John W Lainhart IV CISA CISM CGEIT CIPPG


































- Slides: 77

John W. Lainhart IV CISA, CISM, CGEIT, CIPP/G Partner, Security, Privacy, Wireless & IT Governance IBM Global Business Services Principal Advisory to IT Governance Institute john. w. lainhart@us. ibm. com 301 -803 -2745 COBIT® as a Risk Management Framework

In This Presentation. . . The Governance Environment An introduction to IT Governance An introduction to Control Objectives for Information and related Technology (COBIT®) Overview of COBIT® Supporting Materials COBIT® Mappings to Other Standards An introduction to Val. IT™ An introduction to Risk. IT™ Recently Announced Certification Program – CGEIT Questions

IT Governance, COBIT, Val. IT and Risk. IT Are Brought to You by …

IT Governance Institute is a non-profit research think-tank associated with ISACA®

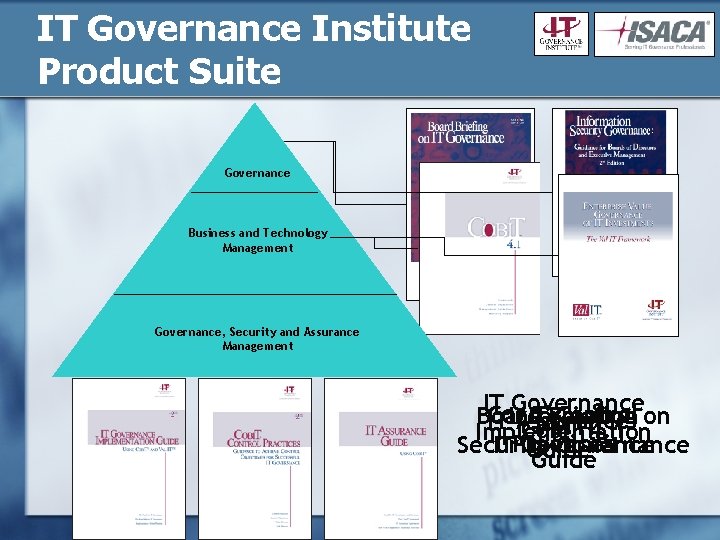
IT Governance Institute Product Suite Governance Business and Technology Management Governance, Security and Assurance Management IT Governance C OBI T Control Board Information Briefing on IT Assurance Val IT COBIT 4. 1 Implementation Practices Security IT Governance Guide

The Governance Environment

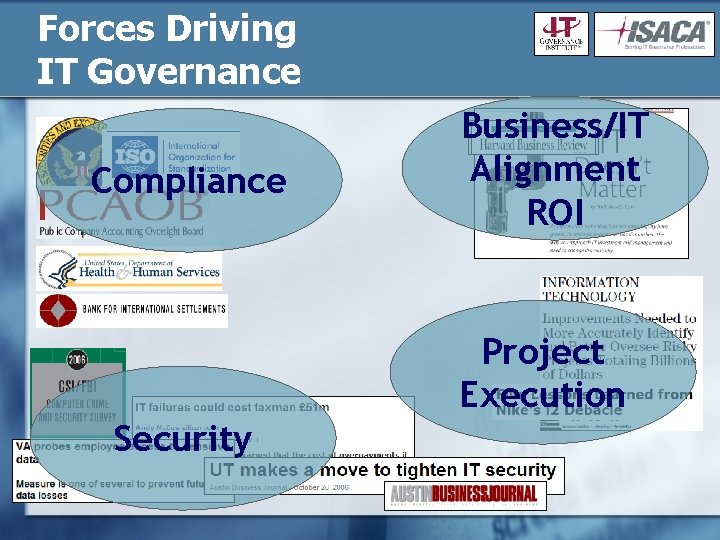
Forces Driving IT Governance Compliance Business/IT Alignment ROI Project Execution Security

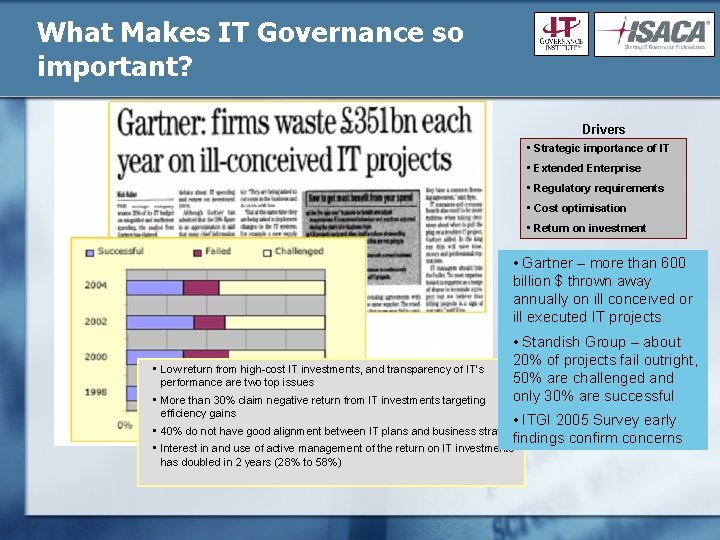
What Makes IT Governance so important? Drivers • Strategic importance of IT • Extended Enterprise • Regulatory requirements • Cost optimisation • Return on investment • Gartner – more than 600 billion $ thrown away annually on ill conceived or ill executed IT projects • Low return from high-cost IT investments, and transparency of IT’s performance are two top issues • More than 30% claim negative return from IT investments targeting efficiency gains • Standish Group – about 20% of projects fail outright, 50% are challenged and only 30% are successful • ITGI 2005 Survey early findings confirm concerns • 40% do not have good alignment between IT plans and business strategy • Interest in and use of active management of the return on IT investments has doubled in 2 years (28% to 58%)

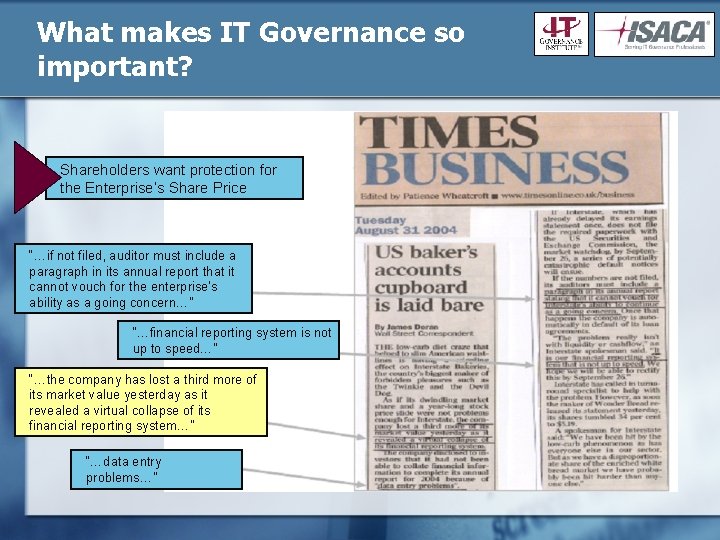
What makes IT Governance so important? Shareholders want protection for the Enterprise’s Share Price “…if not filed, auditor must include a paragraph in its annual report that it cannot vouch for the enterprise’s ability as a going concern…” “…financial reporting system is not up to speed…” “…the company has lost a third more of its market value yesterday as it revealed a virtual collapse of its financial reporting system…” “…data entry problems…”

Global Business Services The Premier IT Leaders polled by Computer. World Magazine put these projects at the top of their to-do lists for 2008 # 1 on this list is IT Governance, including business alignment From the Dec 10, 2007 issue of Computerworld Magazine (pg 74) Computerworld Magazine is a publication of International Data Group Inc. IBM Confidential| © Copyright IBM Corporation 2005

An Overview of IT Governance

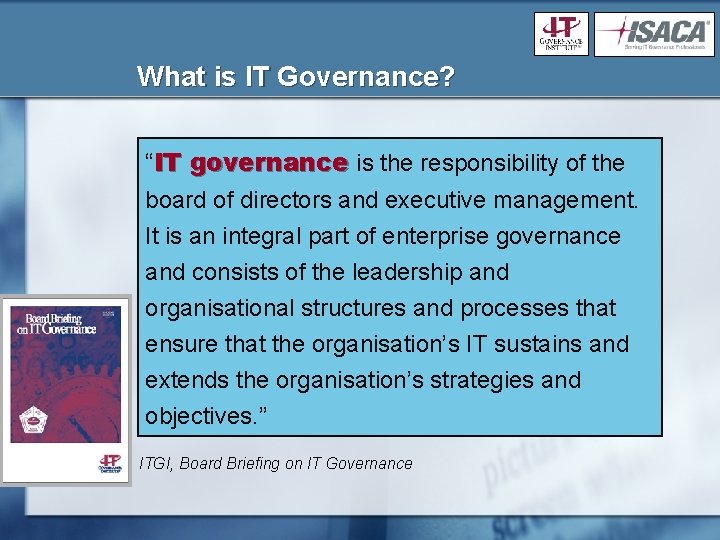
What is IT Governance? “IT governance is the responsibility of the board of directors and executive management. It is an integral part of enterprise governance and consists of the leadership and organisational structures and processes that ensure that the organisation’s IT sustains and extends the organisation’s strategies and objectives. ” ITGI, Board Briefing on IT Governance

