John Carelli Instructor Kutztown University carellikutztown edu 1

![Add A New User useradd [-u uid] [-o] [-g group] [-G group [, group, Add A New User useradd [-u uid] [-o] [-g group] [-G group [, group,](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-3.jpg)
![usermod [-u uid] [-o] [-g group] [-G group [, group, …] [-d home] usermod [-u uid] [-o] [-g group] [-G group [, group, …] [-d home]](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-4.jpg)



![mt [-f tape_device] commands rew offl status fsf [count] command - rewind - mt [-f tape_device] commands rew offl status fsf [count] command - rewind -](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-11.jpg)



![mount [-r] [device] <directory> uses /etc/fstab to get disk info -r for read mount [-r] [device] <directory> uses /etc/fstab to get disk info -r for read](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-16.jpg)

![Who is using a file a directory or a socket? fuser [-u] [-k] Who is using a file a directory or a socket? fuser [-u] [-k]](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-18.jpg)



![Shutdown/Restart commands shutdown [TIME] [message] halt reboot [-p] (-p is poweroff) init <run_level> generally Shutdown/Restart commands shutdown [TIME] [message] halt reboot [-p] (-p is poweroff) init <run_level> generally](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-26.jpg)




![yum install <package. Name> yum update [<package. Name>] yum check-update yum clean all yum yum install <package. Name> yum update [<package. Name>] yum check-update yum clean all yum](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-31.jpg)




- Slides: 41

John Carelli, Instructor Kutztown University carelli@kutztown. edu 1

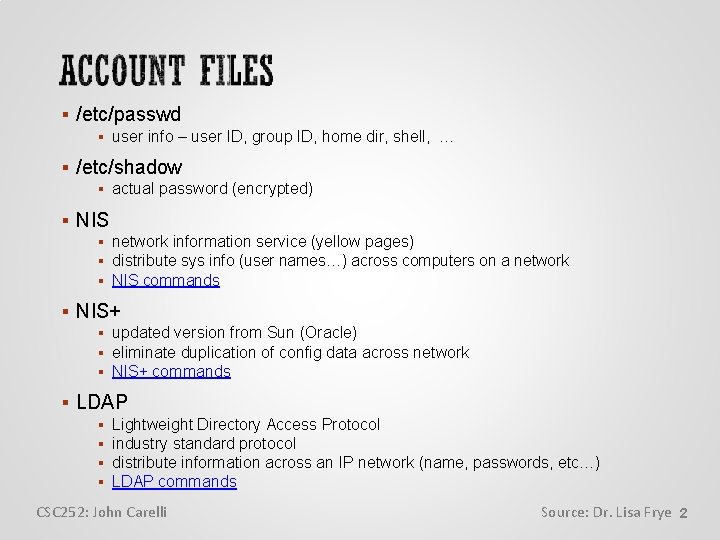
/etc/passwd user info – user ID, group ID, home dir, shell, … /etc/shadow actual password (encrypted) NIS network information service (yellow pages) distribute sys info (user names…) across computers on a network NIS commands NIS+ updated version from Sun (Oracle) eliminate duplication of config data across network NIS+ commands LDAP Lightweight Directory Access Protocol industry standard protocol distribute information across an IP network (name, passwords, etc…) LDAP commands CSC 252: John Carelli Source: Dr. Lisa Frye 2
![Add A New User useradd u uid o g group G group group Add A New User useradd [-u uid] [-o] [-g group] [-G group [, group,](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-3.jpg)
Add A New User useradd [-u uid] [-o] [-g group] [-G group [, group, …] [-d home] [-m] [-k template] [-f inactive] [-r] s shell] [-e expire] [-c comment] login [-p passwd] [- Default settings useradd -D [-g group] [-b base] [-f inactive] [-e expire] login useradd –D to see default settings CSC 252: John Carelli Source: Dr. Lisa Frye 3
![usermod u uid o g group G group group d home usermod [-u uid] [-o] [-g group] [-G group [, group, …] [-d home]](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-4.jpg)
usermod [-u uid] [-o] [-g group] [-G group [, group, …] [-d home] [-m] [-l new_login] [-f inactive] [-r] passwd] [-s shell] [-e expire] [-c comment] login [-p userdel [-r] login CSC 252: John Carelli Source: Dr. Lisa Frye 4

