Java Security Overview Tools to securely manage applications







































































































- Slides: 176

Java™ Security Overview Tools to securely manage applications

Java SE Security l Java security technology includes: ¡ a set of APIs, ¡ tools, ¡ implementations security algorithms, ¡ mechanisms, ¡ protocols.

Java SE Security l The Java security APIs span a wide range of areas, including: ¡ platform Security, ¡ cryptography, ¡ authentication and access control, ¡ secure communication, ¡ public key infrastructure.

Java SE Security l Java security technology provides the developer with a comprehensive security framework for writing applications, l and also provides the user or administrator with a set of tools to securely manage applications.

1 Introduction l Java SE Security Documentation J 2 SE 1. 4. 2 | J 2 SE 5. 0 | Java SE 6

Note l There are three security extensions for use with J 2 SE 1. 3. 1. l They are Java Authentication and Authorization Service, Java Cryptography Extension, and Java Secure Socket Extension. l These three extensions have been integrated into J 2 SE 1. 4.

Java SE Security Overview l Platform Security l Cryptography l Authentication and Access Control l Secure Communications l Public Key Infrastructure (PKI)

3 Basic Security Architecture http: //java. sun. com/javase/6/docs/ technotes/guides/security/overvie w/jsoverview. html

3 Basic Security Architecture l The Java platform defines a set of APIs spanning major security areas, including cryptography, public key infrastructure, authentication, secure communication, and access control.

3 Basic Security Architecture l These APIs allow developers to easily integrate security into their application code. They were designed around the following principles:

3 Basic Security Architecture l Implementation independence Applications do not need to implement security themselves. Rather, they can request security services from the Java platform.

l Implementation independence Security services are implemented in providers (see below), which are plugged into the Java platform via a standard interface. An application may rely on multiple independent providers for security functionality.

3 Basic Security Architecture l Implementation interoperability Providers are interoperable across applications. Specifically, an application is not bound to a specific provider, and a provider is not bound to a specific application.

3 Basic Security Architecture l Algorithm extensibility The Java platform includes a number of built-in providers that implement a basic set of security services that are widely used today. However, some applications may rely on emerging standards not yet implemented, or on proprietary services. The Java platform supports the installation of custom providers that implement such services.

3 Basic Security Architecture l Security Providers l The java. security. Provider class encapsulates the notion of a security provider in the Java platform. l It specifies the provider's name and lists the security services it implements.

3 Basic Security Architecture l Security Providers l Multiple providers may be configured at the same time, and are listed in order of preference. l When a security service is requested, the highest priority provider that implements that service is selected.

3 Basic Security Architecture l Applications rely on the relevant get. Instance method to obtain a security service from an underlying provider. l For example, message digest creation represents one type of service available from providers.

3 Basic Security Architecture l An application invokes the get. Instance method in the java. security. Message. Digest class to obtain an implementation of a specific message digest algorithm, such as MD 5. Message. Digest md = Message. Digest. get. Instance("MD 5");

3 Basic Security Architecture l The program may optionally request an implementation from a specific provider, by indicating the provider name, as in the following: Message. Digest md = Message. Digest. get. Instance("MD 5", "Provider. C");