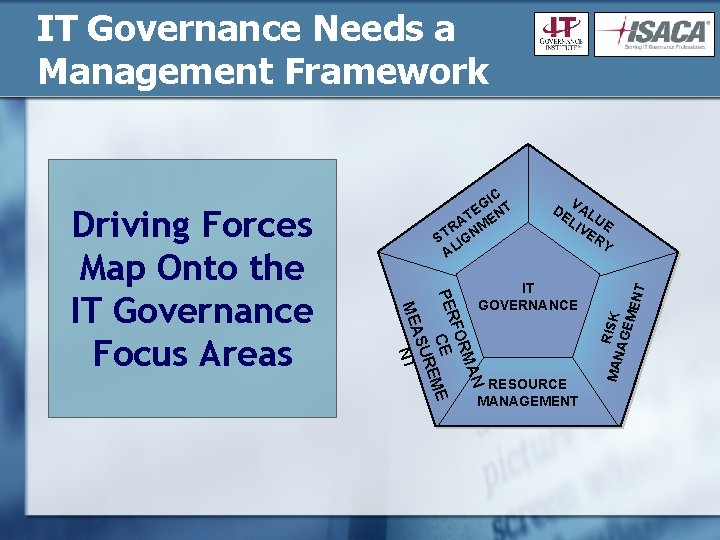
IT Governance Needs a Management Framework MAN RISK AGE MEN RESOURCE MANAGEMENT T V DE AL LI UE VE RY IT GOVERNANCE N MA FOR PER E C E REM ASU ME NT Driving Forces Map Onto the IT Governance Focus Areas C GI T EN A M R ST IGN AL

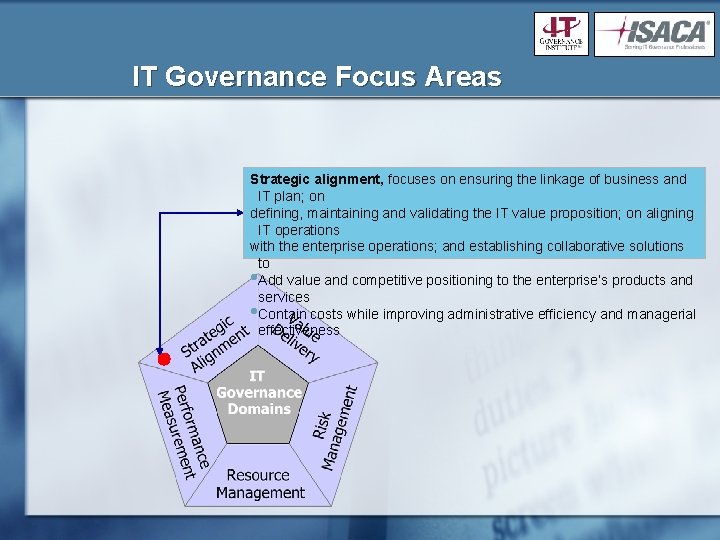
IT Governance Focus Areas Strategic alignment, focuses on ensuring the linkage of business and IT plan; on defining, maintaining and validating the IT value proposition; on aligning IT operations with the enterprise operations; and establishing collaborative solutions to Add value and competitive positioning to the enterprise’s products and services Contain costs while improving administrative efficiency and managerial effectiveness • •

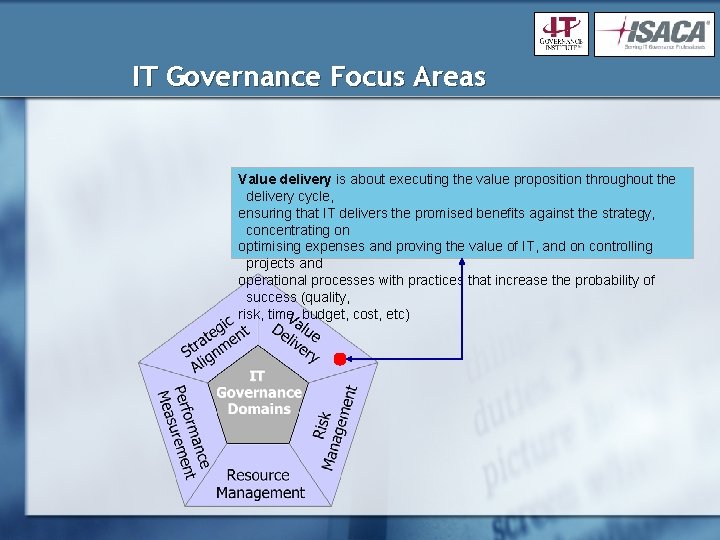
IT Governance Focus Areas Value delivery is about executing the value proposition throughout the delivery cycle, ensuring that IT delivers the promised benefits against the strategy, concentrating on optimising expenses and proving the value of IT, and on controlling projects and operational processes with practices that increase the probability of success (quality, risk, time, budget, cost, etc)

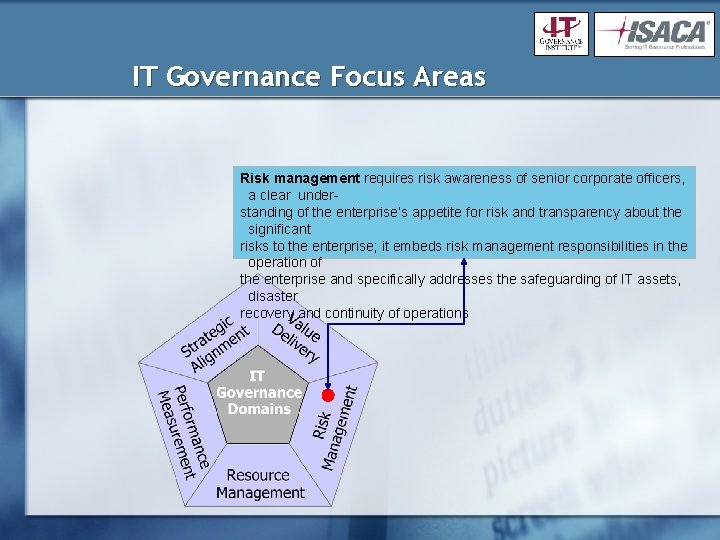
IT Governance Focus Areas Risk management requires risk awareness of senior corporate officers, a clear understanding of the enterprise’s appetite for risk and transparency about the significant risks to the enterprise; it embeds risk management responsibilities in the operation of the enterprise and specifically addresses the safeguarding of IT assets, disaster recovery and continuity of operations

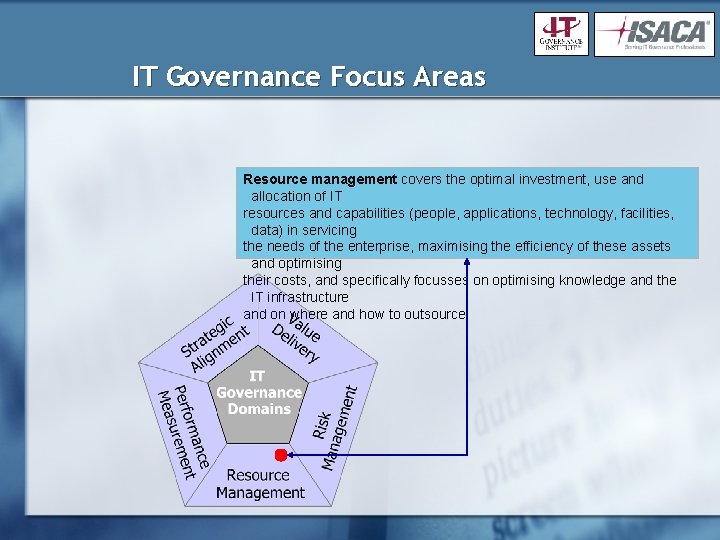
IT Governance Focus Areas Resource management covers the optimal investment, use and allocation of IT resources and capabilities (people, applications, technology, facilities, data) in servicing the needs of the enterprise, maximising the efficiency of these assets and optimising their costs, and specifically focusses on optimising knowledge and the IT infrastructure and on where and how to outsource

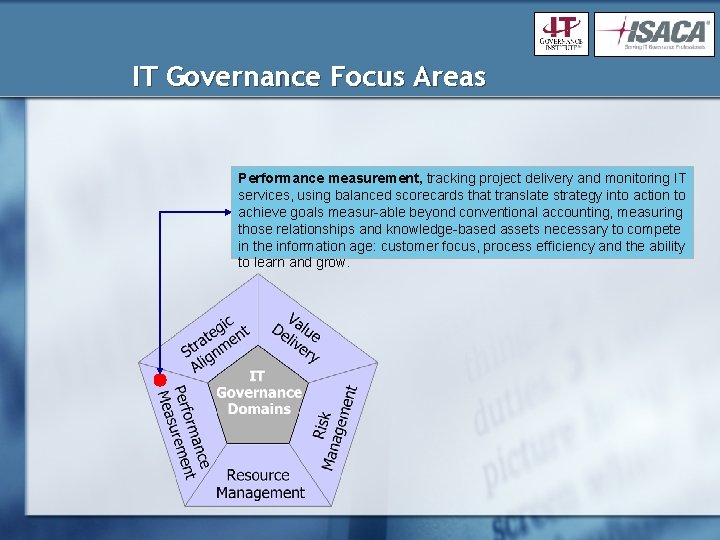
IT Governance Focus Areas Performance measurement, tracking project delivery and monitoring IT services, using balanced scorecards that translate strategy into action to achieve goals measur-able beyond conventional accounting, measuring those relationships and knowledge-based assets necessary to compete in the information age: customer focus, process efficiency and the ability to learn and grow.