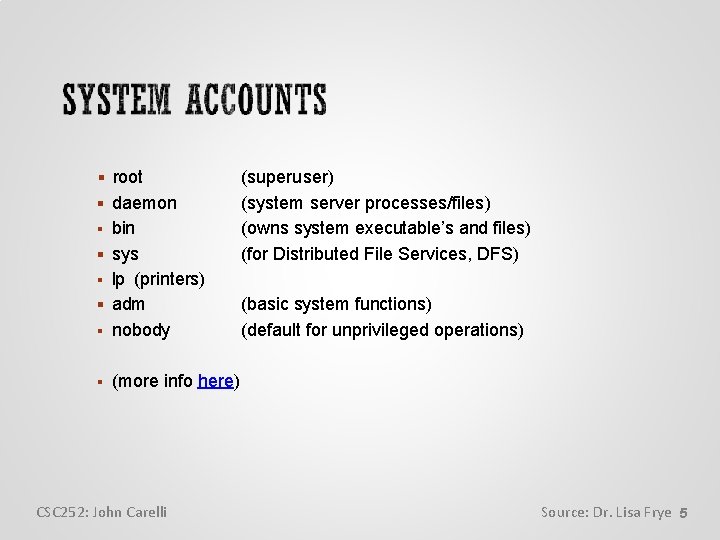
root daemon bin sys (superuser) (system server processes/files) (owns system executable’s and files) (for Distributed File Services, DFS) lp (printers) adm nobody (basic system functions) (default for unprivileged operations) (more info here) CSC 252: John Carelli Source: Dr. Lisa Frye 5

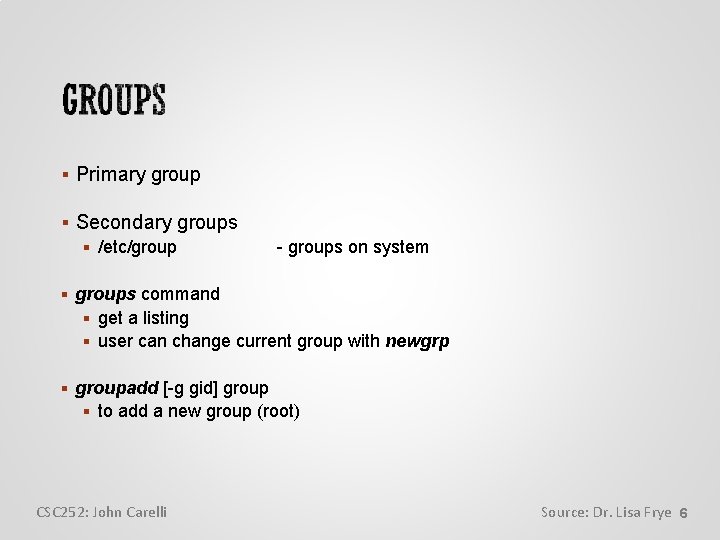
Primary group Secondary groups /etc/group - groups on system groups command get a listing user can change current group with newgrp groupadd [-g gid] group to add a new group (root) CSC 252: John Carelli Source: Dr. Lisa Frye 6

root daemon sys tty bin adm lp mail uucp / nuucp nobody noaccess CSC 252: John Carelli Source: Dr. Lisa Frye 7

backup from one machine label all tapes grandfather / son 3 backup cycles (ex: daily, weekly, monthly) avoids propagating an error https: //www. handybackup. net/grandfather-son-backup. shtml secure backup tapes keep tapes off-site backup appropriately always check restore procedure periodically develop a tape life cycle CSC 252: John Carelli Source: Dr. Lisa Frye 8

activity on filesystem capacity of dump device length of “dump window” amount of redundancy number of tapes available how far back you must be able to recover CSC 252: John Carelli Source: Dr. Lisa Frye 9