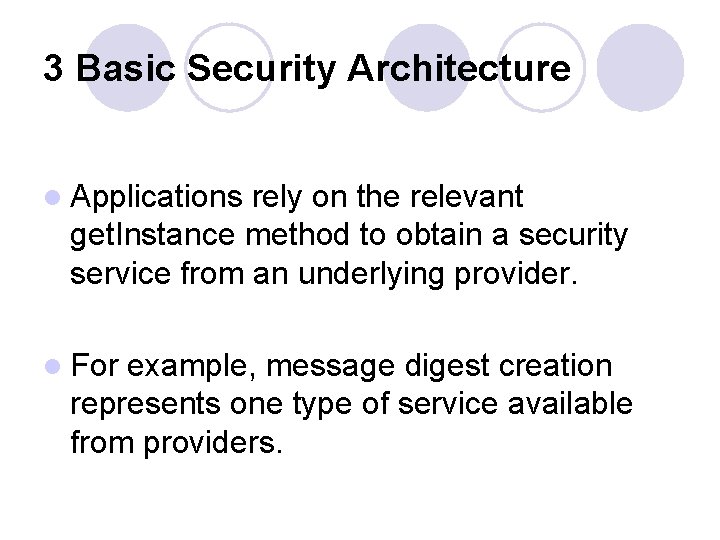
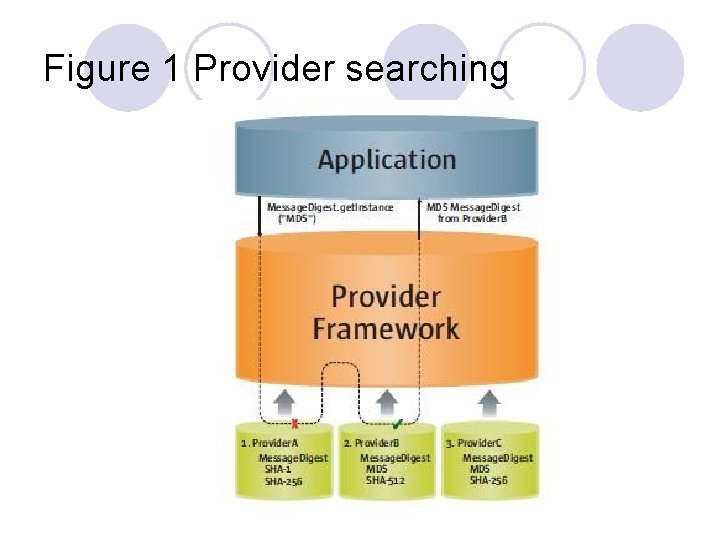
3 Basic Security Architecture l Figures 1 and 2 illustrate these options for requesting an MD 5 message digest implementation.

3 Basic Security Architecture l Both figures show three providers that implement message digest algorithms. The providers are ordered by preference from left to right (1 -3).

3 Basic Security Architecture l In Figure 1, an application requests an MD 5 algorithm implementation without specifying a provider name.

3 Basic Security Architecture l The providers are searched in preference order and the implementation from the first provider supplying that particular algorithm, Provider. B, is returned.

Figure 1 Provider searching

3 Basic Security Architecture l In Figure 2, the application requests the MD 5 algorithm implementation from a specific provider, Provider. C.

3 Basic Security Architecture l This time the implementation from that provider is returned, even though a provider with a higher preference order, Provider. B, also supplies an MD 5 implementation.

Figure 2 Specific provider requested

3 Basic Security Architecture l The Java platform implementation from Sun Microsystems includes a number of pre-configured default providers that implement a basic set of security services that can be used by applications.

3 Basic Security Architecture l Note that other vendor implementations of the Java platform may include different sets of providers that encapsulate vendorspecific sets of security services.

3 Basic Security Architecture l When this paper mentions built-in default providers, it is referencing those available in Sun's implementation.

3 Basic Security Architecture l The sections below on the various security areas (cryptography, authentication, . . ) each include descriptions of the relevant services supplied by the default providers. l A table in Appendix C summarizes all of the default providers.

3 Basic Security Architecture l File Locations l Certain aspects of Java security mentioned in this paper, including the configuration of providers, may be customized by setting security properties.

3 Basic Security Architecture l You may set security properties statically in the security properties file, which by default is the java. security file in the lib/security directory of the directory where the Java™ Runtime Environment (JRE) is installed.

3 Basic Security Architecture l Security properties may also be set dynamically by calling appropriate methods of the Security class (in the java. security package).

3 Basic Security Architecture l The tools and commands mentioned in this paper are all in the ~jre/bin directory, where ~jre stands for the directory in which the JRE is installed.

3 Basic Security Architecture l The cacerts file mentioned in Section 5 is in: ~jre/lib/security.

4 Cryptography

4 Cryptography l The Java cryptography architecture is a framework for accessing and developing cryptographic functionality for the Java platform. l It includes APIs for a large variety of cryptographic services, including: . . .

4 Cryptography l l l Message digest algorithms Digital signature algorithms Symmetric bulk encryption Symmetric stream encryption Asymmetric encryption Password-based encryption (PBE) Elliptic Curve Cryptography (ECC) Key agreement algorithms Key generators Message Authentication Codes (MACs) (Pseudo-) random number generators

4 Cryptography l For historical (export control) reasons, the cryptography APIs are organized into two distinct packages as follow: l The java. security package contains classes that are not subject to export controls (like Signature and Message. Digest).

4 Cryptography l The javax. crypto package contains classes that are subject to export controls (like Cipher and Key. Agreement).

4 Cryptography l The cryptographic interfaces are provider- based, allowing for multiple and interoperable cryptography implementations.

4 Cryptography l Some providers may perform cryptographic operations in software; l Others may perform the operations on a hardware token (for example, on a smartcard device or on a hardware cryptographic accelerator).