IT Governance Life Cycle

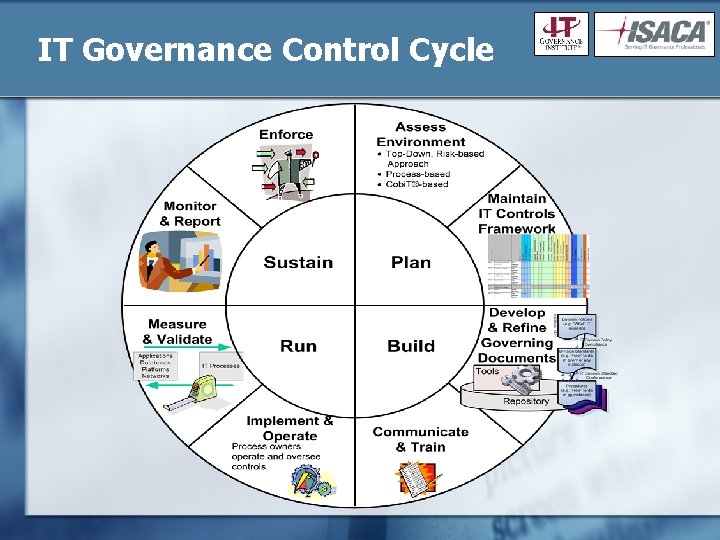
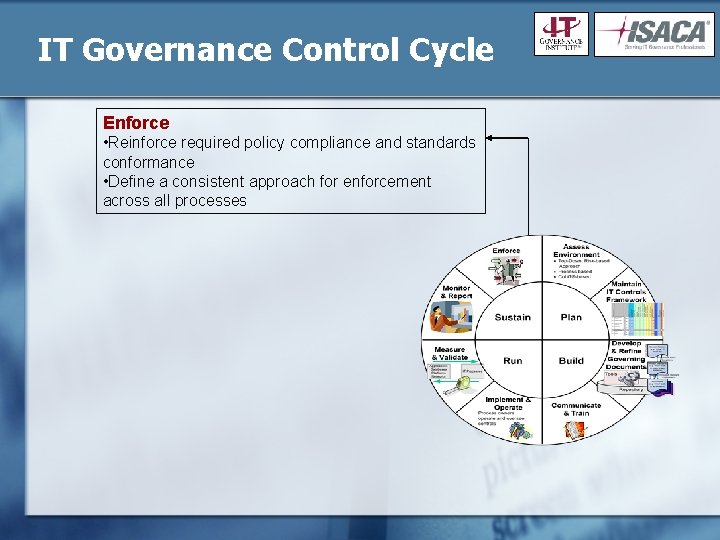
IT Governance Control Cycle

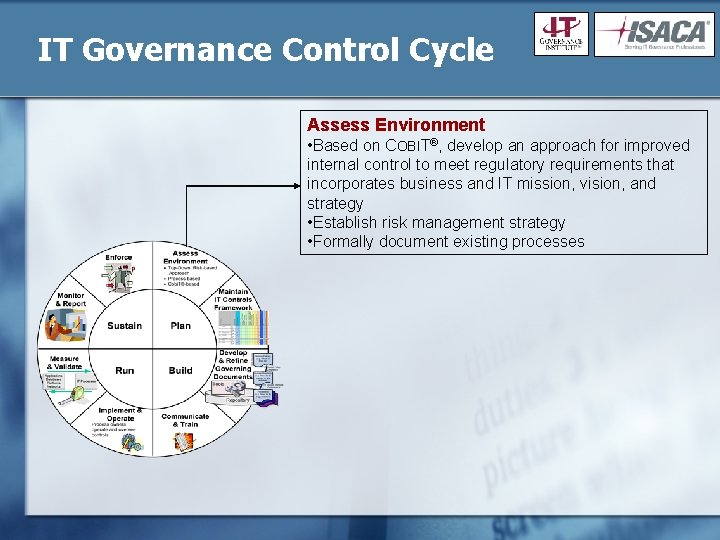
IT Governance Control Cycle Assess Environment • Based on COBIT®, develop an approach for improved internal control to meet regulatory requirements that incorporates business and IT mission, vision, and strategy • Establish risk management strategy • Formally document existing processes

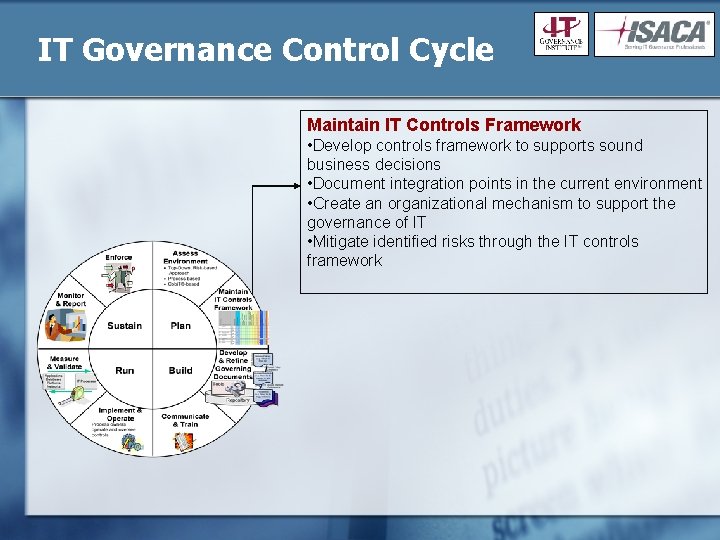
IT Governance Control Cycle Maintain IT Controls Framework • Develop controls framework to supports sound business decisions • Document integration points in the current environment • Create an organizational mechanism to support the governance of IT • Mitigate identified risks through the IT controls framework

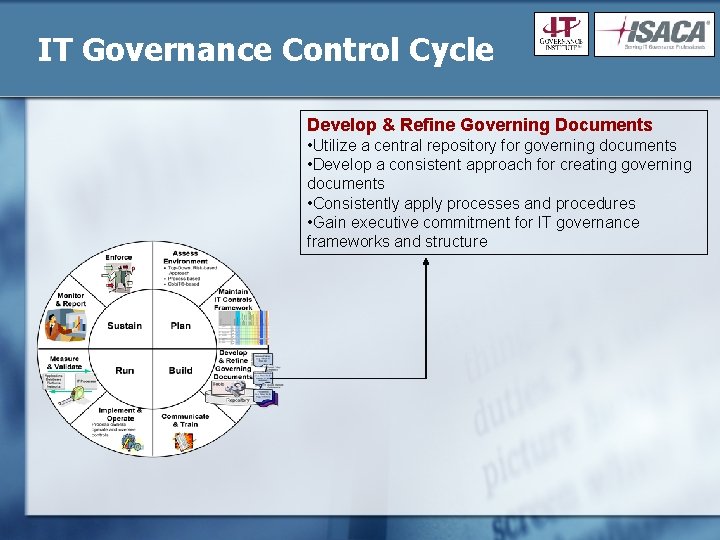
IT Governance Control Cycle Develop & Refine Governing Documents • Utilize a central repository for governing documents • Develop a consistent approach for creating governing documents • Consistently apply processes and procedures • Gain executive commitment for IT governance frameworks and structure

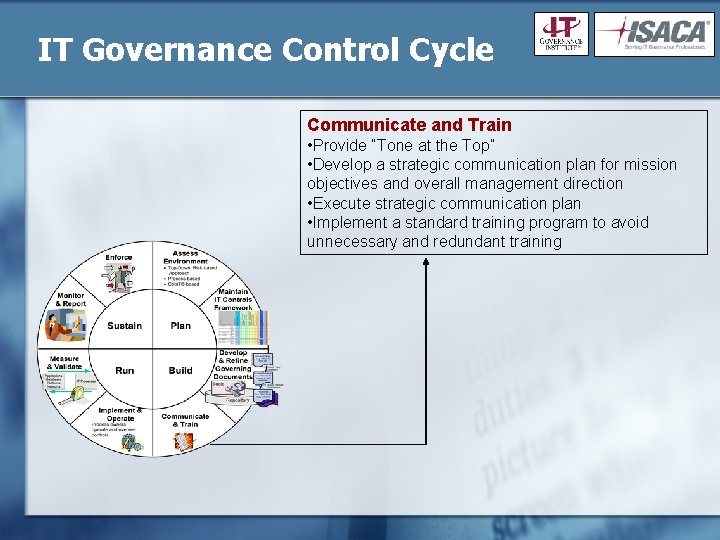
IT Governance Control Cycle Communicate and Train • Provide “Tone at the Top” • Develop a strategic communication plan for mission objectives and overall management direction • Execute strategic communication plan • Implement a standard training program to avoid unnecessary and redundant training