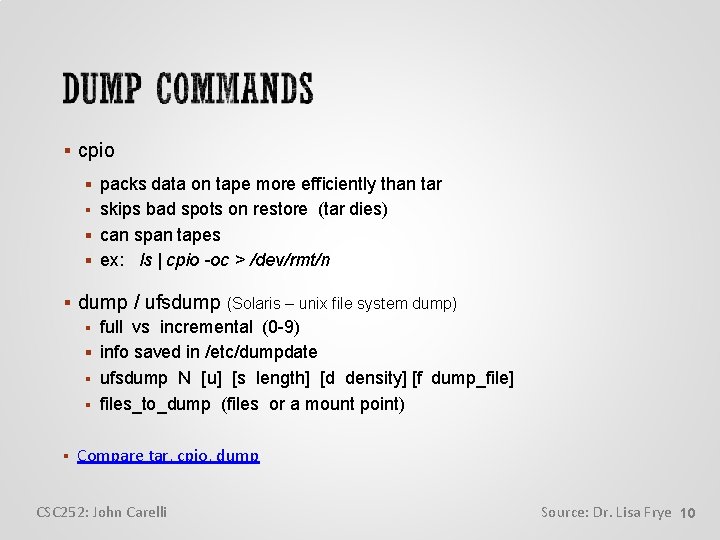
cpio packs data on tape more efficiently than tar skips bad spots on restore (tar dies) can span tapes ex: ls | cpio -oc > /dev/rmt/n dump / ufsdump (Solaris – unix file system dump) full vs incremental (0 -9) info saved in /etc/dumpdate ufsdump N [u] [s length] [d density] [f dump_file] files_to_dump (files or a mount point) Compare tar, cpio, dump CSC 252: John Carelli Source: Dr. Lisa Frye 10
![mt f tapedevice commands rew offl status fsf count command rewind mt [-f tape_device] commands rew offl status fsf [count] command - rewind -](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-11.jpg)
mt [-f tape_device] commands rew offl status fsf [count] command - rewind - offline (unload the tape) - output status info on tape unit - forward space “count” files (i. e. jump ahead) restore [i] [x file_to_restore] [f tape_device] CSC 252: John Carelli Source: Dr. Lisa Frye 11

Linux Device Names (disks) • The first floppy drive is named /dev/fd 0. • The second floppy drive is named /dev/fd 1. • The first hard disk detected is named /dev/sda. • The second hard disk detected is named /dev/sdb, and so on. • The first SCSI CD-ROM is named /dev/scd 0, also known as /dev/sr 0. The partitions on each disk are represented by appending a decimal number to the disk name: sda 1 and sda 2 represent the first and second partitions of the first SCSI disk drive in your system. CSC 252: John Carelli 12

Physically add drive Create entries in /dev mknod command can do this format the drive mkfs (make the file system) newfs a newer, friendlier, version Add entry to /etc/fstab (optional) contains info about how fs should be mounted CSC 252: John Carelli Source: Dr. Lisa Frye 13