4 Cryptography l Providers that implement export-controlled services must be digitally signed. l The Java platform includes built-in providers for many of the most commonly used cryptographic algorithms, including:

4 Cryptography ¡ RSA, ¡ DSA signature algorithms, ¡ DES, AES, ¡ ARCFOUR encryption algorithms, ¡ MD 5 and SHA-1 message digest algorithms, ¡ Diffie-Hellman key agreement algorithm.

PKCS – Public Key Cryptography Standards l In cryptography, PKCS refers to a group of Public Key Cryptography Standards devised and published by RSA Security.

PKCS l RSA Data Security Inc was assigned the licensing rights for the patent on the RSA asymmetric key algorithm and acquired the licensing rights to several other key patents as well (e. g. , the Schnorr patent).

PKCS l As such, RSA Security, and its research division, RSA Labs, were interested in promoting and facilitating the use of public-key techniques. To that end, they developed the PKCS standards.

PKCS l The several PKCS standards can be viewed at: http: //en. wikipedia. org/wiki/PKCS

PKCS #5 l 2. 0 l Password-based Encryption Standard l See RFC 2898 and PBKDF 2.

PKCS #6 l V 1. 5 l Extended-Certificate Syntax Standard l Defines extensions to the old v 1 X. 509 certificate specification. l Obsoleted by v 3 of the same.

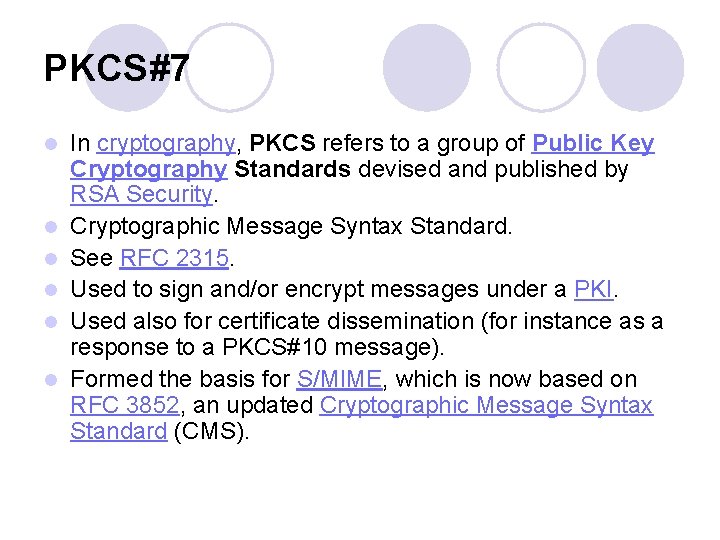
PKCS#7 l l l In cryptography, PKCS refers to a group of Public Key Cryptography Standards devised and published by RSA Security. Cryptographic Message Syntax Standard. See RFC 2315. Used to sign and/or encrypt messages under a PKI. Used also for certificate dissemination (for instance as a response to a PKCS#10 message). Formed the basis for S/MIME, which is now based on RFC 3852, an updated Cryptographic Message Syntax Standard (CMS).

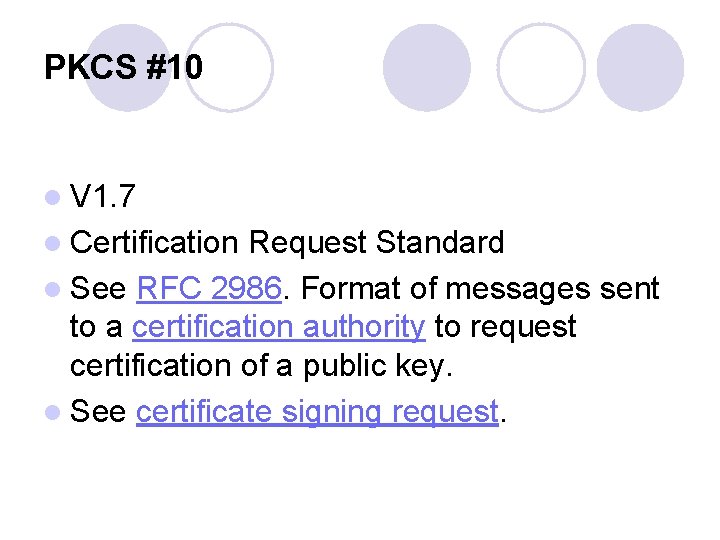
PKCS #10 l V 1. 7 l Certification Request Standard l See RFC 2986. Format of messages sent to a certification authority to request certification of a public key. l See certificate signing request.

