JAVA RING By Sowmya B N Overview Introduction

JAVA RING By Sowmya B N

Overview ØIntroduction ØHistory ØComponents ØWorking ØSecurity ØApplications ØAdvantages ØDisadvantages ØConclusion ØReference

Ø Is a finger ring that contains a small microprocessor with built in capabilities for the user. Ø Is a sort of a smartcard that is wearable on a finger. Ø Is a stainless-steel ring, 16 -millimeters (0. 6 inches) in diameter.
Ø It contains an inexpensive microprocessor in a stainless steel i. Button running a JVM and it is preloaded with applet. Ø The java Ring is an extremely secure Java- Powered electronic token. Ø Java Ring could have a number of real-world application


The Java Ring Ø Contains a tiny Java Virtual Machine Ø Implements the Java Card 2. 0 API Ø Stores information in NVRAM , ROM Ø Runs applets Ø Includes microprocessor, memory, clock and battery


Ø The java ring, which is powered by Java card was introduced at Sun Microsystems's Java. One Conference, in March 1998. Ø It was developed by Dallas Semiconductor. Ø Workstations at the conference had "ring readers" installed on them that downloaded information about the user from the conference registration system. Ø This information was then used to enable a number of personalized services.

Ø Java ring has been tested at Celebration School, an innovative K-12 school, just outside Orlando, FL. The rings are given to students and have been programmed to; Ø store electronic cash to pay for lunches Ø automatically unlock doors Ø take attendance Ø store medical information Ø allow students to check out books. Students simply press the signet of their Java Ring, and it performs the desired function.

Ø The rings given to students are programmed with Java applets that communicate with host applications on networked systems Ø The Java Ring is snapped into a reader, called a Blue Dot receptor, to allow communication between a host system and the Java Ring.

Ø Java Virtual Machine (JVM) Ø RAM Ø ROM Ø real-time clock Ø i. Button Ø Blue dot reciptor

The java virtual machine is the piece of software that recognizes the java language and translates the byte code.

Ø Java ring contains 134 kb of non-volatile random access memory. Ø This non-volatile random access memory offers high read/write speed. Ø It also provides rapid zeroization.

Ø The java ring contains 32 kb of ROM. Ø Special kind of operating system called e- commerce operating system is stored in the ROM.

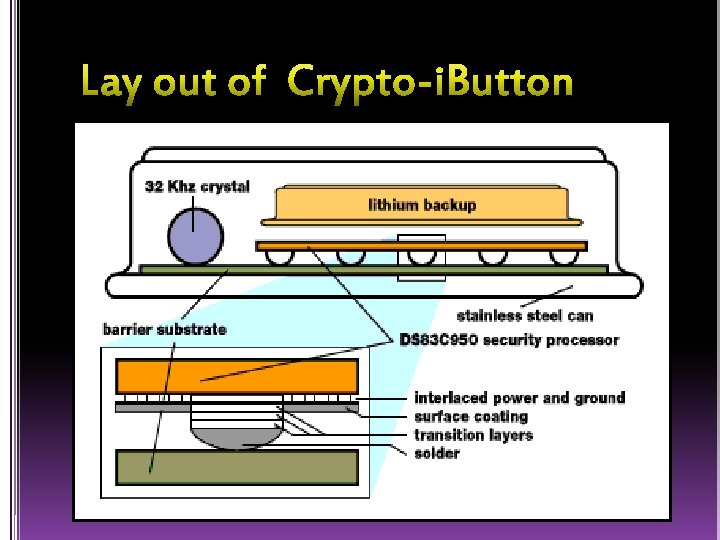
Ø Real time clock gives the exact time of the day and it can run up to 10 years continuously. Ø It is driven by a constant 32 KHz crystal oscillator. Ø In addition , the frequency of the processor clock is not constant ; ranges from 10 -20 MHz. Ø This aspect prohibits hackers in obtaining the information from the i. Button.


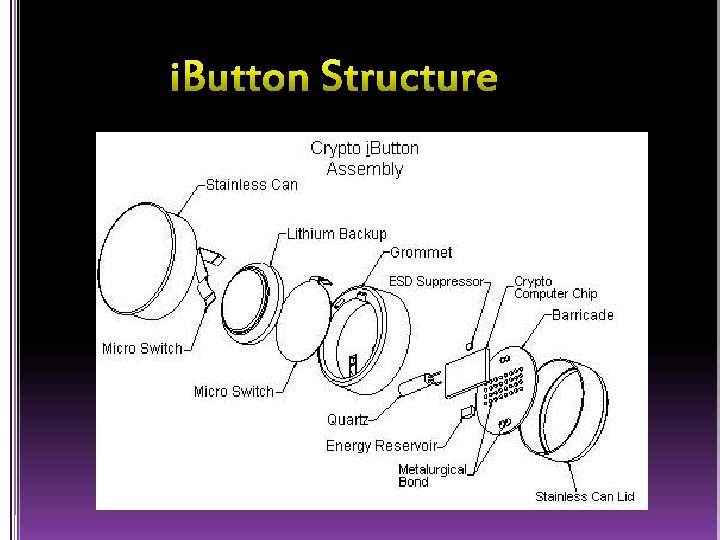
Ø The jewel of the java ring is the i. Button. Ø i. Button is a computer chip enclosed in a thick stainless steel can. Ø It is originally called “touch memory devices they were later renamed as “i. Buttons”. Ø Java ring uses 1 -wire protocol for communication with the host and the i. Button.

