Java Messaging Service JMS and Enterprise Messaging Strategy





















- Slides: 72

Java Messaging Service (JMS) and Enterprise Messaging Strategy Author: Dan Mc. Creary Date: 7/20/2004 Version: 0. 1 M D Copyright 2004 -2008 Dan Mc. Creary & Associates 1

Objectives • Understand strategies for computer-to-computer messaging • Understand how vendors attempt to lock-in customers using proprietary communication APIs • Understand why the Java Messaging Service (JMS) is becoming the de -facto vendor-neutral messaging interface between J 2 EE systems and how JMS helps avoid vendor lock-in • Understand the differences between messaging systems • Understand how messaging systems interoperate • Understand how JMS fits in with other EAI architectures such as Web Services, SOA, ESB, Multi-tier architectures, J 2 EE Architecture, JCA, Microsoft Biz. Talk, Rosetta. Net • Understand how future systems will interoperate • Review references M D Copyright 2004 -2008 Dan Mc. Creary & Associates 2

Messaging Strategy Overview 1. Support cost effective reliable messaging between state law enforcement agencies 2. Allow messages to have guaranteed delivery and be fully encrypted 3. Avoid vendor-specific APIs 4. Integrate with search and workflow 5. Be flexible for future standards 6. Make it easy for developers to use M D Copyright 2004 -2008 Dan Mc. Creary & Associates 3

Vendor Lock-In • Definition: When you spend a lot of time and money building your products around a specific vendor's solution. • Vendor lock-in prevents you from moving your application to another vendor or an open-source solution – Vendor lock-in is Bad – Portability between vendors is Good • Successful Enterprise Architecture Strategies attempt to minimize dependencies on any product due to: – – M D Excessive licensing fees Excessive support fees Vendor support for a specific product Vendor stability Copyright 2004 -2008 Dan Mc. Creary & Associates 4

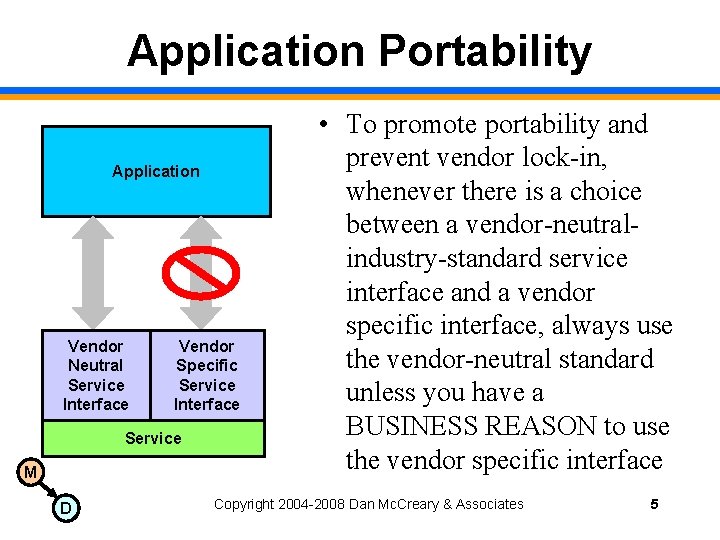
Application Portability Application Vendor Neutral Service Interface Vendor Specific Service Interface Service M D • To promote portability and prevent vendor lock-in, whenever there is a choice between a vendor-neutralindustry-standard service interface and a vendor specific interface, always use the vendor-neutral standard unless you have a BUSINESS REASON to use the vendor specific interface Copyright 2004 -2008 Dan Mc. Creary & Associates 5

What is A Message? • A communication between two things (people, computers) • Typical questions: Joe, Lets mee t for lunc h at the resta urant at 8. - John – Who was the message from? – What is the destination? – Was the message actually received by the recipient? – Was it understood? (what restaurant? , 8 am or 8 pm? ) – Should it be acknowledged? – Could it have been tampered with in transit? – Who really sent it? M D Copyright 2004 -2008 Dan Mc. Creary & Associates 6

Definition Messaging: a method of communication between software components or applications – E-mail is also messaging but it is person to person – In this tutorial, messaging is computer to computer M D Copyright 2004 -2008 Dan Mc. Creary & Associates 7

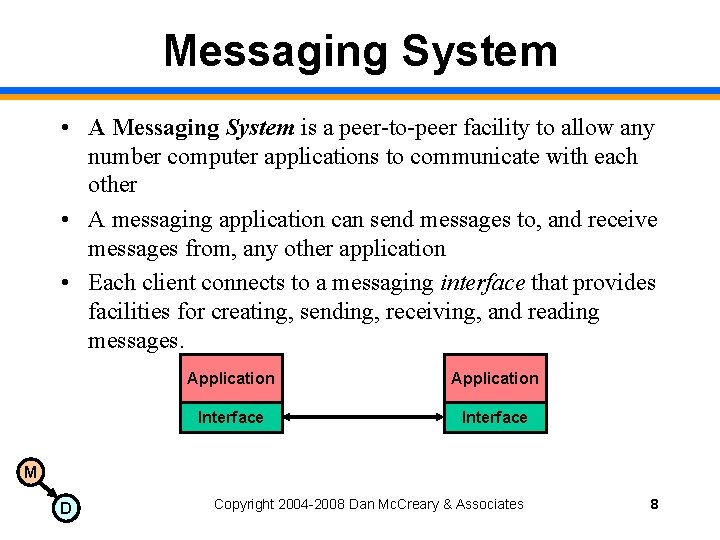
Messaging System • A Messaging System is a peer-to-peer facility to allow any number computer applications to communicate with each other • A messaging application can send messages to, and receive messages from, any other application • Each client connects to a messaging interface that provides facilities for creating, sending, receiving, and reading messages. Application Interface M D Copyright 2004 -2008 Dan Mc. Creary & Associates 8

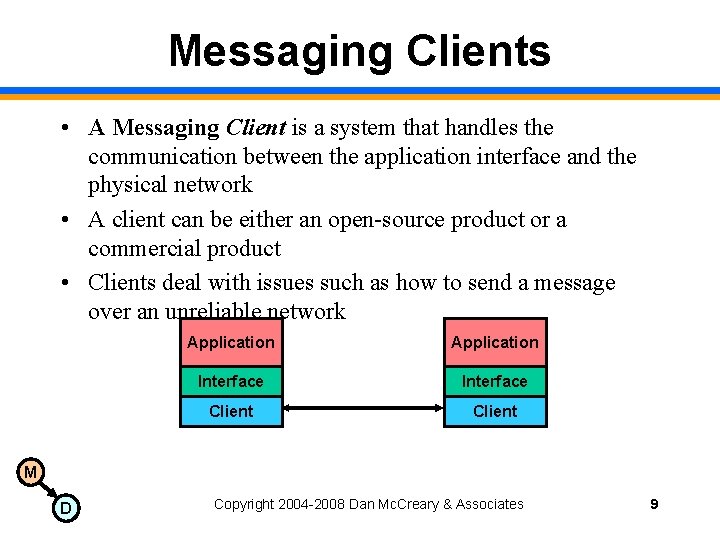
Messaging Clients • A Messaging Client is a system that handles the communication between the application interface and the physical network • A client can be either an open-source product or a commercial product • Clients deal with issues such as how to send a message over an unreliable network Application Interface Client M D Copyright 2004 -2008 Dan Mc. Creary & Associates 9

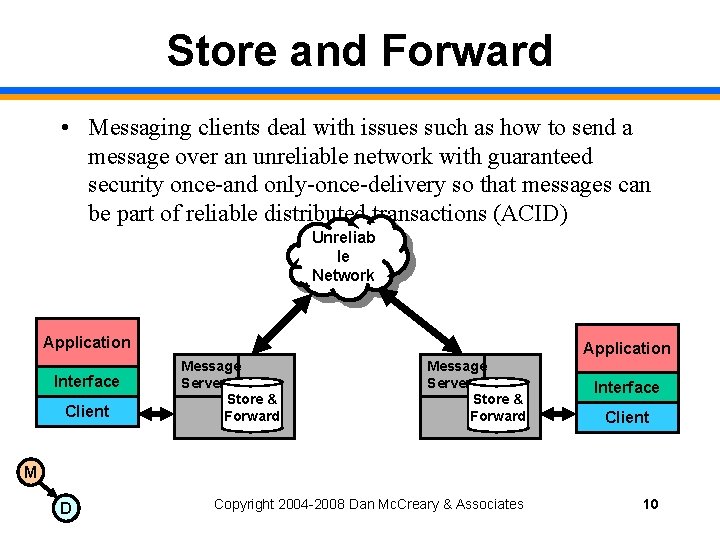
Store and Forward • Messaging clients deal with issues such as how to send a message over an unreliable network with guaranteed security once-and only-once-delivery so that messages can be part of reliable distributed transactions (ACID) Unreliab le Network Application Interface Client Application Message Server Store & Forward Interface Copyright 2004 -2008 Dan Mc. Creary & Associates 10 Client M D

