Java Security Session 19 Objectives n n Explain
Java Security Session 19

Objectives n n Explain the Java Security Model Discuss each of the components that comprise the JSM Describe the security tools available as part of the Java platform Discuss Java cryptography Java Security / 2 of 23

Introduction n n Security of precious goods is only as good as the defense mechanism employed to guard it Security on the Internet is a big issue today n n Corruption of data Denial of access to services Attacks that simply annoy users Security model in Java 2 has been enhanced to enable digitally signed applets to be run on the web Java Security / 3 of 23
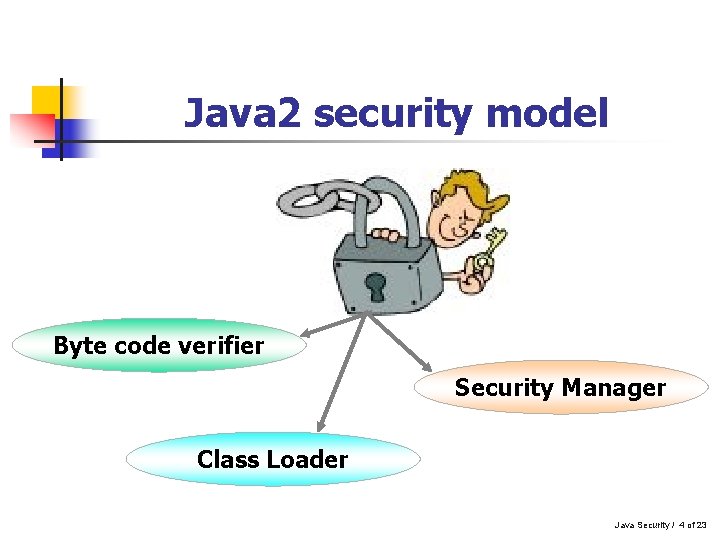
Java 2 security model Byte code verifier Security Manager Class Loader Java Security / 4 of 23

Byte Code Verifier n n Examines the byte codes of a class before executing it This verifies: n n Byte code represent legal JVM operations Possibilities of stack overflow or underflow Byte code does not compromise the type safety of operands Class methods observe all access specifiers such as public, private, etc. Java Security / 5 of 23
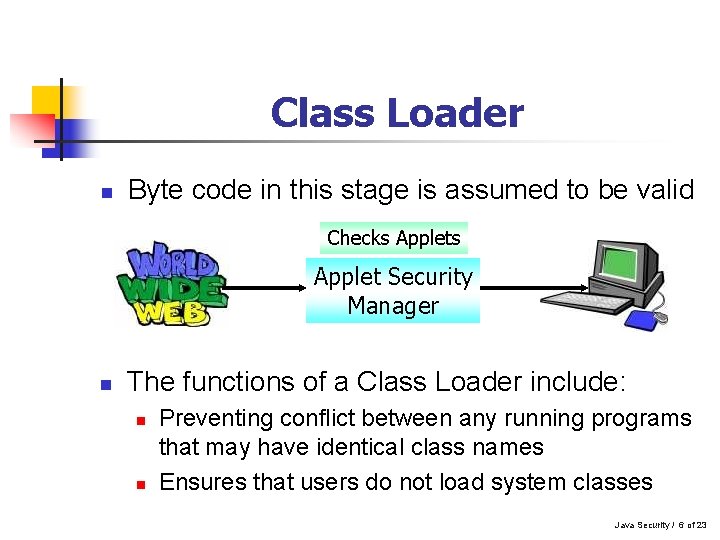
Class Loader n Byte code in this stage is assumed to be valid Checks Applet Security Manager n The functions of a Class Loader include: n n Preventing conflict between any running programs that may have identical class names Ensures that users do not load system classes Java Security / 6 of 23