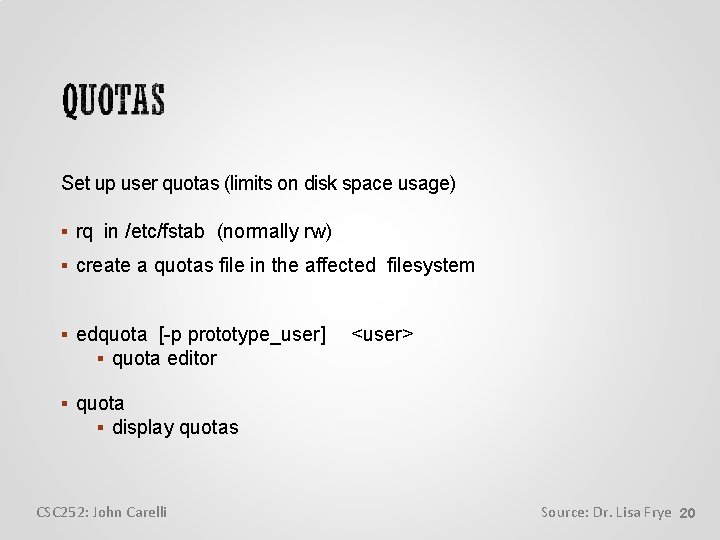
Record characteristics of a file system length of a disk block size and location of inode tables disk block map and usage information size of the cylinder groups other important parameters of the file system more info here: http: //www. linfo. org/superblock CSC 252: John Carelli Source: Dr. Lisa Frye 14

Disk Information Get information about available disks: • df command • • • Disk space usage df –a. Th (more readable format) lsblk command • • useful info about block devices major/minor numbers, /dev name, mount point, … • lsusb command (for usb devices) • fdisk (disk partitioning) • ex: fdisk –l /dev/sda (need to be root to list partitions) CSC 252: John Carelli 15
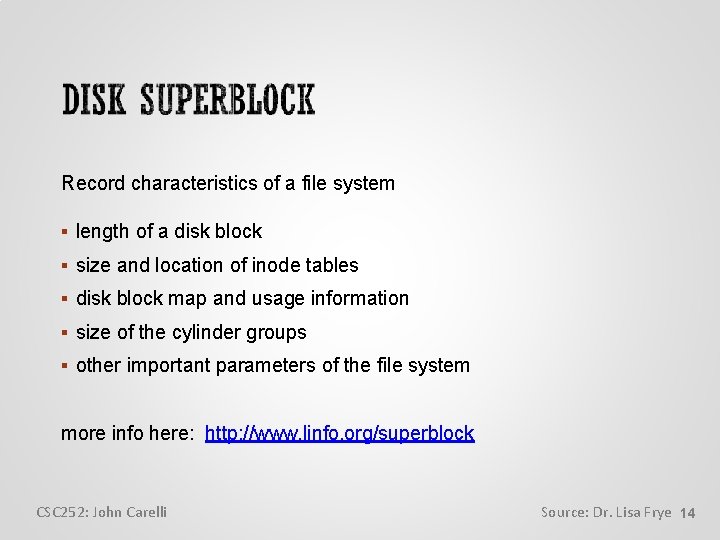
![mount r device directory uses etcfstab to get disk info r for read mount [-r] [device] <directory> uses /etc/fstab to get disk info -r for read](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-16.jpg)
mount [-r] [device] <directory> uses /etc/fstab to get disk info -r for read only mount -t type [device] <directory> specify the type of device mount [-f filesystem_types] “fake” – don’t actually mount anything see what mount is trying to do, or add entries to /etc/mtab (for previously mounted devices) mountall called during boot process uses /etc/fstab to get disk info CSC 252: John Carelli Source: Dr. Lisa Frye 16

umount <filesystem> umountall CSC 252: John Carelli Source: Dr. Lisa Frye 17
![Who is using a file a directory or a socket fuser u k Who is using a file a directory or a socket? fuser [-u] [-k]](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-18.jpg)
Who is using a file a directory or a socket? fuser [-u] [-k] <device> -u for user -k kills the process using the device! -v is verbose ex: fuser –v. Checking a filesystem fsck [-p] [-n] [-y] [-F filesystem_type] [raw_device] careful with this one! CSC 252: John Carelli Source: Dr. Lisa Frye 18

fixes damaged or inconsistent inodes unreferenced inodes large link counts unused data blocks not recorded in block maps data blocks listed as free but also used in a file incorrect summary info in superblock CSC 252: John Carelli Source: Dr. Lisa Frye 19