Java Transaction API M • Java Transactions are handled by the Java Transaction API (JTA) • The JTA makes it easy for Java programmers to do complex transactions involving data on multiple J 2 EE systems located over a wide area network (WAN) • JTA depends on Messages Beans (MBean) and therefore JMS • JTA makes ACID transactions possible D Copyright 2004 -2008 Dan Mc. Creary & Associates 11

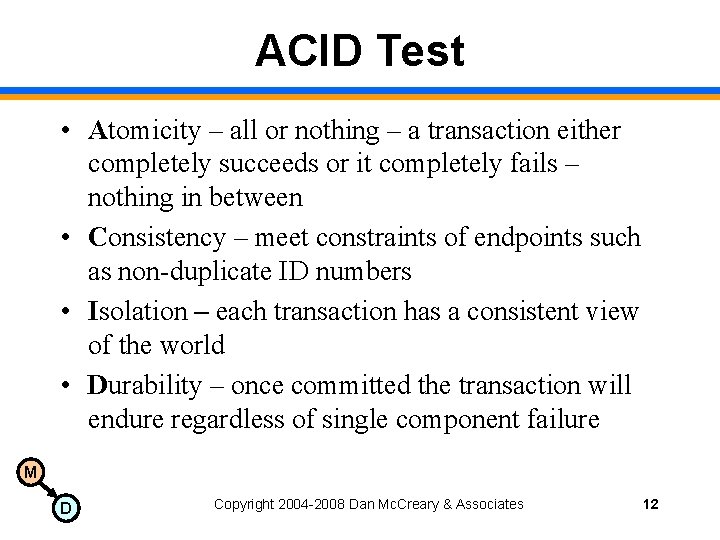
ACID Test • Atomicity – all or nothing – a transaction either completely succeeds or it completely fails – nothing in between • Consistency – meet constraints of endpoints such as non-duplicate ID numbers • Isolation – each transaction has a consistent view of the world • Durability – once committed the transaction will endure regardless of single component failure M D Copyright 2004 -2008 Dan Mc. Creary & Associates 12

A Wire Protocol • A wire protocol is an agreed upon standard between two systems (potentially built with different technologies) that defines how they will communicate with each other Format of messages "on the wire" Examples: HTTP (web), SMTP (mail), SNMP (monitoring) and SOA M D Copyright 2004 -2008 Dan Mc. Creary & Associates 13

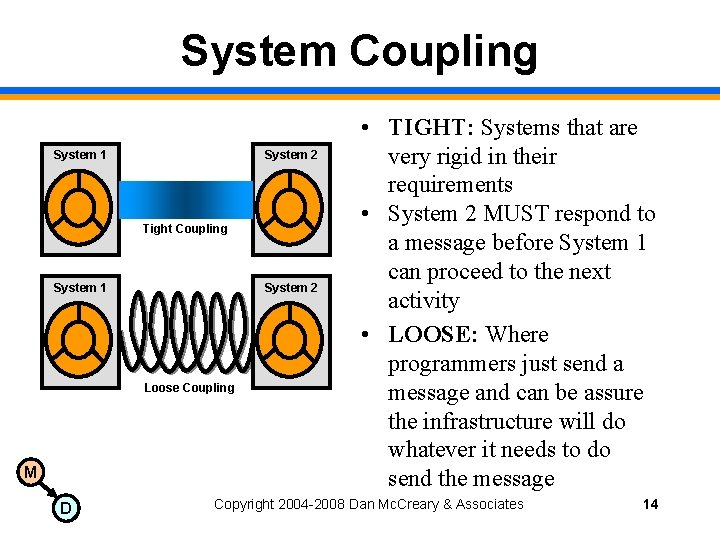
System Coupling System 1 System 2 Tight Coupling System 1 System 2 Loose Coupling M D • TIGHT: Systems that are very rigid in their requirements • System 2 MUST respond to a message before System 1 can proceed to the next activity • LOOSE: Where programmers just send a message and can be assure the infrastructure will do whatever it needs to do send the message Copyright 2004 -2008 Dan Mc. Creary & Associates 14

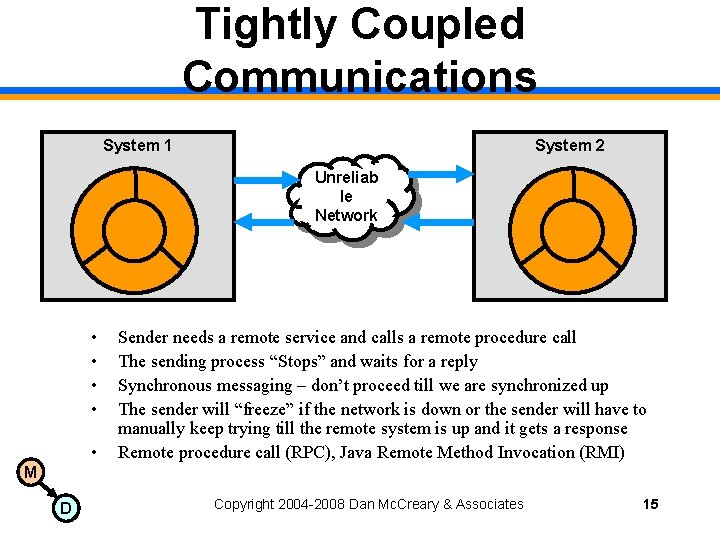
Tightly Coupled Communications System 1 System 2 Unreliab le Network • • • Sender needs a remote service and calls a remote procedure call The sending process “Stops” and waits for a reply Synchronous messaging – don’t proceed till we are synchronized up The sender will “freeze” if the network is down or the sender will have to manually keep trying till the remote system is up and it gets a response Remote procedure call (RPC), Java Remote Method Invocation (RMI) M D Copyright 2004 -2008 Dan Mc. Creary & Associates 15

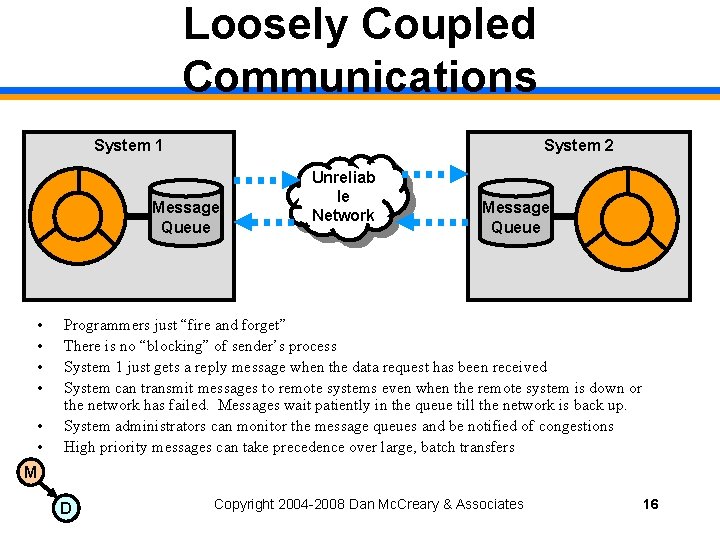
Loosely Coupled Communications System 1 System 2 Message Queue • • • Unreliab le Network Message Queue Programmers just “fire and forget” There is no “blocking” of sender’s process System 1 just gets a reply message when the data request has been received System can transmit messages to remote systems even when the remote system is down or the network has failed. Messages wait patiently in the queue till the network is back up. System administrators can monitor the message queues and be notified of congestions High priority messages can take precedence over large, batch transfers M D Copyright 2004 -2008 Dan Mc. Creary & Associates 16

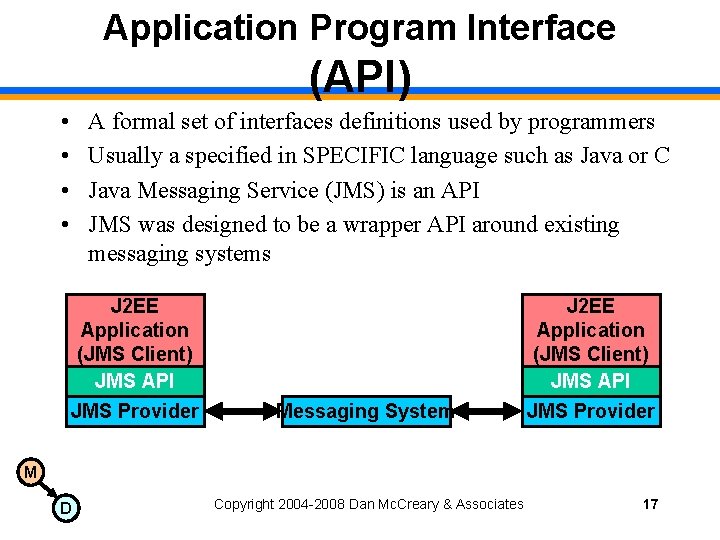
Application Program Interface (API) • • A formal set of interfaces definitions used by programmers Usually a specified in SPECIFIC language such as Java or C Java Messaging Service (JMS) is an API JMS was designed to be a wrapper API around existing messaging systems J 2 EE Application (JMS Client) JMS API JMS Provider Messaging System J 2 EE Application (JMS Client) JMS API JMS Provider M D Copyright 2004 -2008 Dan Mc. Creary & Associates 17