Java Security Manager (JSM) n n n Standalone applications are trusted by default Applets have to be downloaded and hence can cause potential attacks Applets can only manipulate data within a specified area (sandbox) of the hard disk Security Manager provides a sandbox as well as allows one to create a sandbox JSM also controls access to important resources, operations and access to files Java Security / 7 of 23
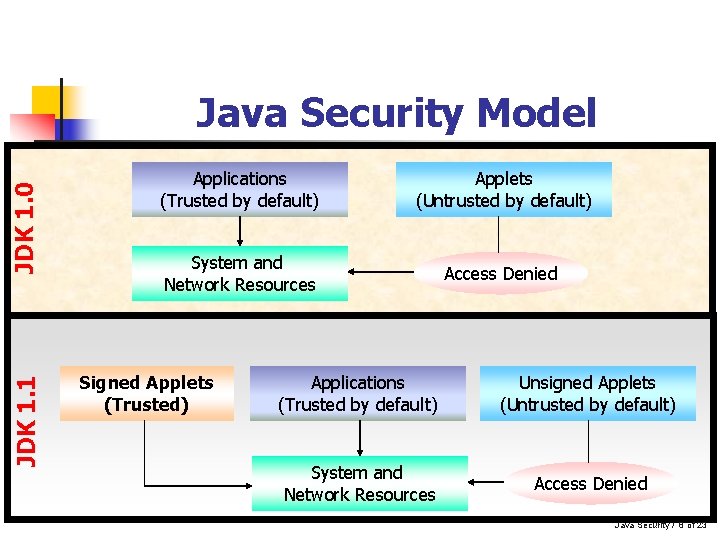
JDK 1. 1 JDK 1. 0 Java Security Model Applications (Trusted by default) Applets (Untrusted by default) System and Network Resources Access Denied Signed Applets (Trusted) Applications (Trusted by default) Unsigned Applets (Untrusted by default) System and Network Resources Access Denied Java Security / 8 of 23

java. policy file n n It is possible to specify a security policy that determines the access type an application or an applet is allowed Security policy file is located at JAVA_HOMElibsecurityjava. policy where JAVA_HOME indicates location of JDK Java Security / 9 of 23
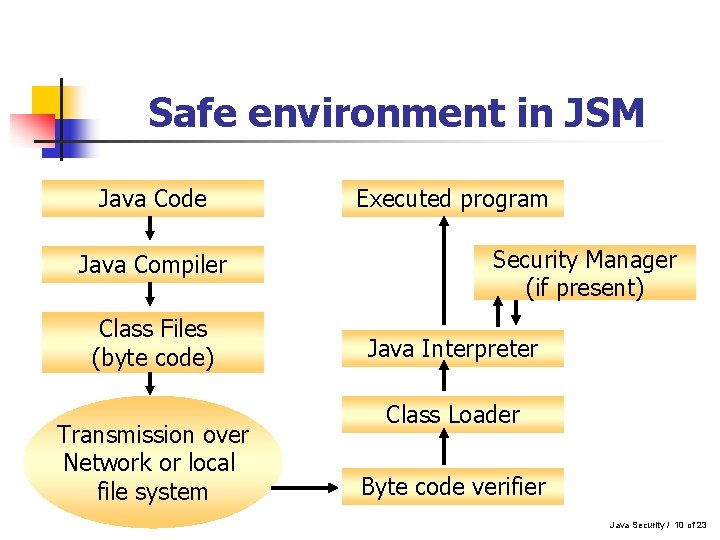
Safe environment in JSM Java Code Java Compiler Class Files (byte code) Transmission over Network or local file system Executed program Security Manager (if present) Java Interpreter Class Loader Byte code verifier Java Security / 10 of 23

JDK security tools n n n A system on the Internet should lookout for components that lay the system open to intruders Authentication is an important and vital issue A digital signature solves two vital security concerns n n n Authentication Integrity Sun offers three tools to digitally sign applets n -jar, jarsigner and keytool Java Security / 11 of 23

The keytool utility (1) n n Used to create and manage public keys, private keys and security certificates In private cryptography, a process takes a piece of data and uses a special key such as password to produce an encrypted password Only with the help of the key, one can decrypt the original message Data Encryption Standard is a widely used cryptographic system Java Security / 12 of 23

The keytool utility (2) n n Public key cryptography is based on mathematical algorithms Two keys that are mathematically related are created One for encryption and the other for decryption Used for: n n Managing public/private key pairs Storing public keys of people and groups Authentication of ones identity Verifying the source and integrity of data Java Security / 13 of 23

