trust and micro-segmentation to enforce network-wide policy Scalable Utilize all network resources to enforce policy and detect threats JUNIPER NETWORKS CONFIDENTIAL © 2016 Juniper Networks, Inc. All rights reserved.

Thank you