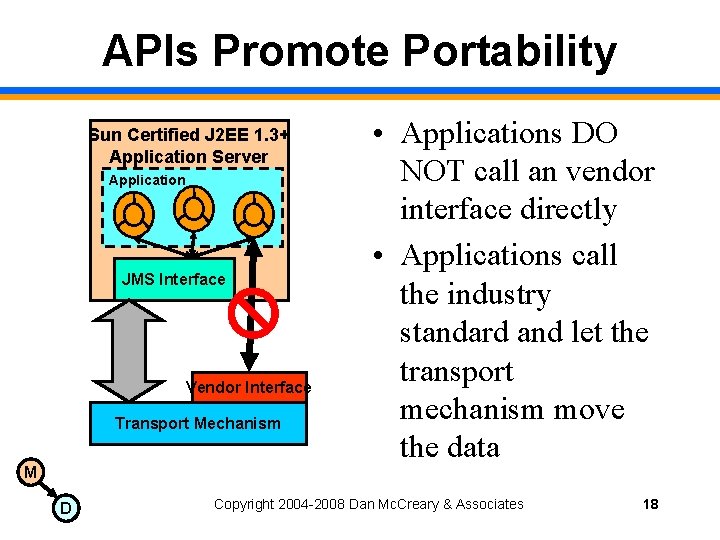
APIs Promote Portability Sun Certified J 2 EE 1. 3+ Application Server Application JMS Interface Vendor Interface Transport Mechanism M D • Applications DO NOT call an vendor interface directly • Applications call the industry standard and let the transport mechanism move the data Copyright 2004 -2008 Dan Mc. Creary & Associates 18

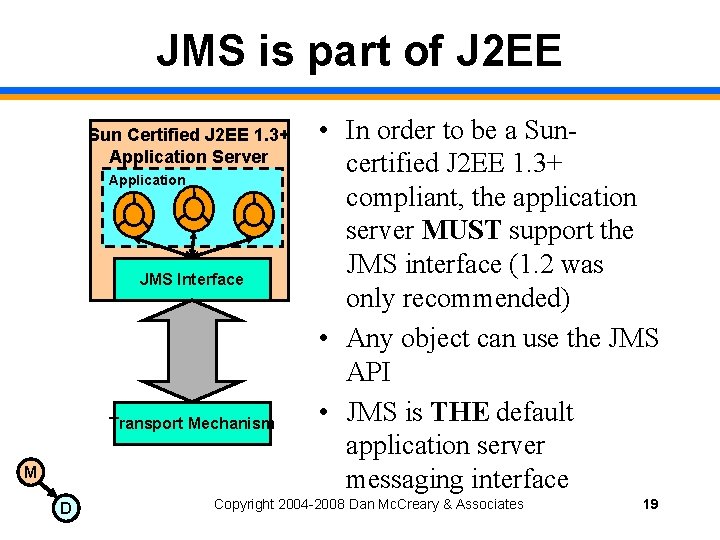
JMS is part of J 2 EE Sun Certified J 2 EE 1. 3+ Application Server Application JMS Interface Transport Mechanism M D • In order to be a Suncertified J 2 EE 1. 3+ compliant, the application server MUST support the JMS interface (1. 2 was only recommended) • Any object can use the JMS API • JMS is THE default application server messaging interface Copyright 2004 -2008 Dan Mc. Creary & Associates 19

JMS Details • JMS is a Messaging API Specification • Published and maintained by Sun Microsystems • First published in August 1998. • Latest version is Version 1. 0. 2 b • See http: //java. sun. com/products/jms/ M D Copyright 2004 -2008 Dan Mc. Creary & Associates 20

Goals of JMS • Minimizes the set of concepts a programmer must learn to use messaging products (programmer friendly) • Provides enough features to support sophisticated messaging applications • Maximize the portability of JMS applications across JMS providers in the same messaging domain M D Copyright 2004 -2008 Dan Mc. Creary & Associates 21

Benefits of JMS M • Simplifies enterprise development • Allows loosely coupled systems (systems that don't block each other) • Provides reliable messaging over an unreliable network • Promotes secure messaging between systems • Messages between JMS systems can be encrypted D Copyright 2004 -2008 Dan Mc. Creary & Associates 22

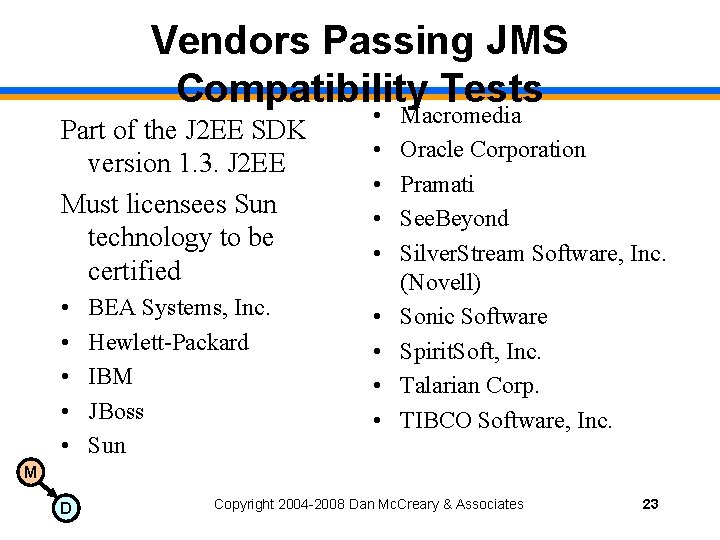
Vendors Passing JMS Compatibility Tests Part of the J 2 EE SDK version 1. 3. J 2 EE Must licensees Sun technology to be certified • • • BEA Systems, Inc. Hewlett-Packard IBM JBoss Sun • • • Macromedia Oracle Corporation Pramati See. Beyond Silver. Stream Software, Inc. (Novell) Sonic Software Spirit. Soft, Inc. Talarian Corp. TIBCO Software, Inc. M D Copyright 2004 -2008 Dan Mc. Creary & Associates 23

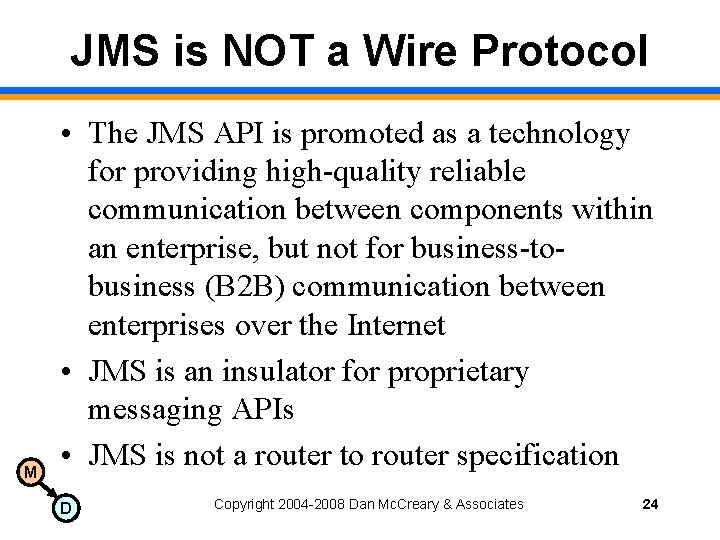
JMS is NOT a Wire Protocol M • The JMS API is promoted as a technology for providing high-quality reliable communication between components within an enterprise, but not for business-tobusiness (B 2 B) communication between enterprises over the Internet • JMS is an insulator for proprietary messaging APIs • JMS is not a router to router specification D Copyright 2004 -2008 Dan Mc. Creary & Associates 24