The keytool utility (3) n n Information managed by keytool is stored in a database called keystore One can check the existence of keystore by: n n n -genkey option of keytool creates a public/private key pair n n keytool –list –keystore C: myfoldermystore keytool –genkey –aliasname While adding a key to a new keystore, a password has to be given Java Security / 14 of 23
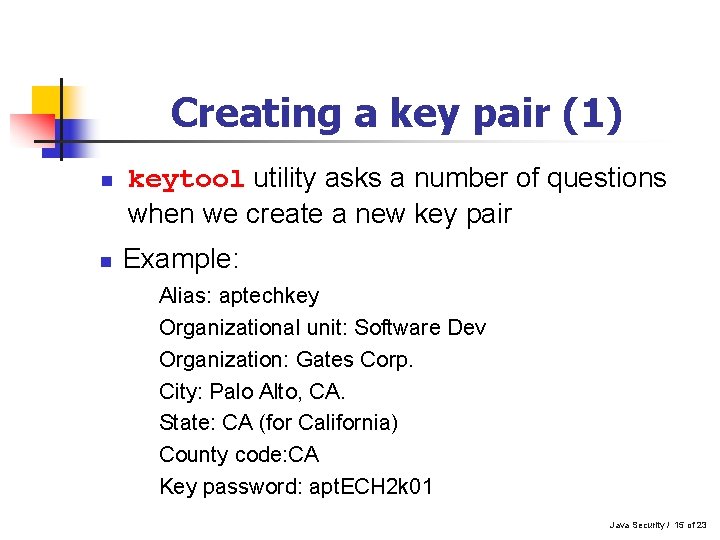
Creating a key pair (1) n n keytool utility asks a number of questions when we create a new key pair Example: Alias: aptechkey Organizational unit: Software Dev Organization: Gates Corp. City: Palo Alto, CA. State: CA (for California) County code: CA Key password: apt. ECH 2 k 01 Java Security / 15 of 23
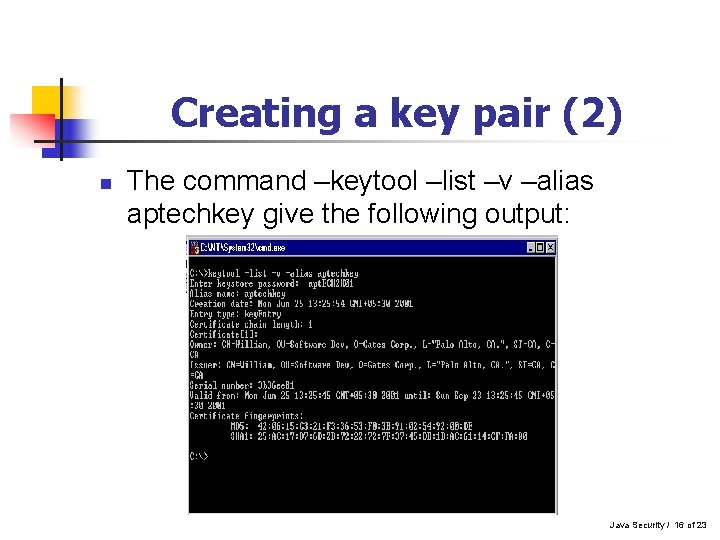
Creating a key pair (2) n The command –keytool –list –v –alias aptechkey give the following output: Java Security / 16 of 23

Working with certificates (1) n n n Statement signed by an authority Indicates that the public key of a person has important value Digital certificates associate an identity with a public key n n Identity is called subject Authority that signs is called signer Java Security / 17 of 23

Working with certificates (2) n n n keytool utility can display, import and export certificates in addition to key pairs Certificates follow the X. 509 standard When we create a new public/private keypair, a self-signed certificate signed by the same entity that created the key pair is obtained n keytool –alias aptechkey –certreq –file aptechreq. txt Java Security / 18 of 23

jar tool and jarsigner tool n n Before java program can be digitally signed, it must be packaged into an archive form consisting of all class files and other files with the help of jar tool jarsigner then digitally signs a java archive n n jarsigner My. Applet. jar aptechkey The key must have gone through a verification process before use Java Security / 19 of 23