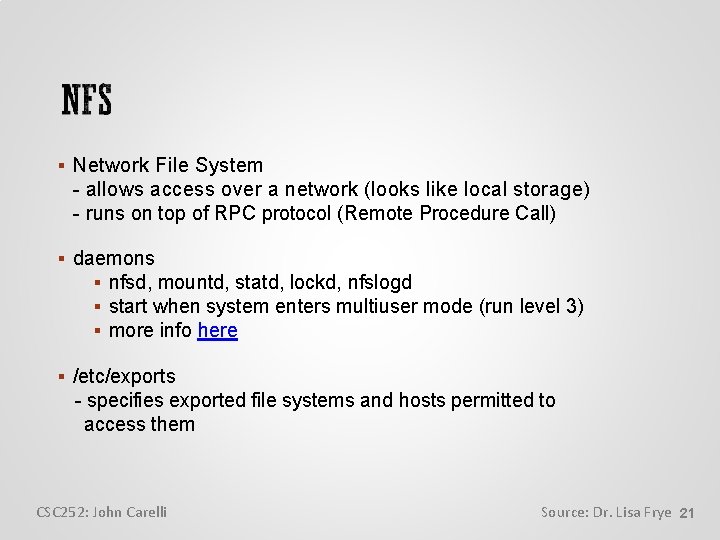
Set up user quotas (limits on disk space usage) rq in /etc/fstab (normally rw) create a quotas file in the affected filesystem edquota [-p prototype_user] quota editor <user> quota display quotas CSC 252: John Carelli Source: Dr. Lisa Frye 20

Network File System - allows access over a network (looks like local storage) - runs on top of RPC protocol (Remote Procedure Call) daemons nfsd, mountd, statd, lockd, nfslogd start when system enters multiuser mode (run level 3) more info here /etc/exports - specifies exported file systems and hosts permitted to access them CSC 252: John Carelli Source: Dr. Lisa Frye 21

Loading and initialization of kernel Device detection and configuration Creation of system processes Operator intervention (manual boot only) Execution of startup scripts (by init) Multiuser operation CSC 252: John Carelli (init spawns getty process) Source: Dr. Lisa Frye 22

Also known as run levels 0 system is completely shut down 1 single-user mode (administration) 2 multi-user mode without NFS (networking) 3 full multi-user mode with networking 4 unused 5 full multi-user mode with networking and X 11 (GUI) 6 reboot startup scripts defined in /etc/rc#. d commands in /etc/rc. local will execute on a runlevel change 23 CSC 252: John Carelli Source: Dr. Lisa Frye

setting the name of the computer setting the time zone checking the disks with fsck mounting the system’s disks removing old files in /tmp configuring network interfaces starting up daemons and network services CSC 252: John Carelli Source: Dr. Lisa Frye 24

logs shutdown kills nonessential processes executes sync waits for filesystem writes to complete halts the kernel CSC 252: John Carelli Source: Dr. Lisa Frye 25
![ShutdownRestart commands shutdown TIME message halt reboot p p is poweroff init runlevel generally Shutdown/Restart commands shutdown [TIME] [message] halt reboot [-p] (-p is poweroff) init <run_level> generally](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-26.jpg)
Shutdown/Restart commands shutdown [TIME] [message] halt reboot [-p] (-p is poweroff) init <run_level> generally run by kernel or, restart with the given run level runlevel command Will show the last 2 run levels CSC 252: John Carelli Source: Dr. Lisa Frye 26

flushes cached superblocks to disk flushes modified inodes and cached data blocks CSC 252: John Carelli Source: Dr. Lisa Frye 27

Updates to system files Correct errors or provide security fix patch applies a diff file to an original CSC 252: John Carelli Source: Dr. Lisa Frye 28