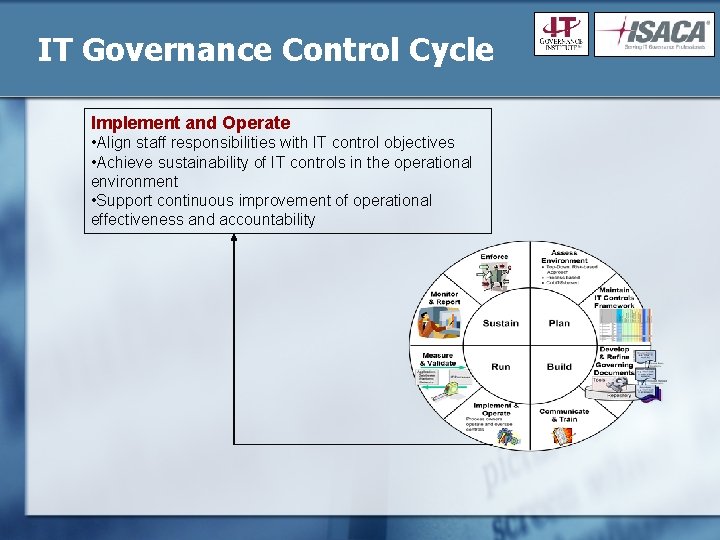
IT Governance Control Cycle Implement and Operate • Align staff responsibilities with IT control objectives • Achieve sustainability of IT controls in the operational environment • Support continuous improvement of operational effectiveness and accountability

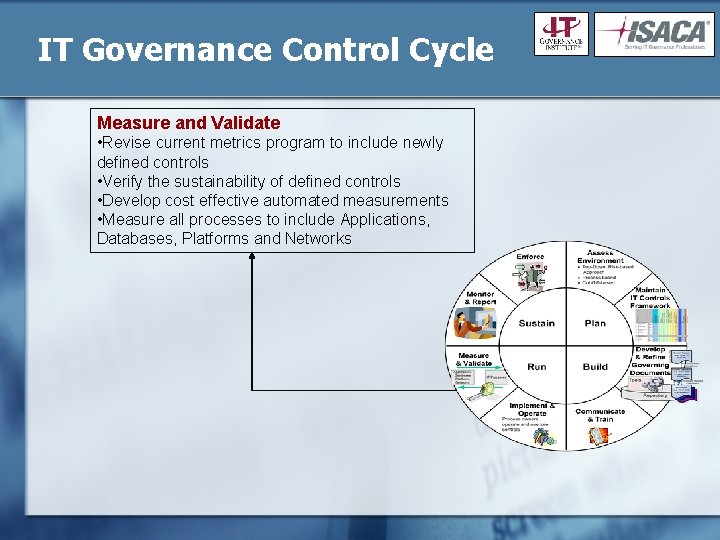
IT Governance Control Cycle Measure and Validate • Revise current metrics program to include newly defined controls • Verify the sustainability of defined controls • Develop cost effective automated measurements • Measure all processes to include Applications, Databases, Platforms and Networks

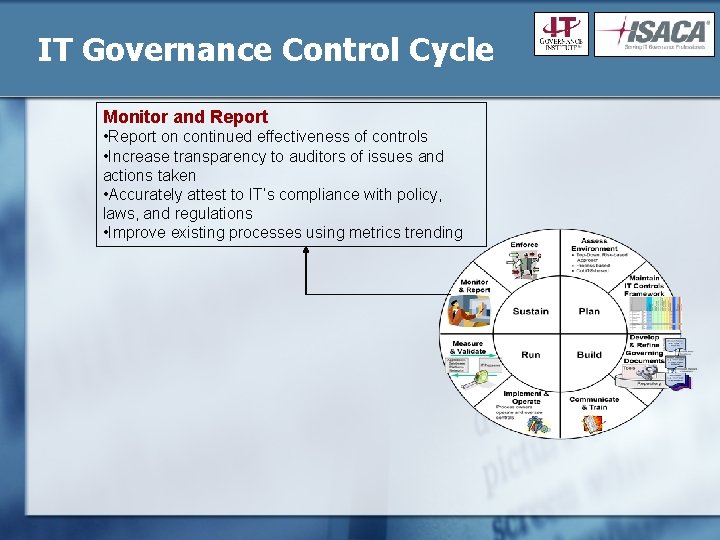
IT Governance Control Cycle Monitor and Report • Report on continued effectiveness of controls • Increase transparency to auditors of issues and actions taken • Accurately attest to IT’s compliance with policy, laws, and regulations • Improve existing processes using metrics trending

IT Governance Control Cycle Enforce • Reinforce required policy compliance and standards conformance • Define a consistent approach for enforcement across all processes

An Overview of COBIT

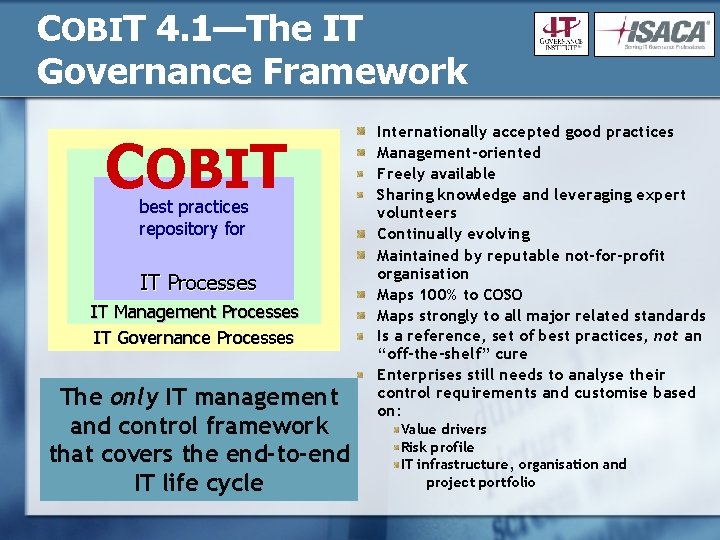
COBIT 4. 1—The IT Governance Framework CCobi. T OBIT best practices repository for IT Processes IT Management Processes IT Governance Processes The only IT management and control framework that covers the end-to-end IT life cycle Internationally accepted good practices Management-oriented Freely available Sharing knowledge and leveraging expert volunteers Continually evolving Maintained by reputable not-for-profit organisation Maps 100% to COSO Maps strongly to all major related standards Is a reference, set of best practices, not an “off-the-shelf” cure Enterprises still needs to analyse their control requirements and customise based on: Value drivers Risk profile IT infrastructure, organisation and project portfolio

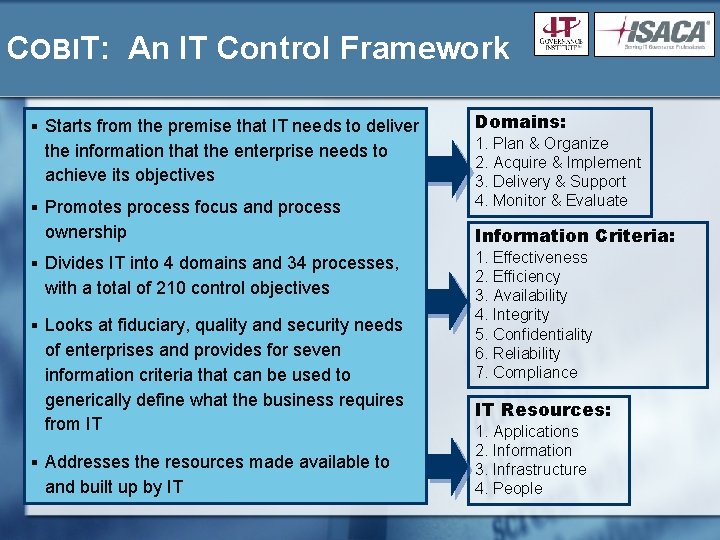
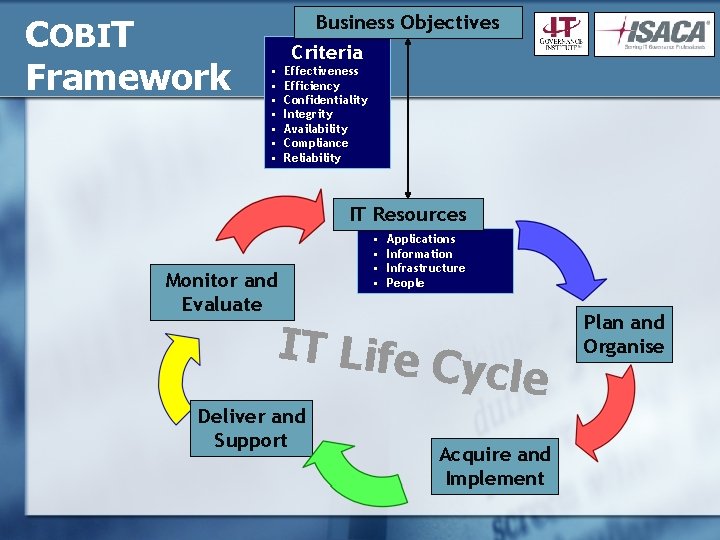
COBIT: An IT Control Framework § Starts from the premise that IT needs to deliver the information that the enterprise needs to achieve its objectives § Promotes process focus and process ownership § Divides IT into 4 domains and 34 processes, with a total of 210 control objectives § Looks at fiduciary, quality and security needs of enterprises and provides for seven information criteria that can be used to generically define what the business requires from IT § Addresses the resources made available to and built up by IT Domains: 1. Plan & Organize 2. Acquire & Implement 3. Delivery & Support 4. Monitor & Evaluate Information Criteria: 1. Effectiveness 2. Efficiency 3. Availability 4. Integrity 5. Confidentiality 6. Reliability 7. Compliance IT Resources: 1. Applications 2. Information 3. Infrastructure 4. People