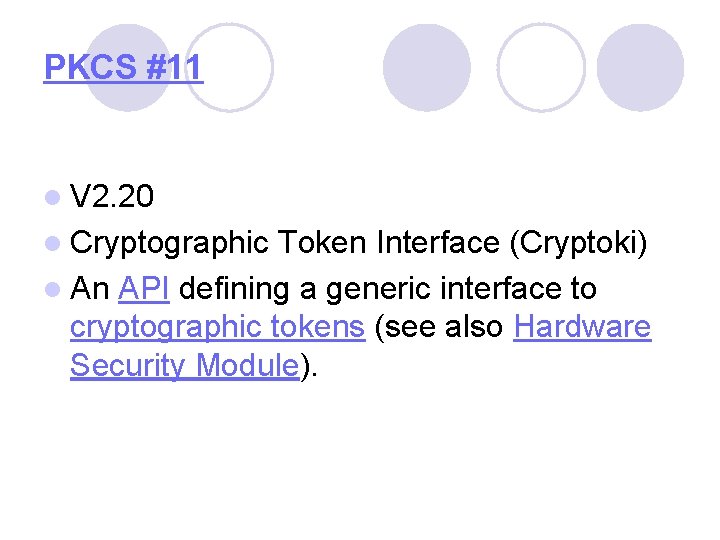
PKCS #11 l V 2. 20 l Cryptographic Token Interface (Cryptoki) l An API defining a generic interface to cryptographic tokens (see also Hardware Security Module).

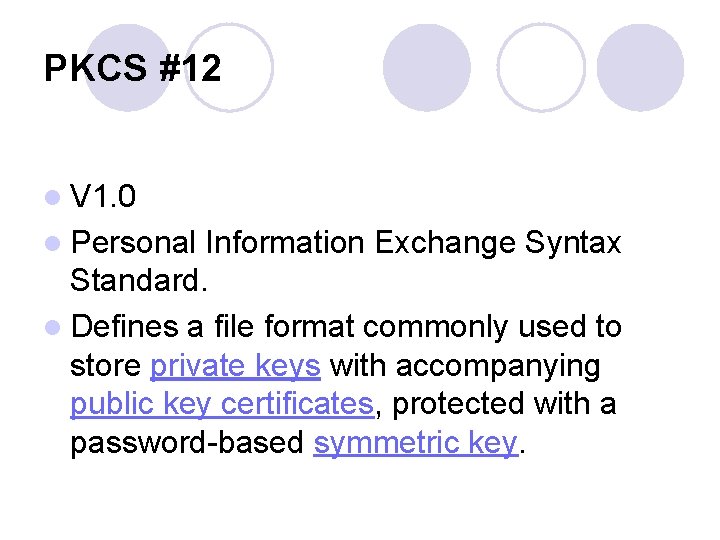
PKCS #12 l V 1. 0 l Personal Information Exchange Syntax Standard. l Defines a file format commonly used to store private keys with accompanying public key certificates, protected with a password-based symmetric key.

PKCS #15 V 1. 1 Cryptographic Token Information Format Standard. l Defines a standard allowing users of cryptographic tokens to identify themselves to applications, independent of the application's Cryptoki implementation (PKCS #11) or other API. l RSA has relinquished IC-card-related parts of this standard to ISO/IEC 7816 -15. [1] l l

4 Cryptography l These default providers implement cryptographic algorithms in Java code. l The Java platform also includes a built-in provider that acts as a bridge to a native PKCS#11 (v 2. x) token.

4 Cryptography l This provider, named Sun. PKCS 11, allows Java applications to seamlessly access cryptographic services located on PKCS#11 -compliant tokens.

Security Token l A security token (or sometimes a hardware token, authentication token or cryptographic token[1]) may be a physical device that an authorized user of computer services is given to aid in authentication. The term may also refer to software tokens.

Several types of security tokens.

Security Token l Hardware tokens are typically small enough to be carried in a pocket or purse and often are designed to attach to the user's keychain.

Security Token l Some may store cryptographic keys, such as a digital signature, or biometric data, such as a fingerprint.

Security Token l Some designs feature tamper resistant packaging, other may include small keypads to allow entry of a PIN.

Secur. ID tokens from RSA Security.

e. Token tokens from Aladdin Knowledge Systems

Activ. Identity Tokens.