CD Download source code Download package CSC 252: John Carelli Source: Dr. Lisa Frye 29

yum apt-get CSC 252: John Carelli Source: Dr. Lisa Frye 30
![yum install package Name yum update package Name yum checkupdate yum clean all yum yum install <package. Name> yum update [<package. Name>] yum check-update yum clean all yum](https://slidetodoc.com/presentation_image_h/1701cd32ed411b4adb016dfc499820d4/image-31.jpg)
yum install <package. Name> yum update [<package. Name>] yum check-update yum clean all yum list available yum search <word> Install package and dependency packages Without package name, updates all installed packages Lists available updates for installed packages Removes all header files used for resolving dependencies and cached packages Lists all available packages Searches for word in package description, summary, packager, and name Groups of packages yum grouplist yum groupinfo Yumdownloader Configuration file: yum. conf CSC 252: John Carelli Source: Dr. Lisa Frye 31

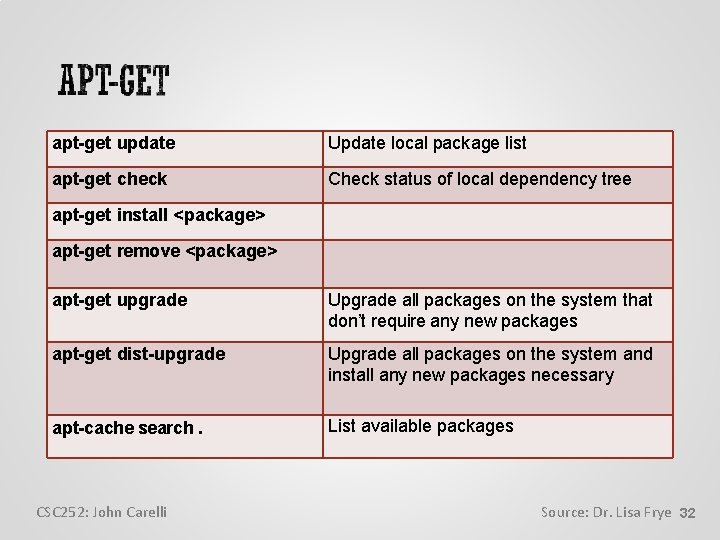
apt-get update Update local package list apt-get check Check status of local dependency tree apt-get install <package> apt-get remove <package> apt-get upgrade Upgrade all packages on the system that don’t require any new packages apt-get dist-upgrade Upgrade all packages on the system and install any new packages necessary apt-cache search. List available packages CSC 252: John Carelli Source: Dr. Lisa Frye 32

A background process that performs a specific function or system-related task CSC 252: John Carelli Source: Dr. Lisa Frye 33

SYSLOGD - system logging Syslog – standardized system for managing system log files programs write to the special file: /dev/log syslogd reads messages from this file consults configuration file: /etc/syslog. conf dispatches each message to appropriate destination Sys Admin should back up and maintain log Common Log Files /var/log/messages /var/log/auth. log /var/log/kern. log /var/log/cron. log /var/log/maillog /var/log/httpd /var/log/boot. log /var/log/mysqld. log /var/log/utmp /var/log/wtmp /var/log/yum. log files CSC 252: John Carelli Source: Dr. Lisa Frye 34

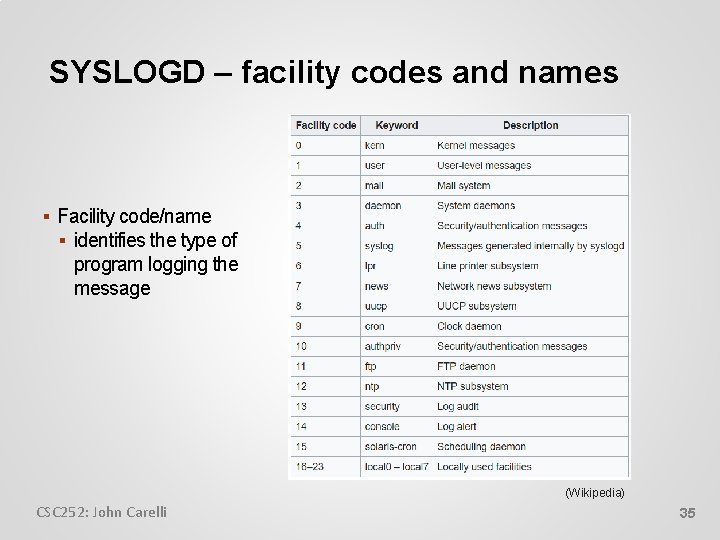
SYSLOGD – facility codes and names Facility code/name identifies the type of program logging the message (Wikipedia) CSC 252: John Carelli 35

