Java Virtual Machine Student Name Wei Liu Student





- Slides: 21

Java Virtual Machine Student Name: Wei Liu Student ID: 104076 1

Java Virtual Machine w JVM is part of Java programming language. w JVM is a software, staying on top of Operating System, such as UNIX, Windows NT. w It help Java create high level of portability by hiding the difference between the Operating System implementations. w It creates an environment that Java language lives. 2

Why JVM? w An ordinary language can not create a system independent program. w Java’s goal is “Write-Once-Run-Anywhere”. Java programs are not computer, operating system dependent. w Need to create an “abstract computer” of its own and runs on it, a kind of virtual machine which hiding the different OS implementations. 3

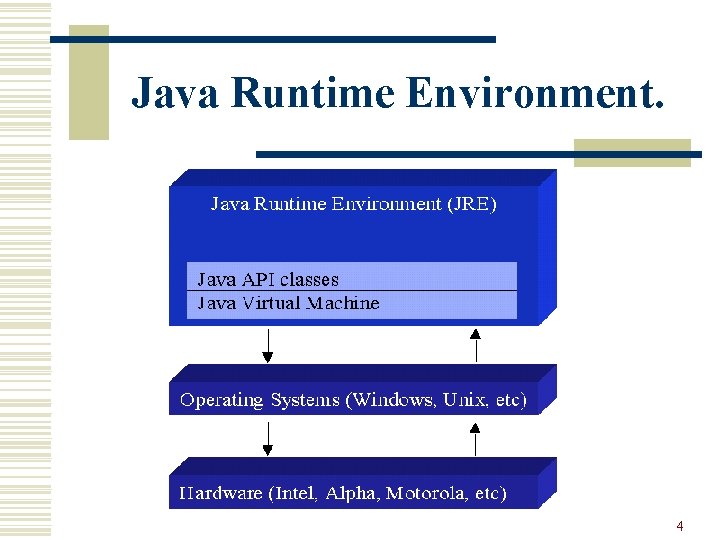
Java Runtime Environment. 4

How JVM works? w Java programs are compiled into byte code. w JVM interprets and converts Java byte code into machine code in order to execute on a CPU. w Most web browser has an integrated JVM to run applets. 5

How JVM works? w Other JVM tasks include: w Object creations of Java programs. w Garbage collection. w Security responsibility. 6

JVM Fundamental Parts. w w w A byte code instruction set A set of registers A stack A garbage-collected heap An area for storing methods All five parts are necessary, may be implemented by a compiler, an interpreter or a hardware chip. 7

Byte Code Instruction Set w JVM keeps a compact set of Byte Code Instructions in order to interpret byte code into native binary code. w Java compilers do not translate programs directly into native binary code, which is system dependent. Instead, programs are translated into byte code, just in its mid-way to a runnable. w JVM interprets these half-cooked byte code into executable machine code on different computer systems and platforms. 8

Registers. w The registers of the Java virtual machine are just like the registers inside a “real” computer. (32 bit wide) w PC: program counter w OPTOP: Pointer to operation stack. w FRAME: Pointer to execution environment of current method. w VARS: Pointer to the first local variable of current method. 9

Stacks w JVM is stack based. w The stack is used to supply parameters to byte codes and methods, and to receive results back from them. w Each stack frame contains three (possibly empty) sets of data: the local variables for the method call, its execution environment, and its operand stack. 10

Heaps. w The heap is that part of memory from which newly created instances (objects) are allocated. w The heap is often assigned a large, fixed size when the Java run-time system is started, but on systems that support virtual memory, it can grow as needed, in a nearly unbounded fashion. w Objects in heap are automatically garbage-collected when they are not needed. 11

The Method Area. w The method area stores the Java byte codes that implement almost every method in the Java system. w The method area also stores the symbol tables needed for dynamic linking, and any other additional information debuggers or development environments might want to associate with each method’s implementation. 12

Drawbacks of JVM. w JVM is a layer on the top of your operating system that consumes additional memory. w JVM is additional layer between compiler and machine. (Comparing Java program and fast C program!) w Byte code is compiled for system independence so it does not take advantage of any particular operating system. 13