5 Public Key Infrastructure

Public Key Infrastructure (PKI) l Tools for managing keys and certificates and comprehensive, abstract APIs with support for the following features and algorithms:

Public Key Infrastructure (PKI) l Certificates and Certificate Revocation Lists (CRLs): X. 509 l Certification Path Validators and Builders: PKIX (RFC 3280), On-line Certificate Status Protocol (OCSP)

Public Key Infrastructure (PKI) l Key. Stores: PKCS#11, PKCS#12 l Certificate Stores (Repositories): LDAP, java. util. Collection

Java ™ Cryptography Architecture (JCA) Reference Guide l for Java. TM Platform Standard Edition 6 l http: //java. sun. com/javase/6/docs/technote s/guides/security/crypto/Crypto. Spec. html l includes the Java Cryptographic Extension (JCE)


6 Authentication

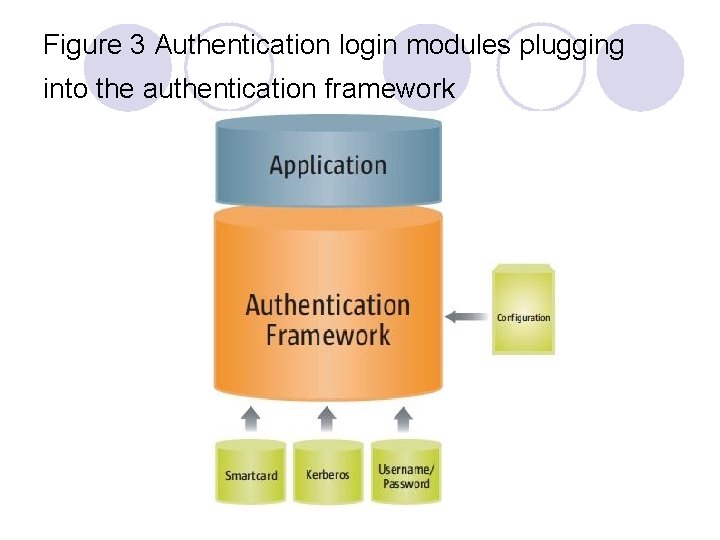
l Abstract authentication APIs that can incorporate a wide range of login mechanisms through a pluggable architecture.

l A comprehensive policy and permissions API that allows the developer to create and administer applications requiring finegrained access to security-sensitive resources.

JAAS l Java Authentication and Authorization Service (JAAS) l Reference Guide l for the Java TM SE Development Kit 6

JAAS l http: //java. sun. com/javase/6/docs/technote s/guides/security/jaas/JAASRef. Guide. html


Figure 3 Authentication login modules plugging into the authentication framework


7 Secure Communication

8 Access Control

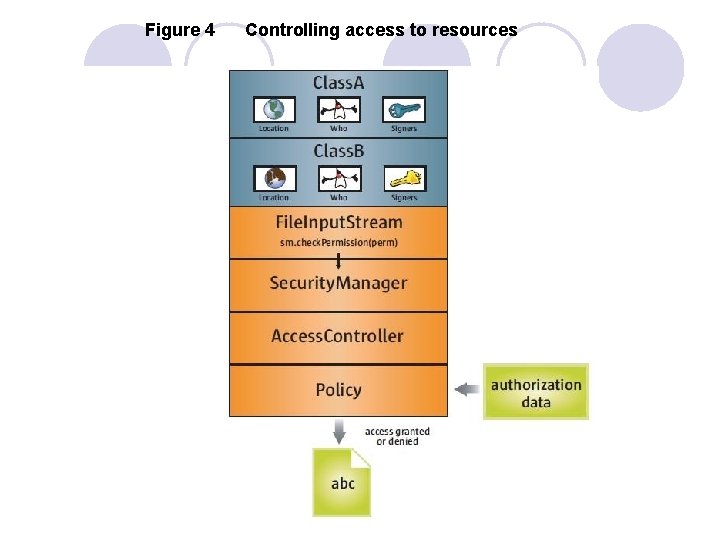
Figure 4 Controlling access to resources

User Guides

l Java SE 6 Security Documentation l Extensive information on the security features of the Java SE 6 release, including reference guides, API specifications (javadocs), tool documentation, and tutorials.

l Java 2 SDK, v 5. 0 Security Documentation l Extensive information on the security features of the Java 2 SDK, v 5. 0 release, including reference guides, API specifications (javadocs), tool documentation, and tutorials.