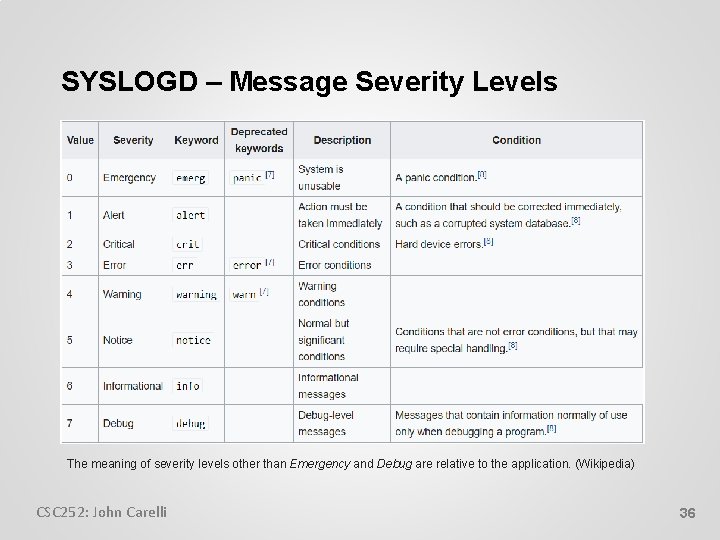
SYSLOGD – Message Severity Levels The meaning of severity levels other than Emergency and Debug are relative to the application. (Wikipedia) CSC 252: John Carelli 36

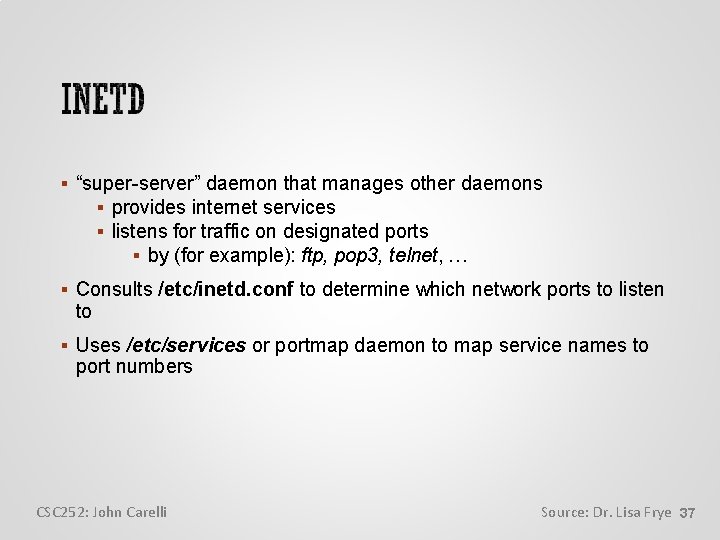
“super-server” daemon that manages other daemons provides internet services listens for traffic on designated ports by (for example): ftp, pop 3, telnet, … Consults /etc/inetd. conf to determine which network ports to listen to Uses /etc/services or portmap daemon to map service names to port numbers CSC 252: John Carelli Source: Dr. Lisa Frye 37

1 3 4 service name type of socket service used (stream or dgram) communication protocol service uses (tcp or udp) wait: service can process multiple requests at one 5 6 nowait - fork a new copy of daemon for each request username under which daemon should run fully qualified pathname of the daemon and its 2 time CSC 252: John Carelli command-line arguments Source: Dr. Lisa Frye 38