Java Cryptography n n n Java Cryptography classes enable us to encrypt and decrypt programs It also provides passwords to secure access Java. security file should include the following line: n policy. url. 2=file: ${user. home}/. java. policy Java Security / 20 of 23
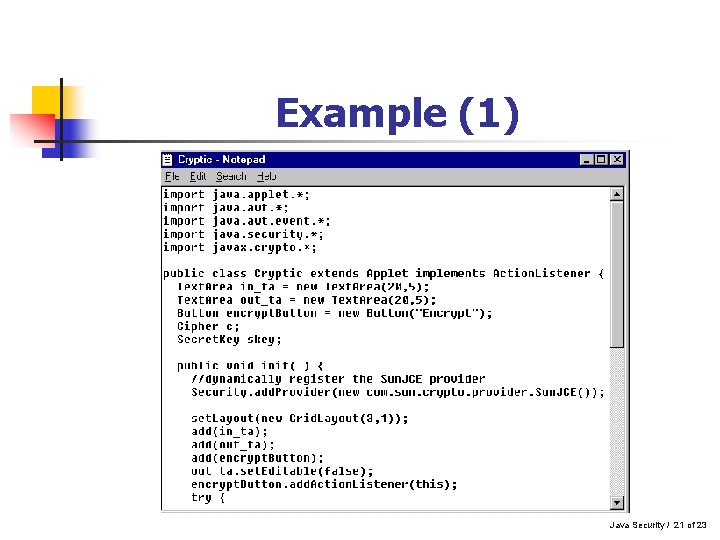
Example (1) Java Security / 21 of 23
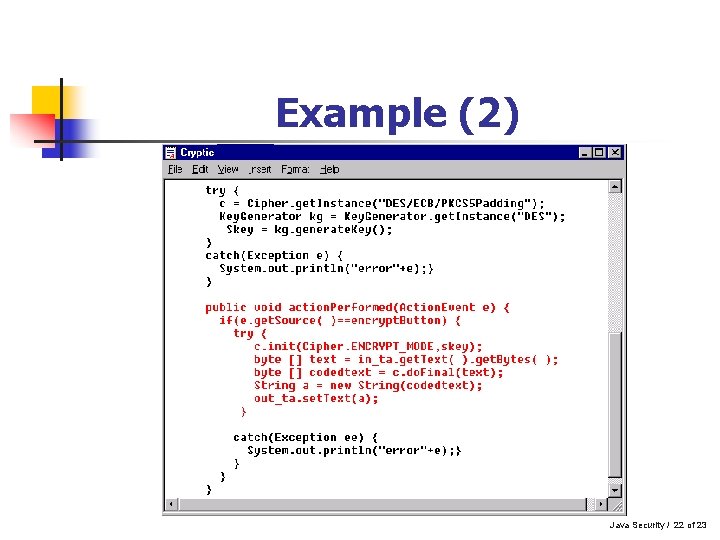
Example (2) Java Security / 22 of 23
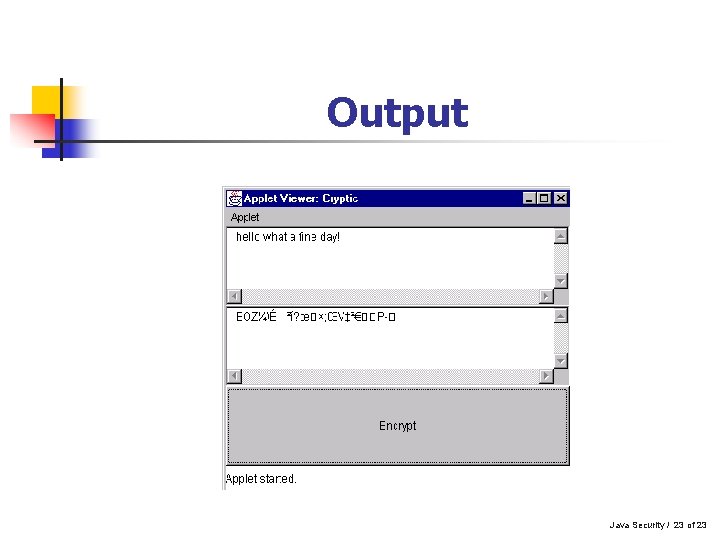
Output Java Security / 23 of 23
- Slides: 23