l Java 2 SDK, v 1. 4 Security Documentation l Extensive information on the security features of the Java 2 SDK, v 1. 4 release, including reference guides, API specifications (javadocs), tool documentation, and tutorials.

l Security Code Guidelines l Some guidelines to allow you to take full advantage of the security provided by the Java platform.

l JAR Guide l A short introduction to using the JAR tool to create JAR files. This describes the applet tag syntax for associating an applet with a. JAR file, instead of a. class file.

l JAR File Specification l JAR file is a file format based on the popular ZIP file format and is used for aggregating many files into one.

l Deploying signed applets in Java Plug- in l A pointer to the Java Plug-in developer guide. l The guide includes a chapter on security and the signed applet support in Java Plug-in, . . .

l. . . which allows users to grant (signed) applets all permissions based on their authenticated signers, without having to configure and deploy any policy or keystore configuration files.

Security Tools Documentation

keytool l Solaris/Linux and Microsoft Windows ¡ keytool is a utility for creating and managing keystores and certificates.

jarsigner l Solaris/Linux and Microsoft Windows ¡ jarsigner is a utility for generating and verifying JAR signatures.

Policy Tool l Solaris/Linux and Microsoft Windows ¡ Policy tool is a GUI tool for creating and managing policy files.

kinit l Microsoft Windows ¡ kinit is a utility for obtaining Kerberos v 5 tickets.

klist l Microsoft Windows ¡ klist is a utility to list entries in a Kerberos v 5 credential cache and key tab.

ktab l Microsoft Windows ¡ ktab is a utility to help the user manage entries in the key table.

Java Security Feedback Alias

l Java Security Feedback Alias l Information about the java- security@sun. com alias, and an online archive of the questions, comments, and answers from the alias.

Products and Technologies

JAAS l Java Authentication and Authorization Service (JAAS)

JAAS l The Java Authentication and Authorization Service (JAAS) is a set of APIs that enable services to authenticate and enforce access controls upon users.

JAAS l It implements a Java technology version of the standard Pluggable Authentication Module (PAM) framework, and supports user-based authorization. » Read More

JAAS l JAAS has now been integrated into the Java 2 SDK, version 1. 4.

JAAS - What’s new – J 2 ME l November 2006 l Foundation Profile 1. 1 JSR 219 l An expert group working via the Java Community Process has defined an optional package comprising the. . .

JAAS in J 2 ME l. . . Java Secure Socket Extension (JSSE), Java Cryptography Extension (JCE), and Java Authentication and Authorization Service (JAAS) APIs for use with Java 2 Platform, Micro Edition Foundation Profile implementations.

JCE l Java Cryptography Extension (JCE)

JCE l The Java Cryptography Extension (JCE) is a set of packages that provides a framework and implementations for: ¡ encryption, ¡ key generation and key agreement, ¡ Message Authentication Code (MAC) algorithms.

JCE l Support for encryption includes symmetric, asymmetric, block, and stream ciphers. The software also supports secure streams and sealed objects.

l JCE in J 2 SE (included as part of J 2 SE 1. 4. x and later)

JCE – What’s new - J 2 ME l June 2003 l Foundation Profile 1. 1 JSR 219 l An expert group working via the Java Community Process has defined an optional package comprising the. . .

JCE in J 2 ME l Java Secure Socket Extension (JSSE), Java Cryptography Extension (JCE), and Java Authentication and Authorization Service (JAAS) APIs for use with Java 2 Platform, Micro Edition (J 2 ME) Foundation Profile implementations.

JSSE l Java Secure Socket Extension (JSSE)

JSSE l The Java Secure Socket Extension (JSSE) is a set of packages that enable secure Internet communications.

JSSE l It implements a Java technology version of Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols.

JSSE l It includes functionality for data encryption, server authentication, message integrity, and optional client authentication.

JSSE l JSSE in J 2 SE (included as part of J 2 SE 1. 4. x and later)

What's New in JSSE l June 2003 l Foundation Profile 1. 1 JSR 219 l An expert group working via the Java Community Process has defined an optional package comprising the

JSSE in J 2 ME l. . . Java Secure Socket Extension (JSSE), Java Cryptography Extension (JCE), and Java Authentication and Authorization Service (JAAS) APIs for use with Java 2 Platform, Micro Edition (J 2 ME) Foundation Profile implementations.