JIT Compiler. w JIT stands for “Just In Time”. w 10 years ago, a smart idea was discovered by Peter Deutsch while trying to make Smalltalk run faster. He called it “dynamic translation” during interpretation. w Every time JIT compiler interprets byte codes, it will keep the binary code in log and optimize it. Next time, when the same method is running, the optimized code will run. Experiments show Java programs using JIT could be as fast as a compiled C program. 14

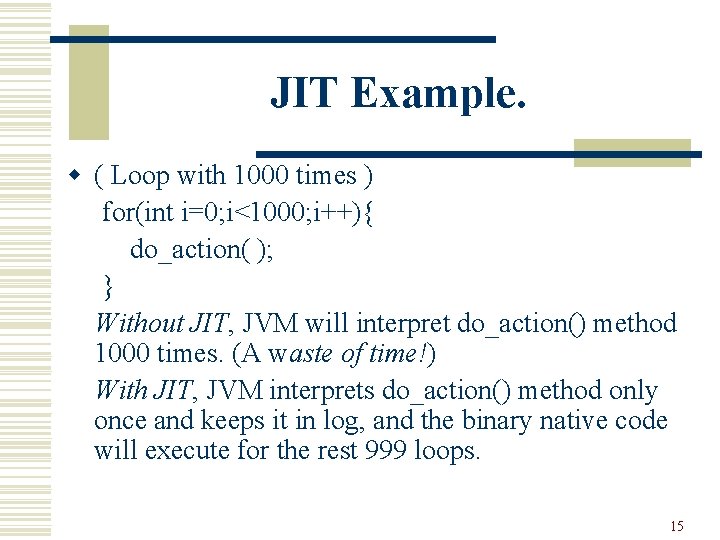
JIT Example. w ( Loop with 1000 times ) for(int i=0; i<1000; i++){ do_action( ); } Without JIT, JVM will interpret do_action() method 1000 times. (A waste of time!) With JIT, JVM interprets do_action() method only once and keeps it in log, and the binary native code will execute for the rest 999 loops. 15

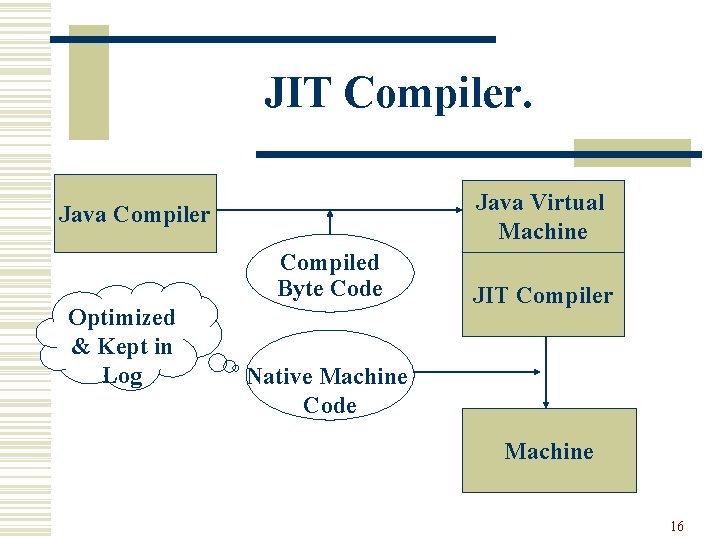
JIT Compiler. Java Virtual Machine Java Compiler Compiled Byte Code Optimized & Kept in Log JIT Compiler Native Machine Code Machine 16

JVM Security Capability. w JVM has many capabilities to keep the security of the computer system. w “Sandbox”: prohibit a Java applet: w Reading or writing to the local disk w Making a network connection to any host, except the host from which the applet came w Creating a new process w Loading a new dynamic library and directly calling a native method 17

Security Holes of JVM w Netscape 4. X consists of JVM that has flaws. w A hostile applet could turn the client browser into an http server that allows almost anyone in the world to read/modify/delete files residing on the client (turned server) machine. w Ways to deal with “malicious” applets. 18

Current JVM. w Microsoft Java Virtual Machine. w Netscape Java Virtual Machine. w Sun Java Virtual Machine. w All these Java Virtual Machines implement Java core class packages and their own specific class packages. 19

References. w w w w http: //java. sun. com http: //www. cs. princeton. edu http: //www. research. IBM. com http: //www. javaworld. com http: //www. sans. org http: //www. javacoffeebreak. com http: //www. computerworld. com http: //www. zdnet. com 20

Questions? 21