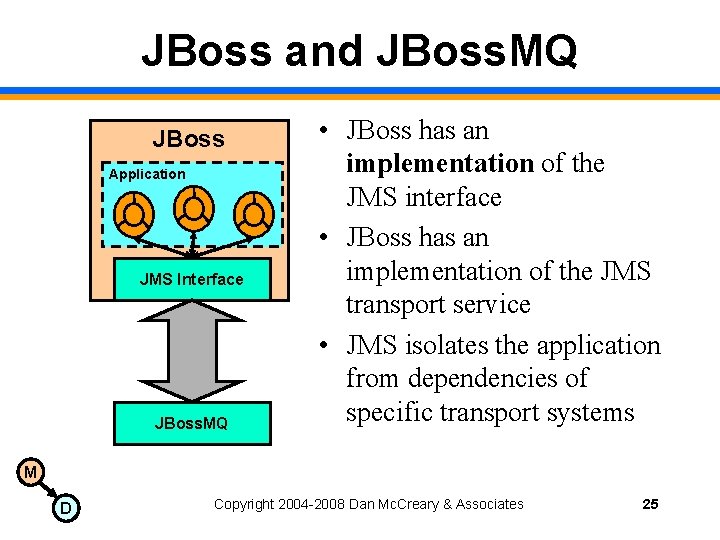
JBoss and JBoss. MQ JBoss Application JMS Interface JBoss. MQ • JBoss has an implementation of the JMS interface • JBoss has an implementation of the JMS transport service • JMS isolates the application from dependencies of specific transport systems M D Copyright 2004 -2008 Dan Mc. Creary & Associates 25

JBoss. MQ • Initially released as spyder. MQ • "clean room" implementation – programmers given an interface specification but have never seen similar systems – very low risk of copyright infringement • First release April 2000 • Active users migrated from standalone spyder. MQ to JBoss. MQ M D Copyright 2004 -2008 Dan Mc. Creary & Associates 26

JBoss. MQ • Full implementation of JMS specification including: – Point-to-point – Publish-subscribe – Durable subscribers – JMS Application Server Facilities – Global work units can be coordinated by transaction manager M D Copyright 2004 -2008 Dan Mc. Creary & Associates 27

When to Use a JMS Interface? • The provider wants the components not to depend on information about other components' interfaces, so that components can be easily replaced • The provider wants the application to run whether or not all components are up and running simultaneously • The application business model allows a component to send information to another and to continue to operate without receiving an immediate response M D Copyright 2004 -2008 Dan Mc. Creary & Associates 28

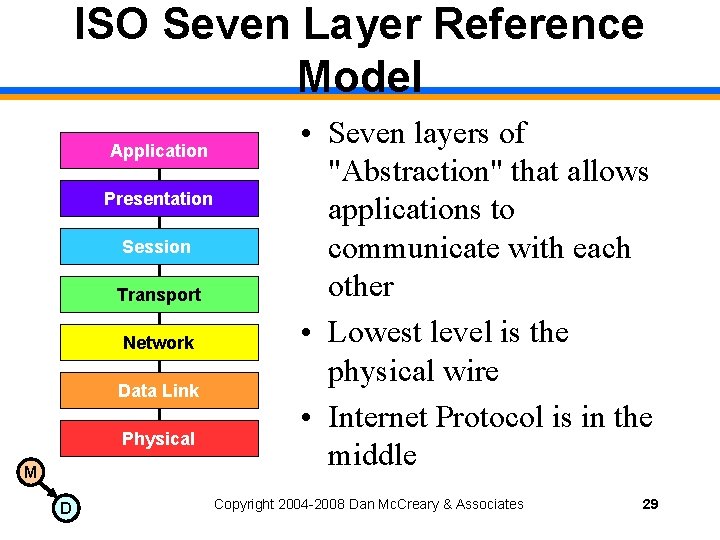
ISO Seven Layer Reference Model Application Presentation Session Transport Network Data Link Physical M D • Seven layers of "Abstraction" that allows applications to communicate with each other • Lowest level is the physical wire • Internet Protocol is in the middle Copyright 2004 -2008 Dan Mc. Creary & Associates 29

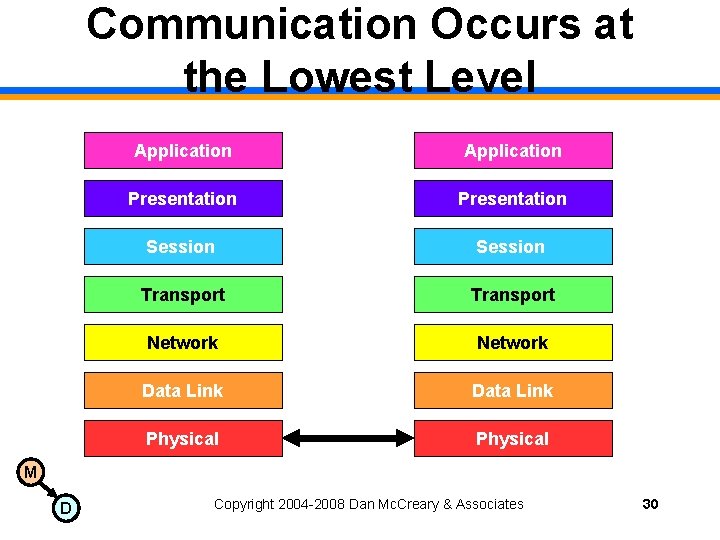
Communication Occurs at the Lowest Level Application Presentation Session Transport Network Data Link Physical M D Copyright 2004 -2008 Dan Mc. Creary & Associates 30

What is a "Common Language"? Problem Solving Conversation Sentences Words Phonemes Sound M D Copyright 2004 -2008 Dan Mc. Creary & Associates 31

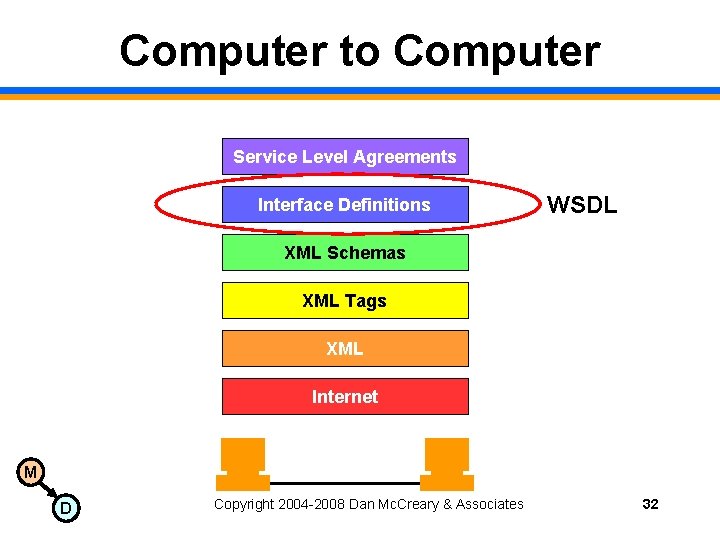
Computer to Computer Service Level Agreements Interface Definitions WSDL XML Schemas XML Tags XML Internet M D Copyright 2004 -2008 Dan Mc. Creary & Associates 32

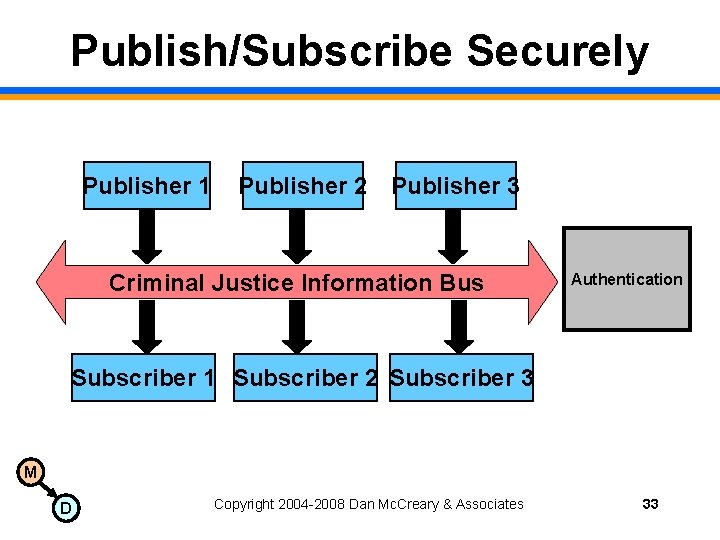
Publish/Subscribe Securely Publisher 1 Publisher 2 Publisher 3 Criminal Justice Information Bus Authentication Subscriber 1 Subscriber 2 Subscriber 3 M D Copyright 2004 -2008 Dan Mc. Creary & Associates 33