Security Resources Free Advice from Security Experts

Free Advice from Security Experts l Sun has compiled its knowledge from over two decades of secure IT designs and deployments. l The resulting architectural blueprints and tools will help you simplify, enhance, and automate security controls throughout your enterprise.

l Developing a Security Policy (PDF) This article details the importance of security policies and the basic steps involved.

l Secure by Design Sun. com Feature Story featuring "10 Steps to Better Security"

l Security Executive Brief (PDF) A printable overview of Sun's vision, methodology, and portfolio

l Systemic Security Executive Overview Presentation (PDF) l Systemic Security Architectural Patterns Presentation (PDF)

Security Alert Feed l Get alerts and solutions for security vulnerabilities directly from the Sun experts

White Papers l These business and technical papers help security and IT professionals understand Sun's recommended approaches and tactics for managing real-world security and compliance goals. More

Webcasts l Listen to and watch Sun's Security Net. Talks. l These on-demand webcasts provide practical and detailed recommendations from Sun and industry experts. l Easy and convenient expertise, ready when you are. More

Reference Documentation l Read Sun's extensive documentation of accrued knowledge on security technology and implementation. l These technical guides are for practitioners -- architects, developers, and system administrators who need tools today. l More

Sun Security Blueprints and Books l Search on security on this site to find the most popular and prolific topic on Sun's free best practices site. l Learn More

Mobile Java Tecnology

Mobile Java Tecnology l Introduction to Mobile Java Technology To develop applications using wireless Java technology, you'll need to assimilate information from several fields.

Mobile Java Tecnology l You'll need to understand something about wireless communications technology, the business of wireless communications, and a lot about the Java platform.

Mobile Java Tecnology l Where should you begin? This page contains a high-level overview of wireless Java technology and many links to detailed information about specific subjects.

l March 7, 2007 An Introduction to the PIM API for Java ME The SDN Mobile Java site is presenting a six part series on the Personal Information Management API (JSR 75). Java ME expert and JCP member Enrique Ortiz provides the definitive text on the PIM API. Jump on Part 1 now and be prepared for the rest of the series in the coming weeks. » Read more

l March 16, 2007 Using the PIM API for Java ME, Part 2 - Portability Considerations In this installment Enrique explores how to test for PIM API presence on your device and test for presence of the various databases and fields. Learn how to navigate the API and build robust applications. » Read more

l March 20, 2007 Using the PIM API for Java ME, Part 3 - Security Considerations Will your application protect the user's address book, calendar and to-do list? In part 3 learn how PIM is designed to work in conjunction with the MIDP 2. 0 security framework. » Read more

March 26, 2007 Design Consideration for Using the PIM API for Java ME l Welcome to Part 4 of the PIM API series. l Now it's time to explore design issues that will affect how your application is developed. l Read this, then start your application design. » Read more l

l April 2, 2007 Managing Personal Information - Using the PIM API for Java ME In the penultimate article in the PIM API series Enrique presents sample source. Small examples of how to do everything from retrieving the names of PIM databases through PIM create/read/update/delete operations to exception handling. Now it's time to play. » Read more

l April 10, 2007 Managing Personal Information - Summary of PIM Fields l In the final installment, it is provided an extensive reference on the PIM fields and pointers to related on-line resources. l Now you have it all. » Read more

The J 2 ME Universe

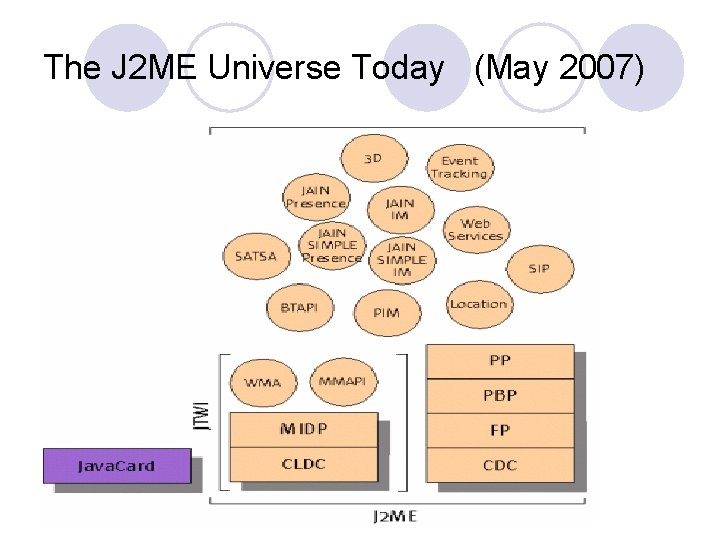
J 2 ME l The current universe of configurations, profiles and optional packages is shown in the diagram below. l The tables immediately following provide more details about the abbreviations in the figure.