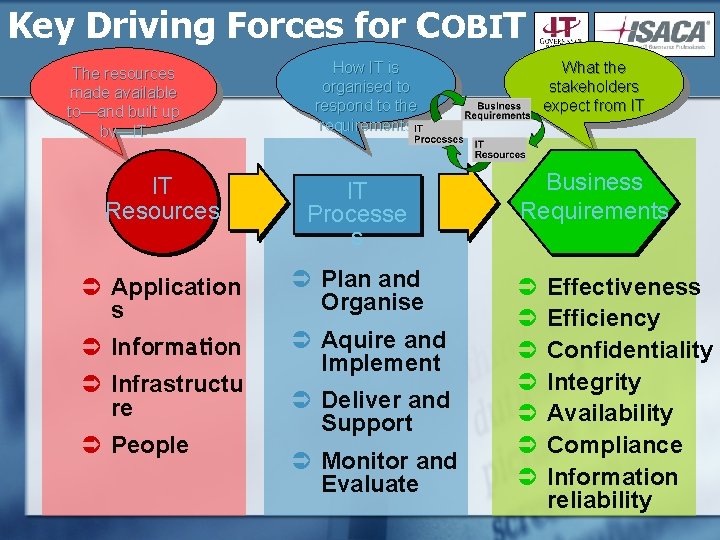
Key Driving Forces for COBIT The resources made available to—and built up by—IT How IT is organised to respond to the requirements IT Resources IT Processe s Ü Application s Ü Plan and Organise Ü Information Ü Aquire and Implement Ü Infrastructu re Ü People Ü Deliver and Support Ü Monitor and Evaluate What the stakeholders expect from IT Business Requirements Ü Ü Ü Ü Effectiveness Efficiency Confidentiality Integrity Availability Compliance Information reliability

COBIT Framework Business Objectives Criteria • • Effectiveness Efficiency Confidentiality Integrity Availability Compliance Reliability IT Resources Monitor and Evaluate • • Applications Information Infrastructure People IT Life C ycle Deliver and Support Acquire and Implement Plan and Organise

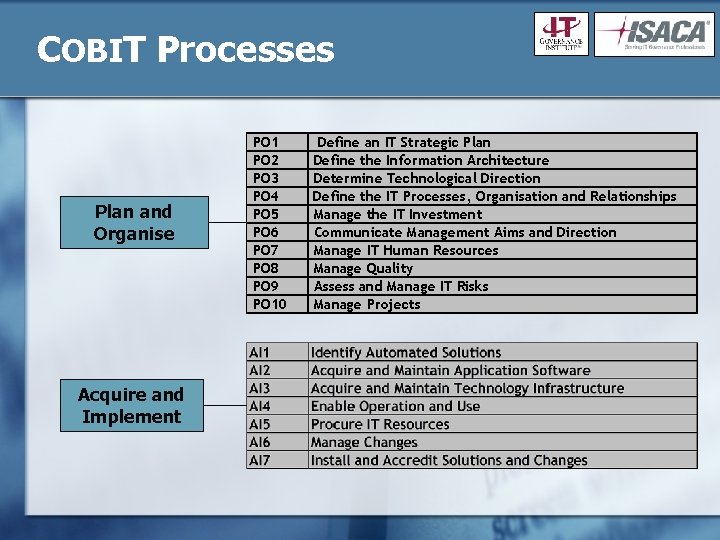
COBIT Processes Plan and Organise Acquire and Implement PO 1 PO 2 PO 3 PO 4 PO 5 PO 6 PO 7 PO 8 PO 9 PO 10 Define an IT Strategic Plan Define the Information Architecture Determine Technological Direction Define the IT Processes, Organisation and Relationships Manage the IT Investment Communicate Management Aims and Direction Manage IT Human Resources Manage Quality Assess and Manage IT Risks Manage Projects

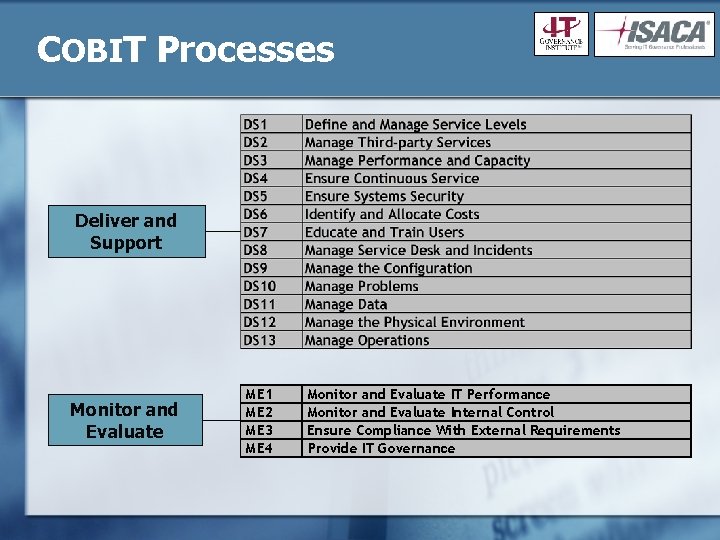
COBIT Processes Deliver and Support Monitor and Evaluate ME 1 ME 2 ME 3 ME 4 Monitor and Evaluate IT Performance Monitor and Evaluate Internal Control Ensure Compliance With External Requirements Provide IT Governance

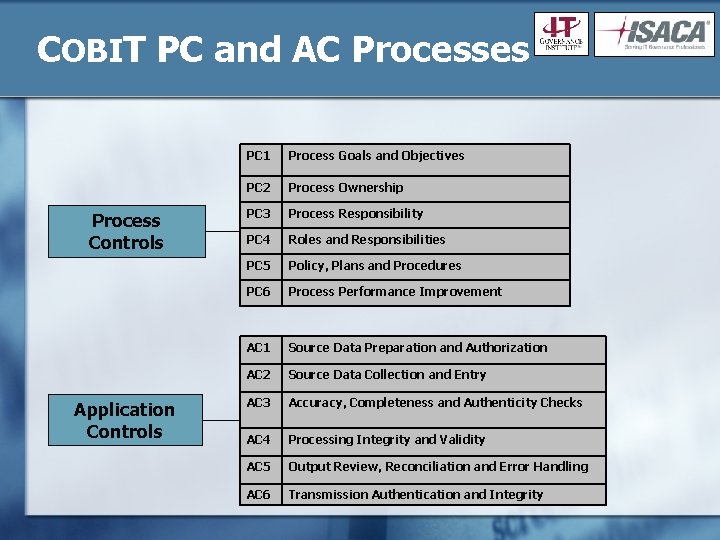
COBIT PC and AC Processes Process Controls Application Controls PC 1 Process Goals and Objectives PC 2 Process Ownership PC 3 Process Responsibility PC 4 Roles and Responsibilities PC 5 Policy, Plans and Procedures PC 6 Process Performance Improvement AC 1 Source Data Preparation and Authorization AC 2 Source Data Collection and Entry AC 3 Accuracy, Completeness and Authenticity Checks AC 4 Processing Integrity and Validity AC 5 Output Review, Reconciliation and Error Handling AC 6 Transmission Authentication and Integrity

Process Level Navigating in COBIT

Control Objectives P 09. 6 Maintenance and Monitoring of a Risk Action Plan Prioritise and plan the control activities at all levels to implement the risk responses identified as necessary, including identification of costs, benefits and responsibility for execution. Obtain approval for recommended actions and acceptance of any residual risks, and ensure that committed actions are owned by the affected process owner(s). Monitor execution of the plans, and report on any deviations to senior management.