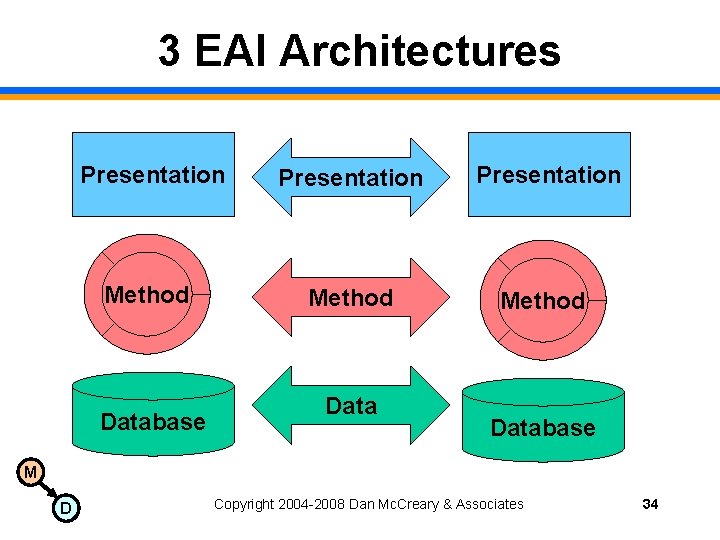
3 EAI Architectures Presentation Method Database M D Copyright 2004 -2008 Dan Mc. Creary & Associates 34

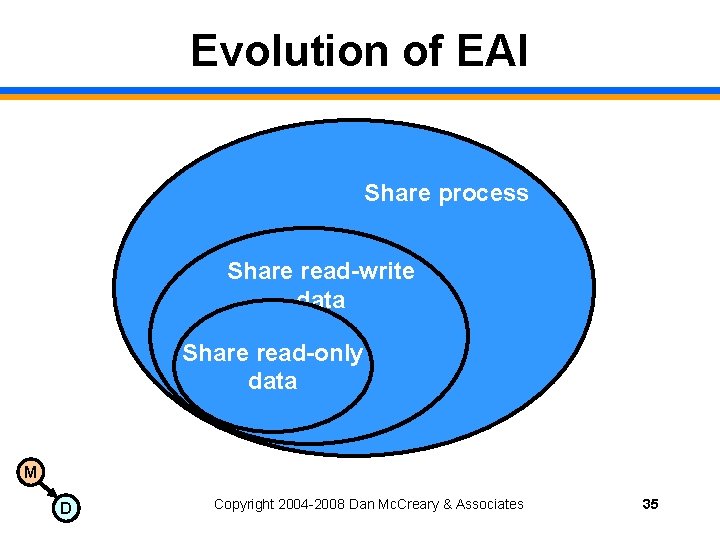
Evolution of EAI Share process Share read-write data Share read-only data M D Copyright 2004 -2008 Dan Mc. Creary & Associates 35

Why Share Process? • Sharing data requires you to know who has the right data: the synchronization problem and the metadata problem. • Sharing process allows you to avoid rewriting code. • Quality of data is dependant on the process that validate it. M D Copyright 2004 -2008 Dan Mc. Creary & Associates 36

Challenges: Share Process and Data • Allow any application developer to easily allow both user and programmatic access to application services. • Often requires developers to reconceptualize their applications as a series of published services: e. g. Web Service M D Copyright 2004 -2008 Dan Mc. Creary & Associates 37

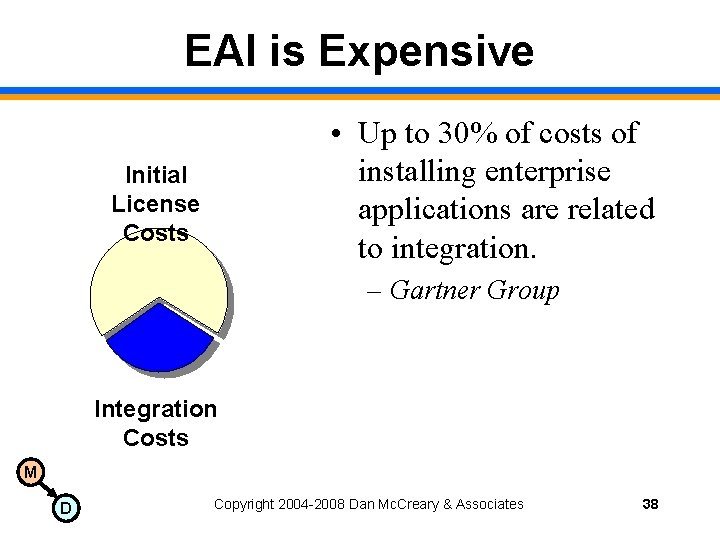
EAI is Expensive • Up to 30% of costs of installing enterprise applications are related to integration. Initial License Costs – Gartner Group Integration Costs M D Copyright 2004 -2008 Dan Mc. Creary & Associates 38

Asynchronous Messaging • Ways that objects communicate • A service of the underlying operating system • Allows programmers to “fire and forget” M D Copyright 2004 -2008 Dan Mc. Creary & Associates 39

Message Brokers Use of a broker will reduce these integration costs by one-third. During maintenance, when a single change to an application can have a rippling effect on several to several dozen interfaces, use of a broker can reduce costs by two-thirds. “ - Gartner Group M D Copyright 2004 -2008 Dan Mc. Creary & Associates 40

Message Queuing • Message Oriented Middleware – Product Classification • IBM MQSeries - Product • Microsoft MSMQ - Product • Java 2 Enterprise Edition (J 2 EE 1. 4)- J 2 EE – Application Server Standard • Java Messaging Service - JMS M D Copyright 2004 -2008 Dan Mc. Creary & Associates 41

Messaging Benefits • Messaging infrastructure guarantees reliable delivery of a message • Once and only once delivery • Messages can have different priority • Transactional control • Transactions can be grouped together • Support of “undo” – reversible operations M D Copyright 2004 -2008 Dan Mc. Creary & Associates 42

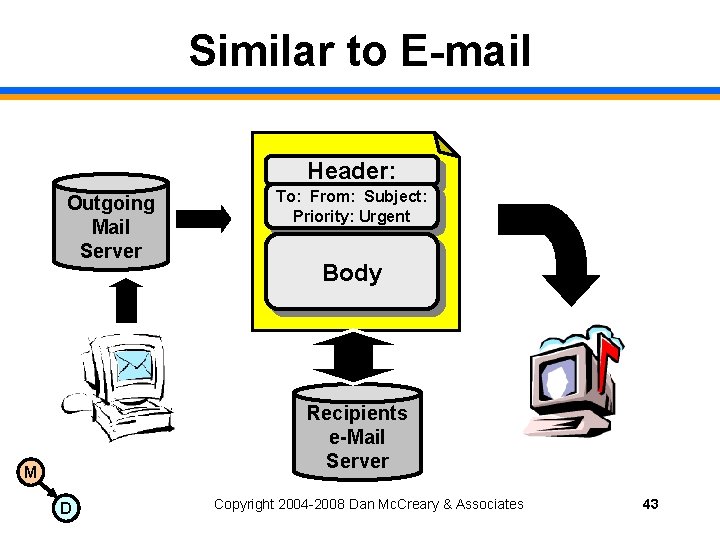
Similar to E-mail Header: Outgoing Mail Server To: From: Subject: Priority: Urgent Body Recipients e-Mail Server M D Copyright 2004 -2008 Dan Mc. Creary & Associates 43

When we send e-mail… • Sender sends a message to the outgoing email server using a standard format ( e. g. Simple Mail Transfer Protocol) • Message is routed to receiver’s e-mail server • Message stored in e-mail server till the receiver picks up the message • Example of asynchronous processing M D Copyright 2004 -2008 Dan Mc. Creary & Associates 44