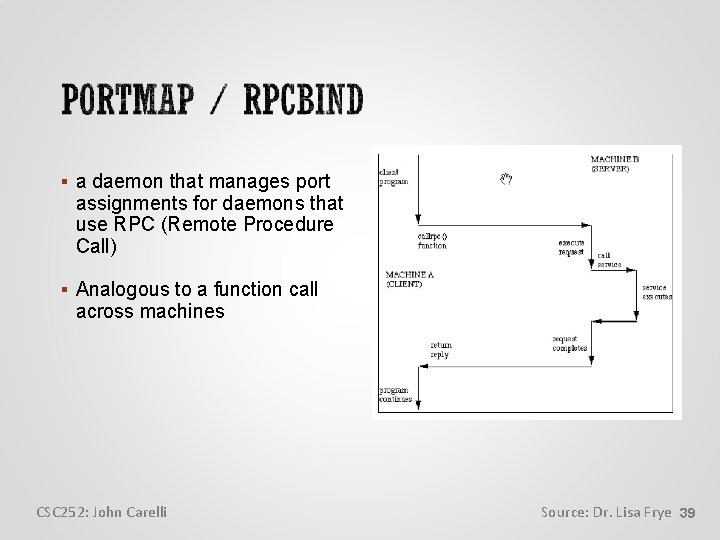
a daemon that manages port assignments for daemons that use RPC (Remote Procedure Call) Analogous to a function call across machines CSC 252: John Carelli Source: Dr. Lisa Frye 39

Report on virtual memory usage Two arguments number of seconds between measuring and reporting values number of times to measure and report values Report First line will be average values since last system reboot Other lines represents current values man vmstat CSC 252: John Carelli Source: Dr. Lisa Frye 40

Report on network connection information Common options netstat –v # verbose netstat –nt # tcp, numeric addresses netstat –nl # listening sockets, numeric addresses netstat –i # interfaces netstat –rn # route, numeric addresses netstat –s # summary statistics CSC 252: John Carelli Source: Dr. Lisa Frye 41
 Carelli kutztown
Carelli kutztown John carelli kutztown
John carelli kutztown Carelli kutztown
Carelli kutztown Carelli
Carelli Carelli kutztown
Carelli kutztown Parson kutztown
Parson kutztown Carelli kutztown
Carelli kutztown Carelli kutztown
Carelli kutztown Edu.sharif.edu
Edu.sharif.edu Spiegel kutztown
Spiegel kutztown Parson weems fable
Parson weems fable Participante contreras
Participante contreras Basic instructor course tcole
Basic instructor course tcole Basic instructor course texas
Basic instructor course texas Basic instructor course #1014
Basic instructor course #1014 Pepperball launcher nomenclature
Pepperball launcher nomenclature Subject verb agreement exercise
Subject verb agreement exercise Instructor vs teacher
Instructor vs teacher Cisco certified instructor
Cisco certified instructor Mptc instructor
Mptc instructor Basic instructor course #1014
Basic instructor course #1014 Basic instructor course texas
Basic instructor course texas Virtual instructor.com
Virtual instructor.com Nfpa 1403
Nfpa 1403 Tp 12863
Tp 12863 Instructor operating station
Instructor operating station Catia instructor
Catia instructor Instructor
Instructor Instructor responsibilities and professionalism lesson plan
Instructor responsibilities and professionalism lesson plan Tcole 1014 basic instructor course
Tcole 1014 basic instructor course Usmc jrotc vacancies
Usmc jrotc vacancies Nrp instructor toolkit
Nrp instructor toolkit Utp cable
Utp cable What is cbrf training
What is cbrf training Nra certified instructor logo
Nra certified instructor logo Naismith was an instructor of
Naismith was an instructor of Please clean your own room
Please clean your own room Tcole advanced instructor course
Tcole advanced instructor course Tcole advanced instructor course
Tcole advanced instructor course Jrotc marksmanship instructor course online
Jrotc marksmanship instructor course online Forced perspective room
Forced perspective room Calcaneum plural
Calcaneum plural