Management Guidelines

Management Guidelines

Maturity Model

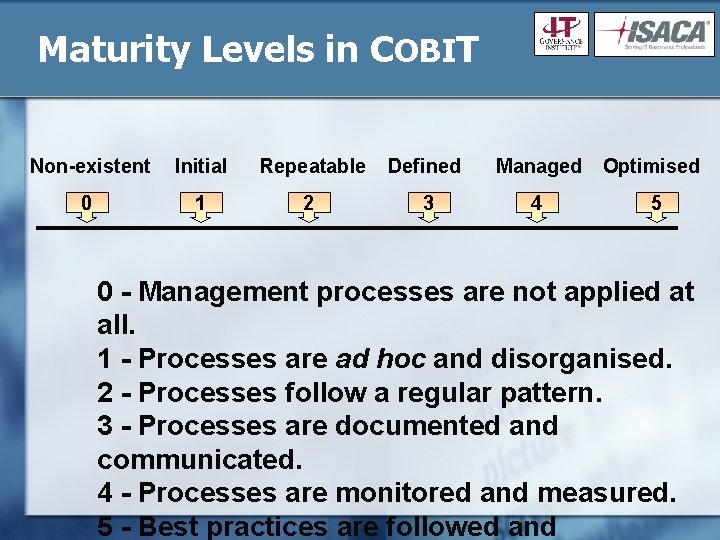
Maturity Levels in COBIT Non-existent Initial Repeatable Defined Managed Optimised 0 1 2 3 4 5 0 - Management processes are not applied at all. 1 - Processes are ad hoc and disorganised. 2 - Processes follow a regular pattern. 3 - Processes are documented and communicated. 4 - Processes are monitored and measured. 5 - Best practices are followed and

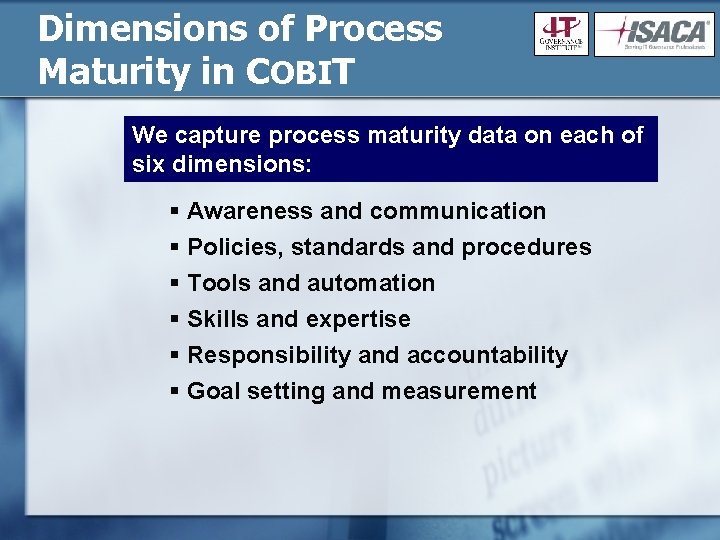
Dimensions of Process Maturity in COBIT We capture process maturity data on each of six dimensions: § Awareness and communication § Policies, standards and procedures § Tools and automation § Skills and expertise § Responsibility and accountability § Goal setting and measurement

Leverage COBIT® Supporting Materials. . .

Implementation Guide

Implementation Guide IT Governance Implementation Guide, 2 nd Edition n Detailed, structured guidance to the implementation of IT governance n Generic IT governance implementation guidance, not just COBIT

Control Practices

Control Practices COBIT Control Practices, 2 nd Edition n Detailed guidance on each of the control objectives n Management-oriented n From three to 12 control practices per control objective

Assurance Guide

Assurance Guide IT Assurance Guide: Using COBIT n Detailed guidance to support assurance practitioners in: Financial statement audit n Internal audit n Value for money n Operational improvement n n Guidance on: How to leverage COBIT for assurance n Detailed assurance testing steps n

Quickstart

Quickstart For small and medium sized organizations and larger organizations wanting to quickstart IT governance n Selection of components from the complete COBIT framework n Can be used as a baseline (set of “smart things to do”) for small and medium-sized enterprises and other entities where IT is not strategic or absolutely critical for survival n Can also be a starting point for larger enterprises in their first moves toward an appropriate level of control and governance of IT

COBIT Security Baseline

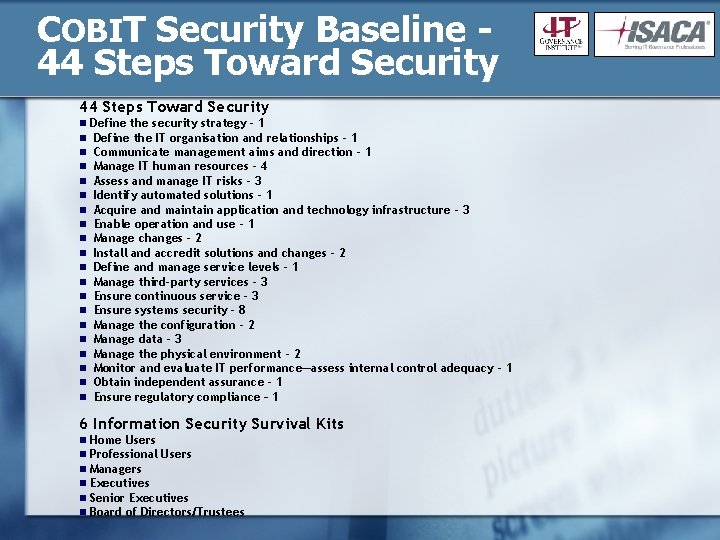
COBIT Security Baseline 44 Steps Toward Security n n n n n Define the security strategy - 1 Define the IT organisation and relationships - 1 Communicate management aims and direction - 1 Manage IT human resources - 4 Assess and manage IT risks - 3 Identify automated solutions - 1 Acquire and maintain application and technology infrastructure - 3 Enable operation and use - 1 Manage changes - 2 Install and accredit solutions and changes - 2 Define and manage service levels - 1 Manage third-party services - 3 Ensure continuous service - 3 Ensure systems security - 8 Manage the configuration - 2 Manage data - 3 Manage the physical environment - 2 Monitor and evaluate IT performance—assess internal control adequacy - 1 Obtain independent assurance - 1 Ensure regulatory compliance – 1 6 Information Security Survival Kits n n n Home Users Professional Users Managers Executives Senior Executives Board of Directors/Trustees

COBIT Mappings to Other Frameworks and Standards

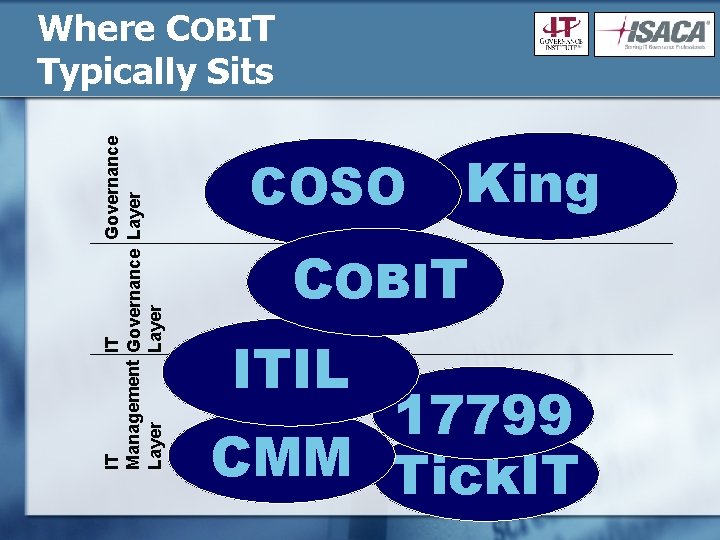
IT IT Governance Management Governance Layer Where COBIT Typically Sits COSO King COBIT ITIL 17799 CMM Tick. IT

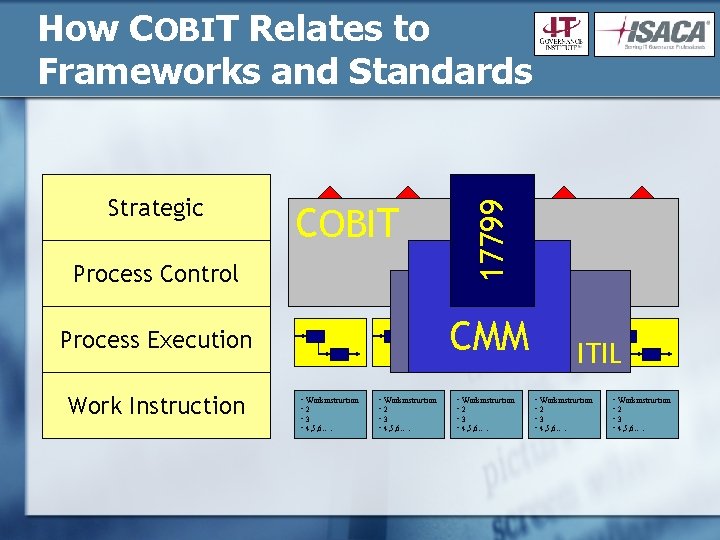
Strategic Process Control COBIT XY XY ## ## XY XY XY ## ## ## CMM Process Execution Work Instruction 17799 How COBIT Relates to Frameworks and Standards • Workinstruction • 2 • 3 • 4, 5, 6…. ITIL • Workinstruction • 2 • 3 • 4, 5, 6….