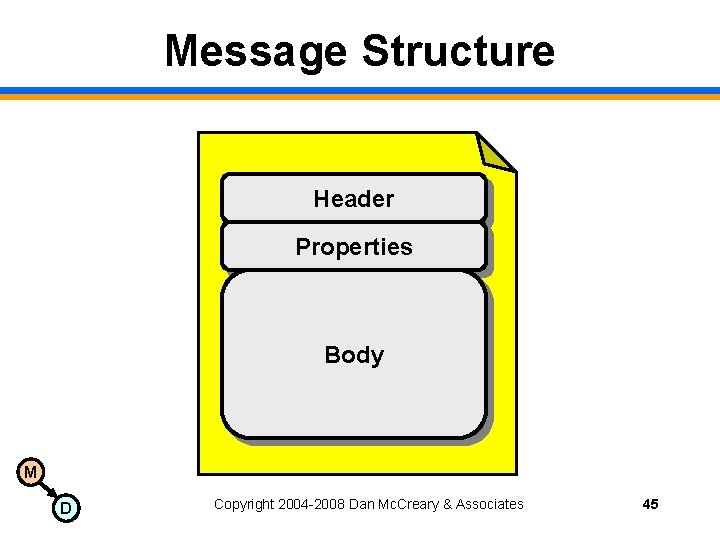
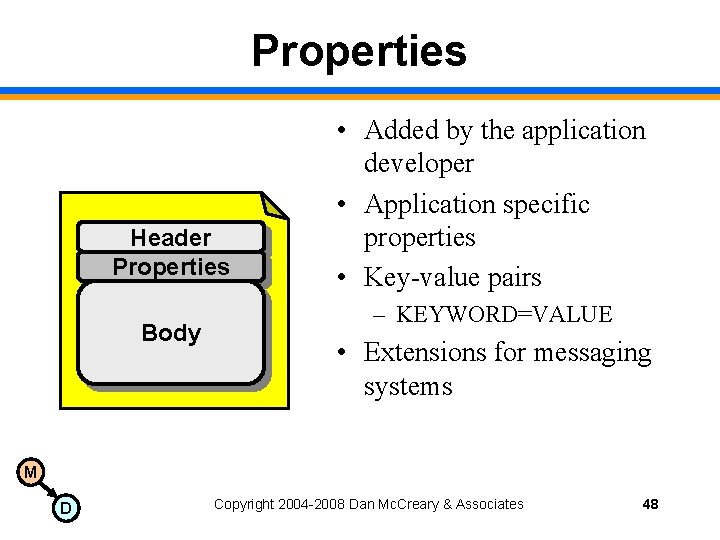
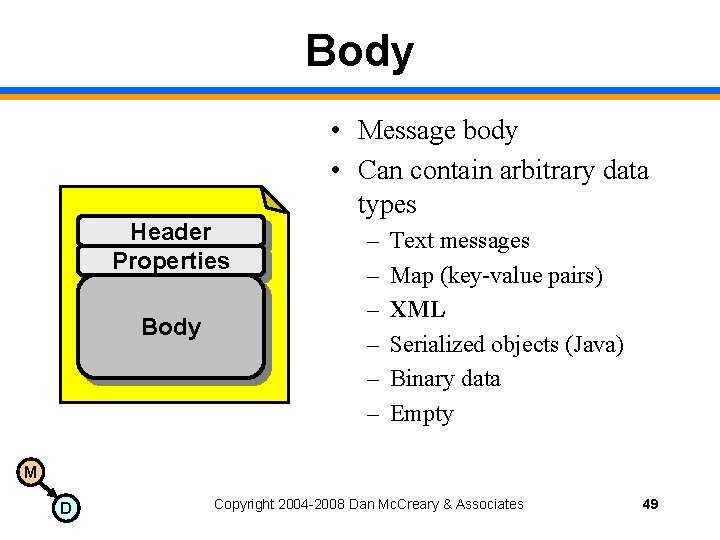
Message Structure Header Properties Body M D Copyright 2004 -2008 Dan Mc. Creary & Associates 45

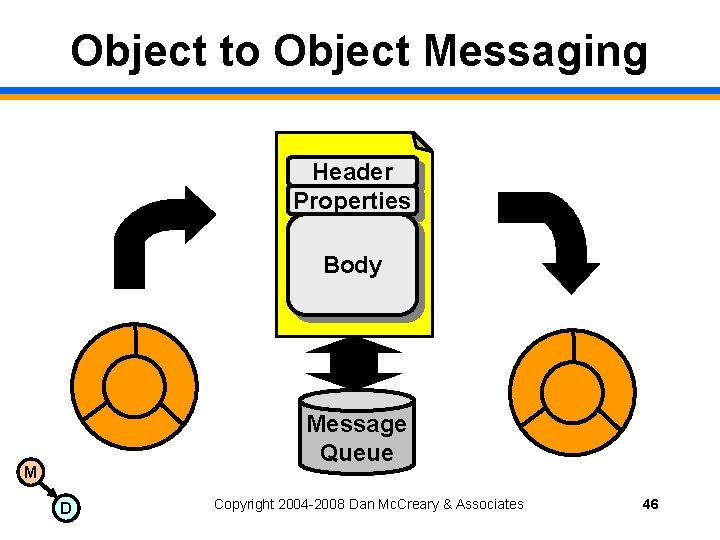
Object to Object Messaging Header Properties Body Message Queue M D Copyright 2004 -2008 Dan Mc. Creary & Associates 46

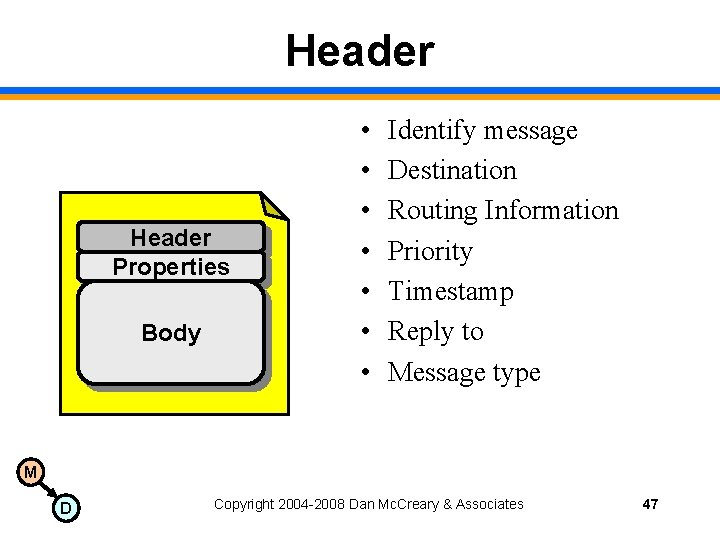
Header Properties Body • • Identify message Destination Routing Information Priority Timestamp Reply to Message type M D Copyright 2004 -2008 Dan Mc. Creary & Associates 47

Properties Header Properties Body • Added by the application developer • Application specific properties • Key-value pairs – KEYWORD=VALUE • Extensions for messaging systems M D Copyright 2004 -2008 Dan Mc. Creary & Associates 48

Body Header Properties Body • Message body • Can contain arbitrary data types – – – Text messages Map (key-value pairs) XML Serialized objects (Java) Binary data Empty M D Copyright 2004 -2008 Dan Mc. Creary & Associates 49

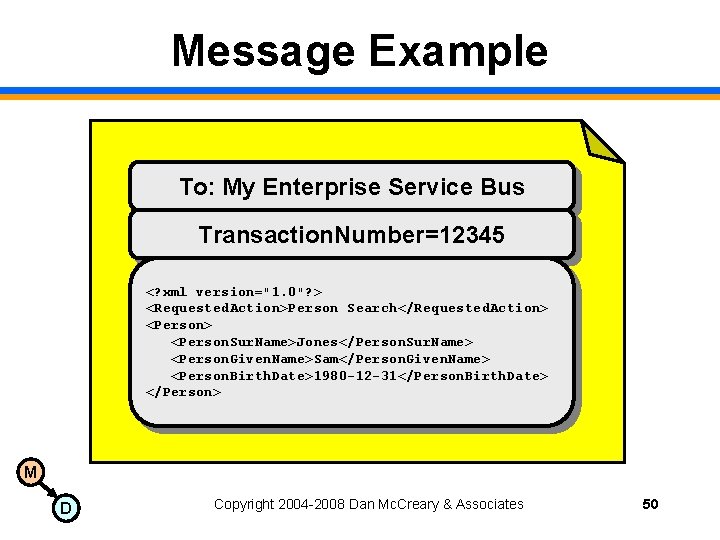
Message Example To: My Enterprise Service Bus Transaction. Number=12345 <? xml version="1. 0"? > <Requested. Action>Person Search</Requested. Action> <Person. Sur. Name>Jones</Person. Sur. Name> <Person. Given. Name>Sam</Person. Given. Name> <Person. Birth. Date>1980 -12 -31</Person. Birth. Date> </Person> M D Copyright 2004 -2008 Dan Mc. Creary & Associates 50

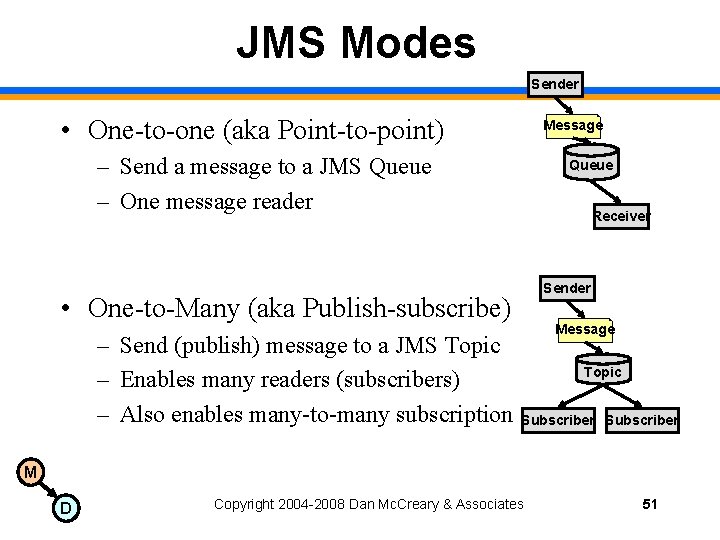
JMS Modes Sender • One-to-one (aka Point-to-point) Message – Send a message to a JMS Queue – One message reader Queue Receiver Sender • One-to-Many (aka Publish-subscribe) – Send (publish) message to a JMS Topic – Enables many readers (subscribers) – Also enables many-to-many subscription Message Topic Subscriber M D Copyright 2004 -2008 Dan Mc. Creary & Associates 51