The J 2 ME Universe Today (May 2007)

Overview of J 2 ME l Unlike J 2 SE, J 2 ME is not a piece of software, nor is it a single specification. l This difference can be confusing, even for developers who are already familiar with J 2 SE.

Overview of J 2 ME l Instead, J 2 MEis a platform, a collection of technologies and specifications that are designed for different parts of the small device market. l Because J 2 ME spans such a variety of devices, it wouldn't make sense to try to create a one-size-fits-all solution.

Overview of J 2 ME l J 2 ME, therefore, is divided into configurations, profiles, and optional packages. l Configurations are specifications that detail a virtual machine and a base set of APIs that can be used with a certain class of device.

Overview of J 2 ME l A configuration, for example, might be designed for devices that have less than 512 KB of memory and an intermittent network connection.

Overview of J 2 ME l The virtual machine is either a full Java Virtual Machine 1 (as described in the specification) or some subset of the full JVM 1. l The set of APIs is customarily a subset of the J 2 SE APIs.

Overview of J 2 ME l A profile builds on a configuration but adds more specific APIs to make a complete environment for building applications.

Overview of J 2 ME l While a configuration describes a JVM 1 and a basic set of APIs, it does not by itself specify enough detail to enable you to build complete applications. l Profiles usually include APIs for application life cycle, user interface, and persistent storage.

Overview of J 2 ME l An optional package provides functionality that may not be associated with a specific configuration or profile.

Overview of J 2 ME l One example of an optional package is the Bluetooth API (JSR 82), which provides a standardized API for using Bluetooth networking. l This optional package could be implemented alongside virtually any combination of configurations and profiles.

The Java Community Process JCP

The Java Community Process (JCP) l Specifications for J 2 SE, J 2 EE, and J 2 ME are developed under the aegis of the Java Community Process (JCP).

The Java Community Process (JCP) l A specification begins life as a Java Specification Request (JSR). l An expert group consisting of representatives from interested companies is formed to create the specification.

The Java Community Process (JCP) l The JSR then passes through various stages in the JCP before it is finished. Every JSR is assigned a number. l J 2 ME specifications are commonly referred to by their JSR number.

Overview of Wireless Communications

Overview of Wireless Communications l Wireless communications is a huge field, encompassing everything from radio and television broadcasting through pagers, mobile phones, and satellite communications.

l The field of mobile phones is expanding very fast at the same time that standards and protocols are being adopted, used, updated, and sometimes discarded.

l The other rapidly expanding part of the wireless world is that of wireless local area networks (LANs).

l Driven by widespread acceptance of the IEEE 802. 11 standard, wireless local networking for computers and other devices is spreading rapidly.

l Although wireless may seem like a special case, it is actually more intuitive and more natural than wired networking. l Some day soon the need to plug a laptop into a network physically will seem quaint and antiquated.

l The notion that you could walk into a room with your cell phone and have it unable to interact with other devices in the room will seem unbelievably primitive. l The future will reveal that wired networks are the special case.

l Conceptually, wireless communications can be split into two types, local and wide area.

l A local device is similar to a key fob with a button that unlocks a car, a 900 MHz cordless phone, a radio control toy, or a Bluetooth network. l All of these devices operate overshort distances, typically just a few meters.

l Wide area wireless devices operate effectively over a much greater area. A pager or mobile phone is a good example.

l You can talk on your mobile phone to any other phone on the planet. l These devices' greater range relieson a trick, however: a more elaborate landbased network.

l A mobile phone doesn't have that much more radio power than a radio control toy. l What it does have is a network of carefully placed radio antennas (cell towers); the phone can continue to operate as long as it is within range of at least one tower.

l The mobile phone device receives service from a wireless carrier, a company that operates the land-based network.

l While a number of industry consortia and standard bodies, such as the International Telecommunication Union, . . .

l … … are trying to define or foster the development of standards for the wireless world, today's wireless world is still fragmented and complex.

l If you buy a mobile phone in the U. S. today, it might run on Motorola's i. DEN network or Sprint's PCS network.

l Take it overseas to Europe and you'll be out of luck--your phone will not work with Europe's GSM network, nor will it work with the PDC network or any of the other mobile networks that live in Japan.

More information about wireless communications l Making Sense of Cellular gives an introductory overview of the wireless radio spectrum. l World of Wireless Communications provides a brief overview of wireless communications and the concept of an embedded device.