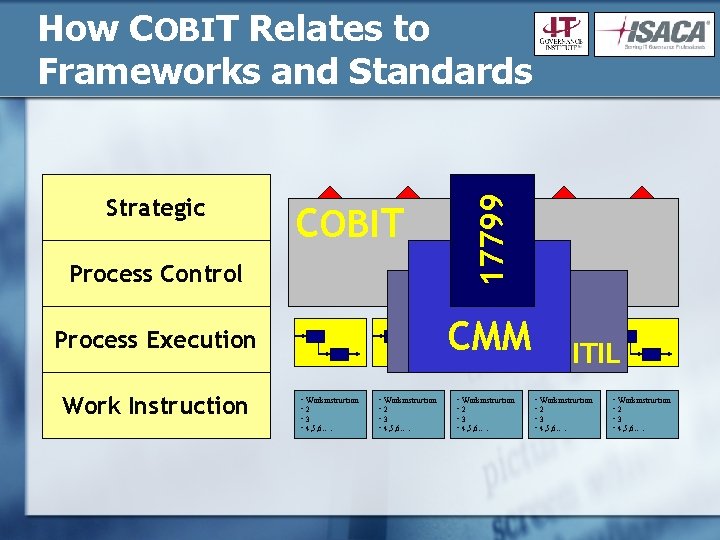
Strategic Process Control COBIT XY XY ## ## XY XY XY ## ## ## CMM Process Execution Work Instruction 17799 How COBIT Relates to Frameworks and Standards • Workinstruction • 2 • 3 • 4, 5, 6…. ITIL • Workinstruction • 2 • 3 • 4, 5, 6….

An Overview of Val. IT

The Information Paradox ? ? ? The value of IT is being increasingly questioned. . . …yet organizations continue to spend more and more on IT 60

The Fundamental Question Are we maximizing the value of our ITenabled business investments such that: Ø we are getting optimal benefits; Ø at an affordable cost; and Ø with an acceptable level of risk? Over the full economic life-cycle of the investment

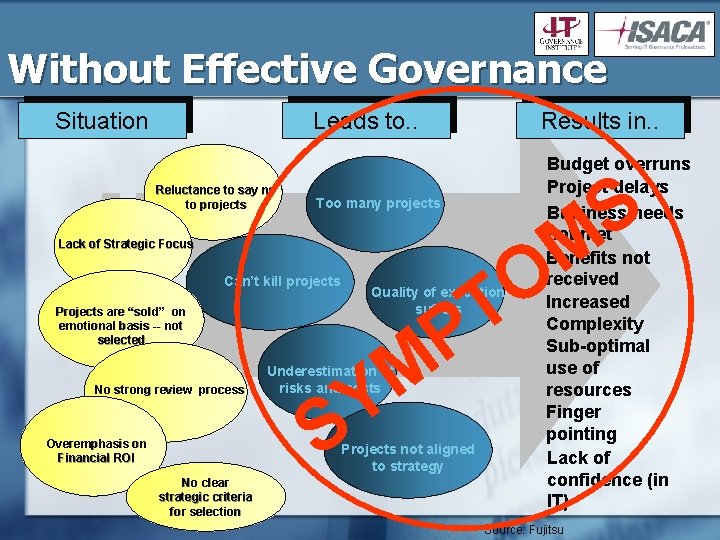
Without Effective Governance Situation Results in. . Leads to. . Reluctance to say no to projects S Too many projects M O Lack of Strategic Focus Can’t kill projects No strong review process Overemphasis on Financial ROI T P Quality of execution suffers Projects are “sold” on emotional basis -- not selected M Y Underestimation of risks and costs S Projects not aligned to strategy No clear strategic criteria for selection Budget overruns Project delays Business needs not met Benefits not received Increased Complexity Sub-optimal use of resources Finger pointing Lack of confidence (in IT) Source: Fujitsu

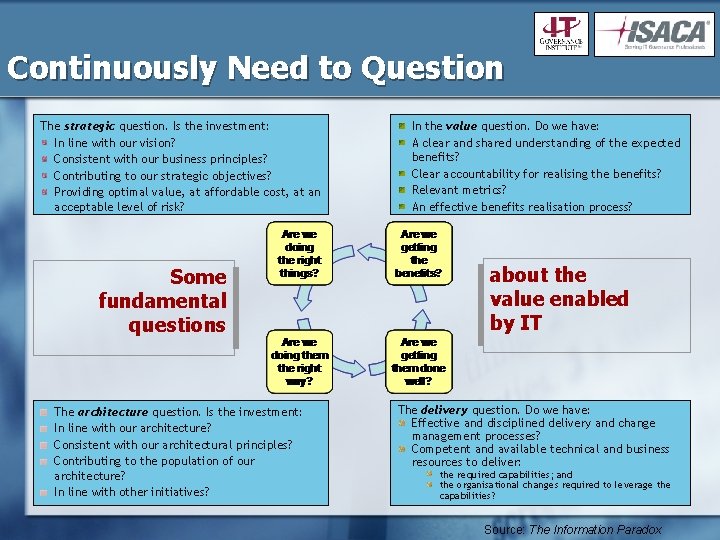
Continuously Need to Question The strategic question. Is the investment: In line with our vision? Consistent with our business principles? Contributing to our strategic objectives? Providing optimal value, at affordable cost, at an acceptable level of risk? Some fundamental questions The architecture question. Is the investment: In line with our architecture? Consistent with our architectural principles? Contributing to the population of our architecture? In line with other initiatives? In the value question. Do we have: A clear and shared understanding of the expected benefits? Clear accountability for realising the benefits? Relevant metrics? An effective benefits realisation process? about the value enabled by IT The delivery question. Do we have: Effective and disciplined delivery and change management processes? Competent and available technical and business resources to deliver: the required capabilities; and the organisational changes required to leverage the capabilities? Source: The Information Paradox

Val IT Processes & Key Management Practices

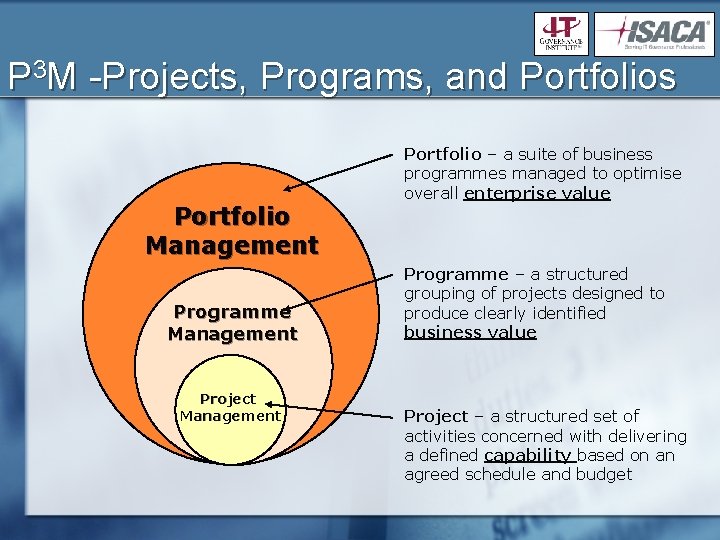
P 3 M -Projects, Programs, and Portfolios Portfolio Management Programme Management Project Management Portfolio – a suite of business programmes managed to optimise overall enterprise value Programme – a structured grouping of projects designed to produce clearly identified business value Project – a structured set of activities concerned with delivering a defined capability based on an agreed schedule and budget

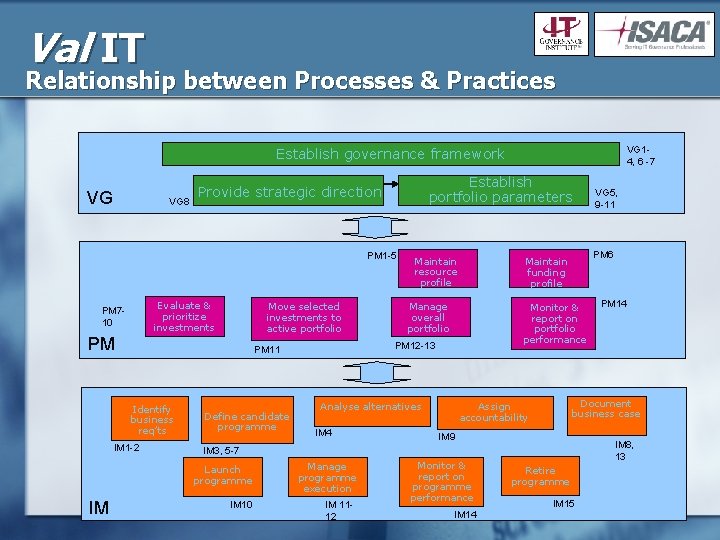
Val IT Relationship between Processes & Practices VG 14, 6 -7 Establish governance framework VG VG 8 Establish portfolio parameters Provide strategic direction PM 1 -5 Evaluate & prioritize investments PM 710 Move selected investments to active portfolio PM IM 1 -2 IM Define candidate programme Manage overall portfolio Monitor & report on portfolio performance Analyse alternatives IM 4 PM 6 Maintain funding profile PM 12 -13 PM 11 Identify business req’ts Maintain resource profile Manage programme execution IM 9 IM 10 IM 1112 Monitor & report on programme performance IM 14 PM 14 Document business case Assign accountability IM 8, 13 IM 3, 5 -7 Launch programme VG 5, 9 -11 Retire programme IM 15