Required Header Types • Automatic – automatically put in EVERY message by the system • Developer-Assigned – required headers that must be set before a send() M D Copyright 2004 -2008 Dan Mc. Creary & Associates 52

Automatic Header Information • Destination – where to send the message (either a queue or a topic) • Delivery. Mode – reliable or not • Message. ID – number that identifies the message • Timestamp – date and time that send() was called • Expiration – time to live in milliseconds – by default is does not expire • Redelivered – not the first try • Priority – Should this message be expedited? M D Copyright 2004 -2008 Dan Mc. Creary & Associates 53

Priority Messages • The JMS API defines ten levels of priority value • 0 as the lowest priority • 9 as the highest • 0 -4 are gradations of normal priority and priorities • 5 -9 are gradations of expedited priority M D Copyright 2004 -2008 Dan Mc. Creary & Associates 54

Developer Assigned • Reply. To – who should the receiver send a reply to • Corrlation. ID – how this message is related to previous messages • Type – The type of the payload – binary, text, XML etc. M D Copyright 2004 -2008 Dan Mc. Creary & Associates 55

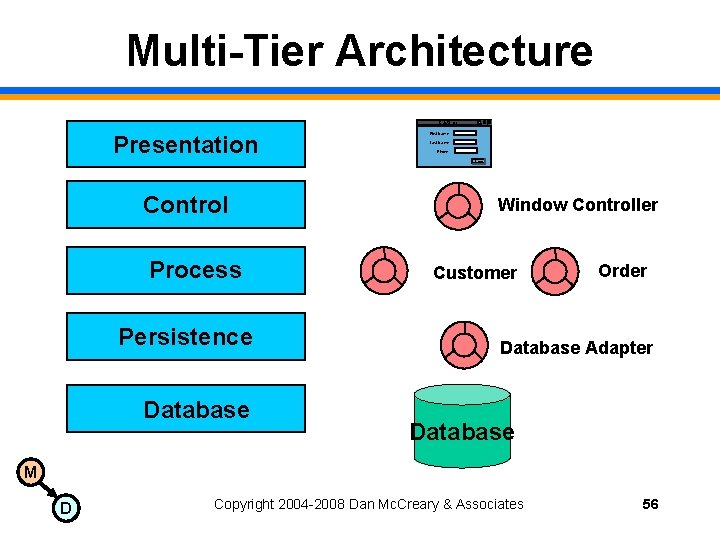
Multi-Tier Architecture Customer Presentation First Name: Last Name: Phone: Save Control Process Persistence Database Window Controller Customer Order Database Adapter Database M D Copyright 2004 -2008 Dan Mc. Creary & Associates 56

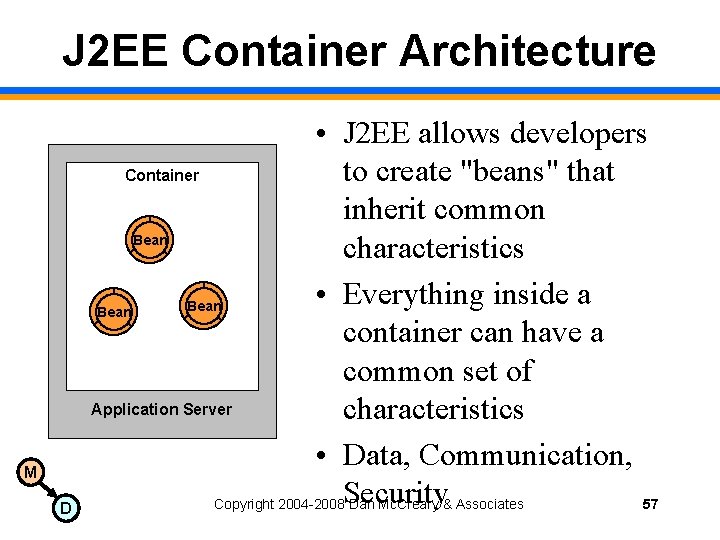
J 2 EE Container Architecture M D • J 2 EE allows developers to create "beans" that Container inherit common Bean characteristics • Everything inside a Bean container can have a common set of Application Server characteristics • Data, Communication, Copyright 2004 -2008 Security Dan Mc. Creary & Associates 57

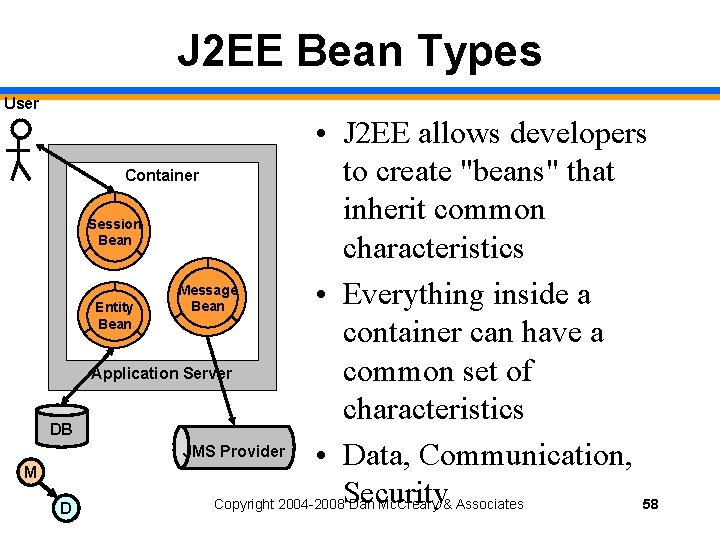
J 2 EE Bean Types User DB M D • J 2 EE allows developers to create "beans" that Container inherit common Session Bean characteristics Message • Everything inside a Bean Entity Bean container can have a Application Server common set of characteristics JMS Provider • Data, Communication, Copyright 2004 -2008 Security Dan Mc. Creary & Associates 58

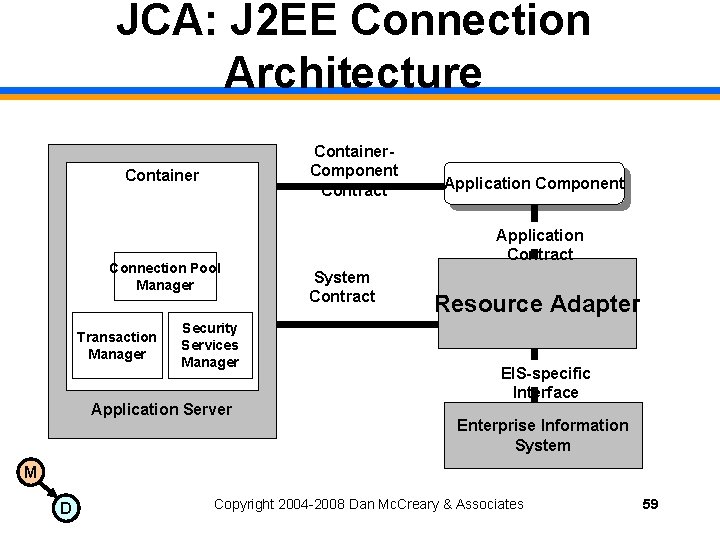
JCA: J 2 EE Connection Architecture Container. Component Contract Container Connection Pool Manager Transaction Manager Security Services Manager Application Server Application Component Application Contract System Contract Resource Adapter EIS-specific Interface Enterprise Information System M D Copyright 2004 -2008 Dan Mc. Creary & Associates 59

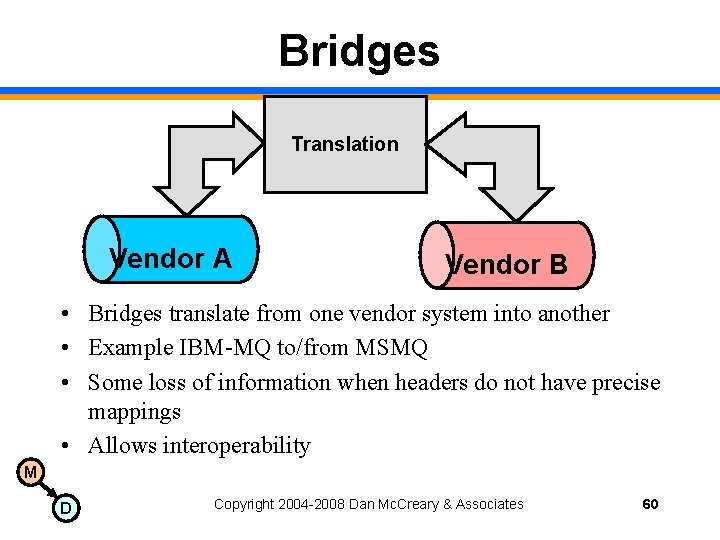
Bridges Translation Vendor A Vendor B • Bridges translate from one vendor system into another • Example IBM-MQ to/from MSMQ • Some loss of information when headers do not have precise mappings • Allows interoperability M D Copyright 2004 -2008 Dan Mc. Creary & Associates 60