Ø The i. Button is a mechanical packaging standard that places a 1 -Wire component inside a small stainless steel "button" similar to a disk-shaped battery. Ø Each i. Button has a unique and unalterable address laser etched onto its chip inside the can. Ø The address can be used as a key or identifier for each i. Button.

Mainly three types of i. Button are in use: 1. Thermochrone i. Button 2. Crypto i. Button 3. Memory i. Button

Ø This includes a thermometer, a clock and a memory. Ø It tracks time and temperature in different environment.

Ø Memories around 64 K can be stored either in typed text or digitized photos. Ø It has ability to operate as mobile databases.
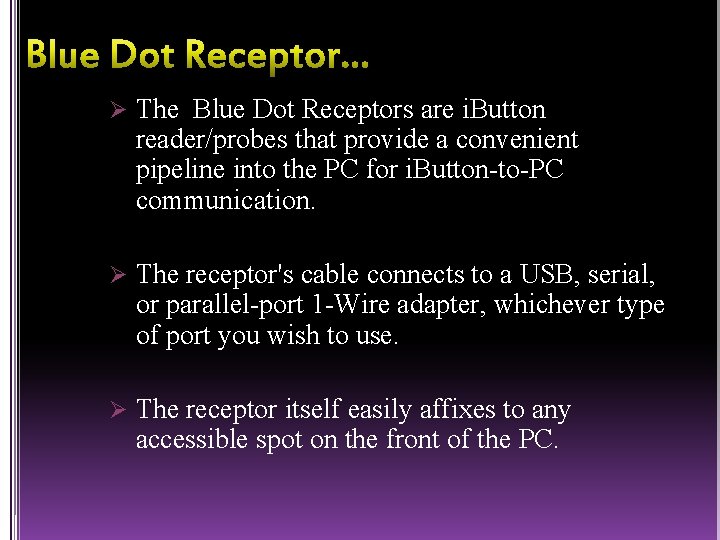
Ø The Blue Dot Receptors are i. Button reader/probes that provide a convenient pipeline into the PC for i. Button-to-PC communication. Ø The receptor's cable connects to a USB, serial, or parallel-port 1 -Wire adapter, whichever type of port you wish to use. Ø The receptor itself easily affixes to any accessible spot on the front of the PC.


q Key features: Ø It has a coiled cable for connecting i. Buttons to 1 -Wire networks. Ø Adhesive pad for mounting on objects. Ø Supports for up to two i. Buttons at once. Ø Can be used with any Dallas Semiconductor port adapter.

Ø Java Ring is programmed with the applets and the programming is done according to our application Ø Whenever the user pushes his ring on a ring reader(Blue Dot Receptor), the corresponding application will take place.


Ø Information is transferred between your i. Button and a PC with a momentary contact at up to 142 kbps. Ø You simply touch your i. Button to a Blue Dot receptor or other i. Button probe, which is connected to a PC. Ø The Blue Dot receptor is cabled to a 1 -Wire adapter that is attached to a spare PC port. 1 Wire adapters exist for USB, serial, and parallel ports.

Ø The barrier substrate and the triple-layer metal construction techniques employed in the silicon fabrication effectively deny unauthorized access to the data stored in the NVRAM. If any attempt is made to penetrate these barriers, the NVRAM data is immediately erased. Ø Java rings are authorized through Personal Identification Numbers (PINs) so that no one can steal a person's ring and use that ring.

The java ring can be used to hold secret codes, credit cards numbers, driver license, other wallet contents, and even some electronic cash. It’s greatest promise appears to lie in its capacity to interact with Internet applications to support strong remote authentication and remotely authorized financial transactions.

Ø For opening the door Ø E-bank application Ø Logging in your PC Ø Providing security in your car.

Ø The Java Rings are very easy and convenient for users. Ø It can function between -40 C to+70 C and in much harsher environment. Ø It has higher durability.

Ø Provides authentication to users which is crucial for many applications. Ø Easier for administrator to maintain the security infrastructure. Ø Provides real memory, more power, and a capacity for dynamic programming

Ø The cost of implementing the system is high. Ø It needs a high level tools and method in order to program application efficiently, reliabily, securily. Ø i. Button has a limited processor capacity and memory , which means an individual might need to carry more than one Java Ring.

Although Java Rings aren't widely used yet, such rings or similar devices could have a number of real-world applications, such as starting your car and having all your vehicle's components (such as the seat, mirrors, and radio selections) automatically adjust to your preferences. The key issue about a wearable computer (java ring) is not whether it is a ring or another form factor: the deciding point is that you will always have it with you.
![[1] http: //www. javaworld. com/ [2]http: //www. electronics. howstuffworks. com/ [3] http: //www. people. [1] http: //www. javaworld. com/ [2]http: //www. electronics. howstuffworks. com/ [3] http: //www. people.](http://slidetodoc.com/presentation_image_h2/3e6ae8d7ff4ffcc721f2b84ae55cac9a/image-37.jpg)
[1] http: //www. javaworld. com/ [2]http: //www. electronics. howstuffworks. com/ [3] http: //www. people. uchicago. edu/

- Slides: 38