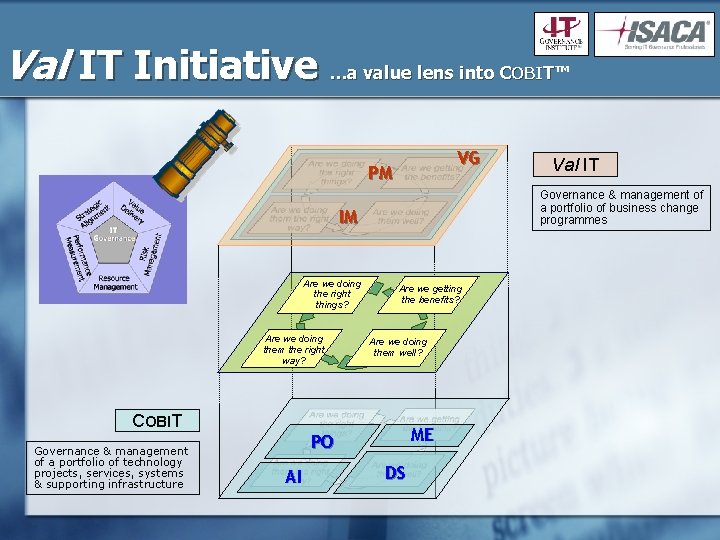
Val IT Initiative …a value lens into C OBIT™ VG PM Governance & management of a portfolio of business change programmes IM Are we doing the right things? Are we doing them the right way? Are we getting the benefits? Are we doing them well? COBIT Governance & management of a portfolio of technology projects, services, systems & supporting infrastructure ME PO AI Val IT DS

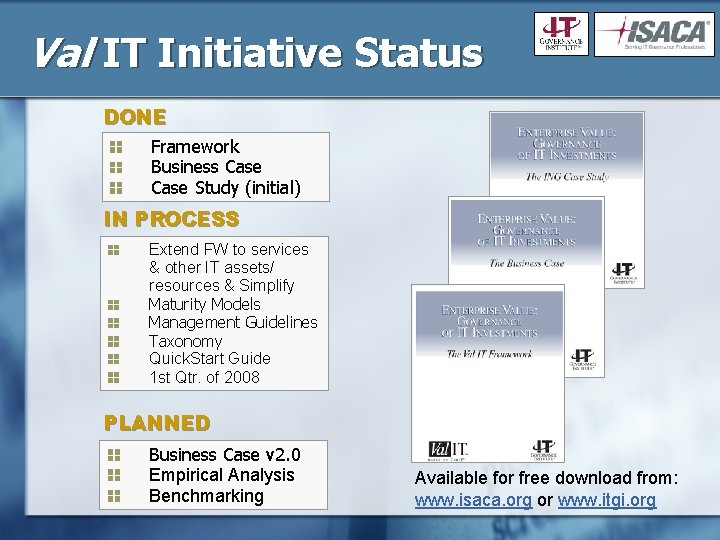
Val IT Initiative Status DONE Framework Business Case Study (initial) IN PROCESS Extend FW to services & other IT assets/ resources & Simplify Maturity Models Management Guidelines Taxonomy Quick. Start Guide 1 st Qtr. of 2008 PLANNED Business Case v 2. 0 Empirical Analysis Benchmarking Available for free download from: www. isaca. org or www. itgi. org

The Business Challenge n Maximizing value and reducing risk made possible by IT both enables and requires a through IT governance approach that: n n n Ensures clarity of, and accountability for the desired outcomes Enables understanding of the full scope of effort Breaks down the “silos” and “connects the dots” Manage the full economic life-cycle Senses and responds to changes and deviations This is a significant leadership challenge, opportunity and responsibility!

The Risk. IT Initiative

RISKIT DESCRIPTION n. A risk management framework that provides the missing link between enterprise risk management and IT Management and control, fitting in the overall IT Governance framework of ITGI, and building upon all existing risk related components within the current frameworks, i. e. , COBIT and Val IT n. A number of related services and products (practical guides, reference data, interfaces/mapping with other standards, …)

RISKIT ACTIONS n ITGI Board discussion on this initiative and decision to proceed with full business case development (July 2007) n Business Case development, (October 2007) including n. Market survey n. Feasibility study n. High-level design of the product/service n. Set-up project governance structure, incl. Core Team, expert team, identify project manager(s) and potential resources n. Define high-level development and roll-out plan ITGI Board approved detailed business case and decision to proceed with full project (November 2007) n Risk. IT Task Force members appointed (December 2007) n First Risk. IT Task Force meeting held in Ghent, Belgium on 18 -19 January 2008 n First draft Risk. IT planned to be issued by December 2008 n

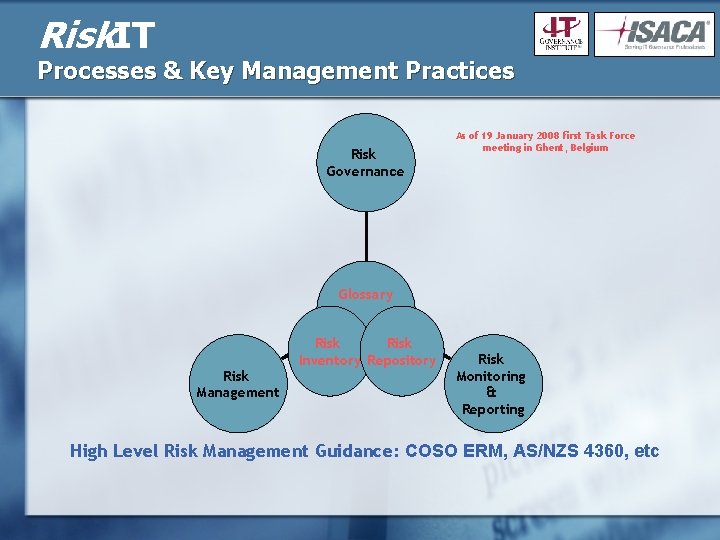
Risk. IT Processes & Key Management Practices Risk Governance As of 19 January 2008 first Task Force meeting in Ghent, Belgium Glossary Risk Management Risk Inventory Repository Risk Monitoring & Reporting High Level Risk Management Guidance: COSO ERM, AS/NZS 4360, etc

RISK IT Product Family – Proposed Content & Lifecycle

RELATIONSHIP OF COBIT/VALIT/RISKIT

Certified in the Governance of Enterprise IT (CGEIT)

Questions
 Keslee lainhart
Keslee lainhart Gcr cism
Gcr cism Spectre cism
Spectre cism Cap ground team handbook
Cap ground team handbook Cisa crisc
Cisa crisc Angeline chen dla piper
Angeline chen dla piper Dr cisa sudbury
Dr cisa sudbury Cisa crr
Cisa crr Cisa domains
Cisa domains Cisa emergency communications division
Cisa emergency communications division Cisa evolution
Cisa evolution Cisa audit methodology
Cisa audit methodology Tim weisenberger
Tim weisenberger John 5:37-39
John 5:37-39 Voltaire john locke
Voltaire john locke John summerscales
John summerscales When did john cabot sail
When did john cabot sail John 20 message
John 20 message John chiappone
John chiappone John 19 14
John 19 14 Pelagia and philammon
Pelagia and philammon John 20:19-31 ceb
John 20:19-31 ceb John capece
John capece John welsh nvidia
John welsh nvidia John deere supply chain
John deere supply chain Vineeth john md
Vineeth john md John voyez
John voyez John morgan russell
John morgan russell John pius boland olympics
John pius boland olympics John mason maths
John mason maths Dystanin
Dystanin Universidad st john's ex hacienda coapa
Universidad st john's ex hacienda coapa Positive negative
Positive negative Dr john wang
Dr john wang It is finished in greek
It is finished in greek John alejandro
John alejandro John oakes phd
John oakes phd Charles john huffan dickens
Charles john huffan dickens St john chrysostom on wealth and poverty pdf
St john chrysostom on wealth and poverty pdf Bobby brown licking whitney houston
Bobby brown licking whitney houston John 35
John 35 John brown's body lies a mouldering in the grave
John brown's body lies a mouldering in the grave The collector john fowles analysis
The collector john fowles analysis Matthew mark luke john old testament
Matthew mark luke john old testament Dining room operations
Dining room operations John 'jack' worthing
John 'jack' worthing John barkai
John barkai I lent a pencil to graham
I lent a pencil to graham 700s dewey decimal system
700s dewey decimal system Dear john letter meaning
Dear john letter meaning John van bemmelen
John van bemmelen Dr john ward geriatrician newcastle
Dr john ward geriatrician newcastle Gardener parable
Gardener parable John 1:29 gnt
John 1:29 gnt John dryden translation theory
John dryden translation theory Msf holland myanmar
Msf holland myanmar John collier the chaser
John collier the chaser If any man wants to come after me
If any man wants to come after me Resource histogram pmp
Resource histogram pmp John ellis physics
John ellis physics Carlos santana e john smith
Carlos santana e john smith Henry ford famous inventions
Henry ford famous inventions Shepard astros
Shepard astros John mathiason
John mathiason John blaine uky
John blaine uky Adams and adams secretarial training
Adams and adams secretarial training Ducksters john f kennedy
Ducksters john f kennedy John newlands
John newlands John donne poem
John donne poem Bendiga con b o v
Bendiga con b o v Amaiya
Amaiya James 4:1-7
James 4:1-7 John money
John money They still haven't found out what caused the accident
They still haven't found out what caused the accident Love's diet analysis
Love's diet analysis Bourbon triumvirate pictures
Bourbon triumvirate pictures The pearl plot
The pearl plot Define john doe
Define john doe