JMS and Web Services M • Web service are similar yet different from JMS • Web services is vendor and language neutral (works with Microsoft, C#, VB etc. ) • Web service can have semantically clear published interfaces • Web service are not inherently reliable and do not offer standards for retransmission • Built on SOAP which is extensible D Copyright 2004 -2008 Dan Mc. Creary & Associates 61

SOAP is a wire protocol for exchanging messages SOAP Document SOAP Header SOAP Body • Any XML tags can be added to SOAP header to tell the receiving system how to transmit the message • Security can also be added • Must agree on what tags to use M D Copyright 2004 -2008 Dan Mc. Creary & Associates 62

Future WS-Reliable, WSSecure • New web-service standards to provide wireprotocol reliable and secure web services • Emerging standards from IBM, Microsoft, TIBCO etc. • Sun, Oracle have a similar standard WSReliability • Wait for standards to shake out before adopting M D Copyright 2004 -2008 Dan Mc. Creary & Associates 63

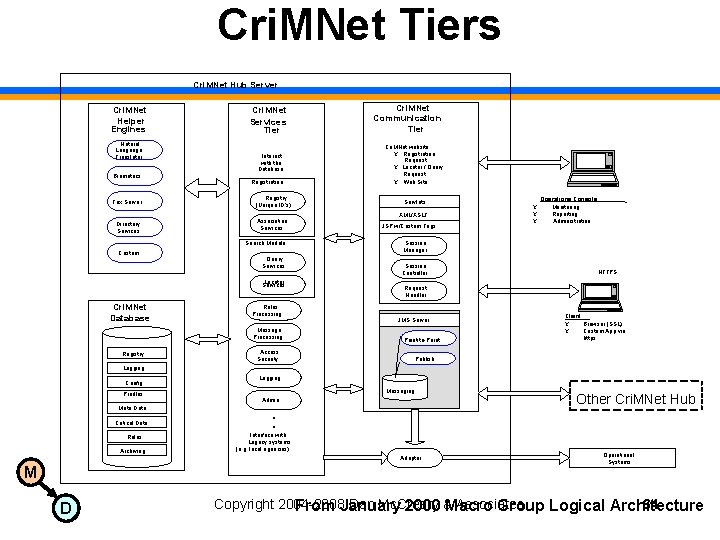
Cri. MNet Tiers Cri. MNet Hub Server Cri. MNet Helper Engines Natural Language Translator Biometrics Cri. MNet Services Tier Interact with the Database Registration Fax Server Registry (Unique ID’s) Directory Services Association Services Search Module Custom Query Services Locator Services Cri. MNet Database Rules Processing Message Processing Registry Cri. MNet Communication Tier Cri. MNet website Ÿ Registration Request Ÿ Locater / Query Request Ÿ Web Site Servlets XML/XSLT JSP w/Custom Tags Ÿ Ÿ Ÿ Operations Console Monitoring, Reporting, Administration Session Manager Session Controller HTTPS Request Handler JMS Server Point-to-Point Access Security Client Ÿ Browser (SSL) Ÿ Custom App via https Publish Logging Config Profiles Meta Data Critical Data Rules Archiving Logging Messaging Admin . . . Interface with Legacy systems (e. g. local agencies) Adaptor M D Other Cri. MNet Hub Operational Systems Copyright 2004 -2008 Dan Mc. Creary Associates 64 From January 2000 &Macro Group Logical Architecture

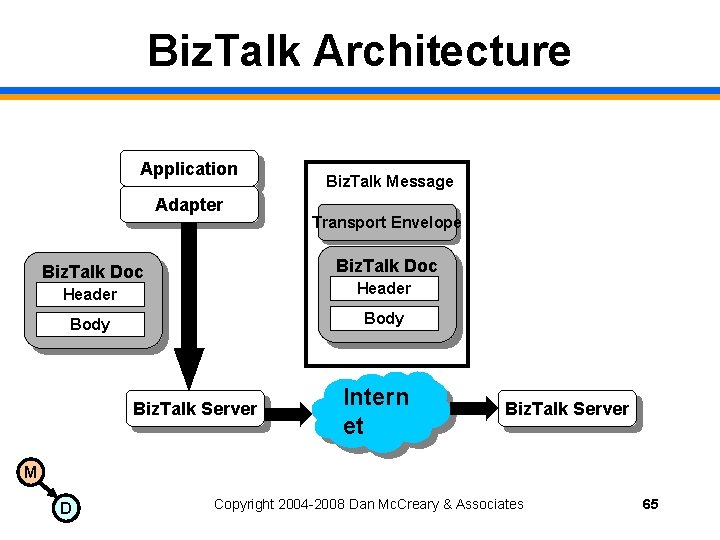
Biz. Talk Architecture Application Adapter Biz. Talk Message Transport Envelope Biz. Talk Doc Header Body Biz. Talk Server Intern et Biz. Talk Server M D Copyright 2004 -2008 Dan Mc. Creary & Associates 65

Biz. Talk Constraints • Protocols are proprietary to Microsoft • XLang is only used by Microsoft • All endpoints are MSMQ M D Copyright 2004 -2008 Dan Mc. Creary & Associates 66

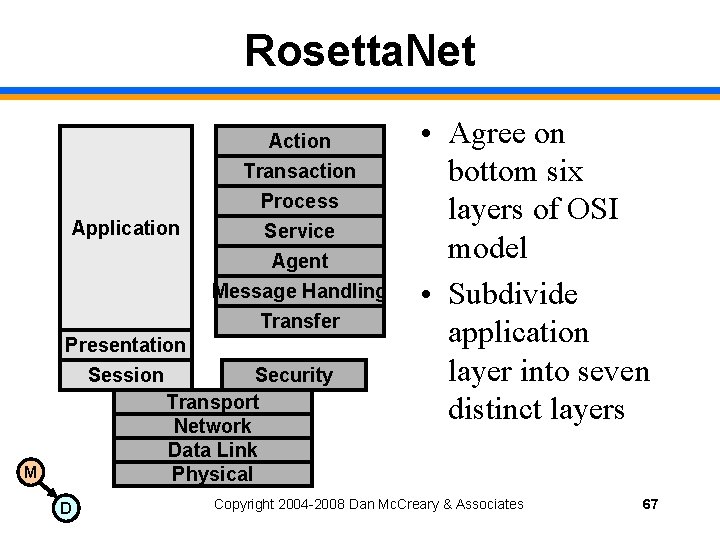
Rosetta. Net Application Action Transaction Process Service Agent Message Handling Transfer M Presentation Session Security Transport Network Data Link Physical D • Agree on bottom six layers of OSI model • Subdivide application layer into seven distinct layers Copyright 2004 -2008 Dan Mc. Creary & Associates 67

JMS and ESB "An ESB can be a sensible first step toward a systematic Enterprise Nervous System because it provides the basic connectivity backbone. It can interoperate with a variety of disparate application servers simultaneously, smoothing over technical differences and also providing services for communication and integration. ” M Roy Schulte VP and Research Fellow Gartner Research D Copyright 2004 -2008 Dan Mc. Creary & Associates 68

References • Best high-level book for EAI architects using J 2 EE – J 2 EE Connector Architecture and Enterprise Application Integration (by Sharma, Stearns and Ng) M D Copyright 2004 -2008 Dan Mc. Creary & Associates 69

JMS Textbooks 1. 2. 3. M D Java Message Service by Richard Monson-Haefel and David Chappell Good explanation on how to use JMS for programmers Java Message Service API Tutorial and Reference: Messaging for the J 2 EE Platform by Mark Hapner, Rich Burridge, Rahul Sharma, Joseph Fialli, Kim Haase Enterprise JMS Programming by Shaun Terry Copyright 2004 -2008 Dan Mc. Creary & Associates 70

JBoss. MQ • JBoss Administration and Development by Marc Fleury, Scott Stark • Chapter 4 has an excellent chapter on JMS and JBoss. MQ • Chapter 6 covers Transactions • Chapter 7 covers Connector Architecture • (book only covers JBoss up to 2. 4. x) M D Copyright 2004 -2008 Dan Mc. Creary & Associates 71

Thank You! Please contact me for more information: • • Enterprise Service Bus Native XML Databases Metadata Management Metadata Registries Service Oriented Architectures Business Intelligence and Data Warehouse Semantic Web Dan Mc. Creary, President Dan Mc. Creary & Associates Metadata Strategy Development dan@danmccreary. com (952) 931 -9198 M D Copyright 2004 -2008 Dan Mc. Creary & Associates 72